Self-C2AD: Enhancing CA Auditing in IoT with Self-Enforcement Based on an SM2 Signature Algorithm
Abstract
:1. Introduction
1.1. Our Contributions
- We propose Dap-SM2, a short efficient double-authentication preventing signature based on an SM2 signature algorithm.
- We provide a security analysis of Dap-SM2, which satisfies the property of existential unforgeability and key-extractability. We also implement it on a PC and provide a detailed efficiency evaluation, whose performance demonstrates that our scheme has good potential for usability.
- We transform Dap-SM2 into Self-C2AD, a real-time CA auditing mechanism with self-enforcement designed to cope with the complex IoT context. Inherited from the Dap-SM2, our Self-C2AD can provide certificate unforgeability and timely key-extractability.
1.2. Organization of This Paper
2. Related Work
3. Preliminaries
3.1. Notations
3.2. Elliptic Curves Cryptography
3.3. Review of Chinese SM2 Signature Algorithm
- Setup: takes as input and outputs the set of public parameters .
- (1)
- Choose a finite field and generate the elliptic curve equation satisfies .
- (2)
- Randomly choose as a generator, where the order of it is q.
- (3)
- Output the public parameters set .
- KeyGen: takes as input and outputs the key pair .
- (1)
- Randomly choose as the private key.
- (2)
- Compute as the public key.
- (3)
- Output the key pair .
- Sign: takes as input and out put the signature σ.
- (1)
- Compute hash value , where .
- (2)
- Set and compute .
- (3)
- Randomly choose , and compute .
- (4)
- Compute . If , then return to Sign.3).
- (5)
- Compute . If , then return to Sign.3).
- (6)
- Output the signature as .
- Verify: takes the signature, as input and output which represents “accept” or “invalid”.
- (1)
- Compute hash value , where .
- (2)
- If , then output 0 and end the algorithm.
- (3)
- Set and compute .
- (4)
- Compute . If , output 0 and end the algorithm.
- (5)
- Compute .
- (6)
- Compute . If , output 1. Otherwise, output 0.
4. Scheme Framework and Security Definitions
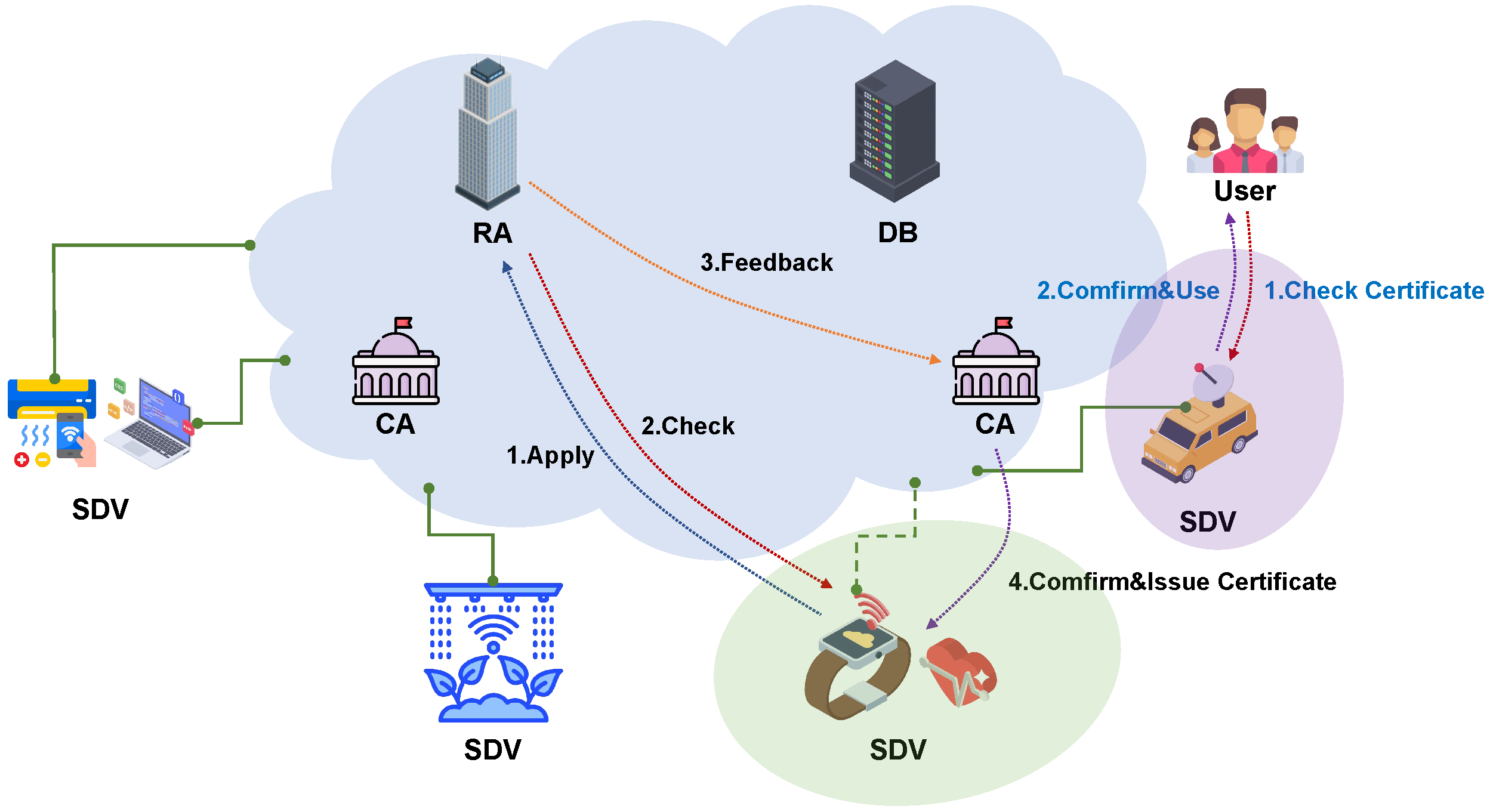
4.1. System Model
- CA: The CA functions as the authentication centre which is mainly responsible for checking the identity validity of the SDV and issues certificates for it if its identity is valid to access the Internet.
