Provably Secure Linearly Homomorphic Aggregate Signature Scheme for Electronic Healthcare System
Abstract
:1. Introduction
1.1. Related Work
1.2. Our Contributions
- A security model of the LHAS scheme is proposed. The security model guarantees an aggregate signature is valid if and only if all the individual signatures generating the aggregate signature are valid;
- An aggregate signature scheme based on a linearly homomorphic signature is proposed, which makes the scheme have both a linearly homomorphic property and an aggregate property, and realizes double data compression. The transmission efficiency is further improved and the storage cost of medical data in EHS is reduced.
- The security of our LHAS scheme is rigorously presented under the proposed security model. Moreover, through the analysis of comparative performance, we show that the scheme is effective in reducing transmission and storage overhead.
1.3. Organization
2. Preliminaries
2.1. Bilinear Pairing
- Bilinear: for all and , .
- Non-degenerate: , where is the identity element of .
- Computable: for all , is efficiently computable.
2.2. Complexity Assumptions
3. Outline of Linearly Homomorphic Aggregate Signature Schemes
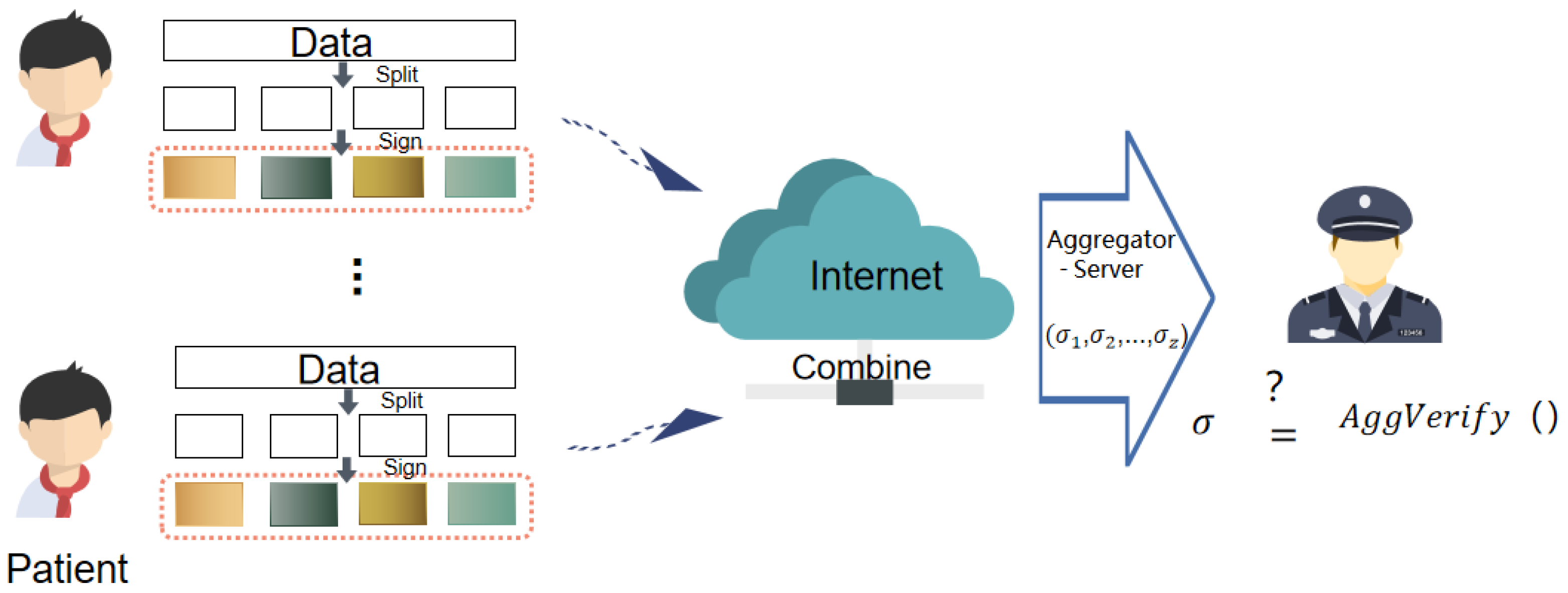
3.1. Definition of LHAS Schemes
- Setup: Given a security parameter k and output the system parameters ;
- KeyExtract: Given the , output a public key and a secret key . ( is the input to the following algorithms);
- Sign: Given a secret key , a file identifier , a vector , outputs a signature ;
- Combine: Given a public key , a file identifier and a set of tuples , where is the signature on vector , outputs a signature on the linear combination without knowledge of ;
- Verify: Given a public key , a file identifier , a signature and a vector , outputs either 1 or 0 ( or );
- Agg: Given an aggregating subset of users , and the signatures on the linear combination (), outputs the aggregate signature;
- AggVerify: Given an aggregating subset U of l aggregating signers with their public keys, an aggregate signature on the vectors () with file identifiers, where vectors is a set of basis of subspaces (), outputs if the aggregate signature is valid, or otherwise.
