Energy-Aware Wireless Sensor Networks for Smart Buildings: A Review
Abstract
:1. Introduction
2. Literature Review
3. Hardware Layer
3.1. The Hardware Platform (Microcontroller and CPU)
3.2. Radio Frequency Module
3.3. Energy-Aware Modulation Techniques
4. Operating System Layer
4.1. TinyOS
4.2. Contiki
4.3. Mantis
4.4. Nano-RK
4.5. LiteOS
5. Application Layer
5.1. Directed Diffusion
5.2. Chain Construction Protocol
5.3. Probabilistic Model
5.4. A Simple, Single Cluster Model Using Data Correlation
5.5. Query Model
5.6. Data Aggregation Techniques
5.7. Energy-Aware Context Recognition Algorithm (EACRA)
6. Networking Layer
6.1. The Network Layer Protocols
- (1)
- Low-Energy Adaptive Clustering Hierarchy (LEACH)
- (2)
- Threshold-Sensitive Energy-Efficient Sensor Network Protocol (TEEN)
- (3)
- Adaptive Periodic Threshold-Sensitive Energy-Efficient Sensor Network Protocol (APTEEN)
- (4)
- Power-Efficient Gathering in Sensor Information Systems (PEGASIS)
- (5)
- Sensor Protocols for Information via Negotiation (SPIN)
- (6)
- Rumor Routing (RR)
- (7)
- Geographical Energy-Aware Routing (GEAR)
- (8)
- Geographic Adaptive Fidelity (GAF)
- (9)
- Energy-Aware Routing Protocol (EARP)
6.2. The Data Link Layer Protocols
- (1)
- Sensor-MAC Protocol
- (2)
- Timeout-MAC Protocol
- (3)
- D-MAC Protocol
- (4)
- Traffic-Adaptive Medium Access (TRAMA)
- (5)
- Sparse Topology and Energy Management (STEM)
6.3. Network Topologies for WSN
- (1)
- Star Topology
- (2)
- Tree Topology
- (3)
- Mesh Topology
- (4)
- Cluster Topology
7. Energy Storage in IoT Devices
7.1. Nickel-Cadmium Battery
7.2. Nickel Metal Hydride (NiMH)
7.3. Alkaline
7.4. Zinc-Carbon
7.5. Lithium Polymer
7.6. Energy Autonomy
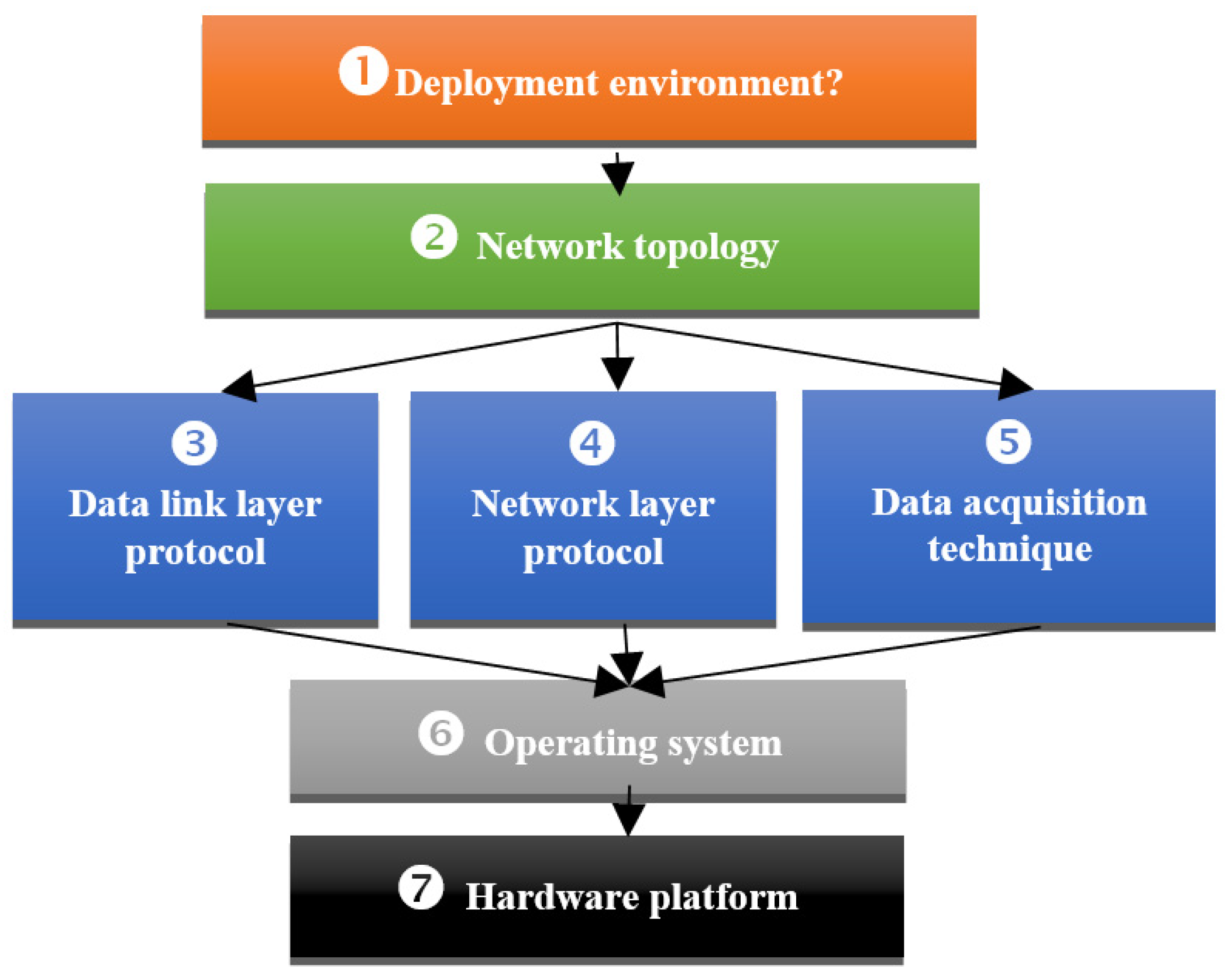
8. Proposed Framework to Design Energy-Aware WSN for SEEB
8.1. Deployment Environment
8.2. Network Topology
8.3. Data Link Layer Protocol
8.4. Network Layer Protocol
8.5. Data Acquisition Technique
8.6. Operating System
8.7. Hardware Platform
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Kanoun, O.; Bradai, S.; Khriji, S.; Bouattour, G.; El Houssaini, D.; Ben Ammar, M.; Naifar, S.; Bouhamed, A.; Derbel, F.; Viehweger, C. Energy-Aware System Design for Autonomous Wireless Sensor Nodes: A Comprehensive Review. Sensors 2021, 21, 548. [Google Scholar] [CrossRef] [PubMed]
- Priyadarshi, R.; Gupta, B.; Anurag, A. Deployment techniques in wireless sensor networks: A survey, classification, challenges, and future research issues. J. Supercomput. 2020, 76, 7333–7373. [Google Scholar] [CrossRef]
- Kandris, D.; Nakas, C.; Vomvas, D.; Koulouras, G. Applications of Wireless Sensor Networks: An Up-to-Date Survey. Appl. Syst. Innov. 2020, 3, 14. [Google Scholar] [CrossRef] [Green Version]
- Singh, P.K.; Bhargava, B.K.; Paprzycki, M.; Kaushal, N.C.; Hong, W.C. (Eds.) Handbook of Wireless Sensor Networks: Issues and Challenges in Current Scenario’s; Springer: Berlin/Heidelberg, Germany, 2020. [Google Scholar]
- Boaventura, A.S.; Carvalho, N.B. A low-power wake-up radio for application in WSN-based indoor location systems. Int. J. Wirel. Inform. Netw. 2013, 20, 67–73. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef] [Green Version]
- Gravina, R.; Alinia, P.; Ghasemzadeh, H.; Fortino, G. Multi-sensor fusion in body sensor networks: State-of-the-art and research challenges. Inf. Fusion 2017, 35, 68–80. [Google Scholar] [CrossRef]
