Abstract
This comprehensive systematic review examines the integration of software-defined networking (SDN) with IoT security frameworks, analyzing recent advancements in encryption, authentication, access control techniques, and intrusion detection systems. Our analysis reveals that while SDN demonstrates promising capabilities in enhancing IoT security through centralized control and dynamic policy enforcement, several critical limitations persist, particularly in scalability and real-world validation. As intrusion detection represents an integral security requirement for robust IoT frameworks, we conduct an in-depth evaluation of Machine Learning (ML) and Deep Learning (DL) techniques that have emerged as predominant approaches for threat detection in SDN-enabled IoT environments. The review categorizes and analyzes these ML/DL implementations across various architectural paradigms, identifying patterns in their effectiveness for different security contexts. Furthermore, recognizing that the performance of these ML/DL models critically depends on training data quality, we evaluate existing IoT security datasets, identifying significant gaps in representing contemporary attack vectors and realistic IoT environments. A key finding indicates that hybrid architectures integrating cloud–edge–fog computing demonstrate superior performance in distributing security workloads compared to single-tier implementations. Based on this systematic analysis, we propose key future research directions, including adaptive zero-trust architectures, federated machine learning for distributed security, and comprehensive dataset creation methodologies, that address current limitations in IoT security research.
1. Introduction
The Internet of Things (IoT) represents a revolutionary advancement in technology that allows everyday devices to connect and communicate with each other through the internet. From smart home devices to industrial sensors, IoT has transformed how we interact with technology in our daily lives. However, this increased connectivity brings significant security challenges that traditional security methods struggle to address [1,2]. As these networks continue to grow, protecting them becomes increasingly complex and critical.
This comprehensive review synthesizes current research in IoT security to provide researchers, practitioners, and students with essential insights into securing IoT networks. By examining the integration of software-defined networking (SDN) with various security mechanisms, readers will gain a thorough understanding of both fundamental concepts and advanced security solutions. Furthermore, this analysis offers critical perspectives on the practical implementation challenges and emerging opportunities in IoT security frameworks.
The security challenges in IoT environments are particularly demanding because of three key factors. First, IoT networks consist of many different types of devices with varying capabilities. Second, many IoT devices have limited computing power and memory, making it difficult to implement complex security measures. Third, these networks must be able to grow and adapt while maintaining security. Traditional security approaches, designed for regular computer networks, often prove inadequate for these unique challenges [1,2].
To address these security concerns, researchers have turned to a promising technology called software-defined networking (SDN). SDN represents a fundamental shift in how networks are managed by separating the network’s control functions (control plane) from its data transmission functions (data plane). This separation allows for centralized network management and better visibility into network activities. More importantly, it enables quick detection of security threats and automated responses to these threats. SDN provides a flexible platform where various security measures can be implemented and adjusted as needed, making it particularly valuable for IoT security [3,4].
As cyber threats become more sophisticated, protecting IoT networks requires both preventive and defensive security measures. Preventive measures include authentication (verifying device identity), encryption (protecting data), and access control (managing who can access what). Defensive measures focus on detecting and stopping threats using intrusion detection and prevention systems (IDPS). These systems increasingly rely on advanced computational approaches called machine learning (ML) and deep learning (DL), which can automatically learn to identify suspicious activities by analyzing large amounts of data.
The combination of ML/DL with SDN creates a powerful approach to IoT security. While SDN provides comprehensive control over the network, ML/DL algorithms can process network data to identify threats more effectively than traditional methods. This integration helps overcome several limitations of conventional security approaches by enabling dynamic responses to threats, efficient security management, and improved threat detection accuracy [5,6].
However, the effectiveness of ML/DL-based security solutions heavily depends on the quality and relevance of the data used to train them. These training datasets must accurately represent real-world scenarios and current cyber threats [6]. As we discuss later in Section 9, current IoT security datasets face significant challenges that need to be addressed to improve the reliability of security systems.
This systematic analysis, conducted in accordance with the PRISMA guidelines [7], aims to elucidate the current state of SDN-enabled IoT security frameworks, examine the integration of diverse security mechanisms—including ML/DL techniques, encryption methods, authentication protocols, and access control systems—and provide insights into extant implementation challenges and emerging solutions. This comprehensive understanding is essential for the development of more efficacious security solutions and the advancement of the IoT security domain.
This analysis aims to assist researchers in developing more robust and intelligent security frameworks that utilize SDN’s capabilities to enhance various security mechanisms, thereby improving the accuracy and effectiveness of IoT security systems.
1.1. Objectives
This comprehensive systematic review addresses critical gaps in understanding IoT security frameworks and their implementation. The following objectives guide the research:
- RO 3: To critically examine existing IoT security datasets and categorize them based on the application, usage, testbed developed and features in Section 9.
- RO 4: To present key takeaways from the review and future research directions in IoT security in Section 10 and Section 11.
1.2. Comparison of Existing Survey Papers
Integrating emerging technologies such as software-defined networking (SDN) and Network Function Virtualization (NFV) with cloud, fog, and edge frameworks presents a promising platform to address the complex security challenges in the IoT domain. During our systematic literature search, we observed that most available survey papers tend to focus on specific aspects of IoT applications rather than providing a holistic view of SDN-enabled IoT security. While numerous studies examine isolated components of IoT security or SDN implementations, there is a notable scarcity of comprehensive reviews that integrate security frameworks, computing paradigms, and dataset considerations across these domains. This gap motivated our selection of the survey papers reviewed below, which, while individually valuable, collectively reveal the need for a more unified analytical framework spanning these interconnected technologies.
At the forefront of this research landscape, the intersection of SDN and IoT-Fog security paradigms [8] provides valuable insights into SDN-enabled secure IoT frameworks and access control techniques, laying a foundation for understanding the architectural implications of SDN in IoT security. Nevertheless, the survey falls short in addressing the critical aspects of machine learning and deep learning integration and analysis of IoT-specific datasets, a crucial aspect for developing robust security solutions.
Building upon this architectural perspective, ref. [5] delves into the realm of deep learning methodologies for cyber threat detection in IoT networks coupled with IoT security datasets, contributing significantly to the evolving landscape of IoT security. However, this survey lacks a comprehensive examination of edge, fog, and cloud collaborative models, an essential aspect for understanding the holistic security architecture in IoT environments.
Addressing the complexity of IoT ecosystems, a holistic approach to security is provided by [9] by comprehensive overview of access control mechanisms across various distributed systems. While exploring edge, fog, and cloud collaborative models alongside SDN-enabled frameworks, the survey lacks in covering encryption and authentication techniques, which are fundamental to securing IoT communications.
In parallel, the dynamic nature of IoT security threats has spurred research into contemporary security trends [10] presenting and encompassing edge, fog, and cloud collaborative models, SDN-enabled secure IoT frameworks, and encryption and authentication techniques, thereby providing a panoramic view of the current IoT security landscape. However, the survey lacks an in-depth analysis of machine learning and deep learning approaches, which are crucial for adaptive threat detection and mitigation.
Discussing the architectural considerations in IoT security, the authors in [11] conduct a systematic analysis of SDN and NFV architectures, focusing on edge, fog, and cloud collaborative models and SDN-enabled secure IoT frameworks, highlighting the potential of these technologies in enhancing IoT environments. However, the work does not sufficiently address the challenges associated with IoT datasets and risk assessment methodologies, which is required for validating and improving security solutions.
The work presented in [12] offers only a superficial examination of SDN and fog computing in IoT security, lacking substantive evaluation of machine learning integration, authentication mechanisms, and access control techniques. Additionally, it offers limited critical assessment of security datasets and emerging threat vectors, particularly those targeting application layers, which significantly limits its utility for researchers developing comprehensive security frameworks.
In response to evolving IoT security challenges, ref. [13] investigates Software-defined Fog computing paradigm, which integrates software-defined networking with fog computing to optimize network topology management while addressing latency and energy consumption issues. While the paper provides a comprehensive analysis of security vulnerabilities in network topology and proposes a promising proxy re-signcryption scheme, it offers limited discussion on advanced threat detection mechanisms that could complement the architectural improvements.
Building upon architectures in IoT security, the authors in [6] examine the integration of ML/DL approaches for intrusion detection systems, providing extensive analysis of datasets and threat detection methodologies. While the survey makes significant contributions to understanding ML/DL applications in IoT security and dataset analysis, it demonstrates limitations in addressing critical infrastructural aspects including SDN-enabled security architectures, authentication mechanisms, and cloud–edge–fog collaborative models.
In addition to intelligent threat detection, the role of data in IoT security research [14] is addressed by examining publicly available IoT datasets utilized in network security research, which contributes to the growing body of knowledge on data-driven approaches to IoT security, facilitating future research endeavors. However, the survey lacks a comprehensive analysis of access control techniques and encryption methods, a crucial element for IoT device protection.
Table 1 shows a comparison of the survey papers.

Table 1.
Review of survey papers.
1.3. Motivations and Contributions
This survey provides a comprehensive analysis that distinguishes itself from existing reviews through its targeted focus on collaborative paradigms across edge, fog, and cloud environments, particularly on SDN-enabled IoT security frameworks, machine learning applications, and authentication mechanisms. Our methodology thoroughly examines access control methodologies, IoT-specific datasets, and cryptographic implementations, offering unprecedented depth in analyzing the IoT security landscape. Through this integrative approach, we facilitate a sophisticated understanding of the interconnected security dimensions within the IoT ecosystem.
The manuscript’s structure follows a logical progression, beginning with an examination of SDN’s pivotal role in IoT security architectures in Section 2, establishing fundamental IoT and SDN concepts. Section 3 delineates our methodological framework, presenting precise inclusion and exclusion criteria for literature selection. Following this methodological groundwork, Section 4 advances into an analytical discussion of IoT frameworks, scrutinizing the security capabilities inherent in cloud, edge, and fog computing paradigms. Building upon these architectural insights, Section 5 evaluates SDN-enabled IoT security frameworks, while Section 6 and Section 7 analyse cryptographic mechanisms, authentication protocols, and access control techniques optimized for IoT environments.
The technical core of our analysis unfolds in Section 8 and Section 9, which are intrinsically linked. Section 8 examines machine learning and deep learning applications in intrusion and threat detection, while Section 9 supports these findings through a comprehensive review of relevant datasets employed in these computational approaches. Drawing together these multiple threads, the survey culminates in Section 10 with synthesized insights and prospective research trajectories through Section 11. Lastly, the conclusion for the paper is presented in Section 12, summarizing our key findings and their implications for advancing IoT security.
2. IoT and SDN Systems
This section explains the importance of SDN in security and collaborative frameworks on edge, fog and cloud.
2.1. Advantages of Using SDN
Software-defined networking (SDN) offers significant advantages that enhance IoT frameworks. By decoupling the control plane from the data plane, SDN provides centralized network control, thereby simplifying management and optimizing service provision. This separation increases network flexibility and programmability, allowing for dynamic adjustments to meet evolving demands. Furthermore, SDN reduces both operational and capital expenditures using open-source software and hardware, which facilitates the integration of third-party applications. Moreover, enhanced network security is achieved through improved threat detection and response mechanisms, enabled by increased network visibility. Additionally, SDN promotes energy efficiency by optimizing resource utilization, thus mitigating the environmental impact of network operations. Collectively, these benefits render SDN essential for advancing contemporary networking and fostering efficiency, security, and innovation [3,4].
2.2. How SDN Enhances IoT Security?
Software-defined networking significantly enhances the security of IoT systems by providing centralized control, dynamic traffic management, dynamic policy enforcement, comprehensive network visibility, and traffic isolation. The centralized visibility enables real-time monitoring and anomaly detection, allowing timely threat response. Dynamic traffic management and policy enforcement support granular security measures, addressing IoT security requirements. Traffic isolation helps prevent attacks spread across network domains through predefined rules. These features collectively bolster the robustness of IoT systems, ensuring energy-efficient management, resource utilization, and high-security standards [4,15].
2.3. Cloud and Edge Model for IoT Security
Edge computing and cloud computing have become crucial to IoT security. The cloud provides computational and storage capabilities, enabling advanced resource-intensive security measures like machine learning approaches. Moreover, centralizing data in the cloud facilitates comprehensive monitoring and analytics, which is crucial for identifying and mitigating security threats across IoT networks and devices [16].
By contrast, edge computing reduces latency and increases real-time data processing capabilities, enabling faster detection and response to security incidents. The edge layer can handle lightweight operations, such as authentication, localized data processing, access control, and network segmentation, which is crucial for maintaining privacy and reducing data breach risk [15].
Cloud and edge computing offers a synergistic approach to IoT security. The cloud provides security management and extensive data analysis capabilities like deep learning for anomaly detection, while the edge offers localized, real-time security enforcement and quick response mechanisms. This collaborative effort ensures a more resilient and efficient security framework for IoT systems. This dual-layered security architecture enhances IoT security robustness with consideration of scalability and adaptability to the evolving landscape in IoT [16,17,18].
2.4. Limitations of SDN
To construct effective security models, various toolsets and functionalities are required, and SDN aids in integrating, coordinating, and managing security functions. This underscores the significance of viewing SDN as a facilitator that enhances the implementation and coordination of security functions, rather than a direct provider of security mechanisms. Therefore, the effectiveness of SDN-based security solutions is largely contingent upon the proper implementation and integration of external security mechanisms such as authentication, encryption, and threat detection.
3. Research Selection Criteria
This systematic literature review adhered to the Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) guidelines to identify and select relevant research papers [7,13].
