Securing IoT-Empowered Fog Computing Systems: Machine Learning Perspective
Abstract
:1. Introduction
2. Information Sources
- IEEE eXplore
- ACM Digital Library
- Wiley Interscience
- ScienceDirect
- Springer
- Semantic Scholar
- Bibliographies of primary research to find relevant articles
- Reports on technical issues
- Edited books and textbooks
2.1. Search Criteria
(“Fog Computing” OR “Machine Learning (ML)”) (“Fog Computing” or “Security”) AND (“Fog Computing” OR “Attacks” OR “Fog Application” OR “Architecture”)
Restrictions
- The journal and conference are included in the index.
- A survey or review of research is introduced in the publications.
- The papers are prepared in the English language.
- The papers follow the peer-reviewed process.
2.2. Extraction of Data
- All of the 154 publications were evaluated by one of the writers to extract the necessary information.
- A random sample of data extraction was used to ensure that the data extraction was consistent.
- All disagreements that arose throughout the cross-checking process were dealt with in a series of meetings.
3. Fundamentals of IoT Security and Privacy
3.1. Concerns
- Sensation module: Hackers are able to cause considerable harm when access is granted to devices including healthcare sensors and pacemakers [16]. As a result, (1) unauthorized data acquisition, (2) device malware of unauthorized access, (3) malware for incorrect data transmission, (4) Denial of Service (DoS) attacks, and (5) unauthorized information acquisition are all potential risks in the sensation layer.
- Networking module: The network’s manageability, scalability, and availability are critical for IoT deployment. IoT devices become ineffective if monitoring applications cannot obtain data in a time-sensitive manner. It is fairly usual to attack the network by transmitting a large amount of data all at once to overload the network and allow for DoS attacks.
- Service module: The service module functions as a link for the hardware module and the application module. Important functions, including information management and device management, are impacted by an attack on the service module, resulting in end users not being served. Service module security includes data integrity, user authentication, communication security, and access control.
- Application module: The application module is the most vulnerable aspect of the IoT network since it sits at the IoT-Fog-cloud’s top-of-stack and serves as a gateway to all the underneath modules. Specifically, the gateway reflects the application module via which IoT devices can be accessed to initialize security attacks. If the interface’s authentication and authorization methods are compromised, the ripple effects may extend to the edge. Because attackers might obtain sensitive information through phishing or related attacks, the end-user is a prospective attack method. In addition, SQL injection, default credentials, cross-site scripting, and insecure password recovery techniques are common on the web and application interfaces. The Open Web Application Security Project (OWASP) summarizes the Top 10 IoT vulnerabilities [17]. A detailed description of corresponding vulnerability is shown in Figure 2 (Source: https://owasp.org/www-project-internet-of-things/ (accessed on 2 February 2022)).

IoT Privacy Concerns
- Identification: The threat of identifying an identifier, such as a name and location, with an individual is known as identification.
- Localization: The vulnerability of identifying and registering a person’s whereabouts in space-time coordinates is known as localization. Most IoT devices collect information which might disclose illnesses, vacation plans, work schedules, and personal details.
- Profiling: Profiling is the danger of leveraging data from IoT devices to categorize individuals into groups. It might result in pricing discrimination, unwanted advertising, social engineering, or erroneous automated choices.
- Interaction and presentation that infringes on privacy: This is the risk of conveying personal data in such a way that it is exposed to an unintended audience. For illustration, anyone using a wristwatch on public transportation may unwittingly allow passersby to read the SMSes because the data appear on the screen as they arrive.
- Lifecycle transitions: Configurations and data are backed up and restored when smart devices undergo lifecycle transitions. In the process, incorrect data may end up in the wrong device, resulting in a privacy breach. For example, images and movies stored on one device may be viewed on another.
- Inventory attack: Hackers can query gadgets to generate an inventory of objects in a certain area since smart things are queryable via the Internet. For example, hackers can find whether a home has a smart meter, a smart thermostat, or smart lighting.
- Linkage: This a technique in which data from several sources, acquired in various situations, are combined to obtain insights about a subject.
4. IoT Security Using ML
4.1. ML Techniques for IoT Security
- Random Forest for malware detection: Agrawal et al. [36] employed the Random Forest technique on Android data of 49,101 instances with 39 attributes in the proposed work for detecting the Android virus. The major objective was to estimate Random Forest’s accuracy for assessing Android applications and classifying them as nondangerous or dangerous. The authors assessed the detection accuracy when the Random Forest algorithm’s attributes were modified, such as the depth of each tree, the number of trees, and the number of attributes. Based on six-fold cross-validation, the results concluded that the Random Forest technique performed with enhanced efficacy, with an overall accuracy of over 98.9% and an error rate of 0.2% for forests with more than 39 trees. Moreover, a root mean squared error of 1.69% for forests with 160 trees was registered.
- SVM-based malware identification: Nakhodchi et al. [37] reviewed several techniques for the identification of malware. These include taint-analysis-based, behavior-based, and signature-based detection. It is depicted that Linear SVM is performed well among ML techniques used for Android Malware Detection. Event information on the device in a behavior-based identification framework, including storage utilization and power consumption, is assessed. ML techniques are used to evaluate the data to discover aberrant patterns.