- Berthier, F.; Beigne, E.; Vivet, P.; Sentieys, O. Power gain estimation of an event-driven wake-up controller dedicated to WSN’s microcontroller. In Proceedings of the IEEE 13th International New Circuits and Systems Conference (NEWCAS), Grenoble, France, 7–10 June 2015; pp. 1–4. [Google Scholar]
- Karray, F.; Jmal, M.W.; Garcia-Ortiz, A.; Abid, M.; Obeid, A.M. A comprehensive survey on wireless sensor node hardware platforms. Comput. Netw. 2018, 144, 89–110. [Google Scholar] [CrossRef]
- Selmic, R.R.; Phoha, V.V.; Serwadda, A. Wireless Sensor Networks; Springer International Publishing AG: New York, NY, USA, 2016. [Google Scholar]
- Rashid, B.; Rehmani, M.H. Applications of wireless sensor networks for urban areas: A survey. J. Netw. Comput. Appl. 2016, 60, 192–219. [Google Scholar] [CrossRef]
- Engmann, F.; Katsriku, F.A.; Abdulai, J.-D.; Adu-Manu, K.S.; Banaseka, F.K. Prolonging the Lifetime of Wireless Sensor Networks: A Review of Current Techniques. Wirel. Commun. Mob. Comput. 2018, 2018, 1–23. [Google Scholar] [CrossRef] [Green Version]
- Kumar, N.; Singh, Y. Routing protocols in wireless sensor networks. In Handbook of Research on Advanced Wireless Sensor Network Applications, Protocols, and Architectures; IGI Global: Hershey, PA, USA, 2017; pp. 86–128. [Google Scholar]
- Li, W.; Kara, S. Methodology for Monitoring Manufacturing Environment by Using Wireless Sensor Networks (WSN) and the Internet of Things (IoT). Procedia CIRP 2017, 61, 323–328. [Google Scholar] [CrossRef]
- Mysore, S.; Agrawal, B.; Chong, F.T.; Sherwood, T. Exploring the Processor and ISA Design for Wireless Sensor Network Applications. In Proceedings of the 21st International Conference on VLSI Design (VLSID 2008), Hyderabad, India, 4–8 January 2008; pp. 59–64. [Google Scholar] [CrossRef] [Green Version]
- Abu Alsheikh, M.; Lin, S.; Niyato, D.; Tan, H.-P. Rate-Distortion Balanced Data Compression for Wireless Sensor Networks. IEEE Sens. J. 2016, 16, 5072–5083. [Google Scholar] [CrossRef] [Green Version]
- Yussoff, Y.; Abidin, H.Z.; Rahman, R.A.; Yahaya, F.H. Development of a PIC-based wireless sensor node utilizing XBee technology. In Proceedings of the 2nd IEEE International Conference on Information Management and Engineering, Chengdu, China, 16–18 April 2010; pp. 116–120. [Google Scholar] [CrossRef]
- Song, Y.; Gong, C.; Feng, Y.; Ma, J.; Zhang, X. Design of Greenhouse Control System Based on Wireless Sensor Networks and AVR Microcontroller. J. Netw. 2011, 6, 1668. [Google Scholar] [CrossRef] [Green Version]
- Handziski, V.; Polastre, J.; Hauer, J.H.; Sharp, C. Flexible hardware abstraction of the TI MSP430 mi-crocontroller in TinyOS. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems; ACM: New York, NY, USA, 2004; pp. 277–278. [Google Scholar]
- Costa, F.M.; Ochiai, H. Energy-Efficient Physical Layer Design for Wireless Sensor Network Links. In Proceedings of the 2011 IEEE International Conference on Communications (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–5. [Google Scholar] [CrossRef]
- Han, D.-M.; Lim, J.-H. Smart home energy management system using IEEE 802.15.4 and zigbee. IEEE Trans. Consum. Electron. 2010, 56, 1403–1410. [Google Scholar] [CrossRef]
- Boonsawat, V.; Ekchamanonta, J.; Bumrungkhet, K.; Kittipiyakul, S. XBee wireless sensor networks for temperature monitoring. In Proceedings of the 2nd Conference on Application Research and Development (ECTI-CARD 2010), Chon Buri, Thailand, 5–8 May 2016. [Google Scholar]
