1. Introduction
The Internet of Things (IoT) offers a new framework for the creation of heterogeneous and distributed networks and has become an increasingly ubiquitous forum for computing services. Over the last decade, several IoT applications have been introduced over various areas, including building and home automation, infrastructure and health care, transportation, manufacturing, and environmental monitoring [
1,
2,
3]. Nonetheless, due to the lack of adequate computing and storage resources for processing and storing large volumes of IoT data, it appears to follow a cloud-based architecture to address the security and resource sharing problems. Therefore, the entire implementation infrastructure must be secured from attacks that can obstruct IoT services and pose a threat to data privacy, credibility, or confidentiality.
The most widely used method for maintaining users’ confidentiality in the cloud environment is encryption. However, security problems dominate IoT-based applications [
3], prompting a major overhaul of established security choices leading many researchers to the evolution of modern techniques. Some of the leading security issues are user access control and maintaining the protection of cloud data. Within the following articles, we highlight some of the latest IoT and cloud computing approaches about access control systems, data protection, and privacy.
Cloud computing is among the most prominent IT technologies that have gained greater attention from government and industry since 2007. The cloud is composed of Service-Oriented Architecture (SOA), virtualization, variety of services, and deployment architecture [
4]. It offers services in a pay-as-you-use procedure. It provides many features like cost, scalability, on-demand access to use the resources effectively. Though the users know about cloud advantages, the challenging task is to provide strong security and storage mechanisms due to its internet-based storage and organization of data. Data to be stored in the cloud are in general sensitive and confidential, for example, Medical data and Military information [
4]. This requires increased security mechanisms to improve data privacy as well as strong mechanisms for authentication and access control.
Before outsourcing to the cloud, user data should be encrypted to achieve enhanced data security [
5]. To encrypt user data, many algorithms are proposed and implemented. The more preferable cryptographic algorithms are public key and secret key algorithms, which keep multiple copies of the same files whenever the data is shared among multiple users. The main issue here is when the key is obtained, all the protected files get leaked out. It is essential to produce the secret key for each user present in the data-sharing mechanism as a way to overcome this. The major concerns in access control-based data outsourcing are key management, and distribution [
6]. There are several access control mechanisms developed since the 1960s [
7]. Amongst these, Bell-la-palda [
8] and Biba [
8] are well-known access models. Access control models can be implemented in different ways, each with a different scope of control as well as a different set of operations and resources.
Attribute-based encryption (ABE) [
9] provides desirable solutions to access control problems. The two important variants in the ABE scheme are KP-ABE (Key-Policy Attribute-Based Encryption) [
10], whereby access policy is defined based on user’s keys as well as attributes used to encrypt the data and CP-ABE [
11,
12], in which the attributes are related with user’s secret key and access policies are related with the ciphertext. Compared to KP-ABE [
10], and fuzzy identity-based encryption [
13], CP-ABE [
14] is more appropriate in offering an efficient fine-grained access control. The access policy is embedded within the ciphertext in CP-ABE. However, the CP-ABE ciphertext is considered to be decrypted by all users. Therefore, there may be a chance to carry out the malicious activity by the authorized user, leading to the existence of insider attack [
11,
15]. To avoid this type of attack, the only option is to verify the data owner’s authentication. The most challenging task in the cloud would be detecting and preventing insider attacks because most of the records stored in the cloud are often sensitive. The Kandias et al. [
15] stated that people who served inside their working organization carry out 85% fraud. Approximately the insider theft reduces 5% of the annual revenue of an organization, and almost 330 cases of insider theft are recognized in 2010. Protecting the privacy of access policy and also providing security against insider attacks is therefore necessary.
