Various Blockchain Governance Games: A Review
Abstract
:1. Introduction
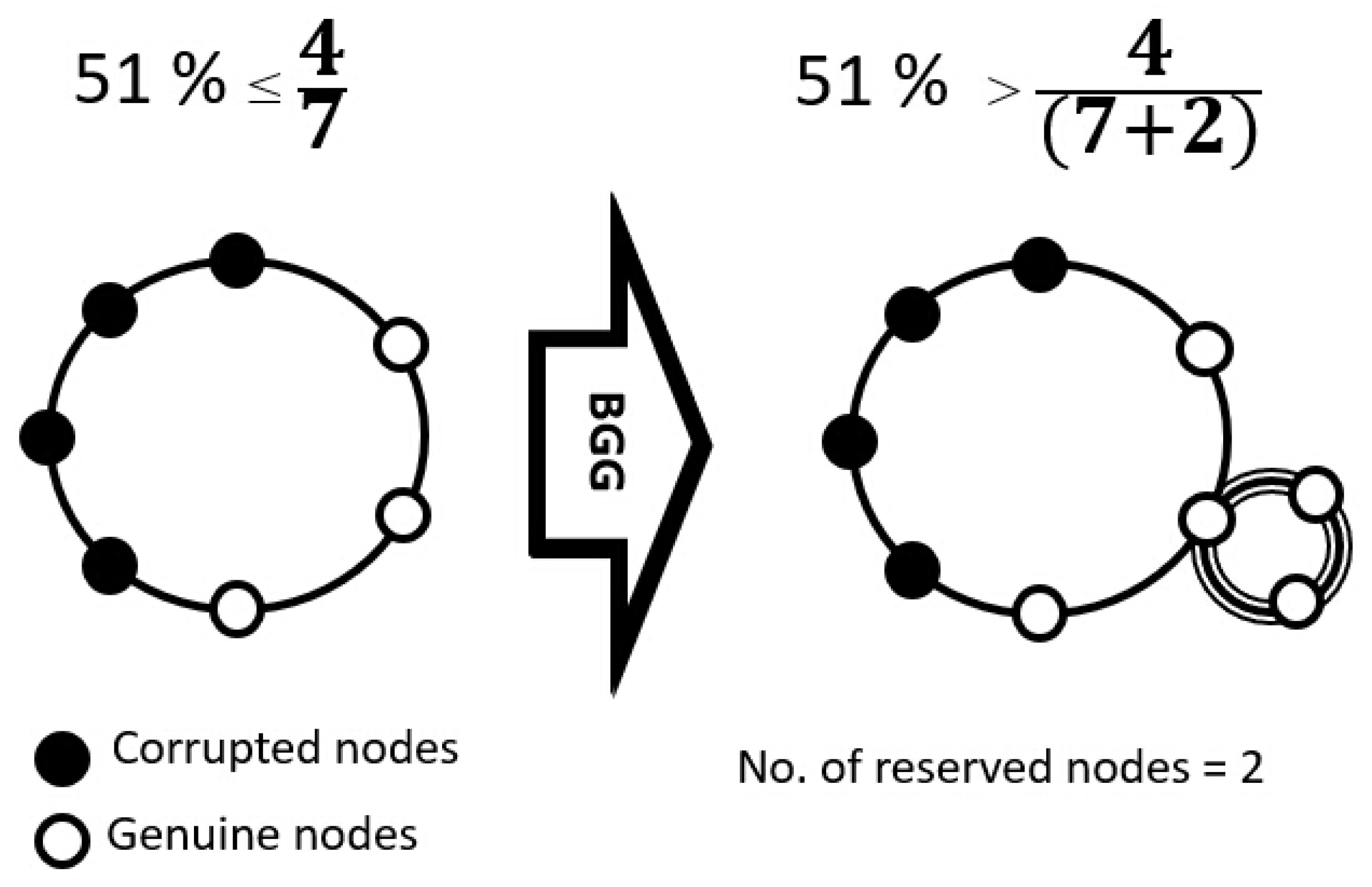
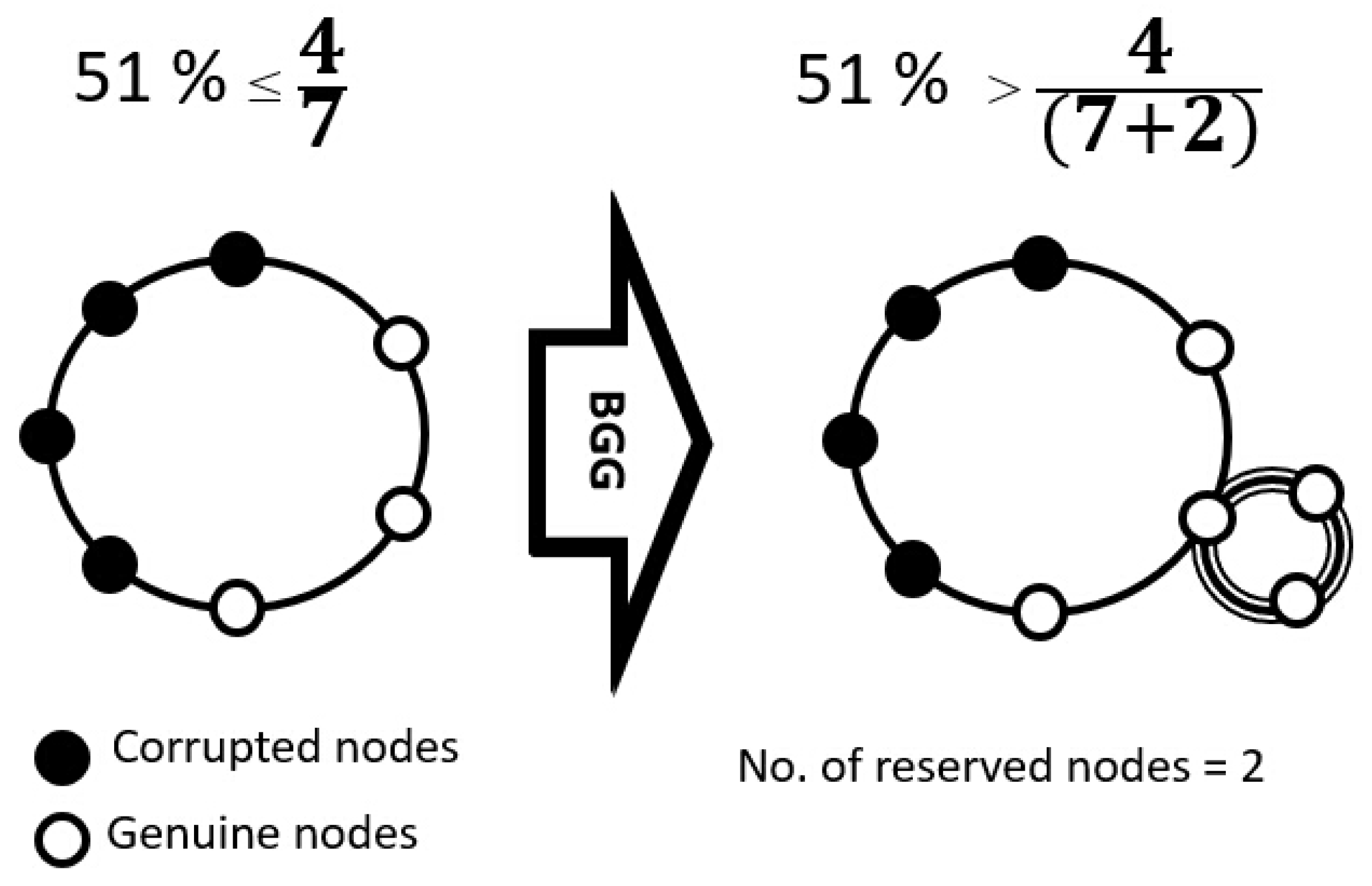
- Blockchain Governance Game (BGG) [14] is a theoretical model that provides a stochastic game framework for determining the best strategies to prevent network failures. The combination of a mixed strategy game and fluctuation theories yields analytically tractable results for enhancing decentralized network securities.
