1. Introduction
With the rapid development of the process industry and the wide application of intelligent information technology, condition monitoring has become a critical part of ensuring the stable, efficient, and safe operation of the process industry [
1]. Condition monitoring alerts operators to take appropriate actions to handle possible or potential faults by alarms [
2]. Owing to the speedy growth of software and hardware technologies, it is no longer difficult to obtain the sample data of process variables in the process industry, so condition monitoring has become simpler and quicker [
3]. However, due to the uncertainty of the industrial environment and the inappropriate design of the condition monitoring system, it will be inevitable to generate a large number of false alarms and missed alarms, so that operators hardly determine the true state of the industrial process ultimately [
4]. Therefore, it is very important to design an appropriate alarm method for condition monitoring.
In the traditional condition monitoring method, the alarm threshold is an important parameter, i.e., an alarm is issued based on whether the sampled value of the process variable exceeds the alarm threshold [
5]. The higher alarm threshold reduces the number of false alarms, but this may miss critical process state information, resulting in untimely alarms and a large number of missed alarms; the lower alarm threshold triggers more false alarms [
6]. Obviously, in practical applications, the alarm design method based on threshold may not be effective in reducing the number of false alarms and missed alarms [
7].
In a univariate industrial process, the conventional alarm design methods based on alarm threshold include a time delay method, a filtering method, a deadband method, and so on [
8]. Specifically, the time delay method issues an alarm when the sampled value of the process variable exceeds the alarm threshold several times in a row [
9]; the filtering method processes the sampled value by the moving variance strategy and then compares the filtered value with the alarm threshold [
10]. The deadband method sets high and low alarm thresholds to issue and clear the alarm, and then an alarm is issued when the sampled value is above the high alarm threshold, and an alarm is cleared when the sample value falls below the low alarm threshold [
11]. These alarm design methods have improved the alarm thresholds and have achieved some effects in univariate condition monitoring.
In fact, due to the increasing complexity of the industrial process, the multivariate industrial process is gradually replacing the univariate industrial process [
12]. The above proposed univariate alarm design methods have some limitations in multivariate industrial processes, such as the inconsistency of alarm results for each variable and the inability to address the complexity of process information. Correspondingly, the multivariable alarm design methods have become a research hotspot in the field of alarm systems, but there is relatively less research on multivariable alarm methods [
13]. For example, ref. [
14] established objective functions based on the false alarm rate and missed alarm rate of any two process variables and obtained optimal alarm thresholds, respectively, and then designed the alarm system and achieved certain effects compared with univariate alarm systems. In essence, this method only preliminarily extends the idea of univariate threshold optimization to multivariate process, i.e., threshold optimization is performed for multivariate processes, and then the univariate alarm systems are still adopted separately for any one variable [
15]. When the number of the process variables are more than two, the order of optimization also needs to be identified. In addition, the alarm results of each variable may be inconsistent or even contradictory, which is a challenge to a certain extent in real application.
In recent years, information fusion theory (IFT) integrates the process information of the multiple variables from various sources to formulate more accurate and consistent decision results though data-driven analysis and has been widely implemented in the domain of pattern recognition, expert systems, and fault diagnosis [
16,
17]. In IFT, the Dempster-Shafer (DS) theory and evidence reasoning (ER) rule are representative methods [
18,
19]. Specifically, DS theory translates the data of process variables into corresponding evidence and obtains accurate fusion results through the process of evidence fusion, which reduces the uncertainty of the process information [
20,
21]. Yang proposed the ER rule based on the DS theory, which further improves the rationality of the evidence fusion process by assigning reliability and weight to evidence [
22]. The reliability reflects the inherent property of evidence and is objective, while the weight reflects the importance of the evidence relative to other evidence and is subjective. Since the introduction of reliability, a series of calculation methods for reliability have been proposed, which all describe reliability as a fixed value [
23]. On the one hand, reliability reflects the inherent change of the evidence, so it is usually difficult for the fixed value form to describe the uncertainty of the evidence. On the other hand, due to various known or unknown factors, the reliability should change randomly with certain regularity. Therefore, this may be a better way that the reliability can be modeled, in the form of random variables within some uncertain interval.