1.1. Motivation
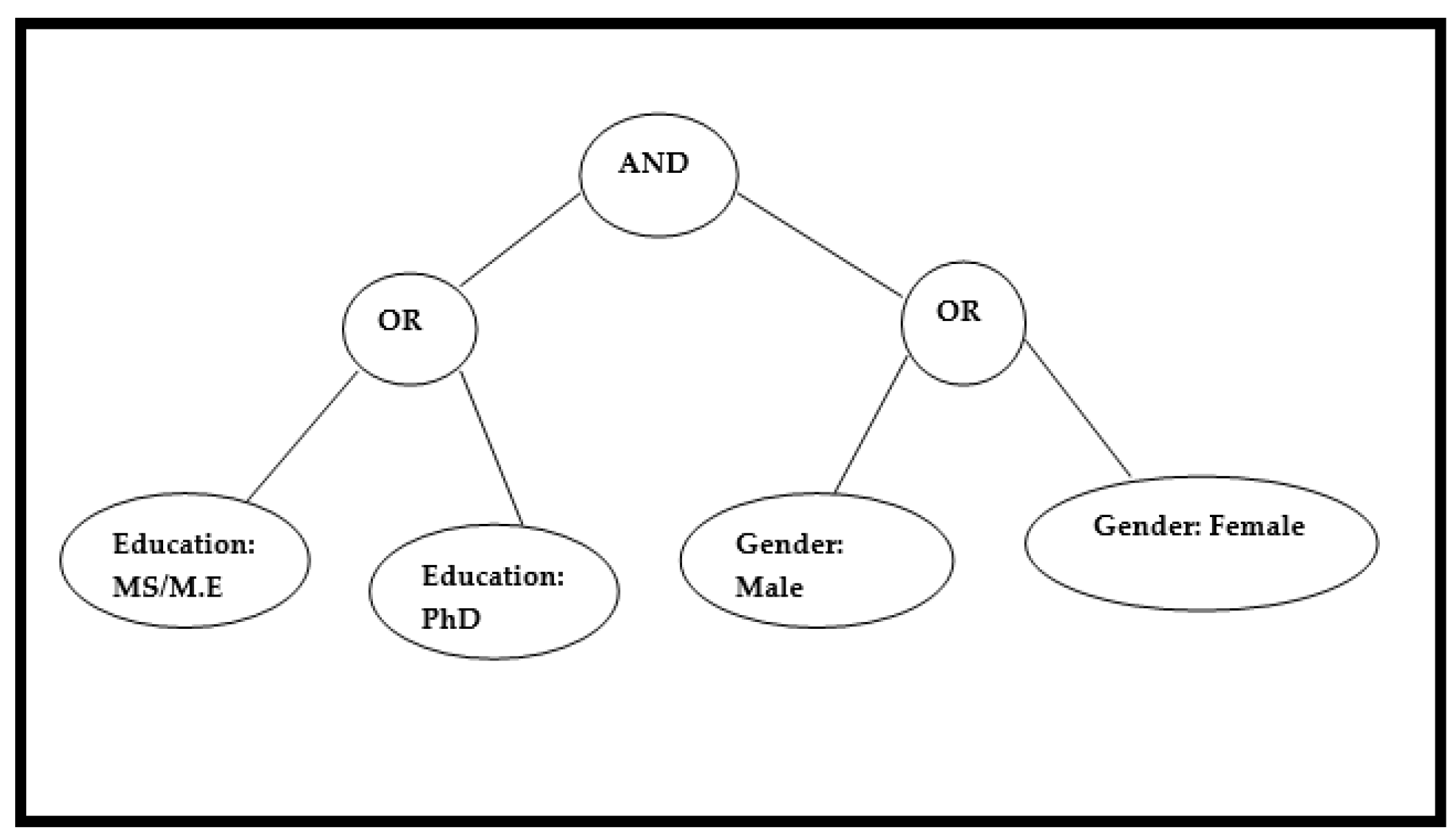
With an example,
Figure 1 and
Figure 2 thoroughly showed the notion of hidden access policy. In this case, the data owner should encrypt the data, which may then be accessed using the public access policy (see
Figure 1), while the confidential data is protected using the anonymized access policy technique (i.e.,
Figure 2).
Traditional CP-ABE methods have several benefits, such as confidentiality, authentication, and access control, although certain issues with access policy privacy, information security, malicious insiders, storage complexity, and interoperability with IoT enabled infrastructures.
1.2. Contributions
Based on the foregoing observations, the following are the key contributions of this article:
- (i)
We propose a new strategy CP-ABE scheme to enhance the security of user data and privacy of the user by hiding the access policy.
- (ii)
The storage overhead of this scheme is reduced by generating constant size ciphertext.