- PCA, Naive Bayes, and KNN Intrusion Detection: Saharkhizan et al. [38] presented a new framework for detecting intrusion based on two-level dimension reduction. Specifically, a two-tier categorization phase is described to detect malicious activities, including remote-to-local and user-to-root attacks. To minimize the dimensions in the dataset, the proposed framework employed Linear Discriminate Analysis (LDA) and Principal Component Analysis (PCA). Moreover, the authors incorporated a two-tier categorization phase with Naive Bayes to detect suspicious activities.
- Classification-based anomaly detection: In the study on creating an IoT gadget for women’s safety, Ramalingam [39] described a gadget that assesses whether or not the wearer is in danger. The gadget sends information on the person’s physiology and bodily posture. Body temperature and the galvanic skin response (GSR) are the communicated physiological signals. The data from a 3D accelerometer are used to estimate body position. The theory says that when a person is confronted with a threatening scenario, adrenalin secretion impacts several physiological systems, resulting in increased blood pressure, heart rate, and perspiration. As measured by GSR, skin conductance rises as a result of this. A classifier examines the data to decide whether or not the subject is in a risky scenario, such as rape.
4.2. Securing IoT Systems Using ANN
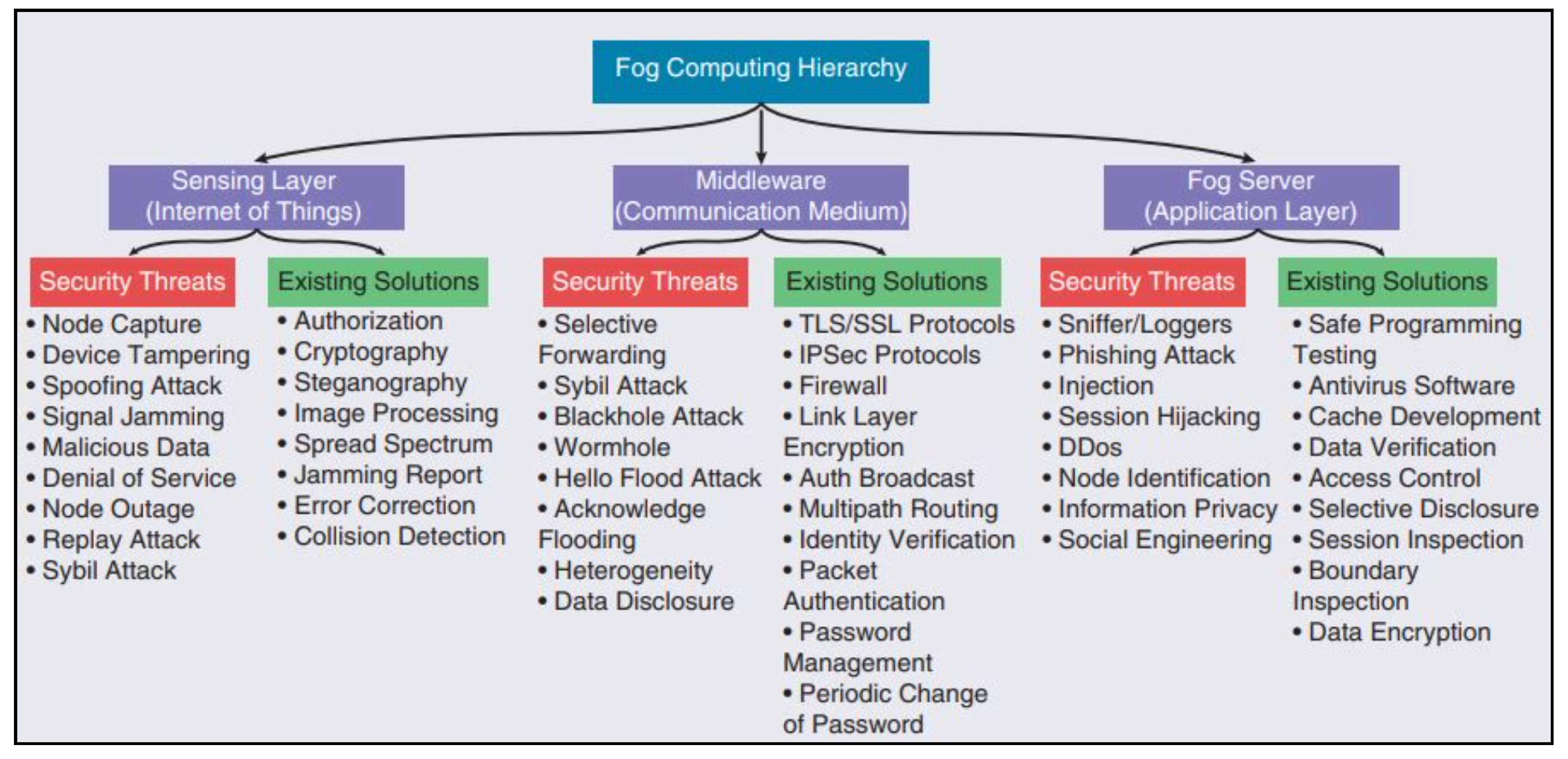
5. Secure Fog Computing
5.1. Fog Computing: Fundamentals
- Analytics in real time: The instances where time-sensitive analysis is required are increasing as IoT adoption develops. For illustration, a security camera may catch a possible burglar loitering at a residence or a fraudster obtaining data regarding unauthorized accounts. It may be too late when data are loaded to the cloud and examined. In these cases, near-instant intelligence is required, which Fog computing may supply.