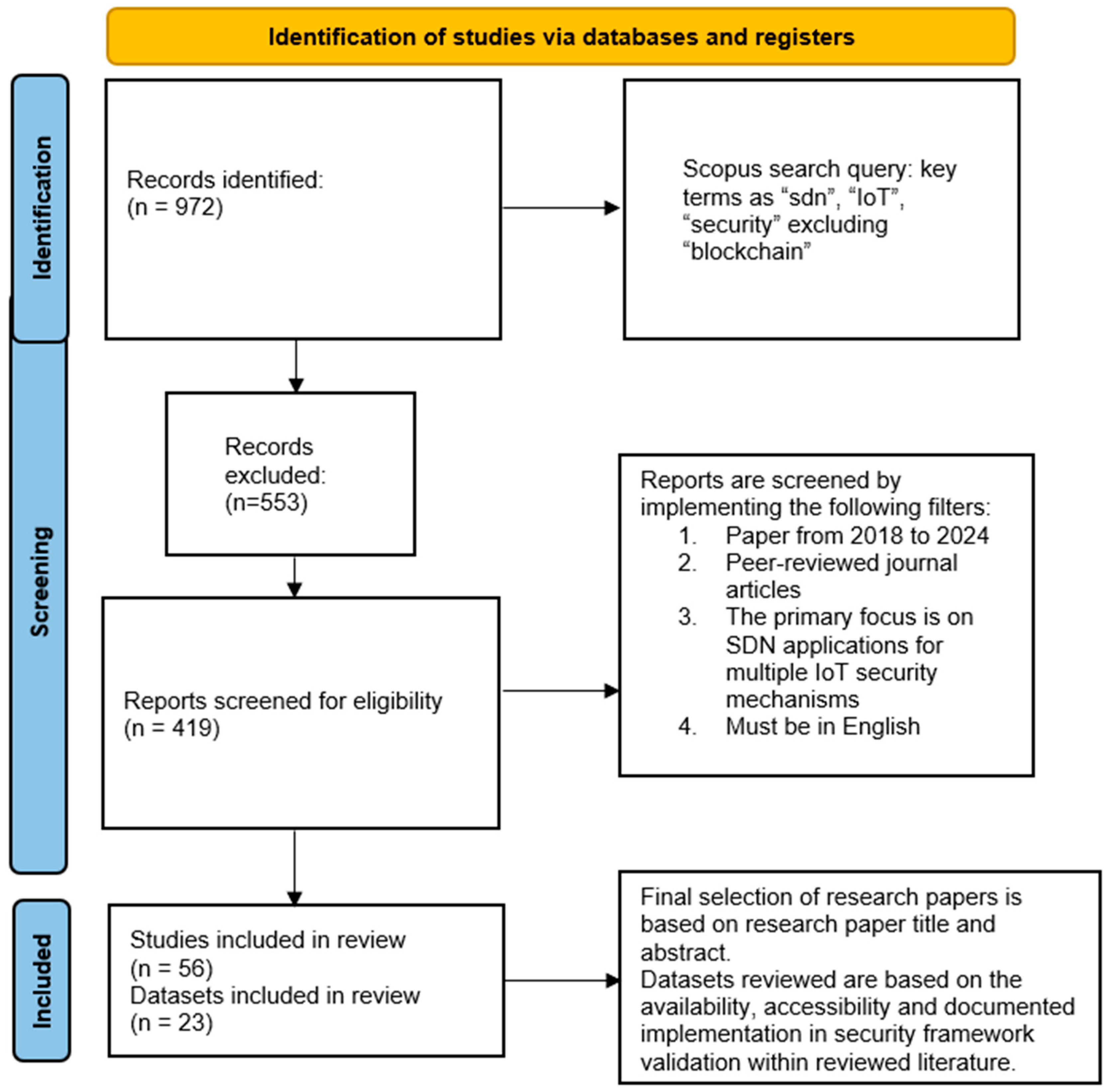
The PRISMA search approach is presented in Figure 1.
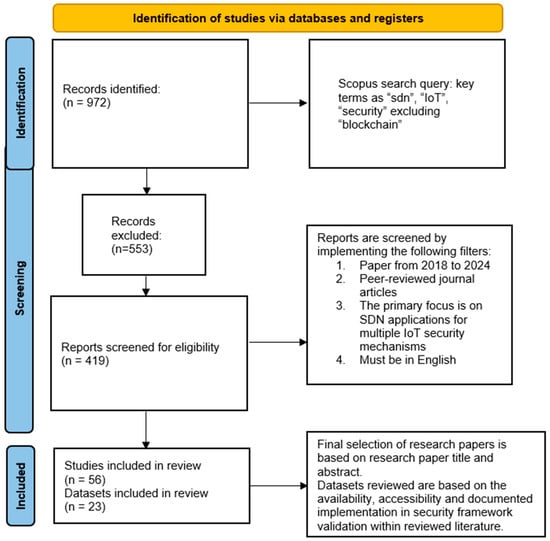
Figure 1.
PRISMA searching strategy for paper selection.
3.1. Search Strategy
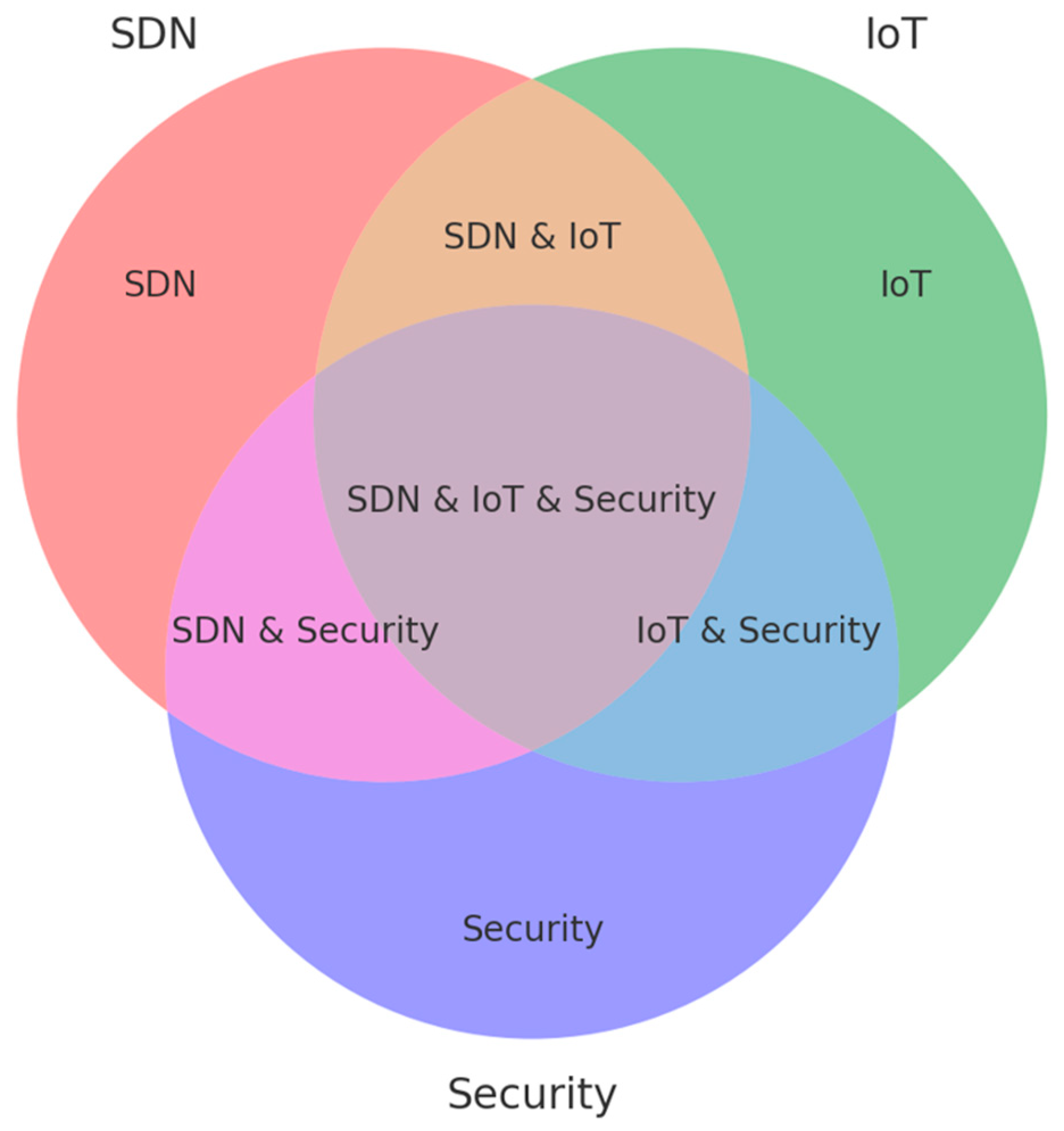
The literature search employed the Scopus database for its comprehensive academic coverage. A Boolean query (“SDN” AND “IoT” AND “security” NOT “Blockchain”) was strategically constructed to identify articles examining the intersection of software-defined networking and IoT security frameworks while excluding blockchain-focused research, which yields 972 papers for review. This approach ensured targeted retrieval of publications addressing the core research questions raised in research objectives 1 and 2 while maintaining domain specificity, as visually represented in Figure 1, where the central area in the Venn diagram in Figure 2 represents the precise scope of investigation.
Figure 2.
Venn Diagram for the search query for research objectives 1 and 2.
For research objectives 3 and 4, we employed a complementary methodological approach. Rather than utilizing additional search terms, we extracted datasets referenced in the literature identified for objectives 1 and 2. Furthermore, the dataset was selected considering the dataset’s availability for public access, incorporates IoT devices in their testbeds and includes both normal and malicious traffic. This approach facilitated a thorough examination of IoT security datasets while maintaining continuity with our primary research focus. Similarly, the synthesis of key takeaways and future research directions (Research Objective 4) emerged naturally from our comprehensive analysis of both the reviewed frameworks and their associated datasets.
The reason for the exclusion of blockchain and research paper focused on specific applications are presented in Section 3.3.
3.2. Inclusion Criteria
From the available 972 papers, search filters were implemented to further screen the papers to 419 papers, excluding 553 paper. The search filters are provided below:
- Publication Type: Peer-reviewed journal articles
- Time Frame: Published between 2018 and 2024
- Language: English
- Focus: Primary emphasis on SDN applications in improving IoT security
Following a systematic screening process, the research findings have been methodically organized across Section 4, Section 5, Section 6, Section 7 and Section 8 presenting a comprehensive analysis of the literature. The dataset selection methodology prioritized three key criteria: public availability, research accessibility, and comprehensive documentation of testbed configurations.
The organization of content across multiple sections facilitates a logical progression of concepts, which would help researchers to perform detailed examination of distinct aspects within the research domain, thereby allowing for a thorough investigation of individual components.
3.3. Exclusion Criteria
The systematic review implemented specific exclusion criteria to refine the literature corpus. Based on the authors’ assessment of implementation challenges, blockchain-centric studies were excluded as blockchain implementations present significant scalability challenges within heterogeneous IoT environments with resource-constrained devices, limiting their practical feasibility in real-world IoT deployments. Furthermore, drawing from analysis of cross-domain applicability requirements, environment-specific research focusing on security techniques tailored for IoT contexts was omitted to prioritize generalizable security approaches capable of implementation across multiple IoT ecosystems, thus enhancing the broader utility and transferability of the review findings.
4. Discussion of Frameworks Used in IoT
After applying the systematic selection criteria outlined in Section 3, this review identified several significant frameworks and architectural approaches that address the complex security challenges in IoT environments. These frameworks demonstrate varying approaches to integrating SDN capabilities with IoT security requirements, ranging from cooperative security models to simulation frameworks and cloud-fog-edge collaborative architectures.
A cooperative security model for early-stage cyber-attack detection is proposed in the paper [19], where threats are detected by IoT devices and efficiently communicated to other devices via an SDN controller, improving the response time by 37%. In this model, the function of detection agents looking for anomalies is performed by IoT devices, by which system logs and traffic patterns are monitored for signs of intrusion. Clarity about the detection model and its computational resource evaluation for IoT devices is lacking in the paper.
A simulation framework called IoTSim-Osmosis is proposed in the paper [20], by which osmotic computing and SD-WAN are utilized to address the issues related to complexity and heterogeneity of Integrated IoT, edge and cloud environments with a flexible simulation framework, with the capability of managing diverse IoT applications through policy-driven task scheduling, resource allocation, and network routing. An empirical validation is performed upon simulation of smart city for electricity management and billing systems and measuring effectiveness of key performance indicators like battery consumption, execution time and energy usage. A significant contribution is added by the solution for simulation frameworks to reflect real-world IoT applications that employ cloud-edge collaborative frameworks accurately.
A comprehensive overview of the integration of Cloud Computing (CC), Fog Computing (FC), and Internet of Things (IoT) technologies is provided in the paper [16,21], discussing limitations of traditional cloud architectures and proposes FC as a solution to extend cloud services to the network edge, providing advantages in latency reduction and mobility support. The primary contribution of research lies in its analysis of collaborative integration of CC-FC-IoT architecture, including the challenges such as authentication and scalability. While a valuable resource for understanding this technological landscape is presented by the paper, it could benefit by more empirical data to substantiate its claims.
5. SDN-Enabled IoT Security Frameworks
This review categorizes software-defined networking (SDN) frameworks for IoT security research into four domains: firstly, Policy-Driven Orchestration Frameworks, which automate security management; secondly, Multi-Layer Threat Mitigation Architectures, integrating defenses across the infrastructure; thirdly, Anomaly Detection and Security Fusion Approaches, leveraging analytics for threat identification; and lastly, NFV-Enhanced Solutions, exploiting virtualized security functions. These categories collectively elucidate the response to emerging challenges in dynamic, software-controlled networks, offering a comprehensive perspective on contemporary SDN security paradigms.
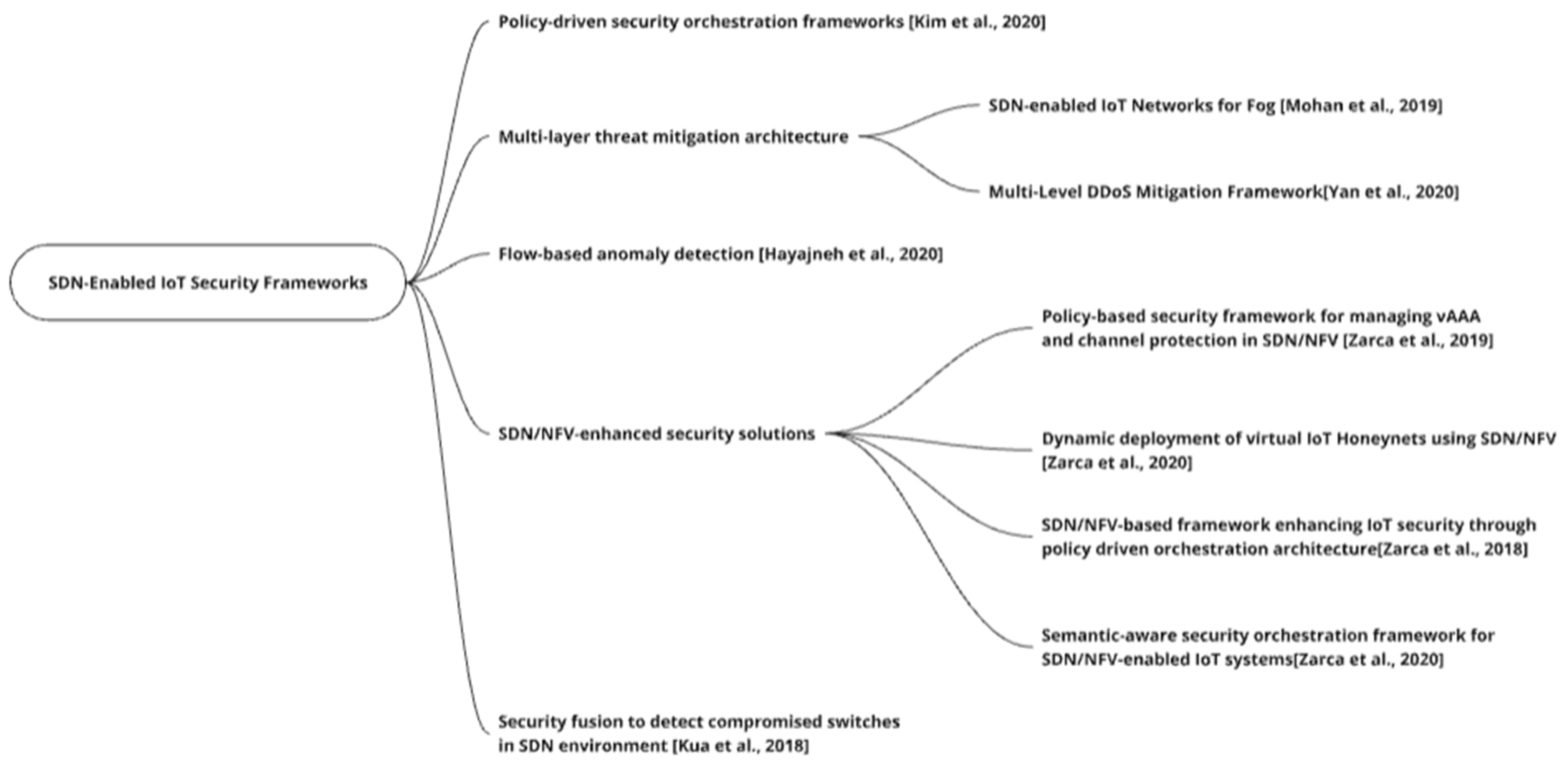
A mind map for SDN-enabled IoT security frameworks is represented in Figure 3.