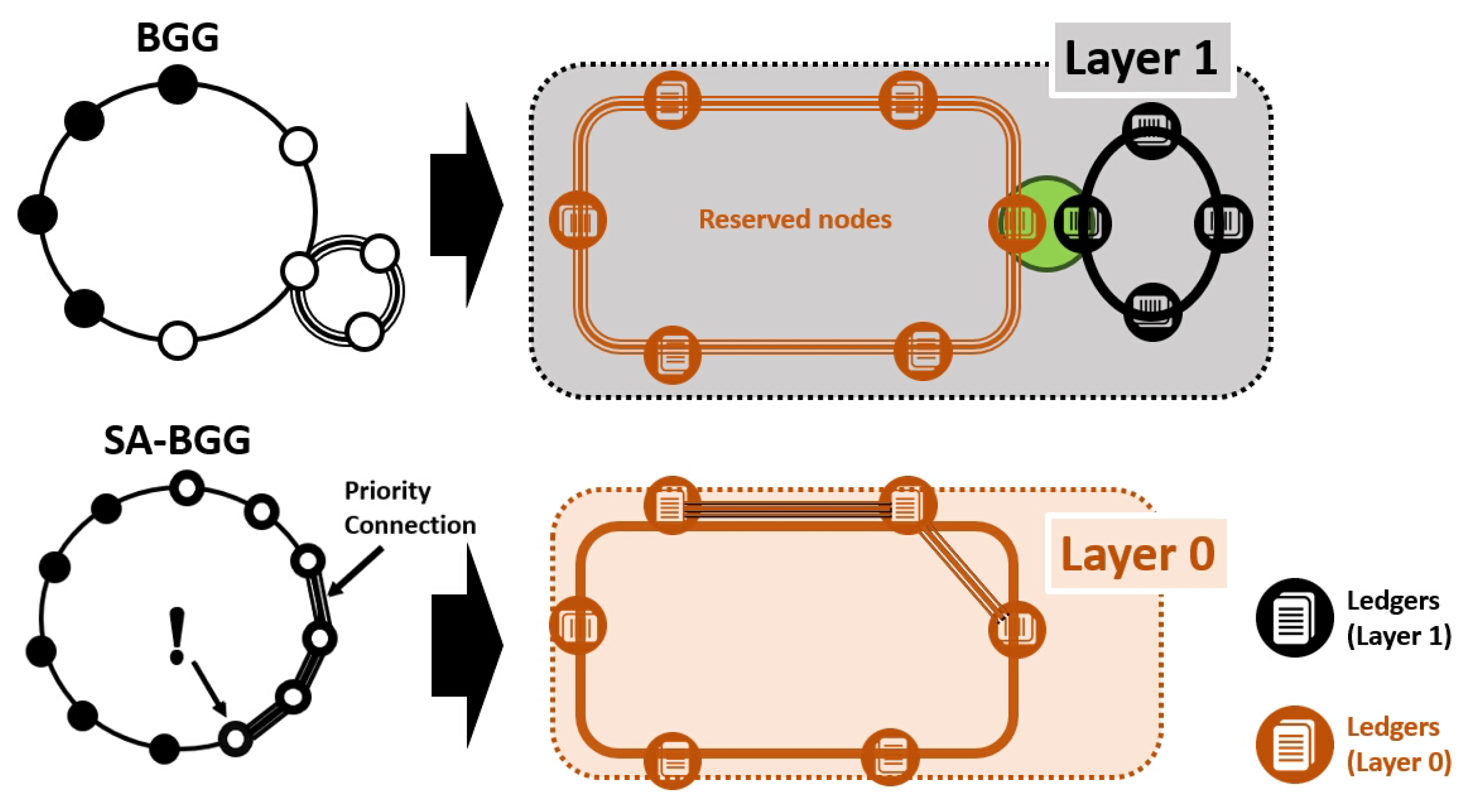
- Strategic Alliance for Blockchain Governance Game (SABGG) provides an alternative method for reserving real nodes [15]. A novel secure blockchain network framework has been suggested for preventing damages. From a strategic management standpoint, the alliance concept is applied on top of a general BGG. This hybrid mathematical model aims to determine the strategies for protecting a network via strategic alliances with other nodes. This model is a combination of a strategic management framework on top of a conventional BGG.
- Multi-Layered Blockchain Governance Game (MLBGG) [16] is a complex model which is an analytical stochastic model for performing a security operation in order to protect entire multi-layered networks from attackers. This study thoroughly analyzes the set of networks using explicit mathematical forms for predicting when a security operation should be performed.
