Internal Interface Diversification as a Security Measure in Sensor Networks †
Abstract
:1. Introduction
2. Interface Diversification
2.1. The Idea of Interface Diversification
2.2. Attack Scenarios Mitigated by Diversification
2.2.1. Infecting the Node
2.2.2. Worm Propagation
2.2.3. An Infected Update
2.2.4. Compromising Node’s Integrity
3. Related Work
4. Diversifiable Interfaces in IoT Operating Systems
- System calls. A system call is the way programs request a service from the operating system and access the computer’s critical resources [25]. To prevent the attacker from using system calls, we can uniquely change the system call numbers [16,26,27]. This interface diversification is then propagated to trusted binaries and libraries, which are diversified accordingly so that they are compatible with the diversified system and can invoke system calls using the new secret system call numbers.
- Functions in shared libraries. System calls can also be invoked indirectly by calling several wrapper functions in many operating system libraries. Malware should be prevented from accessing any critical resources by diversifying these entry points. To this end, any library functions that directly or indirectly issue system calls are diversified [15,18]. This means changing function names and possibly changing the order of parameters in the function signature. Diversification is also propagated to libraries and applications that call these library functions.
- Command shell. Malware does not always use system calls or library functions. Instead, it can employ interpreted languages, such as shell scripts, to achieve its goals. Similarly to the library functions, the language interface of the shell is also an entry point to the resources of a device. Many attacks, such as ShellShock [28], have seized this opportunity. If we change the language interface (the set of tokens used by the command line interpreter), the attacks based on this known language interface will fail [20,21,29]. The shell scripts in the system are then diversified to correspond to the new secret language.
- Memory space. Memory space can also be seen as a diversifiable interface. ASLR is a security approach that provides protection from buffer overflow attacks. In ASLR, the address space positions of the essential parts of a process are randomly rearranged in order to make it more difficult for the adversary to predict where a specific piece of code resides in the memory. With the memory layout randomized, the attacker cannot reliably jump to a specific position in the memory (such as an exploited function) [30]. If one wants to further increase the chance of an attacker guessing the location of a specific randomly placed memory area, it is possible to further increase the amount of virtual memory space where the diversification occurs. To achieve this, however, a memory management unit (MMU) is needed. An MMU is a unit through which the memory references are passed. It takes care of translating the virtual memory addresses into physical addresses. A system without an MMU is limited to the address range of its physical space when ASLR is applied, whereas the MMU usually expands the address space, which allows the placement of mapped sections with much more potential offsets than a physical address space alone would permit.
- Data structures. Related to memory layout randomization, the layout of individual data structures can also be diversified. For example, the order of data items within structures could be changed or additional padding inserted between them. This form of protection has been implemented in the main line Linux kernel: when the kernel is compiled, a special compiler plugin can be invoked to change the layout of the data structures used within the kernel [31]. Since these data structures are internal to the kernel, the changes do not necessarily need to be propagated to other parts of the system. The only challenge with this approach is compatibility with out-of-tree modules that need to be built separately.
- Protocols. As IoT devices operate in a network, they need to use protocols to communicate. These protocols can also be seen as targets for diversification [14]. For example, the Constrained Application Protocol (CoAP) is a software protocol that enables simple electronics devices to communicate with each other [32]. It is an application layer protocol specifically designed for resource-constrained devices, such as “things” in the IoT. By diversifying a protocol, we can create numerous uniquely diversified protocols from the original protocol. Thinking of a protocol as a state machine, this means that diversification can add arbitrarily many new states and transitions to the original protocol. Of course, this protection comes at the price of greater complexity and some performance slowdown. Protocol diversification makes node capture attacks and adding malicious nodes to a network more difficult, as those nodes also have to conform to the diversified protocol in order to successfully interact with other nodes.
