Evolution of V2X Communication and Integration of Blockchain for Security Enhancements
Abstract
1. Introduction
- We survey state-of-the-art V2X technology, including its definition; we highlight the V2X evolution, and provide detailed comparisons of cellular and non-cellular based V2X communication.
- We present a review on the adoption of edge-based computing for V2X communications with particular emphasis on integrating promising technologies, such as MEC and Nonorthogonal multiple access (NOMA), and their applications in data offloading for 5G vehicular networks.
- We investigate the potential of blockchain in V2X networks as a security mechanism. We examine the requirements of V2X and discuss on how the requirements are fulfilled by the blockchain.
- We conducted an in-depth analysis of integrating blockchain with 5G and edge computing in V2X networks, and provide a detailed comparison of the integration of each technology.
- We discuss the open issues and future research directions of integrated V2X networks.
2. V2X Technology
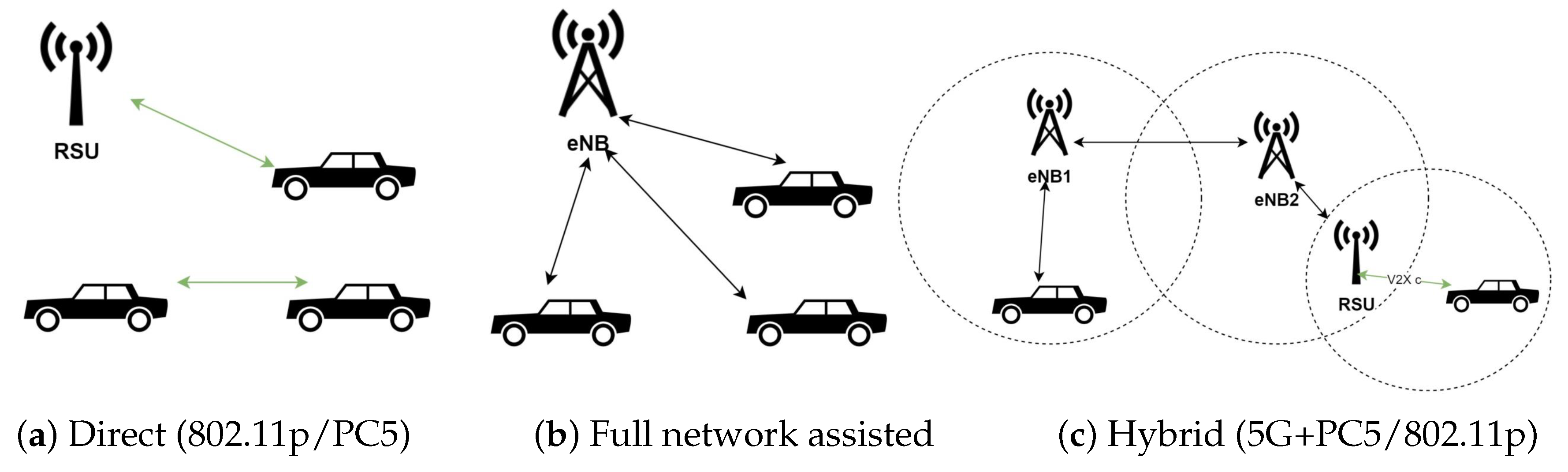
- V2I communication mode: in V2I communications, vehicular nodes communicate with the RSUs within communication range. The RSU can be incorporated in either an eNodeB or a stand-alone traffic signal post.
- V2N communication mode: in V2N mode, vehicular nodes communicate with cellular infrastructures (e.g., eNB), evolved packet switching, remote servers providing extended communication between the vehicles, and cloud-based services through cellular networks. V2N allows to broadcast and unicast communications between vehicular nodes and V2X management systems.
- V2V communication mode: the vehicular nodes communicate with each other at close proximity in an ad-hoc domain, without infrastructures, such as RSUs.
- V2P communication mode: in V2P mode, vehicles connect with pedestrians or bikers on the road to prevent accidents.
2.1. Types of V2X Communications
2.2. State-Of-The-Art V2X Communications
2.2.1. DSRC-Based V2X
2.2.2. Cellular V2X
- V2X based on LTE-Uu Air Interface: LTE-Uu is the standard air interface for connecting User Equipment (UE) and an eNodeB. Each UE that supports the LTE-Uu protocol relays its signal on uplink to the eNB, and the eNB transmits the signal to the destination UE on downlink. The eNB will use semi-persistent scheduling to lower the scheduling overhead that is involved with V2X uplink transmission. In semi-persistent scheduling, the eNB allocates resources to a user over several subsequent transmissions, as most of the traffic is periodic and has similar packet sizes [16].
- V2X based on PC5 Air Interface: according to the the 5G Automotive Association (5GAA), the device-to-device communication mode (i.e., PC-5) must be enabled in C-V2X for direct safety message communication assuring privacy. This mode also works well in the ITS 5.9 GHz band without a paid subscription, and provides privacy. In addition, for commercial applications, such as voice or data access, C-V2X can use V2N mode based on existing licensed cellular networks. The PC5 air interface allows for direct UE communications without requiring each packet to proceed through the eNodeB. The user nodes can exploit the PC5 interface when eNodeB is either present or absent.
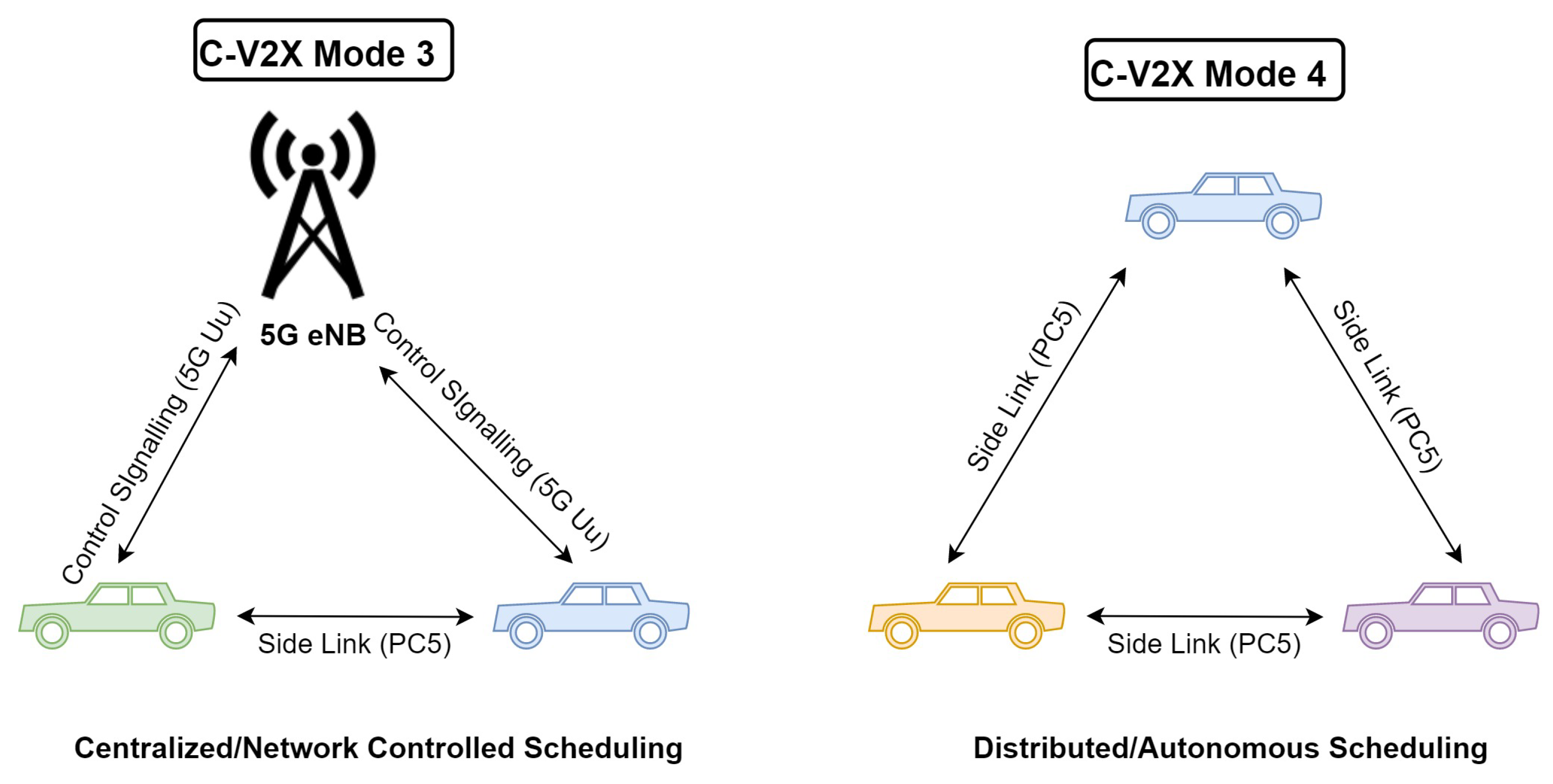
- C-V2X sidelink mode 3: in C-V2X side-link mode 3, the scheduled mode functions only in the presence of a base station or an eNB. The allocation of resources is carried out in a centralized manner by the cellular network. Some of the mode 3 mechanisms are semi-persistent scheduling, UE reports based scheduling, and cross carrier scheduling. However, this mode has an issue in high mobility highway scenarios, where the vehicles should be connected with the eNB.