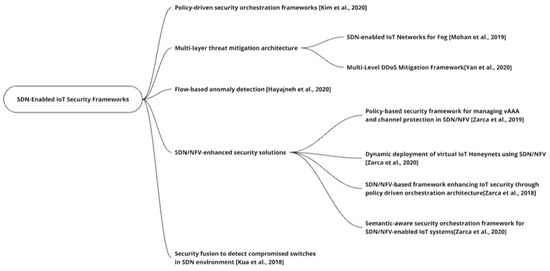
Figure 3.
SDN-enabled IoT security frameworks [22,23,24,25,26,27,28,29].
5.1. Policy-Driven Security Orchestration Frameworks
The growing complexity of network security in Industry 4.0 environments is addressed by the implementation of a virtualized security system [22], built on Interface to network security function (I2NSF) framework and NFV, giving capability to translate high-level user intents to low-level security policies. Standardized interfaces—registration, consumer-facing, and NSF-facing—are integrated in the approach, by which the Event-Condition-Action policy model and YANG data modeling are utilized. The proposed framework is validated by implementing access control for social networking services (SNS) with NSFs such as time-based firewalls and URL filters. Despite the framework’s benefits, the paper lacks extensive real-world validations with different security scenarios and performance evaluations.
5.2. SDN/NFV-Enhanced Security Solutions
A novel policy-based security framework for managing Authentication, Authorization, Accounting (AAA), and channel protection in SDN/NFV enabled IoT networks is introduced in the paper [23]. Virtual AAA components are utilized, and virtual network authenticators are implemented as Virtual Network Functions (VNFs) to facilitate scalable device bootstrapping, access control, and dynamic key distribution. The solution was evaluated on smart building testbed, yielding policy execution in milliseconds and IoT operations completion within 1–8 s. Scalability testing was conducted with up to 500 simulated devices, although large-scale real-world deployments remain to be assessed.
A framework for the dynamic deployment of virtual IoT honeynets using SDN/NFV technologies to counter cyberattacks [24], incorporating a security orchestration plane for policy refinement and a virtualized enforcement plane for honeynet deployment. The framework was validated through simulations of two smart building scenarios with diverse IoT devices. Results yield honeynet deployment times of 60 s for 20 devices and 4 min for 50 devices, outperforming existing solutions. Future research directions could explore integration with 5G networks and scalability for industrial IoT applications.
An SDN/NFV-based framework is proposed for enhancing IoT security through policy-driven orchestration architecture in [25], consisting of user, orchestration, and enforcement planes, utilizing a multi-tiered policy refinement process to convert high-level security policies into low-level configurations for heterogeneous IoT environments. VSFs are dynamically deployed, with firewall capabilities in implementation. Validation using OpenDaylight and ONOS controllers demonstrated superior policy enforcement compared to traditional NETCONF/iptables methods, with 1000 filtering policies deployed in under 30 s. However, the proposed model must be evaluated against advanced threats such as malware, unauthorized access and scalability across diverse IoT devices.
A semantic-aware security orchestration framework for SDN/NFV-enabled IoT systems in [26], employing policy-driven management and conflict detection mechanisms, integrating Security Orchestrator Engine, Policy Interpreter, and Conflict Detector, utilizing a Knowledge Base and rule-based reasoning to identify policy inconsistencies. Validation was conducted through simulations, testing conflict detection with up to 1000 concurrent policies and evaluating an optimization algorithm for VNF placement. Results demonstrated scalable conflict detection (1–3.5 s for complex scenarios) and improved cost-efficiency and latency when edge/cloud node density increased. The research, however, lacks real-world IoT deployment testing, presenting opportunities for future research.
5.3. Multi-Layer Threat Mitigation Architectures
A SDN-enabled Internet of Things (IoT) infrastructure for fog networks was presented in [27], addressing the challenges on DoS, DDoS and MITM, integrating SDN with fog computing and decentralizing network control on edge. The framework facilitates dynamic security policy management and threat response by eight modules: a policy editor tool, a policy interpreter module, a security enabler provider, a security orchestrator, a monitoring module, a reaction module, a control and management domain, and encryption flow rules. Raspberry Pi devices were utilized as fog nodes and SDN controllers in the implementation, whereby over 90% energy efficiency improvement was achieved. However, limitations were exhibited in the study, such as a lack of comparative evaluation against other security models and evaluation of model against application layer attacks.
A Multi-Level DDoS Mitigation Framework (MLDMF) is discussed for IIoT in [28], integrating SDN with edge, fog and cloud. The low-latency response of edge computing are employed for simpler security functions at edge gateway, contextual awareness of fog computing by Collect-Detect-Mitigate (CDM), Honeypot-Detect-React (HDR), and Cloud-Detect-Fog-Mitigate (CDFM) methods, and the computational power of cloud computing for data analytics employing DL and ML techniques were harnessed in the approach. Experimental validation was conducted in a Mininet-simulated environment to test framework’s efficacy against Ping of Death and TCP SYN flood attacks, yielding results of reduction of 37.03% in detection and mitigation of average time delay for TCP SYN flood attack upon comparison. The limitation includes the lack of focus on empirical validation against application-layer DDoS attacks, particularly the exploits with HTTP and HTTPS protocols.
5.4. Flow-Based Anomaly Detection
An SDN-enabled security framework was proposed in [29], incorporating anomaly detection with flow-based analysis to identify potential intrusions. The framework comprised an edge node, an SDN controller to segregate IoT traffic from normal traffic and forward to proxy device to perform deep packet inspection with HTTPS, thereby providing End-to-End security application. The framework’s effectiveness to mitigate attack was evaluated by employing multiple attack scenarios including fake hash, certificates and malwares. However, the model must be evaluated for flooding attacks such as DDoS at Network layer and at application layer with HTTP GET requests.
5.5. Security Fusion to Detect Compromised Switches in SDN Environment
A Security Fusion as a Service (SFaaS) [30] is proposed as a comprehensive approach to detect compromised switches in SDN environments by two-tiered approach: first implementing Sandwich Testing Mechanisms (STM) to detect single compromised switch attacks through forwarding and weighting detection algorithms and then introducing a novel Softwarized Switch Topology Measurement Architecture (SSTMA) to address more complex collusion attacks. Simulations demonstrated the effectiveness of SFaaS in detecting diverse attack models, including incorrect forwarding and DDoS, with damage reduction ratios ranging from 33% to 60%. The model provides security mechanisms focusing on SDN switches employed in IoT environment.
5.6. Critical Analysis
The reviewed frameworks demonstrate significant advancements in SDN/NFV-based security solutions for IoT environments, yet several critical limitations persist across implementations. While frameworks such as I2NSF [17] show promise in security service deployment, they require extensive real-world validation and enhanced scalability features. Integrating AAA services [23] and virtual honeynets [20] presents innovative approaches to security management, though large-scale deployment validation remains pending. Policy-driven architectures [25,26] demonstrate efficient policy enforcement and conflict detection but lack comprehensive resilience testing against advanced threats. Multi-layer approaches, including fog-based infrastructure [27] and MLDMF [28], show impressive energy efficiency and mitigation improvements yet require more robust comparative analysis and application-layer attack validation. Flow-based anomaly detection [25] needed broader attack scenarios where the model must be validated for flooding attacks. While the SFaaS [30] framework proposes security mechanisms for switches in SDN-IoT environments but lacks evaluation against unauthorized access to switches by spoofing.
Future research directions should address these limitations through comprehensive evaluation with real-world IoT devices, scalability evaluation with many IoT devices and traffic flow, and validation against diverse attack vectors, particularly in distributed IoT environments. The review of critical analysis is presented in Table 2.

Table 2.
Review of SDN-enabled IoT security frameworks.
6. Encryption and Authentication
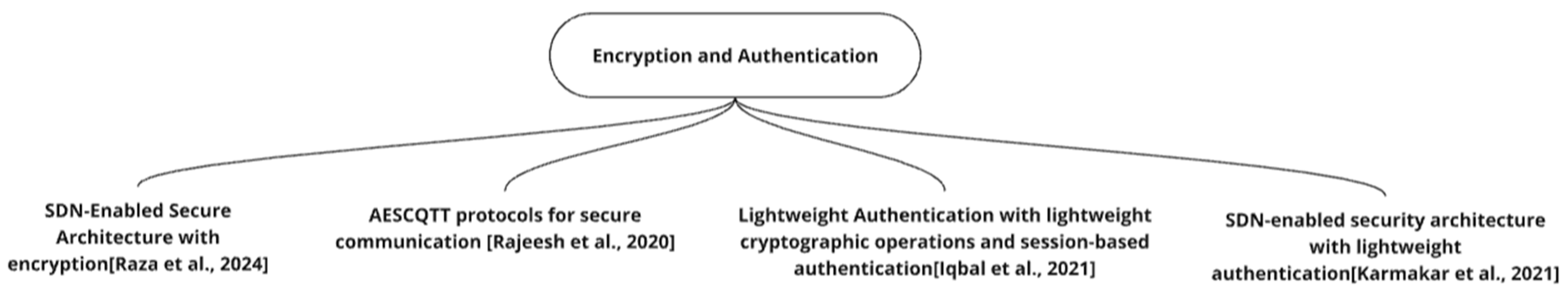
Recent advancements in Internet of Things (IoT) security have introduced novel methodologies to address vulnerabilities in interconnected devices. This paper examines four key studies [31,32,33,34] that propose innovative approaches to enhance authentication, encryption, and overall security architecture in IoT environments, analyzing their methodologies and critiquing their efficacy. The mind map in Figure 4 shows the list of research papers discussed in the section.
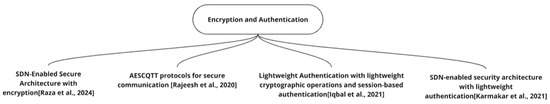
Figure 4.
Encryption and authentication [31,32,33,34].
A multi-faceted solution is proposed in [31], comprising several techniques for IoT security, including device classification based on security levels with ensemble stacking classification, dynamic key generation by the SDN controller and mutual authentication between IoT devices and the SDN controller with public key cryptography. The authentication includes secure exchange of session keys with AES encryption. The model’s validation is conducted through formal security analysis using the AVISPA tool. Performance evaluation measures running time, memory overhead, communication overhead, and energy consumption.
AESCQTT protocols for secure communication between IoT devices are proposed in [32], employing AES for encryption and TLS for secure transmission. Secure key exchange mechanisms between IoT devices and servers are ensured by the protocols through mutual authentication with secure communication channels with capability of retransmission when packet loss or message loss is encountered. Performance evaluation compares CoAP, MQTT and DDS protocols for energy consumption, packet delivery ratio, security and end-to-end delay.
A lightweight authentication mechanism with lightweight cryptographic operations and session-based authentication is proposed in [33] to ensure both security and efficiency. The authentication scheme consists of user and smart devices registration process followed by continuous authentication of user and device with controller. Encryption, session keys, sequence number and timestamp are employed by the scheme to create session ID for communication, thus ensuring mutual authentication, anonymity, resistance to replay attacks and lightweight cryptography. Formal security analysis is conducted by employing BAN logic, while informal security analysis is performed by theoretical reasoning against common attacks. Performance evaluation is carried out by comparison of computational cost and execution time with PrivHome, Grope’s protocol and LAM-CIoT model, achieving superior results. Furthermore, future work is required to validate the model under flooding attacks such as DDoS and high volumetric traffic, consuming CPU resources every time the traffic is encrypted and authenticated.
An SDN-enabled security architecture for IoT integrating lightweight Elliptic Curve Cryptography (ECC) authentication with OAuth-based authorization, with fine-grained policy enforcement mechanisms is proposed in [34], advancing over SDN-IoT security frameworks focusing on flow management and device identification. Empirical validation leveraging a simulated IoT environment with ONOS and Mininet-WiFi is conducted to demonstrate the architecture’s efficacy in mitigating threats such as Mirai-based DDoS and ARP spoofing and measuring performance metrics such as throughput, CPU and memory usage, device power consumption and average path setup. While valuable insights are offered, validation of the model with real-world IoT devices is needed.
Critical Analysis
The reviewed studies present significant advancements in IoT security architectures, demonstrating a clear progression from conventional approaches to more sophisticated, multi-layered security frameworks. While [31,32] leverage SDN capabilities for enhanced security management, with the latter uniquely incorporating ECC and OAuth, studies [33] and [34] focus on protocol-level improvements and lightweight authentication mechanisms, respectively. A critical analysis reveals that these approaches demonstrate promising results in controlled environments. Notably, the scalability of these solutions under real-world conditions, particularly in heterogeneous IoT environments with varying computational capabilities, remains inadequately addressed. Furthermore, the models developed must be evaluated under scenarios where multiple devices are interconnected and flooded with high-volume traffic, thereby testing the capability of the encryption and authentication techniques. This would categorize how effectively the security models can fit to support IoT applications.
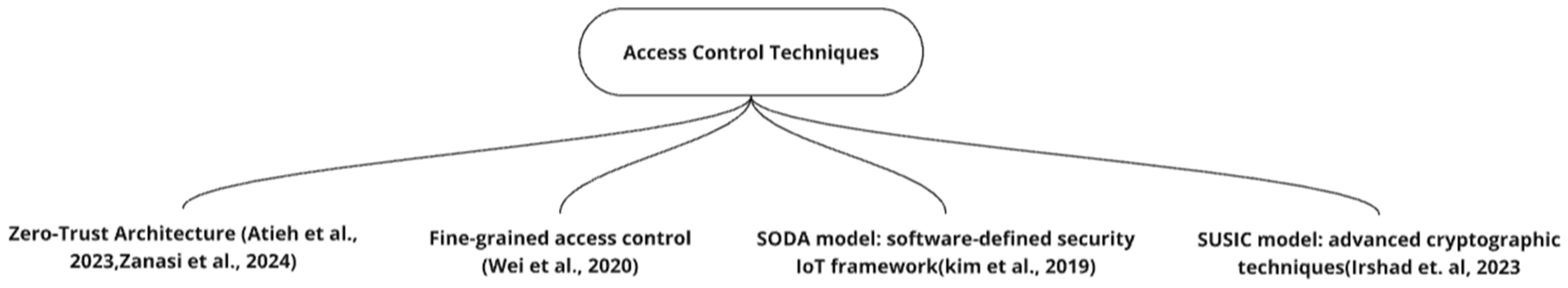
7. Access Control Techniques
This review examines modern approaches to access control and security frameworks that propose solutions that integrate software-defined networking and zero-trust architecture. These frameworks address critical security concerns through fine-grained access control, continuous authentication, and dynamic network segmentation. Our analysis evaluates these proposed systems’ methodologies and implementation strategies.