Diversifiable Interfaces in IoT Operating Systems
5. The Proof-of-Concept Implementations
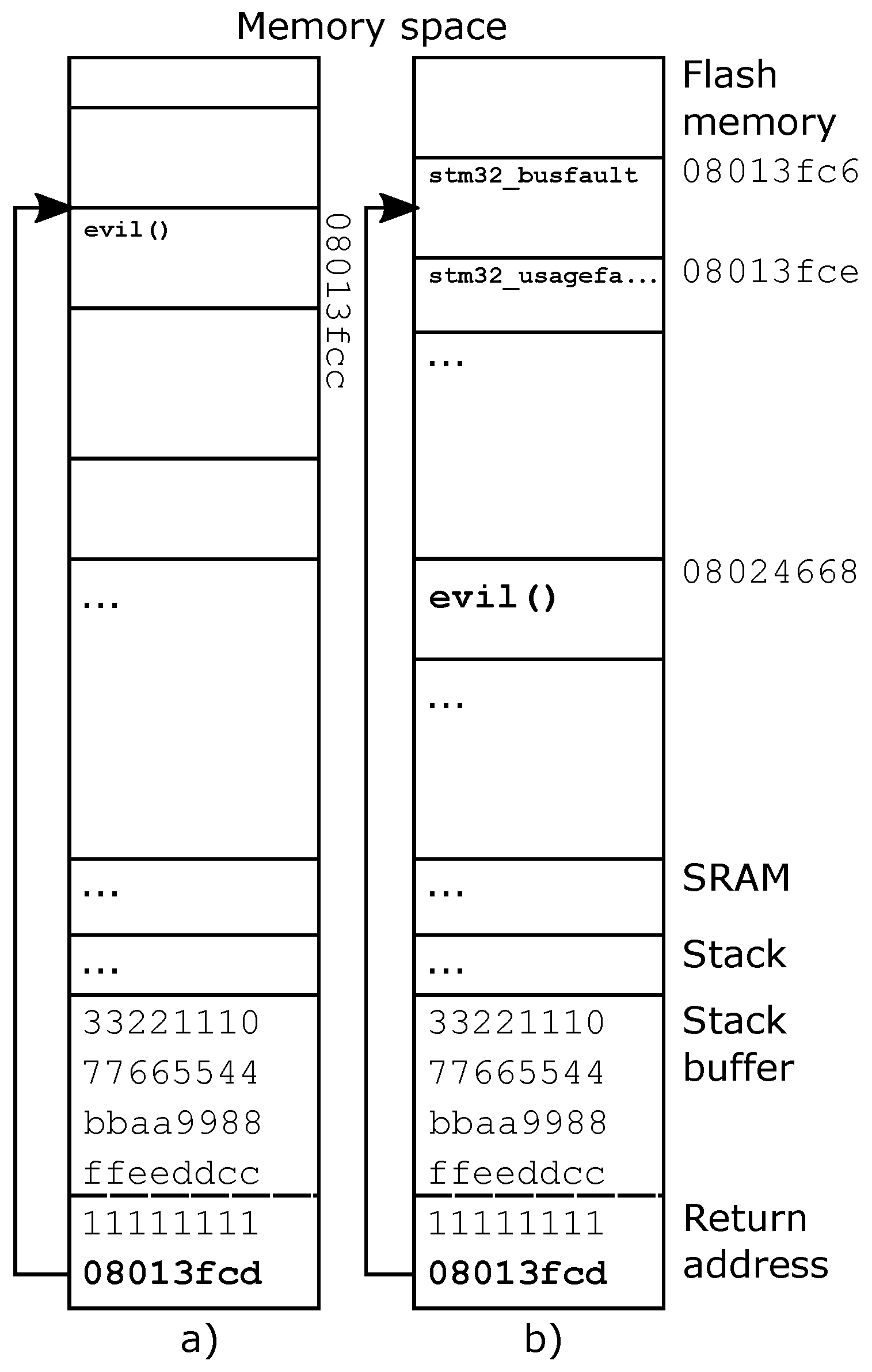
5.1. Layout Shuffling of Thingsee OS on Thingsee One
$ arm-none-eabi-objdump -d nuttx
NuttShell (NSH)
nsh> hello 42 0 20
hello 42 0 20
hex_strcpy: a=20009030; s_d=0; s_n=32
0000000000000000000000000000000064900020b54101087541010800000000
foo 1
B
nsh> hello 10112233445566778899aabbccddeeff11111111cd3f0108
hello 10112233445566778899aabbccddeeff11111111cd3f0108
hex_strcpy: a=20009010; s_d=0; s_n=32
0000000000000000000000000000000044900020b54101087541010800000000
foo 1
(some unintelligible characters)
Evil function!