- C-V2X sidelink mode 4: C-V2X side-link mode 4 functions independently in the absence of eNB support for directly interacting using the PC5 side-link radio interface using a 5.9 GHz frequency band similar to the DSRC. It is also known as autonomous mode. It can interact with other nearby vehicles in a decentralized manner without depending on central cellular network connections. The Mode 4 in C-V2X showed better performance compared to the IEEE 802.11p protocol in several situations during an initial comparison [17]. Moreover, it provides high security for different operating modes.
2.3. Comparison of State-Of-The-Art V2X Technologies
3. Evolution of V2X Technologies
3.1. Evolution of Non-Cellular V2X from 802.11p to 802.11bd
- Coexistence: the 802.11bd standard must coexist with 802.11p. The 802.11bd should detect the 802.11p data transmissions and comply with channel access and vice-versa.
- Interoperability: the 802.11bd and 802.11p standards must be interoperable i.e., devices, information systems or applications should be interoperable in such a way that 802.11p devices can detect and decode at least one of the transmission modes from 802.11bd devices and vice-versa.
- Fairness: the 802.11bd and 802.11p standards must have fair communication and access capabilities in co-channel configurations.
- Backward compatibility: the 802.11bd must be backward compatible in such a way that at least one mode of 802.11bd must be interoperable with 802.11p.
- Midambles: the 802.11p PHY layer was extracted directly from 802.11a, decreasing the spacing of the sub-carrier from 312.5 KHz by a factor of two. In 802.11p, the 156.25 KHz subcarrier spacing generated a trade-off between multipath fading and relative Doppler spread for average vehicle speeds [26]. To overcome this issue, the 802.11bd suggests the use of midambles, similar in structure and function to the preamble except for their position within the frame. The preamble, which is at the start of the frame, is used for the initial estimation of channels. In 802.11bd, the midambles can be inserted with appropriate frequency between OFDM data symbols.
- Re-transmissions: one of the approaches to enhance reliability is to allow one or more packet re-transmissions in both 802.11p and 802.11bd, as shown in Figure 4. For 802.11p applications, the initial transmission and its re-transmissions act as separate packets, and the packets are transmitted successfully as long as one packet is received successfully. Original transmissions and re-transmissions can be either transmitted within the same channel access or by using different contention procedures [27]. In 802.11bd, the Task Group bd (TGbd) introduced an adaptive re-transmission system, where frame re-transmission decisions are based on the level of congestion and the number of re-transmissions [28].
- Alternate OFDM Numerologies: the OFDM performance is based on the ratio of usable symbol length to overall symbol length. The OFDM efficiency increases as subcarrier spacing decreases since the duration of the cyclic prefix becomes invariant to the duration of the symbol. To improve OFDM performance, the 802.11 TGbd participants are investigating the use of narrow OFDM numerologies (i.e., subcarrier spacing) to maximize the number of subcarriers while also maintaining a 10 MHz channel [29]. Nevertheless, the specification of alternative OFDM numerologies should take into account the maximum relative velocities.
- Dual Carrier Modulation (DCM): the DCM is a method used in 802.11ax that includes transmitting the same symbol twice over sufficiently distant sub-carriers to achieve frequency diversity [28]. Because each transmission of symbols is repeated over two different sub-carriers, the order of modulation must be doubled to maintain the throughput. The DCM can help boost the efficiency of block-error-rate (BLER) given the rise in modulation order.
- mmWave Frequencies: the millimeter waves (mmWaves) are usually classified as electromagnetic (radio) waves that lie within the 30–300 GHz frequency spectrum and that can communicate over short distances, but with very high throughput even at lower order MCS (such as video streaming, HD three-dimensional (3D) maps downloading, etc.). The principle for designing mmWave 802.11bd can be legacy 802.11 standards, such as 802.11ad, or its 802.11ay enhancement that already operates within the mmWave bands.
- Other PHY & MAC mechanisms: other characteristics of the PHY layer being considered for use in 802.11bd include the use of Low Density Parity Check (LDPC) codes and multiple transmit/receive antennas to improve the reliability through multiple antennas or increase throughput by spatial multiplexing [24,29]. The 802.11bd standard will leverage the contention parameters of 802.11p with multiple Enhanced Distributed Channel Access types to ensure equitable and fair channel access options for 802.11bd and 802.11p users at the MAC layer.
3.2. Evolution of Cellular V2X
- NR V2X Sidelink Modes: NR V2X defines two side link modes similar to C-V2X. The NR V2X sidelink mode 1 specifies mechanisms, which allows direct vehicle interactions within the coverage of gNodeB. On the other hand, NR V2X side link mode 2 facilitates direct vehicular communications in the out-of-coverage situation.
- Unicast, Groupcast and Broadcast: in Rel.16, NR V2X supports sidelink unicast, groupcast, and broadcast depending upon the scenarios, such as in-coverage, out of coverage, and partial coverage scenarios. For illustration, a transmitting vehicular node that has a single receiver associated with it can transmit in unicast transmission. A vehicle platoon leader can communicate with other platoon member nodes based on groupcast transmission.
- NR Numerologies: a main feature included in 3GPP Rel.15 is the provision of adjustable numerologies. In comparison to a single spacing of the sub-carrier used in LTE, NR embraces various spacings in the sub-carrier, which are multiples of the LTE sub-carrier spacing. The numerology for NR is configured to work with both sub-6 GHz bands and mmWave bands. This is developed by means of multiple numerologies that are formed by the scaling of a fundamental subcarrier spacing (SCS). A scalable OFDM numerology is an improvement introduced in NR, allowing for choice between different subcarrier spacing from 15 KHz up to 480 KHz. The slot length in accordance with these numerologies often varies from 1 ms to 0.031 ms.