A mind map for the research papers in access control techniques is shown in Figure 5.
Figure 5.
Access control techniques [35,36,37,38].
A framework integrating zero-trust architecture with SDN to enforce strict access control and dynamic network segmentation through continuous authentication and authorization of devices and requests is proposed in [35]. Performance evaluation is conducted by simulating a testbed for an industrial IoT environment and measuring latency for the model. However, architecture’s scalability is questioned when a flood of application layer requests requiring deep packet inspection is evaluated, thereby overloading computation for IoT devices.
A 2-layered model integrating industrial gateways and trusted execution environments (TEEs) for protection at both network and edge levels is proposed in [36]. The framework consists of SDN with TEEs for fine-grained access control, where remote maintainer credentials are verified via policy enforcement points and policy administrators, ensuring compliance. The framework is empirically validated on an IIoT testbed consisting of industrial controllers and an Open Floodlight SDN controller. However, the scalability of the controller in managing authentication request surges, a critical consideration for robust implementation, is not addressed in the research.
A solution for fine-grained access control is proposed in [37] by implementing a token-based system that encapsulates key parameters such as subject identity, request actions, time and location, allowing real-time verification of access requests. The solution is validated with physical and virtual IoT devices, but quantitative analysis is lacking. Despite promising results, further investigation into its scalability across multiple heterogeneous IoT devices is needed, presenting challenges for widespread adoption and implementation.
A SUSIC model Is proposed [38] that employs advanced cryptographic techniques such as Elliptic Curve Cryptography (ECC), three-factor authentication (ID, password, biometric data), and a fuzzy extractor for biometric verification. The model consists of multi-phase processes, including system initialization, user registration, login and mutual authentication, providing mutual authentication process between user, SDN controller and IoT devices, thereby enforcing strict access control for IioT resources. To validate the model, formal security analysis is performed employing the RoR model. Performance evaluation shows the model to provide a better trade-off between security and efficiency, making it suitable for deployment. Despite the benefits of the model, complexities are added in implementation due to continuous verifications. Furthermore, the resilience of the model under scenarios where flooding of requests occurs needs to be explored in future research.
SODA, a software-defined security framework for IoT environments enabling device-side dynamic access control and deployment of security services, is presented in [39], leveraging for centralized policy management and offloading security service. Key components include a policy manager for conflict detection/resolution, a session manager for authentication, and an NFV manager for resource allocation. Framework validation is performed on real-world IoT devices with diverse attack scenarios, such as botnet propagation and unauthorized access. The results demonstrated SODA’s ability to mitigate attacks, with 34.4% lower latency compared to existing solutions. The framework’s scalability is constrained for distributed architectures with heterogeneous IoT nodes due to the substantial computational overhead from mandatory encryption and authentication, leading to increased latency. Future research should explore replicability with diverse IoT devices.
Critical Analysis of Papers
Upon analyzing the diverse methodologies presented in contemporary IoT security frameworks [35,36,37,38,39], several critical patterns and limitations emerge in the research landscape. While zero-trust architectures integrated with SDN demonstrate promise in enforcing granular access control [35], they face computational bottlenecks during high-volume application layer inspection, particularly over-utilizing resource-constrained IoT endpoints. Integrating TEEs with industrial gateways [36] presents a robust approach for dual-layer protection, though the scalability of authentication management remains inadequately addressed since multiple authentication requests are needed to allow single users, which can affect the useability of the IoT applications. Token-based systems incorporating contextual parameters [37] offer dynamic verification capabilities, but their efficacy across heterogeneous IoT ecosystems requires further empirical validation. The SUSIC model’s implementation of ECC and three-factor authentication with biometric verification via fuzzy extractors [38] demonstrates enhanced security-efficiency equilibrium, albeit with increased computational overhead during continuous verification processes for accessing and working with IoT traffic. SODA’s software-defined security framework [39], while achieving notable latency improvements through centralized policy management and security service offloading, exhibits limitations in distributed environment scenarios. A common thread across these methodologies reveals a critical research gap in addressing scalability under authentication request surges that requires packet inspection, the ability to manage multiple users and its authentication cycles and the need for a more comprehensive quantitative analysis of performance metrics in large-scale IoT deployments. The review of critical analysis is presented in Table 3.

Table 3.
A review of critical analysis on access control solutions.
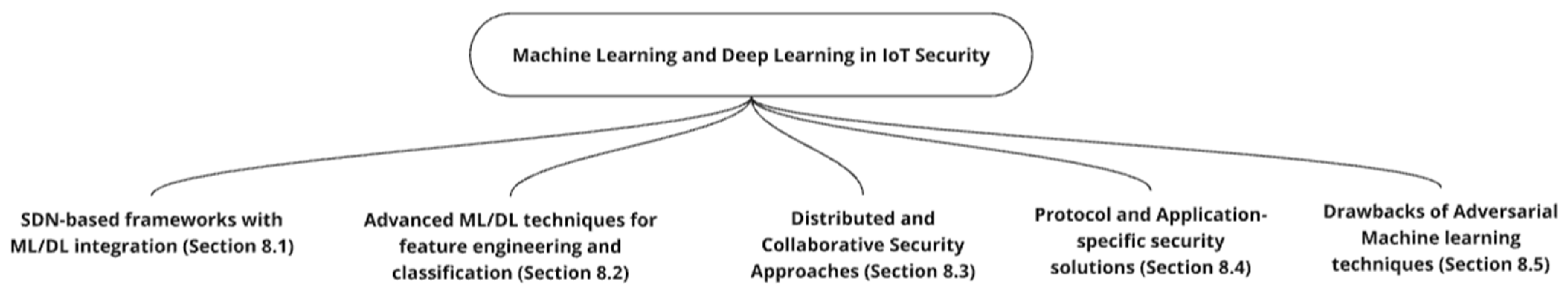
8. Machine Learning and Deep Learning in IoT Security
In response to evolving security threats, intrusion detection and prevention systems have emerged as integral components of comprehensive security frameworks. These systems predominantly leverage Machine Learning (ML) and Deep Learning (DL) techniques, trained on diverse datasets encompassing multiple attack vectors. While software-defined networking (SDN) enhances security framework efficacy through improved network control and visibility, identifying and mitigating threats fundamentally relies on sophisticated intrusion detection mechanisms.
This section reviews recent advancements in IoT security by integrating SDN and ML/DL. The reviewed works are categorized by methodologies and architectures, including SDN-based frameworks with ML/DL integration, Advanced ML/DL techniques for feature engineering and classification, distributed and collaborative security approaches, and protocol and application-specific solutions. A review of papers discussing the limitations of ML techniques is presented. Finally, we present the critical analysis summary for the reviewed research models.
A mind map presenting the categorization of the reviewed research papers is shown in Figure 6.
Figure 6.
ML/DL techniques in IoT security.
8.1. SDN-Based Frameworks with ML/DL Integration
This section discusses several innovative frameworks that harness this synergy to address multifaceted security challenges by leveraging SDN’s programmability and traffic manageability and ML/DL’s intelligence to create effective and resilient security solutions.
A two-phase automated security architecture for IoT environments is presented in [40], consisting of a security engine with an AI-driven sub-layer for feature selection and classification and a configuration engine that facilitates dynamic rule optimization and management without disrupting network operations. Data are captured and transmitted by IoT devices at the sensing layer to the controller layer, where the BAT Algorithm and Random Forest are employed for feature selection and classification, respectively, and integrated with Intrusion detection systems (IDS) and SIEM tools. Feature selection is refined, and detection accuracy is improved by a continuous feedback mechanism, thereby minimizing false positives. However, further validation of this framework for real-world IoT deployments is needed to assess its practical efficacy fully.
SNORT IDS, RYU SDN controller, and lightweight machine learning algorithms (decision trees, logistic regression, support vector machines, and K-nearest neighbors) are integrated in the model proposed in [41] to detect and mitigate DdoS attacks. The trained machine learning model is deployed on an SDN controller that is responsible for supervising traffic between IoT devices. The trained machine learning models detect and mitigate IoT devices while SNORT IDS protects SDN controller from intrusions. Performance validation uses datasets from UNSW-NB15, CICDDoS2019, and IoT testbeds to calculate accuracy, precision, F1-score, and ROC curve. However, the model employs the datasets that lack modern-day attacks that include malware propagation, thereby leaving SDN controllers vulnerable to such attacks.
An IoT-KEEPER model is proposed in [42], implemented on SDN controllers at the network edge facilitating traffic management, security policy enforcement, and anomaly detection using unsupervised machine learning. Data from network traffic is clustered into groups by Fuzzy C-means, and traffic is classified as benign or malicious by fuzzy interpolation. Communication is restricted or the device is isolated through security policies stored in a policy cache upon detection of malicious activity by the enforcement module. The trained model is shared across deployments to enhance scalability. A 99% accuracy, 0.02 false positive rate, and 0.98 true positive rate are achieved in the performance evaluation. However, further analysis is needed to address application-layer attacks, particularly HTTPS based flooding attacks and malware propagation.
SDN controllers and machine learning algorithms are employed in [43] to improvise and simplify security mechanisms by making the system more explainable. A decision tree is generated from a random forest classifier, allowing users to gain insights about features responsible for the classification of traffic into normal or malicious behavior. Although the model is validated using an SDN-specific dataset, details regarding the dataset, including the attacks performed and the testbed, are not provided, leaving the model untested against real-world attacks and IoT devices.
A critical gap In IoT security is addressed in [44] by proposing SDIoT-DdoS-DA, a novel SDN-based framework for DdoS attack detection in resource-constrained IoT environments. Micro-Cluster Outlier Detection (MCOD) for real-time anomaly detection is integrated with a pre-trained Multilayer Perceptron (MLP) for traffic classification, both centralized at the SDN controller to alleviate the computational burden on IoT devices. Using Trinoo-generated DdoS traffic, 99.74% precision and 96.43% recall were achieved in the evaluation, outperforming existing methods like NTP-based detection mechanism and multi-objective particle filter approach for internal and external threat detection. Despite the detection efficacy and resource optimization, a detailed exploration of specific DdoS attack types and insights into scalability for the model is lacking, leaving it for future research.
A hierarchical, SDN-based intrusion detection framework for cloud IoT environments is proposed in [45], integrating Edge, Fog, and Cloud IDS layers with SDN and NFV technologies to improve resource allocation. Machine learning techniques are employed, from lightweight SVM at the Edge to sophisticated deep learning at the Cloud level, facilitating rapid local threat detection. Promising results were yielded in the empirical evaluation using CAIDAm KDD Cup 1999 and UNSW-NB15 datasets: 95.5% accuracy, 7 ms average attack response time, and 9.5–15% communication overhead. Despite these advancements, the framework’s efficacy against modern attacks such as DdoS and application layer vulnerabilities from malwares remains uncertain, highlighting avenues for future research with contemporary threat data.
An SDN-enabled proactive defense mechanism for Fog-of-Things (FoT) critical infrastructure is proposed in [46], leveraging a hybrid deep learning model called Cu-DNNGRU and implementing it in SDN-enabled Fog layers for IoT devices. The CSE-CIC-IDS2018 dataset is utilized for training and testing the model, achieving an overall accuracy of 99.81%, precision of 99.96%, and recall of 99.79%. Although the model demonstrates superior performance compared to Cu-DNN and Cu-LSTM benchmarks. However, a validation for resource efficacy is needed for the model.
A TD-RA based framework for SDN-based IoT environments is presented in [47], integrating threat detection and mitigation capabilities in the architecture with three key modules: Binary Classification (BCM) for initial threat detection, multi-class classification (MCM) for attack classification employing decision trees and random forest, and Policy Enforcement (PEM) for attack mitigation, implemented across two SDN controllers. An accuracy of 99.7% in binary classification and 91.1% in multi-class classification and CPU utilization below 30% is demonstrated by the framework utilizing the IoTID20 dataset. However, further validation against large-scale networks to test scalability.
8.2. Advanced ML/DL Techniques for Feature Engineering and Classification
This group examines machine learning and deep learning approaches that primarily focus on sophisticated feature engineering and classification techniques, aiming to enhance the accuracy and efficiency of threat detection in IoT environments by leveraging advanced algorithms for data preprocessing, feature selection, and classification.
An IDS leveraging Convolutional Neural Networks (CNNs) and enhanced Transient Search Optimization (TSODE) is proposed for feature extraction, selection and classification in [48]. These selected features are fed into a classifier (SoftMax function) to categorize network traffic as normal or malicious. The effectiveness of this approach is demonstrated through empirical evaluations across several datasets, including KDDCup-99, NSL-KDD, BoT-IoT, and CICIDS-2017, where existing models are outperformed in terms of accuracy. However, limitations such as potential overfitting and the need for computational resources to implement the model exist due to the complexity of the deep learning models.
A solution in [49] employs spider monkey optimization for feature selection and stacked deep polynomial network for data classification, addressing the existing gaps in intrusion detection, thereby enhancing system performance by focusing on precise feature selection and robust anomaly detection. The model is validated with NSL-KDD datasets by achieving accuracy of 99.02%, precision of 99.38%, recall of 99.91%, and an F1-score of 99.14%. However, the datasets used to validate the model are older with many inherent flaws and the model faces limitations upon scaling in diverse real-world IoT applications.
A Multi-Attack Intrusion Detection System (MAIDS) for Software-Defined IoT Networks is proposed in [50], comparing five different ML algorithms (KNN, SVM, LR, XGBoost and RF). RF and XGBoost are chosen based on accuracy and speed for classifying traffic and false alarms. Additionally, dataset selection is performed, comparing the NSL-KDD and CICIDS2017 based on their false positive and negative rates. To further enhance the system’s efficacy, Shapley Additive Explanations (SHAP) method is developed to select the relevant features from the datasets. However, the effectiveness of the system depends on older datasets, making the system vulnerable to modern day IoT attacks such as DdoS and malwares.
A comprehensive MUD-based security framework for IoT networks is proposed in [51], integrating SDN and hybrid machine learning techniques such as NDAE and Random Forest to provide dynamic, automated threat detection and mitigation. Datasets such as MUDgee, CICIDS2017, and Bot-IoT are leveraged to train the model, resulting in a performance that achieves a reduction in bootstrapping latency under attack conditions and maintaining high anomaly detection accuracy with a sensitivity of 0.999. The framework’s potential for real-world applications is showcased by its incorporation of a Digital Twin for pre-deployment policy validation and its ability to detect Mirai botnet activities within 4.5 s. The framework relies on pre-defined MUD profiles that is difficult while working with multiple heterogenous IoT devices, limiting their scalability.