cd configs/haltian-tsone/
patch Make.defs <<END_OF_PATCH
79,80c79
< LDFLAGS += --gc-sections
< # --sort-section=shuffle_obfuscation
---
> LDFLAGS += --gc-sections --sort-section=shuffle_obfuscation
END_OF_PATCH
cd ../../tools/
./configure.sh haltian-tsone/nsh
make menuconfig # Enable the “Hello, World!” example
env SHUFFLE_OBFUSCATION_SALT=foo make
# NOTE: set the device to flash mode before executing,
# the hexadecimal number specifies the device
sudo dfu-util -d 0483:df11 -a0 -D nuttx.dfu -s :leave
NuttShell (NSH)
nsh> hello 10112233445566778899aabbccddeeff11111111cd3f0108
hello 10112233445566778899aabbccddeeff11111111cd3f0108
hex_strcpy: a=20009030; s_d=0; s_n=0
foo 1
(some unintelligible characters)
5.2. Symbol Diversification on Raspbian
6. Discussion
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- International Telecommunication Union. Overview of the Internet of Things. Recommendation ITU-T Y.2060; ITU: Geneva, Switzerland, 2012. [Google Scholar]
- Gartner. Gartner Says 6.4 Billion Connected Things Will Be in Use in 2016, up 30 Percent from 2015. Available online: http://www.vxdev.com/docs/vx55man/vxworks/guide/c-vm.html (accessed on 23 June 2016).
- HP Enterprise. Internet of Things Research Study; Hewlett Packard Enterprise: Palo Alto, CA, USA, 2015. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Cohen, F. Operating System Protection through Program Evolution. Comput. Secur. 1993, 12, 565–584. [Google Scholar] [CrossRef]
- Forrest, S.; Somayaji, A.; Ackley, D. Building Diverse Computer Systems. In Proceedings of the 6th Workshop on Hot Topics in Operating Systems (HotOS-VI), HOTOS ’97, Cape Cod, MA, USA, 5–6 May 1997. [Google Scholar]
- Koivunen, L.; Rauti, S.; Leppänen, V. Applying Internal Interface Diversification to IoT Operating Systems. In Proceedings of the 2016 International Conference on Software Security and Assurance (ICSSA), St. Polten, Austria, 24–25 August 2016; pp. 1–5. [Google Scholar]
- Mäki, P.; Rauti, S.; Hosseinzadeh, S.; Koivunen, L.; Leppänen, V. Interface Diversification in IoT Operating Systems. In Proceedings of the 2016 IEEE/ACM 9th International Conference on Utility and Cloud Computing (UCC), Shanghai, China, 6–9 December 2016; pp. 304–309. [Google Scholar]
- Steiner, R.V.; Lupu, E. Attestation in Wireless Sensor Networks: A Survey. ACM Comput. Surv. 2016, 49, 51:1–51:31. [Google Scholar] [CrossRef]
- Larsen, P.; Homescu, A.; Brunthaler, S.; Franz, M. SoK: Automated Software Diversity. In Proceedings of the 2014 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 18–21 May 2014; pp. 276–291. [Google Scholar]
- Hosseinzadeh, S.; Rauti, S.; Laurén, S.; Mäkelä, J.M.; Holvitie, J.; Hyrynsalmi, S.; Leppänen, V. A Survey on Aims and Environments of Diversification and Obfuscation in Software Security. In Proceedings of the 17th International Conference on Computer Systems and Technologies CompSysTech’16, Palermo, Italy, 23–24 June 2016; Rachev, B., Smrikarov, A., Eds.; ACM Press: New York, NY, USA, 2016; pp. 113–120. [Google Scholar]
- Hosseinzadeh, S.; Rauti, S.; Hyrynsalmi, S.; Leppänen, V. Security in the Internet of Things through obfuscation and diversification. In Proceedings of the 2015 International Conference on Computing, Communication and Security (ICCCS), Pamplemousses, Mauritius, 4–5 December 2015; pp. 1–5. [Google Scholar]
- Hosseinzadeh, S.; Hyrynsalmi, S.; Leppänen, V. Obfuscation and Diversification for Securing the Internet of Things (IoT). In Internet of Things: Principles and Paradigms; Buyya, R., Dastjerdi, A.V., Eds.; Elsevier: Amsterdam, The Netherlands, 2016; pp. 259–274. [Google Scholar]
- Hjelmvik, E.; John, W. Breaking and Improving Protocol Obfuscation; Technical Report; Chalmers University of Technology: Göteborg, Sweden, 2010; Volume 123751. [Google Scholar]
