Abstract
In this paper, the optimization of downlink beamforming vectors, uplink transmission power, and power-splitting factors is investigated for a secure two-way SWIPT network in the presence of a hidden eavesdropper and non-linear energy harvesting circuits over both perfect and imperfect channels. The eavesdropper is inactive, so its channel information is not available at the base stations (BSs). The purpose of artificial noise is to create downlink interference with the hidden eavesdropper as much as possible, while satisfying the quality of service for two-way communications. For perfect downlink channels, the semidefinite relaxation (SDR) technique is exploited, and the optimal matrices are proven to satisfy rank-1 conditions, thus providing the optimal beamforming vectors. For imperfect downlink channel state information, we propose an iterative algorithm with a penalty function to obtain the approximate rank-1 matrices. On uplink, we attain the optimal transmission power for users receiving maximum ratio transmission beamforming at the BSs. Eventually, the numerical experiments show the superiority of the proposed scheme, compared to a conventional scheme, in terms of signal-to-interference-plus-noise ratio at the eavesdropper.
1. Introduction
In the novel fifth-generation (5G) network, there exist many potential techniques, such as full-duplexing, simultaneous wireless information and power transfer (SWIPT), and multiple-antenna arrays, to boost the efficiency of spectral and energy transmission as well as to eliminate bottlenecks for energy-constrained wireless users [1,2,3,4,5]. The full-duplex scheme provides the capability of bidirectional transmission over the same time and frequency. Thus, the two-way network can be designed with the potential twofold efficiency of spectral and energy. Moreover, [6] introduces three prospective multiple-antenna techniques including cell-free massive multiple-input multiple-output (MIMO), beamspace massive MIMO, and intelligent reflecting surfaces (IRS) in beyond 5G networks. The first one proposes many multiple-antenna access points that jointly provides services for a much smaller number of users on the same wireless resource. The second one focuses on using the spatial structure of the channels and transceiver precoders to reduce the implementation complexity of massive MIMO while the last one exploits the controllable phase-shift of metasurfaces to change the main direction of the reflected signal with only small operational energy.
Along with enhancing spectral use, wireless users can harvest energy from a radio frequency (RF) source via SWIPT transmission to process information and prolong battery life. Stable and controllable SWIPT energy is extremely useful for networks with low-power devices, such as wireless sensor systems [5,7]. In addition, the energy users have difficulty harvesting a large amount of energy due to the exponential attenuation of RF waves in wireless propagation. Thus, the SWIPT signal normally has a strong power to guarantee for an energy harvesting (EH) threshold. A practical model of the EH circuit is a non-linear function of input signal power instead of the linear model of theoretical assumptions [8,9]. As a result, resource allocation for a non-linear SWIPT network needs to re-optimize system parameters to avoid the loss of energy and spectral efficiency. Naturally, the broadcast characteristic of wireless signals allows many devices to receive information and harvest energy. As a result, SWIPT communications are susceptible to attackers or eavesdroppers [10,11]. To improve physical layer security and SWIPT transmission efficiency, multiple-antenna techniques with the capability of focusing signals on the targets prevents eavesdroppers from intercepting information signals as much as possible [12,13]. In the following subsection, we present works related to multiple-input single-output (MISO) transceiver pairs in a two-way network, SWIPT with non-linear EH circuits, and physical layer security with hidden eavesdropper.
1.1. Related Works and Motivations
The multiple-antenna techniques and energy efficiency metrics are studied in wide areas such as cellular networks, wireless sensor networks, underwater acoustic sensor networks, … In [14], the authors proposed the relay selection protocol and consecutive packets routing scheme to reduce the energy consumption in wake-up radio-enabled wireless sensor network instead of the SWIPT technique with energy harvesting. In [15], the energy was also saved by the proposed bidirectional prediction method in cloud-based underwater acoustic sensor network. Nevertheless, the combination of two-way multiple-antenna system and SWIPT to enhance energy efficiency and secure information have not considered yet. In two-way networks, several prior works have investigated how to optimize power and information efficiency with MISO transceivers [16,17,18,19,20]. Two-way MISO networks with one base station and multiple users were investigated to maximize harvested energy [16] or minimize total transmission power [17]. The S-procedure and the semidefinite relaxation (SDR) technique were applied to channels with imperfect channel state information (CSI). We observed that two-way networks of multiple MISO transceiver pairs have not been studied yet, and the problem of resource allocation is more complicated, since multiple transmitters generate a lot of interference with the receivers. In [18,19,20], the authors considered two-way MISO networks with one pair of MISO transceiversin the presence of an active external eavesdropper. The targets of sum secrecy rate maximization were investigated in CSI cases with a perfect channel, bounded errors, and moment-based random errors when the channel of the external eavesdropper is known at both transmitters.Although a hidden eavesdropper may exist, and can completely hide from the base station, in this case, some related works [21,22,23] injected artificial noise (AN) to protect the information and create interference with the eavesdropper. The transmitters try to use part of their power for the AN signal, while the remain power is reserved for information. In [24], the authors investigated the sum rate maximization in a two-way scenario of a multiple-antenna transceiver pair incorporated by the intelligent reflecting surface. The source precoders and IRS phase-shift matrix are jointly optimizing by an alternating approach. In [25], the secondary IoT controller provided the relay assistance for two-way communication of two primary users and served SWIPT for separate multiple information IoT devices and multiple energy harvesting IoT devices where our proposed two-way scheme is almost different with multiple transceiver pairs.
Almost all the related works have focused on known external or internal eavesdroppers. With an unknown eavesdropper, only a single base station with a single user, or multiple users in one-way networks, has been studied, whereas a scenario with multiple base stations and multiple users in a two-way network has not been investigated yet. In this paper, we consider a secure two-way network under non-linear SWIPT and both perfect and imperfect channels in the presence of a hidden eavesdropper, where multiple base station-user pairs communicate over the same band at the same time. The base stations are equipped with transmitting and receiving antenna arrays, and the users have a single receiving antenna and a single transmitting antenna. On downlink, AN is injected to secure the signals and disrupt the hidden eavesdropper.
1.2. Contributions and Organization
The target is to minimize total power on downlink and uplink to satisfy the signal-to-interference-plus-noise (SINR) threshold, the amount of energy harvesting on downlink, the SINR threshold on uplink, and the limited transmission power in two-way directions. Thus, the AN power is maximized to mask information and create interference against the eavesdropper. Our major contributions are described as follows.
- The model of a secure two-way SWIPT network with a non-convex power transmission minimization problem is proposed under the requirements of SINR and EH downlink thresholds, an SINR uplink threshold, a non-linear EH model, and limited transmission power for the base stations and users.
- In perfect channels, the SDR technique is exploited to make the optimization problem convex. The optimal beamforming vectors, power-splitting factors, and transmit powers are obtained, and SDR is proven to be tight.
- In imperfect channels, the S-procedure and penalty function are applied to solve and approximate rank-1 matrices in the downlink problem. On uplink, the Cauchy-Schwarz inequality is exploited to achieve the approximate convex problem.
- Finally, Monte Carlo numerical simulations show the performance of the proposed AN method is better than the conventional method without AN. We also present the impact of some parameters on secure results in both perfect and imperfect channels.
The rest of this paper is arranged as follows. The model of the two-way network is described in Section 2. The optimization problem and the solution for perfect channels are proposed in Section 3. In Section 4, we investigate a solution with a penalty function for imperfect channels. The numerical evaluations are presented in Section 5, followed by our conclusions in Section 6.
Notations: Boldface lowercase and uppercase letters represent vectors and matrices, respectively. , , and denote the conjugate transpose, trace, and rank of matrix , respectively. We represent with and the positive semidefinite or positive definite, respectively. With and , we denote the norm-2 of complex vector and the absolute value of complex scalar x. We use to denote the space of complex matrices. The identity matrix is denoted by with the proper size. Finally, we denote with the distribution of a circularly symmetric complex Gaussian random vector with mean vector and covariance matrix . The tilde ‘∼’ means distributed as.
