Efficient and Privacy-Preserving Categorization for Encrypted EMR
Abstract
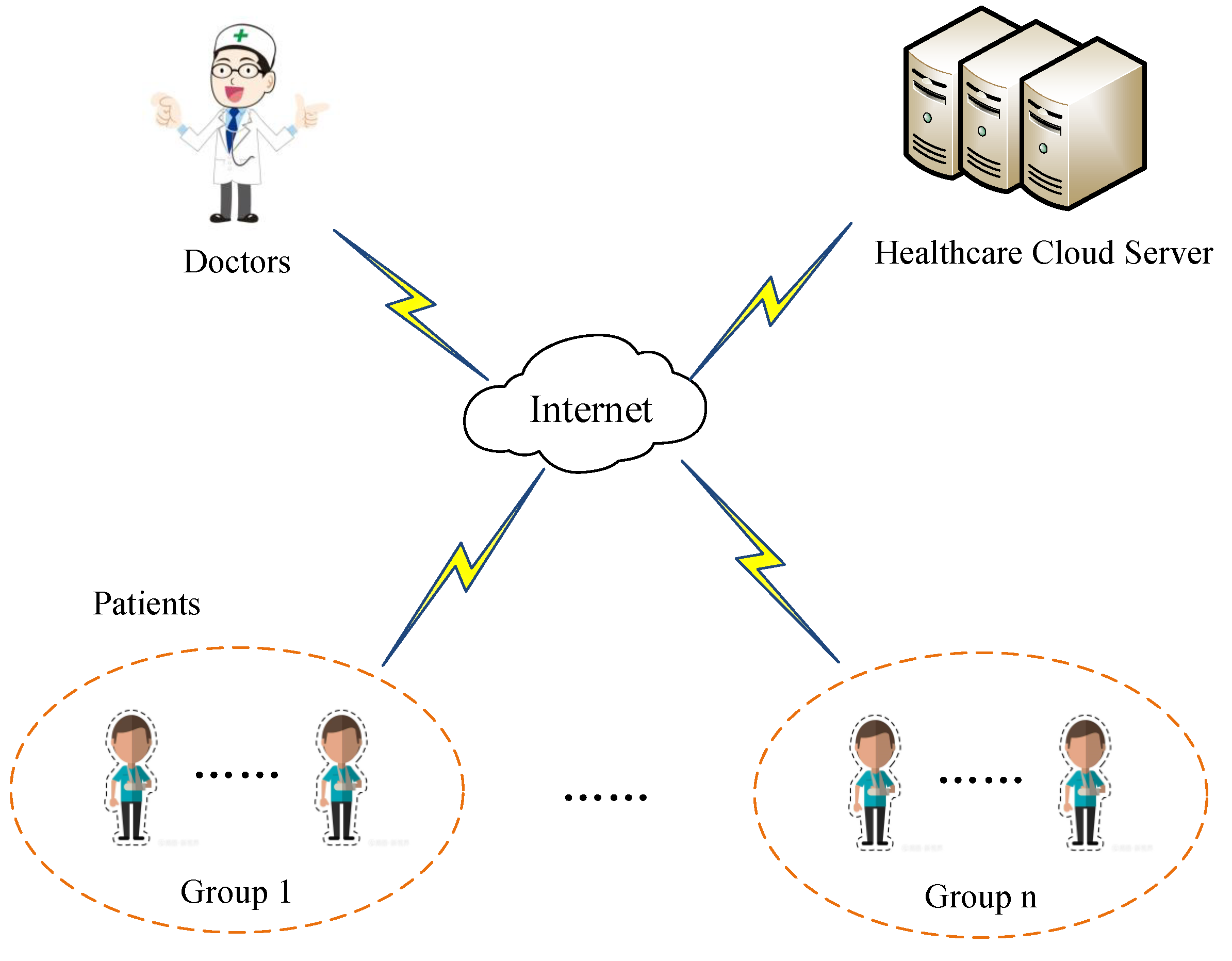
:1. Introduction
1.1. Our Contributions
- We improved the group-oriented PKEET proposed in [14], to be resistant to guessing attack even by the group administrator: in this way, patient privacy was enhanced.