- Increased security: Because Fog is closer to the edge, it may establish security that is specific to devices and their operations. Furthermore, security choices on whether or not to deny access during a breach may be made instantly.
- Edge data thinning: Fog absorbs raw data and makes judgments or delivers insights based on it. It only delivers pertinent, condensed data up the chain of command. As a result, the data quantity sent to a centralized repository is drastically reduced.
- Cost savings: Due to the scattered nature of installations, Fog may have greater setup costs. However, the whole system’s operational expenses and prolonged advantages would be substantial.
5.2. ML for Secure Fog Computing
6. Research Directions
6.1. Management of Trust
6.2. Confidentiality Assessment
6.3. Authentication
- Users, end devices (IoT), applications, and service providers must all be able to use the same authentication mechanisms on the cloud-Fog platform.
- IoT devices have a limited number of resources and must be able to scale up and down with a secure, environmentally friendly, efficient, and scalable solution. Conventional authentication procedures are inefficient. Different context-specific devices and applications demand high levels of security and performance.
- Nodes in the Fog network depart and join dynamically. Hence, this need must consider the dynamic behavior of the Fog environment.
- As a result, the Fog network’s scalability must be ensured using low-complexity-based authentication.
- A dynamic approach to authentication and reauthentication must be maintained.
- The Fog system and IoT devices should use a cryptographic lightweight encryption technique that can easily handle the low processing capacity of IoT devices as an efficient authentication mechanism.
- In exchange for its high usability and low cost, authentication should be user-friendly.
6.4. Access Management
- Fog is a completely virtualized platform by design, and it allows a wide range of settings for the Fog network to operate.
- Due to the nature of sharing resources across untrusted tenants, a side-channeled attack may occur in this instance. As a result, a top priority is building an access control system that can work effectively and securely in a virtualized platform and multitenant environment.
- Access control for the Fog environment must be safe, efficient, and attribute-based, considering minimal computation with outsourced capabilities and characteristics that can regulate user revocation capability.
- A lightweight and fine-grained access control mechanism is needed because of the resource limits faced by IoT devices.
6.5. Attacks and Threats
- Complex trust issues and insecure authentication and authorization systems are to blame for these problems.
- Fog nodes, or servers in the Fog layer, may be dynamically created, deleted, joined, and left.
- Fog nodes constantly leave and rejoin, making detecting malicious or rogue nodes a difficult operation.
- Creating a large-scale, geographically dispersed IDS implementation with low-latency need and high mobility Fog computing system is a difficult challenge.
- It is necessary to use hybrid detection approaches to catch malicious activity in a dispersed context.
- Designing high-security and low-cost threat and attack detection in the Fog environment is a major challenge because of Fog devices’ resource limits. For example, we must be able to identify and prevent attacks from both Fog nodes and Fog users simultaneously.
6.6. Secure 5G Fog Network
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Gill, S.S. A Manifesto for Modern Fog and Edge Computing: Vision, New Paradigms, Opportunities, and Future Directions. In Operationalizing Multi-Cloud Environments; Springer: Berlin/Heidelberg, Germany, 2022; pp. 237–253. [Google Scholar]
- Ammi, M.; Alarabi, S.; Benkhelifa, E. Customized blockchain-based architecture for secure smart home for lightweight IoT. Inf. Process. Manag. 2021, 58, 102482. [Google Scholar] [CrossRef]
- Xiang, G.; Zhu, X.; Ma, L.; Huang, H.; Wu, X.; Zhang, W.; Li, S. Clinical guidelines on the application of Internet of Things (IOT) medical technology in the rehabilitation of chronic obstructive pulmonary disease. J. Thorac. Dis. 2021, 13, 4629. [Google Scholar] [CrossRef] [PubMed]
- Muller, H.; Mayrhofer, M.T.; Van Veen, E.B.; Holzinger, A. The Ten Commandments of ethical medical AI. Computer 2021, 54, 119–123. [Google Scholar] [CrossRef]
- Shapiro, A. ‘Embodiments of the invention’: Patents and urban diagrammatics in the smart city. Convergence 2020, 26, 751–774. [Google Scholar] [CrossRef]
- Pong, P.W.; Annaswamy, A.M.; Kroposki, B.; Zhang, Y.; Rajagopal, R.; Zussman, G.; Poor, H.V. Cyber-enabled grids: Shaping future energy systems. Adv. Appl. Energy 2021, 1, 100003. [Google Scholar] [CrossRef]
- Edwards, C. Real-time advanced analytics, automated production systems, and smart industrial value creation in sustainable manufacturing Internet of Things. J. Self-Gov. Manag. Econ. 2021, 9, 32–41. [Google Scholar]
- Moh, M.; Raju, R. Machine learning techniques for security of Internet of Things (IoT) and fog computing systems. In Proceedings of the 2018 International Conference on High Performance Computing & Simulation (HPCS), Orléans, France, 20 July 2018; pp. 709–715. [Google Scholar]
- Ungurean, I.; Gaitan, N.C. Software Architecture of a Fog Computing Node for Industrial Internet of Things. Sensors 2021, 21, 3715. [Google Scholar] [CrossRef]
- Holzinger, A.; Weippl, E.; Tjoa, A.M.; Kieseberg, P. Digital transformation for sustainable development goals (sdgs)-a security, safety and privacy perspective on ai. In International Cross-Domain Conference for Machine Learning and Knowledge Extraction; Springer: Berlin/Heidelberg, Germany, 2021; pp. 1–20. [Google Scholar]
- Liu, Y.; Wei, X.; Xiao, J.; Liu, Z.; Xu, Y.; Tian, Y. Energy consumption and emission mitigation prediction based on data center traffic and PUE for global data centers. Glob. Energy Interconnect. 2020, 3, 272–282. [Google Scholar] [CrossRef]
- Leyden, J. Water Treatment Plant Hacked, Chemical Mix Changed for Tap Supplies. Register 2016. Available online: https://www.theregister.com/2016/03/24/water_utility_hacked/ (accessed on 2 February 2022).