2. Stochastic Models of Blockchain Governance Game Variants
2.1. Blockchain Governance Game
2.2. Strategic Alliance for Blockchain Governance Game
2.3. Multi-Layered Blockchain Governance Game
3. Blockchain Governance Game Applications
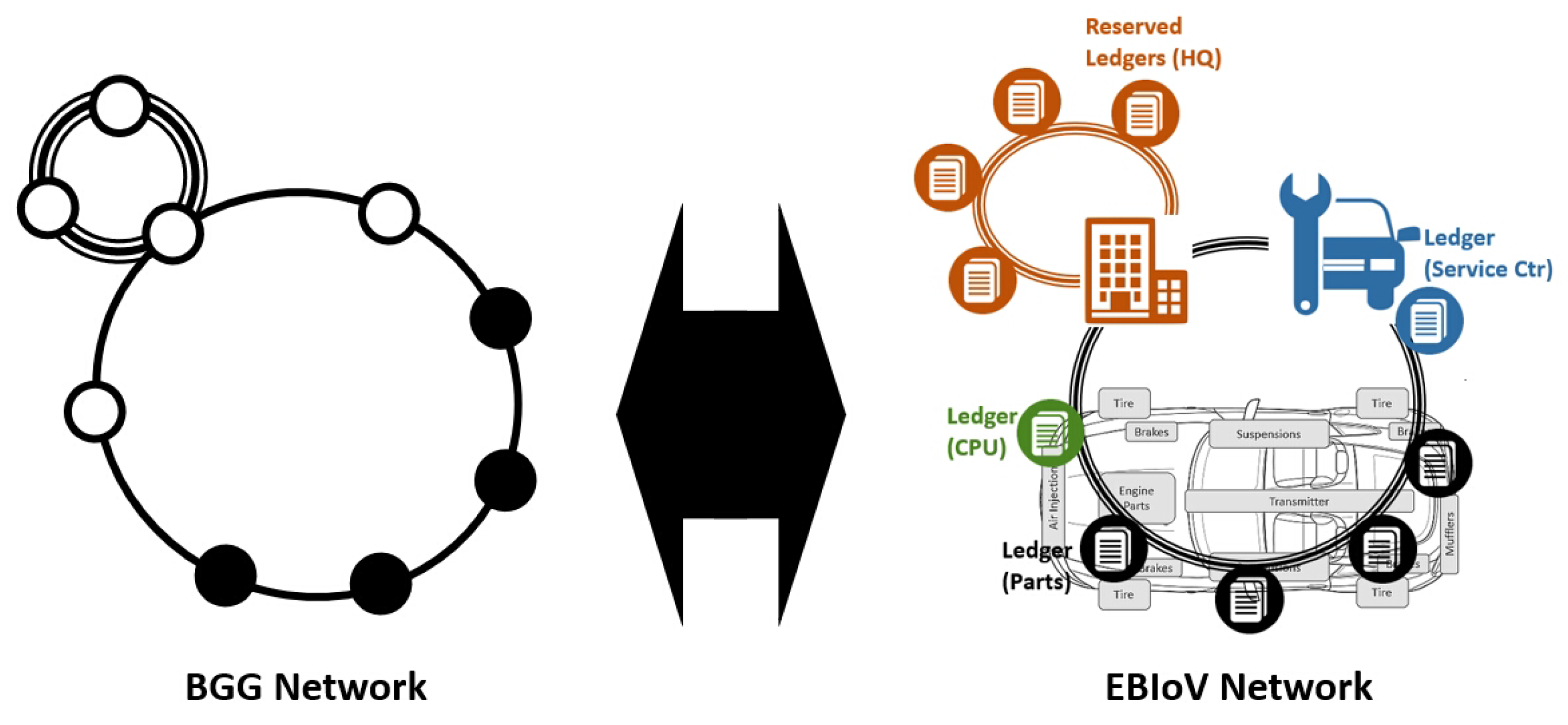
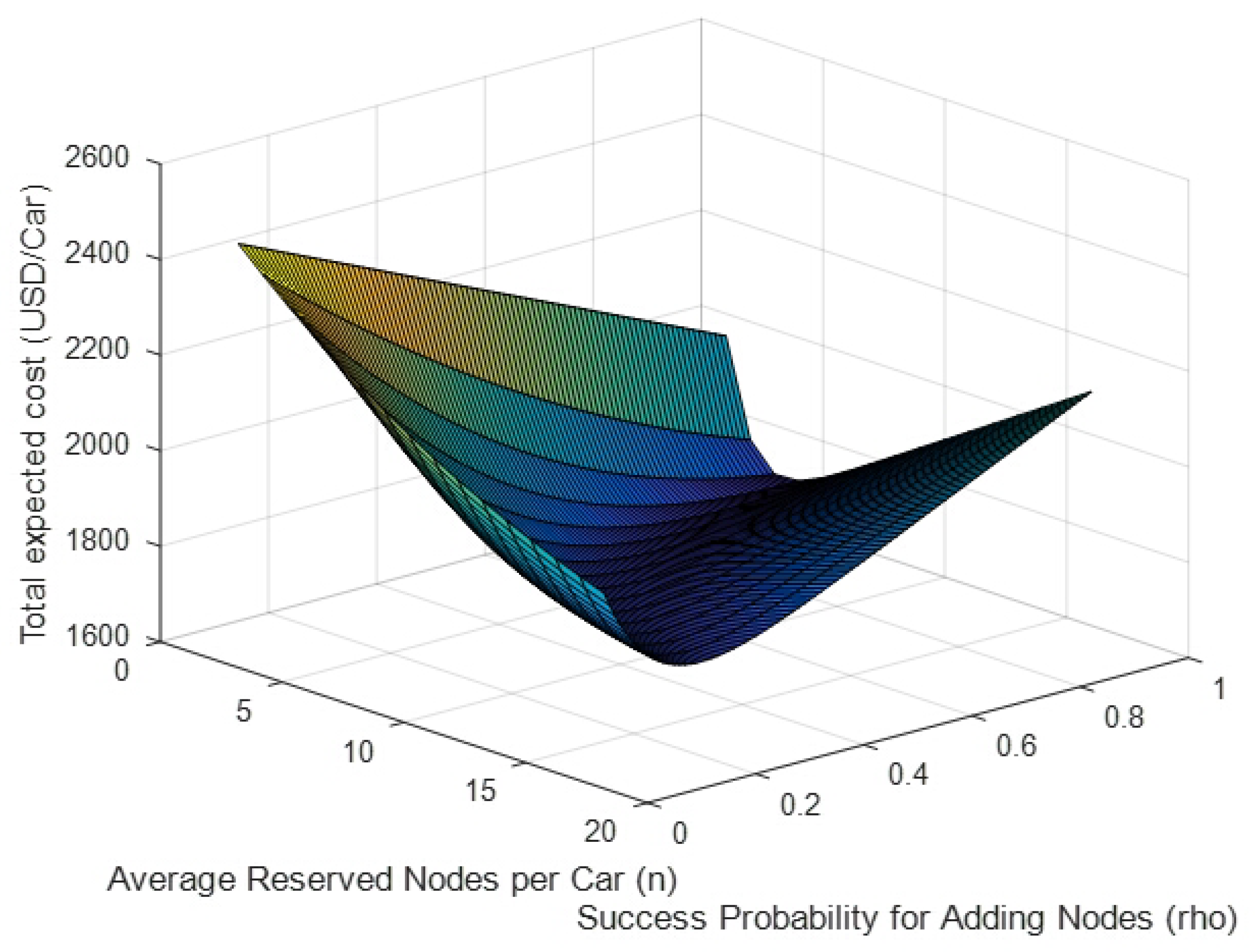
