ELBA-IoT: An Ensemble Learning Model for Botnet Attack Detection in IoT Networks
Abstract
:1. Introduction
- We present a comprehensive efficient detection/classification model/architecture with detailed preprocessing operations that can classify the IoT traffic records of the N-BaIoT2021 dataset into binary classifier (2-class), ternary classifier (3-class), and multiclassifier (10-class).
- We characterize the performance of four machine-learning-based decision tree models: AdaBoosted decision tree, RUSBoosted decision tree, bagged decision tree, and their ensemble learning model.
- We provide an inclusive experimental evaluation to gain more insight into the system efficiency and solution approaches, such as the confusion matrix, model precision, model sensitivity, and others.
- We contrast our best performance results with state-of-the-art works employing several supervised learning algorithms in the same area of study.
2. Related Work
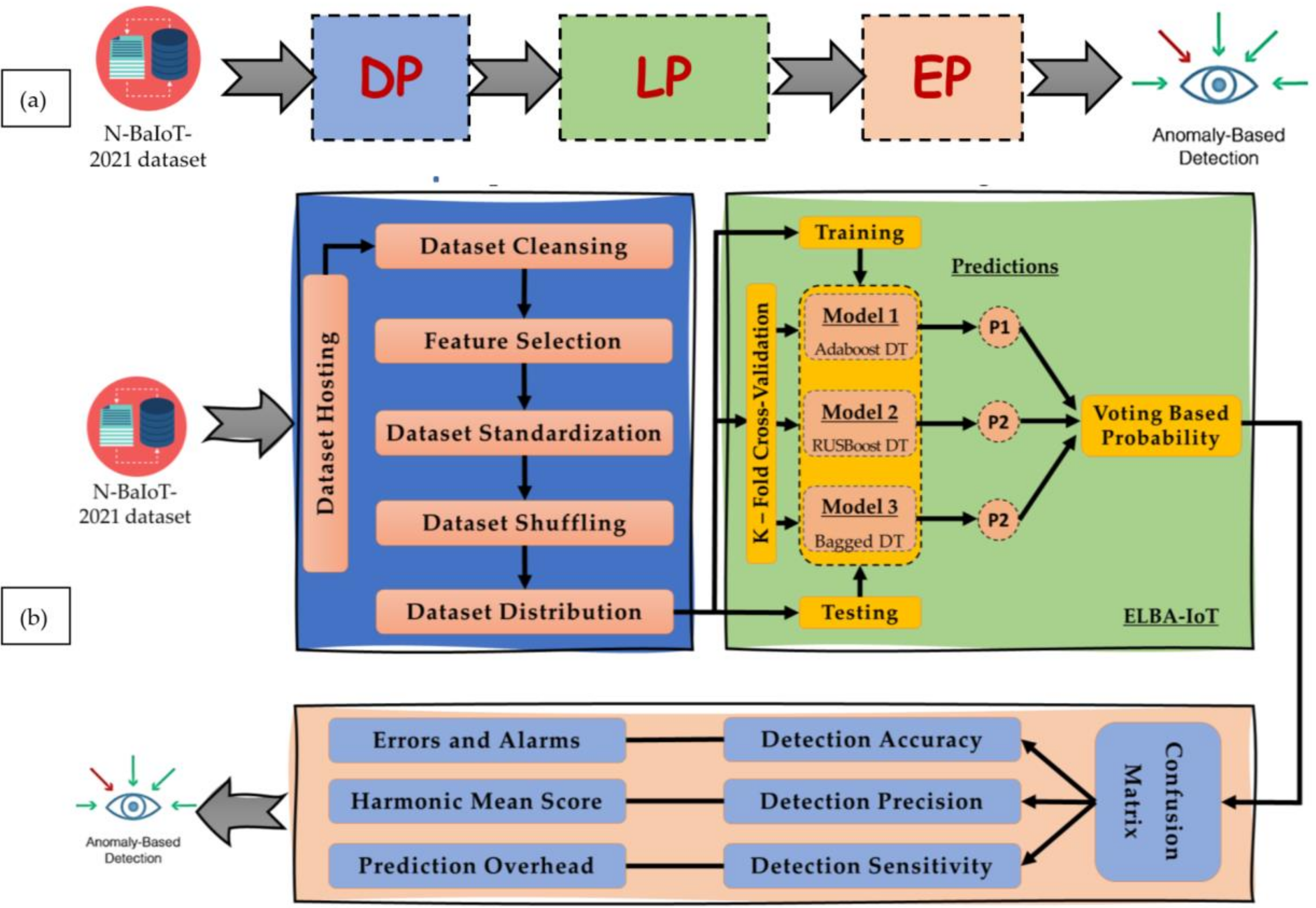
3. ELBA-IoT Model Development
3.1. Implementation of the Data Preparation (DP) Module
3.1.1. Data Hosting Process (DHP)
3.1.2. Data Cleansing Process (DCP)
3.1.3. Feature Selection Process (FSP)
3.1.4. Data Standardization Process (DSP)
3.1.5. Data Shuffling Process (DSH)
 |
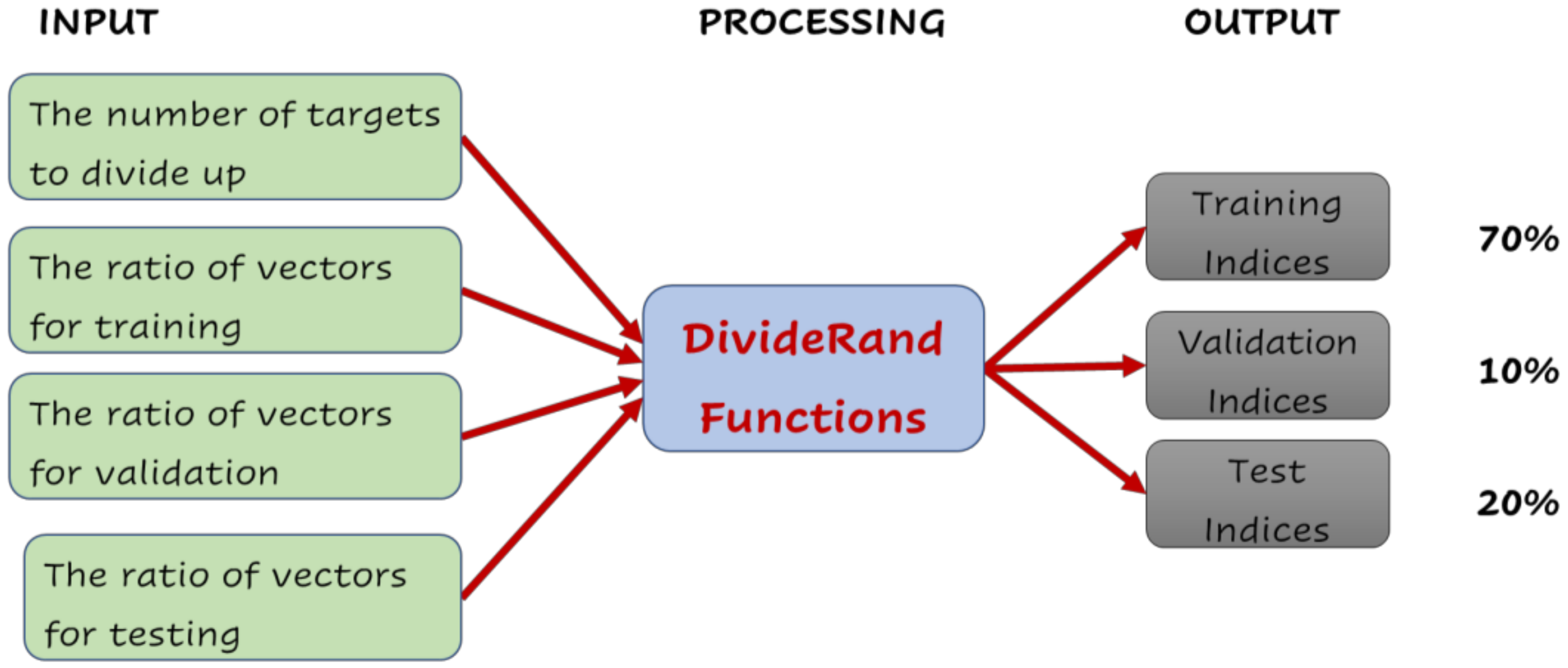
3.1.6. Data Distribution Process (DDP)
3.2. Implementation of the Learning Process (LP) Module
3.3. Implementation of the Evaluation Process (EP) Module
4. Results and Discussion
5. Conclusions and Future Directions
Author Contributions
Funding
Conflicts of Interest
References
- Albulayhi, K.; Smadi, A.A.; Sheldon, F.T.; Abercrombie, R.K. IoT Intrusion Detection Taxonomy, Reference Architecture, and Analyses. Sensors 2021, 21, 6432. [Google Scholar] [CrossRef] [PubMed]
- Statistical Portal. Internet of Things (IoT) Connected Devices Installed Base Worldwide from 2015 to 2025 (in Billions). Available online: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed on 24 December 2018).
- Rose, K.; Eldridge, S.; Chapin, L. The Internet of Things: An Overview Understanding the Issues and Challenges of a More Connected World. 2015. Available online: http://www.internetsociety.org/sites/default/files/ISOC-IoT-Overview-20151022.pdf (accessed on 20 January 2022).