In view of the above-proposed problems and analysis, this paper proposes an alarm design method via ER rule considering interval-valued reliability, which mainly includes the referential evidence matrix (REM) and is constructed based on the data of training samples, which achieves the transformation of the process variable to the referential alarm evidence, and the real-time sample data activates the REM to obtain alarm evidence. The corresponding interval-valued ER rule is then proposed, which can fuse alarm evidence to get the integrated alarm evidence. Among that, in order to accommodate the change of process variables, the interval-valued ER rule describes the reliability as a random variable and adjusts the changing interval of reliability according to evidence variation. Therefore, the interval-valued reliability adjustment can achieve the efficient integration of the process information. Finally, the accurate alarm decision is made based on integrated alarm evidence.
This paper is organized as follows:
Section 2 introduces the theoretical basis of the ER rule;
Section 3 presents the alarm design method based on the interval-valued ER rule;
Section 4 demonstrates the effectiveness of the proposed method through an example of reactor fault in the TE process; finally, this study is concluded in
Section 5.
3. The Multivariate Alarm Design Method via the Interval-Valued ER Rule
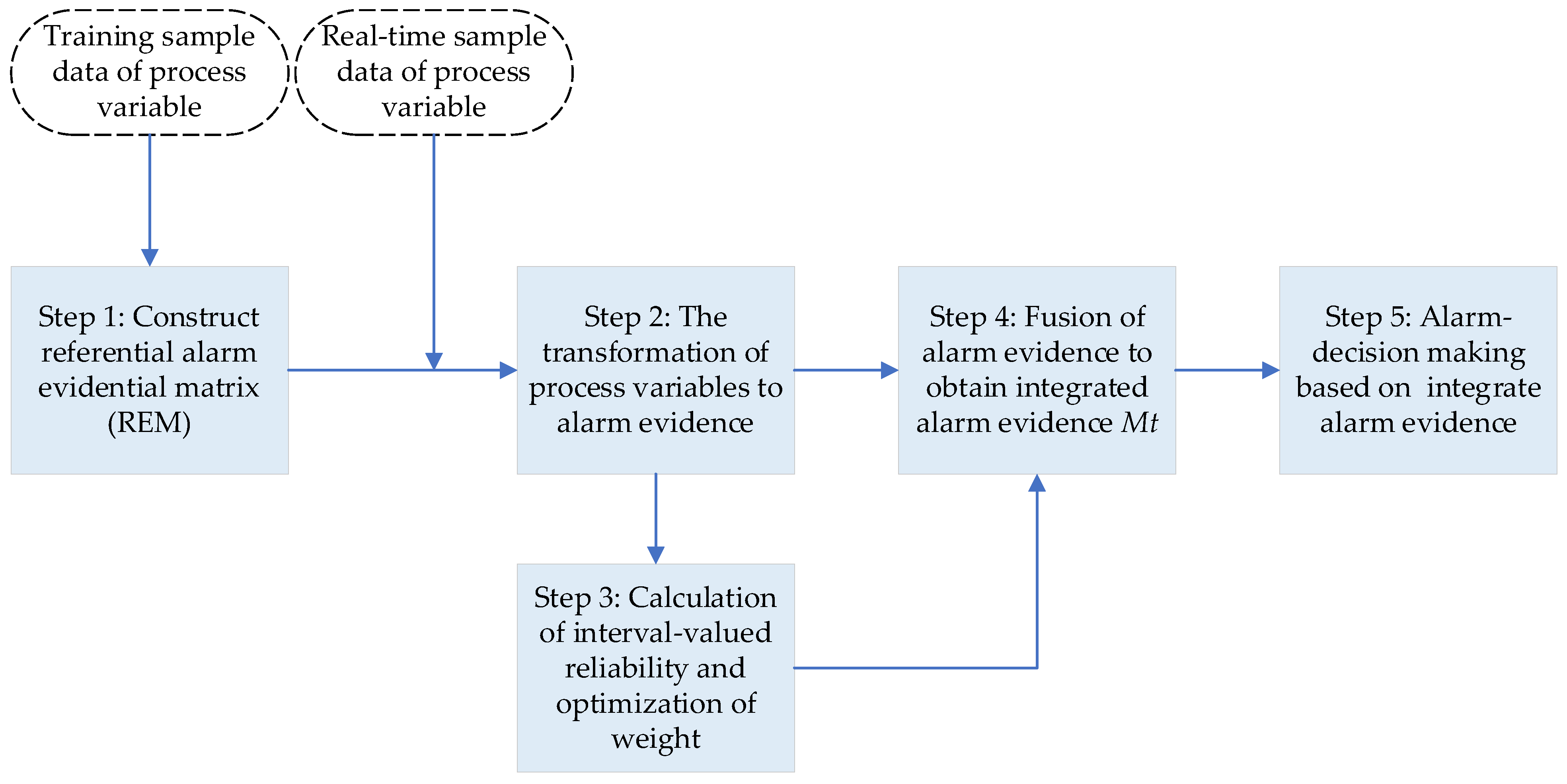
Here,
Section 3.1 first introduces the acquisition of alarm evidence, i.e., the referential evidence matrix (REM) is constructed by casting points that are operation-based on the training set of the process variable, and a real-time sample is transformed into alarm evidence by activating the corresponding REM. Furthermore, in
Section 3.2, the interval-valued reliability is adjusted with the change of alarm evidence, and the importance weight of alarm evidence is optimized. In
Section 3.3, the interval-valued ER rule fuses alarm evidence coming from multiple process variables and obtains the integrated alarm evidence. Finally, in
Section 3.4, the alarm result is obtained based on the integrated alarm evidence. The whole process of the designed multivariate alarm method is shown in
Figure 1.
Step 1 (The construction of REM): The referential evidence matrix (REM) is constructed by casting points operation based on the training set of process variables, which achieves the accurate transformation of process variable data into referential alarm evidence. More details can be found in