- (iii)
The identification and prevention from insider attack is achieved by utilizing the short signature scheme.
- (iv)
An enhancement to the IoT architecture has been designed in addition to making it a secure fine-grained access control system that also prevents insider attacks.
- (v)
A comparison study was conducted to describe the key components of ABE schemes that hide access policies, along with computational overhead analysis, security, and operational attributes of various access control schemes.
1.3. Paper Organization
Rest of the paper is structured as follows.
Section 2 describes the merits and demerits of the existing access control mechanism while
Section 3 discusses the proposed method’s mathematical background.
Section 4 describes the proposed scheme’s system model and
Section 5 discusses the explanation of the proposed method.
Section 6 deals with the implementation and performance assessment of the proposed method.
Section 7 discusses the proposed method’s security analysis and the conclusion is finally stated in
Section 8.
2. Related Works
As related works, we hereby mention works on Attribute-Based Encryption(ABE), Predicate Encryption (PE), Ciphertext-Policy Attribute-Based Encryption (CP-ABE) and CP-ABE with hidden access structure.
As an option to attain privacy and fine-grained access control, Attribute-Based Encryption (ABE) [
16] has been presented by Sahai and Waters [
13] where the encryption is based on both access policy and private keys. They made ciphertext to be associated with set of attributes. In these methods, the ciphertext size, encryption and decryption times vary linearly with respect to the complexity of access formula.
The inner product Predicate Encryption (IPE) is the basis of CP-ABE since the security mechanisms correlate to predicates in PE and attributes is correlated for ciphertext and Katz et al. [
17] implemented it. Pallavi [
18] et al. presented a new CP-ABE method which supports hidden access policy. They used inner product encryption along with attribute hiding to provide unlinkability as well as to improve the patient data privacy. TVX Phuong [
19] et al. presented a unique CP-ABE scheme based on two different processes. The first one is used to achieve only the constant ciphertext size. The second process is used to hide the access policy using Inner Product Encryption (IPE). However, the size of the ciphertext is dynamically changed. K. Frikken [
20] et al. introduced new protocols to preserve sensitive credentials as well as sensitive policies. They used three different protocols to hide the credential information from intruder. X Yao [
21] et al. introduced an anonymous based access control for the clouds. This method is not applicable for other applications because it is designed only for ciphertext. The cost of this scheme is high on user side.
Bethencourt [
22] et al. initiated the CP-ABE scheme that provided security against collusion attacks. Subsequently, Doshi and Jinwala [
23] et al. offered a novel CP-ABE scheme considered to be fully secure under attacks by Chosen Plaintext Attack (CPA) and Chosen Ciphertext Attack (CCA). The multi-authority ABE scheme has recently been studied in [
24,
25].
Helil [
26] et al. presented an innovative CP-ABE scheme with hidden attributes. This is the novel scheme to define the sensitive data sets (SDS) constraint. Here, they used Chinese wall security policy to construct the SDS constraint. Compared to existing methods, this method takes extra communication cost due to SDS constraint. The access control policy and the restriction set are divided and partial information is fed to the proxy server and SDS monitor to prevent commercial errors. Sabitha [
27] et al. introduced a new approach that preserves privacy through secure cloud hidden access policies for data sharing. Among these two [
26,
27] methods, first method is used to improve the privacy of user data and second one to prevent the insider attack. Compared to other attribute-based methods, this method has higher space complexity. Lixian Liu [
28] et al. adopted partially hidden access structure in their proposal. This method was mainly used to improve the privacy of electronic medical record system. Here also, since the ciphertext size is linear, space complexity is high. Balu [
29] et al. submitted a hidden access policy CP-ABE scheme by providing security using the assumption of Decisional Diffie-Hellman (DDH). Yadav [
30] et al. introduced a novel scheme which hides the access policy in ABE. Hiding the access policy is a significant contribution of certain applications like Medical, Military communications etc. The partial information of ciphertext is mainly hidden from user in order to improve the privacy. Zhong [
31] et al. introduced a decentralized multi-authority CP-ABE schemeagain using hidden access policy. The communication and computation cost of this scheme is low. Yang [
32] et al. presented a mechanism for fine-grained data access control with privacy conservation. The murmushash [
33] mehtod is used to improve the policy privacy but with higher communication overhead.