- XBee. XBee-PRO™ OEM RF Modules. In Product Manual v1. xAx-802.15, 4; XBee: Hopkins, MN, USA, 2013. [Google Scholar]
- Schurgers, C.; Aberthorne, O.; Srivastava, M. Modulation scaling for energy aware communication systems. In Proceedings of the 2001 International Symposium on Low Power Electronics and Design; ACM: New York, NY, USA, 2001; pp. 96–99. [Google Scholar]
- Yang, K.; Song, L. AMC for TwoWayAmplify-and-Forward Relay Networks. In Proceedings of the IEEE International Conference on Communications, Xiamen, China, 28–30 July 2021. [Google Scholar]
- Kim, D.; Jung, B.C.; Lee, H.; Sung, D.K.; Yoon, H. Optimal Modulation and Coding Scheme Selection in Cellular Networks with Hybrid-ARQ Error Control. IEEE Trans. Wirel. Commun. 2008, 7, 5195. [Google Scholar] [CrossRef]
- Chen, S.; Zhao, C.; Wu, M.; Sun, Z.; Zhang, H.; Leung, V.C. Compressive network coding for wireless sensor net-works: Spatio-temporal coding and optimization design. Comput. Netw. 2016, 108, 345–356. [Google Scholar] [CrossRef]
- Mazloum, N.S.; Edfors, O. Comparing analog front-ends for duty-cycled wake-up receivers in wireless sensor net-works. IEEE Sens. J. 2016, 16, 7016–7021. [Google Scholar] [CrossRef] [Green Version]
- Middya, R.; Chakravarty, N.; Naskar, M.K. Compressive sensing in wireless sensor networks—A survey. IEEE Tech. Rev. 2017, 34, 642–654. [Google Scholar] [CrossRef]
- Mukesh, S.; Iqbal, M.; Jianhua, Z.; Ping, Z.; Rehman, I.U. Comparative Analysis of M-ary Modulation Techniques for Wireless Ad-hoc Networks. In Proceedings of the 2007 IEEE Sensors Applications Symposium, San Diego, CA, USA, 6–8 February 2007; pp. 1–6. [Google Scholar] [CrossRef]
- Howard, S.L.; Schlegel, C.; Iniewski, K. Error Control Coding in Low-Power Wireless Sensor Networks: When Is ECC Energy Efficient? EURASIP J. Wireless Commun. Netw. 2006, 2006, 74812. [Google Scholar] [CrossRef] [Green Version]
- Kadel, R.; Paudel, K.; Guruge, D.B.; Halder, S.J. Opportunities and Challenges for Error Control Schemes for Wireless Sensor Networks: A Review. Electronics 2020, 9, 504. [Google Scholar] [CrossRef] [Green Version]
- Yang, J.; Khandani, A.K.; Tin, N. Adaptive Modulation and Coding in 3G Wireless Systems; Technical Report Number UWE&CE#2002-15; IEEE: Piscataway, NJ, USA, 2002. [Google Scholar]
- Morelos-Zaragoza, R.H.; Fossorier, M.P.C.; Imai, H. Multilevel Coded Modulation for Unequal Error Protection and Multistage Decoding—Part I: Symmetric Constellations. IEEE Trans. Commun. 2000, 48, 2. [Google Scholar] [CrossRef]
- Salih, S.H.O.; Suliman, M.M.A. Implementation of AMC Technique. Int. J. Sci. Eng. Res. 2011, 2, 5. [Google Scholar]
- Islam, M.R. Error Correction Codes in Wireless Sensor Network: An Energy Aware approach. Int. J. Comput. Inform. Eng. 2010, 4, 1. [Google Scholar]
- Yousof Naderi, M.; Rabiee, H.R.; Khansari, M. Performance Analysis of Selected Error Control Protocols in Wireless Multimedia Sensor Networks. In Proceedings of the 18th Annual IEEE/ACM International Symposium on Modeling, Analysis and Simu-lation of Computer and Telecommunication Systems, Miami Beach, FL, USA, 17–19 August 2010. [Google Scholar]
- Wang, Z.; Chiang, P.-Y.; Nazari, P.; Wang, C.-C.; Chen, Z.; Heydari, P. A CMOS 210-GHz Fundamental Transceiver with OOK Modulation. IEEE J. Solid-State Circuits 2014, 49, 564–580. [Google Scholar] [CrossRef]
