Dynamic Fault Tree Model of Civil Aircraft Avionics Network Transmission Failure Based on Optimized Extended Fuzzy Algorithm
Abstract
1. Introduction
- Addressing the issues of missing transmission failure analysis methods in avionics networks and the mismatch between existing methods and their security requirements, this paper introduces a DFT modeling method for civil aircraft avionics network transmission based on an optimized extended fuzzy algorithm, assessing the reliability of AFDX data transmission;
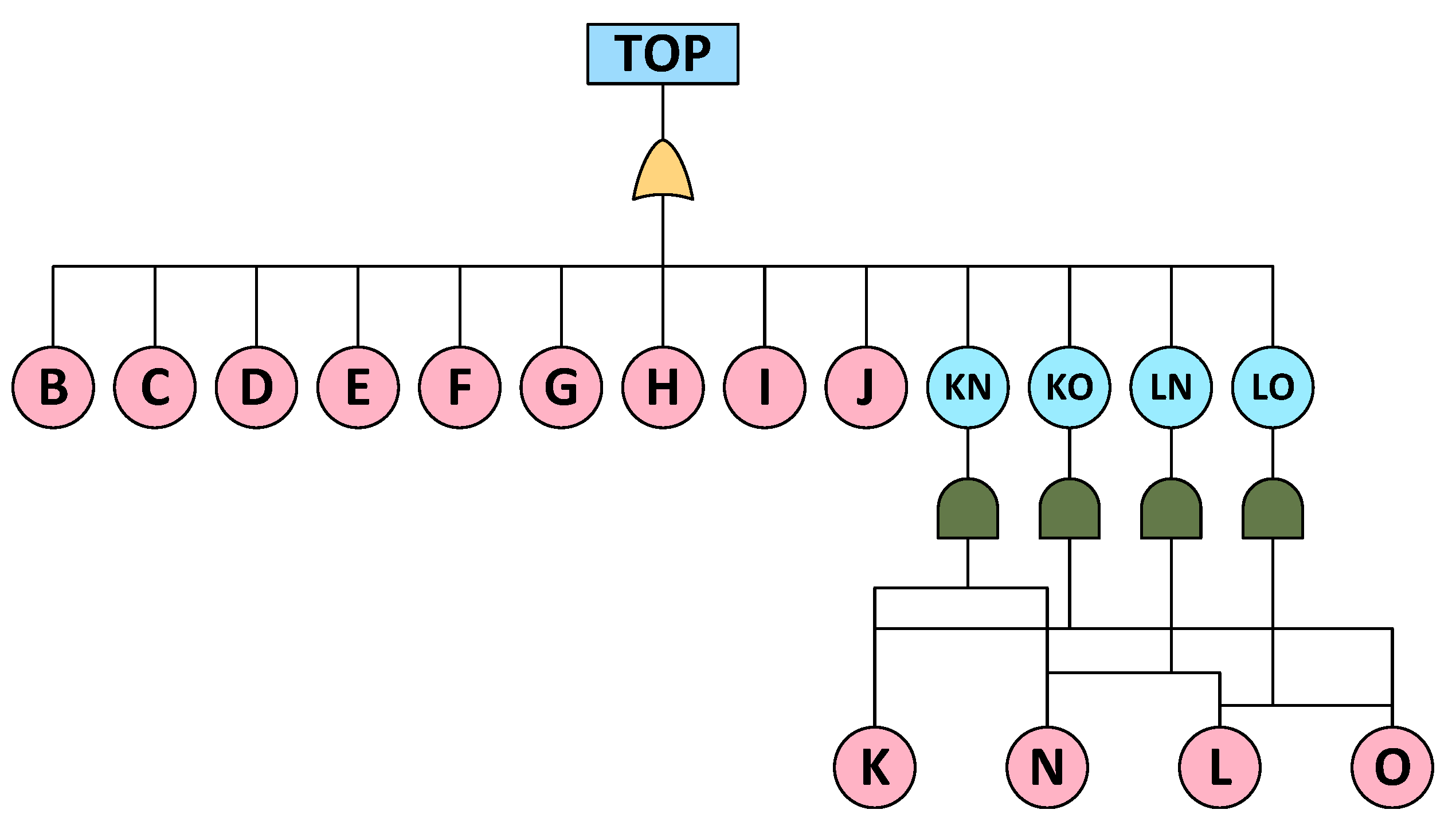
- To address the redundancy structure and event dependencies in the avionics network, dynamic logic gates are employed to construct a DFT model. In line with practical requirements, certain nodes are removed to reconstruct the simplest fault tree by solving the minimal cut set, thereby reducing the accumulated fuzziness in subsequent quantitative analyses;
- Considering the unstable characteristics of the avionics network’s failure states and the disparities between events, a triangular fuzzy representation based on relative confidence levels is applied to depict the failure rates of basic events (BEs).
- To further regulate the fuzzy scale and enhance accuracy, the proposed approach aggregates multisource fuzzy failure probability intervals using the optimized weakest t-norm operator, thereby bolstering the referential reliability of the evaluation results.