Zhang et al. [
34] introduced a new technique known match-then-re-encryption where prior to re-encryption, a matching phase was introduced. In addition, they anonumously checked whether or not the proxy could achieve a proxy re-encryption using separate re-encryption key and ciphertext components. This method was implemented using CP-ABPRE scheme based on Pairing-Based Crypto Library.
Zhang et al. [
35] introduced a Privacy-Aware S-Health (PASH) access control system, in which they used CP-ABE scheme with partially hiding the access policy. In this method, they have hidden the attribute value of access policies in SHR. The performance of this method is better compared to other methods in terms of access policy complexity, enciphering and deciphering time. Only problem here is they hidden the partial information.
Chen et al. [
36] proposed a new scheme named as match-then-decrypt in which the matching phase is introduced before decryption process. This scheme is performed by calculating a distinctive constituent in a ciphertext, the constituents were used to validate that if the secret key matches ciphertext-free hidden access policy. In terms of computation time, public key size, matching phase and decryption phase, this scheme is equated with the existing CP ABE scheme. They focus on decrpytion alone, not a phase of encryption.
The Group Attribute based access control for smart cars, big data, intelligent transportation are discussed from [
37,
38,
39,
40,
41].
The detailed comparison of various CP-ABE schemes with each and every methods techniques, features, security functionalities, computational cost is presented in
Table 1. From this debate, it appears that we will have issues with access policy privacy, user security, insider attack protection, and IoT interoperability. It is noted from this literature survey that the ciphertext size and number of pairing operations vary with regard to the number of attributes in existing ABE methods. This may reduce CP-ABE methods’ efficiency. The proposed CP-ABE method is novel in terms of
Offering encryption at first level of privacy using Ciphertext policy attribute based encryption;
Offering policy anonymization (SHA1) at second level;
Verifying the data owner authentication using BLS signature methods and thereby reducing the potential for insider attack and also;
Solving storage overhead problems by generating constant ciphertext size along with;
An enhanced IoT architecture has been designed which offers secured access control.
3. Preliminary
We present some facts related to groups with bilinear maps that are efficiently computable. The notations of the proposed method is mentioned in
Table 2.
3.1. Basic Concepts of Bilinear Map
The bilinear map is the tool based on pairing-based cryptography. To define the bilinear map, the following notations are used.
Let G and G be two multiplicative cyclic symmetric groups of the prime numbers R.
y is the generator of G.
The bilinear map e is defined as e: G * G→ G.
The properties of bilinear map are as listed below
Bilinearity: e(y, y) → e(y, y), ∀ y, y∈ G and m, n ∈.
Non-degeneracy: e(y, y) ≠ 1.
Computability: The bilinear map (e) is efficiently computable.
3.2. Access Structure
Definition of Attribute Access Structure: Considering A, A, ⋯, A as set of user attributes, the collection ⊆ 2 is monotone if ∀ B, C such that if B ∈ and B ⊆ C, then C ∈. An access structure is a collection of non-empty subsets of A, A, ⋯, A. The sets present in are known as authorized sets, otherwise unauthorized sets.
3.3. Boneh–Lynn–Shacham (BLS) Signature
The Boneh, Lynn and Shacham (BLS) [
42] introduced a simple and deterministic signature scheme. The outcome of the BLS scheme is often referred as short signatures. Although multiple signatures are adopted for cloud computing, it is not possible to verify the authentication of the data owner. We adopt BLS signature scheme for this proposed method to solve this issue. The main task of this BLS scheme is to verify the authenticity of the signer as valid or not. The short signature scheme has three different functions.
Key Generation: Randomly choose a number x from the interval of 0 to R − 1. The output of this function is the private key (x) and public verification key (k = y).
Signing: Given a message (m) and output of the key generation function, calculate = h (i.e., h = H (m)).
Verification: Given a message signature (h, ) and the public key (k), verify that (, y, h) is valid or not [i.e., k = y].
3.4. CP-ABE Definition
An encryption scheme based on a ciphertext-policy attribute consists of four sub basic algorithms: setup, encryption, keygen, and decryption.