- Slot, Mini-slot, and Multi-slot Scheduling: in LTE, the transmission time is closely coupled to the sub frame duration, i.e., all UEs typically communicate for a duration of 1 subframe (1 msec). Besides this, if the user has only a limited amount of data to transmit, which can be accommodated in less than 14 OFDM symbols. It is inefficient to reserve the entire slot for its transmission. In NR V2X, a mini-slot solution is furnished to transfer data using only two, four, or seven OFDM symbols without any slot limits. In addition, slot aggregation (i.e., adding two or more slots to create a multi-slot) would be provided in NR V2X to account for use-cases that need the sharing of large packets.
- Channel Coding: as channel coding has a major effect on the reliability, performance and throughput of wireless systems, more effective and consistent coding methods are implemented. The LTE turbo codes are substituted by LDPC coding for data channel and LTE convolution codes are substituted by Cyclical Redundancy Check (CRC) assisted polar codes for the control channel in NR V2X.
- PHY layer Improvements: NR V2X will provide several other PHY layer improvements, most of which are derived from 5G NR. These involve the use of LDPC coding, higher order MCS like 64-QAM, and a dynamic number of Demodulation Reference Signal (DMRS) symbols per slot.
- New sub-modes of NR Sidelink Mode 2: unlike C-V2X sidelink mode 4, where there are no sub-modes, the 3GPP started evaluating four new sub-modes of NR V2X sidelink mode 2, i.e., from mode 2 (a) to mode 2(d) [30]. C-V2X sidelink mode 4, resource reservation algorithm leverages the periodicity and fixed-size data of basic safety messages. In general, this presumption is no longer valid for use in NR V2X, so the resource selection process should be re-engineered.
3.2.1. Evolution from Lte-V2X to 5G NR V2X
3.2.2. Comparison between Cellular and Non-Cellular V2X Technologies
4. Edge Computing for V2X Communications
- MEC should provide interoperability by allowing exchange of V2X information among vehicles connected through various access technologies or mobile operators or networks.
- MEC should provide service continuity, and access-network coverage across the country and between multi-operators.
- MEC should provide interoperability in a multi-operator environment that enables MEC applications to communicate securely in various systems even in the absence of cellular network.
- MEC should provide secure multi-operator communication between MEC applications with V2X-related core network control functions.
- MEC should provide feedback information from the network to the vehicles in order to guarantee the reliability of the communication channel in supporting V2X functionality.
5. Issues and Challenges in 5G and Edge-Based V2X
5.1. Data Integrity
5.2. Data Availability
5.3. Data Privacy Management
5.4. Immutability
5.5. Transparency Requirements
5.6. Traceability
5.7. Heterogeneity and Interoperability
5.8. Low-Latency
5.9. Wireless Resource Management
5.10. Resource Scaling
6. Blockchain Potential in V2X Networks
6.1. Blockchain Overview
6.2. Blockchain as a Security Mechanism in V2X
- Traceability: each participating vehicle should show data provenance to identify the data flow tracing i.e., the source of the information and any changes in ownership during transmission through the transaction.
- Transparency: the information exchanged between participating vehicles, such as critical accident information, traffic-related messages, etc., should be transparent among the member nodes in the blockchain network, except for the private information. This helps legitimate vehicular nodes obtain information regarding traffic situations and lets them respond accordingly.
- Resilience: if a transaction is erroneous or was corrupted, the corruption is immediately evident, and all the vehicles are kept informed of it. A new transaction can be used to resolve an error, as well as the corrupted transactions can be recovered.
- Immutability: this prevents the event or critical messages from being tampered with after they have been registered in the database.
6.2.1. Motivation for Using Blockchain in V2X
6.2.2. Challenges of Implementing Blockchain in V2X
6.3. Integrating Blockchain with Mec and 5G Technology in V2X Networks
6.3.1. Integration of Blockchain with Cellular Technology in V2X
6.3.2. Integration of Blockchain with Mec in V2X
6.3.3. Integration of Blockchain with 5G-Based Edge Computing in V2X
7. Open Issues and Future Research Directions
7.1. Performance and Scalability Issues
- Storage: a massive volume of data transactions such as information storage, management of resources and vehicle transactions are generated due to the integration of blockchain in 5G-based MEC in vehicular networks. In conventional blockchain, all of the nodes store a copy of complete blockchain transactions. As a result, the blockchain bloats and results in a computational and storage load on resource-constrained vehicles [89].
- Throughput: the performance concerns include limited throughput in terms of number of transactions per second, and delays that are scaused by additional time to add block transactions into the blockchain [90]. The blockchain has limited block size, and the block generation time grows rapidly due to long waiting time for transactions to be added on the chain that results in limited throughput.
- Network Resource: in the context of integrated blockchain and 5G-based MEC environments, high density networks with large number of heterogeneous and resource constrained devices, consume lots of resources. It might be difficult to fulfill the resource requirements of blockchain in order to accomplish large-scale transaction processing. Moreover, the blockchain consumes large network resources in terms of transmission power, mining, and bandwidth based on the consensus mechanism that results in high latency [91].
- Blockchain Incentive and Penalty Mechanisms: an efficient incentive mechanism should be built so that the incentives are assigned to the miners in a fair manner. Thus, a future direction for research is to develop an efficient and robust incentive mechanism with fair distribution to encourage all parties and miners to engage in the blockchain. In addition, penalty systems are also necessary to discourage any malicious entity from performing harmful activities.
7.2. Security and Privacy Issues
7.3. Quality of Service (QoS) Issue
7.4. Future Research Directions
7.4.1. Integrated Blockchain, 5G-Based Mec and Big Data
7.4.2. Blockchain beyond 5G
7.4.3. Machine Learning Integrated with Blockchain for 5G-Based Mec
8. Conclusions
Funding
Conflicts of Interest
References
- US Department of Transportation (DoT). Connected Vehicles. 2020. Available online: https://www.its.dot.gov/cv_basics/cv_basics_what.htm (accessed on 17 February 2020).
