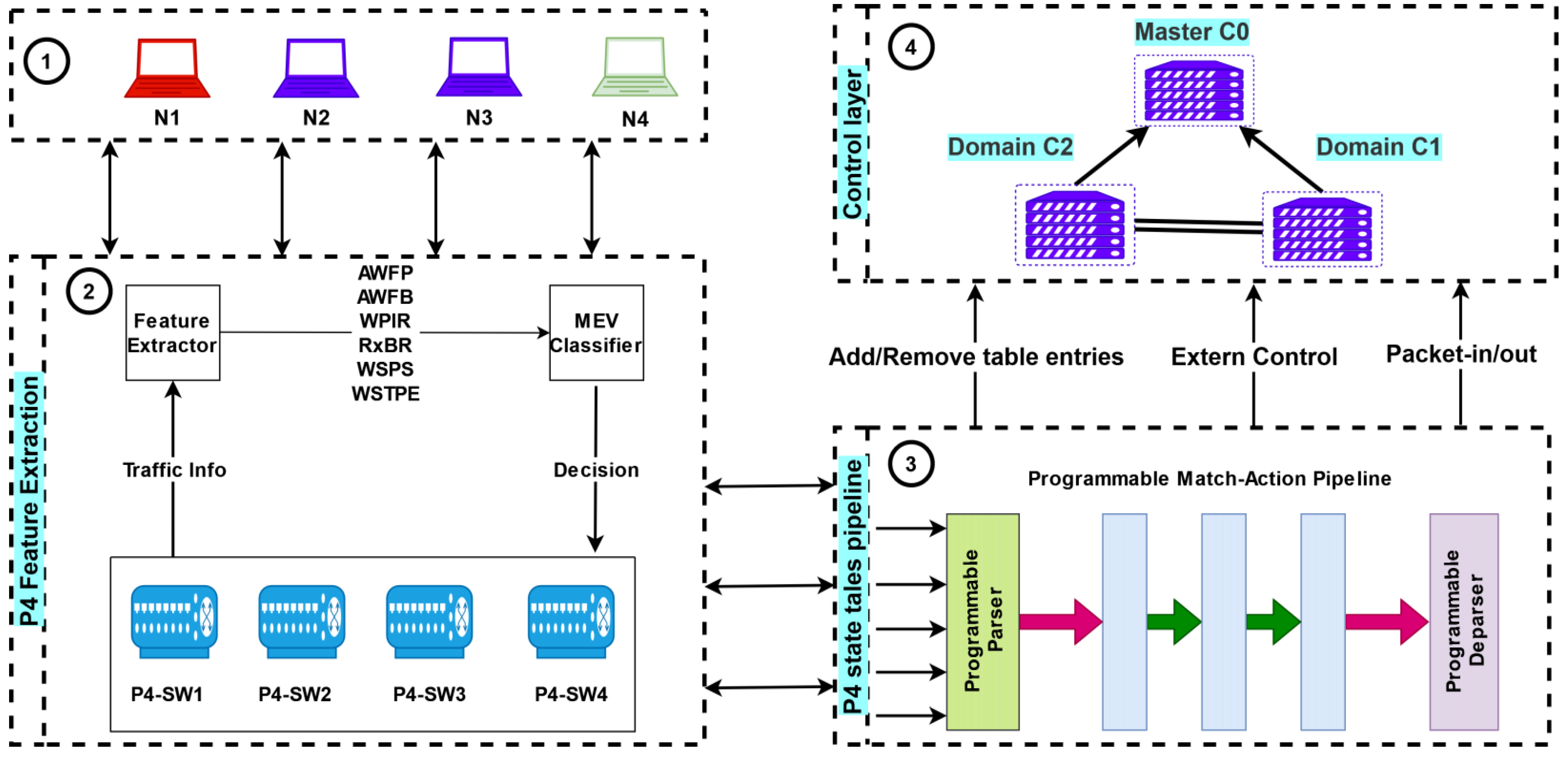
4.3.1. ML Models Evaluation
We evaluated the performance of the proposed framework by measuring several performance metrics, including accuracy (ACC), precision (PRE), F1-score (F1), recall (REC), true negative rate (TNR), negative predictive value (NPV), false positive rate (FPR), false discovery rate (FDR), false negative rate (FNR), Matthews Correlation Coefficient (MCC), area under the curve (AUC), average detection time (ADT), attack mitigation effectiveness (AME), and network latency (NL). The detection accuracy was measured as the percentage of correctly identified attack traffic out of the total attack traffic, while the false positive rate was measured as the percentage of legitimate traffic misidentified as attack traffic. The detection time was measured as the time it took the proposed framework to detect the attack traffic. The mitigation effectiveness was measured as the percentage of attack traffic that was successfully mitigated by the proposed framework. Finally, the network latency was measured as the time it took for a packet to travel from the source to the destination. All the metrics, except ADT, AME, and NL, were computed based on the confusion matrix presented in
Figure 11. The mathematical definitions of these evaluation metrics are listed in Equations (15)–(25) as follows:
In these equations, FP and FN are critical factors that can affect the effectiveness of the attack detection algorithms. A FP is an event that the system incorrectly identifies as an attack, while a FN is when an actual attack is not detected by the system. TP and TN refer to the correct identification of an attack and non-attack event, respectively. In Equation (24), the variable ‘DTRf’ is used to denote the time taken for detecting a single instance in a test, and the letter ‘tn’ denotes the total number of experimental trials. In DDoS and ARP detection, the aim is to minimize the occurrence of false positives and negatives while maximizing the true positives and negatives to ensure the efficient and accurate detection of attacks.