- Chew, M.; Song, D. Mitigating Buffer Overflows by Operating System Randomization; Technical Report CMU-CS-02-197; Carnegie Mellon University: Pittsburgh, PA, USA, 2002. [Google Scholar]
- Rauti, S.; Laurén, S.; Hosseinzadeh, S.; Mäkelä, J.; Hyrynsalmi, S.; Leppänen, V. Diversification of System Calls in Linux Binaries. In Proceedings of the 6th International Conference on Trustworthy Systems (InTrust 2014), Beijing, China, 16–17 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 15–35. [Google Scholar]
- Laurén, S.; Rauti, S.; Leppänen, V. Diversification of System Calls in Linux Kernel. In Proceedings of the 16th International Conference on Computer Systems and Technologies CompSysTech ’15, Dublin, Ireland, 25–26 June 2015; ACM: New York, NY, USA, 2015; pp. 284–291. [Google Scholar]
- Lauren, S.; Mäki, P.; Rauti, S.; Hosseinzadeh, S.; Hyrynsalmi, S.; Leppänen, V. Symbol Diversification of Linux Binaries. In Proceedings of the 2014 World Congress on Internet Security (WorldCIS), London, UK, 8–10 December 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 74–79. [Google Scholar]
- Abrath, B.; Coppens, B.; Volckaert, S.; De Sutter, B. Obfuscating Windows DLLs. In Proceedings of the 1st International Workshop on Software Protection, SPRO ’15. Florence, Italy, 19 May 2015; IEEE Press: Piscataway, NJ, USA, 2015; pp. 24–30. [Google Scholar]
- Uitto, J.; Rauti, S.; Mäkelä, J.M.; Leppänen, V. Preventing Malicious Attacks by Diversifying Linux Shell Commands. In Proceedings of the 14th Symposium on Programming Languages and Software Tools (SPLST’15), Tampere, Finland, 9–10 October 2015; pp. 206–220. [Google Scholar]
- Uitto, J.; Rauti, S.; Leppänen, V. Practical implications and requirements of diversifying interpreted languages. In Proceedings of the 11th Annual Cyber and Information Security Research Conference), Oak Ridge, TN, USA, 5–7 April 2016; ACM: New York, NY, USA, 2016. Article No. 14. [Google Scholar]
- Shacham, H.; Page, M.; Pfaff, B.; Goh, E.J.; Modadugu, N.; Boneh, D. On the Effectiveness of Address-space Randomization. In Proceedings of the 11th ACM Conference on Computer and Communications Security, CCS ’04, Washington, DC, USA, 25–29 October 2004; pp. 298–307. [Google Scholar]
- Bhatkar, E.; Duvarney, D.C.; Sekar, R. Address obfuscation: An efficient approach to combat a broad range of memory error exploits. In Proceedings of the 12th USENIX Security Symposium, Washington, DC, USA, 4–8 August 2003; pp. 105–120. [Google Scholar]
- Höller, A.; Rauter, T.; Iber, J.; Kreiner, C. Towards Dynamic Software Diversity for Resilient Redundant Embedded Systems. In Proceedings of the 7th International Workshop on Software Engineering for Resilient Systems, SERENE 2015, Paris, France, 7–8 September 2015; Springer International Publishing: Cham, Switzerland, 2015; pp. 16–30. [Google Scholar]
- Tanenbaum, A. Modern Operating Systems; Pearson: London, UK, 2014. [Google Scholar]
- Liang, Z.; Liang, B.; Li, L. A System Call Randomization Based Method for Countering Code-Injection Attacks. Int. J. Inf. Technol. Comput. Sci. (IJITCS) 2009, 1, 1. [Google Scholar] [CrossRef]
- Jiang, X.; Wang, H.J.; Xu, D.; Wang, Y. RandSys: Thwarting Code Injection Attacks with System Service Interface Randomization. In Proceedings of the 26th IEEE International Symposium on Reliable Distributed Systems, SRDS 2007, Beijing, China, 10–12 October 2007; pp. 209–218. [Google Scholar]
- National Vulnerability Database. Vulnerability Summary for CVE-2014-6271. Initial CVE of Shellshock Vulnerability. Available online: https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2014-6271 (accessed on 15 December 2017).