- Sjoberg, K.; Andres, P.; Buburuzan, T.; Brakemeier, A. Cooperative Intelligent Transport Systems in Europe: Current Deployment Status and Outlook. IEEE Veh. Technol. Mag. 2017, 12, 89–97. [Google Scholar] [CrossRef]
- Xie, L.; Ding, Y.; Yang, H.; Wang, X. Blockchain-Based Secure and Trustworthy Internet of Things in SDN-Enabled 5G-VANETs. IEEE Access 2019, 7, 56656–56666. [Google Scholar] [CrossRef]
- ETSI. Technical Specification Group Services and System Aspects. In Security Aspect for LTE Support of Vehicle-to-Everything (V2X) Services; Technical Report; 3GPP TS 33.185 V14.1.0.; ETSI: Sophia Antipolis Cedex, France, 2017. [Google Scholar]
- 3GPP. Technical specification group services and system aspects. In Study on Architecture Enhancements for EPS and 5G System to Support Advanced V2X Services; Technical Report; 3GPP TR 23.786 v0.8.0.; 3GPP: Sophia Antipolis Valbonne, France, 2018. [Google Scholar]
- Bazzi, A.; Masini, B.M.; Zanella, A.; Calisti, A. Visible light communications as a complementary technology for the internet of vehicles. Comput. Commun. 2016, 93, 39–51. [Google Scholar] [CrossRef]
- Masini, B.M.; Bazzi, A.; Zanella, A. Vehicular Visible Light Networks for Urban Mobile Crowd Sensing. Sensors 2018, 18, 1177. [Google Scholar] [CrossRef]
- ISO. Technical Committee ISO/TC 204. In Intelligent Transport Systems—Communication Access for Land Mobiles (CALM)—Millimetre Wave Air Interface; ISO: Geneva, Switzerland, 2012. [Google Scholar]
- Choi, J.; Va, V.; Gonzalez-Prelcic, N.; Daniels, R.; Bhat, C.R.; Heath, R.W. Millimeter-Wave Vehicular Communication to Support Massive Automotive Sensing. IEEE Commun. Mag. 2016, 54, 160–167. [Google Scholar] [CrossRef]
- Khairnar, V.D.; Kotecha, K. Performance of Vehicle-to-Vehicle Communication using IEEE 802.11p in Vehicular Ad-hoc Network Environment. Int. J. Netw. Secur. Its Appl. 2013, 5, 143–170. [Google Scholar] [CrossRef]
- Bajracharya, R.; Shrestha, R.; Jung, H. Future Is Unlicensed: Private 5G Unlicensed Network for Connecting Industries of Future. Sensors 2020, 20, 2774. [Google Scholar] [CrossRef]
- Bajracharya, R.; Shrestha, R.; Ali, R.; Musaddiq, A.; Kim, S.W. LWA in 5G: State-of-the-Art Architecture, Opportunities, and Research Challenges. IEEE Commun. Mag. 2018, 56, 134–141. [Google Scholar] [CrossRef]
- ETSI. Digital cellular telecommunications system (Phase 2+) (GSM) TR21.914. In Release Description; Release 14; Technical Report; ETSI: Sophia Antipolis Cedex, France, 2017. [Google Scholar]
- 3GPP. Technical specification Group Radio Access Network. Evolved Universal Terrestrial Radio Access (E-UTRA); Physical layer procedures, Rel.15, TR 36.213 v15.3.0; Technical Report; 3GPP: Sophia Antipolis Valbonne, France, 2018. [Google Scholar]
- Naik, G.; Choudhury, B.; Park, J.M. IEEE 802.11bd 5G NR V2X: Evolution of Radio Access Technologies for V2X Communications. IEEE Access 2019, 7, 70169–70184. [Google Scholar] [CrossRef]
- 3GPP. 3GPP TR 36.885—Study on LTE-Based V2X Services. 2016. Available online: https://itectec.com/archive/3gpp-specification-tr-36-885 (accessed on 25 May 2020).
- Haider, A.; Hwang, S.H. Adaptive Transmit Power Control Algorithm for Sensing-Based Semi-Persistent Scheduling in C-V2X Mode 4 Communication. Electronics 2019, 8, 846. [Google Scholar] [CrossRef]
- 5G Automotive Association. The Case for Cellular V2X for Safety and Cooperative Driving. In 5GAA Whitepaper; 5G Automotive Association: Munich, Germany, 2016; pp. 1–8. [Google Scholar]
- Autotalks. DSRC vs. C-V2X for Safety Applications. 2019. Available online: https://www.auto-talks.com/technology/dsrc-vs-c-v2x-2. (accessed on 1 November 2019).
- 5GAA. 5GAA: Paving the Way towards 5G. Available online: https://5gaa.org/5g-technology/paving-the-way (accessed on 17 February 2020).
- Conway, S. V2X Technology Benchmark Testing. Available online: https://ecfsapi.fcc.gov/file/109271050222769/5GAA%209.25.18%20Ex%20Parte%20Notice.pdf (accessed on 20 May 2020).
- 3GPP. Study on Enhancement of 3GPP Support for 5G V2X Services; Technical Report 22.886, G.T.; 3GPP: Sophia Antipolis Valbonne, France, 2016. [Google Scholar]
- Hassan, M.I.; Vu, H.L.; Sakurai, T. Performance Analysis of the IEEE 802.11 MAC Protocol for DSRC Safety Applications. IEEE Trans. Veh. Technol. 2011, 60, 3882–3896. [Google Scholar] [CrossRef]
- Cao, R.; Zhang, H.; Sharma, P. Potential PHY Designs for NGV. IEEE 802.11-19/0016r0, 01. 2020. Available online: https://mentor.ieee.org/802.11/documents?n=2&is_dcn=ngv (accessed on 17 March 2020).
- Sun, B. 802.11 NGV Proposed PAR. 2020. Available online: https://www.ieee802.org/11/Reports/tgbd_update.htm (accessed on 19 March 2020).
- Cheng, L.; Henty, B.E.; Cooper, R.; Stancil, D.D.; Bai, F. A Measurement Study of Time-Scaled 802.11a Waveforms Over The Mobile-to-Mobile Vehicular Channel at 5.9 GHz. IEEE Commun. Mag. 2008, 46, 84–91. [Google Scholar] [CrossRef]
- Fischer, M.; Filippi, A.; Martinez, V. Additional Details about Interoperable NGV PHY Improvements; NXP: Austin, TX, USA, 2018; pp. 1–16. [Google Scholar]
- Fischer, M. IEEE 802.11-18/1186r0: Interoperable NGV PHY Improvements; Technical Report; NXP: Austin, TX, USA, 2018. [Google Scholar]
- Cao, R.; Zhang, H.; Sharma, P. Doppler Impact on OFDM Numerology for NGV; Marvell: Santa Clara, CA, USA, 2018; Available online: https://mentor.ieee.org/802.11/documents?is_group=0ngv (accessed on 10 September 2018).
- Intel Corporation. R11809867: Offline Summary for NR-V2X Agenda Item—7.2.4.1.4 Resource Allocation Mechanism; Technical Report; Intel Corporation: Gothenburg, Sweden, 2018. [Google Scholar]
- 3GPP. 3GPP: Initial Cellular V2X Standard Completed; 3GPP: Sophia Antipolis Valbonne, France, 2017; Available online: https://www.3gpp.org/newsevents/3gppnews/1798v2x (accessed on 19 July 2020).
- 5G Americas. 5G-Evolution-3GPP-R16-R17; Technical Report; 5G Americas: Bellevue, DC, USA, 2020. [Google Scholar]
- Anwar, W.; Traßl, A.; Franchi, N.; Fettweis, G. On the Reliability of NR-V2X and IEEE 802.11bd. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Mukherjee, A. 5G New Radio: Beyond Mobile Broadband; Artech House: London, UK, 2019. [Google Scholar]
- IEEE. 3GPP Release 15 Overview. 2020. Available online: https://spectrum.ieee.org/telecom/wireless/3gpp-release-15-overview (accessed on 15 May 2020).
- ETSI. Multi-access Edge Computing (MEC): Study on MEC Support for V2X Use Cases; Technical Report; ETSI: Sophia Antipolis Cedex, France, 2018. [Google Scholar]
- Maharjan, S.; Zhu, Q.; Zhang, Y.; Gjessing, S.; Basar, T. Dependable Demand Response Management in the Smart Grid: A Stackelberg Game Approach. IEEE Trans. Smart Grid 2013, 4, 120–132. [Google Scholar] [CrossRef]
- Madhok, A. Global Connected Car Revenues to Grow Five-Fold by 2025; Counterpoint: Hong Kong, China, 2019; Available online: https://www.counterpointresearch.com/connected-car-revenues-grow-five-fold-2025 (accessed on 15 May 2020).