CP-ABE-Setup (1): It produces a public key (PK) and a master secret key (MSK) for the given security parameter .
CP-ABE-Keygen (PK, MSK, S): It produces secret key (SKS) corresponding to a set of user attributes for the given public key (PK), master secret key (MSK).
CP-ABE-Encryption (PK, m, ): For given public key (PK), message (m), access structure (), it produces ciphertext, c.
CP-ABE-Decryption (PK, SK, c): It produces by the original message m for the given public key (PK), secret key (SKS) and ciphertext (c).
3.5. Threat Model and Goals
The proposed model addresses threats that are raised in following two levels.
Data Threat Level: It defines an entity which can perform data operations without proper data owner authentication, risking the confidentiality and privacy of the data received by a user.
Data and Access Policy Integrity Threat Level: It defines a malicious user/insider whose intent is to access the data and abuse the access rights while altering a data owner’s access policy.
We aim to achieve following security objectives in order to to make the system to be resistant against above mentioned threats
Fine-Grained Access Control:
Access policy of the proposed system is embedded in ciphertext to deliver access control. The access policy could be defined depending on user attributes. No one can easily change or recreate the key which is often used for offering an access control because the CP-ABE scheme is implemented from bilinear pairing.
Data Confidentiality:
The user can produce the public/secret key pairs based on bilinear pairing. Hence, only the authorized user gets information about the outsourced document. Therefore, no one can violate data confidentiality.
Authenticity and Integrity:
BLS verification verifies the authentication and integrity of the data outsourced by the data owner.
Privacy Preserving:
In our system, the encryption method offers first level of privacy and policy anonymization scheme (SHA1) offers second level. Hence, users will not know about other users making the proposed method as fully privacy preserving.
5. Process of Proposed Scheme
CP-ABE is one of the ABE most functional and effective version. The important feature of this scheme ensures security and fine-grained access control of outsourced data. However, in an earlier version of CP-ABE, together with the ciphertext, the access policy is provided as plaintext. This may reveal the attributes of user and lead to loss of user’s privacy. In the existing CP-ABE scheme, the authentication of the data owner and the integrity of outsourced data cannot be verified. To do this, we are introducing a new idea to check the data owner’s authentication and check the integrity of outsourced data through BLS short signature scheme. The proposed scheme offers protection against the insider data theft.
In order to improve access policy privacy, we applied policy anonymization scheme in the proposed system. For policy anonymization, as described in Algorithm 1, we used SHA1 hashing algorithm.
| Algorithm 1: Anonymization of the Access Policy |
![Mathematics 10 00068 i001]() |
Throughout an ABE scheme, all insiders are considered legitimate users to obtain the original message. Therefore, it may be possible to encode the generated plaintext again using a similar or dissimilar policy of access. The short signature method is used to identify the insider theft in order to avoid this situation. The two important tasks of the short signature method are to check data owner authentication and validate the reliability of shared data. Under an adaptive message attack, this method is proven secure.
- 1
Setup Algorithm
It is the responsibility of the key generation center to run this algorithm. The KGC selects two finite prime order R random cyclic symmetric groups G and G with y generator. Considering as a public security parameter, the bilinear map is defined as e: G * G→ G. Randomly, KGC chooses two exponents namely , ∈.
The public key PK and a master secret key MSK are generated on the basis of security parameter (
) and two exponents (
,
∈
).
- 2
Key Generation
This procedure runs the public key (PK), master secret key (MSK) and set of attributes (SA) as input, producing a secret key for the legitimate user (U
). Based on two different random numbers M
, M
∈
the secret key is generated.