- SDV: The SDV plays the role of an interface to IoT users. It provides specific functions for users in different scenarios, meeting a variety of needs. There are usually plenty of SDVs in the IoT.
- User: The user is the one who enjoys the services of the IoT. At the same time, the user verifies the certificates of SDVs before using devices.
4.2. Double-Authentication Preventing Signature
- : is a algorithm, which takes the security parameter as input, and outputs a set of public parameters .
- : is a algorithm, which takes the public parameters and the addresses set as input and outputs key pairs for signers.
- : takes input of the public parameters , the signer’s private key , and a message M (where , represents the address and content respectively). It returns a signature as output.
- : takes input of the public parameters , the received signature from signer , the signed message M and the public key . The algorithm outputs 1 if the is valid, otherwise it outputs 0.
- : takes input of the public key , two messages and , and the corresponding signatures and . The algorithm outputs if the and have the same address, otherwise it returns “⊥”.
4.3. Security Definitions
- Sign Oracle (): returns Sign, with input of . If , then it returns ⊥.
- Comp: this requires that producing such that Comp if there is truly no compromising pair of signed messages.
5. Dap-SM2 and Self-C2AD
5.1. The Double-Authentication Preventing Signature from SM2
- Setup(): takes as input and outputs the set of public parameters .
- (1)
- Choose a finite field and generate the elliptic curve equation satisfies .
- (2)
- Randomly choose a generator with order q.
- (3)
- Choose hash functions .
- (4)
- Choose pseudorandom function and the X-axis extraction function .