- We applied our group-oriented PKEET to the healthcare system, so that the EMR were managed efficiently and securely.
1.2. Related Work
1.3. Organization
2. Preliminaries
2.1. Mathematical Background
- bilinear: for any g ∈ G and , ∈ Z, (g,g) = (g,g);
- non-degenerate: (g,g) ≠ 1;
- computable: there is an effective algorithm for computing (g,g) for any g ∈ G.
2.2. Building Block
- Group Administrator (GA) is responsible for generating the group secret key, , and the group public key, , of the system; then, it keeps the , and sends the to the patient.
- Sender: the patient encrypts the electronic medical record with the group public key (gpk) and with the patient’s own secret key (sk), to generate the ciphertext C, then stores it in the cloud server.
- Cloud Server (CS): with the authorization, the cloud server is in charge of performing the equality test, and returns the result to the doctor.
- Receiver: upon receiving the result from the cloud server, the receiver can classify the based on the result.The receiver can use their own private key to decrypt the ciphertext at the same time.
3. System Definition and Security Model
3.1. The Syntax of PKEET
- (): the algorithm inputs a security parameter, , and outputs a public/secret key pair ();
- : the algorithm inputs message M, the receiver’s public key, , and outputs a ciphertext, C;
- : the algorithm inputs a ciphertext, C, the receiver’s secret key, , and outputs a message, M;
- : the algorithm inputs two ciphertexts, , and outputs 1, if and are encrypted from the same plaintexts, and 0 otherwise.
3.2. The Syntax of G-PKEET
- : the algorithm inputs a security parameter, , and outputs as a system parameter;
- : the algorithm inputs system parameter , and outputs (pk,sk) as a public/secret key pair;
- : the algorithm inputs system parameter , and outputs as a group secret key; it is run by GA;
- : the algorithm inputs a group secret key, , a public key, , and outputs as a group public key for group user ; it is run by GA;
- : the algorithm inputs a group public key, , and a secret key, , of the group user , a public key, , of the group user , and a message, m, where and represent the receiver and sender, respectively, and outputs C as a ciphertext;
- : the algorithm inputs a group public key, of the group user , a secret key, , of the group user , where and represent the receiver and sender, respectively, and outputs message M;
- : the algorithm inputs a group secret key, gsk, and outputs a group trapdoor gtd; it is run by GA;
- : the algorithm inputs two ciphertexts, , a group trapdoor, gtd, and outputs 1, if and are encrypted from the same plaintexts, and 0 otherwise.
3.3. Security Models
- Type-I Adversary: the attacker authorized by GA cannot retrieve a message from the challenge ciphertext;
- Type-II Adversary: the attacker unauthorized by GA cannot determine by which plaintext the challenge ciphertext is encrypted.
- 1.
- Setup: With a security parameter, , challenger runs the algorithm to generate public parameter pp; then, it runs the algorithm to generate n group users’ public/secret key pair () (); it runs the algorithm, to generate a group secret key, gsk; it runs the algorithm, to generate n group user’s group public key, (); and it runs the algorithm, to generate a group trapdoor, ; finally giving , all , , and to the adversary .
- 2.
- Phase 1: makes the following queries for polynomial times:
- query sends , and gets from the oracle;
- query sends (), and gets the encryption result of M from the oracle;
- query sends (), and gets the decryption result of from the oracle.
- 3.
- Challenge: The challenge randomly selects a message, M, runs , and sends the output to .
- 4.
- Phase 2: issues queries, as in Phase 1: the constraint is that () cannot appear in .
- 5.
- Guess: outputs a guess, : if , wins the game.
- 1.