3.1. Automotive Vehicle Network Security for Connected Cars
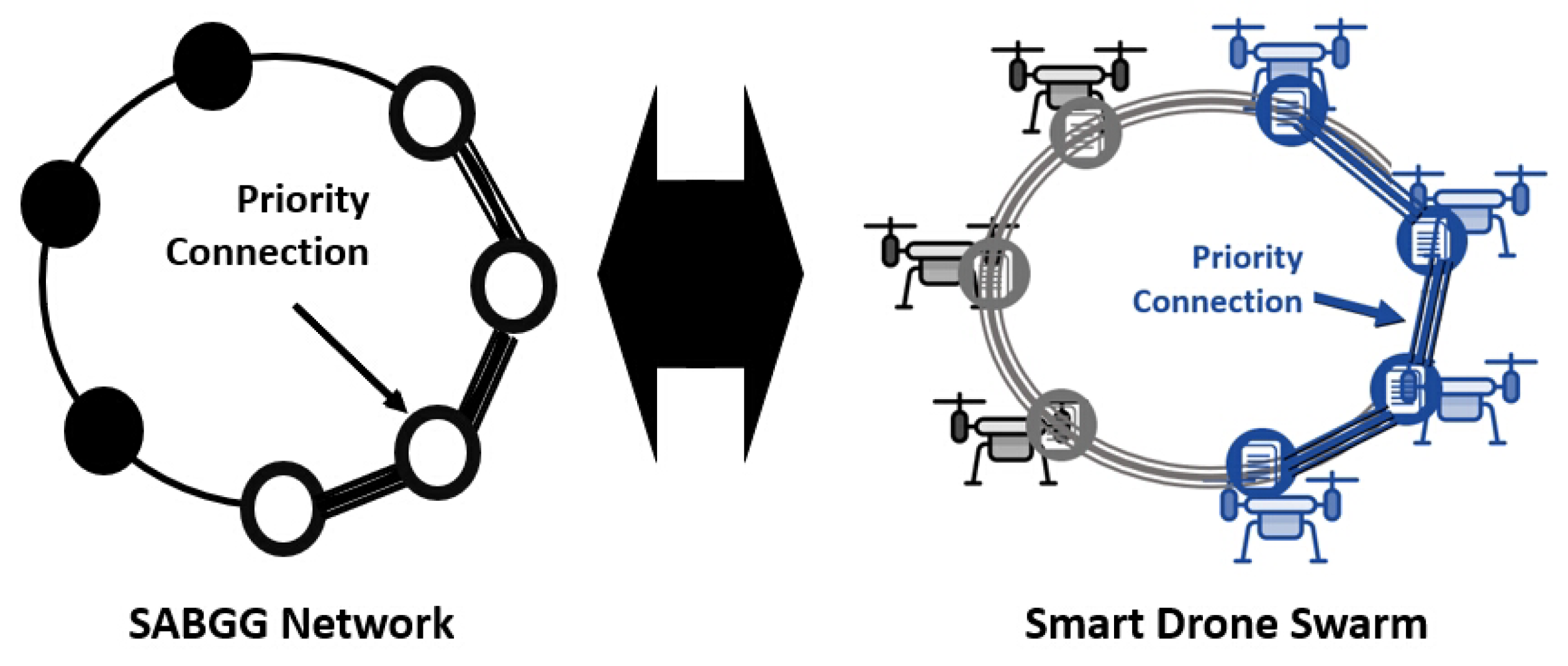
3.2. Security Architecture of Smart Drone Swarm
4. Conclusions and Future Research
- AI-enabled BGG model: predicting the moment of attacks is always challenging and adapting machine learning techniques for forecasting could be considered to improve the BGG models.