- Brand, R.; Timme, S.; Nosrat, S. When pandemic hits: Exercise frequency and subjective well-being during COVID-19 pandemic. Front. Psychol. 2020, 11, 2391. [Google Scholar] [CrossRef]
- Puat, H.A.M.; Abd Rahman, N.A. IoMT: A Review of Pacemaker Vulnerabilities and Security Strategy. J. Phys. Conf. Ser. 2020, 1712, 012009. [Google Scholar] [CrossRef]
- Aazam, M.; Zeadally, S.; Harras, K.A. Deploying Fog Computing in Industrial Internet of Things and Industry 4.0. IEEE Trans. Ind. Inform. 2018, 14, 4674–4682. [Google Scholar] [CrossRef]
- Li, D.; Deng, L.; Cai, Z.; Souri, A. Blockchain as a service models in the Internet of Things management: Systematic review. In Transactions on Emerging Telecommunications Technologies; Wiley: Hoboken, NJ, USA, 2020; p. e4139. [Google Scholar]
- Rizvi, S.; Orr, R.; Cox, A.; Ashokkumar, P.; Rizvi, M.R. Identifying the attack surface for IoT network. Internet Things 2020, 9, 100162. [Google Scholar] [CrossRef]
- Khormali, A.; Park, J.; Alasmary, H.; Anwar, A.; Saad, M.; Mohaisen, D. Domain name system security and privacy: A contemporary survey. Comput. Netw. 2021, 185, 107699. [Google Scholar] [CrossRef]
- Shim, J.P.; Sharda, R.; French, A.M.; Syler, R.A.; Patten, K.P. The Internet of Things: Multi-faceted research perspectives. Commun. Assoc. Inf. Syst. 2020, 46, 21. [Google Scholar] [CrossRef]
- Ogonji, M.M.; Okeyo, G.; Wafula, J.M. A survey on privacy and security of Internet of Things. Comput. Sci. Rev. 2020, 38, 100312. [Google Scholar] [CrossRef]
- Tahsien, S.M.; Karimipour, H.; Spachos, P. Machine learning based solutions for security of Internet of Things (IoT): A survey. J. Netw. Comput. Appl. 2020, 161, 102630. [Google Scholar] [CrossRef] [Green Version]
- Azad, T. Securing Citrix XenApp Server in the Enterprise; Syngress: Waltham, MA, USA, 2008. [Google Scholar]
- Schubert, E.; Sander, J.; Ester, M.; Kriegel, H.P.; Xu, X. DBSCAN revisited, revisited: Why and how you should (still) use DBSCAN. ACM Trans. Database Syst. (TODS) 2017, 42, 1–21. [Google Scholar] [CrossRef]
- Hamerly, G.; Elkan, C. Learning the k in k-means. Adv. Neural Inf. Process. Syst. 2004, 16, 281–288. [Google Scholar]
- Chen, Y.; Zheng, W.; Li, W.; Huang, Y. Large group activity security risk assessment and risk early warning based on random forest algorithm. Pattern Recognit. Lett. 2021, 144, 1–5. [Google Scholar] [CrossRef]
- Uddin, M.P.; Mamun, M.A.; Hossain, M.A. PCA-based feature reduction for hyperspectral remote sensing image classification. IETE Tech. Rev. 2021, 38, 377–396. [Google Scholar] [CrossRef]
- Zhang, H.; Jiang, L.; Yu, L. Attribute and instance weighted naive Bayes. Pattern Recognit. 2021, 111, 107674. [Google Scholar] [CrossRef]
- Chen, W.; Wang, L.; Ren, W.; Zhao, J.; Wang, Z.; Quan, Y.; Zhuang, J. Effect of BaZrO3 amounts on the domain structure and electrical properties of lead-free piezoelectric KNN-based films. Mater. Sci. Eng. B 2022, 276, 115552. [Google Scholar] [CrossRef]
- Chen, Y.; Huang, W.; Nguyen, L.; Weng, T.W. On the Equivalence between Neural Network and Support Vector Machine. Adv. Neural Inf. Process. Syst. 2021, 34. Available online: https://arxiv.org/abs/2111.06063 (accessed on 2 February 2022).