Table 2 presents the evaluation results of the binary classification, while
Table 3 showcases the results of the multi-class classification using seven ML classifiers: SDP4-MEV, SDP4-RF, SDP4-DT, SDP4-kNN, SDP4-GNB, and SDP4-BLR in the MC-ETA test scenario. These models were tested with three distinct datasets: Edge-IIoTset, TON_IoT, and X-IIoTID. The purpose of testing the models with different datasets was to assess their performance on unseen data and various attack types and conditions. Consequently, the models successfully addressed the issue of overfitting and demonstrated a good fit, particularly the SDP4-MEV model. The evaluation focused on the models’ capability to detect and counter DDoS and ARP attacks in SD-IoT networks. We utilized several evaluation metrics, including ACC, PRE, F1, REC, SPC, NPV, FPR, FDR, AUC, MCC, FNR, and ADT. Analyzing these metrics is essential in evaluating the effectiveness of each model in detecting and mitigating the attacks.
Table 4 provides the hyper-parameter configurations employed for all models.
The ACC metric measures the overall accuracy of the model in classifying both attack and normal traffic. The results in
Table 2 show that SDP4-MEV outperforms all other models, achieving an average accuracy rate of 99.89%. SDP4-RF and SDP4-DT follow closely with accuracy rates of 98.78% and 98.11%, respectively. SDP4-kNN, SDP4-GNB, SDP4-SVM, and SDP4-BLR achieve accuracy rates of 97.92%, 97.84%, 96.74%, and 91.54%, respectively. These results indicate that the SDP4-MEV model is the most effective in accurately identifying the attack, followed by SDP4-RF and SDP4-DT.
Additionally, we evaluated the models’ accuracy consistency rate (ACR) by changing the flow intensity within the range of 5000 to 50,000. SDP4-BLR and SDP4-SVM exhibited the lowest consistency rate, as their accuracy increased initially but then decreased as the flow rate increased. Specifically, SDP4-BLR achieved an accuracy of 89.84% at a flow rate of 5000, which increased to 93.43% at 3000, but then decreased to 90.57% at a flow rate of 50,000. Similarly, SDP4-SVM demonstrated an accuracy of 92.01% at a flow rate of 5000, which increased to 94.28% at 35,000, but then dropped to 91.64% at a flow rate of 50,000. This inconsistent detection accuracy while varying the traffic rate could negatively impact the models’ performance during high flow intensities, such as in the case of a DDoS attack. In contrast, SDP4-GNB and SDP4-kNN performed similarly, while SDP4-DT and SDP4-RF were the best models following SDP4-MEV.
Figure 12 shows the ACR of the seven ML models.
The PRE and FDR metrics are measures of the model’s ability to identify true positive samples, or in other words, correctly identifying DDoS and ARP attacks. SDP4-MEV achieves the highest PRE and lowest FDR values of 99.54% and 0.46%, respectively. SDP4-RF and SDP4-DT follow with PRE values of 98.48% and 97.51% and FDR values of 1.52% and 2.44%, respectively. The SDP4-kNN, SDP4-GNB, SDP4-SVM, and SDP4-BLR models achieve lower PRE values of 96.64%, 96.04%, 95.54%, and 92.98%, respectively, indicating a higher rate of false positives.