Section 3.1.1.
Step 2 (The transformation of process variables to alarm evidence): The real-time sample of the process variable is transformed into alarm evidence by activating the corresponding REM. More details can be found in
Section 3.1.2.
Step 3 (The calculation of interval-valued reliability and the optimization of weight): Before using the interval-valued ER rule to fuse alarm evidence, it is important to adjust the reliability intervals and the weights of the corresponding alarm evidence. Therefore, the interval-valued ER rule catering for interval-valued reliability is proposed. Wherein, the reliability of alarm evidence is inscribed by random variables with certain probability distribution characteristics on the interval, and the interval of reliability is adaptively adjusted according to the change of the real-time sample of the process variable, which improves the reasonability of the fusion process. More details are presented in
Section 3.2.
Step 4 (The fusion of alarm evidence based on the interval-valued ER rule): On the basis of step 3, this step extends the original ER rule to the interval-valued ER rule, which can fuse alarm evidence to get integrated alarm evidence. More details can be found in
Section 3.3.
Step 5 (Alarm-decision making based on integrated alarm evidence): Based on alarm-decision criteria, the alarm decision is made through integrated alarm evidence. More details are shown in
Section 3.4.
3.1. The Acquisition of Alarm Evidence
3.1.1. The Construction of REM
Step 1.1: In the context of the alarm system, the discernment framework is defined as Θ = {NA, A}, where “NA” stands for the proposition “no alarm” and “A” represents the proposition “alarm”. Let the set of training samples be V = [xi(k), y(k)], i = 1, 2, …, I, k = 1, 2, 3, …, K, where I is the number of the process variable, the process variable xi(k) is the input of the alarm system, and y(k) is the output of the alarm system. Let the reference value set of the input xi as Oi = {|ni = 1, 2…, Ni}, Ni is the number of reference values of xi(k), which can be defined based on expert knowledge. The reference value set of the output y(k) is Z = {Ze, e = 1, 2}, where Z1 = NA = 0 and Z2 = A = 1. Therefore, the relationship between the input xi(k) and the output y(k) can be represented by the corresponding relationship between the input reference values and the output reference values.