8.3. Distributed and Collaborative Security Approaches
The papers in this group explore distributed and collaborative security mechanisms designed to address the challenges of IoT ecosystems. By integrating concepts such as fog computing, edge computing, and federated learning, these studies aim to develop privacy-preserving and resource-efficient security frameworks that can adapt to the dynamic nature of IoT environments.
An Innovative fog-assisted IDPS for IoT networks is proposed in [52], addressing IoT security requirements through an entropy-based triple machine learning classifier, integrating the strength of RNN, MLP and ADT. IDPS coordinators, resource managers, SDN fabric managers, and feature selectors are integrated in the architecture. SDN controllers are implemented on fog nodes to ensure efficient network management and timely anomaly detection, improving response time and model detection compared to individual classifiers. Since the training dataset is UNSW-NB15, modern attack vectors such as DdoS and malware attacks are lacking. Furthermore, the model does not address application-specific security needs for IoT networks, making it vulnerable to unauthorized access and man-in-the-middle attacks.
Scalability in security system is addressed in [53] proposing a distributed security mechanism using SDN and fog computing, where the functionalities of SDN and fog nodes are presented as a containerized cognitive security system. Cloud-fog architecture is employed in the model where supervised (Naïve Bayes), and unsupervised (K-means clustering) machine learning algorithms are used for user and entity behavioral analysis and pushed to fog nodes. The model is tested on AWID datasets, achieving accuracy of 90.64%, precision, recall, and F1 score of 0.9, demonstrating improved throughput and energy efficiency in fog environments. However, the study falls short regarding the solution’s accuracy, whereas another ML-based solution achieves an accuracy rate of 98%. Furthermore, a comparative evaluation of resource efficiency and response rates is lacking in the paper.
A secure middleware solution for IoT networks is presented in [54], addressing DdoS attacks and botnet formation by integrating beats agent for data collection, SDN for traffic management, fog computing, and ML models such as SVM and Random Forest for anomaly detection in the architecture. The ELK stack for SIEM functionality is incorporated in the system, achieving high accuracy (99.2% with SVM, 99.8% with Random Forest) on the KDD99 dataset. The dataset used for validation consists of outdated attacks. Hence, evaluation with datasets containing emerging threats related to DdoS and Malware is needed for the model.
A scalable and energy-efficient anomaly detection scheme (SEE-ADS) tailored for wireless SDN-based mMTC IoT networks is presented in [55], employing a multi-layered detection, leveraging both lightweight detection and heavy-weight detection modules, activated when no flow policy exists, saving energy consumption. A Strategy Selection Module takes decisions with game theory to pass, block, or escalate packets for heavyweight analysis using LESLA module, thus balancing detection accuracy and energy efficiency. The detection accuracy is validated with the CTU-13 dataset; however, it lacks modern day attacks such as DdoS and cross-site scripting. Furthermore, validation of the scheme’s scalability in a real-world IoT environment is needed.
An innovative cloud-edge collaborative approach for IoT intrusion detection is proposed in [56], combining SSAE-TCN architecture with federated learning to address resource constraints and privacy concerns. The authors demonstrated significant reductions in computational requirements while maintaining detection accuracy comparable to centralized training using the CIC-IDS-2017 dataset. Moreover, the method enables the identification of previously unknown attacks and effective model training across heterogeneous data distributions, thus enhancing privacy, efficiency, and collaborative threat intelligence sharing across IoT environments. Nevertheless, further model validation necessitates a comprehensive evaluation of resource utilization for real-world IoT devices.
8.4. Protocol and Application-Specific Security Solutions
This category focuses on security solutions tailored to specific protocols and applications within the IoT domain. The papers focus on recognizing that generic security approaches may not adequately address the unique requirements of various IoT protocols and applications. By developing targeted solutions, these studies aim to provide more effective and efficient security measures considering the specific characteristics and vulnerabilities of IoT deployments.
A Protocol-Based Deep Intrusion Detection (PB-DID) architecture is proposed in [57] addressing DoS and DdoS attacks in IoT environments, combining UNSW-NB15 and Bot-IoT datasets and employing an LSTM-based unsupervised model to detect anomalies. The model achieves a classification accuracy of 96.3% and a binary classification accuracy of over 99%. Although DoS/DdoS traffic is effectively detected, differentiation between these attack types is challenging for the model. Furthermore, the model has some limitations, such as an imbalance of datasets, overfitting issues, and adaptability to emerging threats at the application layer, particularly HTTPS request flooding, leaving scope for future research work.
A hybrid DL-driven framework is proposed in [58] that employs features of programmability and centralized control of SDN, utilizing hybrid deep learning algorithms, specifically CuDNNLSTM and CuDNNGRU, for efficient threat detection without overloading resource-constrained IoT devices. Performance evaluation includes testing and training from the CICDDoS2019 dataset in a simulated IoT environment. Future research is required for resource efficiency for real-world IoT devices.
8.5. Drawbacks of Adversarial Machine Learning Techniques
Some of the critical challenges of adversarial machine learning techniques are discussed in [59], addressing the vulnerability due to adversarial attacks for deep learning-based NIDS in IoT environments. A two-phase attack method combining Model Extraction and Adversarial Example Generation is proposed, exploiting small perturbations in network traffic to bypass detection. Testing on the Kitsune NIDS using Mirai botnet and Video Injection datasets achieves a 94.31% success rate with minimal packet modifications. The research exposes a critical weakness in deep learning-enhanced NIDS, emphasizing the need for more robust defense mechanisms against adversarial techniques in IoT security.
8.6. Critical Analysis of the Review Papers
This comprehensive review examines diverse methodologies for enhancing IoT security. Researchers explore SDN-based frameworks integrated with ML/DL techniques [40,41,42,43,44,45,46,47], advanced feature engineering and classification approaches [48,49,50,51], distributed and collaborative security mechanisms [52,53,54,55,56], and protocol-specific solutions [57,58]. These studies employ various ML algorithms, from lightweight classifiers to sophisticated deep learning models, aiming to improve threat detection accuracy and efficiency. Critical analyses reveal common limitations across papers, including reliance on outdated datasets [50,53], insufficient real-world validation [40,54], and inadequate scalability testing [40]. Many proposed frameworks struggle with application-layer attacks [42,45] and emerging threat vectors [57,58]. The review also highlights the vulnerability of ML-based NIDS to adversarial attacks [59], underscoring the need for more robust defense mechanisms in IoT security.
A review of the methodology and critical analysis is presented in Table 4.

Table 4.
Review of ML/DL techniques, methodology used and its critical analysis.
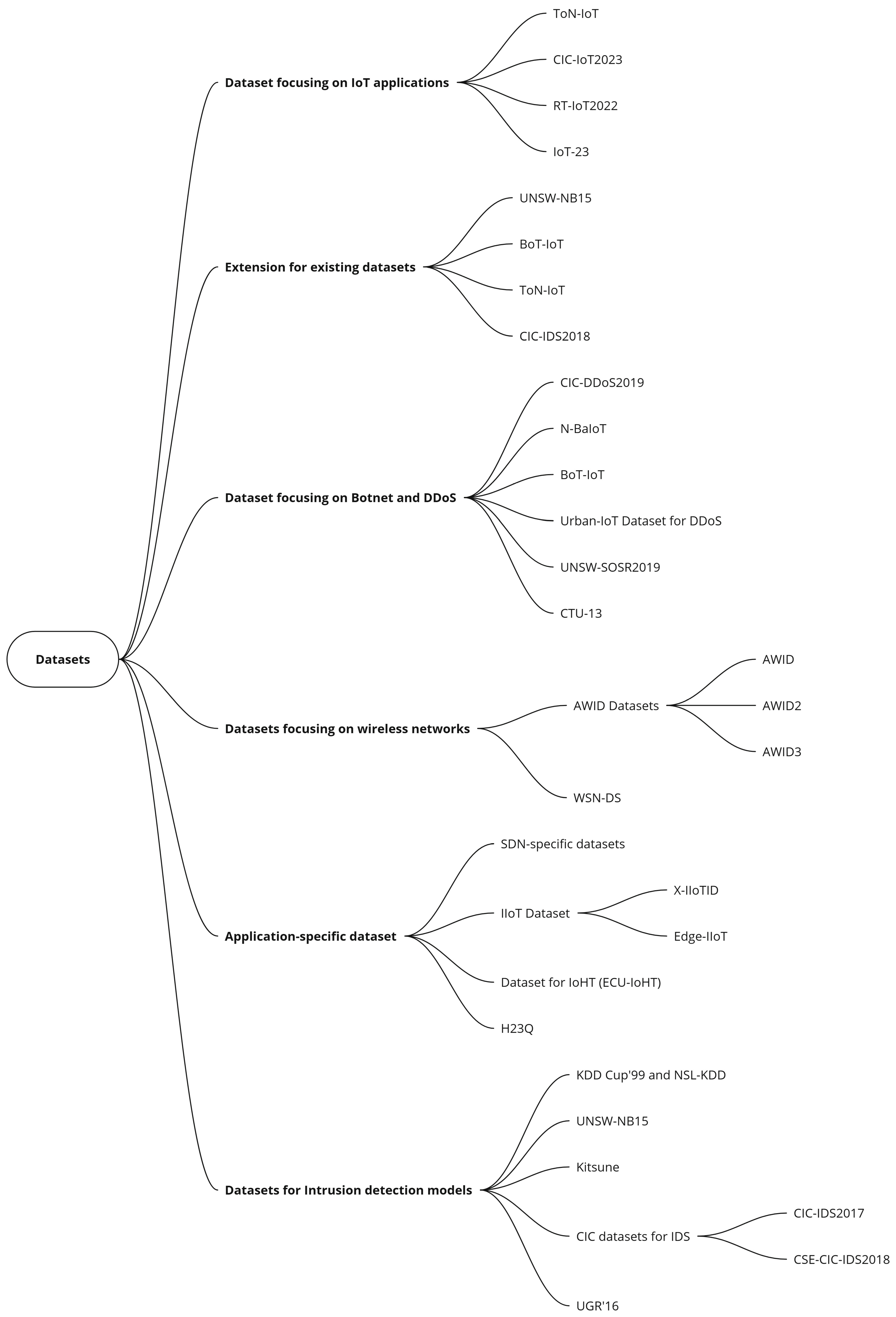
9. Datasets
In the previous section, we discussed several ML/DL techniques whose effectiveness depends critically on the datasets used for training. To develop reliable intrusion detection models and validate security frameworks comprehensively, a thorough understanding of available datasets and their testing environments is essential. Datasets not only influence the performance of ML/DL-based security solutions but also serve as benchmarks for evaluating overall framework effectiveness across diverse attack scenarios. In this section, the datasets that can be employed to train ML/DL techniques are discussed into 5 distinct categories: network intrusion datasets, application-specific datasets, datasets focusing on wireless networks, datasets focusing on IoT, datasets focusing on Botnet and DDoS, and extension of the dataset.
The mind map for the datasets is presented in Figure 7.
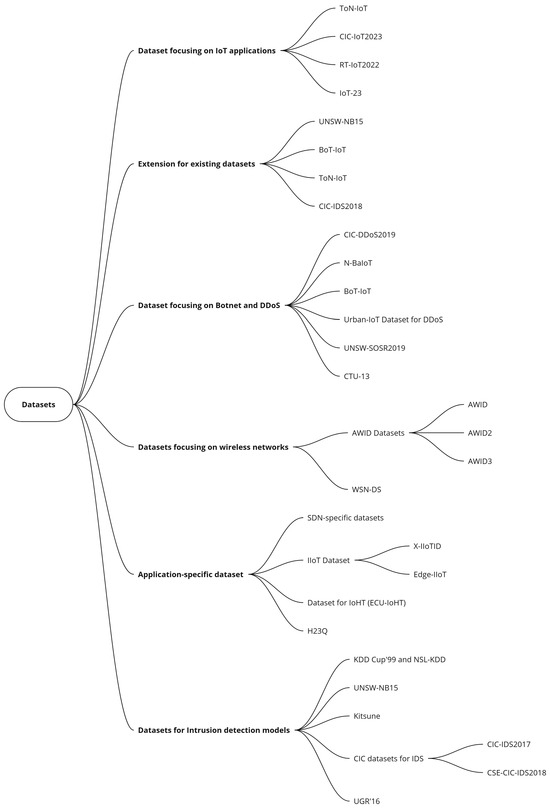
Figure 7.
Datasets.
9.1. Datasets for Intrusion Detection Models
Network intrusion detection datasets are the foundation for developing and evaluating IDSs that aim to identify malicious activities within network traffic by encompassing various attack types and normal network behavior. This enables the training and testing of machine learning models for anomaly detection and classification. The datasets in this category, such as UNSW-NB15, KDD Cup’99, NSL-KDD, CIC-IDS2017, CSE-CIC-IDS2018, and UGR’16, provide a comprehensive representation of network traffic patterns and facilitate the development of general-purpose intrusion detection solutions.
9.1.1. KDD Cup’99 and NSL-KDD
Initially developed for the detection of network intrusions, the DARPA dataset incorporates attacks Denial of Service (DoS), Remote to Local (R2L), User to Root (U2R), and Probe attacks. KDD Cup’99, the initial dataset, was published with some notable issues, particularly in relation to data duplication. A later version of KDD Cup’99, the NSL-KDD dataset, was introduced in response to the concerns regarding duplication. NSL-KDD, however, continues to suffer from limitations related to class imbalance, use of obsolete devices, traffic patterns and older sets of attacks [60].
9.1.2. UNSW Datasets
The UNSW-NB15 dataset [61], the first dataset released by the university, includes various attack types such as reconnaissance, shellcode, exploits, fuzzes, worms, and DoS attacks. However, the dataset [62] suffers from class imbalance and overlapping data, with attacks reflecting older methodologies and lacking security events against IoT and operating systems.
9.1.3. Kitsune Dataset
The Kitsune dataset [63] evaluates intrusion detection systems in diverse network environments, encompassing IP camera for video surveillance network and a heterogeneous IoT devices to support the ecosystems, simulating nine distinct attack scenarios, including reconnaissance, man-in-the-middle, denial of service, and botnet infections. Notably, the dataset incorporates 115 statistical features extracted from network packets across multiple time windows. However, the dataset lacks many modern-day attack scenarios like DDoS and malware attacks, necessary for designing intrusion detection systems.
9.1.4. CIC Datasets for IDS
The Canadian Institute for Cybersecurity has published some notable datasets such as CIC-IDS2017 and CSE-CIC-IDS2018 to formulate intrusion detection systems.