- Dambaye, S.S.; Kolhe, M.V.L. A Survey: Managing Resource-Constrained Devices in IoT. Int. J. Innov. Res. Comput. Commun. Eng. 2016, 4, 21011–21015. [Google Scholar]
- Al-Haija, Q.A. On the Security of Cyber-Physical Systems Against Stochastic Cyber-Attacks Models. In Proceedings of the 2021 IEEE International IoT, Electronics, and Mechatronics Conference (IEMTRONICS), Toronto, ON, Canada, 21–24 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Al Dalaien, M.N.; Bensefia, A.; Hoshang, S.A.; Bathaqili, A.R.A.; Xu, X.; Mohanan, V.; Budiarto, R.; Aldmour, I. Internet of Things (IoT) Security and Privacy. In Powering the Internet of Things with 5G Networks; Mohanan, V., Budiarto, R., Aldmour, I., Eds.; IGI Global: Hershey, PA, USA, 2018; pp. 247–267. [Google Scholar] [CrossRef]
- Albulayhi, K.; Sheldon, F.T. An Adaptive Deep-Ensemble Anomaly-Based Intrusion Detection System for the Internet of Things. In Proceedings of the 2021 IEEE World AI IoT Congress (AIIoT), Seattle, WA, USA, 10–13 May 2021; pp. 187–196. [Google Scholar] [CrossRef]
- Sagi, O.; Rokach, L. Ensemble learning: A survey. WIREs Data Min. Knowl. Discov. 2018, 8, e1249. [Google Scholar] [CrossRef]
- Tsogbaatar, E.; Bhuyan, M.H.; Taenaka, Y.; Fall, D.; Gonchigsumlaa, K.; Elmroth, E.; Kadobayashi, Y. SDN-enabled IoT anomaly detection using ensemble learning. In Proceedings of the 16th International Conference on Artificial Intelligence Applications and Innovations (AIAI), Halkidiki, Greece, 5–7 June 2020. [Google Scholar]
- Median, Y.; Bogadana, M.; Mathov, Y.; Mirsky, Y.; Shabtai, A.; Breitenbacher, D.; Elovici, Y. N-BaIoT—Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef] [Green Version]
- Basavaraj, D.; Tayeb, S. Towards a Lightweight Intrusion Detection Framework for In-Vehicle Networks. J. Sens. Actuator Netw. 2022, 11, 6. [Google Scholar] [CrossRef]
- Samara, M.A.; Bennis, I.; Abouaissa, A.; Lorenz, P. A Survey of Outlier Detection Techniques in IoT: Review and Classification. J. Sens. Actuator Netw. 2022, 11, 4. [Google Scholar] [CrossRef]