2. System Model
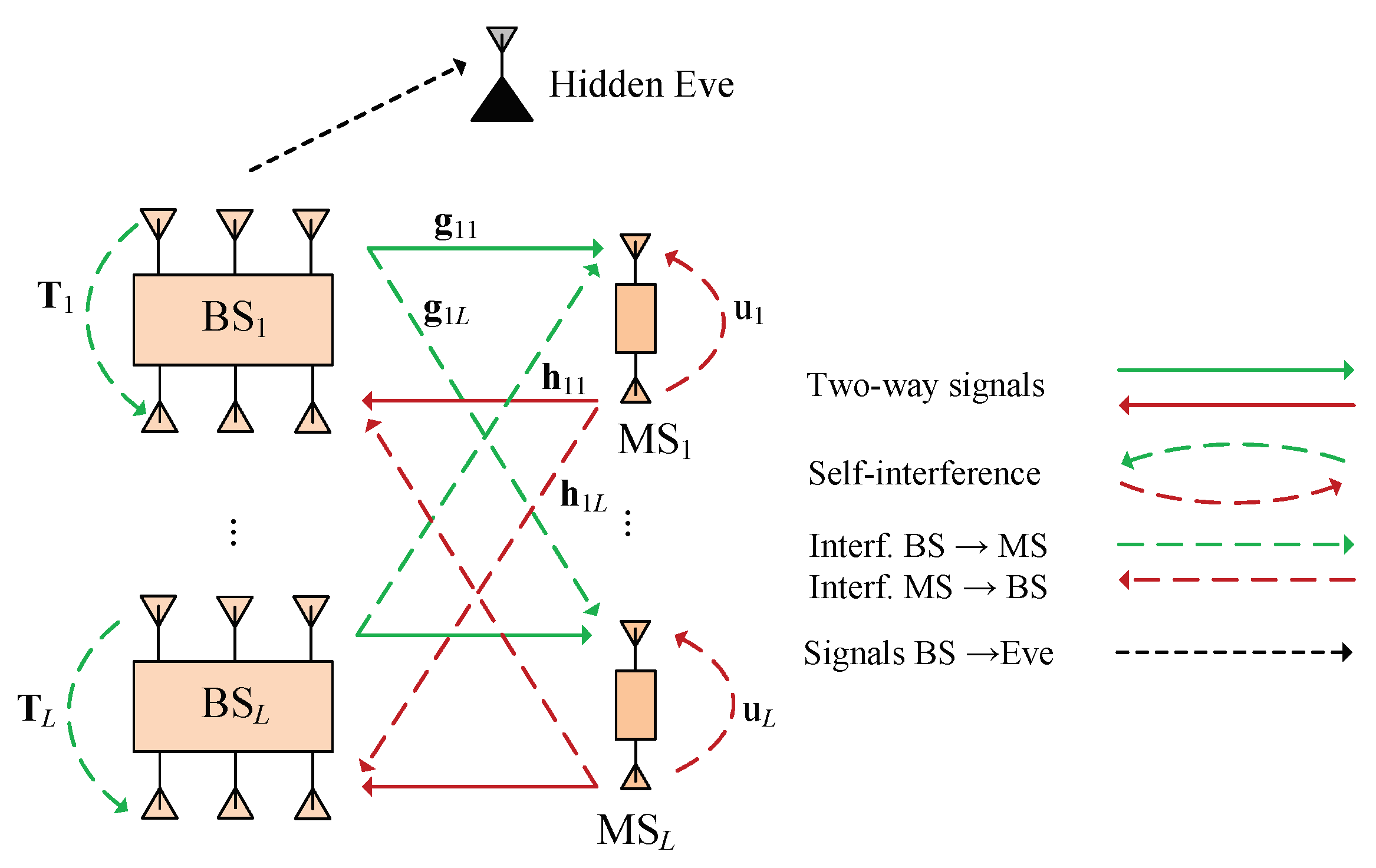
As shown in Figure 1, the considered two-way network includes multiple base station-mobile station (BS-MS) transceiver pairs where full-duplex antennas are equipped for both base stations and users. The base stations have two antenna arrays, with one of the N antennas for transmitting, and one of the N antennas for receiving. The users have two antennas with one for receiving signals and harvesting energy, and one for transmitting information to the corresponding base station. The BSs with affordable energy can transfer both data and energy to users on downlink, and receive information from users on uplink.
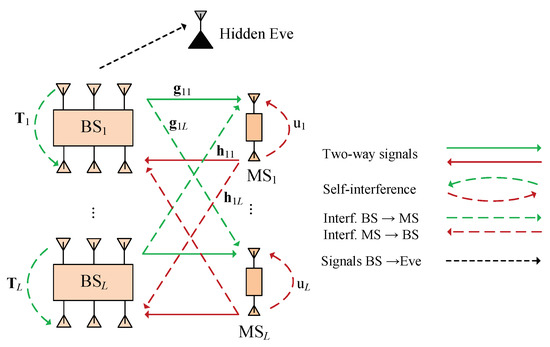
Figure 1.
Secure two-way network with SWIPT and hidden eavesdropper.
On downlink, the channel state information vectors from base station to mobile user , , are represented by . The CSI matrix of self-interference from the N transmission antennas to the N reception antennas at base station is denoted by , . In Figure 1, the green and dark red lines denote the signals transferred from the base stations to the mobile users, and vice versa, respectively. On uplink, the CSI vectors from mobile user to base station are represented by , . The complex scalar, , indicates a self-interference channel from the transmission antenna to the reception antenna at user , . To obtain the downlink channels at the base station BSs and the uplink channels at the receivers MSs, there are two conventional methods where the first one is by estimating the reverse link channel based on the training signals from the BSs in the uplink or the MSs in the downlink, and the second one is to perform channel estimation (from the BSs to the MSs in the downlink or from the MSs to BSs in the uplink) and send CSI feedback via feedback channel [26,27,28]. Another method to save energy is proposed by one-bit feedback but only applied in wireless power transfer networks [28]. We note that the energy-constrained receivers MSs can consume part of the energy harvesting in the SWIPT downlink for transmitting training signals or processing complex baseband signal. Furthermore, there exists a tradeoff between the channel estimation accuracy and the energy consumption. It means that more spending energy for estimation may give the higher CSI accuracy and the larger harvested energy. Similar to [27], we suppose that the energy consumption of estimation at the receiver MSs is trivial compared to the harvested energy for simplicity.
In this work, we consider a security scenario where a hidden eavesdropper exists and overhears the information from the base stations to the mobile users. In particular, the CSI of the eavesdropper is not collected by the base stations, since it might stay silent to hide the attack. To protect the data messages, the base stations will inject artificial noise along with the data to disturb and degrade the eavesdropping performance. The transmitted signal from base station to mobile user in the l-th two-way transceiver pair is represented by where denotes the precoded beamforming vectors, represents the artificial noise signal with a Gaussian distribution, i.e., with covariance matrix . In addition, with average power is the data symbol for proposed mobile user . Therefore, the average consumed power of base station is formulated by . On uplink, mobile user transmits the signal, with power and data symbol , where . As a result, the downlink received signal at is expressed as:
where indicates the Gaussian noise at the antenna of mobile user . The received signal is composed of the intended signal plus AN, the interference from other BSs, self-interference from the transmitting antenna, and antenna noise. Since user knows its transmitting symbol, , we assume that the self-interference, , can be canceled completely.
To compensate for a portion of the consumed energy, is equipped with a power-splitting circuit in order to simultaneously decode information and harvest power from the incoming signal. splits the incoming signal into two streams, where the first stream, with energy fraction , is used for decoding information, and the second, with energy fraction , is used for harvesting power. Then, the signal for receiving information at is formulated as , where data processing at generates noise, . The signal for harvesting energy is . As a result, the SINR at mobile user on downlink is expressed as:
In the theoretical linear model of an EH circuit, the mobile nodes receive the total harvested power of the incoming signal, given as:
To obtain (3), some manipulations are performed as Appendix A. In the practical non-linear model of an EH circuit, the harvested power of the mobile nodes is given by the logistic function [8,9]:
where indicates the saturated harvested power, and represent the constant benefit provided by the data-fitting method at mobile node .
The hidden eavesdropper without channel information at the BSs tries to intercept the information from the BSs to the mobile nodes. We only consider a secure downlink scenario, since it is highly possible for an eavesdropper to attack the strong SWIPT signals from the BSs. The received SINR of the signal at the eavesdropper is represented by:
where is the wiretap channel from , and is the variance of noise at the eavesdropper for all l.