Step 1.2: The similarity distribution of
xi(
k) in
V = [
xi(
k),
y(
k)] relative to the reference values set
Oi is calculated by the following information transformation method:
where
represents the similarity of
xi(
k) matching input reference value
.
The similarity distribution of
y(
k) in
V = [
xi(
k),
y(
k)] matching the reference value
Ze is
Q(y) = {(
Ze,
)|
e = 1, 2}, among them:
where,
represents the similarity of
y(
k) matching the output reference value
Ze.
Therefore, each sample [
xi(
k),
y(
k)] in
V is transformed into a similarity distribution with the form
, where
represents the joint similarity of
xi(
k) matching
and
y(
k) matching
Ze, and the sample cast point table shown in
Table 1 is constructed.
represents the sum of the similarity of all samples whose input
xi(
k) matches
and output
y(
k) matches
Ze.
represents the sum of the joint similarity of all output
y(
k) matching
Ze.
represents the sum of the joint similarity of all input
xi(
k) matching
. Obviously, there is
.
Step 1.3: According to the sample cast point table, when the value of the process variable
xi(
k) is relative to the input reference value
, the belief that the output
y(
k) is relative to the output reference value
Ze can be calculate by
and
, then the alarm evidence corresponding to the input reference value
can be defined as
Therefore, the referential evidence matrix (REM) table as shown in
Table 2 can be constructed to describe the relationship between the input
xi(
k) and the output
y(
k).
3.1.2. The Transformation of Process Variables to Alarm Evidence
Step 2: For the real-time sample
xi(
t),
t = 1, 2, 3, …, it necessarily falls into the interval [
,
] composed of two reference values,
and
, and the referential alarm evidence,
and
, corresponding to these two reference values, are activated, and then the alarm evidence
corresponding to the real-time sample
xi(
t) can be obtained by the weighted sum form of
and
.
, which is represented as follows:
For ease of understanding, this alarm evidence can be rewritten as follows:
where
and
denote the belief of “No alarm (
NA)” and “alarm (
A)” respectively, and
+
= 1.
3.2. The Calculation of Interval-Valued Reliability and the Optimization of Weight
In the original ER rule, the reliability and weight of alarm evidence are generally expressed in the form of a fixed value based on expert knowledge [
22,
23]. However, since the process variables are constantly changing, the corresponding alarm evidence also changes accordingly. This single fixed reliability and weight in the fusion process may make the fusion results unreasonable. Furthermore, in the original ER rule, the reliability
r is defined as the ability of evidence to provide correct results for a particular question and is the objective nature of evidence. On the contrary, the weight
w is the importance of the current evidence relative to other evidence and is the subjective nature of evidence. Therefore, reliability is an inherent property which is not affected by other pieces of evidence. In addition, the alarm evidence changes irregularly at each moment, which makes it impossible to calculate the accurate value of the reliability by a functional relationship, so it is a more efficient way to express the reliability of alarm evidence in the form of an interval value. Unlike reliability, the weight of some evidence (a certain process variable) represents the relative importance when it is combined with other evidence (other process variables), hence it can be set as a single value and optimized according to decision objectives.
Through the above analysis for the reliability factor r and the importance weight w, this section designs the interval-valued ER rule catering for interval-type reliability, in which the reliability of each piece of alarm evidence can be adaptively adjusted on a certain interval, and the weight can be obtained by classical optimization algorithms, such as gradient descent algorithm and evolutionary algorithm. This mechanism can ensure the accuracy of the fusion process and improve the efficiency of fusion process.