- Al-Omary, A. A Secure Framework for Mobile Cloud Computing. In Proceedings of the 2019 International Conference on Innovation and Intelligence for Informatics, Computing, and Technologies (3ICT), Sakhier, Bahrain, 22–23 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Shah, S.A.A.; Ahmed, E.; Imran, M.; Zeadally, S. 5G for Vehicular Communications. IEEE Commun. Mag. 2018, 56, 111–117. [Google Scholar] [CrossRef]
- Ning, Z.; Wang, X.; Huang, J. Mobile Edge Computing-Enabled 5G Vehicular Networks: Toward the Integration of Communication and Computing. IEEE Veh. Technol. Mag. 2019, 14, 54–61. [Google Scholar] [CrossRef]
- Zhang, Y.; Yu, R.; Xie, S.; Yao, W.; Xiao, Y.; Guizani, M. Home M2M networks: Architectures, standards, and QoS improvement. IEEE Commun. Mag. 2011, 49, 44–52. [Google Scholar] [CrossRef]
- Zhang, Y.; Yu, R.; Nekovee, M.; Liu, Y.; Xie, S.; Gjessing, S. Cognitive machine-to-machine communications: Visions and potentials for the smart grid. IEEE Netw. 2012, 26, 6–13. [Google Scholar] [CrossRef]
- Li, J.; Wu, J.; Chen, L. Block-secure: Blockchain based scheme for secure P2P cloud storage. Inf. Sci. 2018, 465, 219–231. [Google Scholar] [CrossRef]
- Liu, H.; Zhang, P.; Pu, G.; Yang, T.; Maharjan, S.; Zhang, Y. Blockchain Empowered Cooperative Authentication With Data Traceability in Vehicular Edge Computing. IEEE Trans. Veh. Technol. 2020, 69, 4221–4232. [Google Scholar] [CrossRef]
- Musaddiq, A.; Ali, R.; Bajracharya, R.; Qadri, Y.A.; Al-Turjman, F.; Kim, S.W. Trends, Issues, and Challenges in the Domain of IoT-Based Vehicular Cloud Network BT—Unmanned Aerial Vehicles in Smart Cities; Springer: Cham, Switzerland, 2020; pp. 49–64. [Google Scholar] [CrossRef]
- Lewis, G.A. Role of Standards in Cloud-Computing Interoperability. In Proceedings of the 2013 46th Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2013; pp. 1652–1661. [Google Scholar]
- Asadi, A.; Wang, Q.; Mancuso, V. A Survey on Device-to-Device Communication in Cellular Networks. IEEE Commun. Surv. Tutor. 2014, 16, 1801–1819. [Google Scholar] [CrossRef]
- Cloud Standards Customer Council. Interoperability and Portability for Cloud Computing: A Guide Version 2.0; Technical Report; Object Management Group (OMG): Milford, CT, USA, 2017. [Google Scholar]
- Olaniyan, R.; Fadahunsi, O.; Maheswaran, M.; Zhani, M.F. Opportunistic Edge Computing: Concepts, opportunities and research challenges. Future Gener. Comput. Syst. 2018, 89, 633–645. [Google Scholar] [CrossRef]
- Shrestha, R.; Kim, S. Integration of IoT with blockchain and homomorphic encryption: Challenging issues and opportunities. In Advances in Computers; Kim, S., Deka, G.C., Zhang, P., Eds.; Elsevier: Amsterdam, The Netherlands, 2019; Volume 115, pp. 293–331. [Google Scholar] [CrossRef]
- Shrestha, R.; Bajracharya, R.; Nam, S.Y. Blockchain-based Message Dissemination in VANET. In Proceedings of the 2018 IEEE 3rd International Conference on Computing, Communication and Security (ICCCS), Kathmandu, Nepal, 25–27 October 2018; pp. 161–166. [Google Scholar]
- Singh, M.; Kim, S. Branch based blockchain technology in intelligent vehicle. Comput. Netw. 2018, 145, 219–231. [Google Scholar] [CrossRef]
- Dorri, A.; Steger, M.; Kanhere, S.; Jurdak, R. BlockChain: A distributed solution to automotive security and privacy. IEEE Commun. Mag. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef]
- Makhdoom, I.; Abolhasan, M.; Abbas, H.; Ni, W. Blockchain’s adoption in IoT: The challenges, and a way forward. J. Netw. Comput. Appl. 2019, 125, 251–279. [Google Scholar] [CrossRef]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 3690–3700. [Google Scholar] [CrossRef]
- Tian, F. An agri-food supply chain traceability system for China based on RFID & blockchain technology. In Proceedings of the 2016 13th International Conference on Service Systems and Service Management (ICSSSM), Kunming, China, 24–26 June 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Gao, J.; Asamoah, K.O.; Sifah, E.B.; Smahi, A.; Xia, Q.; Xia, H.; Zhang, X.; Dong, G. GridMonitoring: Secured Sovereign Blockchain Based Monitoring on Smart Grid. IEEE Access 2018, 6, 9917–9925. [Google Scholar] [CrossRef]
- Mubarakali, A.; Bose, S.C.; Srinivasan, K.; Elsir, A.; Elsier, O. Design a secure and efficient health record transaction utilizing block chain (SEHRTB) algorithm for health record transaction in block chain. J. Ambient. Intell. Humaniz. Comput. 2019. [Google Scholar] [CrossRef]
- Chen, B.; He, D.; Kumar, N.; Wang, H.; Choo, K.R. A Blockchain-Based Proxy Re-Encryption with Equality Test for Vehicular Communication Systems. IEEE Trans. Netw. Sci. Eng. 2020. [Google Scholar] [CrossRef]
- Shrestha, R.; Bajracharya, R.; Shrestha, A.; Nam, S.Y. A New-Type of Blockchain for Secure Message Exchange in VANET. Digit. Commun. Netw. 2020, 6, 177–186. [Google Scholar] [CrossRef]
- Buterin, V. ANext-generation Smart Contract and Decentralized Application Platform. In When Satoshi Nakamoto; Ethereum Foundation, 2015; pp. 1–36. Available online: https://blockchainlab.com/pdf/Ethereum_white_paper-a_next_generation_smart_contract_and_decentralized_application_platform-vitalik-buterin.pdf (accessed on 19 July 2020).