- Hahm, O.; Baccelli, E.; Petersen, H.; Tsiftes, N. Operating Systems for Low-End Devices in the Internet of Things: A Survey. IEEE Internet Things J. 2016, 3, 720–734. [Google Scholar] [CrossRef] [Green Version]
- Sharma, D. Low Cost Experimental set up for Real Time Temperature, Humidity Monitoring through WSN. Int. J. Eng. Sci. 2017, 7, 4340. [Google Scholar]
- Amjad, M.; Sharif, M.; Afzal, M.K.; Kim, S.W. TinyOS-new trends, comparative views, and supported sensing applications: A review. IEEE Sens. J. 2016, 16, 2865–2889. [Google Scholar] [CrossRef]
- Durmaz, C.; Challenger, M.; Dagdeviren, O.; Kardas, G. Modelling Contiki-Based IoT Systems; OA-SIcs-OpenAccess Series in Informatics; Schloss Dagstuhl-Leibniz-Zentrum fuer Informatik: Wadern, Germany, 2017; Volume 56. [Google Scholar]
- Bhatti, S.; Carlson, J.; Dai, H.; Deng, J.; Rose, J.; Sheth, A.; Shucker, B.; Gruenwald, C.; Torgerson, A.; Han, R. MANTIS OS: An Embedded Multithreaded Operating System for Wireless Micro Sensor Platforms. Mob. Netw. Appl. 2005, 10, 563–579. [Google Scholar] [CrossRef]
- Eswaran, A.; Rowe, A.; Rajkumar, R. Nano-rk: An energy-aware resource-centric rtos for sensor net-works. In Proceedings of the 26th IEEE International Real-Time Systems Symposium (RTSS’05), Miami, FL, USA, 5–8 December 2005; p. 10. [Google Scholar]
- Cao, Q.; Abdelzaher, T. LiteOS: A lightweight operating system for C++ software development in sensor networks. In Proceedings of the 4th International Conference on Embedded Networked Sensor Systems; ACM: New York, NY, USA, 2006; pp. 361–362. [Google Scholar]
- Intanagonwiwat, C.; Govindan, R.; Estrin, D. Directed diffusion: A scalable and robust communication paradigm for sensor networks. In Proceedings of the 6th Annual International Conference on Mobile Computing and Networking; ACM: New York, NY, USA, 2000; pp. 56–67. [Google Scholar]
- Du, K.; Wu, J.; Zhou, D. Chain-Based Protocols for Data Broadcasting and Gathering in the Sensor Networks; IEEE: Piscataway, NJ, USA, 2003; p. 8. [Google Scholar] [CrossRef] [Green Version]
- Chen, J.; Li, J.; He, S.; Sun, Y.; Chen, H.-H. Energy-Efficient Coverage Based on Probabilistic Sensing Model in Wireless Sensor Networks. IEEE Commun. Lett. 2010, 14, 833–835. [Google Scholar] [CrossRef]
- Jiang, H.; Jin, S.; Wang, C. Prediction or Not? An Energy-Efficient Framework for Clustering-Based Data Collection in Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2010, 22, 1064–1071. [Google Scholar] [CrossRef]
- Chipara, O.; Lu, C.; Roman, G.-C. Real-Time Query Scheduling for Wireless Sensor Networks. In 28th IEEE International Real-Time Systems Symposium (RTSS 2007); IEEE: Piscataway, NJ, USA, 2007; pp. 389–399. [Google Scholar] [CrossRef] [Green Version]
- Singh, K. WSN LEACH based protocols: A structural analysis. In 2015 International Conference and Workshop on Computing and Communication (IEMCON); IEEE: Piscataway, NJ, USA, 2015; pp. 1–7. [Google Scholar] [CrossRef]
- Madden, S.; Franklin, M.J.; Hellerstein, J.M.; Hong, W. TAG: A tiny aggregation service for ad-hoc sensor networks. ACM SIGOPS Oper. Syst. Rev. 2002, 36, 131–146. [Google Scholar] [CrossRef]
- Mahajan, S.; Dhiman, P.K. Clustering in Wireless Sensor Networks: A Review. Int. J. Adv. Res. Comput. Sci. 2016, 7, 3. [Google Scholar]
- Ambigavathi, M.; Sridharan, D. Energy-Aware Data Aggregation Techniques in Wireless Sensor Network. In Advances in Power Systems and Energy Management; Springer: Berlin/Heidelberg, Germany, 2018; pp. 165–173. [Google Scholar] [CrossRef]