The CIC-IDS2017 dataset [64], developed in 2017, simulates real-world network flow attacks, such as botnets, brute force, probe scans, web attacks, and infiltration attacks, targeting the network and application layers. Extending and improvising upon CIC-IDS2017, the CSE-CIC-IDS2018 dataset [65] includes similar attacks on same testbed with varied configurations and OSs. However, the testbed lacks real-world IoT devices and its applications.
9.1.5. UGR’16
In [66], UGR’ 16 dataset, developed in 2016 for cyclostationary network IDS, including attacks such as low-rate DoS, port scanning and botnets. The dataset is developed by recording NetFlow record over 4 months in a tier-3 ISP’s providing diverse client services. Since the attacks employed to generate the dataset are old, they cannot be used to develop modern-day security systems or intrusion detection systems.
9.2. Application-Specific Datasets
This section examines datasets developed for Industrial IoT (IIoT), software-defined networking (SDN), Internet of Healthcare Things (IoHT), and web protocols, analyzing their methodological contributions and inherent limitations in addressing domain-specific security challenges.
9.2.1. Industrial IoT Datasets
UNSW and Edith Cowan University have published X-IIoTID and Edge-IIoT datasets, respectively, focusing on Industrial IoT environments.
The X-IIoTID dataset [67], developed in 2021, simulates the IIoT environment, including many IoT connectivity protocols such as Modbus, WebSocket, CoAP, MQTT, TCP, ARP, HTTP, DNS, ICMP, SMTP, and UDP. One such limitation of the testbed is that the attacker has direct access to the network from the switch, a scenario that does not reflect the real-world IIoT environment.
On the other hand, the Edge-IIoT dataset [68] was developed to simulate realistic IoT/IIoT environment by employing 7 layers, includes cloud computing, network function virtualization, blockchain network, fog computing, software-defined networking, edge computing and perception layer. DoS/DDoS attacks, information gathering, MITM, Injection attacks and malware attacks are simulated in the testbed. However, there are certain limitations to the testbed and dataset such as lack of security measures in the testbed such as segmentation, attacking devices having information and access to the network, lack of information of behavior of IoT nodes that are in control of attacker to check the access control measures.
9.2.2. SDN-Specific Datasets
The authors of [69] present a novel dataset for intrusion detection in SDN managed IoT environments, utilizing Mininet, an ONOS controller and IoT devices with both benign and malicious traffic, attacks such as DoS, DDoS, port scanning, OS fingerprinting and fuzzing. In total, 33 real-time, SDN-specific features are extracted with static and dynamic IoT networks. Despite the novelty of dataset, it exhibits certain limitations such as constrained diversity of simulated IoT devices and the absence of emerging attack such as malwares and botnet.
9.2.3. Datasets for IoHT
An ECU-IoHT dataset [70] was proposed, addressing a critical gap in IoHT security research. Utilizing a Libelium MySignals healthcare kit, the authors simulated various cyberattacks, including Nmap scans, ARP poisoning, DoS attacks, and smurf attacks within a controlled testbed environment. The resulting dataset comprises 8905 network flows, encompassing both normal and malicious traffic, with features such as byte counts, packet counts, and protocol information. Notably, the limited attack types and relatively small dataset size may limit its generalizability to real-world healthcare environments. Despite these shortcomings, the dataset serves as a crucial steppingstone for future research in IoHT security.
9.2.4. H23Q Datasets
Focusing on various attacks on HTTP/2, HTTP/3 and QUIC services, the H23Q dataset [71] was developed in 2023, with a testbed comprising six servers deployed on Azure cloud with 13 clients. The dataset created only focuses on application layer attacks specific to HTTP and QUIC protocols on cloud, failing to replicate real-world IoT devices.
9.3. Datasets Focusing on Wireless Networks
The section of the survey paper focuses on datasets that target wireless networks, including datasets from University of Aegean and Prince Sultan University.
9.3.1. AWID, AWID2 and AWID3
The University of Aegean has published some notable datasets such as AWID, AWID2 and AWID3 datasets. Initially, the AWID dataset was published employing a WEP-protected wireless network with real traces of both normal and intrusive 802.11 traffic. However, this dataset exhibited certain limitations, such as an imbalance of attributes and a lack of normalization, which was addressed in AWID2 datasets [72] by including both benign and malicious traffic with normalization, class balancing, and feature selection.
Later in 2021, the AWID3 dataset [73] was published, focusing on enterprise networks and multilayer attacks, featuring a testbed with a single wireless access point and multiple clients connecting to one SSID. In this environment, the attacker performs various wireless attacks within the 802.1X EAP framework. The dataset developed incorporates secure authentication protocols such as 802.1X EAP, which complicates the implementation due to the resource-constrained behavior of IoT networks. However, the inclusion of malware and application layer attacks related to wireless protocols can be leveraged to develop secure intrusion detection systems.
9.3.2. WSN-DS
The WSN-DS dataset [74] was developed at Prince Sultan University with Network Simulator 2 (NS-2) to aid in the detection and classification of Denial of Service (DoS) attacks in Wireless Sensor Networks (WSNs) by including data from 100 sensor nodes employing LEACH protocol within a 100 m × 100 m network area. Four types of DoS attacks were simulated such as Blackhole, Grayhole, Flooding, and Scheduling attacks by altering the behavior of certain nodes, such as packets droppage, sending excessive advertisement messages, and causing data collisions. Since attackers were integrated into the network by acting as malicious cluster heads, no IoT devices were used and only DoS attacks were focused, the dataset is unable to replicate a real-world scenario for an IoT environment.
9.4. Datasets Focusing on Botnet and DDoS
The section discusses the datasets that focus predominantly on DDoS and Botnets.
9.4.1. CIC-DDoS2019
The CIC-DDoS2019 dataset [75], developed in 2019 by the Canadian Institute of Cybersecurity, focuses on a wide range of DDoS attacks on networks, consisting of PCs and servers, aiding to develop a security model to tackle DDoS attacks. The datasets use similar testbeds that are used to develop CIC-IDS2017 and CSE-CIC-IDS2018 datasets, thereby including same limitations of lack of real-world IoT devices in the testbed.
9.4.2. N-BaIoT
The N-BaIoT dataset [76], proposed by UC Irvine, includes real-world network traffic from nine commercial IoT devices infected with Mirai and BASHLITE botnets, encompassing attack types, such as scanning, flooding, and spam data transmission, providing a comprehensive foundation for anomaly detection research. However, the dataset lacks application layer attacks that includes HTTP and HTTPS attacks.
9.4.3. BoT-IoT
The BoT-IoT dataset [77] was developed in 2021, simulating botnets for IoT environment, including attacks such as DoS, DDoS, information theft, and reconnaissance, across five IoT devices. However, the dataset has certain limitations, such as a class imbalance due to the predominance of malicious traffic and the focus on only the network layer.
9.4.4. Urban-IoT Dataset for DDoS
The paper [78] presents a large-scale dataset of urban IoT activity for synthetic DDoS attack emulation, derived from 4060 real IoT nodes over a month-long period, offering insights into spatial and temporal patterns of device activity. However, a notable limitation, such as synthetic attack model, based solely on device activity status, lacks the complexity of real-world DDoS attacks. Furthermore, the dataset does not share insights about inter-node correlations.
9.4.5. UNSW-SOSR2019
The UNSW-SOSR2019 dataset [58,79] is created on a cloud-based testbed and generates large volumes of traffic at the network layer, focusing on ARP spoofing, TCP SYN flooding, Fraggle, ping of death, SNMP, SSDP, TCP SYN, and Smurf attacks. However, the dataset has certain shortfalls; it does not encompass many application layer attacks, such as HTTPS flooding-related attacks.
9.4.6. CTU-13
The CTU-13 dataset [80] was developed for robust and well-structured resource for evaluating botnet detection methods, featuring real, labeled network traffic, including botnet, normal, and background data. Generated within a controlled university network environment, the dataset includes traffic from virtual machines infected with various botnet malware such as Neris, Rbot, and Virut. However, the datasets, testbed and the attacks encompassed in it were very old and lacks latest botnets like Mirai Botnets.
9.5. Dataset Focusing on IoT Applications
This section discusses about datasets that were developed on testbed formed by IoT devices and includes IoT applications.
9.5.1. ToN-IoT
The ToN-IoT dataset [81] was developed in 2020, simulating a home IoT environment with home IoT devices, Windows and Linux operating systems. Some of the limitations of the testbed are the lack of information about pre-defined security measures like network segmentation and access control, commonly found in real-time IoT environments. Additionally, the dataset resembles common attacks and excludes malware and unauthorized access [62].
9.5.2. CIC-IoT2023
In contrast, the CIC-IoT2023 dataset [82] targets a home IoT network, simulating attacks such as DDoS, DoS, Recon, web-based attacks, brute force, spoofing, and Mirai botnets. Some of the limitations of the dataset are that it lacks common security measures placed on IoT gateway and attacking system has direct access to the IoT network. Thus, a real case scenario is not depicted in the dataset.
9.5.3. RT-IoT2022
The RT-IoT2022 [83] dataset is derived from a real-time IoT infrastructure created by integrating a diverse range of IoT devices and sophisticated network attack methodologies. It encompasses both normal and adversarial network behaviors, providing a general representation of real-world scenarios. The IoT devices used are ThingSpeak-LED, Wipro-Bulb, and MQTT-Temp, and attacks simulated are Brute-Force SSH attacks, DDoS attacks using Hping and Slowloris, and Nmap patterns. The bidirectional attributes of network traffic are meticulously captured using the Zeek network monitoring tool and the Flowmeter plugin. The dataset can be specifically used for forming Intrusion Detection Systems (IDS), fostering the development of robust and adaptive security solutions for real-time IoT networks. Despite its benefits, the dataset lacks attacks related to unauthorized access and does not follow any attack methodologies such as cyber kill chain, which is a common technique to conduct cyber-attacks.
9.5.4. IoT-23
The IoT-23 dataset [84], developed by the Stratosphere Laboratory at CTU University and funded by Avast Software, comprises 23 network traffic captures from IoT devices, including 20 malware-infected scenarios and 3 benign device scenarios. It aims to provide a labeled dataset for developing machine learning algorithms to detect IoT malware. The dataset includes real network traffic from devices like Philips HUE, Amazon Echo, and smart door locks captured in a controlled environment. However, the dataset does not include the attacker’s activity in case the access to the devices is breached.
9.6. Extension to UNSW-NB15, BoT-IoT, ToN-IoT and CSE-CIC-IDS2018 Datasets
The authors [85] propose a standardized NetFlow-based feature set for NIDS datasets to address the limitations of existing datasets, particularly their lack of standardized feature sets and generalizability. They created new versions of four popular datasets (UNSW-NB15, BoT-IoT, ToN-IoT, CSE-CIC-IDS2018) using 43 NetFlow features to provide a common ground for evaluating ML-based NIDSs across different network scenarios. Despite the benefits, the NetFlow features are limited to capture of certain attack behaviors ignoring the packets that require deep packet inspection for malware.
A summary of the testbed and critical analysis is represented in Table 5.

Table 5.
Review of datasets on description and critical analysis.
9.7. Limitations of Datasets
The systematic review of IoT security datasets reveals pervasive limitations that significantly impact their utility in developing robust security solutions. A fundamental concern emerges from the unrealistic network access scenarios, where multiple datasets [65,66,80] grant attackers direct network accessibility, failing to replicate authentic threat vectors. This architectural shortcoming is compounded by the absence of essential security controls and network segmentation in testbed environments [78,79]. The data quality dimension presents another critical challenge, with prevalent class imbalance issues manifesting across several prominent datasets [60,61,74], potentially skewing machine learning model development. Furthermore, the technological obsolescence of datasets such as KDD Cup’99, NSL-KDD, and UGR’16 [60,64] undermines their relevance, as they contain outdated attack signatures and traffic patterns that poorly reflect contemporary threat landscapes.
A significant limitation lies in the coverage scope, where numerous datasets [61,73,74] predominantly focus on network layer attacks while neglecting crucial application layer threats. This narrow focus is particularly problematic in datasets like UNSW-SOSR2019 and N-BaIoT [61,73], which lack comprehensive coverage of modern attack vectors such as HTTPS flooding and sophisticated malware variants. The environmental constraints further diminish dataset utility, with many [67,68] featuring limited device diversity and artificial traffic patterns that fail to capture the complexity of production environments. The IoT-specific datasets [80,81,82] exhibit shortcomings in representing realistic security measures and attack scenarios, often lacking crucial elements such as unauthorized access patterns and sophisticated attack methodologies.
The architectural limitations extend to the representation of modern network paradigms, with datasets [65,66] inadequately capturing the nuances of distributed architectures and edge computing scenarios. This deficiency is evident in testbeds that fail to implement realistic security controls and lack proper validation against real-world deployment scenarios. The standardization effort through NetFlow-based features [83], while addressing some consistency issues, introduces new limitations by potentially missing critical attack behaviors that require deep packet inspection. These multifaceted limitations underscore the pressing need for more comprehensive, standardized, and contemporary datasets that accurately reflect modern threat landscapes and network architectures while maintaining rigorous validation methodologies.
The synthesis of these limitations reveals a critical gap in the current dataset ecosystem, potentially hampering the development of effective security solutions for modern IoT environments. Datasets focusing on specific attack types, such as CTU-13 [77] and WSN-DS [72], while valuable for targeted research, fail to provide the comprehensive coverage necessary for developing robust, general-purpose security solutions. This comprehensive analysis of limitations provides crucial insights for researchers and practitioners working to develop more effective IoT security solutions, while also highlighting the urgent need for new dataset development initiatives that address these identified shortcomings.
These limitations underscore the need for more comprehensive and realistic datasets that accurately represent the complexity of modern networks and IoT environments. Future dataset development must address these shortcomings to enhance the efficacy of machine learning-based security solutions.
9.8. Requirements
Considering the limitations identified in the previous section, it is evident that current datasets fall short of meeting the demands necessary to develop effective IoT security frameworks. To address these challenges, this section outlines the essential requirements for developing new datasets, aiming to bridge existing gaps by ensuring comprehensive coverage, realistic threat representation, and alignment with contemporary network architectures. Specifically, the new datasets must achieve the following:
- Accurately replicate realistic IoT scenarios, including multiple in-house users, diverse IP addresses, and varied user interactions to reflect authentic usage patterns.
- Incorporate the propagation of malicious traffic by compromised users to other IoT nodes, facilitating a thorough analysis of malicious traffic patterns between trusted nodes.
- Be designed to simulate real-world conditions where attackers have limited or no prior information about the network, necessitating them to execute all stages of the cyber kill chain to infiltrate the network.
- Integrate typical security measures employed by network administrators, thereby replicating a realistic and secured IoT environment.
- Include information on both normal and malicious data transmitted by IoT nodes, highlighting potential risks to the IoT environment.
Such improvements in testbed design and dataset characteristics are crucial for the development of robust IoT security solutions capable of withstanding multi-stage and multi-layer attacks.