- Developing the applications for MLBGG: the direct applications for MLBGG (multi-layered BGG) have not been found to date.
- Actual implementations of BGG models: implementing BGG models with the VRF on real blockchain networks is a challenging task. It is noted that the VRF shall be implemented on the Ethereum virtual machine before implementing the BGGs to see how these theorical models actually work.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. The Marginal Mean of the First Exceed Index under Memoryless Observation Process
Appendix A.1. Memoryless BGG Model
- is a linear functional with fixed points at constant functions;
- .
Appendix A.2. Memoryless SABGG Model
References
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 December 2021).
- Beikverdi, A.; Song, J. Trend of centralization in Bitcoin’s distributed network. In Proceedings of the 2015 IEEE/ACIS 16th International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Takamatsu, Japan, 1–3 June 2015; pp. 1–6. [Google Scholar]
- Yli-Huumo, I.; Ko, D.; Choi, S.; Park, S.; Smolander, K. Where Is Current Research on Blockchain Technology? A Systematic Review. PLoS ONE 2016, 11, e0163477. [Google Scholar] [CrossRef] [PubMed]
- Liu, Z.; Luong, N.C.; Wang, W.; Niyato, D.; Wang, P.; Liang, Y.-C.; Kim, D.I. A Survey on Applications of Game Theory in Blockchain (2019). Available online: https://arxiv.org/abs/1902.10865 (accessed on 1 May 2019).
- Decker, C.; Wattenhofer, R. Information propagation in the Bitcoin network. In Proceedings of the IEEE P2P 2013 Proceedings, Trento, Italy, 9–11 September 2013; pp. 1–10. [Google Scholar]
- Kim, W. Bitcoin, Blockchain Mechanism and Its Evolution. 2018. Available online: http://www.itfind.or.kr/publication/ (accessed on 1 December 2021). (In Korean).
- Narayanan, A.; Clar, J. Bitcoin’s Academic Pedigree. Mag. Commun. ACM 2017, 60, 36–45. [Google Scholar] [CrossRef]
- Weiss, M.; Corsi, E. Bitfury: Blockchain for Government. HBP Case 2018, 12, 818-031. [Google Scholar]
- Armknecht, F.; Karame, G.O.; Mandal, A.; Youssef, F.; Zenner, E. Ripple: Overview and Outlook. In Trust and Trustworthy Computing, Proceedings of the 8th International Conference, Heraklion, Greece, 24–26 August 2015; Lecture Notes in Computer Science; Springer: Cham, Switzerland, 2015; Volume 9229, pp. 163–180. [Google Scholar]
- Bhuiyan, B. An Overview of Game Theory and Some Applications. Philos. Prog. 2016, 59, 111–128. Available online: https://www.banglajol.info/index.php/PP/article/view/36683 (accessed on 1 May 2019). [CrossRef]
- Antonopoulos, A.M. Mastering Bitcoin: Programming the Open Blockchain, 2nd ed.; O’Reilly: Sebastopol, CA, USA, 2017. [Google Scholar]
- Eyal, I.; Sirer, E. Majority Is Not Enough: Bitcoin Mining Is Vulnerable; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2014; Volume 8437, pp. 436–454. [Google Scholar]
- Garay, J.; Kiayias, A.; Leonardos, N. The Bitcoin Backbone Protocol: Analysis and Applications; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2015; Volume 9057, pp. 281–310. [Google Scholar]
- Kim, S.-K. Blockchain Governance Game. Comput. Ind. Eng. 2019, 136, 373–380. [Google Scholar] [CrossRef]
- Kim, S.-K. Strategic Alliance for Blockchain Governance Game. Probab. Eng. Inf. Sci. 2020, 36, 184–200. [Google Scholar] [CrossRef]
- Kim, S.-K. Multi-Layered Blockchain Governance Game. Axioms 2022, 11, 109. [Google Scholar] [CrossRef]
- Kang, J.; Xiong, Z.; Niyato, D.; Ye, D.; Kim, D.I.; Zhao, J. Toward Secure Blockchain-Enabled Internet of Vehicles: Optimizing Consensus Management Using Reputation and Contract Theory. IEEE Trans. Veh. Technol. 2019, 68, 2906–2920. [Google Scholar] [CrossRef]