- (5)
- Output public parameters set .
- KeyGen(): takes and as input and performs the following steps.
- (1)
- Initialize functions , .
- (2)
- Randomly choose as SOT private key.
- (3)
- For all addresses :
- (a)
- .
- (b)
- Compute .
- (c)
- Compute .
- (d)
- For address as , compute partial public key , random element .
- (e)
- Let .
- (f)
- Let
- (4)
- Let , .
- (5)
- Return key pair .
- Sign(): here, the signed message .
- (1)
- Phase the message .
- (2)
- Compute .
- (3)
- Compute the point .
- (4)
- Compute , and .
- (5)
- Output the signature s.
- Verify(): verifier performs the following steps.
- (1)
- Phase the message .
- (2)
- Compute .
- (3)
- Compute , and .
- (4)
- Check if , output 1 represents “valid” or 0 represents “invalid”.
- Extract(): anyone can perform the following steps.
- (1)
- Phase the messages , .
- (2)
- Compute .
- (3)
- If , then continue. Otherwise, output “⊥”.
- (4)
- Compute , , and .
- (5)
- Compute .
- (6)
- Compute .
- (7)
- Compute .
- (8)
- Return the private key of malicious user .
5.2. Correctness Analysis
5.3. Security Analysis
5.4. The Self-C2AD Mechanism
- Initialization: this algorithm is performed by the control centre. It performs Dap-SM2.setup to generate the system parameters .
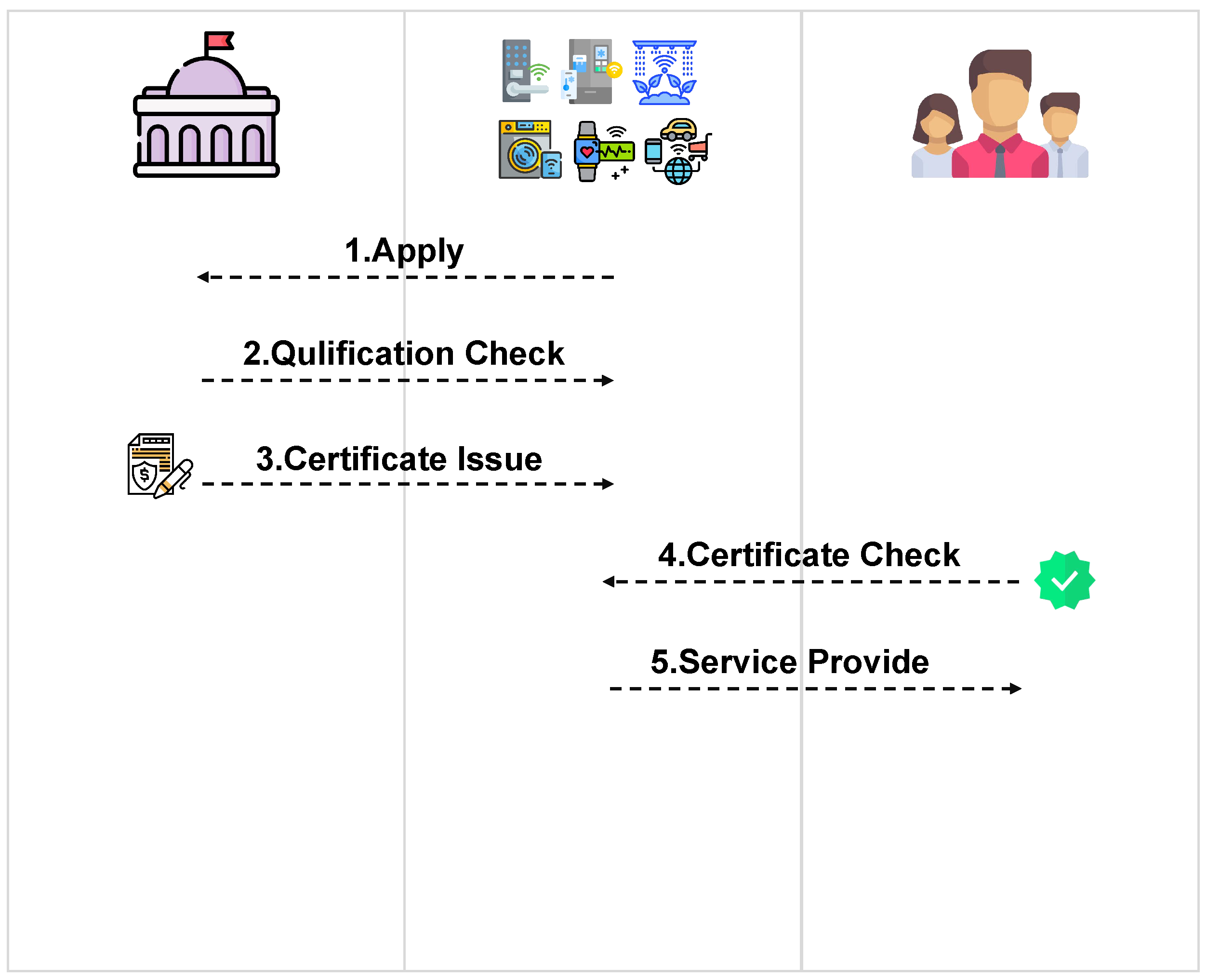
- KeyGen: this algorithm is performed by the CA. When a CA receives a set of applications from SDVs, it gathers DIDs into a set and runs DAP-SM2. KeyGen to generate key pairs .
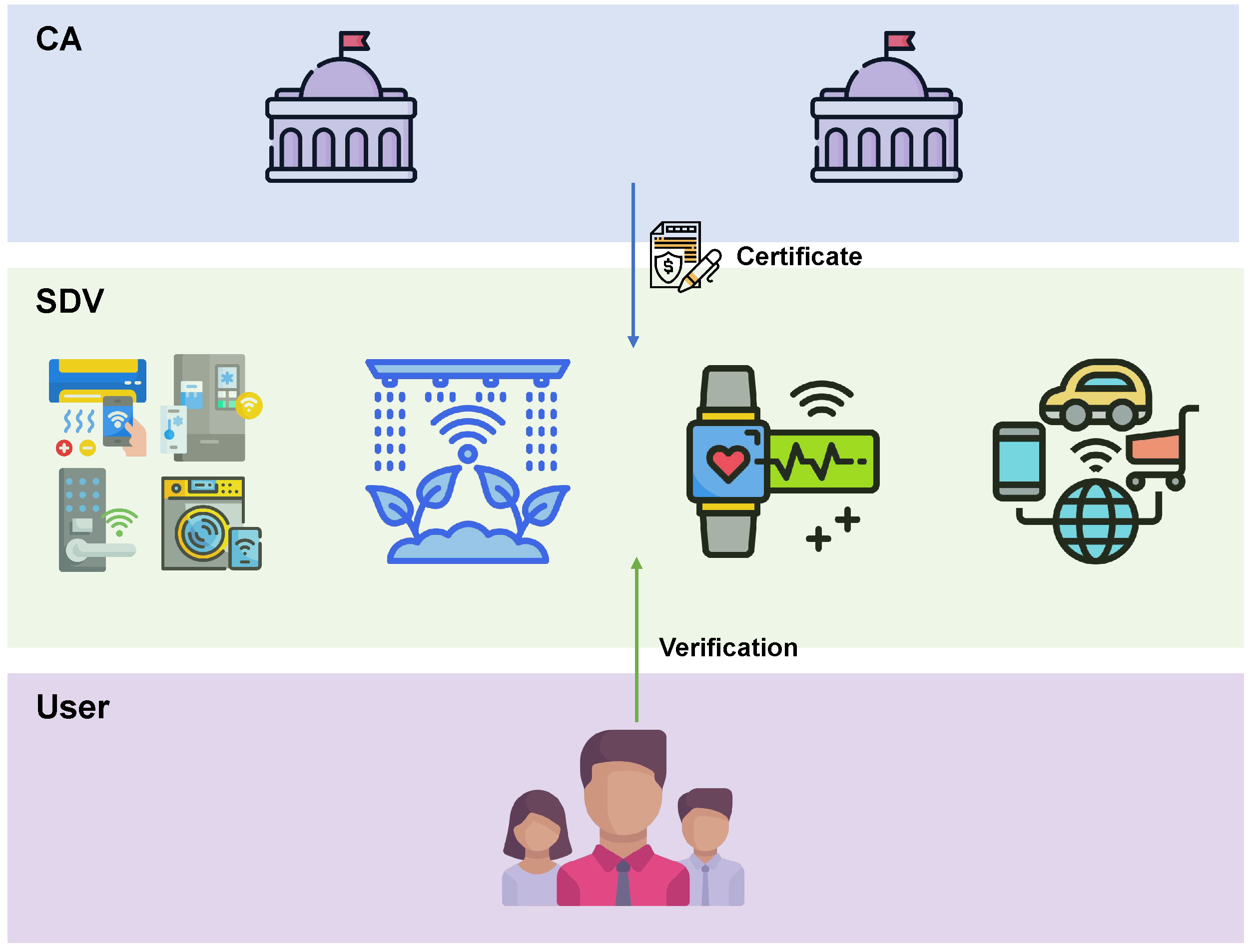
- Certificate Issue: this algorithm is performed by the CA. For an SDV, CA checks its validity and issues a certificate by generating a signature on the message by the corresponding partial private key if possible.