- Setup: With a security parameter, , challenger runs the algorithm to generate public parameter PP; then, it runs the algorithm to generate n group users’ public/secret key pair, () (); it runs the algorithm to generate a group secret key, gsk; it runs the algorithm to generate n group user’s group public key, (); and it runs the algorithm to generate a group trapdoor, ; finally, it gives , all , , and to the adversary, .
- 2.
- Phase 1: makes the following queries for polynomial times:
- query sends , and gets from the oracle;
- query : sends (), and gets the encryption result of M from the oracle;
- query sends (), and gets the decryption result of from the oracle.
- 3.
- Challenge: randomly selects two messages, , and sends them to challenge ; then, randomly selects , runs , and sends to .
- 4.
- Phase 2: issues queries, as in Phase 1. The constraint is that () cannot appear in .
- 5.
- Guess: returns a guess, . If , wins the game.
4. Construction
- : this algorithm is performed by Key Generation Center (KGC). KGC inputs security parameter , and outputs public parameters . are four collision-resistant hash functions:
- -
- H: → G,
- -
- H:G → G,
- -
- H:G → ,
- -
- H:, where l and l represent the length of message and the length of Z.
- : this algorithm is performed by the patient, who randomly selects , and outputs a public/secret key pair,
- : this algorithm is performed by the GA (for example, the hospital director), who randomly selects s, s, and: (1) outputs a group secret key, gsk = (s, s); (2) sets the group trapdoor, gtd = s.
- : this algorithm is performed by GA, and outputs a group public key for group patients, U:
- : this algorithm is performed by patient i. To encrypt , say , patient i randomly chooses two random numbers, , and uses doctor j’s public key, , to set the ciphertext, C = (C,C,C,C,C), as follows:
- : this algorithm is performed by a doctor, and computes () ← , then decides if the following equation holds:if yes, then the doctor obtains the EHRs’ .In the decryption step, a verification operation is performed, to prevent attackers from decrypting the modified ciphertext to obtain the plaintext; data security is ensured.
- : this algorithm is performed by GA, and outputs a group gtd = to the cloud server, for the next testing step.
- : the algorithm is performed by tester (cloud server). Given ciphertexts, group trapdoor, the algorithm outputs 1 if the following equation holds:Note: We presented a detailed construction for the G-PKEET scheme as above, and compared it to Ling et al.’s scheme [14]. We made some improvements to the encryption part, by using a pair of generated private keys to encrypt the EHRs, so that only the server could test the ciphertext if it got the group trapdoor.
5. Security Analysis
- 1.
- , , , sk = (), pk = (), , gsk = (s, s), gpk = (g, g), gtd = s. H, H, H, and H are random oracles. H-query. The challenger prepares four hash tables, to record and respond to queries.query given a , the challenger randomly selects , computes , saves () into , and sends to .query given a , the challenger chooses a compatible random value, , and saves () into for .query given a , the challenger chooses a compatible value, , uniformly from the set that is returned, and saves () into for .query given a , the challenger chooses a compatible value, , uniformly from the set that is returned, and saves () into for .
- 2.
- state ← where the oracles are simulated as follows, and cannot appear in oracle:query input index i; the challenger sends () to ;query input two indexes, i, j, and a plaintext M; the challenger runs the algorithm, and returns = ;query input two indexes, i,j, and a ciphertext, ; the challenger runs the algorithm, and returns M = .
- 3.
- , , and computes:
- 4.
- The constraint is that () cannot appear in , and cannot appear inLet denote the event in Game 1.0. Thus, the advantage of is as follows:Game 1.1: In this game, the performance of the challenger is the same as in Game 1.0, except for the following:
- 1.
- query : the challenge selects , and returns a ciphertext, , to , then computesit executes a query on , with input M to return , a query on , with input to return , and a query on , with input to return ; then, it computesand, finally, it executes a query on with input to return ; then, it setsThe challenger saves (), (), (), () to , and returns toquery : the challenger executes a query on on input , and gets the answer ; it then computes , to get , and checks if the following equations hold:If either fails to be maintained, the challenger sends ⊥ to ; otherwise, it sends to .