10. Key Discussion
Our systematic analysis of SDN-enabled IoT security implementations reveals a complex interplay between architectural decisions, security mechanisms, and implementation challenges. Through rigorous examination of the literature, we have identified three fundamental dimensions that significantly influence the effectiveness of IoT security frameworks: architectural design paradigms, security mechanism integration, and operational validation methodologies. These dimensions provide a comprehensive framework for understanding current limitations and future research directions in IoT security.
Regarding architectural design paradigms, our analysis demonstrates that hybrid approaches integrating cloud–edge–fog architectures exhibit superior performance characteristics compared to single-tier implementations. These hybrid frameworks facilitate optimal distribution of security functions across the infrastructure, particularly critical given the inherent resource constraints of IoT devices. The evidence suggests that such distributed approaches enable more efficient allocation of security workloads, with computational tasks distributed according to the capabilities available at different architectural tiers. However, our review also reveals that many proposed architectures struggle with scalability challenges when deployed in production environments, particularly in scenarios involving heterogeneous IoT devices operating under varying resource constraints.
In examining security mechanism integration, our research reveals that the synthesis of encryption protocols, authentication methodologies, and access control mechanisms represents a critical aspect of framework design. The integration of these security elements with SDN frameworks significantly enhances control over inter-node communications. While fine-grained access control mechanisms coupled with continuous authentication processes demonstrate robust security postures in theoretical frameworks, a significant gap exists in their empirical validation, particularly regarding performance under high-traffic scenarios when traffic is flooded on IoT devices and scalability in real-world deployments with heterogenous IoT devices and considering multiple IoT devices.
From an operational validation methodology perspective, our analysis reveals significant challenges in current approaches to framework evaluation and testing. The analysis of threat detection implementations highlights a contradiction between signature-based and machine learning-based approaches. While signature-based systems benefit from community-driven threat intelligence, machine learning approaches face substantial challenges related to dataset limitations. This observation leads to a critical concern regarding the current state of IoT security datasets, highlighting significant gaps in contemporary attack vector representation. These limitations manifest in several critical areas, including limited coverage of emerging threats, unrealistic attack scenarios that fail to reflect authentic threat actor behaviors and insufficient representation of real-world network conditions and attack patterns. These dataset limitations have profound implications for machine learning and deep learning-based intrusion detection systems, potentially compromising their effectiveness in real-world deployments.
11. Future Research Directions
We have found several aspects for future research areas extracted from our study, outlined in Figure 8. The research directions are further discussed and elaborated in the following paragraphs.
Figure 8.
Research directions and overview.
11.1. Federated Machine Learning for Distributed Security
Integrating federated machine learning presents a significant opportunity for advancing IoT security. Future research could focus on developing distributed computing frameworks that leverage unsupervised learning in cloud environments, with model deployment across fog and edge layers. This approach could enable collaborative security models with multiple training instances, facilitating bidirectional learning flows between edge/fog layers and cloud infrastructure. Cross-organizational security model sharing while maintaining privacy becomes possible through this framework, ultimately enhancing threat detection through distributed intelligence. Developing such systems would significantly improve the adaptability and effectiveness of IoT security measures while preserving resource efficiency.
11.2. Adaptive Zero-Trust Architectures
Future research endeavors could prioritize the advancement of adaptive zero-trust architectures tailored specifically for IoT environments. This research direction necessitates the investigation of context-aware authentication mechanisms and dynamic authorization frameworks that respond intelligently to device behavior and capabilities. The authentication and authorization mechanisms could be calibrated based on comprehensive device profiling, whereby the verification requirements are proportionally adjusted according to the device’s computational resources, historical behavior patterns, and security risk assessment. For instance, resource-constrained devices operating within expected parameters might undergo streamlined verification processes, while devices exhibiting anomalous behavior or accessing critical resources would be subject to more rigorous multi-factor authentication protocols. Such advancements would facilitate the implementation of granular security controls while optimizing system performance and maintaining operational efficiency. This adaptive approach would represent a significant evolution in IoT security architecture, balancing robust security measures with the practical constraints of diverse IoT deployments.
11.3. Comprehensive Dataset Development
There is a critical need for more robust and representative IoT security datasets. To address these challenges and limitations discussed in Section 9, we need a dataset that outlines the essential requirements for developing new datasets, aiming to bridge existing gaps by ensuring comprehensive coverage, realistic threat representation, and alignment with contemporary network architectures, discussed in Section 9.8.
11.4. Application-Centric Security Frameworks
The development of application-specific security models represents an important research direction. Future work could focus on semantic-aware security policies that understand the context of the application and implement logical segmentation based on application boundaries. This includes developing fine-grained access control aligned with application requirements and cross-application security policy coordination. Context-aware threat detection and response mechanisms would further enhance the effectiveness of these frameworks, providing more targeted and efficient security measures for specific IoT applications.
11.5. Intent-Based Security Using Generative AI
The integration of generative AI technologies with security orchestration presents novel research opportunities. This includes developing natural language interfaces for security policy definition and automated translation of high-level security intents to enforceable policies. AI-driven policy conflict detection and resolution mechanisms would streamline security management, while contextual security policy recommendation systems could enhance decision-making processes. Developing user-friendly security management interfaces that abstract technical complexity would make IoT security more accessible to non-expert users while maintaining robust protection.
These research directions collectively address the identified gaps while advancing the state of IoT security. Future research efforts could consider the interdependencies between these areas, as advances in one domain may enable or require corresponding advances in others. Additionally, researchers should maintain their focus on practical implementability while pursuing these directions, ensuring that proposed solutions remain viable within the resource constraints and operational requirements of IoT systems. Success in these areas would contribute significantly to developing more robust, usable, and effective security solutions for IoT environments.
12. Conclusions
This comprehensive systematic review has addressed all four stated research objectives, providing significant insights into SDN-enabled IoT security frameworks and their integration with machine learning techniques. Our analysis revealed that while hybrid architectures integrating cloud–edge–fog computing demonstrate superior performance in distributing security workloads, current implementations face significant challenges in scalability and real-world validation. The examination of authentication, encryption, and access control mechanisms highlighted promising advances in adaptive authentication frameworks and lightweight cryptographic operations, though their effectiveness remains constrained in resource-limited IoT environments.
The study’s critical analysis of existing IoT security datasets uncovered substantial limitations in representing contemporary threat landscapes, particularly regarding application layer attacks and emerging security measures. Based on these findings, we have identified several promising future research directions, including the development of adaptive zero-trust architectures, implementation of federated machine learning for distributed security, and creation of more comprehensive datasets. These insights not only contribute to the current body of knowledge but also provide a clear roadmap for advancing IoT security through improved frameworks, methodologies, and datasets that better reflect modern security challenges.
Author Contributions
Conceptualization: S.R.M. and B.S.; Methodology: S.R.M. and K.C.Y.; Validation: S.R.M. and K.C.Y.; Formal Analysis: S.R.M. and B.S.; Resource: S.T.; Writing—Original Draft Preparation: S.R.M.; Writing—Review and Editing: S.R.M., B.S., K.C.Y. and S.T.; Supervision: B.S., K.C.Y. and S.T.; Project Administration: S.T.; Funding: S.T. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
No datasets have been generated.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Waseem, Q.; Isni Sofiah Wan Din, W.; Aminuddin, A.; Hussain Mohammed, M.; Alfa Aziza, R.F. Software-Defined Networking (SDN): A Review. In Proceedings of the ICOIACT 2022—5th International Conference on Information and Communications Technology: A New Way to Make AI Useful for Everyone in the New Normal Era, Proceeding, Yogyakarta, Indonesia, 24–25 August 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022; pp. 30–35. [Google Scholar]
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A Survey on Internet of Things Security: Requirements, Challenges, and Solutions. Internet Things 2021, 14, 100129. [Google Scholar] [CrossRef]
- Jimenez, M.B.; Fernandez, D.; Rivadeneira, J.E.; Bellido, L.; Cardenas, A. A Survey of the Main Security Issues and Solutions for the SDN Architecture. IEEE Access 2021, 9, 122016–122038. [Google Scholar] [CrossRef]
- Siddiqui, S.; Hameed, S.; Shah, S.A.; Ahmad, I.; Aneiba, A.; Draheim, D.; Dustdar, S. Toward Software-Defined Networking-Based IoT Frameworks: A Systematic Literature Review, Taxonomy, Open Challenges and Prospects. IEEE Access 2022, 10, 70850–70901. [Google Scholar] [CrossRef]
- Aldhaheri, A.; Alwahedi, F.; Ferrag, M.A.; Battah, A. Deep Learning for Cyber Threat Detection in IoT Networks: A Review. Internet Things Cyber-Phys. Syst. 2024, 4, 110–128. [Google Scholar] [CrossRef]
- Rahman, M.M.; Shakil, S.A.; Mustakim, M.R. A Survey on Intrusion Detection System in IoT Networks. Cyber Secur. Appl. 2025, 3, 100082. [Google Scholar] [CrossRef]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G. Preferred Reporting Items for Systematic Reviews and Meta-Analyses: The PRISMA Statement. BMJ 2009, 339, 332–336. [Google Scholar] [CrossRef]
- Javanmardi, S.; Shojafar, M.; Mohammadi, R.; Alazab, M.; Caruso, A.M. An SDN Perspective IoT-Fog Security: A Survey. Comput. Netw. 2023, 229, 109732. [Google Scholar] [CrossRef]
- Golightly, L.; Modesti, P.; Garcia, R.; Chang, V. Securing Distributed Systems: A Survey on Access Control Techniques for Cloud, Blockchain, IoT and SDN. Cyber Secur. Appl. 2023, 1, 100015. [Google Scholar] [CrossRef]
- Harbi, Y.; Aliouat, Z.; Refoufi, A.; Harous, S. Recent Security Trends in Internet of Things: A Comprehensive Survey. IEEE Access 2021, 9, 113292–113314. [Google Scholar] [CrossRef]
- Ray, P.P.; Kumar, N. SDN/NFV Architectures for Edge-Cloud Oriented IoT: A Systematic Review. Comput. Commun. 2021, 169, 129–153. [Google Scholar] [CrossRef]
- Salman, O.; Elhajj, I.; Chehab, A.; Kayssi, A. IoT Survey: An SDN and Fog Computing Perspective. Computer Netw. 2018, 143, 221–246. [Google Scholar] [CrossRef]
- Ogonji, M.M.; Okeyo, G.; Wafula, J.M. A Survey on Privacy and Security of Internet of Things. Comput. Sci. Rev. 2020, 38, 100312. [Google Scholar] [CrossRef]
- De Keersmaeker, F.; Cao, Y.; Ndonda, G.K.; Sadre, R. A Survey of Public IoT Datasets for Network Security Research. IEEE Commun. Surv. Tutor. 2023, 25, 1808–1840. [Google Scholar] [CrossRef]
- Farris, I.; Taleb, T.; Khettab, Y.; Song, J. A Survey on Emerging SDN and NFV Security Mechanisms for IoT Systems. IEEE Commun. Surv. Tutor. 2019, 21, 812–837. [Google Scholar] [CrossRef]
- Sha, K.; Yang, T.A.; Wei, W.; Davari, S. A Survey of Edge Computing-Based Designs for IoT Security. Digit. Commun. Netw. 2020, 6, 195–202. [Google Scholar] [CrossRef]
- Casola, V.; De Benedictis, A.; Di Martino, S.; Mazzocca, N.; Starace, L.L.L. Security-Aware Deployment Optimization of Cloud-Edge Systems in Industrial IoT. IEEE Internet Things J. 2021, 8, 12724–12733. [Google Scholar] [CrossRef]
- De Donno, M.; Tange, K.; Dragoni, N. Foundations and Evolution of Modern Computing Paradigms: Cloud, IoT, Edge, and Fog. IEEE Access 2019, 7, 150936–150948. [Google Scholar] [CrossRef]
- Grigoryan, G.; Liu, Y.; Njilla, L.; Kamhoua, C.; Kwiat, K. Enabling Cooperative IoT Security via Software Defined Networks (SDN). In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]