- Certificate Check: this algorithm is performed by the IoT user. Assuming that there is a user Alice who wants to use a SDV, she first runs Dap-SM2.Verify to check the validity of the SDV certificate. If the outcome is 1, she can use it safely, otherwise, she would give it up.
- Self-Auditing: this algorithm is performed automatically by the IoT system. It detects in a timely way whether there is a malicious CA issuing two s for the same DID by performing DAP-SM2.Extract, where . The private key of the malicious CA will be extracted in public.
- Certificate Unforgeability: this means that there is no way that any adversary can successfully forge a certificate for an SDV without obtaining the corresponding partial private key.
- Timely Key-Extractability: this means that there is no way that any malicious CA can prevent being punished if it produces a compromising pair of s; moreover, this process is performed in a timely way.
6. Efficiency Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wu, Y.; Shen, C.; Chen, S.; Wu, C.; Li, S.; Wei, R. Intelligent Orchestrating of IoT Microservices Based on Reinforcement Learning. Chin. J. Electron. 2022, 31, 930–937. [Google Scholar] [CrossRef]
- Chen, Q.; Ye, A.; Zhang, Q.; Huang, C. A new edge perturbation mechanism for privacy-preserving data collection in iot. Chin. J. Electron. 2023, 32, 603–612. [Google Scholar] [CrossRef]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Guizani, M. Blockchain-Assisted Secure Device Authentication for Cross-Domain Industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar] [CrossRef]
- Obiri, I.A.; Yang, J.; Xia, Q.; Gao, J. A Sovereign PKI for IoT Devices Based on the Blockchain Technology. In Proceedings of the 2021 18th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Chengdu, China, 17–19 December 2021; pp. 110–115. [Google Scholar]
- Laurie, B.; Langley, A.; Kasper, E. RFC 6962: Certificate Transparency. Available online: https://www.rfc-editor.org/rfc/rfc6962.html (accessed on 15 June 2013).
- Bonneau, J. EthIKS: Using ethereum to audit a CONIKS key transparency log. In Proceedings of the International Conference on Financial Cryptography and Data Security, Church, Barbados, 22–25 February 2016. [Google Scholar]