- Lohachab, A.; Garg, S.; Kang, B.; Amin, M.B.; Lee, J.; Chen, S.; Xu, X. Towards Interconnected Blockchains: A Comprehensive Review of the Role of Interoperability among Disparate Blockchains. ACM Comput. Surv. 2021, 54, 1–39. [Google Scholar] [CrossRef]
- Erfan, F.; Bellaiche, M.; Halabi, T. Game-theoretic Designs for Blockchain-based IoT: Taxonomy and Research Directions. In Proceedings of the 2022 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Newark, CA, USA, 15–18 August 2022; pp. 27–37. [Google Scholar]
- Liu, Y.; Lu, Q.; Zhu, L.; Paik, H.Y.; Staples, M. A systematic literature review on blockchain governance. J. Syst. Softw. 2023, 197, 111576. [Google Scholar] [CrossRef]
- Alkadi, R.; Alnuaimi, N.; Yeun, C.Y.; Shoufan, A. Blockchain Interoperability in Unmanned Aerial Vehicles Networks: State-of-the-Art and Open Issues. IEEE Access 2022, 10, 14463–14479. [Google Scholar] [CrossRef]
- Liu, Z.; Luong, N.C.; Wang, W.; Niyato, D.; Wang, P.; Liang, Y.C.; Kim, D.I. A Survey on Blockchain: A Game Theoretical Perspective. IEEE Access 2019, 7, 47615–47643. [Google Scholar] [CrossRef]
- Yang, X.; Gong, G.; Tian, Y. Optimal Game Theory in Complicated Virtual-modeling and CGF Decision-making with Multi-granularities. In Proceedings of the 2008 International Conference on Smart Manufacturing Application, Goyangi, Republic of Korea, 9–11 April 2008; pp. 95–99. [Google Scholar]
- Yang, X.; Gong, G.; Tian, Y. Generalized Optimal Game Theory in virtual decision-makings. In Proceedings of the 2008 Chinese Control and Decision Conference, Yantai, China, 2–4 July 2008; pp. 196–1964. [Google Scholar]
- Kim, S.-K. Enhanced IoV Security Network by Using Blockchain Governance Game. Mathematics 2021, 9, 109. [Google Scholar] [CrossRef]
- Kim, S.-K. Advanced Drone Swarm Security by Using Blockchain Governance Game. Mathematics 2022, 10, 3338. [Google Scholar] [CrossRef]
- Ramirez, M.A.; Kim, S.-K.; Al Hamadi, H.; Damiani, E.; Byon, Y.-J.; Kim, Y.-J.; Cho, C.-S.; Yeun, C.Y. Poisoning Attacks and Defenses on Artificial Intelligence: A Survey. 2022. Available online: https://arxiv.org/abs/2202.10276 (accessed on 1 April 2023).
- Biggio, B.; Corona, I.; Maiorca, D.; Nelson, B.; Šrndić, N.; Laskov, P.; Giacinto, G.; Roli, F. Evasion attacks against machine learning at test time. Proc. Joint Eur. Conf. Mach. Learn. Knowl. Discov. Databases 2013, 8190, 387–402. [Google Scholar]
- Paudice, A.; Muñoz-González, L.; Gyorgy, A.; Lupu, E.C. Detection of adversarial training examples in poisoning attacks through anomaly detection. arXiv 2018, arXiv:1802.03041. [Google Scholar]
- Liu, X.; Xie, L.; Wang, Y.; Zou, J.; Xiong, J.; Ying, Z.; Vasilakos, A.V. Privacy and Security Issues in Deep Learning: A Survey. IEEE Access 2020, 9, 4566–4593. [Google Scholar] [CrossRef]
- Xue, M.; Yuan, C.; Wu, H.; Zhang, Y.; Liu, W. Machine Learning Security: Threats, Countermeasures, and Evaluations. IEEE Access 2020, 8, 4720–74742. [Google Scholar] [CrossRef]
- Qi, X.; Zeyi, T.; Zijiang, H.; Qun, L. FABA: An algorithm for fast aggregation against byzantine attacks in distributed neural networks. In Proceedings of the Twenty-Eighth International Joint Conference on Artificial Intelligence (IJCAI), Macao, China, 10–16 August 2019; pp. 4824–4830. [Google Scholar]
- Wang, B.; Gong, N.Z. Stealing hyperparameters in machine learning. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 36–52. [Google Scholar]
- Tramer, F.; Zhang, F.; Juels, A.; Reiter, M.K.; Ristenpart, T. Stealing machine learning models via prediction apis. In Proceedings of the 25th USENIX Security Symposium, USENIX Security 16, Austin, TX, USA, 11 August 2016; pp. 601–618. [Google Scholar]
- Juuti, M.; Szyller, S.; Marchal, S.; Asokan, N. PRADA: Protecting against DNN model stealing attacks. arXiv 2018, arXiv:1805.02628. [Google Scholar]