- Guo, H.; Nguyen, H.; Bui, X.N.; Armaghani, D.J. A new technique to predict fly-rock in bench blasting based on an ensemble of support vector regression and GLMNET. Eng. Comput. 2021, 37, 421–435. [Google Scholar] [CrossRef]
- Haruna, S.; Malami, S.I.; Adamu, M.; Usman, A.; Farouk, A.; Ali, S.I.A.; Abba, S. Compressive Strength of Self-Compacting Concrete Modified with Rice Husk Ash and Calcium Carbide Waste Modeling: A Feasibility of Emerging Emotional Intelligent Model (EANN) Versus Traditional FFNN. Arab. J. Sci. Eng. 2021, 46, 11207–11222. [Google Scholar] [CrossRef]
- Castillo, I.; Ročková, V. Uncertainty quantification for Bayesian CART. Ann. Stat. 2021, 49, 3482–3509. [Google Scholar] [CrossRef]
- Montgomery, D.C.; Peck, E.A.; Vining, G.G. Introduction to Linear Regression Analysis; John Wiley & Sons: Hoboken, NJ, USA, 2021. [Google Scholar]
- Hubona, G.S.; Schuberth, F.; Henseler, J. A clarification of confirmatory composite analysis (CCA). Int. J. Inf. Manag. 2021, 61, 102399. [Google Scholar] [CrossRef]
- Yousefi, S.; Derakhshan, F.; Karimipour, H. Applications of big data analytics and machine learning in the internet of things. In Handbook of Big Data Privacy; Springer: Cham, Switzerland, 2020; pp. 77–108. [Google Scholar]
- Agrawal, P.; Trivedi, B. Machine learning classifiers for Android malware detection. In Data Management, Analytics and Innovation; Springer: Berlin/Heidelberg, Germany, 2021; pp. 311–322. [Google Scholar]
- Nakhodchi, S.; Upadhyay, A.; Dehghantanha, A. A comparison between different machine learning models for iot malware detection. In Security of Cyber-Physical Systems; Springer: Berlin/Heidelberg, Germany, 2020; pp. 195–202. [Google Scholar]
- Saharkhizan, M.; Azmoodeh, A.; HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G. A Hybrid Deep Generative Local Metric Learning Method for Intrusion Detection. 2020. Available online: https://doi.org/10.1007/978-3-030-38557-6_16 (accessed on 2 February 2022).
- Ramalingam, A. Child and Women’s Safety with Wearable Devices: Wearable devices for security. SPAST Abstr. 2021, 1. Available online: https://spast.org/techrep/article/view/1985 (accessed on 2 February 2022).
- Bagaa, M.; Taleb, T.; Bernabe, J.B.; Skarmeta, A. A machine learning security framework for iot systems. IEEE Access 2020, 8, 114066–114077. [Google Scholar] [CrossRef]
- Askawiec, S.; Choraś, M.; Kozik, R.; Varadarajan, V. Intelligent operator: Machine learning based decision support and explainer for human operators and service providers in the fog, cloud and edge networks. J. Inf. Secur. Appl. 2021, 56, 102685. [Google Scholar]
- Zhang, C. Design and application of fog computing and Internet of Things service platform for smart city. Future Gener. Comput. Syst. 2020, 112, 630–640. [Google Scholar] [CrossRef]
- Rauf, A.; Shaikh, R.A.; Shah, A. Security and privacy for IoT and fog computing paradigm. In Proceedings of the 2018 15th Learning and Technology Conference (L&T), Jeddah, Saudi Arabia, 25–26 February 2018; pp. 96–101. [Google Scholar]
- Wang, T.; Zhang, G.; Bhuiyan, M.Z.A.; Liu, A.; Jia, W.; Xie, M. A novel trust mechanism based on fog computing in sensor–cloud system. Future Gener. Comput. Syst. 2020, 109, 573–582. [Google Scholar] [CrossRef]
- Rahman, F.H.; Au, T.W.; Newaz, S.S.; Suhaili, W.S.; Lee, G.M. Find my trustworthy fogs: A fuzzy-based trust evaluation framework. Future Gener. Comput. Syst. 2020, 109, 562–572. [Google Scholar] [CrossRef] [Green Version]
- Soleymani, S.A.; Abdullah, A.H.; Zareei, M.; Anisi, M.H.; Vargas-Rosales, C.; Khan, M.K.; Goudarzi, S. A secure trust model based on fuzzy logic in vehicular ad hoc networks with fog computing. IEEE Access 2017, 5, 15619–15629. [Google Scholar] [CrossRef]
- Yuan, J.; Li, X. A reliable and lightweight trust computing mechanism for IoT edge devices based on multi-source feedback information fusion. IEEE Access 2018, 6, 23626–23638. [Google Scholar] [CrossRef]
- Dang, T.D.; Hoang, D. A data protection model for fog computing. In Proceedings of the 2017 Second International Conference on Fog and Mobile Edge Computing (FMEC), Valencia, Spain, 8–11 May 2017; pp. 32–38. [Google Scholar]
- Wang, H.; Wang, Z.; Domingo-Ferrer, J. Anonymous and secure aggregation scheme in fog-based public cloud computing. Future Gener. Comput. Syst. 2018, 78, 712–719. [Google Scholar] [CrossRef]
- Yang, R.; Xu, Q.; Au, M.H.; Yu, Z.; Wang, H.; Zhou, L. Position based cryptography with location privacy: A step for fog computing. Future Gener. Comput. Syst. 2018, 78, 799–806. [Google Scholar] [CrossRef]
- Kumar, P.; Zaidi, N.; Choudhury, T. Fog computing: Common security issues and proposed countermeasures. In Proceedings of the 2016 International Conference System Modeling & Advancement in Research Trends (SMART), Moradabad, India, 25–27 November 2016; pp. 311–315. [Google Scholar]