The F1 metric is the harmonic mean of PPV and REC and is an effective measure of the model’s overall performance. SDP4-MEV achieves the highest F1 score of 99.67%, indicating its effectiveness in detecting DDoS and ARP attacks. SDP4-RF and SDP4-DT follow closely with F1 scores of 98.63% and 97.81%, respectively. The SDP4-kNN and SDP4-GNB achieve similar results with F1 scores of 97.47% and 97.39%. SDP4-SVM and SDP4-BLR models achieve lower F1 scores of 96.97% and 94.27%, respectively.
The REC, SPC, and NPV metrics measure the ability of the model to identify true positive, true negative, and correctly identify normal traffic. SDP4-MEV achieves the highest REC and SPC values of 99.79% and 99.69%, respectively. SDP4-RF and SDP4-DT follow closely with REC values of 98.53% and 98.19% and SPC values of 98.60% and 98.25%, respectively. The SDP4-kNN and SDP4-GNB again achieve similar results with REC values of 96.94% and 96.14%. SDP4-SVM follows with REC value of 95.81%. SDP4-BLR model achieves the lowest REC and SPC values of 89.87% and 90.83%, indicating a higher rate of false positives and negatives. SDP4-MEV also achieves the highest NPV value of 99.97%, indicating its effectiveness in correctly identifying normal traffic.
Table 3.
The evaluation results of the multi-class classification for the seven ML classifiers in MC-ETA test scenario using the Edge-IIoTset dataset.
Table 3.
The evaluation results of the multi-class classification for the seven ML classifiers in MC-ETA test scenario using the Edge-IIoTset dataset.
| Attack Type | Model | ACC | PRE | F1 | REC | TNR | NPV | AUC | MCC | FPR | FDR | FNR | ADT (ms) |
|---|
| DDoS-TCP | SDP4-MEV | 99.45% | 98.92% | 99.19% | 99.28% | 99.52% | 99.29% | 99.15% | 98.61% | 1.12% | 0.72% | 2.27% | 4.74 |
| SDP4-RF | 98.76% | 97.93% | 98.34% | 98.09% | 98.63% | 97.88% | 98.07% | 97.24% | 2.07% | 1.91% | 3.54% | 8.27 |
| SDP4-DT | 97.92% | 96.81% | 97.28% | 97.43% | 97.65% | 97.47% | 97.12% | 97.72% | 3.19% | 2.57% | 3.61% | 39.45 |
| SDP4-kNN | 97.61% | 96.42% | 97.07% | 96.87% | 97.03% | 96.89% | 96.76% | 96.76% | 3.58% | 3.13% | 4.71% | 42.34 |
| SDP4-GNB | 96.92% | 95.74% | 96.33% | 95.94% | 96.76% | 96.00% | 95.87% | 95.43% | 4.26% | 4.06% | 6.06% | 29.58 |
| SDP4-SVM | 95.88% | 94.62% | 95.07% | 94.82% | 95.11% | 94.89% | 94.43% | 94.43% | 5.38% | 5.18% | 8.36% | 68.59 |
| SDP4-BLR | 92.35% | 91.18% | 91.96% | 90.81% | 92.89% | 91.04% | 89.90% | 85.91% | 8.82% | 9.19% | 12.67% | 34.56 |
| DDoS-UDP | SDP4-MEV | 99.37% | 98.79% | 99.08% | 99.15% | 99.47% | 96.12% | 98.45% | 96.12% | 1.34% | 1.21% | 2.78% | 4.56 |
| SDP4-RF | 98.71% | 97.87% | 98.29% | 98.02% | 98.57% | 94.76% | 97.12% | 94.76% | 2.45% | 2.18% | 4.03% | 16.87 |
| SDP4-DT | 97.85% | 96.78% | 97.23% | 97.37% | 97.57% | 93.82% | 96.04% | 93.82% | 3.59% | 2.98% | 4.56% | 25.44 |