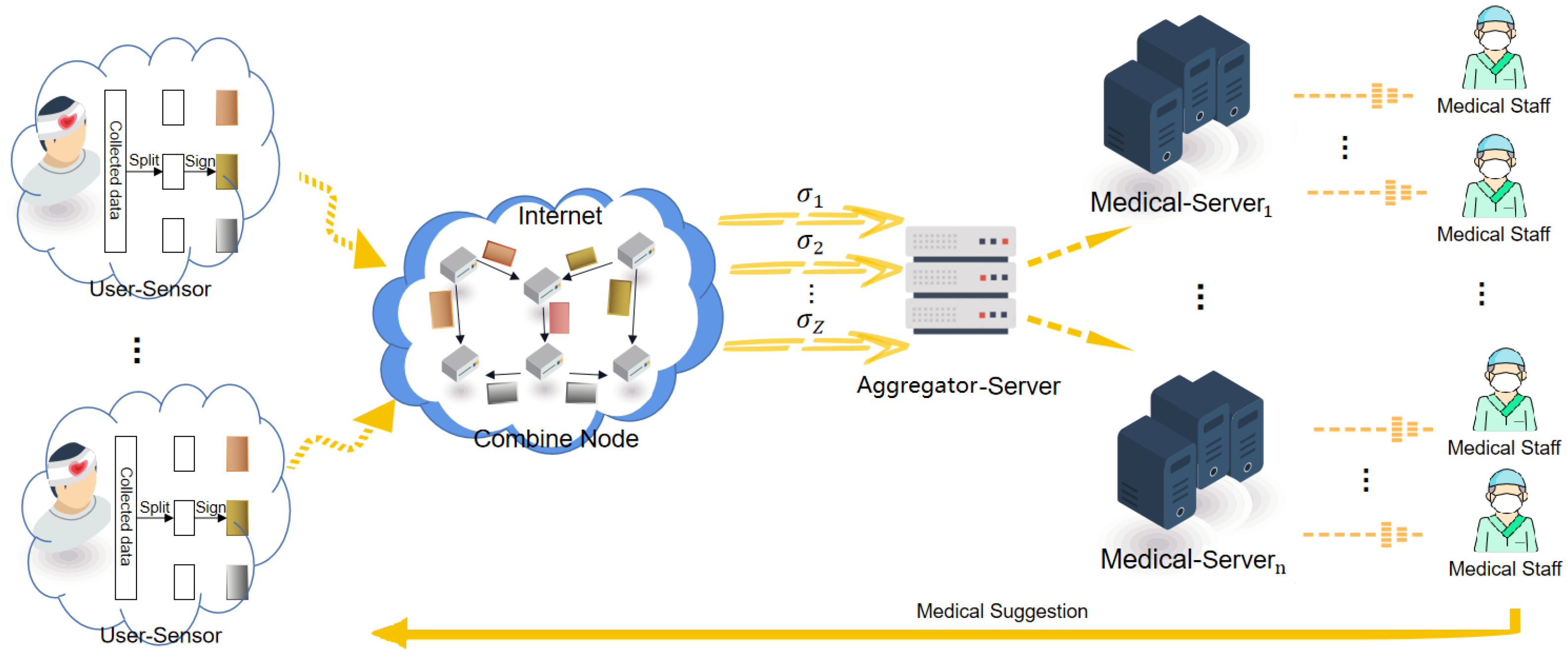
3.2. System Model of LHAS-EHS
- Health-Center: The Health-Center generates the system public parameters by running the algorithm Setup. In the initialization phase, it generates the required public-private key pairs for User-Sensor and Medical-Server;
- User-Sensor: The User-Sensor as the source node connects the patient’s body to obtain various medical information. It is a resource-limited device, which belongs to a care district. The node divides the collected data packet into m vectors and signs them. Then, the node loads vectors and related signature information into a data packet. After processing the collected data, the node sends data packets to the neighbor nodes, the Combine-Node;
- Combine-Node: The nodes combine all data packets and the corresponding signatures with the coding coefficient. Then, the nodes forward merged data packet to the Aggregator-Server;
- Aggregator-Server: A device that is honest but curious and has certain calculation and communication capabilities. The device can randomly obtain a Medical-Server’s public key, collect and aggregate a set of the merged data packets. Finally, send the generated aggregate signature to the destination Medical-Server;
- Medical-Server: A device that has strong computing power and storage space can process all medical data collected by the User-Sensors. The device works as a designated verifier who can verify the aggregate signature using its secret key. If the aggregate signature can pass the verification, the Medical-Server provides the patients’ data information to the medical staff. Then, the medical staff will provide corresponding medical suggestions to patients according to the data received.
3.3. Security Model
- -
- The basic signature scheme involved is existentially unforgeable against adaptive chosen message attacks (EUF-CMA secure);
- -
- The security of aggregate algorithm should stand up against all kinds of coalition attacks.
- Setup: When inputting the security parameter k, the challenger generates the system parameters . Furthermore, randomly generates the public-secret key pair for a designated verifier, then gives the and ;
- Queries: can access the following queries:
- –
- Secret key request query: requests such a query, generates the key pairs by running the algorithm Key Extract, then returns to ;
- –
- AggVerify request query: On receiving such a query, responds whether is valid by running algorithm AggVerify. Where subspace is depicted as a set of basis vectors , ;