- Alrubayyi, H.; Goteng, G.; Jaber, M.; Kelly, J. Challenges of Malware Detection in the IoT and a Review of Artificial Immune System Approaches. J. Sens. Actuator Netw. 2021, 10, 61. [Google Scholar] [CrossRef]
- Ioannou, C.; Vassiliou, V. Network Attack Classification in IoT Using Support Vector Machines. J. Sens. Actuator Netw. 2021, 10, 58. [Google Scholar] [CrossRef]
- Ramadan, R.A. Efficient Intrusion Detection Algorithms for Smart Cities-Based Wireless Sensing Technologies. J. Sens. Actuator Netw. 2020, 9, 39. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q. Top-Down Machine Learning-Based Architecture for Cyberattacks Identification and Classification in IoT Communication Networks. Front. Big Data 2022, 4, 782902. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Al-Badawi, A. Attack-Aware IoT Network Traffic Routing Leveraging Ensemble Learning. Sensors 2022, 22, 241. [Google Scholar] [CrossRef] [PubMed]
- Al-Haija, Q.A.; Saleh, E.; Alnabhan, M. Detecting Port Scan Attacks Using Logistic Regression. In Proceedings of the 2021 4th International Symposium on Advanced Electrical and Communication Technologies (ISAECT), Khobar, Saudi Arabia, 6–8 December 2021; pp. 1–5. [Google Scholar] [CrossRef]
- Tsogbaatar, E.; Bhuyan, M.H.; Taenaka, Y.; Fall, D.; Gonchigsumlaa, K.; Elmroth, E.; Kadobayashi, Y. DeL-IoT: A deep ensemble learning approach to uncover anomalies in IoT. Internet Things 2021, 14. [Google Scholar] [CrossRef]
- Rezaei, A. Using Ensemble Learning Technique for Detecting Botnet on IoT. SN Comput. Sci. 2021, 4, 148. [Google Scholar] [CrossRef]
- Özçelik, M.; Chalabianloo, N.; Gür, G. Software-Defined Edge Defense against IoT-Based DDoS. In Proceedings of the 2017 IEEE International Conference on Computer and Information Technology (CIT 17), Helsinki, Finland, 21–23 August 2017. [Google Scholar] [CrossRef]
- Summerville, D.H.; Zach, K.M.; Chen, Y. Ultra-Lightweight Deep Packet Anomaly Detection for Internet of Things Devices. In Proceedings of the 2015 IEEE 34th International Performance Computing and Communications Conference (IPCCC 15), Mamkomg, China, 14–16 December 2015. [Google Scholar] [CrossRef]
- Yang, L.; Shami, A. A Lightweight Concept Drift Detection and Adaptation Framework for IoT Data Streams. IEEE Internet Things Mag. 2021, 4, 96–101. [Google Scholar] [CrossRef]