- 3
Signing the Keygen
Data owner randomly chooses a number x from the interval, 0 to R − 1. The output of this function is the private key (x) and public verification key (k = y), where y is the generator of G
- 4
Encryption and Signing
The access policy is inserted into the ciphertext in our proposed system to provide access control. The access policy is expressed as an access structure as in
Figure 4. The threshold gates are defined in interior nodes and user credentials/attributes are defined in leaf nodes. The access policy has been anonymized by utilizing Algorithm 1. Before starting the process, the message P is encrypted that use the public key. The proposed encryption and signature scheme is explained in Algorithm 2 with collection of leaf nodes (L).
| Algorithm 2: Algorithm for data encryption |
![Mathematics 10 00068 i002]() |
The output of this function can be expressed as
The signature signing is done by BLS [
15] signature scheme. Let y be the generator of gap group G
with the finite prime order of R and a hash function (h). Using the hash function, the short signature can be calculated and attached with the shared ciphertext (Algorithm 3).
where
= = h (P
).
| Algorithm 3: Algorithm to generate a signature |
Function
(Function Signing (P, x)) Compute hash(P) Assign signature = h(P) |
Figure 5 illustrates the outsourced file structure in the cloud. The first column represents the unique identity of shared data, the second column represents the signature (P) and final column represents the ciphertext (CT).
- 5
Decryption and Verification
DecipherVerify (PK, SK, CT, , pk) → P, Success/Failure
The decryption operation is successful whenever the attributes of access policy, which is embedded inside the ciphertext is matched with the attribute of the cloud user. If it is not, then the cloud user cannot decrypt the ciphertext. The BLS short signature is used to check whether the data owner is authentic or not, in order to avoid the insider attack. The decryption process of our proposed method is shown in Algorithms 4 and 5.
| Algorithm 4: Algorithm for Decryption and Verification |
![Mathematics 10 00068 i003]() |
| Algorithm 5: Algorithm for Node Decryption |
![Mathematics 10 00068 i004]() |
Suppose leaf node l is not in L, access structure (SA) is satisfied by access tree. Now, decipher function will repeatedly compute and return e (y, y) = e(y, y). After that, the plaintext (P) can be easily calculated from the ciphertext (CT).
- 6
Signature Verification
This algorithm takes a message (P), computed hash (
) and the public key of users (pk) and verifies the signature as shown in Algorithm 6
| Algorithm 6: Algorithm to Verify the Signature |
![Mathematics 10 00068 i005]() |
5.1. Correctness Proof of Our Proposed Method
From Algorithm 4, e (D, C) can be written as,