- Portokalidis, G.; Keromytis, A. Global ISR: Toward a Comprehensive Defense Against Unauthorized Code Execution. In Moving Target Defense, Creating Asymmetric Uncertainty for Cyber Threats, Advances in Information Security 54; Springer: New York, NY, USA, 2014; pp. 469–480. [Google Scholar]
- Xu, H.; Chapin, S. Address-space Layout Randomization Using Code Islands. J. Comput. Secur. 2009, 17, 331–362. [Google Scholar] [CrossRef]
- Cook, K. Introduce Struct Layout Randomization Plugin. Available online: https://lwn.net/Articles/723997/ (accessed on 15 December 2017).
- Shelby, Z.; Hartke, K.; Bormann, C. The Constrained Application Protocol (CoAP); Internet Engineering Task Force (IETF): Fremont, CA, USA, 2014. [Google Scholar]
- SYSCALLS.TXT. Available online: https://android.googlesource.com/platform/bionic.git/+/brillo-m9-dev/libc/SYSCALLS.TXT (accessed on 15 December 2017).
- ChibiOS/RT: Syscalls.c Source File. Available online: http://chibios.sourceforge.net/html/syscalls_8c_source.html (accessed on 15 December 2017).
- Contiki Wiki. Available online: https://github.com/contiki-os/contiki/wiki (accessed on 15 December 2017).
- Contiki Homepage. Available online: http://www.contiki-os.org/ (accessed on 15 December 2017).
- Cloud-Native IoT Operating System for Microcontrollers. Available online: https://github.com/aws/amazon-freertos (accessed on 15 December 2017).
- INTEGRITY Real-Time Operating System. Available online: http://www.ghs.com/products/rtos/integrity.html (accessed on 15 December 2017).
- Bhatti, S.; Carlson, J.; Dai, H.; Deng, J.; Rose, J.; Sheth, A.; Shucker, B.; Gruenwald, C.; Torgerson, A.; Han, R. MANTIS OS: An embedded multithreaded operating system for wireless micro sensor platforms. Mob. Netw. Appl. 2005, 10, 563–579. [Google Scholar] [CrossRef]
- mbed OS uVisor. Available online: https://github.com/ARMmbed/uvisor (accessed on 15 December 2017).
- Apache Mynewt Repository. Available online: https://github.com/apache/mynewt-core (accessed on 15 December 2017).
- Baselibc Library—Apache Mynewt. Available online: https://mynewt.apache.org/latest/os/modules/baselibc/ (accessed on 15 December 2017).
- Nano-RK: A Wireless Sensor Networking Real-Time Operating System. Available online: http://www.nano-rk.org/projects/nanork/wiki (accessed on 15 December 2017).
- QNX Developer Support. Available online: http://www.qnx.com/developers/docs/6.3.0SP3/neutrino/sys_arch/proc.html (accessed on 15 December 2017).
- QNX SDP 6.6 Documentation. Available online: http://www.qnx.com/developers/docs/660/index.jsp?topic=%2Fcom.qnx.doc.neutrino.getting_started%2Ftopic%2Fs1_procs_Starting_with_system.html (accessed on 15 December 2017).
- Memory Configurations. Available online: http://nuttx.org/doku.php?id=wiki:nxinternal:memconfigs (accessed on 15 December 2017).
- Firmware for Particle Devices. Available online: https://github.com/spark/firmware (accessed on 15 December 2017).