- Qaddoura, R.; Al-Zoubi, A.M.; Almomani, I.; Faris, H. A Multi-Stage Classification Approach for IoT Intrusion Detection Based on Clustering with Oversampling. Appl. Sci. 2021, 11, 3022. [Google Scholar] [CrossRef]
- Shi, W.C.; Sun, H.M. DeepBot: A time-based botnet detection with deep learning. Soft. Comput. 2020, 24, 16605–16616. [Google Scholar] [CrossRef]
- Nguyen, H.-T.; Ngo, Q.-D.; Le, V.-H. IoT Botnet Detection Approach Based on PSI graph and DGCNN classifier. In Proceedings of the 2018 IEEE International Conference on Information Communication and Signal Processing (ICICSP), Singapore, 28–30 September 2018; pp. 118–122. [Google Scholar] [CrossRef]
- McDermott, C.D.; Majdani, F.; Petrovski, A.V. Botnet Detection in the Internet of Things using Deep Learning Approaches. In Proceedings of the 2018 International Joint Conference on Neural Networks (IJCNN), Rio de Janeiro, Brazil, 8–13 July 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Stiawan, D.; Suryani, M.E.; Susanto; Idris, M.Y.; Aldalaien, M.N.; Alsharif, N.; Budiarto, R. Ping Flood Attack Pattern Recognition Using a K-Means Algorithm in an Internet of Things (IoT) Network. IEEE Access 2021, 9, 116475–116484. [Google Scholar] [CrossRef]
- Al-Haija, Q.A.; Smadi, A.A.; Allehyani, M.F. Meticulously Intelligent Identification System for Smart Grid Network Stability to Optimize Risk Management. Energies 2021, 14, 6935. [Google Scholar] [CrossRef]
- Chandra, B.E.; Karthikeyan, E. Sigmis: A feature selection algorithm using the correlation-based method. J. Algorithms Comput. Technol. 2012, 6, 385–394. [Google Scholar]
- Singh, D.; Birmohan, S. Investigating the impact of data normalization on classification performance. Appl. Soft Comput. 2020, 97, 105524. [Google Scholar] [CrossRef]
- Al-Haija, Q.A.; Alsulami, A.A. High Performance Classification Model to Identify Ransomware Payments for Heterogeneous Bitcoin Networks. Electronics 2021, 10, 2113. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Krichen, M.; Abu Elhaija, W. Machine-Learning-Based Darknet Traffic Detection System for IoT Applications. Electronics 2022, 11, 556. [Google Scholar] [CrossRef]