- Forge: Finally, outputs its forgery
- -
- The aggregate signature is valid;
- -
- At least one single signature is invalid.
4. The Linearly Homomorphic Aggregate Signature Scheme
- Setup: Given a security parameter k, Health-Center runs this algorithm:
- –
- Generate a bilinear group , where . are two multiplicative cyclic groups with the same prime order p;
- –
- Generate a generator h in ;
- –
- Let and be two collision resistant hash functions.
The system parameters , where N is the maximum dimension of a subspace. - KeyExtract: A specific User-Sensor picks randomly, then computes . The sensor’s public-secret key pair is ;
- Sign: For a specific User-Sensor with the secret key , the node first divides the collected medical data into m packets, where each packet can be regarded as a m-dimensional vector =. Let = () denote the subspace with the file identifier , where is any basis of . Then the node can compute the signature as the following:
- Combine: Given a specific User-Sensor with the public key , a file identifier and , where is the coefficient and is the signature on vector , then the Combine-Node computes:
- Verify: Given a signature , vectors = coefficients and a specific User-Sensor’s public key u, compute , and denote , then check if the equation,holds or not. If it holds, then accept; otherwise, reject.
- Agg: Let be the aggregating subset of User-Sensors, and let . Every User-Sensor with public key generates the signature on the linear combination (), where vectors are a set of the basis of an -dimensional subspace (). Moreover, denote X as the public key of a Medical-Server (), the designated verifier. The Aggregator-Server computes:The aggregate signature is .
- AggVerify: Given an aggregating subset U of l aggregating User-Sensors, the signers, with public key , an aggregate signature on the vectors () with file identifiers , where vectors is a set of basis of the -dimensional subspace and = . The Medical-Server with private key x accepts if the following equation holds:whereCorrectness: If the combine signature is generated on the specific User-Sensor with public key , then the following equations hold for :So,Then,
5. Security Analysis
5.1. The Security of Basic Signature Scheme
- if the corresponding tuple already exists in the list, output ;
- otherwise,
- –
- if , randomly choose , and set , ;
- –
- else, choose at random, and set , ;
- –
- add to the list, ;
- output .