- Incel, O.D.; Krishnamachari, B. Enhancing the Data Collection Rate of Tree-Based Aggregation in Wireless Sensor Networks. In Proceedings of the 5th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, San Francisco, CA, USA, 16–20 June 2008; pp. 569–577. [Google Scholar] [CrossRef]
- Qing, L.; Zhu, Q.; Wang, M. Design of a distributed energy-efficient clustering algorithm for heterogeneous wireless sensor networks. Comput. Commun. 2006, 29, 2230–2237. [Google Scholar] [CrossRef]
- Vikash; Mishra, L.; Varma, S. Middleware Technologies for Smart Wireless Sensor Networks towards Internet of Things: A Comparative Review. Wirel. Pers. Commun. 2021, 116, 1539–1574. [Google Scholar] [CrossRef]
- Naji, N.; Abid, M.R.; Krami, N.; Benhaddou, D. An Energy-Aware Wireless Sensor Network for Data Acquisition in Smart Energy Efficient Building. In 2019 IEEE 5th World Forum on Internet of Things (WF-IoT); IEEE: Piscataway, NJ, USA, 2019; pp. 7–12. [Google Scholar]
- Manjeshwar, A.; Agrawal, D. TEEN: A routing protocol for enhanced efficiency in wireless sensor networks. In Proceedings of the15th International Parallel and Distributed Processing Symposium, IPDPS 2001, San Francisco, CA, USA, 23–27 April 2001; pp. 2009–2015. [Google Scholar] [CrossRef]
- Manjeshwar, A.; Agrawal, D.P. APTEEN: A hybrid protocol for efficient routing and comprehensive information retrieval in wireless sensor networks. In Proceedings of the International Parallel and Distributed Processing Symposium (IPDPSí); IEEE: Piscataway, NJ, USA, 2002; p. 195. [Google Scholar]
- Lindsey, S.; Raghavendra, C. PEGASIS: Power-efficient gathering in sensor information systems. In IEEE Aerospace Conference; IEEE: Piscataway, NJ, USA, 2003. [Google Scholar] [CrossRef]
- Jing, L.; Liu, F.; Li, Y. Energy saving routing algorithm based on SPIN protocol in WSN. In 2011 International Conference on Image Analysis and Signal Processing; IEEE: Piscataway, NJ, USA, 2011; pp. 416–419. [Google Scholar] [CrossRef]
- Braginsky, D.; Estrin, D. Rumor routing algorthim for sensor networks. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications; ACM: New York, NY, USA, 2002; pp. 22–31. [Google Scholar]
- Nadeem, Q.; Rasheed, M.B.; Javaid, N.; Khan, Z.A.; Maqsood, Y.; Din, A. M-GEAR: Gateway-based energy-aware multi-hop routing protocol for WSNs. In 2013 Eighth International Conference on Broadband and Wireless Computing, Communication and Applications (BWCCA); IEEE: Piscataway, NJ, USA, 2013; pp. 164–169. [Google Scholar]
- Roychowdhury, S.; Patra, C. Geographic Adaptive Fidelity and Geographic Energy Aware Routing in Ad Hoc Routing. Int. J. Comput. Commun. Technol. 2011, 2, 91–95. [Google Scholar] [CrossRef]
- Liu, M.; Cao, J.; Chen, G.; Wang, X. An Energy-Aware Routing Protocol in Wireless Sensor Networks. Sensors 2009, 9, 445–462. [Google Scholar] [CrossRef]
- Le, H.P.; John, M.; Pister, K. Energy-Aware Routing in Wireless Sensor Networks with Adaptive Energy-Slope Control; EE290Q-2 Spring; IEEE: Piscataway, NJ, USA, 2009. [Google Scholar]
- Amdouni, I.; Adjih, C.; Aitsaadi, N.; Muhlethaler, N. ODYSSE: A Routing Protocol for Wireless Sensor Networks. RR-8873, UPEC; Inria Saclay; Inria: Paris, France, 2016. [Google Scholar]