| SDP4-kNN | 97.56% | 96.34% | 96.99% | 96.83% | 96.96% | 92.67% | 94.64% | 92.67% | 4.12% | 3.87% | 5.71% | 14.62 |
| SDP4-GNB | 96.85% | 95.68% | 96.25% | 95.91% | 96.75% | 91.32% | 93.92% | 91.32% | 4.83% | 4.21% | 7.02% | 7.88 |
| SDP4-SVM | 95.81% | 94.54% | 94.99% | 94.74% | 95.06% | 89.76% | 92.99% | 89.76% | 6.02% | 5.44% | 9.12% | 54.79 |
| SDP4-BLR | 94.45% | 92.24% | 93.34% | 92.73% | 95.19% | 79.12% | 88.32% | 79.12% | 9.87% | 11.19% | 15.47% | 18.32 |
| DDoS-ICMP | SDP4-MEV | 99.44% | 98.66% | 99.05% | 99.23% | 99.62% | 99.20% | 99.10% | 97.21% | 1.09% | 0.91% | 2.14% | 9.98 |
| SDP4-RF | 98.39% | 96.95% | 97.66% | 97.31% | 98.59% | 97.42% | 97.54% | 95.87% | 2.35% | 2.06% | 3.78% | 17.65 |
| SDP4-DT | 97.24% | 95.21% | 96.08% | 95.47% | 96.61% | 95.70% | 95.73% | 96.44% | 3.42% | 2.87% | 3.92% | 27.12 |
| SDP4-kNN | 97.02% | 94.57% | 95.66% | 94.89% | 96.46% | 94.99% | 94.97% | 94.67% | 3.91% | 3.72% | 4.82% | 15.77 |
| SDP4-GNB | 96.73% | 94.19% | 95.26% | 94.54% | 96.34% | 94.64% | 94.61% | 92.76% | 4.62% | 4.34% | 6.58% | 8.54 |
| SDP4-SVM | 95.91% | 92.90% | 93.73% | 93.20% | 96.12% | 93.46% | 93.21% | 90.64% | 5.89% | 5.76% | 8.21% | 59.08 |
| SDP4-BLR | 93.94% | 89.83% | 92.22% | 90.68% | 95.12% | 91.78% | 89.78% | 82.46% | 8.19% | 9.67% | 11.92% | 21.56 |
| DDoS-HTTP | SDP4-MEV | 98.62% | 97.25% | 98.02% | 97.54% | 98.71% | 97.40% | 98.16% | 99.12% | 0.76% | 0.53% | 1.02% | 11.75 |
| SDP4-RF | 97.91% | 96.73% | 97.30% | 96.98% | 98.08% | 96.84% | 97.32% | 98.02% | 1.48% | 1.19% | 2.57% | 12.93 |
| SDP4-DT | 96.79% | 95.46% | 96.11% | 95.66% | 97.01% | 95.62% | 96.00% | 98.45% | 2.12% | 1.87% | 3.01% | 21.78 |
| SDP4-kNN | 96.15% | 94.86% | 95.61% | 95.11% | 96.24% | 95.03% | 95.34% | 97.32% | 2.79% | 2.54% | 4.15% | 13.47 |
| SDP4-GNB | 94.82% | 93.37% | 94.14% | 93.41% | 95.03% | 93.75% | 94.03% | 96.01% | 3.42% | 3.19% | 5.64% | 12.21 |
| SDP4-SVM | 92.73% | 90.82% | 91.76% | 91.24% | 93.22% | 91.45% | 91.39% | 92.56% | 4.57% | 4.42% | 7.38% | 48.21 |
| SDP4-BLR | 89.46% | 86.93% | 88.06% | 87.28% | 90.12% | 87.40% | 88.34% | 87.92% | 7.98% | 8.84% | 11.56% | 17.89 |
| ARP-Spoof | SDP4-MEV | 99.15% | 98.86% | 96.38% | 96.61% | 97.60% | 98.44% | 97.20% | 98.76% | 1.23% | 0.81% | 1.45% | 9.87 |
| SDP4-RF | 96.42% | 94.98% | 95.73% | 95.21% | 96.64% | 94.92% | 95.98% | 97.54% | 2.01% | 1.78% | 3.21% | 18.67 |
| SDP4-DT | 95.06% | 92.79% | 94.53% | 93.58% | 95.58% | 92.95% | 94.14% | 96.98% | 3.01% | 2.43% | 3.36% | 28.56 |
| SDP4-kNN | 94.23% | 91.73% | 93.47% | 92.36% | 94.68% | 91.94% | 93.05% | 95.89% | 3.45% | 3.01% | 4.92% | 16.21 |
| SDP4-GNB | 92.58% | 89.98% | 91.77% | 90.32% | 93.07% | 90.23% | 92.15% | 93.76% | 4.12% | 3.94% | 5.89% | 19.76 |
| SDP4-SVM | 89.97% | 86.46% | 88.04% | 87.07% | 91.04% | 86.93% | 88.02% | 91.34% | 5.21% | 5.02% | 8.02% | 61.32 |