- Shrestha, R.; Bajracharya, R.; Nam, S.Y. Centralized Approach for Trustworthy Message Dissemination in VANET. In Proceedings of the NOMS 2018—2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, 23–27 April 2018. [Google Scholar]
- Park, J.H.; Park, J.H. Blockchain Security in Cloud Computing: Use Cases, Challenges, and Solutions. Symmetry 2017, 9, 164. [Google Scholar] [CrossRef]
- Kim, S. Blockchain for a Trust Network Among Intelligent Vehicles, 1st ed.; Elsevier Inc.: Amsterdam, The Netherlands, 2018; Volume 111. [Google Scholar] [CrossRef]
- Singh, M.; Kim, S. Trust Bit: Reward-based intelligent vehicle commination using blockchain paper. In Proceedings of the 2018 IEEE 4th World Forum on Internet of Things (WF-IoT), Singapore, 5–8 February 2018; pp. 62–67. [Google Scholar] [CrossRef]
- Kim, M.; Jang, I.; Choo, S.; Koo, J.; Pack, S. Collaborative security attack detection in software-defined vehicular networks. In Proceedings of the 2017 19th Asia-Pacific Network Operations and Management Symposium (APNOMS), Seoul, Korea, 27–29 September 2017; pp. 19–24. [Google Scholar] [CrossRef]
- Kim, S.; Deka, G.C. Advanced Applications of Blockchain Technology; Springer: Singapore, 2020. [Google Scholar] [CrossRef]
- De La Torre, G.; Rad, P.; Choo, K.K.R. Driverless vehicle security: Challenges and future research opportunities. Future Gener. Comput. Syst. 2018, 108, 1092–1111. [Google Scholar] [CrossRef]
- Leiding, B.; Memarmoshrefi, P.; Hogrefe, D. Self-managed and blockchain-based vehicular ad-hoc networks. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing Adjunct—UbiComp ’16, Heidelberg, Germany, 12–16 September 2016; pp. 137–140. [Google Scholar] [CrossRef]
- Shrestha, R.; Nam, S.Y. Regional Blockchain for Vehicular Networks to Prevent 51% Attacks. IEEE Access 2019, 7, 95033–95045. [Google Scholar] [CrossRef]
- Rasheed, I.; Zhang, L.; Hu, F. A privacy preserving scheme for vehicle-to-everything communications using 5G mobile edge computing. Comput. Netw. 2020, 176, 1–12. [Google Scholar] [CrossRef]
- Huang, X.; Yu, R.; Kang, J.; He, Y.; Zhang, Y. Exploring Mobile Edge Computing for 5G-Enabled Software Defined Vehicular Networks. IEEE Wirel. Commun. 2017, 24, 55–63. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Zhang, Y. Joint Computation Offloading and User Association in Multi-Task Mobile Edge Computing. IEEE Trans. Veh. Technol. 2018, 67, 12313–12325. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Zhang, Y. Joint Load Balancing and Offloading in Vehicular Edge Computing and Networks. IEEE Internet Things J. 2019, 6, 4377–4387. [Google Scholar] [CrossRef]
- Chen, M.; Hao, Y.; Hu, L.; Hossain, M.S.; Ghoneim, A. Edge-CoCaCo: Toward Joint Optimization of Computation, Caching, and Communication on Edge Cloud. IEEE Wirel. Commun. 2018, 25, 21–27. [Google Scholar] [CrossRef]
- Nguyen, D.C.; N Pathirana, P.; Ding, M.; Seneviratne, A. Blockchain for 5G and Beyond Networks: A State of the Art Survey. arXiv 2019, arXiv:1912.05062. [Google Scholar]
- Bajracharya, R.; Shrestha, R.; Kim, S.W. An admission control mechanism for 5G LWA. Sustainability 2018, 10, 1999. [Google Scholar] [CrossRef]
- Ortega, V.; Bouchmal, F.; Monserrat, J.F. Trusted 5G Vehicular Networks: Blockchains and Content-Centric Networking. IEEE Veh. Technol. Mag. 2018, 13, 121–127. [Google Scholar] [CrossRef]
- Rahmadika, S.; Lee, K.; Rhee, K. Blockchain-Enabled 5G Autonomous Vehicular Networks. In Proceedings of the 2019 International Conference on Sustainable Engineering and Creative Computing (ICSECC), Bandung, Indonesia, 20–22 August 2019; pp. 275–280. [Google Scholar] [CrossRef]
- Aujla, G.S.; Singh, A.; Singh, M.; Sharma, S.; Kumar, N.; Choo, K.R. BloCkEd: Blockchain-Based Secure Data Processing Framework in Edge Envisioned V2X Environment. IEEE Trans. Veh. Technol. 2020, 69, 5850–5863. [Google Scholar] [CrossRef]
- Cebe, M.; Erdin, E.; Akkaya, K.; Aksu, H.; Uluagac, S. Block4Forensic: An Integrated Lightweight Blockchain Framework for Forensics Applications of Connected Vehicles. IEEE Commun. Mag. 2018, 56, 50–57. [Google Scholar] [CrossRef]
- Singh, M.; Kim, S. Blockchain Based Intelligent Vehicle Data sharing Framework. arXiv 2017, arXiv:1708.09721. [Google Scholar]
- Liu, M.; Yu, F.R.; Teng, Y.; Leung, V.C.M.; Song, M. Computation Offloading and Content Caching in Wireless Blockchain Networks With Mobile Edge Computing. IEEE Trans. Veh. Technol. 2018, 67, 11008–11021. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Zhang, K.; Maharjan, S.; Zhang, Y. Deep Reinforcement Learning and Permissioned Blockchain for Content Caching in Vehicular Edge Computing and Networks. IEEE Trans. Veh. Technol. 2020, 69, 4312–4324. [Google Scholar] [CrossRef]
- Iqbal, S.; Malik, A.W.; Rahman, A.U.; Noor, R.M. Blockchain-Based Reputation Management for Task Offloading in Micro-Level Vehicular Fog Network. IEEE Access 2020, 8, 52968–52980. [Google Scholar] [CrossRef]
- Mukherjee, M.; Matam, R.; Shu, L.; Maglaras, L.; Ferrag, M.A.; Choudhury, N.; Kumar, V. Security and Privacy in Fog Computing: Challenges. IEEE Access 2017, 5, 19293–19304. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Chen, Z.; He, Q.; Zhang, Y. Blockchain and Deep Reinforcement Learning Empowered Intelligent 5G Beyond. IEEE Netw. 2019, 33, 10–17. [Google Scholar] [CrossRef]
- Wang, W.; Hoang, D.T.; Hu, P.; Xiong, Z.; Niyato, D.; Wang, P.; Wen, Y.; Kim, D.I. A Survey on Consensus Mechanisms and Mining Strategy Management in Blockchain Networks. IEEE Access 2019, 7, 22328–22370. [Google Scholar] [CrossRef]
- Kim, S.; Kwon, Y.; Cho, S. A Survey of Scalability Solutions on Blockchain. In Proceedings of the 9th International Conference on Information and Communication Technology Convergence: ICT Convergence Powered by Smart Intelligence, ICTC 2018, Jeju, Korea, 17–19 October 2018; pp. 1204–1207. [Google Scholar] [CrossRef]
- Xie, J.; Yu, F.R.; Huang, T.; Xie, R.; Liu, J.; Liu, Y. A Survey on the Scalability of Blockchain Systems. IEEE Netw. 2019, 33, 166–173. [Google Scholar] [CrossRef]
- Sanka, A.I.; Cheung, R.C.C. Efficient High Performance FPGA based NoSQL Caching System for Blockchain Scalability and Throughput Improvement. In Proceedings of the 2018 26th International Conference on Systems Engineering (ICSEng), Sydney, Australia, 18–20 December 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Hazari, S.S.; Mahmoud, Q.H. A Parallel Proof of Work to Improve Transaction Speed and Scalability in Blockchain Systems. In Proceedings of the 2019 IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 916–921. [Google Scholar] [CrossRef]
- Xiong, W.; Xiong, L. Smart Contract Based Data Trading Mode Using Blockchain and Machine Learning. IEEE Access 2019, 7, 102331–102344. [Google Scholar] [CrossRef]
- Ali, S.; Wang, G.; White, B.; Cottrell, R.L. A Blockchain-Based Decentralized Data Storage and Access Framework for PingER. In Proceedings of the 2018 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 1303–1308. [Google Scholar] [CrossRef]
- Petrillo, A.; Pescapé, A.; Santini, S. A collaborative approach for improving the security of vehicular scenarios: The case of platooning. Comput. Commun. 2018, 122, 59–75. [Google Scholar] [CrossRef]