- Generate a file identifier randomly. Seek or make H queries get and , .
- –
- if , then abort;
- –
- else, set , compute ;
- output and .
- if , then abort;
- else set , compute , if , then abort;
- else compute , and output .
5.2. The Security of Aggregate Signature Algorithm
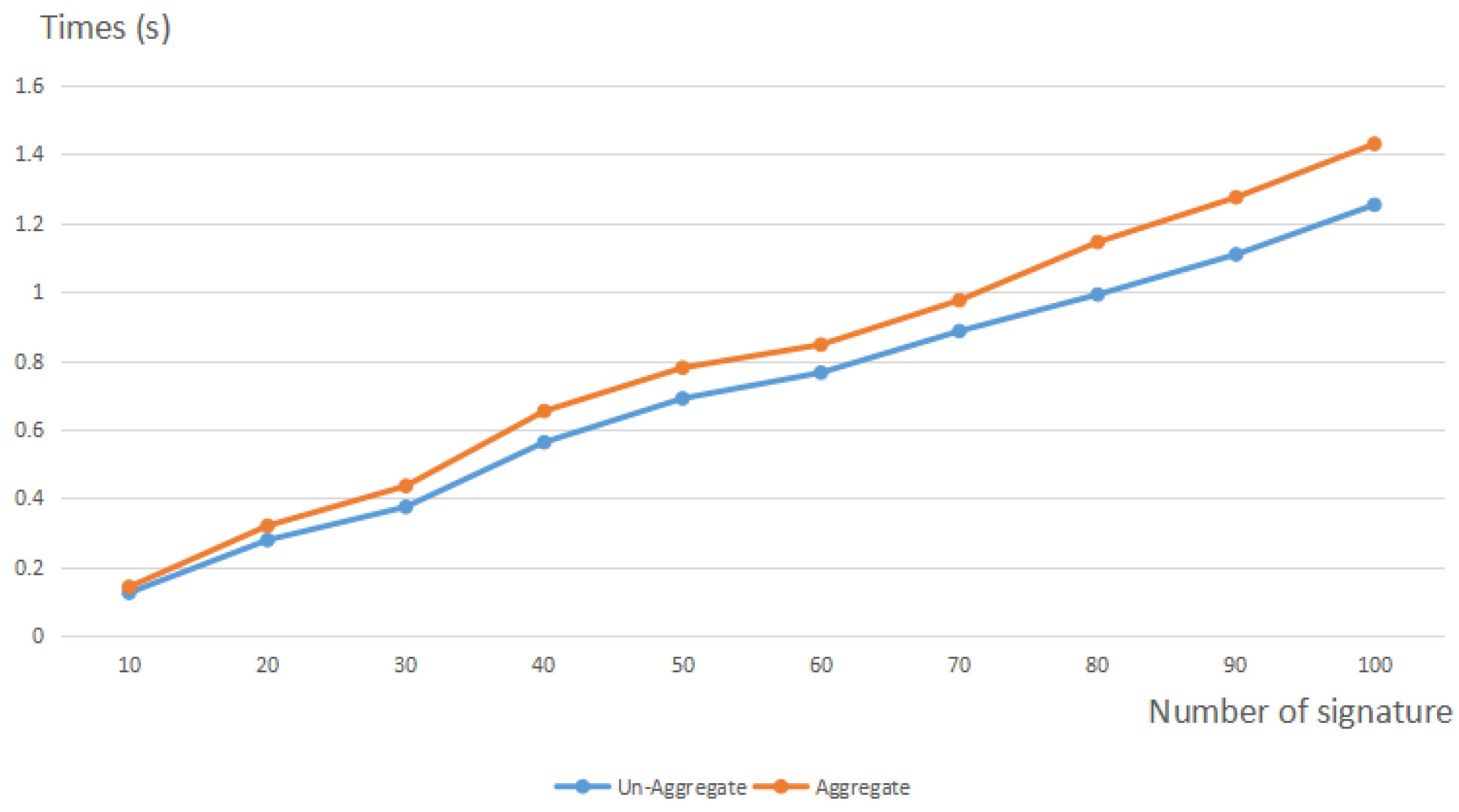
6. Performance Analysis
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ahlswede, R.; Cai, N.; Li, S.Y.; Yeung, R.W. Network information flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216. [Google Scholar] [CrossRef]
- Johnson, R.; Molnar, D.; Song, D.; Wagner, D. Homomorphic signature schemes. In Proceedings of the Cryptographers’ Track at the RSA Conference, San Jose, CA, USA, 18–22 February 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 244–262. [Google Scholar]
- Boneh, D.; Freeman, D.; Katz, J.; Waters, B. Signing a linear subspace: Signature schemes for network coding. In Proceedings of the International Workshop on Public Key Cryptography, Irvine, CA, USA, 18–20 March 2009; Springer: Berlin/Heidelberg, Germany, 2009; pp. 68–87. [Google Scholar]
- Zhang, Y.; Jiang, Y.; Li, B.; Zhang, M. An efficient identity-based homomorphic signature scheme for network coding. In Proceedings of the International Conference on Emerging Internetworking, Data & Web Technologies, Wuhan, China, 10–11 June 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 524–531. [Google Scholar]
- Wu, B.; Wang, C.; Yao, H. A certificateless linearly homomorphic signature scheme for network coding and its application in the IoT. Peer-to-Peer Netw. Appl. 2021, 14, 852–872. [Google Scholar] [CrossRef]
- Attrapadung, N.; Libert, B. Homomorphic network coding signatures in the standard model. In Proceedings of the International Workshop on Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 17–34. [Google Scholar]
- Cheng, C.; Lee, J.; Jiang, T.; Takagi, T. Security analysis and improvements on two homomorphic authentication schemes for network coding. IEEE Trans. Inf. Forensics Secur. 2016, 11, 993–1002. [Google Scholar] [CrossRef]
- Chang, J.; Ji, Y.; Shao, B.; Xu, M.; Xue, R. Certificateless homomorphic signature scheme for network coding. IEEE/ACM Trans. Netw. 2020, 28, 2615–2628. [Google Scholar] [CrossRef]
- Li, Y.; Zhang, F.; Sun, Y. Lightweight certificateless linearly homomorphic network coding signature scheme for electronic health system. IET Inf. Secur. 2021, 15, 131–146. [Google Scholar] [CrossRef]
- Al-Zubaidie, M.; Zhang, Z.; Zhang, J. REISCH: Incorporating lightweight and reliable algorithms into healthcare applications of WSNs. Appl. Sci. 2020, 10, 2007. [Google Scholar] [CrossRef] [Green Version]