- 2.
- , , , computesFinally, the challenger saves the tuple into tables for .Let denote the event in Game 1.1. Given the idealness of the random oracle, Game 1.1 is the same as Game 1.0, and we haveGame 1.2: In this game, the performance of the challenger is the same as in Game 1.1, except for the following:
- 1.
- query is the same as that in Game 1.1; in addition, if asks , denote this event by E;
- 2.
- query is the same as that in Game 1.1; in addition, if requests the decryption of () after receiving the challenge ciphertext , where , the challenger sends ⊥ to
- 3.
- , , , is defined as follows:Finally, the tuple is saved into tables for .Let S denote the event that in Game 1.2. The challenge ciphertext generated in Game 1.1 is identically distributed to that in Game 1.2, as is a random value in both Game 1.1 and Game 1.2; therefore, if event E does not happen, Game 1.2 is identical to Game 1.1, and we have
- 1.
- sets PP = (); it chooses two random values, , , and sets gsk = , , , and . Then, it chooses random value , and sets , and gtd = . are four random oracles. H-query. prepares four hash tables to record and respond to queries, where all the hash tables are initialized to empty:query : same as that in Game 1.1;query : same as that in Game 1.1;query : same as that in Game 1.1;query : same as that in Game 1.1, except that if asks , we denote this event by
- 2.
- state ← where the oracles are simulated as follows:: same as that in Game 1.1;: same as that in Game 1.1, except that if query , chooses random values, , and outputs a ciphertext, , defined asthen it executes a query on , with input M to return , a query on , with input to return , and a query on , with input to return ; then, it computesfinally, it executes a query on , with input to return , and setsThe challenger saves to table for , to table for , to table for , to table for , and returns to .query : same as that in Game 1.1. In addition to query , if asks the decryption of () after obtaining the challenger ciphertext , and , the challenger sends ⊥ to . For the tuple (), , after computing , verifies if ; otherwise, it returns ⊥; then, it inputs to get , and verifies if : if so, it returns M; if a compatible tuple does not exist, it returns ⊥.
- 3.
- , , , , defined as follows:finally, it saves the tuple () into table , where Indicates that the value is unknown.
- 4.
- . The constraints are that cannot appear in , and () cannot appear in .Indistinguishable simulation. Based on the setting of the simulation, the correctness and randomness of the simulation hold, given a ciphertext for a decryption query, if , is able to execute decryption simulation; if , we have the following scenarios:
- has been queried to before decryption query is asked: in this case, is uniquely determined after is queried to ; then, the decryption oracle is perfectly simulated;
- has never been queried to when the decryption query is asked: in this case, ⊥ is returned by the decryption oracle if the simulation fails; however, the idealness of the random oracle happens with probability .
- 1.
- , , , sk = (), pk = (), , gsk = (s, s), gpk = (g, g), gtd = s. H, H, H, and H are random oracles. H-query. The challenger prepares four hash tables, to record and respond to queries:query given a , the challenger randomly selects , computes , saves () into , and sends to ;query given a , the challenger chooses a compatible random value , and saves () into for ;query given a , the challenger chooses a compatible value uniformly from the set that is returned, and saves () into , for ;query given a , the challenger chooses a compatible value uniformly from the set that is returned, and saves () into , for ;
- 2.
- () ← , where the oracles are simulated as follows:query input two indexes, i, j, and a plaintext M; the challenger runs algorithm, and returns = ();query input two indexes, i, j, and a ciphertext, ; the challenger runs a algorithm, and returns M = ().
- 3.
- , , computes:
- 4.
- . The constraints are that cannot appear in , and () cannot appear in .Let denote the event in Game 2.0. Thus, the advantage of is as follows:Game 2.1: In this game, the performance of challenger is the same as in Game 2.0, except for the following:
- 1.