2. Related Work
2.1. Avionics Network Transmission
2.2. Fault Tree Analysis
2.3. Fuzzy Set Theory
2.4. Chapter Summary
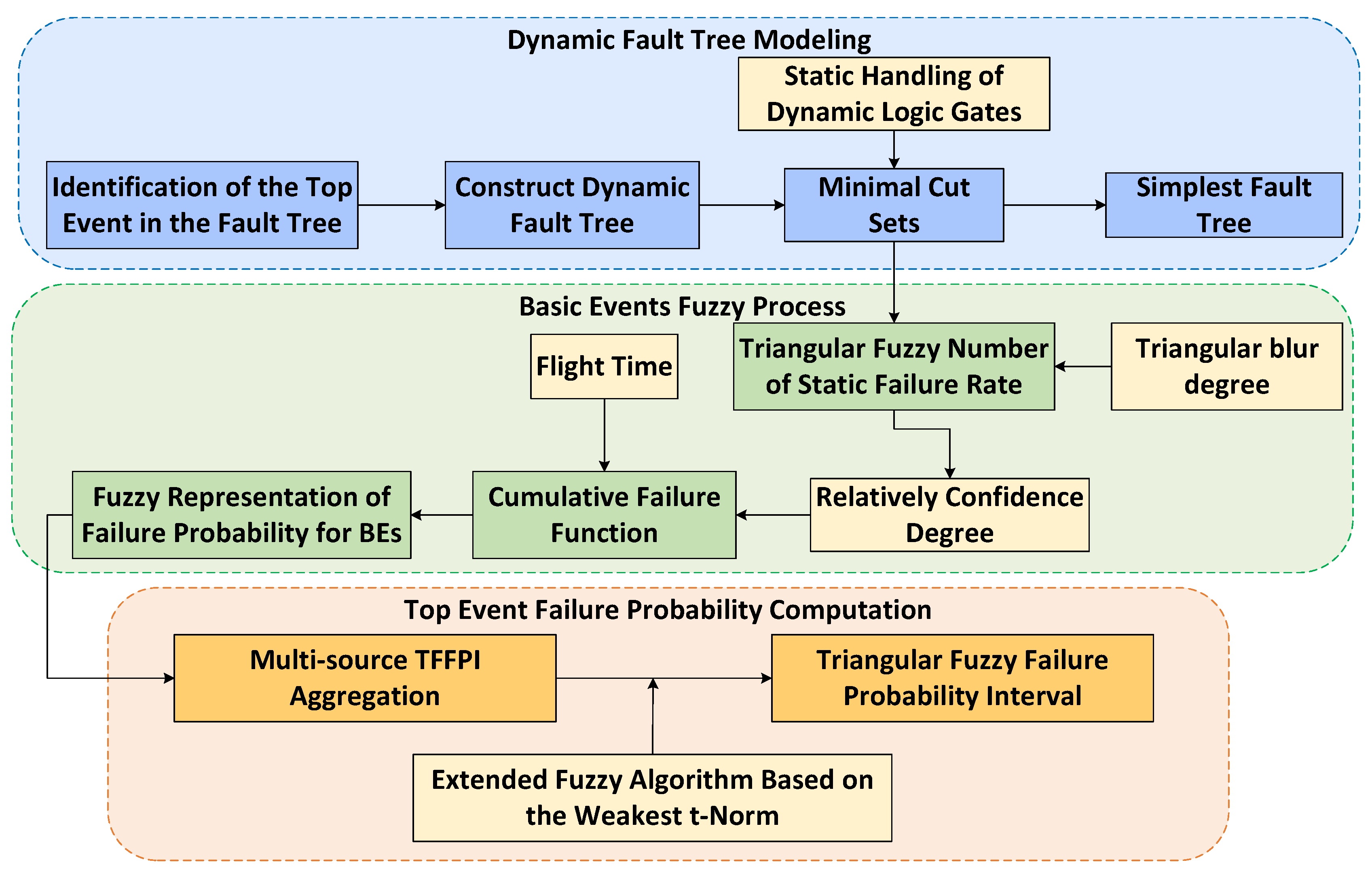
3. Proposed Method
3.1. Dynamic Fault Tree Construction
3.2. Fuzzy Representation of the Basic Events
3.3. Extended Aggregation of the BE Fuzzy Intervals
4. Case Studies
4.1. Experimental Object
4.2. Experimental Design
- Preflight: configuring the avionics network settings and verifying that the AFDX data bus is fully operational and ready for deployment.
- Take off and climb: Ensuring real-time data transmission with minimal latency for critical systems. This includes transmitting flight state data from sensors and accessing historical reference information from the onboard database.
- Cruise, descent, and approach: continuously monitoring and managing data flow to maintain consistent performance and reliability throughout these phases.
- Landing: providing dependable communication to support landing procedures and facilitating fault detection.
- Post-flight: Collecting and analyzing data for maintenance and troubleshooting purposes.