- Stamp, M. A survey of machine learning algorithms and their application in information security. In Guide to Vulnerability Analysis for Computer Networks and Systems; Springer: Cham, Switzerland, 2018; pp. 33–55. [Google Scholar]
- Timčenko, V.; Gajin, S. Ensemble classifiers for supervised anomaly-based network intrusion detection. In Proceedings of the 2017 13th IEEE International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 7–9 September 2017; pp. 13–19. [Google Scholar] [CrossRef]
- Gaikwad, D.P.; Thool, R.C. Intrusion detection system using bagging with partial decision treebase classifier. Procedia Comput. Sci. 2015, 49, 92–98. [Google Scholar] [CrossRef] [Green Version]
- Al-Haija, Q.A.; Ishtaiwi, A. Multiclass Classification of Firewall Log Files Using Shallow Neural Network for Network Security Applications. In Soft Computing for Security Applications. Advances in Intelligent Systems and Computing; Ranganathan, G., Fernando, X., Shi, F., El-Allioui, Y., Eds.; Springer: Singapore, 2022; Volume 1397. [Google Scholar] [CrossRef]
- Aygun, R.C.; Yavuz, A.G. Network anomaly detection with stochastically improved autoencoder based models. In Proceedings of the 4th International Conference on Cyber Security and Cloud Computing, New York, NY, USA, 26–28 June 2017; pp. 193–198. [Google Scholar]
- Kumar, A.; Lim, T.J. EDIMA: Early detection of IoT malware network activity using machine learning techniques. In Proceedings of the 2019 IEEE 5th World Forum on Internet of Things (WF-IoT), Limerick, Ireland, 15–18 April 2019; pp. 289–294. [Google Scholar]
- Ioannou, C.; Vassiliou, V. Classifying Security Attacks in IoT Networks Using Supervised Learning. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini Island, Greece, 29–31 May 2019; pp. 652–658. [Google Scholar]
- Gao, X.; Shan, C.; Hu, C.; Niu, Z.; Liu, Z. An Adaptive Ensemble Machine Learning Model for Intrusion Detection. IEEE Access 2019, 7, 82512–82521. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; Sabatto, S.Z. An Efficient Deep-Learning-Based Detection and Classification System for Cyber-Attacks in IoT Communication Networks. Electronics 2020, 9, 2152. [Google Scholar] [CrossRef]