- Liu, J.; Li, J.; Zhang, L.; Dai, F.; Zhang, Y.; Meng, X.; Shen, J. Secure intelligent traffic light control using fog computing. Future Gener. Comput. Syst. 2018, 78, 817–824. [Google Scholar] [CrossRef]
- Qin, Z.; Yi, S.; Li, Q.; Zamkov, D. Preserving secondary users’ privacy in cognitive radio networks. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 772–780. [Google Scholar]
- Ibrahim, M.H. OCTOPUS: An edge-fog mutual authentication scheme. Int. J. Netw. Secur. 2016, 18, 1089–1101. [Google Scholar]
- Yu, Z.; Au, M.H.; Xu, Q.; Yang, R.; Han, J. Towards leakage-resilient fine-grained access control in fog computing. Future Gener. Comput. Syst. 2018, 78, 763–777. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V. Design of secure key management and user authentication scheme for fog computing services. Future Gener. Comput. Syst. 2019, 91, 475–492. [Google Scholar] [CrossRef]
- Dsouza, C.; Ahn, G.J.; Taguinod, M. Policy-driven security management for fog computing: Preliminary framework and a case study. In Proceedings of the 2014 IEEE 15th International Conference on Information Reuse and Integration (IEEE IRI 2014), Redwood City, CA, USA, 13–15 August 2014; pp. 16–23. [Google Scholar]
- Alharbi, S.; Rodriguez, P.; Maharaja, R.; Iyer, P.; Subaschandrabose, N.; Ye, Z. Secure the internet of things with challenge response authentication in fog computing. In Proceedings of the 2017 IEEE 36th International Performance Computing and Communications Conference (IPCCC), San Diego, CA, USA, 10–12 December 2017; pp. 1–2. [Google Scholar]
- Amor, A.B.; Abid, M.; Meddeb, A. A privacy-preserving authentication scheme in an edge-fog environment. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October–3 November 2017; pp. 1225–1231. [Google Scholar]
- Hu, P.; Ning, H.; Qiu, T.; Song, H.; Wang, Y.; Yao, X. Security and privacy preservation scheme of face identification and resolution framework using fog computing in internet of things. IEEE Internet Things J. 2017, 4, 1143–1155. [Google Scholar] [CrossRef]
- Ha, D.A.; Nguyen, K.T.; Zao, J.K. Efficient authentication of resource-constrained IoT devices based on ECQV implicit certificates and datagram transport layer security protocol. In Proceedings of the Seventh Symposium on Information and Communication Technology, Ho Chi Minh, Vietnam, 8–9 December 2016; pp. 173–179. [Google Scholar]
- Fan, K.; Wang, J.; Wang, X.; Li, H.; Yang, Y. A secure and verifiable outsourced access control scheme in fog-cloud computing. Sensors 2017, 17, 1695. [Google Scholar] [CrossRef]
- Lu, R.; Heung, K.; Lashkari, A.H.; Ghorbani, A.A. A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT. IEEE Access 2017, 5, 3302–3312. [Google Scholar] [CrossRef]
- Zhang, P.; Chen, Z.; Liu, J.K.; Liang, K.; Liu, H. An efficient access control scheme with outsourcing capability and attribute update for fog computing. Future Gener. Comput. Syst. 2018, 78, 753–762. [Google Scholar] [CrossRef]
- Vohra, K.; Dave, M. Multi-authority attribute based data access control in fog computing. Procedia Comput. Sci. 2018, 132, 1449–1457. [Google Scholar] [CrossRef]
- Popa, L.; Yu, M.; Ko, S.Y.; Ratnasamy, S.; Stoica, I. CloudPolice: Taking access control out of the network. In Proceedings of the 9th ACM SIGCOMM Workshop on Hot Topics in Networks, Monterey, CA, USA, 20–21 October 2010; pp. 1–6. [Google Scholar]
- Gope, P.; Sikdar, B. Lightweight and privacy-preserving two-factor authentication scheme for IoT devices. IEEE Internet Things J. 2018, 6, 580–589. [Google Scholar] [CrossRef]
- Xiao, M.; Zhou, J.; Liu, X.; Jiang, M. A hybrid scheme for fine-grained search and access authorization in fog computing environment. Sensors 2017, 17, 1423. [Google Scholar] [CrossRef]
- Zaghdoudi, B.; Kaffel-Ben Ayed, H.; Harizi, W. Generic access control system for ad hoc MCC and fog computing. In International Conference on Cryptology and Network Security; Springer: Berlin/Heidelberg, Germany, 2016; pp. 400–415. [Google Scholar]
- Yavuz, F.Y. Deep Learning in Cyber Security for Internet of Things. Master’s Thesis, Fen Bilimleri Enstitüsü, Istanbul, Turkey, 2018. [Google Scholar]
- Torres, P.; Catania, C.; Garcia, S.; Garino, C.G. An analysis of recurrent neural networks for botnet detection behavior. In Proceedings of the 2016 IEEE Biennial Congress of Argentina (ARGENCON), Buenos Aires, Argentina, 15–17 June 2016; pp. 1–6. [Google Scholar]
- Canedo, J.; Skjellum, A. Using machine learning to secure IoT systems. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 219–222. [Google Scholar]
- Wang, N.; Jiang, T.; Lv, S.; Xiao, L. Physical-layer authentication based on extreme learning machine. IEEE Commun. Lett. 2017, 21, 1557–1560. [Google Scholar] [CrossRef]