4.3. Results Analysis and Discussion
4.3.1. Transmission Failure Dynamic Fault Tree
4.3.2. BE Failure Probability Fuzzy Interval
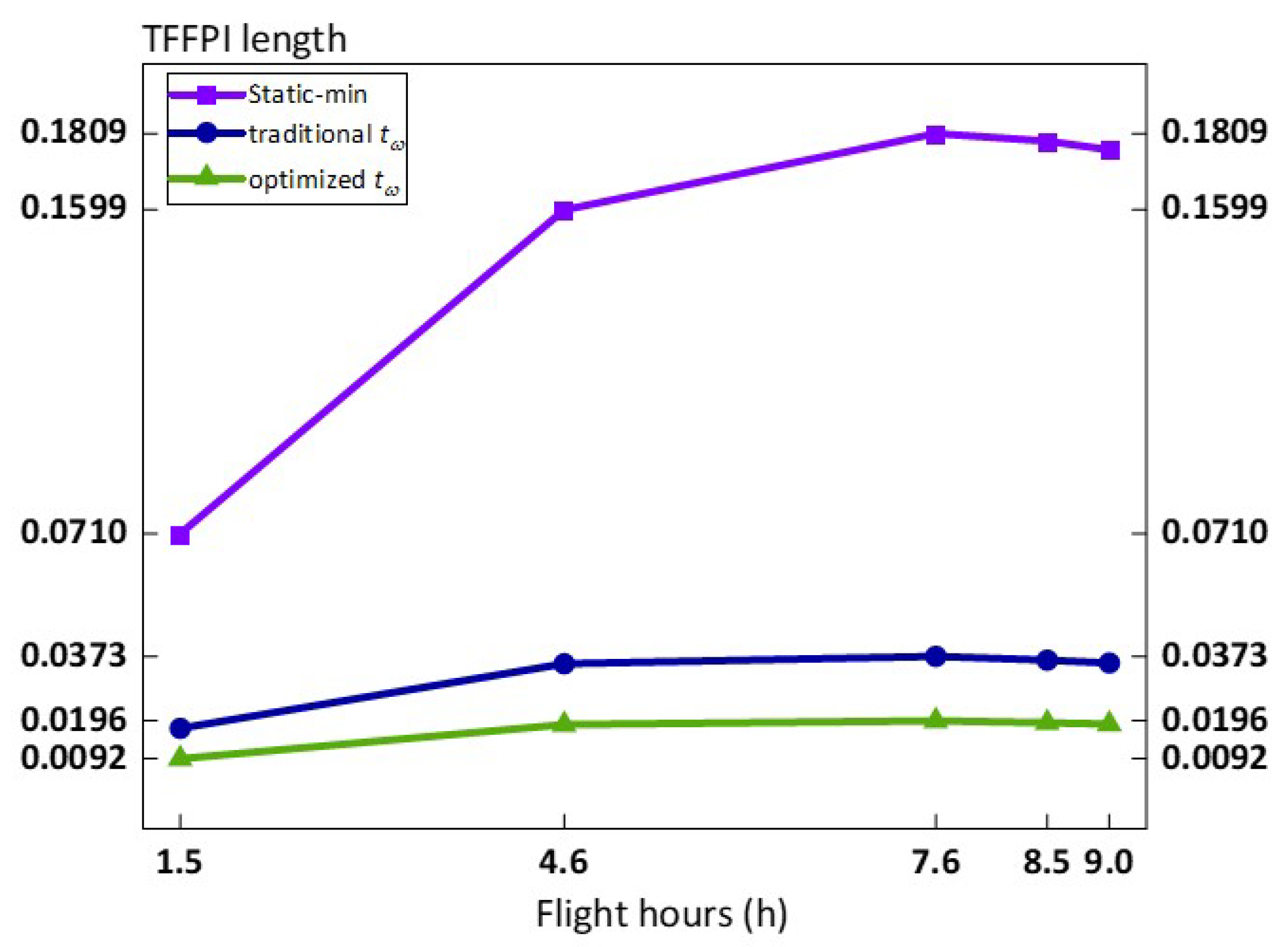
4.3.3. Failure Probability Aggregation and T-Norm Effects
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Aeronautical Radio Inc. ARINC 664: Aircraft Data Network, Part 7: Avionics Full Duplex Switched Ethernet Network; Electronic Engineering Committee: New York, NY, USA, 2009. [Google Scholar]
- Kirshner, M. Model-based systems engineering cybersecurity for space systems. Aerospace 2023, 10, 116. [Google Scholar] [CrossRef]
- Fusco, F.; Castrillo, V.U.; Giannetta, H.M.R.; Albano, M.; Cavallini, E. Methods, Standards and Components for Wireless Communications and Power Transfer Aimed at Intra-Vehicular Applications of Launchers. Aerospace 2024, 11, 132. [Google Scholar] [CrossRef]
- Chen, W.; Tian, Y.; Sun, S.; Liu, R. Interference Study of 5G System on Civil Aircraft Airborne Beidou RDSS System in Takeoff and Landing Phase. Aerospace 2024, 11, 522. [Google Scholar] [CrossRef]
- Aeronautical Radio Inc. ARINC 811: Commercial Aircraft Information Security Concepts of Operation and Process Framework; Electronic Engineering Committee: New York, NY, USA, 2005. [Google Scholar]
- Society of Automotive Engineers. ARP4754A Guidelines for Development of Civil Aircraft Systems; SAE International: Warrendale, PA, USA, 2011. [Google Scholar]
- Society of Automotive Engineers. ARP4761, Guidelines and Methods for Conducting the Safety Assessment Process on Civil Airborne Systems and Equipment; SAE International: Warrendale, PA, USA, 1996. [Google Scholar]
- Dong, H.; Zhai, Z.; Lu, Y.; Gu, Q.; Wang, G.; Wang, M. Availability Analysis of Electronic Flight Instrument System Based on Dynamic Fault Dependent Matrix. In Proceedings of the 2019 IEEE 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019. [Google Scholar]
- Dou, X. Big data and smart aviation information management system. Cogent Bus. Manag. 2020, 7, 1766736. [Google Scholar] [CrossRef]
- Haiyong, D.; Guoqing, W.; Zhengjun, Z.; Yanhong, L.; Qingfan, G. Availability analysis of electronic flight instrument system based on dynamic fault tree. In Proceedings of the 2018 Tenth International Conference on Advanced Computational Intelligence (ICACI), Xiamen, China, 29–31 March 2018. [Google Scholar]
- Haiyun, Y.; Sun, Y. A combination method for integrated modular avionics safety analysis. Aircr. Eng. Aerosp. Technol. 2023, 95, 345–357. [Google Scholar]
- Volkan, S.; Friedl, F.; Schmehl, R. Improving reliability and safety of airborne wind energy systems. Wind. Energy 2020, 23, 340–356. [Google Scholar]
- Mohit, K.; Walia, G.K.; Shingare, H.; Singh, S.; Gill, S.S. AI-Based Sustainable and Intelligent Offloading Framework for IIoT in Collaborative Cloud-Fog Environments. IEEE Trans. Consum. Electron. 2023, 70, 1414–1422. [Google Scholar]
- Anas, A.S.; Samriya, J.K.; Kumar, M.; Gill, S.S.; Khan, R.A. Intelligent Fog-IoT Networks with 6G Endorsement: Foundations, Applications, Trends and Challenges. In 6G Enabled Fog Computing in IoT: Applications and Opportunities; Springer: New York, NY, USA, 2023; pp. 287–307. [Google Scholar]