- Yoo, H.; Shim, M.; Kim, D.; Kim, K.H. GLOBAL: A Gradient-based routing protocol for load-balancing in large-scale wireless sensor networks with multiple sinks. In Proceedings of the IEEE Symposium on Computers and Communications, Riccione, Italy, 22–25 June 2010; pp. 556–562. [Google Scholar] [CrossRef]
- Shirazi, S.S.; Haqiqat, A.T. Energy Efficient Hierarchical Cluster-Based Routing for Wireless Sensor Networks. Int. J. Comput. Sci. Netw. Secur. 2016, 16, 115. [Google Scholar]
- Faheem, M.; Gungor, V. Energy efficient and QoS-aware routing protocol for wireless sensor network-based smart grid applications in the context of industry 4. Appl. Soft Comput. 2018, 68, 910–922. [Google Scholar] [CrossRef]
- Khoufi, I.; Minet, P.; Laouiti, A.; Mahfoudh, S. Survey of deployment algorithms in wireless sensor networks: Coverage and connectivity issues and challenges. Int. J. Autonomous Adapt. Commun. Syst. 2017, 10, 341–390. [Google Scholar] [CrossRef]
- Maimour, M.; Zeghilet, H.; Lepage, F. Sustainable Wireless Sensor Networks; Cluster-based Routing Protocols for Energy-Efficiency in Wireless Sensor Networks; Intech: Vienna, Austria, 2010; pp. 167–188. [Google Scholar]
- Wei, C.; Yang, J.; Gao, Y.; Zhang, Z. Cluster-based Routing Protocols in Wireless Sensor Networks: A Survey. In Proceedings of the International Conference on Computer Science and Network Technology (ICCSNT ’11), Harbin, China, 24–26 December 2011; pp. 1659–1663. [Google Scholar]
- Guleria, K.; Verma, A.K. Comprehensive review for energy efficient hierarchical routing protocols on wireless sensor networks. Wirel. Netw. 2019, 25, 1159–1183. [Google Scholar] [CrossRef]
- Anasane, A.A.; Satao, R.A. A Survey on Various Multipath Routing Protocols in Wireless Sensor Networks. Procedia Comput. Sci. 2016, 79, 610–615. [Google Scholar] [CrossRef] [Green Version]
- Liu, X. A Survey on Clustering Routing Protocols in Wireless Sensor Networks. Sensors 2012, 12, 11113–11153. [Google Scholar] [CrossRef]
- Manap, Z.; Ali, B.M.; Ng, C.K.; Noordin, N.K.; Sali, A. A Review on Hierarchical Routing Protocols for Wireless Sensor Networks. Wirel. Pers. Commun. 2013, 72, 1077–1104. [Google Scholar] [CrossRef]
- Gherbi, C.; Aliouat, Z.; Benmohammed, M. A survey on clustering routing protocols in wireless sensor networks. Sens. Rev. 2017, 37, 12–25. [Google Scholar] [CrossRef]
- Sikander, G.; Zafar, M.H.; Raza, A.; Babar, M.I.; Mahmud, S.A.; Khan, G.M. A Survey of Cluster-based Routing Schemes for Wireless Sensor Networks. Smart Comput. Rev. 2013, 3, 261–275. [Google Scholar] [CrossRef]
- Singh, S.P.; Sharma, S. A Survey on Cluster Based Routing Protocols in Wireless Sensor Networks. Procedia Comput. Sci. 2015, 45, 687–695. [Google Scholar] [CrossRef] [Green Version]
- Mehmood, A.; Song, H. Smart Energy Efficient Hierarchical Data Gathering Protocols for Wireless Sensor Networks. Smart Comput. Rev. 2015, 425–462. [Google Scholar] [CrossRef]
- Liu, X. Atypical Hierarchical Routing Protocols for Wireless Sensor Networks: A Review. IEEE Sens. J. 2015, 15, 5372–5383. [Google Scholar] [CrossRef]
- Abid, R.M.; Saad, B. An interference-aware routing metric for Wireless Mesh Networks. Int. J. Mob. Commun. 2011, 9, 619. [Google Scholar] [CrossRef]
- Abid, M.R. AAI3446193—Link Quality Characterization in IEEE 802.11s Wireless Mesh Networks. Ph.D. Thesis, Auburn University, Auburn, AL, USA, 2010. [Google Scholar]