- Du, H.; Wen, Q.; Zhang, S. An efficient certificateless aggregate signature scheme without pairings for healthcare wireless sensor network. IEEE Access 2019, 7, 42683–42693. [Google Scholar] [CrossRef]
- Arshad, K.; Imran, M.A. Wireless Sensing for Human Activity Recognition Using USRP. In Proceedings of the Body Area Networks: Smart IoT and Big Data for Intelligent Health Management: 16th EAI International Conference, BODYNETS 2021, Virtual Event, 25–26 October 2021; Springer Nature: Berlin, Germany, 2022; Volume 420, p. 52. [Google Scholar]
- Shen, L.; Ma, J.; Liu, X.; Miao, M. A provably secure aggregate signature scheme for healthcare wireless sensor networks. J. Med. Syst. 2016, 40, 1–10. [Google Scholar] [CrossRef]
- Verma, G.K.; Singh, B.; Singh, H. Bandwidth efficient designated verifier proxy signature scheme for healthcare wireless sensor networks. Ad Hoc Netw. 2018, 81, 100–108. [Google Scholar] [CrossRef]
- Deng, L.; Yang, Y.; Gao, R. Certificateless designated verifier anonymous aggregate signature scheme for healthcare wireless sensor networks. IEEE Internet Things J. 2021, 8, 8897–8909. [Google Scholar] [CrossRef]
- Li, Q.; Zhu, H.; Xiong, J.; Mo, R.; Ying, Z.; Wang, H. Fine-grained multi-authority access control in IoT-enabled mHealth. Ann. Telecommun. 2019, 74, 389–400. [Google Scholar] [CrossRef]
- Li, Q.; Xia, B.; Huang, H.; Zhang, Y.; Zhang, T. TRAC: Traceable and revocable access control scheme for mHealth in 5G-enabled IIoT. IEEE Trans. Ind. Inform. 2021. [Google Scholar] [CrossRef]
- Dong, J.; Curtmola, R.; Sethi, R.; Nita-Rotaru, C. Toward secure network coding in wireless networks: Threats and challenges. In Proceedings of the 2008 4th Workshop on Secure Network Protocols, Orlando, FL, USA, 19 October 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 33–38. [Google Scholar]
- Wang, F.; Hu, Y.; Wang, B. Lattice-based linearly homomorphic signature scheme over binary field. Sci. China Inf. Sci. 2013, 56, 1–9. [Google Scholar] [CrossRef] [Green Version]
- Boneh, D.; Freeman, D.M. Linearly homomorphic signatures over binary fields and new tools for lattice-based signatures. In Proceedings of the International Workshop on Public Key Cryptography, Taormina, Italy, 6–9 March 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 1–16. [Google Scholar]
- Boneh, D.; Gentry, C.; Lynn, B.; Shacham, H. Aggregate and verifiably encrypted signatures from bilinear maps. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Warsaw, Poland, 4–8 May 2003; Springer: Berlin/Heidelberg, Germany, 2003; pp. 416–432. [Google Scholar]