- Yousefi-Azar, M.; Varadharajan, V.; Hamey, L.; Tupakula, U. Autoencoder-based feature learning for cyber security applications. In Proceedings of the 2017 International Joint Conference on Neural Networks (IJCNN), Anchorage, AK, USA, 14–19 May 2017; pp. 3854–3861. [Google Scholar]
- Li, L.; Xiaoguang, H.; Ke, C.; Ketai, H. The applications of wifi-based wireless sensor network in internet of things and smart grid. In Proceedings of the 2011 6th IEEE Conference on Industrial Electronics and Applications, Beijing, China, 21–23 June 2011; pp. 789–793. [Google Scholar]
- Aminanto, M.E.; Kim, K. Improving detection of Wi-Fi impersonation by fully unsupervised deep learning. In International Workshop on Information Security Applications; Springer: Berlin/Heidelberg, Germany, 2017; pp. 212–223. [Google Scholar]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Comput. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Abeshu, A.; Chilamkurti, N. Deep learning: The frontier for distributed attack detection in fog-to-things computing. IEEE Commun. Mag. 2018, 56, 169–175. [Google Scholar] [CrossRef]
- Saied, A.; Overill, R.E.; Radzik, T. Detection of known and unknown DDoS attacks using Artificial Neural Networks. Neurocomputing 2016, 172, 385–393. [Google Scholar] [CrossRef]
- Chen, Y.; Zhang, Y.; Maharjan, S. Deep learning for secure mobile edge computing. arXiv 2017, arXiv:1709.08025. [Google Scholar]
- Shi, C.; Liu, J.; Liu, H.; Chen, Y. Smart user authentication through actuation of daily activities leveraging WiFi-enabled IoT. In Proceedings of the 18th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Chennai, India, 10–14 July 2017; pp. 1–10. [Google Scholar]
- Alzaylaee, M.K.; Yerima, S.Y.; Sezer, S. DL-Droid: Deep learning based android malware detection using real devices. Comput. Secur. 2020, 89, 101663. [Google Scholar] [CrossRef]






| Reference | Use Case | Algorithm | Domain | Limitations |
|---|---|---|---|---|
| [23] | Pattern discovery | DBSCAN | Importance of using DBSCAN technique for attack detection | It is not effective for data clusters having similar densities |
| [24] | Pattern discovery | K-means | Fundamentals of K-means are discussed in security | It is effective only when data is numerical |
| [25] | Discovery of unusual data points | Random Forest | Random forest technique for security risk assessment | A large delay was registered |
| [26] | Discovery of unusual data points | PCA | PCA-based feature reduction for remote sensing secure applications | Minimal accuracy was registered |
| [27] | Discovery of unusual data points | Naive Bayes | Exploration of probabilistic attack detection | Data dependence reduces the accuracy |
| [28] | Discovery of unusual data points | KNN | The utilization of KNN for nearest neighbor detection | The value of K should be fixed initially |
| [29] | Discovery of unusual data points | Support Vector Machine | Prediction-based attack detection | It is less effective for time-sensitive applications |
| [30] | Prediction of values & categories | Support Vector Regression | The detection of UAV-specific attacks | There was a delay and accuracy was minimal |
| [31] | Prediction of values & categories | FFNN | Novel vision for data security in smart soil application | The domain of applicability is limited |
| [32] | Prediction of values & categories | CART | Uncertainty detection and quantification for security | It is not reliable as it based on probability |
| [33] | Prediction of values & categories | Linear Regression | Linear regression analysis for data variability | The attack detection effectiveness is limited |
| [34] | Feature extraction | CCA | The fundamentals of feature extractions are discussed | Security is minimally addressed |
| Use Case | Reference | ML Technique |
|---|---|---|
| Malware Detection | [29] | SVM |
| Malware Detection | [25] | Random Forest |
| Anomaly Detection | [27] | Naive Bayes |
| Anomaly Detection | [35] | ANN |
| Intrusion Detection | [26] | PCA |
| Intrusion Detection | [28] | KNN |
| Intrusion Detection | [27] | Naive Bayes |
| Use Case | ML Technique |
|---|---|
| Industry | Predictive models |
| Industry | Anomaly detection |
| Industry | Optimization technique |
| Retail | Time series clustering |
| Retail | Statistical technique |
| Self-Driving Cars | Reinforced learning |
| Self-Driving Cars | Anomaly detection |
| Self-Driving Cars | Image processing |
| Ref. | Highlights | Trust | Privacy | Auth | Accessible | Confidential | Integral |
|---|---|---|---|---|---|---|---|
| [43] | Proposed a risk-based trust model for the IoT environment. | Y | N | N | N | Y | N |