- Poettering, B.; Stebila, D. Double-authentication-preventing signatures. Int. J. Inf. Secur. 2017, 16, 1–22. [Google Scholar] [CrossRef]
- Lu, S.; Lu, J.; An, K.; Wang, X.; He, Q. Edge computing on IoT for machine signal processing and fault diagnosis: A review. IEEE Internet Things J. 2023, 10, 1093–11116. [Google Scholar] [CrossRef]
- State Cryptography Administration, China. Public Key Cryptographic Algorithm SM2 Based on Elliptic Curves—Part 2: Digital Signature Algorithm. Available online: http://www.sca.gov.cn/sca/xwdt/2010-12/17/content_1002386.shtml (accessed on 17 December 2010).
- Wu, M.; Li, M.; Shao, X.; Liu, Y.; Gao, M.; Yang, X.; Bian, Z. Research on certificate management and key management of C-V2X security authentication technology in intelligent network vehicle. In Proceedings of the International Conference on Cryptography, Network Security, and Communication Technology (CNSCT 2023), SPIE, Sanya, China, 6–8 January 2023; Volume 12641, pp. 115–123. [Google Scholar]
- Wu, K.; Cheng, R.; Cui, W.; Li, W. A lightweight SM2-based security authentication scheme for smart grids. Alex. Eng. J. 2021, 60, 435–446. [Google Scholar] [CrossRef]
- Wang, Z.; Dong, H.; Chi, Y.; Zhang, J.; Yang, T.; Liu, Q. Research and Implementation of Hybrid Encryption System Based on SM2 and SM4 Algorithm. In Proceedings of the 9th International Conference on Computer Engineering and Networks, Shanghai, China, 25–27 February 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 695–702. [Google Scholar]
- Zou, J.; He, D.; Bi, S.; Wu, L.; Liu, Z.; Peng, C. A certificateless Multi-recerver Encryption scheme based on SM2 signature algorithm. High-Confid. Comput. 2023, 3, 100103. [Google Scholar] [CrossRef]
- ISO/IEC. ISO/IEC 14888-3/Amd1; ISO: Berlin, Germany, 2016. [Google Scholar]
- Poettering, B. Shorter double-authentication preventing signatures for small address spaces. In Proceedings of the Progress in Cryptology—AFRICACRYPT 2018: 10th International Conference on Cryptology in Africa, Marrakesh, Morocco, 7–9 May 2018; Proceedings 10. Springer: Berlin/Heidelberg, Germany, 2018; pp. 344–361. [Google Scholar]