- Jung, W.; Zhao, H.; Sun, M.; Zhou, G. IoT botnet detection via power consumption modeling. Smart Health 2020, 15, 100103. [Google Scholar] [CrossRef]
- Ashraf, J.; Keshk, M.; Moustafa, N.; Abdel-Basset, M.; Khurshid, H.; Bakhshi, A.D.; Mostafa, R.R. IoTBoT-IDS: A novel statistical learning-enabled botnet detection framework for protecting networks of smart cities. Sustain. Cities Soc. 2021, 72, 103041. [Google Scholar] [CrossRef]
- Abu Al-Haija, Q.; al Badawi, A.; Bojja, G.R. Boost-Defence for resilient IoT networks: A head-to-toe approach. Expert Syst. 2022, 39, e12934. [Google Scholar] [CrossRef]



| Paper | Attack(s) | Detection Approach | Deployment Level | Assumed Environment | Data for Evaluation |
|---|---|---|---|---|---|
| [11] | DoS attacks, probe attacks, root-to-local (r2l) attacks, user-to-root (u2r) attacks | CNN | Layered approach | Platform independent | NSL-KDD dataset |
| [12] | OS Scan attack, Fuzzing attack, video injection, ARP attack, active wiretap attack, SSDP flood attack, SYN DoS attack, SSL renegotiation attack, and Mirai attack | Ensemble-learning-based Boosted Trees | Network | - | Distilled-Kitsune-2018 dataset |
| [13] | Port scan attack | Logistic regression | Network | Windows environment | Port scanning dataset 2017 |
| [14] | - | DeL-IoT | Network | - | - |
| [15] | DoS attack, spam, and data theft | Ensemble learning | Network | - | Network traffic |
| [16] | Mirai-infected IoT devices scan for further devices | Dynamic updating of flow rules | “Thin fog” | Critical infrastructures | Emulated IoT nodes, simulated data |
| [17] | Worm propagation, code injection, tunneling attack | Deep learning | Host | - | Two real devices |
| [18] | - | LightGBM model and drift adaptation | - | - | IoT data streams |
| [19] | - | SLFN, SVM-SMOTE | Network | - | IoT network data |
| [20] | - | DeepBot-deep learning model | Network | - | Network packets |
| [21] | Botnet IoT malware scan | PSI graph and CNN classifier | Host | Linux environment | 10033 ELF (4002 IoT botnet samples and 6031 benign files) |
| [22] | IoT-based DDoS | BLSTM-RNN detection model | Host/ Network | - | - |