- Alwasel, K.; Jha, D.N.; Habeeb, F.; Demirbaga, U.; Rana, O.; Baker, T.; Dustdar, S.; Villari, M.; James, P.; Solaiman, E.; et al. IoTSim-Osmosis: A Framework for Modeling and Simulating IoT Applications over an Edge-Cloud Continuum. J. Syst. Archit. 2021, 116, 101956. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Yadav, J.; Ansar, S.A.; Khan, M.W.; Pandey, D.; Khan, R.A. A Novel Paradigm: Cloud-Fog Integrated IoT Approach. In Proceedings of the Proceedings—2022 3rd International Conference on Computation, Automation and Knowledge Management, ICCAKM 2022, Dubai, United Arab Emirates, 15–17 November 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022. [Google Scholar]
- Kim, J.T.; Kim, E.; Yang, J.; Jeong, J.P.; Kim, H.; Hyun, S.; Yang, H.; Oh, J.; Kim, Y.; Hares, S.; et al. IBCS: Intent-Based Cloud Services for Security Applications. IEEE Commun. Mag. 2020, 58, 45–51. [Google Scholar] [CrossRef]
- Zarca, A.M.; Garcia-Carrillo, D.; Bernabe, J.B.; Ortiz, J.; Marin-Perez, R.; Skarmeta, A. Enabling Virtual AAA Management in SDN-Based IoT Networks. Sensors 2019, 19, 295. [Google Scholar] [CrossRef]
- Zarca, A.M.; Bernabe, J.B.; Skarmeta, A.; Alcaraz Calero, J.M. Virtual IoT HoneyNets to Mitigate Cyberattacks in SDN/NFV-Enabled IoT Networks. IEEE J. Sel. Areas Commun. 2020, 38, 1262–1277. [Google Scholar] [CrossRef]
- Molina Zarca, A.; Bernal Bernabe, J.; Farris, I.; Khettab, Y.; Taleb, T.; Skarmeta, A. Enhancing IoT Security through Network Softwarization and Virtual Security Appliances. Int. J. Netw. Manag. 2018, 28, e2038. [Google Scholar] [CrossRef]
- Zarca, A.M.; Bagaa, M.; Bernabe, J.B.; Taleb, T.; Skarmeta, A.F. Semantic-Aware Security Orchestration in SDN/NFV-Enabled IoT Systems. Sensors 2020, 20, 3622. [Google Scholar] [CrossRef] [PubMed]
- Mohan, K.V.M.; Kodati, S.; Krishna, V. Securing SDN Enabled IoT Scenario Infrastructure of Fog Networks From Attacks. In Proceedings of the 2nd International Conference on Artificial Intelligence and Smart Energy, ICAIS 2022, Coimbatore, India, 23–25 February 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022; pp. 1239–1243. [Google Scholar]
- Yan, Q.; Huang, W.; Luo, X.; Gong, Q.; Yu, F.R. A Multi-Level DDoS Mitigation Framework for the Industrial Internet of Things. IEEE Commun. Mag. 2018, 56, 30–36. [Google Scholar] [CrossRef]
- Hayajneh, A.A.; Bhuiyan, M.Z.A.; McAndrew, I. Improving Internet of Things (IoT) Security with Software-Defined Networking (SDN). Computers 2020, 9, 8. [Google Scholar] [CrossRef]
- Kuo, C.T.; Chi, P.W.; Chang, V.; Lei, C.L. SFaaS: Keeping an Eye on IoT Fusion Environment with Security Fusion as a Service. Future Gener. Comput. Syst. 2018, 86, 1424–1436. [Google Scholar] [CrossRef]
- Raza, A.; Khan, S.; Shrivastava, S.; Ashraf, M.W.A.; Wang, T.; Wu, K.; Wang, L. A Lightweight Group-Based SDN-Driven Encryption Protocol for Smart Home IoT Devices. Comput. Netw. 2024, 250, 110537. [Google Scholar] [CrossRef]
- Rajeesh, R.K.; P., M.K. Application of SDN for Secure Communication in IoT Environment. Comput. Commun. 2020, 151, 60–65. [Google Scholar] [CrossRef]
- Iqbal, W.; Abbas, H.; Deng, P.; Wan, J.; Rauf, B.; Abbas, Y.; Rashid, I. ALAM: Anonymous Lightweight Authentication Mechanism for SDN-Enabled Smart Homes. IEEE Internet Things J. 2021, 8, 9622–9633. [Google Scholar] [CrossRef]
- Karmakar, K.K.; Varadharajan, V.; Nepal, S.; Tupakula, U. SDN-Enabled Secure IoT Architecture. IEEE Internet Things J. 2021, 8, 6549–6564. [Google Scholar] [CrossRef]
- Atieh, A.; Nanda, P.; Mohanty, M. A Zero-Trust Framework for Industrial Internet of Things. In Proceedings of the 2023 International Conference on Computing, Networking and Communications, ICNC 2023, Honolulu, HI, USA, 20–22 February 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 331–335. [Google Scholar]
- Zanasi, C.; Russo, S.; Colajanni, M. Flexible Zero Trust Architecture for the Cybersecurity of Industrial IoT Infrastructures. Ad. Hoc. Netw. 2024, 156, 103414. [Google Scholar] [CrossRef]
- Wei, M.; Liang, E.; Nie, Z. A SDN-Based IoT Fine-Grained Access Control Method; IEEE: Piscataway, NJ, USA, 2020; ISBN 9781728141992. [Google Scholar]
- Irshad, A.; Mallah, G.A.; Bilal, M.; Chaudhry, S.A.; Shafiq, M.; Song, H. SUSIC: A Secure User Access Control Mechanism for SDN-Enabled IIoT and Cyber-Physical Systems. IEEE Internet Things J. 2023, 10, 16504–16515. [Google Scholar] [CrossRef]
- Kim, Y.; Nam, J.; Park, T.; Scott-Hayward, S.; Shin, S. SODA: A Software-Defined Security Framework for IoT Environments. Comput. Netw. 2019, 163, 106889. [Google Scholar] [CrossRef]
- Safaeisisakht, M.; Hsu, C.H.; Hsu, P.Y.; Chen, M.Y. An Intelligent Two-Phase Automated Architecture for Securing SDN-Based IoT Infrastructure. In Proceedings of the 2023 IEEE 3rd International Conference on Electronic Communications, Internet of Things and Big Data, ICEIB 2023, Taichung, Taiwan, 14–16 April 2023; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2023; pp. 12–16. [Google Scholar]
- Garba, U.H.; Toosi, A.N.; Pasha, M.F.; Khan, S. SDN-Based Detection and Mitigation of DDoS Attacks on Smart Homes. Comput. Commun. 2024, 221, 29–41. [Google Scholar] [CrossRef]
- Hafeez, I.; Antikainen, M.; Ding, A.Y.; Tarkoma, S. IoT-KEEPER: Detecting Malicious IoT Network Activity Using Online Traffic Analysis at the Edge. IEEE Trans. Netw. Serv. Manag. 2020, 17, 45–59. [Google Scholar] [CrossRef]
- Sarica, A.K.; Angin, P. Explainable Security in SDN-Based IoT Networks. Sensors 2020, 20, 7326. [Google Scholar] [CrossRef]
- Wani, A.; Revathi, S. DDoS Detection and Alleviation in IoT Using SDN (SDIoT-DDoS-DA). J. Inst. Eng. Ser. B 2020, 101, 117–128. [Google Scholar] [CrossRef]
- Nguyen, T.G.; Phan, T.V.; Nguyen, B.T.; So-In, C.; Baig, Z.A.; Sanguanpong, S. SeArch: A Collaborative and Intelligent NIDS Architecture for SDN-Based Cloud IoT Networks. IEEE Access 2019, 7, 107678–107694. [Google Scholar] [CrossRef]
- Khan, M.T.; Akhunzada, A.; Zeadally, S. Proactive Defense for Fog-to-Things Critical Infrastructure. IEEE Commun. Mag. 2022, 60, 44–49. [Google Scholar] [CrossRef]
- Lahlou, S.; Moukafih, Y.; Sebbar, A.; Zkik, K.; Boulmalf, M.; Ghogho, M. TD-RA Policy-Enforcement Framework for an SDN-Based IoT Architecture. J. Netw. Comput. Appl. 2022, 204, 103390. [Google Scholar] [CrossRef]
- Fatani, A.; Elaziz, M.A.; Dahou, A.; Al-Qaness, M.A.A.; Lu, S. IoT Intrusion Detection System Using Deep Learning and Enhanced Transient Search Optimization. IEEE Access 2021, 9, 123448–123464. [Google Scholar] [CrossRef]
- Otoum, Y.; Liu, D.; Nayak, A. DL-IDS: A Deep Learning–Based Intrusion Detection Framework for Securing IoT. Trans. Emerg. Telecommun. Technol. 2022, 33, e3803. [Google Scholar] [CrossRef]
- Ferrão, T.; Manene, F.; Ajibesin, A.A. Multi-Attack Intrusion Detection System for Software-Defined Internet of Things Network. Comput. Mater. Contin. 2023, 75, 4985–5007. [Google Scholar] [CrossRef]
- Krishnan, P.; Jain, K.; Buyya, R.; Vijayakumar, P.; Nayyar, A.; Bilal, M.; Song, H. MUD-Based Behavioral Profiling Security Framework for Software-Defined IoT Networks. IEEE Internet Things J. 2022, 9, 6611–6622. [Google Scholar] [CrossRef]
- Shafi, Q.; Basit, A.; Qaisar, S.; Koay, A.; Welch, I. Fog-Assisted SDN Controlled Framework for Enduring Anomaly Detection in an IoT Network. IEEE Access 2018, 6, 73713–73723. [Google Scholar] [CrossRef]
- Prabavathy, S.; Supriya, V. SDN Based Cognitive Security System for Large-Scale Internet of Things Using Fog Computing. In Proceedings of the 2021 International Conference on Emerging Techniques in Computational Intelligence, ICETCI 2021, Hyderabad, India, 25–27 August 2021; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2021; pp. 129–134. [Google Scholar]
- Lakpriya, R.A.K.; Rathsara, W.A.S.; Fernando, P.N.R.S.; Thenuwara, H.S.; Ruggahakotuwa, L.O.; Senarathne, A.N. Secure IoT Middleware Using SDN and Intent-Based Routing. In Proceedings of the 2022 IEEE 7th International conference for Convergence in Technology, I2CT 2022, Mumbai, India, 7–9 April 2022; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2022. [Google Scholar]
- Wang, B.; Sun, Y.; Xu, X. A Scalable and Energy-Efficient Anomaly Detection Scheme in Wireless SDN-Based MMTC Networks for IoT. IEEE Internet Things J. 2021, 8, 1388–1405. [Google Scholar] [CrossRef]
- Yang, R.; He, H.; Xu, Y.; Xin, B.; Wang, Y.; Qu, Y.; Zhang, W. Efficient Intrusion Detection toward IoT Networks Using Cloud–Edge Collaboration. Comput. Netw. 2023, 228, 109724. [Google Scholar] [CrossRef]
- Zeeshan, M.; Riaz, Q.; Bilal, M.A.; Shahzad, M.K.; Jabeen, H.; Haider, S.A.; Rahim, A. Protocol-Based Deep Intrusion Detection for DoS and DDoS Attacks Using UNSW-NB15 and Bot-IoT Data-Sets. IEEE Access 2022, 10, 2269–2283. [Google Scholar] [CrossRef]
- Javeed, D.; Gao, T.; Khan, M.T. Sdn-Enabled Hybrid Dl-Driven Framework for the Detection of Emerging Cyber Threats in Iot. Electronics 2021, 10, 918. [Google Scholar] [CrossRef]
- Qiu, H.; Dong, T.; Zhang, T.; Lu, J.; Memmi, G.; Qiu, M. Adversarial Attacks against Network Intrusion Detection in IoT Systems. IEEE Internet Things J. 2021, 8, 10327–10335. [Google Scholar] [CrossRef]
- Choudhary, S.; Kesswani, N. Analysis of KDD-Cup’99, NSL-KDD and UNSW-NB15 Datasets Using Deep Learning in IoT. Procedia Comput. Sci. 2020, 167, 1561–1573. [Google Scholar] [CrossRef]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Military Communications and Information Systems Conference (MilCIS), Canberra, ACT, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Tareq, I.; Elbagoury, B.M.; El-Regaily, S.; El-Horbaty, E.S.M. Analysis of ToN-IoT, UNW-NB15, and Edge-IIoT Datasets Using DL in Cybersecurity for IoT. Appl. Sci. 2022, 12, 9572. [Google Scholar] [CrossRef]
- Mirsky, Y.; Doitshman, T.; Elovici, Y.; Shabtai, A. Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection. arXiv 2018, arXiv:1802.09089. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the International Conference on Information Systems Security and Privacy, Funchal, Portugal, 22–24 January 2018. [Google Scholar]
- CSE-CIC-IDS2018. Available online: https://www.unb.ca/cic/datasets/ids-2018.html (accessed on 28 February 2025).
- Maciá-Fernández, G.; Camacho, J.; Magán-Carrión, R.; García-Teodoro, P.; Therón, R. UGR‘16: A New Dataset for the Evaluation of Cyclostationarity-Based Network IDSs. Comput. Secur. 2018, 73, 411–424. [Google Scholar] [CrossRef]
- Al-Hawawreh, M.; Sitnikova, E.; Aboutorab, N. X-IIoTID: A Connectivity-Agnostic and Device-Agnostic Intrusion Data Set for Industrial Internet of Things. IEEE Internet Things J. 2022, 9, 3962–3977. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Friha, O.; Hamouda, D.; Maglaras, L.; Janicke, H. Edge-IIoTset: A New Comprehensive Realistic Cyber Security Dataset of IoT and IIoT Applications for Centralized and Federated Learning. IEEE Access 2022, 10, 40281–40306. [Google Scholar] [CrossRef]
- Sarica, A.K.; Angin, P. A Novel SDN Dataset for Intrusion Detection in IoT Networks. In Proceedings of the 2020 16th International Conference on Network and Service Management (CNSM), Izmir, Turkey, 2–6 November 2020. [Google Scholar]
- Ahmed, M.; Byreddy, S.; Nutakki, A.; Sikos, L.F.; Haskell-Dowland, P. ECU-IoHT: A Dataset for Analyzing Cyberattacks in Internet of Health Things. Ad. Hoc. Networks 2021, 122, 102621. [Google Scholar] [CrossRef]
- Chatzoglou, E.; Kouliaridis, V.; Kambourakis, G.; Karopoulos, G.; Gritzalis, S. A Hands-on Gaze on HTTP/3 Security through the Lens of HTTP/2 and a Public Dataset. Comput. Secur. 2023, 125, 103051. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Gritzalis, S. Intrusion Detection in 802.11 Networks: Empirical Evaluation of Threats and a Public Dataset. IEEE Commun. Surv. Tutor. 2016, 18, 184–208. [Google Scholar] [CrossRef]
- Chatzoglou, E.; Kambourakis, G.; Kolias, C. Empirical Evaluation of Attacks against IEEE 802.11 Enterprise Networks: The AWID3 Dataset. IEEE Access 2021, 9, 34188–34205. [Google Scholar] [CrossRef]
- Almomani, I.; Al-Kasasbeh, B.; Al-Akhras, M. WSN-DS: A Dataset for Intrusion Detection Systems in Wireless Sensor Networks. J. Sens. 2016, 2016, 4731953. [Google Scholar] [CrossRef]
- A Realistic Cyber Defense Dataset (CSE-CIC-IDS2018). Available online: https://registry.opendata.aws/cse-cic-ids2018 (accessed on 14 March 2025).
- Breitenbacher, D.; Elovici, Y. N-BaIoT-Network-Based Detection of IoT Botnet Attacks Using Deep Autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar]
- Gopalan, S.S. Towards Effective Detection of Botnet Attacks Using BoT-IoT Dataset. Master’s Thesis, Rochester Institute of Technology, Rochester, NY, USA, 2021. Available online: https://repository.rit.edu/theses/10698 (accessed on 15 January 2025).
- Hekmati, A.; Grippo, E.; Krishnamachari, B. Large-scale Urban IoT Activity Data for DDoS Attack Emulation. In Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems (SenSys’21), Coimbra, Portugal, 15–17 November 2021; Association for Computing Machinery: New York, NY, USA, 2021; pp. 560–564. [Google Scholar] [CrossRef]
- Hamza, A.; Gharakheili, H.H.; Benson, T.A.; Sivaraman, V. Detecting Volumetric Attacks on loT Devices via SDN-Based Monitoring of MUD Activity. In Proceedings of the 2019 ACM Symposium on SDN Research (SOSR’19), San Jose, CA, USA, 3–4 April 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 36–48. [Google Scholar] [CrossRef]
- García, S.; Grill, M.; Stiborek, J.; Zunino, A. An Empirical Comparison of Botnet Detection Methods. Comput. Secur. 2014, 45, 100–123. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Adna, N. Anwar TON-IoT Telemetry Dataset: A New Generation Dataset of IoT and IIoT for Data-Driven Intrusion Detection Systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Neto, E.C.P.; Dadkhah, S.; Ferreira, R.; Zohourian, A.; Lu, R.; Ghorbani, A.A. CICIoT2023: A Real-Time Dataset and Benchmark for Large-Scale Attacks in IoT Environment. Sensors 2023, 23, 5941. [Google Scholar] [CrossRef]
- Sharmila, B.S.; Nagapadma, R. Quantized Autoencoder (QAE) Intrusion Detection System for Anomaly Detection in Resource-Constrained IoT Devices Using RT-IoT2022 Dataset. Cybersecurity 2023, 6, 41. [Google Scholar] [CrossRef]
- Garcia, S.; Parmisano, A.; Erquiaga, M.J. IoT-23: A Labeled Dataset with Malicious and Benign IoT Network Traffic, version 1.0.0; [Data set]. Zenodo, 2020. [Google Scholar] [CrossRef]
- Sarhan, M.; Layeghy, S.; Moustafa, N.; Portmann, M. NetFlow Datasets for Machine Learning-Based Network Intrusion Detection Systems. In Big Data Technologies and Applications; Springer: Cham, Switzerland, 2020. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).