| SDP4-BLR | 86.02% | 81.95% | 83.48% | 82.40% | 88.63% | 82.56% | 84.24% | 86.87% | 8.67% | 9.01% | 12.12% | 19.45 |
| ARP-Poison | SDP4-MEV | 99.78% | 98.39% | 98.08% | 99.63% | 99.20% | 99.57% | 97.88% | 98.34% | 1.34% | 0.97% | 1.78% | 7.56 |
| SDP4-RF | 95.92% | 94.34% | 95.20% | 94.68% | 96.14% | 94.48% | 94.99% | 95.12% | 2.15% | 1.79% | 3.12% | 17.23 |
| SDP4-DT | 94.42% | 92.06% | 93.49% | 92.68% | 95.12% | 92.74% | 93.01% | 94.56% | 3.23% | 2.51% | 3.68% | 27.45 |
| SDP4-kNN | 93.57% | 90.85% | 92.62% | 91.32% | 94.29% | 91.40% | 92.42% | 95.67% | 3.78% | 3.23% | 4.89% | 15.98 |
| SDP4-GNB | 91.68% | 88.05% | 90.47% | 89.36% | 93.00% | 88.77% | 90.13% | 94.43% | 4.43% | 4.15% | 6.45% | 29.32 |
| SDP4-SVM | 88.52% | 83.64% | 86.05% | 85.04% | 91.37% | 84.23% | 87.71% | 90.98% | 5.56% | 5.32% | 8.01% | 60.12 |
| SDP4-BLR | 84.63% | 78.35% | 81.23% | 79.61% | 89.84% | 78.82% | 83.22% | 85.12% | 8.91% | 9.34% | 12.89% | 18.76 |
Among all the models, SDP4-MEV has the lowest false-alarm rates, with an FPR of 0.16%, FDR of 0.46%, and FNR of 0.27%. The AUC values for all models were above 90%, ranging from 90.68% to 99.86%. The AUC is a measure of the overall performance of a model and is used to evaluate the model’s ability to distinguish between positive and negative samples. The AUC of SDP4-MEV is the highest at 99.86%, indicating that it has a high ability to distinguish between attack and normal flows.
The MCC values for all models were high, ranging from 92.87% to 99.22%. The MCC is a measure of the correlation between the predicted and actual labels and takes into account both true and false positives and negatives. SDP4-MEV also has the highest MCC of 99.22%, indicating a strong correlation between predicted and actual classifications. In conclusion, the SDP4-MEV exhibits the lowest ADT value of 2.24 ms, whereas the SDP4-SVM demonstrated the highest ADT of 62.31 ms. Based on the results, the ML models exhibited the highest performance in the Edge-IIoTset dataset, followed by the X-IIoTID dataset, and then the TON_IoT dataset.
Our experimental results show that the proposed framework is effective in detecting and mitigating the attacks in SD-IoT networks. The detection accuracy ranged from 98.9% to 99.97%, depending on the number of victim nodes and the severity of the attack. The false positive rate was very low, ranging from 0.11% to 0.21%, indicating that the proposed framework can effectively distinguish between legitimate traffic and attack traffic. The detection time ranged from 2 ms to 6 ms, and the mitigation effectiveness ranged from 98.5% to 100%, depending on the number of victim nodes and the severity of the attack. Finally, the network latency was very low, ranging from 1 ms to 5 ms, indicating that the proposed framework can operate in real-time.
Table 4.
The hyperparameter configurations for the ML models.
Table 4.