On uplink, the incoming signal at the receiving antennas of base station is formulated as:
where receiving unit-norm beamforming vectors, , are used at the base stations to decode the symbols, and is the antenna noise vectors at with . Since knows its transmitting symbol, , and generates artificial noise, it is assumed to remove the self-interference completely. Therefore, the SINR at base station is formulated by:
where is the variance of additive noise at the receiving antenna array of .
3. Problem Formulation
The object of this study is to minimize the total transmission downlink and uplink power under the limited transmit power at the base stations and users, based on the quality of service for the users and the base stations in terms of SINR and EH thresholds. It means that the AN power is supposed to maximize interference against the hidden eavesdropper. The precoding beamforming vectors, artificial noise, the power-splitting (PS) factors, and the transmission powers are achieved in the optimization problem as follows:
The objective function is the total transmission power on both uplink and downlink of the base station-user pairs. The downlink SINR restriction guarantees the data rate under the minimum threshold, . The amount of energy harvested by users is greater than the minimum threshold, , with the non-linear EH circuits. On uplink, the SINR restriction provides the uplink data rate based on the minimum threshold, . Furthermore, the uplink transmission power is limited by the maximum power of the user, . The maximum downlink power at the base station, , is exploited to provide the most energy for AN when increasing the interference with the eavesdropper. Lastly, the PS factor, , is limited in the period . The energy harvesting restrictions (10c) are converted to constraints of simple form as follows:
where . The details of conversion are presented in Appendix B. Instead of threshold in (10c), we consider a novel EH threshold, , in equation form (11). Then, the secure two-way problem of minimizing transmission power (10) is re-expressed as follows:
To simplify optimization problem (12), we separate problem (12) into two sub-problems where the first problem with variable group is given as:
and the second problem with variable group , is expressed as follows:
In the next section, we present the solutions for the downlink problem (13) and the uplink problem (14) with perfect channels.
4. Optimization of Perfect Channels
4.1. Solving Downlink Problem
We first transform problem (13) into the standard optimization form, as follows:
Problem (15) is solved by applying the SDR technique [29] based on the well-known form . We set , , , and use , , . Then, when using the SDR method, we achieve the following problem:
By dropping the rank-1 condition (16g), the problem becomes convex, called (16)-SDR, which can obtain the optimal solution by using the CVX solver [30,31]. Based on the structure of the convex problem (16)-SDR, we show optimal matrix solution , satisfying the rank-1 condition.
Theorem 1.
Assume that problem (16)-SDR is feasible; the optimal solution, , of (16)-SDR satisfies the rank-1 condition.
Proof.
The proof of Theorem 1 is given in the Appendix C. □
The convex semidefinite programing problem (16)-SDR is solved by CVX tool which uses the interior point method. The computational complexity largely depends on matrix variables of size and linear constraints. According to [32], the worst-case complexity of (16)-SDR solution is calculated as with the solution accuracy .
4.2. Solving Uplink Problem
We choose the receiving vector as the maximum ratio transmission (MRT) [33], , and therefore, , . Then, uplink problem (14) becomes:
The SINR conditions are transformed as convex form:
As a result, we achieve the convex problem as:
That can be solved effectively by using convex solver CVX [31]. The convex linear program (19) has L non-negative variables and linear constraints. The computational complexity of solving convex problem (19) is calculated as [32] with the accuracy .
5. Optimization of Imperfect Channels
5.1. Solving Downlink Problem
In an empirical system, many elements affect the accuracy of the channel estimation, such as imperfect hardware in the BS and MS, limited CSI feedback quantization, and user mobility. Therefore, we modeled the error of channels as a deterministic ellipsoid [34], as follows:
where the uncertain errors, , are limited by with the radii of error bound , and denotes the estimated channel values of . Under uncertain CSI, problem (13) can be expressed as:
We propose the novel auxiliary variables , to simplify the constraints (21c), (21d) as:
Therefore, problem (21) with uncertain channels is formulated as follows:
We use the S-procedure [30,35] to transform conditions (23e)–(23h) into the finite constraints that remove the uncertain errors.
Theorem 2.
(S-Procedure) Define the expressions
with , , , and . Then, the implication holds if and only if there exists a where
assumed that there exists a point such that .
Inequality constraint (23e) is changed to a suitable structure with Theorem 2:
Then we expressed as follows:
with new variable . Based on Theorem 2, there exists a achieving:
We also transform condition (23f) with the novel variable into:
By the same method, we replace conditions (23g) by (29) as:
and (23h) by (30) as:
where , are the novel variables. Then, the equivalent optimization problem of (23) with uncertain channels is given by:
The challenge of the uncertainty problem (31) is the non-convex condition (31k) where we cannot obtain the rank-1 optimal solution as the perfect problem. To overcome this, the penalty function method is proposed to find a suboptimal solution approximating rank-1. We note that is positive semidefinite matrix, so all eigenvalues of are non-negative. Therefore, where is the maximum eigenvalue of . The equality holds, i.e., , if and only if . From this insight, we want as small as possible. Under the penalty method [30], we add to the objective function the term , where is a penalty factor. As a result, the uncertain problem (31) is converted as follows:
When is large enough, the solution, , will satisfy . We observe that is a convex function [30], so we exploit the iterative approximation to find the solution. We first restate the following Theorem 3 (introduced in [36]).
Theorem 3.
Denote as the maximum eigenvalue function. If and are positive semidefinite matrices, we achieve , where is the eigenvector according to the maximum eigenvalue of .
From Theorem 3, we obtain the inequality for two positive semidefinite matrices, and :
where is the eigenvector according to the maximum eigenvalue of . In the n-th iteration with fixed point , we solve the convex sub-problem as follows:
The (n+1)-th iteration with fixed point is updated by the optimal solution, , of the n-th convex sub-problem. In Algorithm 1, the proposed iterative algorithm based on the penalty function method is presented in detail.
| Algorithm 1 Proposed iterative algorithm with a penalty function for solving problem (31) |
|
For each iteration, the proposed Algorithm 1 solves the convex problem (33) where the complexity mostly depends on approximate linear matrix inequality constraints of size . Then, the worst-case complexity is roughly computed as [37] where is the convergent iteration number of proposed Algorithm 1 and denotes the solution accuracy.
5.2. Solving Uplink Problem
The CSI error model is given as:
where the uncertain errors, , are limited by with the radii of error bound , and are the estimated channel values of . Power minimization problem with the uncertain channel on uplink is presented as:
We also choose the receiving vector as MRT beamforming , then and . Therefore, the uplink problem (35) becomes as follows:
The SINR constraints (36b) are transformed into standard form:
To guarantee the SINR conditions, we find the worst case of (37) in the first sub-problem, as follows:
That can be manipulated approximately as:
And the second sub-problem is:
That can be approximated as:
Please note that we achieve the bound of error value that is much smaller than channel value in practical terms. As a result, the convex problem is obtained as follows:
This problem can be solved effectively by using Matlab’s CVX. Similar to problem (19) in the case of perfect channels, the computational complexity of problem (42) is [32] with the accuracy .
6. Numerical Evaluations
In this section, the numerical evaluations of the proposed algorithms for perfect and imperfect CSI are shown via the Monte Carlo method. The system parameters presented in Table 1 are used in the numerical evaluations. In Table 1, the variance values of antenna and processing noises and are referred from [38] where the values of processing noises are normally larger than that of antenna noises. Moreover, the parameters of non-linear EH circuit are referred from [9] where the saturated value is the maximum harvested energy of non-linear model, .

Table 1.
System Parameters.
Based on other SWIPT networks [38,39,40], the downlink channel from base station to user is modeled as a Rician fading channel with , in which Rician factor . The line-of-sight deterministic part is for the direct channels, and it is for the indirect channels with . In addition, the non-line-of-sight follows Rayleigh fading with distributions and for direct and indirect links, respectively. Furthermore, the values of covariances ( and ) represent the large-scale fading effects in the channel model. Here, the electric angle is where the antenna distance is half the carrier wavelength. We assign direct angles as , and indirect angles as . The uplink channels are , the line-of-sight and non-line-of-sight parts are similar to the downlink channels. The normalized errors of downlink and uplink estimations are assigned as and , respectively.