| [44] | Performed a Fog-based hierarchical trust mechanism. | Y | N | N | N | Y | Y |
| [45] | A broker-based trust mechanism approach in Fog. | Y | N | N | N | N | N |
| [46] | Secured trust establishment among vehicles. | Y | N | N | N | Y | Y |
| [47] | Reliable and lightweight trust evaluation mechanism. | Y | N | N | N | N | N |
| [48] | A data protection scheme was used for Fog computing. | Y | N | N | N | N | N |
| [49] | Fog-based public cloud computing | N | Y | N | N | N | Y |
| [50] | Introduced secure positioning protocols by preserving location privacy. | N | Y | N | N | Y | Y |
| [51] | Data confidentiality and location privacy were focused on. | N | Y | N | N | Y | Y |
| [52] | Fog-based vehicular ad hoc network (VANET). | N | Y | N | N | N | N |
| [53] | Preservation of the privacy of the end users over a radio network. | N | Y | N | N | N | N |
| [54] | An efficient and secure mutual authentication method for the cloud-Fog-edge system architecture. | N | N | Y | N | N | N |
| [55] | Fine-grained access control and privacy were provided for Fog computing. | N | N | N | Y | Y | Y |
| [56] | Fog devices’ security can be ensured through key management and authentication schemes. | N | N | Y | N | Y | Y |
| [57] | Introduced policy-based resource management in the Fog network. | N | N | Y | N | Y | Y |
| [58] | Ensured secure communication among the various IoT devices. | N | N | Y | N | Y | Y |
| [59] | Introduced anonymous mutual authentication amongst the Fog users and Fog servers. | N | N | Y | N | Y | Y |
| [60] | Highlighted privacy preservation and security methods for Fog-based image processing applications. | N | N | Y | N | Y | Y |
| [61] | An efficient and elliptic cryptographic-based mutual authentication technique for IoT-based resource-constrained devices. | N | N | Y | N | Y | Y |
| [62] | CP-ABE-based multiauthority data access control scheme in Fog-cloud computing systems. | N | N | N | Y | Y | Y |
| [63] | Employing a lightweight privacy preserving data aggregation method for Fog and IoT systems. | N | Y | N | N | Y | Y |
| [64] | A promising CP-ABE-based access control method for a Fog computing environment. | N | N | N | Y | N | N |
| [65] | Fog-based decentralized multiauthority attribute-based data access control. | N | N | N | Y | N | N |
| [66] | A distributed multitenancy approach to access control. | N | N | N | Y | N | N |
| [67] | Deliberated two-factor lightweight and privacy preserving authentication method for resource-constrained IoT devices. | N | N | Y | N | N | N |
| [68] | A hybrid and fine-grained access control solution. | N | N | N | Y | Y | Y |
| [69] | Access control mechanisms proposed for Fog computing and ad hoc MCC. | N | N | N | Y | Y | Y |
| Reference | Year | ANN | CNN | RNN | AF | RBM | DBN | GAN | EDL | Threat |
|---|---|---|---|---|---|---|---|---|---|---|
| [70] | 2015 | Y | – | – | – | – | – | – | – | Routing attack detection |
| [71] | 2014 | – | – | Y | – | – | – | – | – | Malicious behavior detection |
| [72] | 2009 | Y | – | – | – | – | – | – | – | Data tampering |
| [73] | 2013 | Y | – | – | – | – | – | – | – | Spoofing attack detection |
| [74] | 2017 | – | – | – | Y | – | – | – | – | Malware detection |
| [75] | 2015 | Y | – | – | Y | – | – | – | – | Impersonation attacks |
| [76] | 2018 | – | – | – | Y | – | – | – | – | Impersonation attacks |
| [77] | 2016 | Y | – | – | – | – | – | – | – | Cyber attacks |
| [78] | 2017 | – | – | – | Y | – | – | – | – | Cyber attacks |
| [79] | 2017 | Y | – | – | – | – | – | – | – | DDoS attack detection |
| [80] | 20N6 | – | – | – | – | – | Y | – | – | Malicious attack detection |
| [81] | 2017 | Y | – | – | – | – | – | – | – | Authentication |
| [82] | 2016 | – | Y | – | – | – | – | – | – | Malware detection |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahanger, T.A.; Tariq, U.; Ibrahim, A.; Ullah, I.; Bouteraa, Y.; Gebali, F. Securing IoT-Empowered Fog Computing Systems: Machine Learning Perspective. Mathematics 2022, 10, 1298. https://doi.org/10.3390/math10081298
Ahanger TA, Tariq U, Ibrahim A, Ullah I, Bouteraa Y, Gebali F. Securing IoT-Empowered Fog Computing Systems: Machine Learning Perspective. Mathematics. 2022; 10(8):1298. https://doi.org/10.3390/math10081298
Chicago/Turabian StyleAhanger, Tariq Ahamed, Usman Tariq, Atef Ibrahim, Imdad Ullah, Yassine Bouteraa, and Fayez Gebali. 2022. "Securing IoT-Empowered Fog Computing Systems: Machine Learning Perspective" Mathematics 10, no. 8: 1298. https://doi.org/10.3390/math10081298
APA StyleAhanger, T. A., Tariq, U., Ibrahim, A., Ullah, I., Bouteraa, Y., & Gebali, F. (2022). Securing IoT-Empowered Fog Computing Systems: Machine Learning Perspective. Mathematics, 10(8), 1298. https://doi.org/10.3390/math10081298