- Ye, W.; Heidemann, J.; Estrin, D. An energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the INFOCOM 21st Annual Joint Conference of the IEEE Computer and Communications Societies; IEEE: Piscataway, NJ, USA, 2002; Volume 3, pp. 1567–1576. [Google Scholar]
- Van Dam, T.; Langendoen, K. An adaptive energy-efficient MAC protocol for wireless sensor networks. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems; ACM: New York, NY, USA, 2003; pp. 171–180. [Google Scholar]
- Lu, G.; Krishnamachari, B.; Raghavendra, C. An adaptive energy-efficient and low-latency MAC for data gathering in wireless sensor networks. In 18th International Parallel and Distributed Processing Symposium; IEEE: Piscataway, NJ, USA, 2004; p. 224. [Google Scholar] [CrossRef]
- Ye, W.; Heidemann, J.; Estrin, D. Medium Access Control with Coordinated Adaptive Sleeping for Wireless Sensor Networks. IEEE/ACM Trans. Netw. 2004, 12, 493–506. [Google Scholar] [CrossRef] [Green Version]
- Schurgers, C.; Tsiatsis, V.; Srivastava, M. STEM: Topology management for energy efficient sensor networks. In IEEE Aerospace Conference; IEEE: Piscataway, NJ, USA, 2003; Volume 3. [Google Scholar] [CrossRef]
- Linden, D. Handbook of Batteries and Fuel Cells; McGraw-Hill Book Co.: New York, NY, USA, 1984; 1075p. [Google Scholar]
- Varghese, S.G.; Kurian, C.P.; George, V.I.; John, A.; Nayak, V.; Upadhyay, A. Comparative study of zigBee topologies for IoT-based lighting automation. IET Wirel. Sens. Syst. 2019, 9, 201–207. [Google Scholar] [CrossRef]
- Ari, D.; Cibuk, M.; Aggun, F. The Comparison of Energy Consumption of Different Topologies in Multi-hop Wireless Sensor Networks. In 2018 International Conference on Artificial Intelligence and Data Processing (IDAP); IEEE: Piscataway, NJ, USA, 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Buk, M.; Cengiz, M.S. Determination of Energy Consumption According to Wireless Network Topologies in Grid-Free Lighting Systems. Light Eng. 2020, 28, 2. [Google Scholar]
- Gawali, S.K.; Deshmukh, M.K. Energy Autonomy in IoT Technologies. Energy Procedia 2019, 156, 222–226. [Google Scholar] [CrossRef]
- Ashraf, S.; Saleem, S.; Ahmed, T.; Aslam, Z.; Muhammad, D. Conversion of adverse data corpus to shrewd output using sampling metrics. Vis. Comput. Ind. Biomed. Art 2020, 3, 1–13. [Google Scholar] [CrossRef] [PubMed]
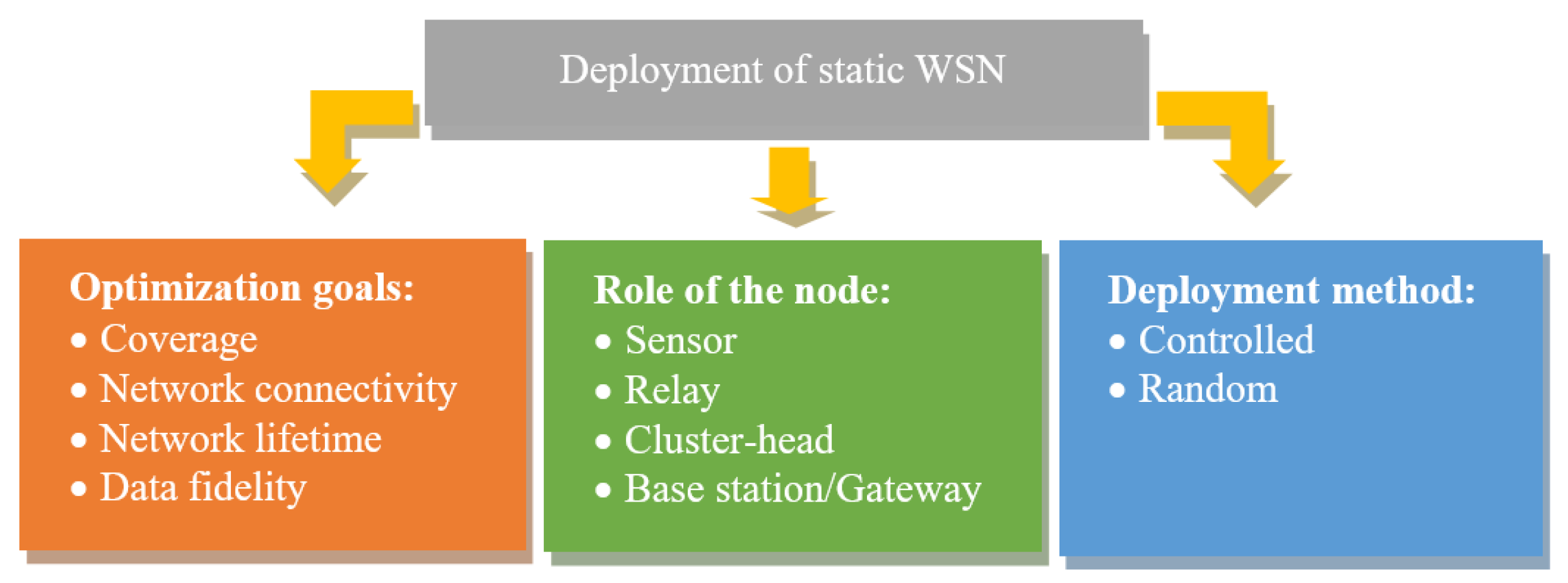
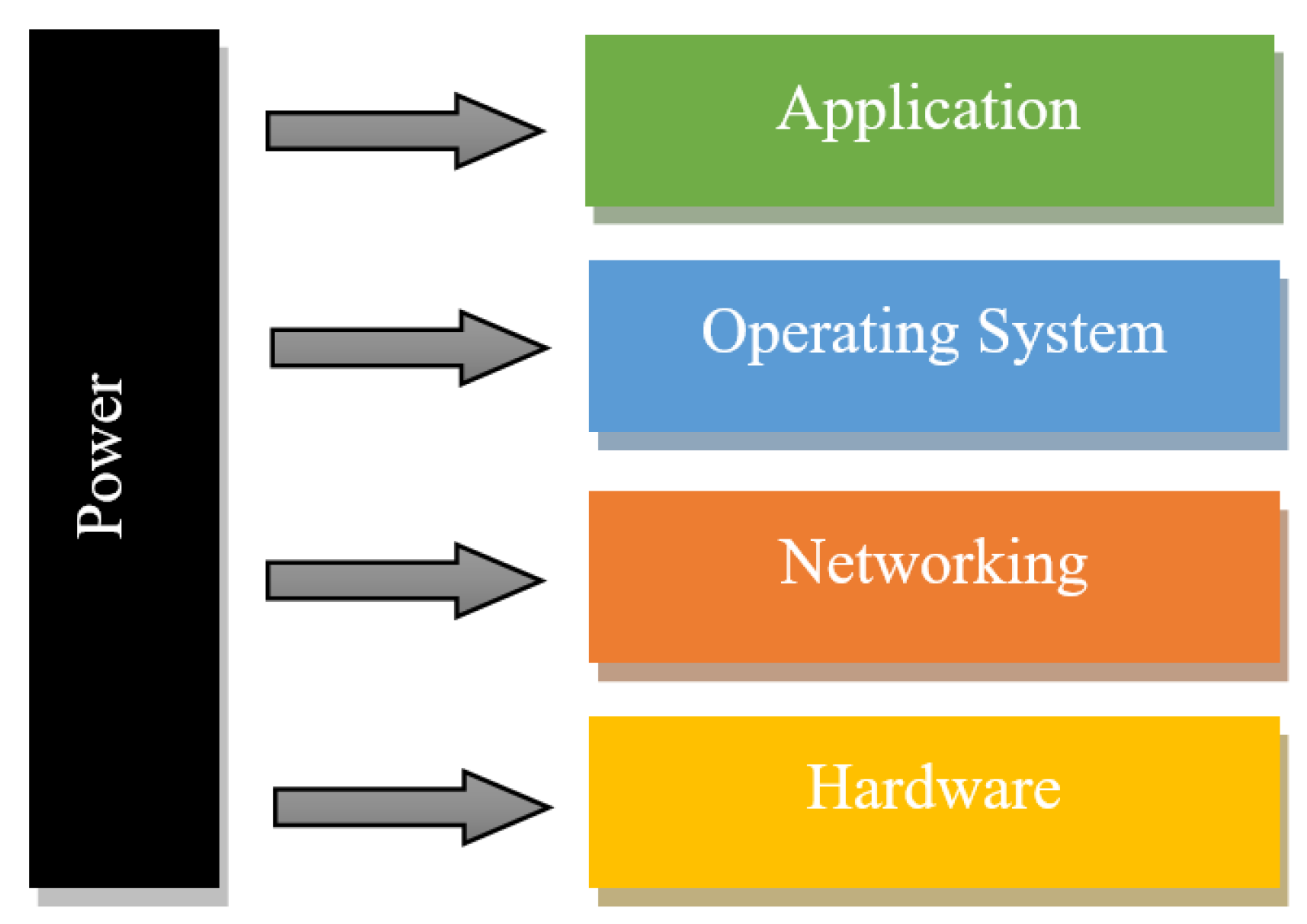
| Features | Architecture | CPU | RAM | Storage | Input Voltage | Power Consumption | Wake-Up Time | |
|---|---|---|---|---|---|---|---|---|
| Microcontroller | ||||||||
| MSP430F5529 | Mixed (von-Neumann and RISC | 25 Mhz | 10 KB | 128 Kbytes | 3.6 v | Active: 404 μA/1 MHz Standby: 2.5 μA/1 MHz | 3.5 ns | |
| MSP430F5514 | Mixed (von-Neumann and RISC | 25 Mhz | 6 | 64 | 3.6 | Active: 404 μA/1 MHz Standby: 2.5 μA/1 MHz | 3.5 ns | |
| Atmega128 | AVR (modified Harvard) | 16 Mhz | 4 Kbytes | 128 Kbytes | 5.5 v | Active: 19 mA/1 MHz Standby: 11 mA/1 MHz Power save mode: 15μA/1 MHz | 65 ms | |
| Atmega328 | AVR (modified Harvard) | 16 Mhz | 2 Kbytes | 32 Kbytes | 5.5 v | Active: 0.2 mA/1 MHz Standby: 0.1 μA/1 MHz Power save mode: 0.75 μA/1MHz | 65 ms | |
| PIC16F877A | Harvard | 20 Mhz | 368 Bytes | 8 Kbytes | 5.5 v | Active: 15 mA/1 MHz Standby: 7 nA/1 MHz Power save mode: 0.75 μA/1 MHz | 72 ms | |
| PIC18F46J50 | Harvard | 48 Mhz | 16 Kbytes | 4 Kbytes | 5.5 v | Active: 19 μA/1 MHz Standby: 1.5 μA/1 MHz Power save mode: 0.75 μA/1 MHz | 105 ns | |
| XBee RF | XBee | XBee Pro | |
|---|---|---|---|