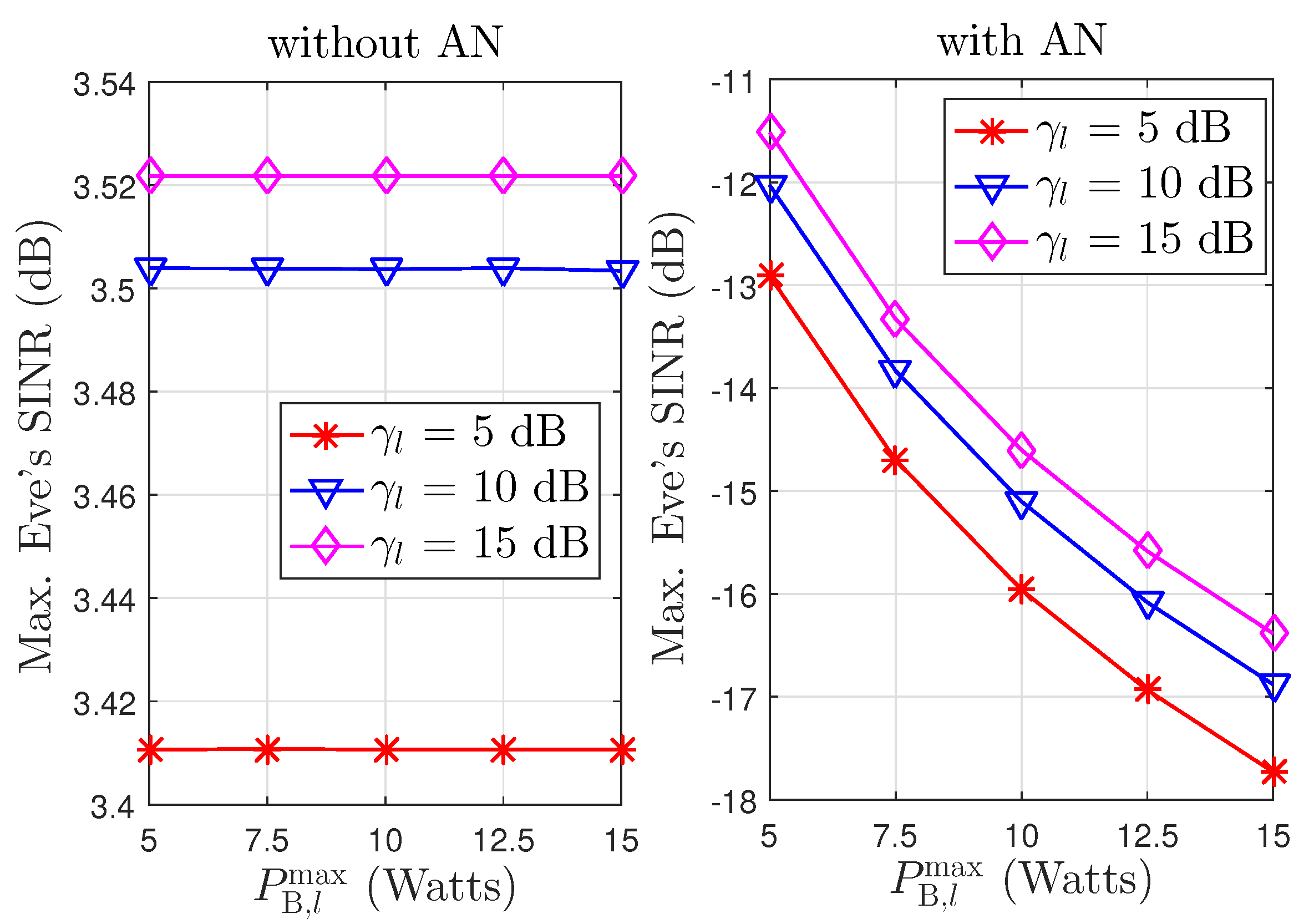
Figure 2 shows the maximum SINR wiretapped by the eavesdropper according to transmission power at the downlink transmitters with a perfect channel. In this evaluation, the SINR threshold at the users is and the EH threshold is . The performance of the proposed approach aided by AN is obtained when downlink problem (16)-SDR is figured out, and where the achieved beamforming matrices satisfy the rank-1 conditions, as shown in Theorem 1. The baseline results without AN in Figure 2 ignore security from the hidden eavesdropper. In this scheme without AN, downlink transmission power minimization is studied while obtaining the data rate and harvested energy thresholds. In the proposed scheme with AN, the eavesdropper receives much lower SINR values than under the scheme without AN. For example, when the maximum transmission power , the maximum SINR of Eve rises with the increase of and achieves for the without AN case, for the proposed with AN case, respectively. That is explained because the injected AN in the proposed scheme creates interference with the eavesdropper to reduce the received SINR. We also see that the leakage of information to the eavesdropper is reduced when transmission power increases, since the BSs have more energy to generate AN interference.
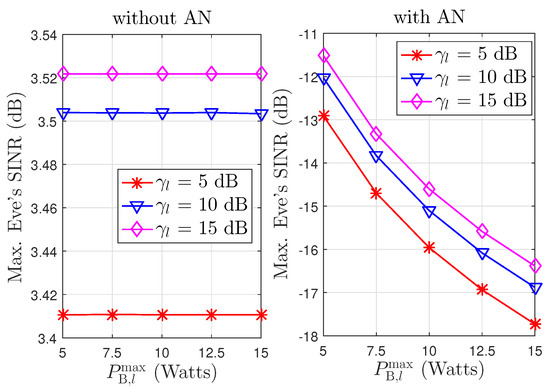
Figure 2.
Maximum Eve’s SINR according to maximum allowable BS’s power in a perfect channel scenario.
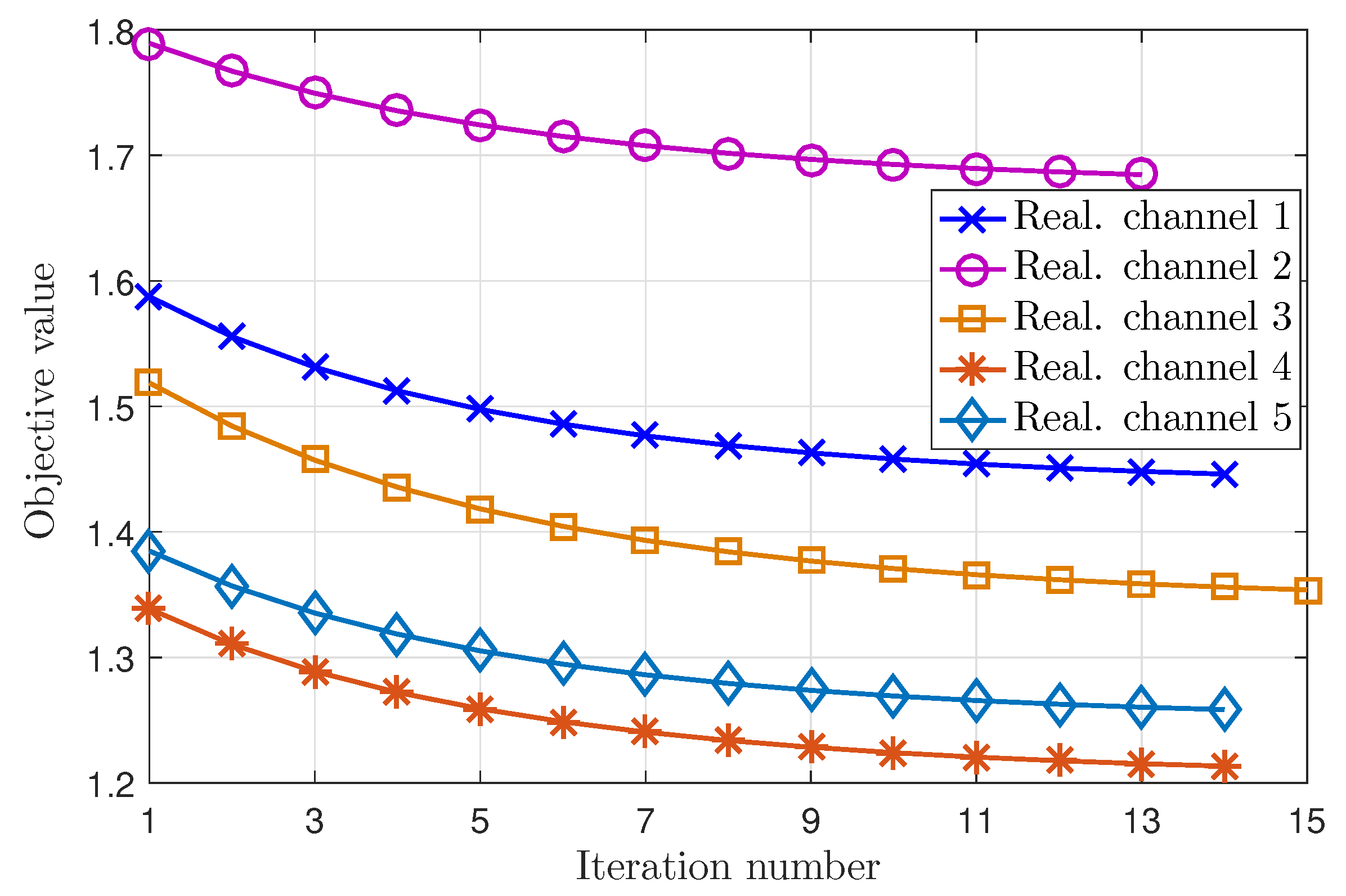
Figure 3 presents the convergence of the proposed iterative algorithm with the penalty function in several random realization channels where the parameters are set as follows: normalized error bound , convergent tolerance , and penalty factor . The penalty factor is chosen empirically to provide good convergent in experiments. As seen in Figure 3, the objective values of problem (33) decrease and converge in about 15 iterations. Moreover, the objective values converge to different points via the values of random channels.