- Petrillo, A.; Pescapé, A.; Santini, S. A Secure Adaptive Control for Cooperative Driving of Autonomous Connected Vehicles in the Presence of Heterogeneous Communication Delays and Cyberattacks. IEEE Trans. Cybern. 2020, 1–16. [Google Scholar] [CrossRef] [PubMed]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Future Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Möser, M.; Soska, K. An empirical analysis of linkability in the monero blockchain. arXiv 2017, arXiv:1704.04299. [Google Scholar]
- Luu, L.; Velner, Y.; Teutsch, J.; Saxena, P. Smartpool: Practical Decentralized Pooled Mining. In Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 1409–1426. [Google Scholar]
- Cheng, R.; Zhang, F.; Kos, J.; He, W.; Hynes, N.; Johnson, N.; Juels, A.; Miller, A.; Song, D. Ekiden: A Platform for Confidentiality-Preserving, Trustworthy, and Performant Smart Contracts. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy (EuroS&P), Stockholm, Sweden, 17–19 June 2019; pp. 185–200. [Google Scholar] [CrossRef]
- Tsankov, P.; Dan, A.; Drachsler-Cohen, D.; Gervais, A.; Bünzli, F.; Vechev, M. Securify: Practical Security Analysis of Smart Contracts; Association for Computing Machinery: New York, NY, USA, 2018; pp. 67–82. [Google Scholar] [CrossRef]
- Yu, F.R. “vDLT: A Service-Oriented Blockchain System with Virtualization and Decoupled Management/Control and Execution. arXiv 2018, arXiv:1809.00290. [Google Scholar]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017; pp. 618–623. [Google Scholar] [CrossRef]
- Kim, T.; Noh, J.; Cho, S. SCC: Storage Compression Consensus for Blockchain in Lightweight IoT Network. In Proceedings of the 2019 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 11–13 January 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, K.; Lin, Y.; Xu, W. LightChain:A Lightweight Blockchain System for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2019, 15, 3571–3581. [Google Scholar] [CrossRef]
- Zaman, M.U.; Shen, T.; Min, M. Proof of Sincerity: A New Lightweight Consensus Approach for Mobile Blockchains. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Shen, H.; Zhou, J.; Cao, Z.; Dong, X.; Choo, K.R. Blockchain-based Lightweight Certificate Authority for Efficient Privacy-preserving Location-Based Service in Vehicular Social Networks. IEEE Internet Things J. 2020, 7, 6610–6622. [Google Scholar] [CrossRef]
- Xiong, Z.; Feng, S.; Niyato, D.; Wang, P.; Han, Z. Optimal Pricing-Based Edge Computing Resource Management in Mobile Blockchain. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Qiu, C.; Yao, H.; Jiang, C.; Guo, S.; Xu, F. Cloud Computing Assisted Blockchain-Enabled Internet of Things. IEEE Trans. Cloud Comput. 2019, 1. [Google Scholar] [CrossRef]
- Sharma, P.K.; Singh, S.; Jeong, Y.S.; Park, J.H. DistBlockNet: A Distributed Blockchains-Based Secure SDN Architecture for IoT Networks. IEEE Commun. Mag. 2017, 55, 78–85. [Google Scholar] [CrossRef]
- Mishra, A.D.; Singh, Y.B. Big data analytics for security and privacy challenges. In Proceedings of the 2016 International Conference on Computing, Communication and Automation (ICCCA), Noida, India, 29–30 April 2016; pp. 50–53. [Google Scholar] [CrossRef]
- Sultan, K.; Ali, H.; Zhang, Z. Big Data Perspective and Challenges in next Generation Networks. Future Internet 2018, 10, 56. [Google Scholar] [CrossRef]
- Karafiloski, E.; Mishev, A. Blockchain solutions for big data challenges: A literature review. In Proceedings of the IEEE EUROCON 2017—17th International Conference on Smart Technologies, Ohrid, Macedonia, 6–8 July 2017; pp. 763–768. [Google Scholar] [CrossRef]
- Uchibeke, U.U.; Schneider, K.A.; Kassani, S.H.; Deters, R. Blockchain Access Control Ecosystem for Big Data Security. In Proceedings of the 2018 IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1373–1378. [Google Scholar] [CrossRef]
- Lampropoulos, K.; Georgakakos, G.; Ioannidis, S. Using Blockchains to Enable Big Data Analysis of Private Information. In Proceedings of the 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Limassol, Cyprus, 11–13 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Saad, W.; Bennis, M.; Chen, M. A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems. IEEE Netw. 2020, 34, 134–142. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. arXiv 2019, arXiv:1909.11315. [Google Scholar] [CrossRef]
- Yaacoub, E.; Alouini, M.S. A Key 6G Challenge and Opportunity—Connecting the Remaining 4 Billions: A Survey on Rural Connectivity. arXiv 2019, arXiv:1906.11541. [Google Scholar]
- Tiba, K.; Choo, K.K.R.; Parizi, R.M.; Zhang, Q.; Dehghantanha, A.; Karimipour, H.; Choo, K.K.R. Secure Blockchain-Based Traffic Load Balancing Using Edge Computing and Reinforcement Learning. In Blockchain Cybersecurity, Trust and Privacy; Advances in Information Security; Dehghantanha, A., Reza, M., Eds.; Springer Nature: Geneva, Switzerland, 2020; Volume 79, pp. 99–128. [Google Scholar] [CrossRef]


| Components | DSRC V2X | Cellular V2X |
|---|---|---|
| Specification Completion | Completed | Rel.14/15 completed & Rel.16 in progress (as of 2019) |
| Technology | Wi-Fi | LTE/ 4G |
| Modulation | OFDM | SC-FDM |
| Retransmission | No HARQ | HARQ |
| Connectivity | Hybrid mode, i.e., connects with cellular network for non-safety services | Hybrid model, i.e., connects with peer vehicles based on PC5 mode |
| Network communication | Limited (Via APs only) | Full support |
| Resource selection | CSMA-CA | Semi persistent Tx with comparative energy-based selection |
| Line coding | Convolution code | Turbo code |
| Deployment | Started in 2017. Commercialized in 2019 | Mass market distribution in China by the end of 2020 |
| Future guideline | Backward compatible and interoperable upgrade to 802.11bd | C-V2X Rel.16 based on 5G NR and operates on different channel |
| Latency | Low latency for V2V communications | Round trip latency less than 1ms, minor delay due to centralized communication |
| Range | Good for short radio range | Good for extended communication |
| High mobility support | Upto relative speed of 500 km/h with advanced receiver support | Up to 500km/hr as a minimum requirement |
| High density support | Packet loss at high density | No packet loss guaranteed at high density |
| Security and Privacy on V2V/ V2I/V2P | Yes (based on IEEE WAVE & ETSI ITS security services) | Yes (based on IEEE WAVE & ETSI ITS security services) |
| Security and Privacy on V2N | N/A | Yes |
| Evolution path | Towards 802.11bd | Compatible with Rel -14/15 |
| Use Case | Communication Mode | Pyaload (Bytes) | Max. Delay (msec) | Datarate (Mbps) | Minimum Range (m) | Reliability |
|---|---|---|---|---|---|---|
| Advanced driving | V2V, V2I | 300–12,000 | 3∼100 ms | 10–50 | 360–500 | 90–99.999 |
| Remote driving | V2N | - | 5 ms | UL:25/DL:1 | - | 99.999 |
| Vehicle platooning | V2V, V2I | 50–6000 | 10∼500 ms | 50–65 | 80–350 | 90–99.99 |
| Extended sensors | V2V, V2I, V2P | 1600 | 3∼100 ms | 10–1000 | 50–1000 | 90–99.999 |
| Features/ Mechanisms | 802.11bd | 802.11p |
|---|---|---|
| Frequency band | 5.9 GHz/60 GHz | 5.9 GHz |
| Sub-carrier spacing | 312.5 KHz/156.25 KHz/78.125 KHz | 156.25 KHz |
| Channel coding | LDPC | BCC |
| Re-transmission | Congestion dependent | None |
| Cyclic Prefix (CP) | 1.6 us and 3.2 us | 1.6 us |
| Spatial streams | Multiple | One |