Step 3: The reliability of alarm evidence is described by a continuous random variable with uniform distribution characteristics on an interval, as shown in the following form
ri represents the interval-valued reliability of alarm evidence.
and
can be calculated by the following equation
where
is the optimal reliability obtained by training set. Namely, the sample data of the process variable is defined as the training set and transformed into the alarm evidence
.
and
wi as the optimal reliability and weight, respectively, are obtained by optimizing distance between the fusion alarm evidence
mt and the standardized evidence {
fNA = (1,0,0),
fA = (0,1,0)}. Specially,
mt is obtained by Equation (6). The optimization process can be realized by genetic optimization algorithms. It should be noted that
is an optimal fixed value reliability through the training set, and the
wi is used for the entire fusion process. The optimization model based on genetic algorithm is constructed as follows:
where
ζ(
P) represents the optimization objective function,
P = {(
wi,
) |
i =1,2,3} represents the parameter set to be optimized, and the value range of
wi and
is [0, 1]. The
dE indicates the fusion result, that is, the evidence distance between the integrated alarm evidence
Mt and the standardized evidence {
fNA = (1, 0, 0),
fA = (0, 1, 0)}. This optimization process can be done through the optimization toolbox in Matlab. Finally, the performance of the model is gradually optimized due to the change of the optimized parameter set.
In Equation (17),
αi is a reliability adjustment factor based on the similarity between pieces of alarm evidence, calculated by the following equation:
where
di is the distance defined in Equation (1) between the alarm evidence
and the normalized evidence
fNA,
fA in the discernment framework, shown as follows:
where the alarm evidence can be represented by
in
Section 2. Thus, the order of
G is 3, that is:
di represents the adjustment of interval-valued reliability according to dynamical changing of process variable information. Thus, the interval-valued reliability
ri is a precise description to the statistical property of the alarm evidence in real time.
Remark 1. In this section, according to the analysis of reliability described as interval-valued form, interval-valued reliability does not mean that the reliability is chosen as a fixed value or a specific part of interval. The purpose of interval-valued reliability is to portray the variation of reliability with the input information by taking equal probability values in a specific interval. Therefore, among the common probability distributions of continuous random variables, the uniform distribution is more suitable for describing interval-valued reliability due to its characteristic of equal probability distribution.
3.3. The Fusion of Alarm Evidence Based on the Interval-Valued ER Rule
This section extends the original ER rule in Equation (5) to the interval-valued ER rule. According to the interval-valued ER rule, the pieces of alarm evidence from the real-time samples are fused to obtain the integrated alarm evidence Mt = (Mt (NA), Mt(A), Mt(Θ)). The specific process is shown as follows.
Step 4.1: First, the interval-valued ER rule is shown as follows:
where the interval-valued reliability
ri and weight
wi of
can be obtained in
Section 3.2. According to the proposed interval-valued ER rule,
Lt is the fusion result by fusing alarm evidence. Obviously,
Lt is an interval whose optimization model is established as follows:
The extreme value of Lt is calculated by optimizing the above model.
Step 4.2: For making alarm result conveniently, according to mathematical principle, the integrated alarm evidence
Mt = (
Mt (
NA),
Mt(
A),
Mt(
Θ)) is obtained by means of mathematical expectations for fusion results
Lt.
where
E(
Lt) represents the mathematical expectation of
Lt and Ω is an area determined by
ri.
In addition, the proof of the following theorems can verify the interval-valued ER rule proposed in this paper.
Theorem 1. Expectation and variance of Lt always exist.
Proof of Theorem 1. Assuming i = 2, Equation (25) can be considered as a double integral of r1 and r2. According to the property of the double integral, it can be concluded that the integral must exist as long as the integrand is continuous over the definition domain. Obviously, the integrand is a continuous binary elementary function in the equation. Therefore, the expectation and variance of Lt always exist. By analogy, the theorem still applies when .□
Theorem 2. The original ER rule is a special case of the interval-valued ER rule.