- Lin, X.; Sun, X.; Ho, P.H.; Shen, X. GSIS: A Secure and Privacy-Preserving Protocol for Vehicular Communications. IEEE Trans. Veh. Technol. 2007, 56, 3442–3456. [Google Scholar]
- Han, L.; Cao, S.; Yang, X.; Zhang, Z. Privacy Protection of VANET Based on Traceable Ring Signature on Ideal Lattice. IEEE Access 2020, 8, 206581–206591. [Google Scholar] [CrossRef]
- Boneh, D.; Kim, S.; Nikolaenko, V. Lattice-Based DAPS and Generalizations: Self-enforcement in Signature Schemes. In Proceedings of the Applied Cryptography and Network Security: 15th International Conference, ACNS 2017, Kanazawa, Japan, 10–12 July 2017; Proceedings 15. Springer: Berlin/Heidelberg, Germany, 2017; pp. 457–477. [Google Scholar]
- Mundhe, P.; Yadav, V.K.; Verma, S.; Venkatesan, S. Efficient Lattice-Based Ring Signature for Message Authentication in VANETs. IEEE Syst. J. 2020, 14, 5463–5474. [Google Scholar] [CrossRef]
- Merkle, R.C. A digital signature based on a conventional encryption function. In Proceedings of the Advances in Cryptology—CRYPTO’87, Barbara, CA, USA, 16–20 August 1987; Proceedings 7. Springer: Berlin/Heidelberg, Germany, 1988; pp. 369–378. [Google Scholar]
- Krawczyk, H.; Rabin, T. Chameleon Hashing and Signatures. U.S. Patent US6108783A, 22 August 2000. [Google Scholar]
- Ruffing, T.; Kate, A.; Schröder, D. Liar, liar, coins on fire! Penalizing equivocation by loss of bitcoins. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, Denver, CO, USA, 12–16 October 2015; pp. 219–230. [Google Scholar]
- Bellare, M.; Poettering, B.; Stebila, D. Deterring certificate subversion: Efficient double-authentication-preventing signatures. In Proceedings of the Public-Key Cryptography–PKC 2017: 20th IACR International Conference on Practice and Theory in Public-Key Cryptography, Amsterdam, The Netherlands, 28–31 March 2017; Proceedings, Part II 20. Springer: Berlin/Heidelberg, Germany, 2017; pp. 121–151. [Google Scholar]
- Bellare, M.; Poettering, B.; Stebila, D. From identification to signatures, tightly: A framework and generic transforms. In Proceedings of the Advances in Cryptology–ASIACRYPT 2016: 22nd International Conference on the Theory and Application of Cryptology and Information Security, Hanoi, Vietnam, 4–8 December 2016; Proceedings, Part II 22. Springer: Berlin/Heidelberg, Germany, 2016; pp. 435–464. [Google Scholar]