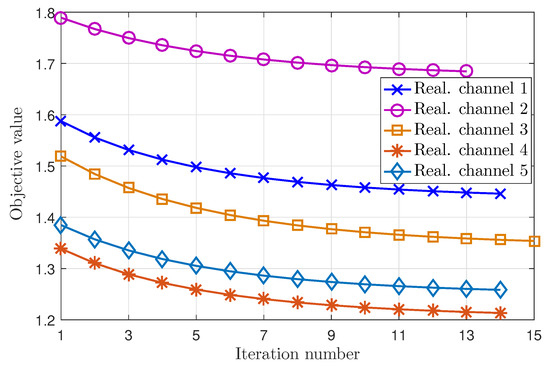
Figure 3.
The convergence of the proposed iterative algorithm with the penalty function, as detailed in Algorithm 1.
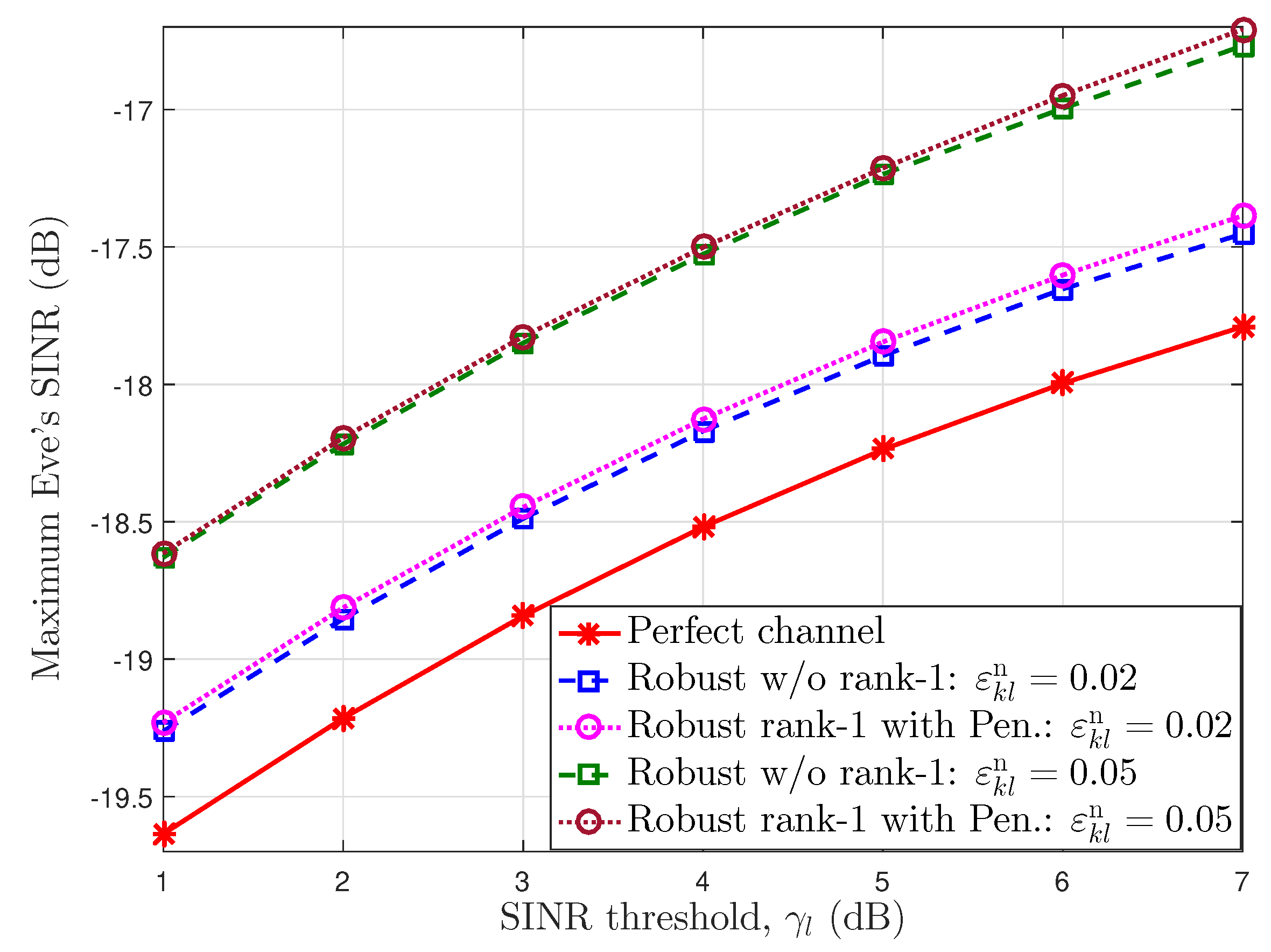
In Figure 4, we reveal the maximum eavesdropper’s SINR via the SINR threshold for the users on perfect and imperfect channels with error bounds and . We observe that a perfect channel provides the lowest values, since the BSs have exact information channels for designing the optimal beamforming and PS ratios. For example, at the SINR threshold , the maximum Eve’s SINR obtains the values of according to the perfect channel scheme, robust without rank-1 and with penalty function Algorithm 1 schemes under , respectively. In addition, the information leaked to the eavesdropper grows as the downlink SINR threshold increases in all cases. This is because the BS expends more power for information transfer and less power for AN. Furthermore, the proposed robust algorithm with a penalty function achieves the rank-1 matrix solution, and the eavesdropper’s SINR nears that of the robust algorithm without the rank-1 solution. We can also see that the eavesdropper can collect more information when the error bound increases. The reason is that the extra power is needed to compensate for a large channel estimation error that results in low interference power for AN.
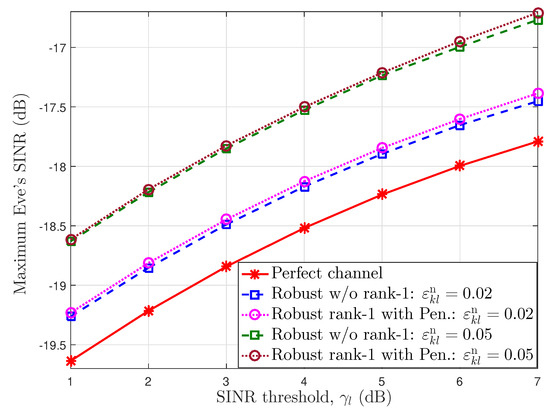
Figure 4.