| Features | |||
| Indoor | Up to 30 m | Up to 90 m | |
| Transmit power | 1 mW | 63 mW | |
| Data rate | 250 Kps | 250 Kps | |
| TX current | 45 mA | 250 mA | |
| RX current | 50 mA | 55 mA | |
| Power down current | <10 μA | <10 μA | |
| ADC converter | Yes | Yes | |
| Input voltage | 3.3 V | 3.3 V | |
| Sleep Mode | Wake-Up Time | Power Consumption at VCC 5 V |
|---|---|---|
| Pin Hebirnate (SM = 1) | 13.2 ms | <10 μA |
| Pin Doze (SM = 2) | 2 ms | <50 μA |
| Cyclic Sleep (SM = 4) | 2 ms | <50 μA |
| Cyclic Sleep with pin wake-up (SM = 5) | 2 ms | <50 μA |
| Features | System Performance | |
|---|---|---|
| Modulation Technique | ||
| BPSK, QPSK, 16QAM, 64QAM | Good | |
| BPSK, QPSK, 16QAM, 64QAM | Efficient physical layer design | |
| BPSK, QPSK, 16QAM, 64QAM | Better energy efficiency | |
| QPSK, 16QAM | BCH code is comparatively better than other codes | |
| MPSK MQAM MFSK | Suitable for short-distance communication | |
| MPSK MQAM MFSK | Analog decodes are energy efficient | |
| Operating System | TinyOS | Contiki | Free RTOS | MANTIS | Nano-RK | LiteOS | |
|---|---|---|---|---|---|---|---|
| Features | |||||||
| Architecture | Monolithic | Modular | Microkernel RTOS | Virtual machine | Monolithic | Modular | |
| Supported microcontrollers | AVR MSP430 | AVR MSP430 ARM PIC32 Cortex-M | AVR MSP430 ARM | AVR MSP430 | AVR MSP430 | AVR | |
| Programming model | Event-driven | Event-driven Multi-threading | Multi-threading | Event-driven Multi-threading | Multi-threading | Event-driven Multi-threading | |
| License | BSD | BSD | GPL | BSD | GPL | GPL | |
| Topology | Star | Tree | Mesh | Cluster | |
|---|---|---|---|---|---|
| Data Acquisition Technique | |||||
| Directed diffusion | YES | YES | YES | YES | |
| Chain construction | NO | YES | YES | YES (Between cluster heads) | |
| Probabilistic model | YES | YES | YES | YES | |
| Data correlation | NO | NO | NO | YES | |
| Query model | NO | YES | YES | YES | |
| Topology | Star | Tree | Mesh | Cluster | |
|---|---|---|---|---|---|
| Routing Protocol | |||||
| LEACH | NO | NO | NO | YES | |
| TEEN | NO | NO | NO | YES | |
| APTEEN | NO | NO | NO | YES | |
| PEGASIS | NO | YES | YES | NO | |
| SPIN | NO | NO | YES | NO | |
| RR | NO | NO | YES | YES | |
| GEAR | NO | NO | YES | YES | |
| GAF | NO | NO | YES | YES | |
| EAP | NO | NO | NO | YES | |
| GBR | NO | NO | NO | YES | |
| AESC | NO | YES | YES | YES | |
| PERP | NO | YES | YES | YES | |
| ODYSSE | NO | YES | YES | YES | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Naji, N.; Abid, M.R.; Krami, N.; Benhaddou, D. Energy-Aware Wireless Sensor Networks for Smart Buildings: A Review. J. Sens. Actuator Netw. 2021, 10, 67. https://doi.org/10.3390/jsan10040067
Naji N, Abid MR, Krami N, Benhaddou D. Energy-Aware Wireless Sensor Networks for Smart Buildings: A Review. Journal of Sensor and Actuator Networks. 2021; 10(4):67. https://doi.org/10.3390/jsan10040067
Chicago/Turabian StyleNaji, Najem, Mohamed Riduan Abid, Nissrine Krami, and Driss Benhaddou. 2021. "Energy-Aware Wireless Sensor Networks for Smart Buildings: A Review" Journal of Sensor and Actuator Networks 10, no. 4: 67. https://doi.org/10.3390/jsan10040067
APA StyleNaji, N., Abid, M. R., Krami, N., & Benhaddou, D. (2021). Energy-Aware Wireless Sensor Networks for Smart Buildings: A Review. Journal of Sensor and Actuator Networks, 10(4), 67. https://doi.org/10.3390/jsan10040067