Proof of Theorem 2. Supposing
i = 2,
and
of intervals tend to a quantitative value, shown as follows
From Equation (22), the fusion equation is expressed as follows
In the original ER rule, the fusion result is shown as follows
Actually, the expectation of
Lt can be further calculated by
where Ω is the region defined by
r1 and
r2.
Equation (33) is simplified as follows
According to L’hospital law, Equation (34) can be further calculated by the following equation
When
,
approaches to 0. Therefore, we have
Obviously, when and of interval tend to the quantitative value, . It shows that the original ER rule is a special case of the interval-valued ER rule.
Similarly, when i > 2, the theorem still holds.□
Theorem 3. In Equation (22), Lt is a probability function about (r1, r2, …, rI). Taking two pieces of evidence as an example, there exists at least one pointsatisfying the following equation.
Proof of Theorem 3. Suppose c1 and C1 denote the upper and lower bounds of , respectively, which can be calculated by the following optimization model:
When
is considered as greater than 0, the following inequality can be obtained:
Based on the property of the double integral, we have
and
From the above equations, we have
From Equation (45), E(U) is a determined value between c1 and C1. Obviously, Lt (r1, r2) is a continuous function. According to the intermediate theorem of continuous functions on the closed regions, there is at least one point on Ω that makes equal to E(U). Based on the above derivation, the theorem can be extended to the fusing situation with more than two pieces of evidence.□
3.4. Making Alarm-Decision Based on Integrated Alarm Evidence
Step 5: Through the fusion method in
Section 3.3, the integrated alarm evidence
Mt = (
Mt (
NA),
Mt(
A),
Mt(
Θ)) can be obtained. The alarm decision is made, according to the following alarm-decision criteria:
if Mt (
NA) ≥
Mt(
A),
output yt(
k) = 0,
no alarm;
if Mt (
NA) <
Mt(
A),
output yt(
k) = 1,
alarm.
4. Comparative Analysis of Experiment
This section demonstrates the design process of the multivariate alarm method based on the interval-valued ER rule through the following experiment. The Tennessee Eastman (TE) process as a chemical benchmark simulation model as shown in
Figure 2, provides a display environment for evaluating process control and monitoring methods and has been widely used as a research platform for continuous process monitoring, regulation, and diagnosis [
27]. According to
http://web.mit.edu/braatzgroup/links.html (accessed on 13 August 2022), its experimental data can be downloaded. The TE process has 53 process variables and 21 different fault types [
28]. The process variables include 12 operational variables and 41 measured variables (22 continuous, 19 component variables). In this benchmark set, each fault in the training set contains 480 samples, and each fault in the test set contains 960 samples, where the fault corresponding to the 161st sample are introduced from the eighth hour, with a sampling interval of 3 min. To address the problem of less training data in the dataset, according to the principle of the TE process and its data characteristics, this experiment combines the original training set with the first 160 samples in the test set under normal conditions to form a new training set. This section takes the reactor fault in the TE process as an alarm example and selects the flow rates of process variables material A, B, and C as input variables
x1(
k),
x2(
k) and
x3(
k), shown as
Figure 3,
Figure 4 and
Figure 5, and the effectiveness of the proposed method is verified by comparison of other traditional alarm design methods and the original ER rule method.
Step 1 (The construction of REM): Firstly, for the three input variables
xi(
k),
i = 1, 2, 3, this newly composed 640 samples of each sequence are considered as training samples. According to expert knowledge, the reference value sets of the input variable
xi(
k) are
O1 = {14, 15.2, 16.4, 17.6, 18.8, 20, 21.2, 22.4, 23.6, 24.8, 26},
O2 = {51, 52.4, 53.8, 55.2, 56.6, 58, 59.4, 60.8, 62.2, 63.6, 65},
O3 = {13.1, 13.2, 13.3, 13.4, 13.5, 13.6, 13.7, 13.8, 13.9, 14.0, 14.1}, and the reference value set of the output
y(
k) is {0,1}. According to
Section 3.1.1, the referential evidence matrixes (REMs) are established by Equations (7)–(13), as shown in
Table 3,
Table 4 and
Table 5, and the alarm evidence
corresponding real-time sample is obtained by activating the corresponding REM. According to
Section 3.2, the optimal reliabilities and weights of the alarm evidence are obtained, i.e.,
= 0.74,
= 0.70,
= 0.60 and
w1 = 0.92,
w2 = 0.86,
w3 = 0.90.