- Kumar, S.J.; Kumar, M.; Gill, S.S. Secured data offloading using reinforcement learning and Markov decision process in mobile edge computing. Int. J. Netw. Manag. 2023, 33, E2243. [Google Scholar]
- Kumar, S.J.; Kumar, M.; Tiwari, R. Energy-aware aco-dnn optimization model for intrusion detection of unmanned aerial vehicle (uavs). J. Ambient. Intell. Humaniz. Comput. 2023, 14, 10947–10962. [Google Scholar]
- Kang, J.; Xiong, Z.; Wang, R.; Hua, B. Resilient Multi-Source Integrated Navigation Method for Aerospace Vehicles Based on On-Line Evaluation of Redundant Information. Aerospace 2022, 9, 333. [Google Scholar] [CrossRef]
- Xueqian, T.; Li, Q.; Lu, G.; Xiong, H. A Revised Trajectory Approach for the Worst-Case Delay Analysis of an AFDX Network. IEEE Access 2019, 7, 142564–142573. [Google Scholar]
- Anaïs, F.; Mifdaoui, A. Worst-case timing analysis of AFDX networks with multiple TSN/BLS shapers. IEEE Access 2020, 8, 106765–106784. [Google Scholar]
- Meng, L.; Zhu, G.; Savaria, Y.; Lauer, M. Reliability enhancement of redundancy management in AFDX networks. IEEE Trans. Ind. Inform. 2017, 13, 2118–2129. [Google Scholar]
- Lan, M.; Wang, Y. Mitigation of Sequence Inversion in AFDX based on Time-triggered Scheduling. In Proceedings of the 2022 Integrated Communication, Navigation and Surveillance Conference (ICNS), Herndon, VI, USA, 5–7 April 2022. [Google Scholar]
- Wang, Y.; Haolin, M.; Meng, Y.; Zhijun, W. Optimization of Airborne AFDX Transmission Delay Based on Revised RSP Method. In Proceedings of the 2021 IEEE 6th International Conference on Computer and Communication Systems (ICCCS), Chengdu, China, 23–26 April 2021. [Google Scholar]
- Tyler, P.; Sugunaraj, N.; Ranganathan, P. Aircraft Communication Systems-Topologies, Protocols, and Vulnerabilities. J. Netw. Comput. Appl. 2023. Available online: https://commons.und.edu/ee-stu/11/ (accessed on 12 June 2024).
- Uncu, A.; Üzümcü, S.; Mert, A.A. Cyber Security Concerns Regarding Federated, Partly IMA and Full IMA Implementations. In Proceedings of the 2019 IEEE/AIAA 38th Digital Avionics Systems Conference (DASC), San Diego, CA, USA, 8–12 September 2019. [Google Scholar]
- Klaus, K.; Fruhmann, M.; Gebeshuber, K.; Leitgeb, E.; Gruber, M. Evaluation of Cyber Security in Digital Avionic Systems. In Proceedings of the 2020 IEEE 91st Vehicular Technology Conference (VTC2020-Spring), Antwerp, Belgium, 25 May–31 July 2020. [Google Scholar]
- Predescu, A.V.; Stelkens-Kobsch, T.H. Aviation Security Lab: A testbed for security testing of current and future aviation technologies. In Proceedings of the 2022 IEEE/AIAA 41st Digital Avionics Systems Conference (DASC), Portsmouth, VI, USA, 18–22 September 2022. [Google Scholar]
- Naeem, M.H.; Abbasi, I.H.; Mohsin, M. An Autonomous Intrusion Detection System for Ethernet-Based Avionics Communication Bus. In Proceedings of the 2021 International Conference on Engineering and Emerging Technologies (ICEET), Istanbul, Turkey, 27–28 October 2021. [Google Scholar]
- Gascard, E.; Simeu-Abazi, Z. Quantitative analysis of dynamic fault trees using Monte Carlo simulations: Event-driven simulation approach. Reliab. Eng. Syst. Saf. 2018, 180, 487–504. [Google Scholar] [CrossRef]