- Bellare, M.; Namprempre, C.; Neven, G. Unrestricted aggregate signatures. In Proceedings of the International Colloquium on Automata, Languages, and Programming, Wroclaw, Poland, 9–13 July 2007; Springer: Berlin/Heidelberg, Germany, 2007; pp. 411–422. [Google Scholar]
- Wen, Y.; Ma, J.; Huang, H. An aggregate signature scheme with specified verifier. Chin. J. Electron. 2011, 20, 333–336. [Google Scholar]
- Gentry, C.; Ramzan, Z. Identity-based aggregate signatures. In Proceedings of the International Workshop on Public Key Cryptography, New York, NY, USA, 24–26 April 2006; Springer: Berlin/Heidelberg, Germany, 2006; pp. 257–273. [Google Scholar]
- Herranz, J. Deterministic identity-based signatures for partial aggregation. T Comput. J. 2006, 49, 322–330. [Google Scholar] [CrossRef] [Green Version]
- Shim, K.A. An ID-based aggregate signature scheme with constant pairing computations. J. Syst. Softw. 2010, 83, 1873–1880. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, F. A new certificateless aggregate signature scheme. Comput. Commun. 2009, 32, 1079–1085. [Google Scholar] [CrossRef]
- Liu, J.; Wang, L.; Yu, Y. Improved security of a pairing-free certificateless aggregate signature in healthcare wireless medical sensor networks. IEEE Internet Things J. 2020, 7, 5256–5266. [Google Scholar] [CrossRef]
- Zhao, Y.; Hou, Y.; Wang, L.; Kumari, S.; Khan, M.K.; Xiong, H. An efficient certificateless aggregate signature scheme for the Internet of Vehicles. Trans. Emerg. Telecommun. Technol. 2020, 31, e3708. [Google Scholar] [CrossRef]
- Zuo, W.; Liu, Y. A Provably Secure Certificate-Based Aggregate Signature Scheme. In Proceedings of the 2020 IEEE 6th International Conference on Computer and Communications (ICCC), Chengdu, China, 4 December 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 2099–2103. [Google Scholar]
- Verma, G.K.; Singh, B.; Kumar, N.; Kaiwartya, O.; Obaidat, M.S. PFCBAS: Pairing free and provable certificate-based aggregate signature scheme for the e-healthcare monitoring system. IEEE Syst. J. 2019, 14, 1704–1715. [Google Scholar] [CrossRef]
- Li, T.; Wang, H.; He, D.; Yu, J. Permissioned Blockchain-Based Anonymous and Traceable Aggregate Signature Scheme for Industrial Internet of Things. IEEE Internet Things J. 2021, 8, 8387–8398. [Google Scholar] [CrossRef]
- Zhang, F.; Shen, L.; Wu, G. Notes on the security of certificateless aggregate signature schemes. Inf. Sci. 2014, 287, 32–37. [Google Scholar] [CrossRef]
- Shen, L.; Ma, J.; Liu, X.; Wei, F.; Miao, M. A secure and efficient ID-based aggregate signature scheme for wireless sensor networks. IEEE Internet Things J. 2016, 4, 546–554. [Google Scholar] [CrossRef]