The maximum Eve’s SINR according to the SINR threshold at the users.
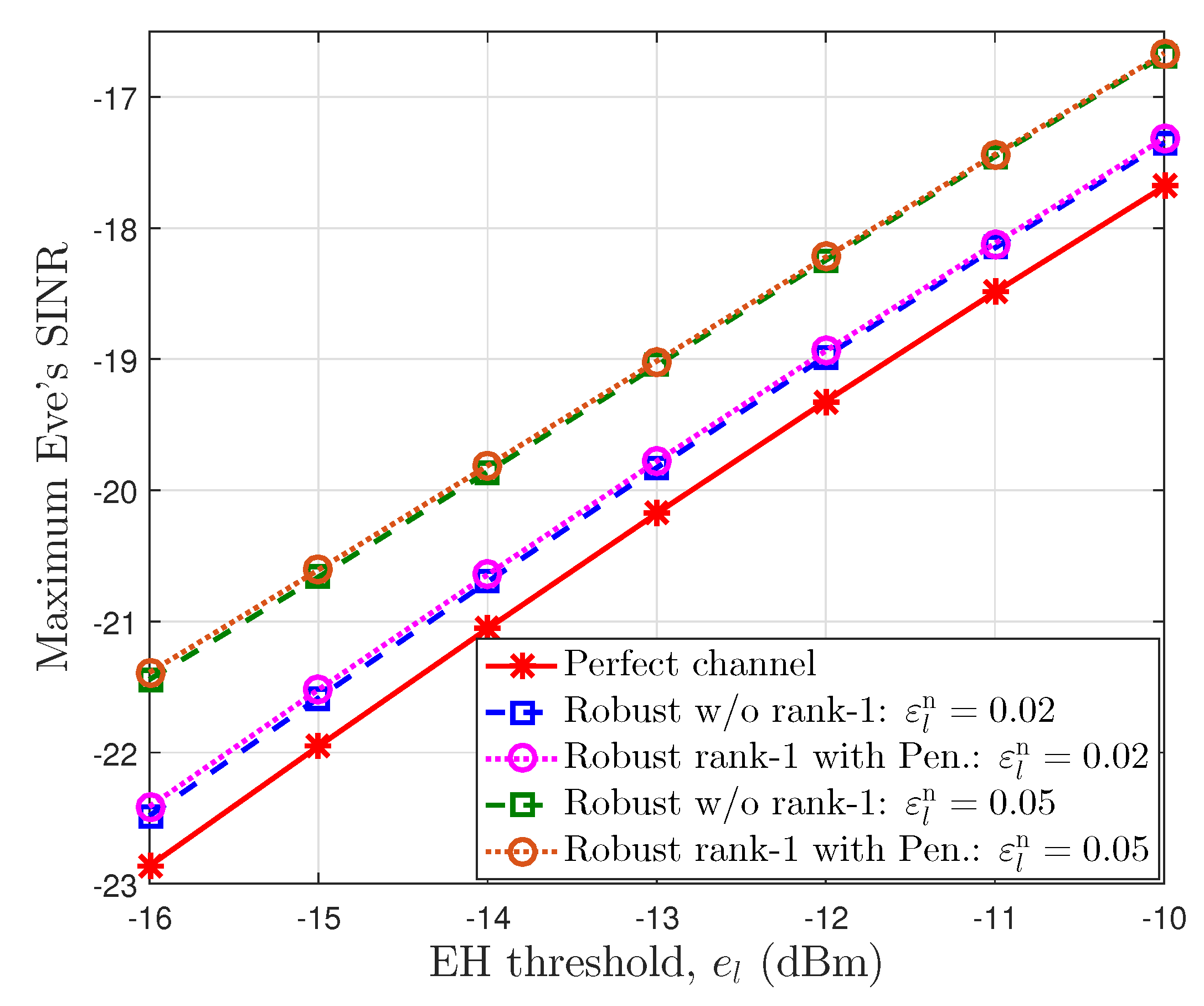
In Figure 5, we reveal the impact of EH thresholds on the eavesdropper’s SINR for the different channel error bounds with downlink SINR threshold . Similar to Figure 4, a perfect channel provides the lowest eavesdropper SINR. When the EH threshold becomes larger, the eavesdropper SINR also increases. The users have to reduce the value of the PS factor in the power-splitting unit for energy harvesting, i.e., rising the part of the received signal power that is transferred to the EH unit. It means that they need to increase the information power of intended signal to obtain the required SINR threshold. Moreover, the higher error bound allows more information leakage to the eavesdropper, since the BSs must share more power for signals and must decrease the AN interference power. For an imperfect channel, the proposed iterative algorithm with a penalty function satisfying rank-1 constraints obtains a result for the eavesdropper’s SINR that is a little higher than that of the robust case without rank-1 constraints.
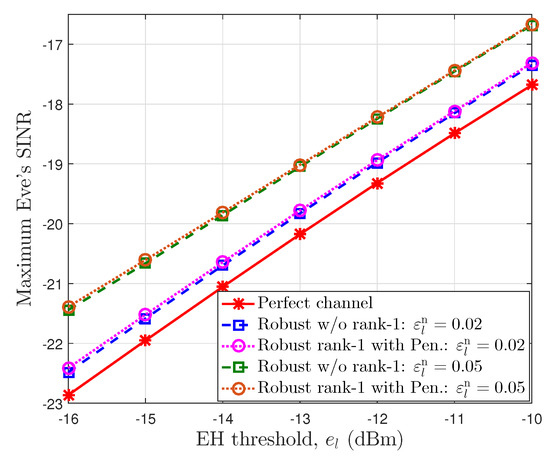
Figure 5.
The maximum Eve’s SINR according to the EH threshold at the users.
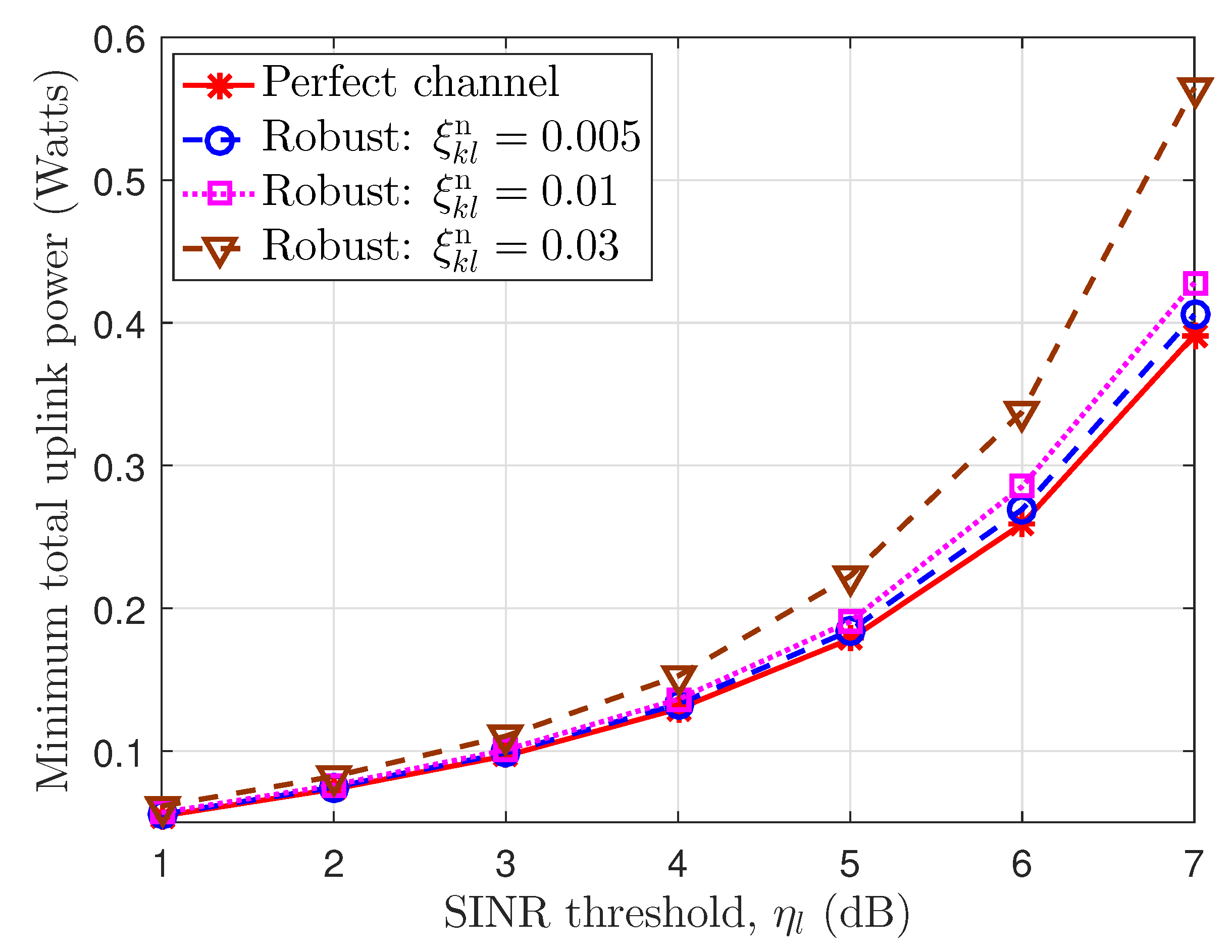
In Figure 6, we present the maximum total uplink power according to the SINR threshold at the BSs under perfect CSI and imperfect CSI with uplink error bounds . As seen in Figure 6, the perfect channel provides the lowest power values, and the imperfect uplink channel gives higher values via the larger uplink error bounds as well as the SINR threshold. For example, at the required SINR threshold, , the minimum total uplink power achieves according to the perfect channel, the imperfect channels with normalized error bounds, , respectively. The reason is that the users must expend more energy to compensate for the errors and to guarantee the receiving SINR at the BSs.