substitute e (D, C) value in Algorithm 5.
Finally, substitute the value of e (D, C)/A in Algorithm 4.
5.2. Application Scenario for Proposed Method
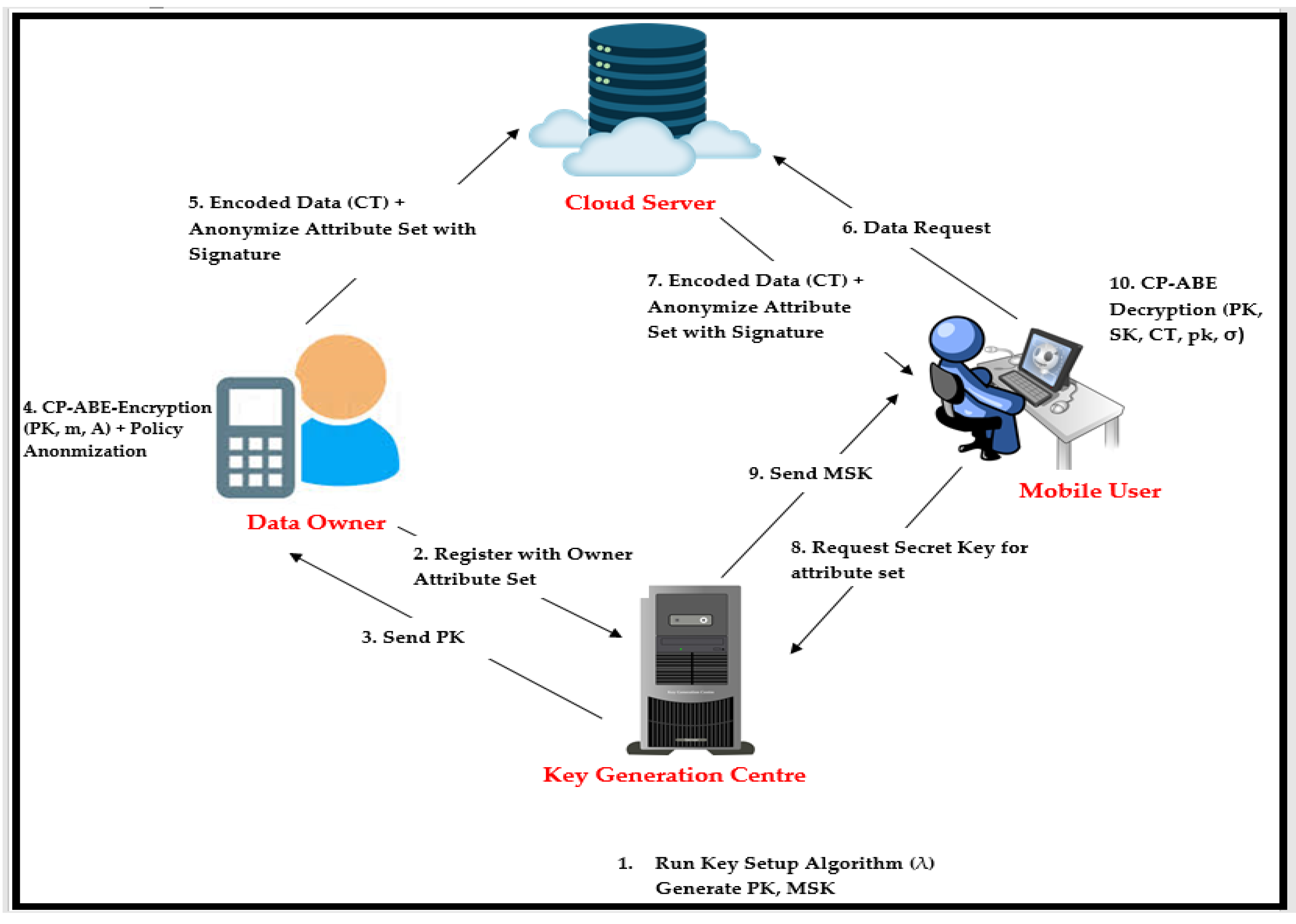
Figure 6 illustrates the scenario of Hospital Information System when data is shared between users (Patients, Insurance Companies, Government bodies etc.) and Smart Devices (Data Owners). The example scenario work flow gets started by key generation authorities to generate the Public key and Master Secret Key (MSK). Then, each smart device registers with key generation authorities by sending their attributes. After registration, KGC sends Public Key (PK) to the concerned smart device. With this key, the smart device can encrypt its data using Ciphertext Policy Attribute Based Encryption and also can hide the access policy using policy anonymization method. To verify the authenticity of smart devices, short signature scheme (BLS) is used. The encoded files, anonymized policy, signature is uploaded to the hospital service provider (HIS). At that point, the patients or smart devices send requests to HIS and in turn, HIS sends encrypted data, anonymized policy, and signature to the patients or smart devices. In order to view the encoded data, patients or smart devices need to complete the decoding process. During decoding, the order is matching of policy, matching of the data owner attributes and finally verifying the data owner signature. If anyone of these three matching is not satisfied, the opponents or users will not be able to view the original information of the data owner.
7. Security Evaluation
We analyze the impact of indistinguishable adaptive chosen-ciphertext attacks for our proposed method using a two-player game.
7.1. Indistinguishable Adaptive Chosen-Ciphertext Attack (IND-CCA2)
The security model of the proposed CP-ABE method against an indistinguishable adaptive chosen ciphertext attack (IND-CCA2) is explained by an activity between an adversary (AD) and a challenger (CHR), as below:
Init: The dare access structure, CAS*, is declared by an adversary (AD).
Setup: A challenger (CHR) selects a public security parameter, , processes the setup algorithm, distributes a public key (PK) to the adversary (AD), and secretly saves the master secret key (MSK). Two random exponents, , ∈ are selected.
Phase 1: The adversary (AD) creates a polynomial time request and the challenger (CHR) provides consistent answers.
- (a)
Secret Key Request: The adversary (AD) creates a continuous request to produce a secret key, SK, with a set of user attributes, W, W,⋯,W∈ A. The challenger (CHR) replies with the secret key, SK, by running the KeyGen algorithm. A number, r, is randomly chosen and matched to every attribute of j ∈ A. The secret key can be calculated as D = y * H W (j), D’ (j) = y and distributed to the adversary (AD).