- Shen, L.; Ma, J.; Miao, Y.; Liu, H. Provably secure certificateless aggregate signature scheme with designated verifier in an improved security model. IET Inf. Secur. 2019, 13, 167–173. [Google Scholar] [CrossRef]
- Xie, Y.; Xu, F.; Li, X.; Zhang, S.; Zhang, X.; Israr, M. EIAS: An efficient identity-based aggregate signature scheme for WSNS against coalition attack. CMC-Comput. Mater. Contin. 2019, 59, 903–924. [Google Scholar] [CrossRef]
- Wu, G.; Zhang, F.; Shen, L.; Guo, F.; Susilo, W. Certificateless aggregate signature scheme secure against fully chosen-key attacks. Inf. Sci. 2020, 514, 288–301. [Google Scholar] [CrossRef]
- Zhang, P.; Yu, J.; Wang, T. A homomorphic aggregate signature scheme based on lattice. Chin. J. Electron. 2012, 21, 701–704. [Google Scholar]
- Jing, Z. An efficient homomorphic aggregate signature scheme based on lattice. Math. Probl. Eng. 2014, 2014. [Google Scholar] [CrossRef]
- Boneh, D.; Lynn, B.; Shacham, H. Short signatures from the Weil pairing. In Proceedings of the International Conference on the Theory and Application of Cryptology and Information Security, Singapore, 6–10 December 2001; Springer: Berlin/Heidelberg, Germany, 2001; pp. 514–532. [Google Scholar]

| CPU | Intel(R) Core(TM) it-4200H CPU @ 2.8 GHz |
| Operation System | 64-bit Ubuntu 20.04 |
| Library | PyCharm, PBC Library, Charm-Crypto Library |
| Notation | Definition |
|---|---|
| Aggregate | aggregate scheme |
| Un-Aggregate | un-aggregate scheme |
| the overall length of { ,,…, } | |
| the computation cost of scalar multiplication calculation in or | |
| the computation cost of exponentiation calculation in or | |
| the computation cost of paring operation in | |
| the computation cost of map-to-point |
| Un-Aggregate | Aggregate | |
|---|---|---|
| Combine-Node → Aggregator-Server | ||
| Aggregator-Server→ Medical-Server |
| Un-Aggregate | Aggregate | |
|---|---|---|
| Medical-Server.Verify | 2+)+ | +++ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gu, Y.; Shen, L.; Zhang, F.; Xiong, J. Provably Secure Linearly Homomorphic Aggregate Signature Scheme for Electronic Healthcare System. Mathematics 2022, 10, 2588. https://doi.org/10.3390/math10152588
Gu Y, Shen L, Zhang F, Xiong J. Provably Secure Linearly Homomorphic Aggregate Signature Scheme for Electronic Healthcare System. Mathematics. 2022; 10(15):2588. https://doi.org/10.3390/math10152588
Chicago/Turabian StyleGu, Yanyan, Limin Shen, Futai Zhang, and Jinbo Xiong. 2022. "Provably Secure Linearly Homomorphic Aggregate Signature Scheme for Electronic Healthcare System" Mathematics 10, no. 15: 2588. https://doi.org/10.3390/math10152588