| Relative vehicle speed | 500 km/hr | 252 km/h |
| Doppler shift counter measures | High density midambles | None |
| Features | LTE | 5G NR |
|---|---|---|
| Frequency band | Up to 6 GHz | Up to 5.9 GHz; mmWave (upto 52 GHz) |
| PHY layer | SC-FDMA | SC-FDMA, OFDM |
| Carrier aggregation | Up to 32 | Up to 16 |
| Digital beamforming | Up to 8 layers | Up to 12 layers |
| Channel coding | Data: Turbo coding Control: Convolution coding | Data: LDPC coding Control: Polar coding |
| MCS | QPSK, 16-QAM | QPSK, 16-QAM, 64- QAM |
| Control & data multiplexing | FDM | TDM |
| Scheduling interval | One sub-frame | Slot, mini-slot or multi-slot |
| Side link modes | Modes 3 and 4 | Modes 1 and 2 |
| Spectrum occupancy | Up to 90% of channel BW | Up to 98% of channel BW |
| Features | 802.11p | 802.11bd | LTE V2X | NR V2X |
|---|---|---|---|---|
| Base technology | 802.11a/n | IEEE802.11n/ac | 4G/LTE | 5GNR |
| Radio bands | 5.9 GHz | 5.9 GHz,60 GHz | 5.9 GHz | 5.9 GHz∼52.6 GHz including mmWave |
| Channel coding | BCC | LDPC | Data:Turbo coding Control:Convolution coding | Data:LDPC Control: Polar coding |
| Subcarrier spacing | 156.25 KHz | 312.5 KHz, 156.25 KHz, 78.15 KHz | 15 KHz | Sub-6 GHz:15,30,60 KHz mmWave:60, 120 KHz |
| Retransmission | None | Congestion dependent | Blind | HARQ-based |
| Modes | Broadcast | Broadcast, groupcast | Broadcast | Broadcast, groupcast, unicast |
| PHY layer | N/A | OFDM | SC-FDMA | SC-FDMA, OFDM |
| Interoperability | N/A | Yes | N/A | Non co-channel |
| mmWave support | N/A | Yes | N/A | Yes |
| Items | MEC | MCC |
|---|---|---|
| Architecture | Distributed | Centralized |
| Operators | Mobile operators | Cloud providers |
| Target user | Mobile devices | Internet users |
| Hierarchy | Three-tier | Two-tier |
| Data storage | Short duration | Long duration |
| Server nodes | Large in number | small in number |
| Bandwidth demands | Based on data sent to clouds | Based on data generated by users |
| Location awareness | Yes | No |
| Communication overhead | Medium | High |
| Information access | Localized information | Globalized information |
| Delay allowance | Lesser than 10ms | Few seconds or greater |
| Connectivity | Intermittent | uninterrupted |
| Service provider | Cisco IOx | Amazon, IBM, Microsoft |
| Environment | Can exist indoors or outdoors | Exists indoor/consumes large space |
| Authors | Ref. | Description | Block Chain | MEC | Cellular /5G | System Characteristics |
|---|---|---|---|---|---|---|
| Leiding et al. (2016) | [70] | Proposed a self-managed, Ethereum blockchain- based VANET | Private BC | No | No | Ethereum incorporated with VANET; applications related to traffic regulations, traffic jams, weather etc. |
| Shrestha et.al (2016) | [71] | Proposed a regional blockchain based VANET to prevent 51% attacks | Regional BC | No | No | Designed regional blockchain to achieve low 51% attack success probability with several control parameters |
| Rasheed et. al. (2020) | [72] | Presented new privacy- preserving protocol in VANET using 5G-based edge computing | No | MEC | Yes | Effective privacy preservation method, which can be applied by MEC based on 5G-V2X communications architecture with enhanced iCLASC security scheme. |
| Huang et al. (2017) | [73] | Proposed 5G-enabled SDVNs with MEC to handle vehicle groups in 5G | No | MEC | Yes | VANET integrated with MEC to push the computation from vehicles to the Edge node for improved performance. |
| Paper | Ref. No. | Description | Blockchain/ Consensus | Edge Comp. | Cellular /5G | System Characteristics |
|---|---|---|---|---|---|---|
| Ortega et al. (2018) | [79] | Presented Content Centric Networking (CCN) based on BC for secure vehicular communications | Permiss- ioned BC | No | Yes | Used CCN instead of TCP/ IP & allowed BC to monitor source confidentiality, quality & authenticity of shared data |
| Rahma- dika et al (2019) | [80] | Proposed BC-enabled 5G autonomous vehicular networks | Permiss- ioned BC/ BFT/PoD | No | Yes | Presented secondary auth- entication in 5G networks & model inter BC comm. |
| Dorri et al. (2017) | [54] | Proposed a BC-based vehicular networks to protect vehicle privacy & improve security | Public BC managed by overlay nodes | Cloud storage | No | Decentralized security & privacy via overlay netwo- rks for smart cars;immune to prevalent security threats |
| Cebe et al. (2018) | [82] | Proposed a BC for hand- ling vehicle data & foren- sics applications | Permiss- ioned BC /PoC | Private cloud | No | Used decentralized ledger with reduced storage & consumes low overhead |
| Liu et al. (2018) | [84] | Proposed computation offloading & content caching in BC with MEC | Public BC /PoW | MEC | No | Used MEC enabled-block chain using two offloading modes;offl- oadsPoW & content caching using stochastic game theory. |
| Dai et al. (2020) | [85] | Proposed deep RL & per- missioned BC for content caching in edge-based vehicular networks | Permiss- ioned BC/ PoU | MEC | No | Vehicles & RSU acts as edge servers for intelligent content caching; caching at edge are performed by integrating BC using PoU & DLR. |
| Singh et al. (2017) | [83] | Proposed an intelligent vehicles data sharing framework based on BC | Permiss- ioned BC /PoD | VCC | No | Seven-layer conceptual struc- ture layout compatible with real-time traffic information |
| Iqbal et al. (2020) | [86] | Proposed Fog-computing using RSUs to offload tasks to neighboring fog vehicles, based on reput ation scores held at BC | semi-private consortium/ PoET | Fog | No | System maintains BC at RSUs, retaining a social reputation in VANET. Evaluate system based on task completion, end-to-end delay & queuing delay. |
| Xie et al. (2019) | [3] | Investigates security, privacy & trust issues combined with BC in SDN-enabled 5G-VANET. | PoW + PoS | Cloud -based | Yes | BC is maintained by OBUs, RSUs and gNBs that records all road information & maintains trust management to evade fake msg. |
| Dai et al. (2019) | [88] | Proposed a secure and intelligent architecture for 5G & beyond net- works by integrating deep RL & BC in V2X. | Consort- ium BC /PoW | MEC | Yes | Adopt BC-enabled resource management, spectrum sharing, content caching, & offload com- putation. Max. system utility by sharing problem in BC em- powered by DRL in 5G VANET. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shrestha, R.; Nam, S.Y.; Bajracharya, R.; Kim, S. Evolution of V2X Communication and Integration of Blockchain for Security Enhancements. Electronics 2020, 9, 1338. https://doi.org/10.3390/electronics9091338
Shrestha R, Nam SY, Bajracharya R, Kim S. Evolution of V2X Communication and Integration of Blockchain for Security Enhancements. Electronics. 2020; 9(9):1338. https://doi.org/10.3390/electronics9091338
Chicago/Turabian StyleShrestha, Rakesh, Seung Yeob Nam, Rojeena Bajracharya, and Shiho Kim. 2020. "Evolution of V2X Communication and Integration of Blockchain for Security Enhancements" Electronics 9, no. 9: 1338. https://doi.org/10.3390/electronics9091338
APA StyleShrestha, R., Nam, S. Y., Bajracharya, R., & Kim, S. (2020). Evolution of V2X Communication and Integration of Blockchain for Security Enhancements. Electronics, 9(9), 1338. https://doi.org/10.3390/electronics9091338