- Baccelli, E.; Hahm, O.; Gunes, M.; Wahlisch, M.; Schmidt, T.C. RIOT OS: Towards an OS for the Internet of Things. In Proceedings of the 2013 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Turin, Italy, 14–19 April 2013; pp. 79–80. [Google Scholar]
- TinyOS Documentation Wiki. Available online: http://tinyos.stanford.edu/tinyos-wiki (accessed on 22 June 2016).
- Cao, Q.; Abdelzaher, T.; Stankovic, J.; He, T. The liteos operating system: Towards unix-like abstractions for wireless sensor networks. In Proceedings of the 2008 International Conference On Information Processing in Sensor Networks, IPSN ’08, St. Louis, MO, USA, 22–24 April 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 233–244. [Google Scholar]
- Wind River Systems. VxWorks Kernel Programmer’s Guide; Wind River: Alameda, CA, USA, 2003. [Google Scholar]
- ZwAllocateVirtualMemory Routine (Windows Drivers). Available online: https://msdn.microsoft.com/en-us/library/windows/hardware/ff566416(v=vs.85).aspx (accessed on 15 December 2017).
- MMU/MPU Samples—Zephyr Project Documentation. Available online: http://docs.zephyrproject.org/samples/mpu/index.html (accessed on 15 December 2017).
- Zephyr Project: System Calls. Available online: http://docs.zephyrproject.org/kernel/usermode/syscalls.html (accessed on 15 December 2017).
- Portokalidis, G.; Keromytis, A. Fast and Practical Instruction-set Randomization for Commodity Systems. In Proceedings of the 26th Annual Computer Security Applications Conference, ACSAC ’10, Austin, TX, USA, 6–10 December 2010; ACM: New York, NY, USA, 2010; pp. 41–48. [Google Scholar]
- Amadeo, R. Google’s new “Android Things” OS hopes to solve awful IoT security. Ars Technica 2016. Available online: https://arstechnica.com/gadgets/2016/12/google-brillo-rebrands-as-android-things-googles-internet-of-things-os/ (accessed on 15 December 2017).
- Shelby, Z.; Bormann, C. 6LoWPAN: The Wireless Embedded Internet; John Wiley & Sons: Hoboken, NJ, USA, 2011; Volume 43. [Google Scholar]
- Sastry, N.; Wagner, D. Security considerations for IEEE 802.15. 4 networks. In Proceedings of the 3rd ACM Workshop on Wireless Security, Philadelphia, PA, USA, 1 October 2004; ACM: New York, NY, USA, 2004; pp. 32–42. [Google Scholar]
- FreeRTOS-MPU—ARM Cortex-M3 and ARM Cortex-M4 Memory Protection Unit Support in FreeRTOS. Available online: https://www.freertos.org/FreeRTOS-MPU-memory-protection-unit.html (accessed on 15 December 2017).
- CVE-2016-3714. Available online: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2016-3714 (accessed on 15 December 2017).
- Pop, A.R. DEP/ASLR Implementation Progress in Popular Third-Party Windows Applications; Secunia Research: Itasca, IL, USA, 2010. [Google Scholar]
- Kil, C.; Jun, J.; Bookholt, C.; Xu, J.; Ning, P. Address Space Layout Permutation (ASLP): Towards Fine-Grained Randomization of Commodity Software. In Proceedings of the 22nd Annual Computer Security Applications Conference, ACSAC ’06, Miami Beach, FL, USA, 11–15 December 2006; pp. 339–348. [Google Scholar]
- Shacham, H. The Geometry of Innocent Flesh on the Bone: Return-into-libc Without Function Calls (on the x86). In Proceedings of the 14th ACM Conference on Computer and Communications Security, CCS ’07, Alexandria, VA, USA, 29 October 2017–2 November 2007; ACM: New York, NY, USA, 2007; pp. 552–561. [Google Scholar]
- Crane, S.J.; Volckaert, S.; Schuster, F.; Liebchen, C.; Larsen, P.; Davi, L.; Sadeghi, A.R.; Holz, T.; De Sutter, B.; Franz, M. It’s a TRaP: Table Randomization and Protection Against Function-Reuse Attacks. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, It’s a TRaP: Table Randomization and Protection Against Function-Reuse, CCS ’15, Attacks, CO, USA, 12–16 October 2015; ACM: New York, NY, USA, 2015; pp. 243–255. [Google Scholar]
- Diversification on Thingsee One Firmware. Available online: https://gitlab.utu.fi/soft/thingsee-sdk (accessed on 15 December 2017).