- Wang, Y.; Lei, H.; Hackett, R.; Beeby, M. Safety assessment process optimization for integrated modular avionics. IEEE Aerosp. Electron. Syst. Mag. 2019, 34, 58–67. [Google Scholar] [CrossRef]
- Nobakhti, A.; Raissi, S.; Damghani, K.K.; Soltani, R. Dynamic reliability assessment of a complex recovery system using fault tree, fuzzy inference and discrete event simulation. Eksploat. Niezawodn. 2021, 23, 593–604. [Google Scholar] [CrossRef]
- Yazdi, M.; Kabir, S. Fuzzy evidence theory and Bayesian networks for process systems risk analysis. Hum. Ecol. Risk Assess. Int. J. 2020, 26, 57–86. [Google Scholar] [CrossRef]
- Ung, S.T. Evaluation of human error contribution to oil tanker collision using fault tree analysis and modified fuzzy Bayesian Network based CREAM. Ocean. Eng. 2019, 179, 159–172. [Google Scholar] [CrossRef]
- Xue, L.; MacKenzie, C.A. Assessing risk in different types of supply chains with a dynamic fault tree. Comput. Ind. Eng. 2019, 137, 106061. [Google Scholar]
- Höflinger, K.; Müller, S.; Peng, T.; Ulmer, M.; Lüdtke, D.; Gerndt, A. Dynamic fault tree analysis for a distributed onboard computer. In Proceedings of the 2019 IEEE Aerospace Conference, Dayton, OH, USA, 15–19 July 2019. [Google Scholar]
- Chong, W.; Wang, L.; Chen, H.; Yang, Y.; Li, Y. Fault diagnosis of train network control management system based on dynamic fault tree and Bayesian network. IEEE Access 2020, 9, 2618–2632. [Google Scholar]
- Koorosh, A.; Latif-Shabgahi, G.-R. A hierarchical approach for dynamic fault trees solution through semi-Markov process. IEEE Trans. Reliab. 2019, 69, 986–1003. [Google Scholar]
- Jiang, G.J.; Li, Z.Y.; Qiao, G.; Chen, H.X.; Li, H.B.; Sun, H.H. Reliability analysis of dynamic fault tree based on binary decision diagrams for explosive vehicle. Math. Probl. Eng. 2021, 2021, 5559475. [Google Scholar]
- Sohag, K.; Aslansefat, K.; Sorokos, I.; Papadopoulos, Y.; Konur, S. A hybrid modular approach for dynamic fault tree analysis. IEEE Access 2020, 8, 97175–97188. [Google Scholar]
- Marwan, A.; Hamad, G.B.; Mohamed, O.A.; Savaria, Y. Towards an accurate probabilistic modeling and statistical analysis of temporal faults via temporal dynamic fault-trees (TDFTs). IEEE Access 2019, 7, 29264–29276. [Google Scholar]
- Aikhuele, D.O.; Ighravwe, D.E.; Akinyele, D. Evaluation of renewable energy technology based on reliability attributes using hybrid fuzzy dynamic decision-making model. Technol. Econ. Smart Grids Sustain. Energy 2019, 4, 16. [Google Scholar] [CrossRef]
- Torra, V. Hesitant fuzzy sets. Int. J. Intell. Syst. 2010, 25, 529–539. [Google Scholar] [CrossRef]
- Baklouti, A.; Nguyen, N.; Mhenni, F.; Choley, J.Y.; Mlika, A. Dynamic fault tree generation for safety-critical systems within a systems engineering approach. IEEE Syst. J. 2019, 14, 1512–1522. [Google Scholar] [CrossRef]
- Hongyu, Y.; Feng, Y. A Pythagorean fuzzy Petri net based security assessment model for civil aviation airport security inspection information system. Int. J. Intell. Syst. 2021, 36, 2122–2143. [Google Scholar]