- Chen, Z.; Lv, N.; Liu, P.; Fang, Y.; Chen, K.; Pan, W. Intrusion Detection for Wireless Edge Networks Based on Federated Learning. IEEE Access 2020, 8, 217463–217472. [Google Scholar] [CrossRef]
- Chakarov, A.; Nori, A.; Rajamani, S.; Sen, S.; Vijaykeerthy, D. Debugging machine learning tasks. arXiv 2016, arXiv:1603.07292v1. [Google Scholar]
- Kleinrock, L. Queueing Systems, Volume 1: Theory; Wiley-Interscience: New York, NY, USA, 1975. [Google Scholar]
- Kim, Y.; Lim, H. Multi-Agent Reinforcement Learning-Based Resource Management for End-to-End Network Slicing. IEEE Access 2021, 9, 56178–56190. [Google Scholar] [CrossRef]
- Dshalalow, J.H. First Excess Level Process, Advances in Queueing; CRC Press: Boca Raton, FL, USA, 1995; pp. 244–261. [Google Scholar]
- Dshalalow, J.H.; Ke, H.-J. Layers of noncooperative games. Nonlinear Anal. 2009, 71, 283–291. [Google Scholar] [CrossRef]
- Whittington, R.; Regnér, P.; Angwin, D.; Johnson, G.; Scholes, K. Exploring Strategy Text and Cases, 11th ed.; Pearson: Harlow, UK, 2017. [Google Scholar]
- Dorri, A.; Steger, M.; Kanhere, S.S.; Jurdak, R. BlockChain: A Distributed Solution to Automotive Security and Privacy. IEEE Commun. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef]
- Baker, J. Edge Computing—The New Frontier of the Web. 2017. Available online: https://hackernoon.com/edge-computing-a-beginners-guide-8976b6886481 (accessed on 1 December 2021).
- ERPINNEW. Fog Computing vs. Edge Computing. 2017. Available online: https://erpinnews.com/fog-computing-vs-edge-computing (accessed on 1 May 2019).
- Cisco Networking Academy. Connecting Networks Companion Guide; Cisco Press: Indianapolis, IN, USA, 2014. [Google Scholar]
- Rouse, M. Internet of Vehicles. 2018. Available online: https://whatis.techtarget.com/definition/Internet-of-Vehicles (accessed on 1 May 2019).
- Kim, S.; Shrestha, R. Internet of Vehicles, Vehicular Social Networks, and Cybersecurity. In Automotive Cyber Security; Springer: Singapore, 2020. [Google Scholar]
- Micali, S.; Vadhan, S.; Rabin, M. Verifiable random functions. In Proceedings of the 40th IEEE Symposium on Foundations of Computer Science, New York, NY, USA, 17–19 October 1999; pp. 120–130. [Google Scholar]
- Dodis, Y.; Yampolskiy, A. A Verifiable Random Function with Short Proofs and Keys. Lect. Notes Comput. Sci. 2005, 3386, 416–431. [Google Scholar]
- Gorbunov, S. Algorand Releases First Open-Source Code: Verifiable Random Function. 2018. Available online: https://medium.com/algorand/ (accessed on 1 May 2019).
- Zhao, W. MIT Professor’s Blockchain Protocol Nets 62 Million in New Funding. 2018. Available online: https://www.coindesk.com/mit-professors-Blockchain-protocol-nets-62-million-in-new-funding (accessed on 1 May 2019).
- Kihei, B.; Copeland, J.A.; Chang, Y. Automotive Doppler sensing: The Doppler profile with machine learning in vehicle-to-vehicle networks for road safety. In Proceedings of the 2017 IEEE 18th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Sapporo, Japan, 3–6 July 2017; pp. 1–5. [Google Scholar]

Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, S.-K. Various Blockchain Governance Games: A Review. Mathematics 2023, 11, 2273. https://doi.org/10.3390/math11102273
Kim S-K. Various Blockchain Governance Games: A Review. Mathematics. 2023; 11(10):2273. https://doi.org/10.3390/math11102273
Chicago/Turabian StyleKim, Song-Kyoo (Amang). 2023. "Various Blockchain Governance Games: A Review" Mathematics 11, no. 10: 2273. https://doi.org/10.3390/math11102273
APA StyleKim, S.-K. (2023). Various Blockchain Governance Games: A Review. Mathematics, 11(10), 2273. https://doi.org/10.3390/math11102273