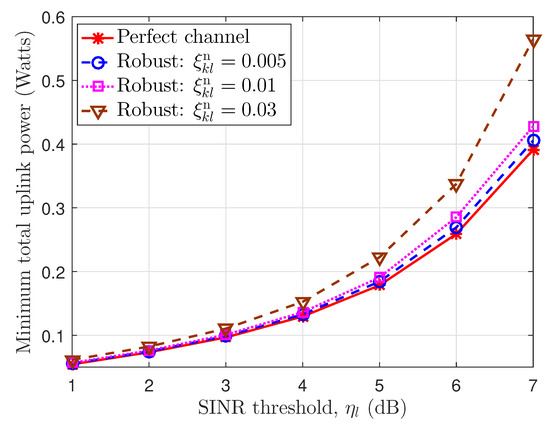
Figure 6.
The minimum total uplink power according to the SINR threshold at the base stations.
7. Conclusions and Further Work
In this work, we studied a two-way SWIPT network with multiple base station-user pairs where the goal is to secure downlink information in the presence of a hidden eavesdropper, and to provide the SINR threshold and amount of harvested energy for users, the SINR threshold for base stations, and limit transmission powers. In perfect channels, we use the SDR method and achieve optimal beamforming precoders with rank-1 proof on downlink. On the other hand, the penalty function is applied in the proposed iterative algorithm for approximating rank-1 matrices on imperfect channels. On uplink, the transmission power minimization problems are manipulated to convert and solve them in convex form.
For future research, we discuss some interesting ideas as follows. First, the imperfect practical self-interference cancelation where self-interference is not canceled completely is an attractive and complicated direction for the future. Second, we investigated the secure two-way network where the users are equipped with single receive antenna and single transmit antenna. Thus, the case of multiple-antenna users is potential to improve performance but complicated in future work. Finally, the intelligent reflecting surfaces with reconfigurable phase-shift capabilities [6] can enhance the signal transmission by constructive reflection for intended signal and destructive reflection for interference in two-way networks. The optimization of joint conventional beamforming vectors and new refection matrices in the proposed secure system is a promising direction.
Author Contributions
Conceptualization, P.V.T., P.N.S. and I.K.; Formal analysis, P.V.T., T.T.D. and S.Q.N.; Methodology, P.V.T., V.Q.B.N.; Supervision, I.K.; Writing—original draft, P.V.T.; Writing—review & editing, D.V.Q. and I.K.; Funding acquisition, P.N.S. and I.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2019.13.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| SWIPT | Simultaneous Wireless Information and Power Transfer |
| SDR | Semidefinite Relaxation |
| Eve | Eavesdropper |
| CSI | Channel State Information |
| AN | Artificial Noise |
| BS | Base Station |
| MS | Mobile User |
| MRT | Maximum Ratio Transmission |
| MISO | Multiple-Input Single-Output |
| MIMO | Multiple-Input Multiple-Output |
| IRS | Intelligent Reflecting Surfaces |
| SINR | Signal-to-Interference-plus-Noise Ratio |
| EH | Energy Harvesting |
| PS | Power-Splitting |
| KKT | Karush–Kuhn–Tucker |
Appendix A. Obtaining Equation of Theoretical Harvested Power
The total harvested power of the incoming EH signal at is expressed as:
where denotes the statistical expectation. After canceling self-interference in (1), we obtain:
We note that are independent circularly symmetric complex Gaussian random variables with zero mean and variances , respectively. Moreover, the artificial noise signal is . Therefore, we achieve Equation (3) for energy harvesting at .
Appendix B. Obtaining Simple Form of Energy Harvesting Constraints
We have constraint (10c) as . From (10c), we first move to the right-hand side (RHS), then to RHS to obtain:
Then, we move to the denominator of the left-hand side (LHS) and to RHS. After changing 1 from RHS to LHS, the new inequality is expressed as follows:
Using the function for both sides, then we achieve:
We move to LHS and invert the sign of the inequality, then to LHS. Lastly, we obtain constraint (11) as where we denote .
Appendix C
Proof of Theorem 1.