- Żyluk, A.; Kuźma, K.; Grzesik, N.; Zieja, M.; Tomaszewska, J. Fuzzy Logic in Aircraft Onboard Systems Reliability Evaluation—A New Approach. Sensors 2021, 21, 7913. [Google Scholar] [CrossRef]
- Goncharenko, Y.; Blyskun, O.; Martyniuk, O. Flight safety fuzzy risk assessment for combat aviation system. In Proceedings of the 2nd IEEE International Conference on Advanced Trent in Information Theory, Kyiv, Ukraine, 25–27 November 2020. [Google Scholar]
- Zhou, H.; Zhao, Y.; Shen, Q.; Yang, L.; Cai, H. Risk assessment and management via multi-source information fusion for undersea tunnel construction. Autom. Constr. 2020, 111, 103050. [Google Scholar] [CrossRef]
- Pan, Y.; Zhang, L.; Li, Z.; Ding, L. Improved fuzzy Bayesian network-based risk analysis with interval-valued fuzzy sets and D–S evidence theory. IEEE Trans. Fuzzy Syst. 2019, 28, 2063–2077. [Google Scholar] [CrossRef]
- Li, Y.-F.; Huang, H.Z.; Mi, J.; Peng, W.; Han, X. Reliability analysis of multi-state systems with common cause failures based on Bayesian network and fuzzy probability. Ann. Oper. Res. 2022, 311, 195–209. [Google Scholar] [CrossRef]
- Zhou, X.; Peng, T. Application of multi-sensor fuzzy information fusion algorithm in industrial safety monitoring system. Saf. Sci. 2020, 122, 104531. [Google Scholar] [CrossRef]
- Gil Casals, S. Risk Assessment and Intrusion Detection for Airbone Networks. Ph.D. Thesis, INSA, Toulouse, France, 2014. [Google Scholar]
- Guo, Y.; Zhong, M.; Gao, C.; Wang, H.; Liang, X.; Yi, H. A discrete-time Bayesian network approach for reliability analysis of dynamic systems with common cause failures. Reliab. Eng. Syst. Saf. 2021, 216, 108028. [Google Scholar] [CrossRef]
- Zhu, C.; Zhang, T. A review on the realization methods of dynamic fault tree. Qual. Reliab. Eng. Int. 2022, 38, 3233–3251. [Google Scholar] [CrossRef]
- Tang, X.; Luo, Z.; Qu, G. Worst-Case End-to-End Delay Analysis for an AFDX Evolution Network. In Proceedings of the 2020 IEEE 6th International Conference on Computer and Communications (ICCC), Chengdu, China, 11–14 December 2020. [Google Scholar]
- Villegas, J.; Fortes, S.; Escaño, V.; Baena, C.; Colomer, B.; Barco, R. Verification and Validation Framework for AFDX Avionics Networks. IEEE Access 2022, 10, 66743–66756. [Google Scholar] [CrossRef]
- Dai, J.; Li, C.; Wang, K.; Zhao, C. Application prospect of time-sensitive network in airborne communication network. J. Phys. Conf. Ser. 2022, 2253, 012035. [Google Scholar] [CrossRef]
- Aslansefat, K.; Kabir, S.; Gheraibia, Y.; Papadopoulos, Y. Dynamic fault tree analysis: State-of-the-art in modeling, analysis, and tools. In Reliability Management and Engineering; CRC Press: Boca Raton, FL, USA, 2020; pp. 73–112. [Google Scholar]
- Xiang, J.; Machida, F.; Tadano, K.; Yanoo, K.; Sun, W.; Maeno, Y. A static analysis of dynamic fault trees with priority-and gates. In Proceedings of the 2013 Sixth Latin-American Symposium on Dependable Computing, Rio de Janeiro, Brazil, 1–5 April 2013. [Google Scholar]
- Fahmy, R.A.; Selim, H.K. Application of dynamic fault tree technique in safety assessment for the containment spray system of nuclear power plant. Electr. Eng. 2023, 105, 3411–3421. [Google Scholar] [CrossRef]