- Derler, D.; Ramacher, S.; Slamanig, D. Short double-and n-times-authentication-preventing signatures from ECDSA and more. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS&P), IEEE, London, UK, 24–26 April 2018; pp. 273–287. [Google Scholar]
- Liu, J.; Yu, Y.; Jia, J.; Wang, S.; Fan, P.; Wang, H.; Zhang, H. Lattice-based double-authentication-preventing ring signature for security and privacy in vehicular Ad-Hoc networks. Tsinghua Sci. Technol. 2019, 24, 575–584. [Google Scholar] [CrossRef]
- Derler, D.; Ramacher, S.; Slamanig, D. Generic double-authentication preventing signatures and a post-quantum instantiation. In Proceedings of the Provable Security: 12th International Conference, ProvSec 2018, Jeju, Republic of Korea, 25–28 October 2018; Proceedings 12. Springer: Berlin/Heidelberg, Germany, 2018; pp. 258–276. [Google Scholar]
- Hoffman, P.; Schlyter, J. The DNS-Based Authentication of Named Entities (DANE) Transport Layer Security (TLS) Protocol: TLSA; Technical Report; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2012. [Google Scholar]
- Evans, C.; Palmer, C.; Sleevi, R. Public Key Pinning Extension for HTTP; Technical Report; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2015. [Google Scholar]
- Safdar, G.; McLoone, M. Randomly Shifted Certification Authority Authentication Protocol for MANETs. In Proceedings of the 2007 16th IST Mobile and Wireless Communications Summit, Budapest, Hungary, 1–5 July 2007; pp. 1–5. [Google Scholar]
- Hossain, M.; Hasan, R.; Zawoad, S. Probe-IoT: A public digital ledger based forensic investigation framework for IoT. In Proceedings of the IEEE INFOCOM 2018—IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Honolulu, HI, USA, 15–19 April 2018. [Google Scholar]
- Koblitz, N. Elliptic curve cryptosystems. Math. Comput. 1987, 48, 203–209. [Google Scholar] [CrossRef]
- Catalano, D.; Fuchsbauer, G.; Soleimanian, A. Double-authentication-preventing signatures in the standard model. J. Comput. Secur. 2022, 30, 3–38. [Google Scholar] [CrossRef]