- (b)
Decipher Request: The adversary (AD) selects a ciphertext randomly decrypted by the access structure (CAS*). The challenger (CHR) then runs the DecipherVerify algorithm to decipher the ciphertext using the SK The resultant plaintext is sent to the adversary (AD).
Challenge: The adversary (AD) submits two messages of equal length, P, P, to the challenger (CHR). The CHR chooses a random number, ∈ 0, 1, and encrypts the message, P, using the challenge access structure, CAS*. The resultant ciphertext (CT*) is sent to the AD.
Phase 2: Similar to Phase 1, the restriction here is that the submitted ciphertext, CT, is not identical to the generated ciphertext, CT*.
Guess: The adversary (AD) outputs a guess, of .
At the end of this game, we say that an adversary has succeeded if
==
. The advantage of this game is defined as
From this two-player game, we conclude that the proposed system offers security against an indistinguishable adaptive chosen-ciphertext attack (IND-CCA2).
7.2. Security against Secure Signatures
Definition 1 (Security of Signatures).
A counterfeiter (CF) [50] may be expected to (t, Q, Q, ϕ) break the BLS scheme σ { Keygen, Sign, Verify} using an adaptive chosen message attack if, after several Q enquiries to the hash model with t processing time, it produces an output as a valid counterfeiter with the probability of a minimum ϕ. A signature method (t, Q, Q, ) is said to be secure if no counterfeiter can break the (t, Q, Q, ) scheme.
Proof. In the short signature method, we need to make a hash query (Q) before signing the message, P. □
Suppose a counterfeiter (CF) (t, Q, Q, ) breaks the BLS method by means of an adaptive chosen message attack. This can be explained by a two-player game against an adversary (AD) and thecounterfeiter (CF).
Step 1: The counterfeiter (CF) runs a SignKey algorithm and produces a public key (pk) and a secret key (sk). The public key is forwarded to the adversary (AD).
Step 2: The adversary (AD) makes a continuous polynomial time request (t) and the counterfeiter (CF) answers hash and signature enquiries.
- (a)
Hash enquiries (Q): The adversary makes a request on a hash oracle model on messages P for 1 ≤ k ≤ Q. The counterfeiter (CF) responds with responses already prepared for hash queries (X, X,⋯, X) on P.
- (b)
Signature Enquiries (Q): The adversary (AD) makes a request on a signature oracle model for the given messages, P = (p, p,⋯, p) ∈ 0, 1*, using the public key (pk). The counterfeiter (CF) responds with a signature (→ Signing (P, sk) to the adversary (AD).
Step 3: Finally, the counterfeiter (CF) halts the process, gives the message signature pair as (P, ), verifies the validity of (P, , pk), and outputs (P, , X, X,⋯, X). The counterfeiter, however, will fail our BLS method.
It is evident from the two-player game that any advantage an adversary has is small. Therefore, the proposed CP-ABE method has shown itself secure against the adaptive chosen message attack, since no counterfeiter (CF) (t, Q, Q, ) can break the system for signature (Q) enquiries. In case the counterfeiter (CF) does manage to break the system, the adversary still has a advantage.
7.3. Threat Model for AI enabled IoT Devices
7.3.1. Case 1: Mismatching of Attributes
In this scenario, the patient acts as intruder trying to access the encrypted information of medical data. The intruder may pass all the intermediate levels except attribute authorization process from KGC. However, KGC gives authorization only to the attribute matched user. Otherwise, proposed system denies the access for intruder is shown in
Figure 16.
7.3.2. Case 2: Hash Value of Access Policy Mismatching
In
Figure 17, we depict the scenario where the intruder may overcome the attribute checking process but fail to match the hash value of the access policy. This is possible due to the policy anonymization method which helps to achieve two important security properties such as confidentiality and authentication.
7.3.3. Case 3. Data Owner Verification
Figure 18 setup explains verifying the authenticity of the data owner or AI enabled IoT devices. Let us consider the scenario in which intruder has cracked the hash value and access policy matching of our proposed system. To handle such a case, we have further imposed additional security mechanism to verify the authenticity of the data owner using the BLS short signature scheme. This permits only the authorized user to run the verification function of BLS scheme and hence ensures privacy of the data owner.