- Seresht, N.G.; Fayek, A.R. Computational method for fuzzy arithmetic operations on triangular fuzzy numbers by extension principle. Int. J. Approx. Reason. 2019, 106, 172–193. [Google Scholar] [CrossRef]
- Kumar, M. A novel weakest t-norm based fuzzy fault tree analysis through qualitative data processing and its application in system reliability evaluation. J. Intell. Syst. 2018, 29, 977–993. [Google Scholar] [CrossRef]
- Komal. Fuzzy fault tree analysis for patient safety risk modeling in healthcare under uncertainty. Appl. Soft Comput. 2015, 37, 942–951. [Google Scholar] [CrossRef]


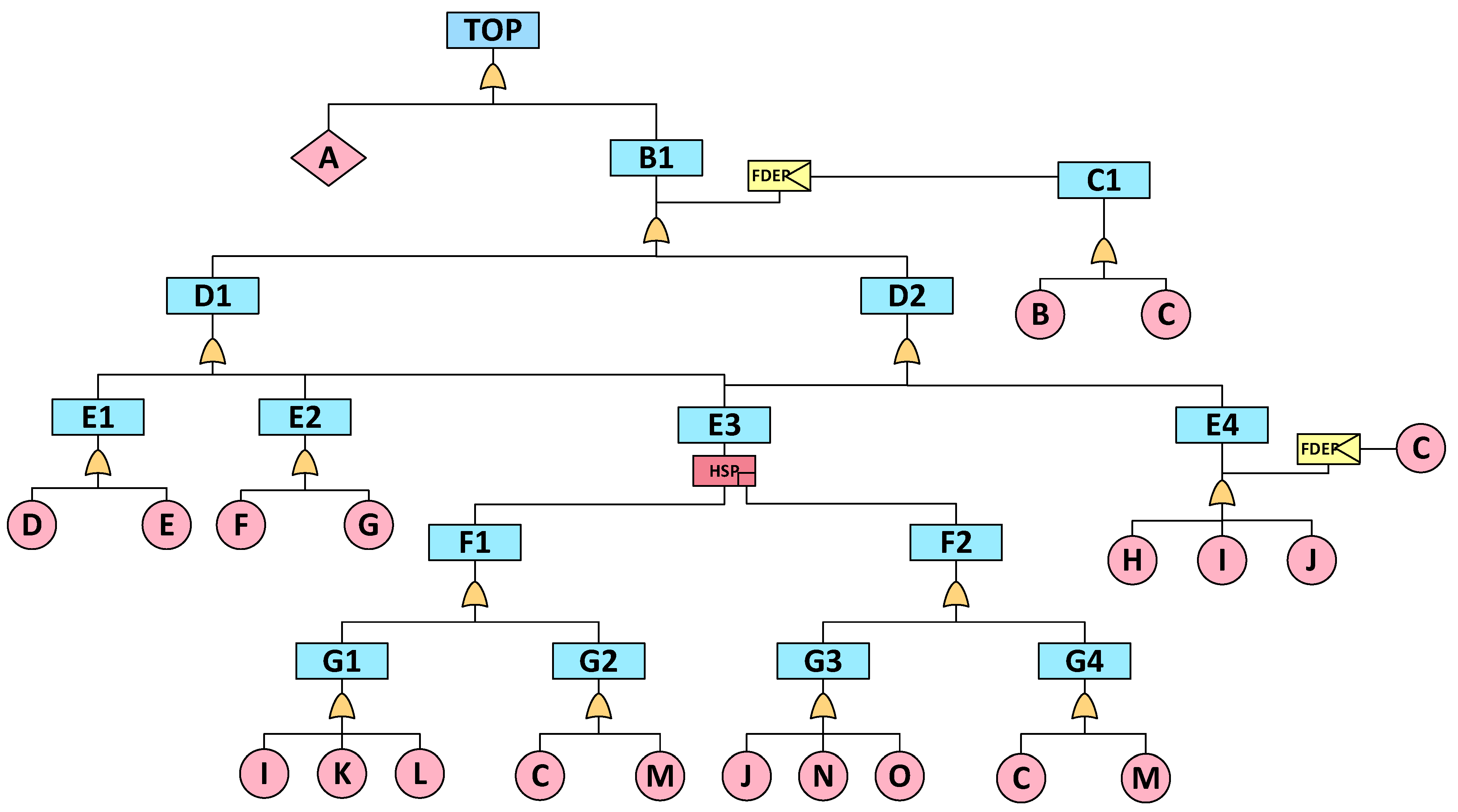
| Content | Symbol |
|---|---|
| PAND |  |
| FDEP |  |
| HSP |  |
| Undertermined Event |  |
| Symbol | Meaning | Symbol | Meaning |
|---|---|---|---|
| TOP | AFDX data transmission failure | A | Actively discard data frames |
| B1 | Data frame passive loss | B | VL configuration error |
| C1 | VL failure | C | Physical damage |
| D1 | Data frames in the wrong order | D | Data frame copy error |
| D2 | Data frame lost | E | The data frame was not sent |
| E1 | Sender failed | F | Integrity check failure |
| E2 | Receiver failure | G | Redundancy check failure |
| E3 | Redundant network failure | H | Link congestion |
| E4 | Data frame delay | I | Network A buffer failure |
| F1 | Network A fails | J | Network B buffer failure |
| F2 | Network B fails | K | Network A data frame filtering failure |
| G1 | Network A switch logic error | L | Network A data frame shaping failure |
| G2 | Network A switch is damaged | M | Equipment worn out |
| G3 | Network B switch logic error | N | Network B data frame filtering failure |
| G4 | Network B switch is damaged | O | Network B data frame shaping failure |
| BE | Failure Rate | Static TFFRI | Relative Confidence Level | Relative Confidence TFFRI |
|---|---|---|---|---|
| B | [0.0008240, 0.0010300, 0.0012875] | 1.735% | [0.0010264, 0.0010300, 0.0010345] | |
| C | [0.0061040, 0.0076300, 0.0095375] | 12.852% | [0.0074339, 0.0076300, 0.0078752] | |
| D | [0.0195200, 0.0244000, 0.0305000] | 41.099% | [0.0223944, 0.0244000, 0.0269071] | |
| E | [0.0027520, 0.0034400, 0.0043000] | 5.794% | [0.0034001, 0.0034400, 0.0034898] | |
| F | [0.0024080, 0.0030100, 0.0037625] | 5.070% | [0.0029795, 0.0030100, 0.0030482] | |
| G | [0.0068720, 0.0085900, 0.0107375] | 14.469% | [0.0083414, 0.0085900, 0.0089007] | |
| H | [0.0043440, 0.0054300, 0.0067875] | 9.146% | [0.0053307, 0.0054300, 0.0055542] | |
| I | [0.0249600, 0.0312000, 0.0390000] | 52.553% | [0.0279207, 0.0312000, 0.0352991] | |
| J | [0.0249600, 0.0312000, 0.0390000] | 52.553% | [0.0279207, 0.0312000, 0.0352991] | |
| K | [0.0050720, 0.0063400, 0.0079250] | 10.679% | [0.0062046, 0.0063400, 0.0065093] | |
| L | [0.0451200, 0.0564000, 0.0705000] | 95% | [0.0456840, 0.0564000, 0.0697950] | |
| N | [0.0050720, 0.0063400, 0.0079250] | 10.679% | [0.0062046, 0.0063400, 0.0065093] | |
| O | [0.0451200, 0.0564000, 0.0705000] | 95% | [0.0456840, 0.0564000, 0.0697950] |
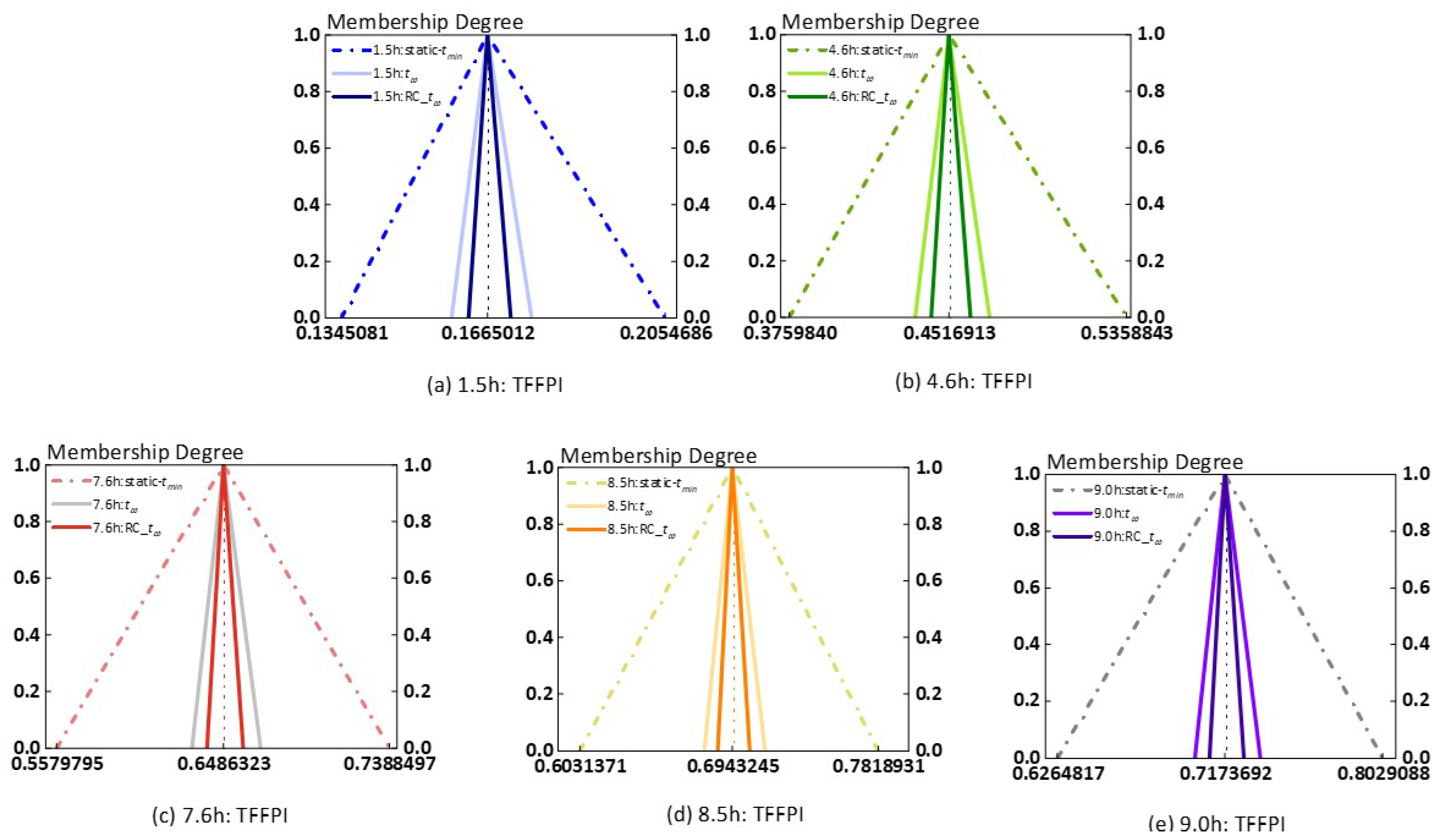
| Flight Hours | Static-Minimum t-Norm | COG | Traditional Weakest t-Norm | COG | Relative Confidence—Optimized the Weakest t-Norm | COG |