| [23] | Ping flood attacks | K-Means | Network | - | IoT network data |
| Classifier | Normal | Botnet(s) |
|---|---|---|
| Binary Classifier | 0 (normal) | 1 (anomaly) |
| Ternary Classifier | 0 (normal) |
|
| Multiclassifier | 0 (normal) |
|
| Classifier | Model 1 | Model 2 | Model 3 | Model 4 |
|---|---|---|---|---|
| Model Preset | Decision trees | Decision trees | Decision trees | Ensemble learning |
| Learner Type | AdaBoosted | RUSBoosted | Bagged | Bagged, AdaBoosted, RUSBoosted |
| Maximum Number of Splits | 20 | 20 | 20 | 1–611358 |
| Number of Learners | 30 | 30 | 30 | 10–500 |
| Learning Rate | 0.1 | 0.1 | 0.1 | 0.001–1 |
| Summary of General Implementation Specifications | ||||
| Feature Selection | Validation | Shuffling Process | ||
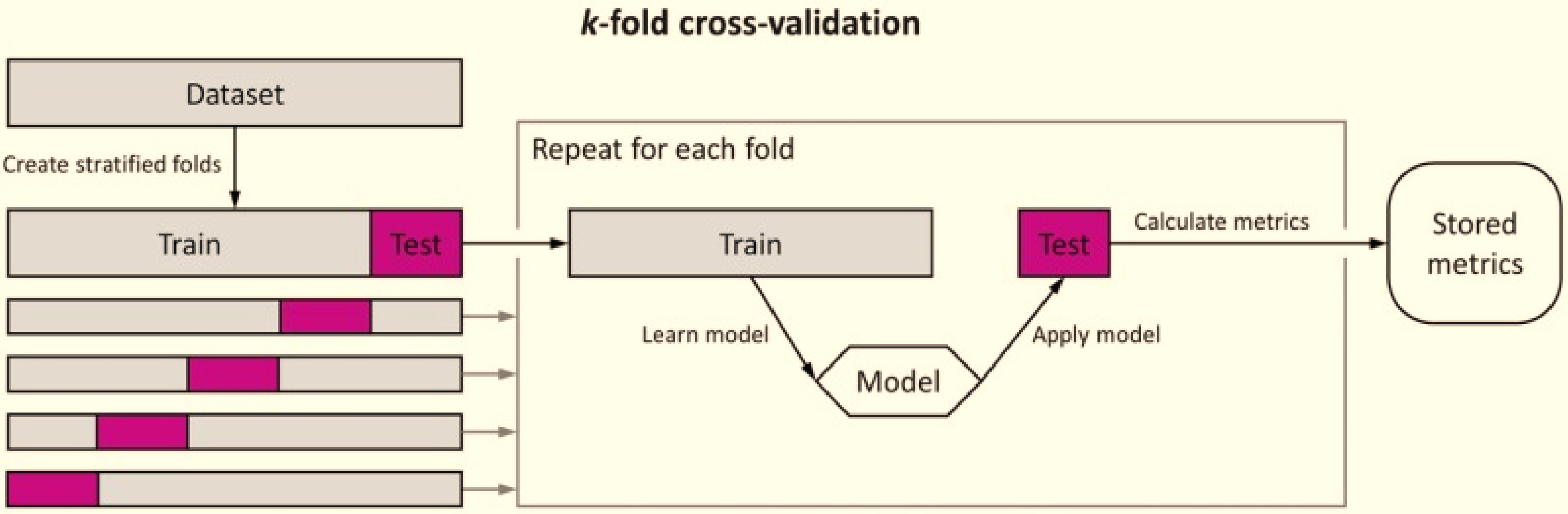
| CCS Approach | 5-fold cross-validation | Uniform shuffling at every epoch | ||
| Data Distribution | Standardization Process | Computing Platform | ||
| Divide-Rand | Z-score normalization | Windows 11/MATLAB2021/GPU+CPU | ||
| DAC | DPR | DSN | DHS | IAE | IME | INE | NMS# | NCS# | |
|---|---|---|---|---|---|---|---|---|---|
| ADA-IoT | 99.9% | 99.7% | 99.5% | 99.6% | 0.1% | 0.3% | 0.5% | 611 | 610748 |
| RUS-IoT | 99.5% | 99.3% | 99.3% | 99.3% | 0.5% | 0.7% | 0.7% | 3056 | 608303 |
| BAG-IoT | 99.7% | 99.5% | 99.4 | 99.4% | 0.3% | 0.5% | 0.6% | 1834 | 609525 |
| ELBA-IoT | 100% | 100% | 100% | 100% | 0.0% | 0.0% | 0.0% | 13 | 611346 |
| DAC | DPR | DSN | DHS | IAE | IME | INE | NMS# | NCS# | |
|---|---|---|---|---|---|---|---|---|---|
| ADA-IoT | 99.8% | 99.7% | 99.7% | 99.7% | 0.1% | 0.3% | 0.3% | 672 | 610687 |
| RUS-IoT | 99.4% | 99.4% | 99.2% | 99.3% | 0.6% | 0.4% | 0.8% | 3655 | 607704 |
| BAG-IoT | 99.5% | 99.5% | 99.4% | 99.4% | 0.5% | 0.5% | 0.6% | 3117 | 608242 |
| ELBA-IoT | 100% | 100% | 100% | 100% | 0.0% | 0.0% | 0.0% | 30 | 611329 |
| DAC | DPR | DSN | DHS | IAE | IME | INE | NMS# | NCS# | |
|---|---|---|---|---|---|---|---|---|---|
| ADA-IoT | 97.3% | 95.5% | 92.2% | 93.9% | 2.7% | 4.5% | 7.8% | 16506 | 594853 |
| RUS-IoT | 97.7% | 96.9% | 95.7% | 96.3% | 2.3% | 3.1% | 4.3% | 14061 | 597298 |
| BAG-IoT | 96.2% | 92.4% | 90.6% | 91.5% | 3.8% | 7.6% | 9.4% | 23231 | 588128 |