Meanwhile, based on the above training set, some traditional alarm design methods are selected as comparison methods to obtain the optimal alarm threshold, such as the 3
σ method commonly used in industry, the filtering method, the time delay method, the FAP-MAP method based on multivariate alarm threshold optimization [
29]. Among the traditional alarm design method, the FAP-MAP method constructs the objective function
, where
Px,f and
Py,f are the false alarm rate (FAR) for variables
x and
y, respectively;
Px,m and
Py,m are the missed alarm rate (MAR) of variables
x and
y respectively;
w1 and
w2 are the weight factors, generally
w1 =
w2 = 0.5;
x0 and
y0 are the optimal thresholds [
14]. In each traditional alarm design method, the optimal thresholds of corresponding variable are shown in
Table 6.
Step 2 (The transformation of process variables to alarm evidence): Next, the alarm system based on the interval-valued ER rule is designed. According to the simulation platform
http://depts.washington.edu/control/LARRY/TE/download.html (accessed on 13 August 2022), the test set of input variable
xi(
k) is randomly generated, including 900 samples. The first step is to obtain the alarm evidence at each moment. The reference values of input and output are obtained in the training experiment. According to the REM shown in
Table 3,
Table 4 and
Table 5, the real-time samples are transformed into corresponding alarm evidence.
Step 3 (The calculation of interval-valued reliability and the optimization of weight): Furthermore, the optimal reliabilities and weights of alarm evidence are obtained by Equation (18) in the training experiment, and the reliability adjustment factor αi corresponding to alarm evidence at each moment is calculated by Equations (19)–(21), and the interval of ri is obtained combining Equation (17).
Step 4 (The fusion of alarm evidence based on the interval-valued ER rule): According to
Section 3.3, the original ER rule Equation (6) is extended to the interval-valued ER rule Equation (22), which can fuse the alarm evidence
(
i = 3) to get integrated alarm evidence
Lt.
Lt is an interval, whose optimization model is established by Equation (23). The extreme value of
Lt is calculated by optimizing the model. For making alarm results conveniently, according to mathematical principle, the integrated alarm evidence
Mt = (
Mt (
NA),
Mt(
A),
Mt(
Θ)) is obtained by Equations (24) and (25).
Mt is obtained based on the interval-valued ER rule.
Step 5 (Alarm-decision making based on integrated alarm evidence): Finally, based on the alarm-decision criteria of
Section 3.4, the alarm decision is made through
Mt = (
Mt (
NA),
Mt(
A),
Mt(
Θ)), and missed alarm number (
m(MA)) is 31 and false alarm number (
m(FA)) is 1. In addition, another alarm system based on the original ER rule is designed as a comparative experiment. Repeat the above experimental steps, when using Equation (23) to fuse the alarm evidence
, the optimal fusion weights {
w1 = 0.92,
w2 = 0.86,
w3 = 0.90} and optimal reliabilities {
= 0.74,
= 0.70,
= 0.60} are obtained according to the training set, and the results are
m(MA) = 79 and
m(FA) = 9 respectively.
Table 7 shows a part of the interval-valued reliability under the interval-valued ER rule. As can be shown in
Table 7, the interval-valued reliability
ri dynamically changes according to the input information in real-time. It is obvious that this is more in line with the actual change of the input variable. On the contrary, whether the optimal values of reliability are obtained based on expert knowledge or based on optimization of the training set, reliabilities of the original ER rule are quantitative values in each fusion, which limits the performance of designing alarm system based on the ER rule to a certain extent.