|---|---|---|---|---|---|---|
| 1.5 h | [0.1345081, 0.1665012, 0.2054686] | 0.1688260 | [0.158663, 0.1665012, 0.1761963] | 0.1671202 | [0.1623911, 0.1665012, 0.1716104] | 0.1668342 |
| 4.6 h | [0.375984, 0.4516913, 0.5358843] | 0.4545199 | [0.4357246, 0.4516913, 0.4710159] | 0.4528106 | [0.4433575, 0.4516913, 0.4619334] | 0.4523274 |
| 7.6 h | [0.5579795, 0.6486323, 0.7388497] | 0.6484872 | [0.6315676, 0.6486323, 0.668856] | 0.6496853 | [0.6397652, 0.6486323, 0.6594099] | 0.6492691 |
| 8.5 h | [0.6031371, 0.6943245, 0.7818931] | 0.6931182 | [0.6776738, 0.6943245, 0.7139335] | 0.6953106 | [0.6856842, 0.6943245, 0.7047916] | 0.6949334 |
| 9.0 h | [0.6264817, 0.7173692, 0.8029088] | 0.7155866 | [0.7010425, 0.7173692, 0.7365295] | 0.7183137 | [0.7089034, 0.7173692, 0.7276062] | 0.7179596 |
| Flight Hours | Static-Minimum t-Norm | Traditional Weakest t-Norm | Relative Confidence—Optimized the Weakest t-Norm |
|---|---|---|---|
| 1.5 h | 0.0023248 | 0.0006190 | 0.0003330 |
| 4.6 h | 0.0028286 | 0.0011193 | 0.0006361 |
| 7.6 h | 0.0001451 | 0.0010530 | 0.0006368 |
| 8.5 h | 0.0012063 | 0.0009861 | 0.0006089 |
| 9.0 h | 0.0017826 | 0.0009445 | 0.0005904 |
| Average | 0.0016575 | 0.0009444 | 0.0005610 |
| BE | Constant Value | Static-Minimum t-Norm | Traditional Weakest t-Norm | Relative Confidence—Optimized the Weakest t-Norm | Ranking of Importance |
|---|---|---|---|---|---|
| B | 0.0027613 | 0.0027020 | 0.0027530 | 0.0027563 | 13 |
| C | 0.0209775 | 0.0205328 | 0.0209146 | 0.0209394 | 7 |
| D | 0.0715905 | 0.0701349 | 0.0713759 | 0.0714607 | 3 |
| E | 0.0093073 | 0.0091084 | 0.0092794 | 0.0092904 | 9 |
| F | 0.0081305 | 0.0079566 | 0.0081061 | 0.0081158 | 10 |
| G | 0.0237040 | 0.0232026 | 0.0236330 | 0.0236610 | 6 |
| H | 0.0148036 | 0.0144884 | 0.0147592 | 0.0147767 | 8 |
| I | 0.0940236 | 0.0921509 | 0.0937418 | 0.0938532 | 1 |
| J | 0.0940236 | 0.0921509 | 0.0937418 | 0.0938532 | 1 |
| K | 0.0066504 | 0.0065344 | 0.0066305 | 0.0066383 | 11 |
| L | 0.0552759 | 0.0544736 | 0.0551102 | 0.0551757 | 4 |
| N | 0.0066504 | 0.0065344 | 0.0066305 | 0.0066383 | 11 |
| O | 0.0552759 | 0.0544736 | 0.0551102 | 0.0551757 | 4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gu, Z.; Zhang, Y.; Sui, H. Dynamic Fault Tree Model of Civil Aircraft Avionics Network Transmission Failure Based on Optimized Extended Fuzzy Algorithm. Aerospace 2024, 11, 631. https://doi.org/10.3390/aerospace11080631
Gu Z, Zhang Y, Sui H. Dynamic Fault Tree Model of Civil Aircraft Avionics Network Transmission Failure Based on Optimized Extended Fuzzy Algorithm. Aerospace. 2024; 11(8):631. https://doi.org/10.3390/aerospace11080631
Chicago/Turabian StyleGu, Zhaojun, Yinuo Zhang, and He Sui. 2024. "Dynamic Fault Tree Model of Civil Aircraft Avionics Network Transmission Failure Based on Optimized Extended Fuzzy Algorithm" Aerospace 11, no. 8: 631. https://doi.org/10.3390/aerospace11080631
APA StyleGu, Z., Zhang, Y., & Sui, H. (2024). Dynamic Fault Tree Model of Civil Aircraft Avionics Network Transmission Failure Based on Optimized Extended Fuzzy Algorithm. Aerospace, 11(8), 631. https://doi.org/10.3390/aerospace11080631