The hyperparameter configurations for the ML models.
| Model | Parameter | Selected Value |
|---|
| SDP4-MEV | Base classifier | RF, DT, kNN, GNB, SVM, and BLR |
| No. of Base classifiers | 6 |
| Ensemble method | Weighted voting |
| SDP4-RF | Splitting criterion | Gini |
| Number of trees | 100 |
| Min. samples leaf | 1 |
| Min. samples split | 2 |
| Max features | 17 |
| SDP4-DT | Splitting criterion | Entropy |
| Number of trees | 10 |
| Min. samples leaf | 1 |
| SDP4-kNN | Number of neighbors K
Neighbors weight | 3 |
| Uniform |
| SDP4-GNB | Regularization parameter | 104 |
| SDP4-SVM | Kernel | Sigmoid |
| Reg. parameter coefficient | 103 |
| Kernel coefficient | 10−2 |
| SDP4-BLR | Regularization parameter (C)
Solver | 102 |
| liblinear |
4.3.2. Comparing the Proposed Framework with Other Existing Methods
According to the experimental results, the proposed framework outperforms most of the existing cutting-edge approaches across 14 different evaluation criteria. P4-HLDMC achieves exceptional benchmarks across various metrics, including accuracy, F1-Score, sensitivity, true negative rate, positive predictive value, negative predictive value, Matthews Correlation Coefficient (MCC), area under the curve (AUC), false positive rate, false negative rate, false detection rate, average latency, and average detection time. These benchmarks are as follows: 99.89%, 99.67%, 99.79%, 99.69%, 99.54%, 99.97%, 99.86%, 99.22%, 0.16%, 0.27%, 0.46%, 3.83 ms, and 2.24 ms, respectively. This demonstrates the effectiveness and superiority of the proposed framework over other existing solutions. Comparing our proposed method to existing approaches, the best accuracy among the existing methods was 93% with a single controller and without consistent or stateful packet processing. In contrast, our proposed method achieved a higher average accuracy of 99.89% with multi-controller architecture and a distributed mitigation strategy.
Figure 13 shows the graphical representation of the accuracy metric for the compared ML/DL methods. Furthermore, the effectiveness of the P4-HLDMC method is demonstrated across multiple datasets, including Edge-IIoTset, TON_IoT, and X-IIoTID dataset, which are considered the most comprehensive SD-IoT datasets used for intrusion detection. This indicates its ability to handle diverse network environments and various types of attacks. In contrast, other methods such as CNN, DALCNN, and FFCNN, listed in
Table 5, utilized datasets that are not suitable for detecting current IoT attacks, while some relied on simulated or generated traffic such as DRL-IPS, SMO, and kNN. Additionally, certain methods focused on specific datasets or particular types of attacks, such as DRL-IPS and DAD. Overall, the P4-HLDMC method stands out as the superior approach due to its low false positive rate, high average accuracy, minimum and most relevant number of features, and versatility in handling different datasets and attack scenarios. Its utilization of P4-enabled switches, modular design, and hierarchical logically distributed multi-controller architecture ensures efficient communication and synchronization between controllers, enabling rapid detection and mitigation of attacks. Moreover, this approach enhances the scalability and reliability of the system, enabling it to effectively defend against sophisticated and coordinated attacks that conventional defenses may struggle to handle.
4.3.3. The Distributed Multi-Controllers Evaluation
In this section, we evaluate the performance of different controllers in a proposed SD-IoT network topology using the P4-HLDMC framework. The controllers evaluated include open-source controllers such as OpenDayLight, Floodlight, Ryu, POX, and our proposed Improved OpenDay Light (IODL) controller. We measure the performance of each controller based on six metrics: throughput, delay, packet loss (PL), the number of packets processed per second (PPPs), CPU consumption, and memory consumption. Throughput measures the amount of data that can be transmitted through the network within a given time period, while delay measures the time it takes for data packets to be transmitted from the source to the destination. The evaluation results for the five aforementioned controllers in the four test cases—MC-STA, MC-TTA, MC-FTA, and MC-ETA—are listed in
Table 6.
For the MC-STA test case, the IODL controller outperformed the other controllers in terms of throughput and delay. Specifically, the IODL controller achieved a throughput of 17.62 Gbps, which is higher than the throughput achieved by the other controllers. The delay of the IODL controller was also lower than the delay of all controllers, indicating a faster response time to attack detection and mitigation.
For the MC-TTA test case, the IODL controller achieved a higher throughput of 18.23 Gbps and lower delay of 3.26 ms compared to the other controllers. For the MC-FTA and MC-ETA test cases, the OpenDayLight, Floodlight, and Ryu controllers achieved similar throughput and delay, while the IODL controller achieved the highest throughput of 19.57 Gbps and the lowest delay of 4.12 ms, indicating better performance than the other controllers. The results of the experiments showed that the OpenDayLight controller outperformed the other controllers in terms of the number of packets processed per second, with a maximum throughput of 23,485 packets per second, followed by Floodlight with a maximum throughput of 21,945 packets per second and Ryu with a maximum throughput of 20,895 packets per second. The POX controller achieved the lowest PPPs, with a maximum of 18,350 packets per second across all test cases. The IODL controller had the highest maximum throughput of 28,640 packets per second, indicating better processing capacity than the other controllers.