In order to show the effectiveness of the proposed method, use the above proposed simulation platform to randomly generate 100 test sets, and each test set includes 900 samples. Repeat the above experimental steps and perform multiple test experiment. Calculate the average of
m(MA) and
m(FA) for each variable, shown in
Figure 5 and
Figure 6.
As shown in
Figure 6 and
Figure 7, under the 3σ method,
m(MA) = 604.3 and
m(FA) = 2.5 for
x1,
m(MA) = 356.1 and
m(FA) = 3.6 for
x2,
m(MA) = 180.7 and
m(FA) = 3.8 for
x3; all results are higher than the interval-valued ER rule method, especially the
m(MA) of
x1 is very high, so the 3σ method is inappropriate in practical applications, while
m(MA) = 30.1 and
m(FA) = 0.6 under the interval-valued ER rule method, which is far below the 3σ method. Under the filtering method,
m(MA) = 542.5 and
m(FA) = 2.5 for
x1,
m(MA) = 302.4 and
m(FA) = 3.2 for
x2,
m(MA) = 123.7 and
m(FA) = 3.9 for
x3. The filtering method has some advantages over the 3σ method, but
m(MA) and
m(FA) of the filtering method is still relatively high compared with the interval-valued ER rule method. Under the time delay method,
m(MA) = 529.2 and
m(FA) = 2.4 for
x1,
m(MA) = 311.3 and
m(FA) = 3.2 for
x2,
m(MA) = 141.4 and
m(FA) = 3.4 for
x3. The performance of the time delay method is similar to that of the filtering method. Under the FAP-MAP method,
m(MA) = 506.3 and
m(FA) = 3.1 for
x1,
m(MA) = 281.6 and
m(FA) = 3.3 for
x2,
m(MA) = 130.7 and
m(FA) = 3.7 for
x3. The performance of the FAP-MAP method is the best among the traditional methods, but it also has a certain gap with the interval-valued ER rule method. According to the above results, traditional alarm design methods expose the limitations in multivariate industrial processes, i.e., traditional alarm design methods only consider the alarm results of univariate and lack the ability to handle multivariable alarms simultaneously, which makes the alarm result lack consistency. On the contrary, the interval-valued ER rule method obtains consistent results compared with traditional alarm design methods for multivariate alarm system. It can be seen from
Figure 6 and
Figure 7 that
m(MA) and
m(FA) under the interval-valued ER rule method are the lowest compared with traditional alarm design methods, and they are 30.1 and 0.6 respectively. In the interval-valued ER rule method, the alarm evidence is obtained through the data-driven REM, which can be considered as a lossless conversion from process variables to alarm evidence and accurately describes the statistical characteristics of the sample data, so this can significantly reduce
m(FA) and
m(MA).
In addition, as shown in
Figure 6 and
Figure 7, the
m(MA) = 80.2 and
m(FA) = 2.5 for the original ER rule method, and the
m(MA) and
m(FA) under the interval-valued ER rule method are reduced of 50.1 and 1.9 respectively compared with the original ER rule method. On the one hand, because fixed reliability lacks the ability to handle objective uncertainty, the effectiveness of the original ER rule method is certainly not as good as the interval-valued ER rule method. On the other hand, the interval-valued ER rule can accurately describe process variables by the adjustment of interval-valued reliability. The reliability of alarm evidence is described by the form of random variables, which makes the interval-valued ER rule possess the ability to maximize the process of input information. In summary, the alarm design method based on the interval-valued ER rule can greatly reduce both
m(MA) and
m(FA).
However, the alarm design method based on the interval-valued ER rule also has certain weaknesses. Due to the limitation of ER algorithm, when the dimensionality of process variables increases, the computational difficulty also rises correspondingly. To address the above weaknesses, in future work, we consider introducing dimensionality reduction methods as well as vectorization methods to reduce the dimensionality of process variables and filter out the appropriate process variables, which can reduce the computational difficulty and obtain the most rational alarm result.