- Shuffle-ld—Layout Shuffling Diversification—Binutils. Available online: https://gitlab.utu.fi/soft/binutils-gdb (accessed on 15 December 2017).
- Procedure Call Standard for the ARM® Architecture. 2015. Available online: http://infocenter.arm.com/help/topic/com.arm.doc.ihi0042f/IHI0042F_aapcs.pdf (accessed on 15 December 2017).
- Lopez, J.; Roman, R.; Alcaraz, C. Analysis of Security Threats, Requirements, Technologies and Standards in Wireless Sensor Networks. In Foundations of Security Analysis and Design V: FOSAD 2007/2008/2009 Tutorial Lectures; Aldini, A., Barthe, G., Gorrieri, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 289–338. [Google Scholar]
- Rault, T.; Bouabdallah, A.; Challal, Y. Energy efficiency in wireless sensor networks: A top-down survey. Comput. Netw. 2014, 67, 104–122. [Google Scholar] [CrossRef]
| OS | Source Code | MMU Support | System Calls | Shell |
|---|---|---|---|---|
| Android Things | Available | Yes | Yes [33] | Yes |
| ChibiOS | Available | No | Minimal [34] | Yes |
| Contiki | Available | No | No [35] | Yes [36] |
| Amazon FreeRTOS | Available | No | No [37] | Yes |
| GNU/Linux | Available | Required | Yes | Yes |
| Integrity | Closed | Yes | Yes [38] | No |
| MANTIS | Available | No | No [39] | Yes |
| mbed | Available | No/uVisor | Partial [40] | Yes |
| Mynewt | Available | No [41] | No [42] | Yes |
| Nano-RK | Available | No | No [43] | No |
| Neutrino | Closed | Yes [44] | Yes [45] | Yes |
| NuttX | Available | Partial | Yes [46] | Yes |
| Particle | Available | No | No [47] | Yes |
| RIOT | Available | No | No [48] | Yes |
| TinyOS | Available | No | No [49] | Yes |
| UIUC LiteOS | Available | No | Yes [50] | No |
| VxWorks | Closed | Yes | Yes [51] | Yes |
| Windows IoT | Closed | Yes | Yes [52] | Yes |
| Yocto Project | Available | Based on GNU/Linux | ||
| Zephyr | Available | Yes [53] | Yes [54] | Yes |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rauti, S.; Koivunen, L.; Mäki, P.; Hosseinzadeh, S.; Laurén, S.; Holvitie, J.; Leppänen, V. Internal Interface Diversification as a Security Measure in Sensor Networks. J. Sens. Actuator Netw. 2018, 7, 12. https://doi.org/10.3390/jsan7010012
Rauti S, Koivunen L, Mäki P, Hosseinzadeh S, Laurén S, Holvitie J, Leppänen V. Internal Interface Diversification as a Security Measure in Sensor Networks. Journal of Sensor and Actuator Networks. 2018; 7(1):12. https://doi.org/10.3390/jsan7010012
Chicago/Turabian StyleRauti, Sampsa, Lauri Koivunen, Petteri Mäki, Shohreh Hosseinzadeh, Samuel Laurén, Johannes Holvitie, and Ville Leppänen. 2018. "Internal Interface Diversification as a Security Measure in Sensor Networks" Journal of Sensor and Actuator Networks 7, no. 1: 12. https://doi.org/10.3390/jsan7010012
APA StyleRauti, S., Koivunen, L., Mäki, P., Hosseinzadeh, S., Laurén, S., Holvitie, J., & Leppänen, V. (2018). Internal Interface Diversification as a Security Measure in Sensor Networks. Journal of Sensor and Actuator Networks, 7(1), 12. https://doi.org/10.3390/jsan7010012