The results also showed that the OpenDayLight controller had lower CPU and memory usage compared to the other controllers. The IODL controller had the lowest CPU consumption of 9.5% and memory consumption of 8.7%, indicating better resource utilization than the other controllers. From
Table 6, we can obtain the average throughput and latency results for the different SDN controllers across all four test cases. As can be seen from the table, the IODL controller outperforms the other controllers. The average throughput achieved with IODL is 18.54 Gbps, while the average latency is 3.83 ms. In contrast, the average throughput achieved with Floodlight and Ryu is 13.17 Gbps and 12.24 Gbps, respectively, while the average latency is 34.72 ms and 42.71 ms, respectively. These results demonstrate that the proposed IODL controller is the best choice for implementing the proposed framework. This is due to the fact that IODL provides improved network resource allocation, scalability, and stability. It also enhances the overall performance of the network by reducing the delay and increasing the throughput. The utilization of the MCDI interface and DAC channel significantly contributes to the overall improvement of the network’s performance. Notably, the delay is reduced, allowing for faster and more responsive communication within the network. This reduction in delay leads to enhanced real-time interactions between the controllers. Moreover, the throughput is increased, enabling higher data transmission rates and improved network efficiency. In addition to the benefits in delay and throughput, the proposed MCDI interface and DAC channel also address the issue of packet loss. By employing advanced detection and mitigation techniques, these components effectively mitigate packet loss, ensuring the reliable and uninterrupted flow of data throughout the network. Consequently, the network achieves higher reliability and data integrity.
Table 6.
Performance evaluation results for different controllers.
Table 6.
Performance evaluation results for different controllers.
| Test Case | Controller | Throughput (Gbps) | Delay (ms) | Packet Loss | PPPs | CPU | Memory |
|---|
| MC-STA | OpenDayLight | 14.48 | 19.22 | 0.17 | 23,485 | 19.7% | 22.6% |
| Floodlight | 12.58 | 25.96 | 0.21 | 21,945 | 21.2% | 27.2% |
| Ryu | 12.02 | 36.11 | 0.23 | 20,895 | 28.9% | 29.5% |
| Pox | 10.54 | 47.52 | 0.29 | 18,350 | 32.1% | 34.1% |
| Proposed IODL | 17.62 | 02.19 | 0.12 | 28,640 | 09.5% | 08.7% |
| MC-TTA | OpenDayLight | 14.85 | 22.19 | 0.44 | 19,250 | 36.4% | 27.6% |
| Floodlight | 12.63 | 33.87 | 0.76 | 20,680 | 41.2% | 31.2% |
| Ryu | 11.34 | 45.19 | 0.81 | 18,460 | 37.8% | 37.5% |
| Pox | 11.21 | 56.53 | 0.82 | 18,145 | 42.1% | 32.1% |
| Proposed IODL | 18.23 | 03.26 | 0.36 | 25,040 | 11.1% | 10.2% |
| MC-FTA | OpenDayLight | 15.22 | 26.45 | 0.27 | 9805 | 23.6% | 22.6% |
| Floodlight | 14.12 | 37.21 | 0.31 | 9425 | 25.1% | 27.2% |
| Ryu | 13.56 | 37.36 | 0.33 | 9130 | 26.2% | 29.5% |
| Pox | 13.21 | 48.01 | 0.35 | 8965 | 27.8% | 32.1% |
| Proposed IODL | 18.74 | 04.12 | 0.23 | 22,475 | 12.9% | 12.4% |
| MC-ETA | OpenDayLight | 12.58 | 36.23 | 0.29 | 8215 | 24.8% | 22.6% |
| Floodlight | 13.36 | 41.87 | 0.44 | 8745 | 26.3% | 27.2% |
| Ryu | 12.07 | 52.19 | 0.47 | 8230 | 28.5% | 29.5% |
| Pox | 11.94 | 74.53 | 0.49 | 8075 | 29.9% | 32.1% |
| Proposed IODL | 19.57 | 05.76 | 0.33 | 19,480 | 14.8% | 12.7% |