The Lagrangian function of problem (16)-SDR is formulated as follows:
where , and are the dual variables according to constraints (16b)–(16e), respectively. We rewrite the Lagrangian in simplified form as follows:
where
and the term is relative to other variables. From KKT optimal conditions, we have , , and . Therefore, we achieve:
where ‘*’ denotes optimal variables. Since , then denote . Thus, we derive . Moreover, , so . From (A8a), we derive
From (A8c) and (A9), we have . To satisfy the SINR constraints, is different from 0, so . As a result, Theorem 1 is obtained completely. □
References
- Clerckx, B.; Zhang, R.; Schober, R.; Ng, D.W.K.; Kim, D.I.; Poor, H.V. Fundamentals of Wireless Information and Power Transfer: From RF Energy Harvester Models to Signal and System Designs. IEEE J. Sel. Areas Commun. 2019, 37, 4–33. [Google Scholar] [CrossRef]
- Bi, S.; Ho, C.K.; Zhang, R. Wireless powered communication: Opportunities and challenges. IEEE Commun. Mag. 2015, 53, 117–125. [Google Scholar] [CrossRef]
- Hu, J.; Yang, K.; Wen, G.; Hanzo, L. Integrated data and energy communication network: A comprehensive survey. IEEE Commun. Surv. Tuts. 2018, 20, 3169–3219. [Google Scholar] [CrossRef]
- Lu, X.; Wang, P.; Niyato, D.; Kim, D.I.; Han, Z. Wireless networks with RF energy harvesting: A contemporary survey. IEEE Commun. Surv. Tuts. 2015, 17, 757–789. [Google Scholar] [CrossRef]
- Qi, Q.; Chen, X.; Ng, D.W.K. Robust beamforming for NOMA-based cellular massive IoT with SWIPT. IEEE Trans. Signal Process. 2020, 68, 211–224. [Google Scholar] [CrossRef]
- Zhang, J.; Björnson, E.; Matthaiou, M.; Ng, D.W.K.; Yang, H.; Love, D.J. Prospective Multiple Antenna Technologies for Beyond 5G. IEEE J. Sel. Areas Commun. 2020, 1–24. [Google Scholar] [CrossRef]
- Tuan, P.V.; Koo, I. Robust weighted sum harvested energy maximization for SWIPT cognitive radio networks based on particle swarm optimization. Sensors 2017, 17, 2275. [Google Scholar] [CrossRef]
- Boshkovska, E.; Ng, D.W.K.; Zlatanov, N.; Schober, R. Practical non-linear energy harvesting model and resource allocation for SWIPT systems. IEEE Commun. Lett. 2015, 19, 2082–2085. [Google Scholar] [CrossRef]
- Xiong, K.; Wang, B.; Liu, K.J.R. Rate-energy region of SWIPT for MIMO broadcasting under nonlinear energy harvesting model. IEEE Trans. Wirel. Commun. 2017, 16, 5147–5161. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Liu, L.; Zhang, R.; Chua, K.C. Secrecy wireless information and power transfer with MISO beamforming. IEEE Trans. Signal Process. 2014, 62, 1850–1863. [Google Scholar] [CrossRef]
- Chen, X.; Ng, D.W.K.; Chen, H.H. Secrecy Wireless Information and Power Transfer: Challenges and Opportunities. IEEE Wirel. Commun. 2016, 23, 54–61. [Google Scholar] [CrossRef]
- Li, Q.; Ma, W.K. Spatially selective artificial-noise aided transmit optimization for MISO multi-eves secrecy rate maximization. IEEE Trans. Signal Process. 2013, 61, 2704–2717. [Google Scholar] [CrossRef]
- Peng, M.; Liu, W.; Wang, T.; Zeng, Z. Relay Selection Joint Consecutive Packet Routing Scheme to Improve Performance for Wake-Up Radio-Enabled WSNs. Wirel. Commun. Mob. Comput. 2020, 1–32. [Google Scholar] [CrossRef]
- Wang, T.; Zhao, D.; Cai, S.; Jia, W.; Liu, A. Bidirectional Prediction based Underwater Data Collection Protocol for End-Edge-Cloud Orchestrated System. IEEE Trans. Ind. Informatics 2020, 16, 4791–4799. [Google Scholar] [CrossRef]
- Wen, Z.; Guo, Z.; Beaulieu, N.C.; Liu, X. Robust beamforming design for multi-user MISO full-duplex SWIPT system with channel state information uncertainty. IEEE Trans. Veh. Technol. 2019, 68, 1942–1947. [Google Scholar] [CrossRef]
- Okandeji, A.A.; Khandaker, M.R.A.; Wong, K.K.; Zheng, G.; Zhang, Y.; Zheng, Z. SWIPT in MISO full-duplex systems. J. Commun. Netw. 2017, 19, 470–480. [Google Scholar]
- Feng, R.; Li, Q.; Zhang, Q.; Qin, J. Robust secure beamforming in MISO full-duplex two-way secure communications. IEEE Trans. Veh. Technol. 2016, 65, 408–414. [Google Scholar] [CrossRef]
- Wang, Y.; Li, Q.; Zhang, Q.; Qin, J. Optimal and suboptimal full-duplex secure beamforming designs for MISO two-way communications. IEEE Wirel. Commun. Lett. 2015, 4, 493–496. [Google Scholar]
- Li, Q.; Zhang, Y.; Lin, J.; Wu, S.X. Full-duplex bidirectional secure communications under perfect and distributionally ambiguous eavesdropper’s CSI. IEEE Trans. Signal Process. 2017, 65, 4684–4697. [Google Scholar] [CrossRef]
- Tuan, P.V.; Koo, I. Robust Secure Transmit Design for SWIPT System with Many Types of Wireless Users and Passive Eavesdropper. IEICE Trans. Commun. 2018, E101, 441–450. [Google Scholar] [CrossRef]
- Xiong, J.; Ma, D.T.; Wong, K.K.; Wei, J.B. Robust masked beamforming for MISO cognitive radio networks with unknown eavesdroppers. IEEE Trans. Veh. Technol. 2015, 65, 744–755. [Google Scholar] [CrossRef]
- Zhang, M.; Cumanan, K.; Ni, L.; Hu, H.; Burr, A.G.; Ding, Z. Robust beamforming for AN aided MISO SWIPT system with unknown eavesdroppers and non-linear EH model. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–7. [Google Scholar]
- Zhang, Y.; Zhong, C.; Zhang, Z.; Lu, W. Sum Rate Optimization for Two-Way Communications with Intelligent Reflecting Surface. IEEE Commun. Lett. 2020, 24, 1090–2020. [Google Scholar] [CrossRef]
- Deng, Z.; Li, Q.; Zhang, Q.; Yang, L.; Qin, J. Beamforming Design for Physical Layer Security in a Two-Way Cognitive Radio IoT Network with SWIPT. IEEE Internet Things J. 2019, 6, 10786–10798. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Lo, E.S.; Schober, R. Robust beamforming for secure communication in systems with wireless information and power transfer. IEEE Trans. Wirel. Commun. 2014, 13, 4599–4615. [Google Scholar] [CrossRef]
- Xu, J.; Liu, L.; Zhang, R. Multiuser MISO beamforming for simutaneous wireless information and power transfer. IEEE Trans. Signal Process. 2014, 62, 4798–4810. [Google Scholar] [CrossRef]
- Xu, J.; Zhang, R. Energy Beamforming with One-Bit Feedback. IEEE Trans. Signal Process. 2014, 62, 5370–5381. [Google Scholar] [CrossRef]
- Luo, Z.Q.; Ma, W.K.; So, A.M.C.; Ye, Y.; Zhang, S. Semidefinite relaxation of quadratic optimization problems. IEEE Signal Process. Mag. 2010, 27, 20–34. [Google Scholar] [CrossRef]
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Grant, M.; Boyd, S. CVX: Matlab Software for Disciplined Convex Programming Version 2.1. 2017. Available online: http://cvxr.com/cvx (accessed on 22 December 2019).
- Karipidis, E.; Sidiropoulos, N.D.; Luo, Z.Q. Quality of service and max-min fair transmit beamforming to multiple cochannel multicast groups. IEEE Trans. Signal Process. 2008, 56, 1268–1279. [Google Scholar] [CrossRef]
- Bjornson, E.; Bengtsson, M.; Ottersten, B. Optimal multiuser transmit beamforming: A difficult problem with a simple solution structure [lecture notes]. IEEE Signal Process. Mag. 2014, 31, 142–148. [Google Scholar] [CrossRef]
- Lu, Y.; Xiong, K.; Fan, P.; Zhong, Z.; Letaief, K.B. Coordinated Beamforming with Artificial Noise for Secure SWIPT under Non-Linear EH Model: Centralized and Distributed Designs. IEEE J. Sel. Areas Commun. 2018, 36, 1544–1563. [Google Scholar] [CrossRef]
- Lemon, A.; So, A.M.C.; Ye, Y. Low-Rank Semidefinite Programming: Theory and Applications. Found. Trends Optim. 2016, 2, 1–156. [Google Scholar] [CrossRef]
- Phan, A.H.; Tuan, H.D.; Kha, H.H.; Ngo, D.T. Nonsmooth optimization for efficient beamforming in cognitive radio multicast transmission. IEEE Trans. Signal Process. 2012, 60, 2941–2951. [Google Scholar] [CrossRef]
- Wang, K.Y.; So, A.M.C.; Chang, T.H.; Ma, W.K.; Chi, C.Y. Outage constrained robust transmit optimization for multiuser MISO downlinks: Tractable approximations by conic optimization. IEEE Trans. Signal Process. 2014, 62, 5690–5705. [Google Scholar] [CrossRef]
- Shi, Q.; Liu, L.; Xu, W.; Zhang, R. Joint transmit beamforming and receive power splitting for MISO SWIPT systems. IEEE Trans. Wirel. Commun. 2014, 13, 3269–3280. [Google Scholar] [CrossRef]
- Tuan, P.V.; Koo, I. Optimal Multiuser MISO Beamforming for Power-Splitting SWIPT Cognitive Radio Networks. IEEE Access 2017, 5, 14141–14153. [Google Scholar] [CrossRef]
- Timotheou, S.; Krikidis, I.; Zheng, G.; Ottersten, B. Beamforming for MISO Interference Channels with QoS and RF Energy Transfer. IEEE Trans. Wirel. Commun. 2014, 13, 2646–2658. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).