- Johnson, D.; Menezes, A.; Vanstone, S. The elliptic curve digital signature algorithm (ECDSA). Int. J. Inf. Secur. 2001, 1, 36–63. [Google Scholar] [CrossRef]
| Notations | Definitions |
|---|---|
| E | The elliptic curve equation |
| The finite field contained q elements | |
| An elliptic curve group of order q | |
| G | A generator of group |
| The k times of the point P on E | |
| The concatenation of two strings a and b | |
| The security parameter | |
| The identity of the user | |
| The length of the user’s identity | |
| The function of generating user’s public key | |
| The function of generating user’s partial public key used to extract private key | |
| The pseudorandom function takes k as evaluation key | |
| The X-axis extraction function takes point R as input and returns its X-axis | |
| SOT | The abbreviation of the One-time signatures |
| ROM | The abbreviation of the Random Oracle model |
| The set of addresses | |
| The abbreviation of probabilistic polynomial time | |
| The negligible function | |
| The event A can deduce to event B |
| Scheme | Sub-Algorithm | ||
|---|---|---|---|
| KeyGen (ms) | Sign (ms) | Verify (ms) | |
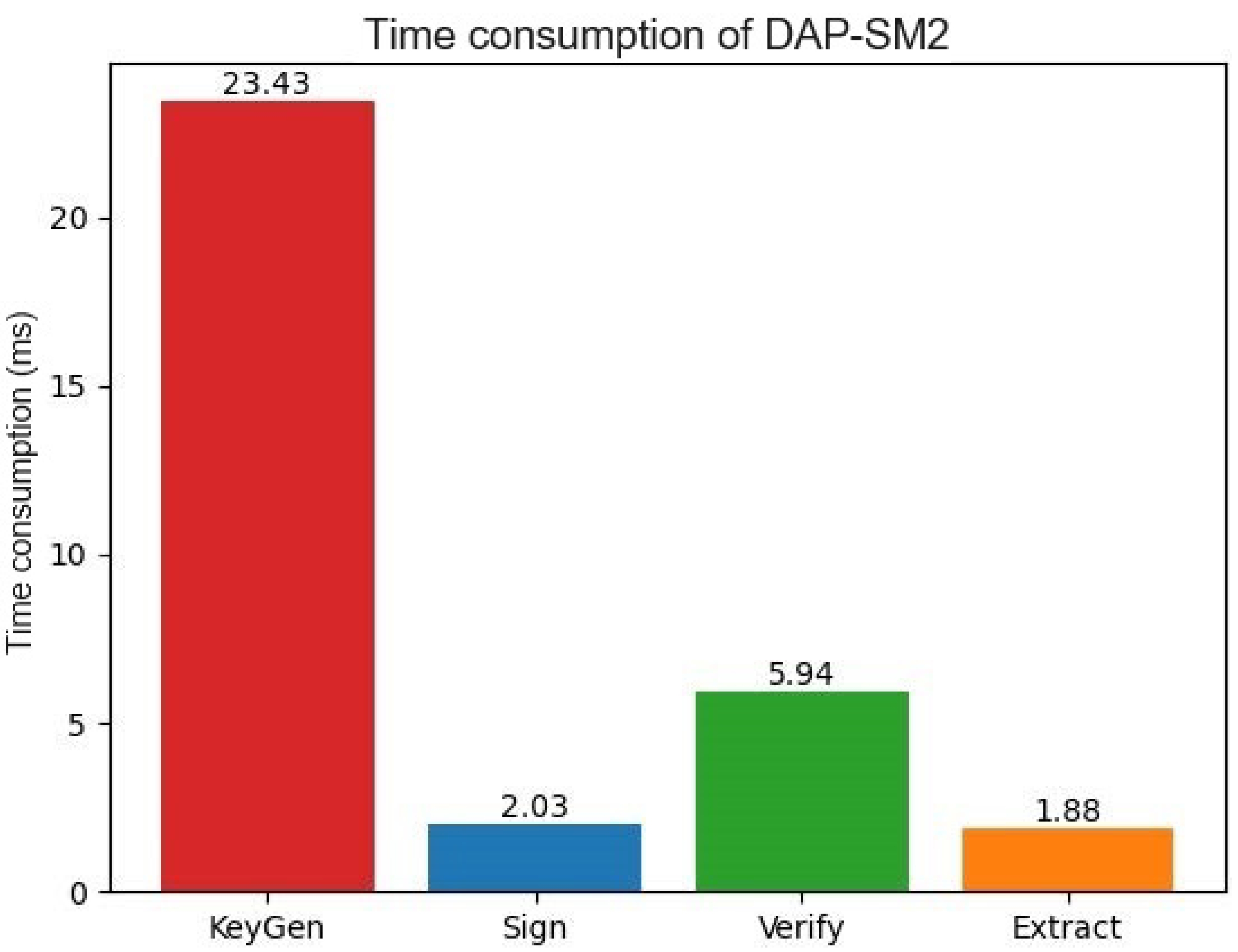
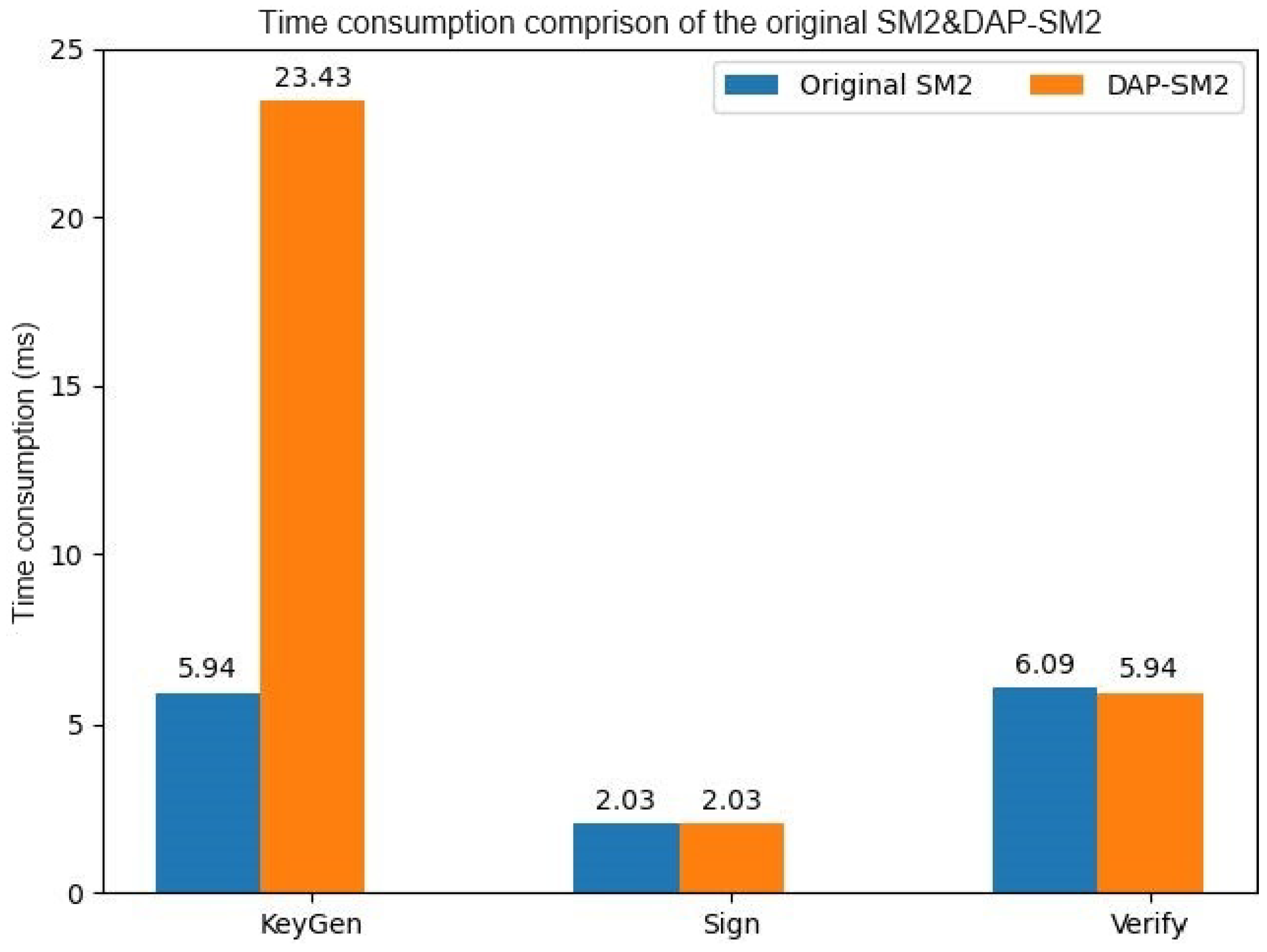
| Original SM2 | 5.94 | 2.03 | 6.09 |
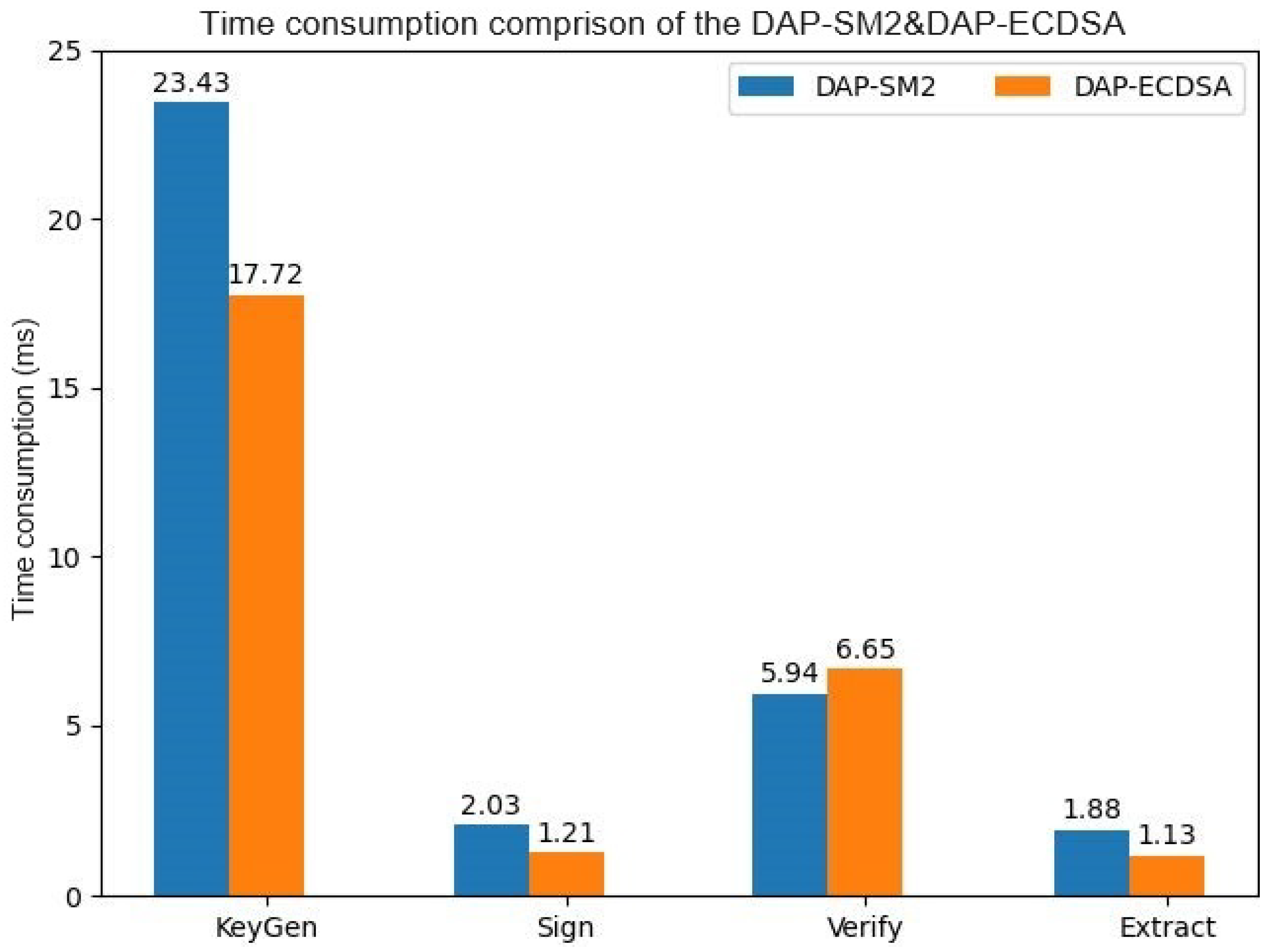
| Dap-SM2 | 23.43 | 2.03 | 5.94 |
| Size | Time Consuming (ms) |
|---|---|
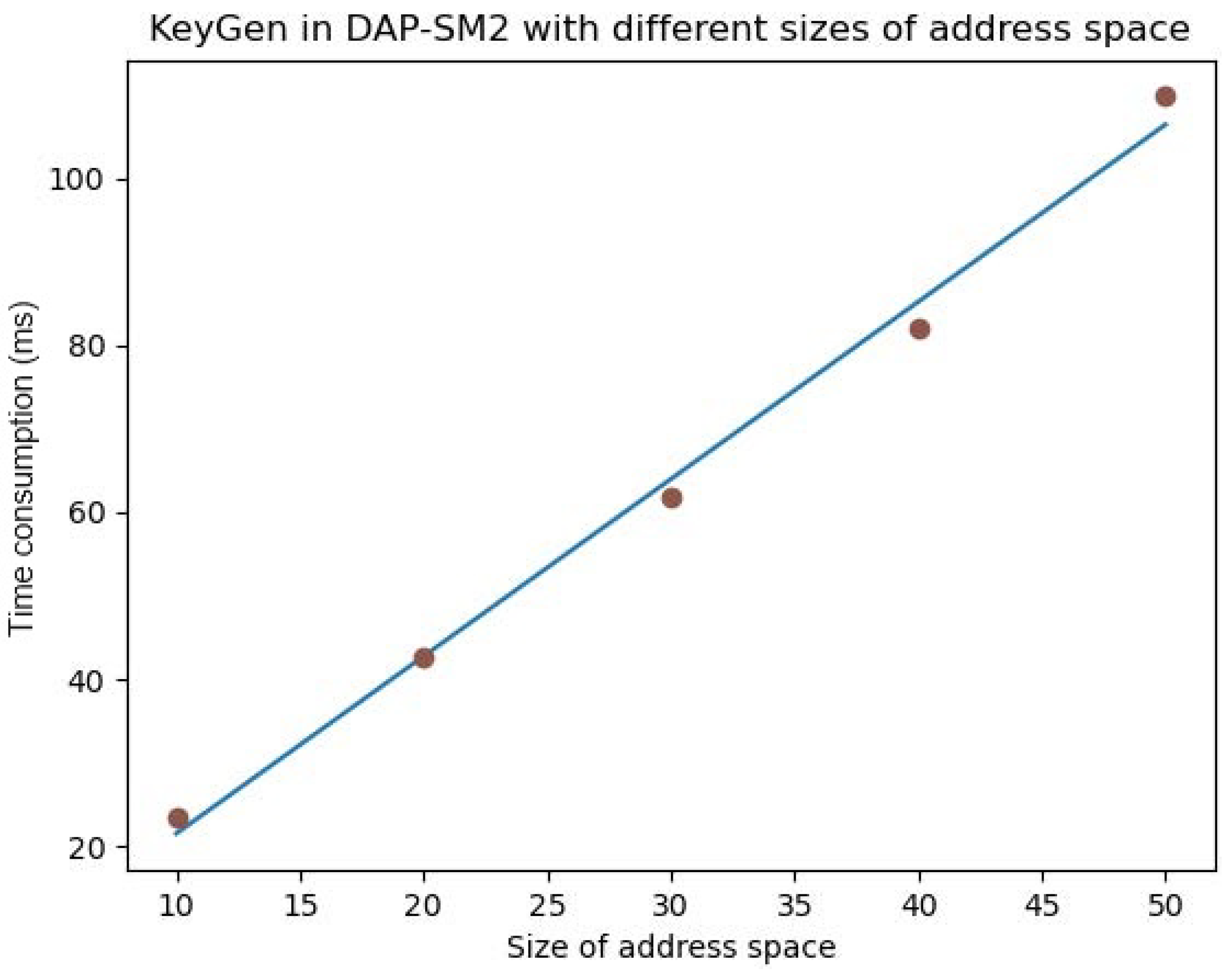
| 10 | 23.43 |
| 20 | 42.66 |
| 30 | 61.87 |
| 40 | 82.18 |
| 50 | 109.81 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, J.; Liu, Y.; Li, S.; Zhang, G.; Gao, X.; Gong, P. Self-C2AD: Enhancing CA Auditing in IoT with Self-Enforcement Based on an SM2 Signature Algorithm. Mathematics 2023, 11, 3887. https://doi.org/10.3390/math11183887
Li J, Liu Y, Li S, Zhang G, Gao X, Gong P. Self-C2AD: Enhancing CA Auditing in IoT with Self-Enforcement Based on an SM2 Signature Algorithm. Mathematics. 2023; 11(18):3887. https://doi.org/10.3390/math11183887
Chicago/Turabian StyleLi, Jianfeng, Yu Liu, Siqi Li, Guangwei Zhang, Xiang Gao, and Peng Gong. 2023. "Self-C2AD: Enhancing CA Auditing in IoT with Self-Enforcement Based on an SM2 Signature Algorithm" Mathematics 11, no. 18: 3887. https://doi.org/10.3390/math11183887