| ELBA-IoT | 99.6% | 98.4% | 97.1% | 97.7% | 0.4% | 1.6% | 2.9% | 2445 | 608914 |
| ADA-IoT | RUS-IoT | BAG-IoT | ELBA-IoT | |
|---|---|---|---|---|
| PRS (Samples/Sec) | 12,000 | 13,000 | 12,000 | 25,000 |
| PRT (in µ-Second) | 83.33 | 76.92 | 83.33 | 40.00 |
| Paper/ Year | Detection Model | Attack Categories | Number of Classes | Validation Accuracy |
|---|---|---|---|---|
| [38]/2017 | HAEs | DOS, PROBE, R2L, U2R | 5 Classes | 88.65% |
| [27]/2018 | BLSTM-RNN | MIRAI, UDP, ACK, DNS | 5 Classes | 97.5% |
| [26]/2018 | DG-CNN | PORT SCANNING, MIRAI, QBOT, DICTIONARY | 2 Classes | 92.0% |
| [39]/2019 | kNN | TELNET, HTTP_POST, HTTP_GET | 3 Classes | 94.45% |
| [40]/2019 | SVM | DOS, PROBE, R2L, U2R | 5 Classes | 81.00% |
| [41]/2019 | Hybrid-ML | DOS, PROBE, R2L, U2R | 5 Classes | 85.20% |
| [25]/2020 | LSTM + RNN | MIRAI AND ITS VARIANTS | 2 Classes | 99.30% |
| [42]/2020 | S-CNN | DOS, PROBE, R2L, U2R | 5 Classes | 98.20% |
| [43]/2020 | D-CNN | MIRAI HAJIME, BRICKERBOT, MASUTA, SORA | 4 Classes | 90.00% |
| [44]/2021 | SL-BMM-CE | MIRAI + BASHLITE | 7 Classes | 99.20% |
| [45]/2022 | ADA-DT | DDoS, INJC, MITM, PSWD, SCAN, XSS, BKDR, RNSM | 10 Classes | 98.60% |
| ELBA-IoT | EL-DTs | MIRAI + BASHLITE | 10 Classes | 99.60% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Abu Al-Haija, Q.; Al-Dala’ien, M. ELBA-IoT: An Ensemble Learning Model for Botnet Attack Detection in IoT Networks. J. Sens. Actuator Netw. 2022, 11, 18. https://doi.org/10.3390/jsan11010018
Abu Al-Haija Q, Al-Dala’ien M. ELBA-IoT: An Ensemble Learning Model for Botnet Attack Detection in IoT Networks. Journal of Sensor and Actuator Networks. 2022; 11(1):18. https://doi.org/10.3390/jsan11010018
Chicago/Turabian StyleAbu Al-Haija, Qasem, and Mu’awya Al-Dala’ien. 2022. "ELBA-IoT: An Ensemble Learning Model for Botnet Attack Detection in IoT Networks" Journal of Sensor and Actuator Networks 11, no. 1: 18. https://doi.org/10.3390/jsan11010018
APA StyleAbu Al-Haija, Q., & Al-Dala’ien, M. (2022). ELBA-IoT: An Ensemble Learning Model for Botnet Attack Detection in IoT Networks. Journal of Sensor and Actuator Networks, 11(1), 18. https://doi.org/10.3390/jsan11010018