- query the challenger chooses two random values, , and returns a ciphertext, , then computesIt executes a query on with input M to return , a query on with input to return , and a query on with input to return ; then, it computesand, finally, executes a query on , with input to return , then sets:The challenger saves (), (), (), () to , and returns to
- 2.
- , , , computes:Finally, the tuple is saved into tables, , for .
- 3.
- . The constraints are that cannot appear in , and () cannot appear in .
- Let denote the event in Game 2.1. The idealness of the random oracle, Game 2.1, is the same as Game 1.0, and we have
- Game 2.2: in this game, the performance of the challenger is the same as in Game 2.1, except for the following:
- 1.
- query same as that in Game 2.1, except that if asks , we denote this event by .
- 2.
- same as that in Game 2.1, except that if asks the decryption of () after receiving the challenge ciphertext , where , the challenger sends ⊥ to .
- 3.
- , , , , defined as follows:Finally, the tuple is saved into tables .Let S denote the event that in Game 2.2. The challenge ciphertext generated in Game 2.1 is identically distributed to that in Game 2.2, as is a random value in both Game 2.1 and Game 2.2; therefore, if event E does not happen, Game 1.2 is equal to Game 2.1, and we haveGame 2.3: In this game, the performance of the challenger is the same as in Game 2.2, except for the following:
- 1.
- , , , , , defined as follows:Finally, the tuple , is saved into table , .Let denote the event in Game 2.3. Given the idealness of the random oracle, Game 2.3 is the same as Game 2.2, and we haveGame 2.4: In this game, the performance of the challenger is the same as in Game 2.3, except for the following:
- 1.
- query same as that in Game 2.3, except that if asks , we denote this event by ;
- 2.
- query same as that in Game 2.3, except that if asks the decryption of () after receiving the challenge ciphertext , where and , the challenger sends ⊥ to ;
- 3.
- , , , , , defined as follows:Finally, the tuple , is saved to table , .Let S denote the event that in Game 2.4. The challenge ciphertext generated in Game 2.3 is equally distributed to that in Game 2.4, as is a random value in both Game 2.3 and Game 2.4; therefore, if event E does not happen, Game 2.4 is the same as Game 2.3, and we have
- 1.
- sets PP = (); it chooses two random values , and sets , , ; it chooses a random value, , and sets , , , and gtd = ⊤. are four random oracles.H-query. prepares four hash tables to record and respond to queries, where all the hash tables are initialized to empty:query : same as that in Game 2.3;query : same as that in Game 2.3;query : same as that in Game 2.3;query : same as that in Game 2.3, except that asks , and we denote this event by .
- 2.
- state ← , where the oracles are simulated as follows, and cannot appear in :query : same as that in Game 2.3;query : same as that in Game 2.3;query : same as that in Game 2.3.
- 3.
- , , , , , defined as follows:Finally, the tuple is saved into table for , and the tuple into table for .
- 4.
- . The constraints are that cannot appear in , and () cannot appear in .
- has been queried to before decryption query is asked: in this case, is uniquely determined after is queried to ; then, the decryption oracle is perfectly simulated.
- has never been queried to when the decryption query is asked: in this case, ⊥ is returned by the decryption oracle if the simulation fails. The idealness of the random oracle happens with probability .
6. Comparison and Performance Evaluation
6.1. Comparison
6.2. Performance Evaluation
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yu, Y.; Li, Y.; Tian, J. Blockchain-based solutions to security and privacy issues in the Internet of Things. IEEE Wirel. Commun. 2019, 25, 12–18. [Google Scholar] [CrossRef]
- Amato, A.; Coronato, A. An IoT-aware architecture for smart healthcare coaching systems. In Proceedings of the 2017 IEEE 31st International Conference on Advanced Information Networking and Applications (AINA), Taipei, Taiwan, 27–29 March 2017; pp. 1027–1034. [Google Scholar]
- Demirkan, H. A smart healthcare systems framework. IT Prof. 2013, 15, 38–45. [Google Scholar] [CrossRef]
- Rao, Y.S. A secure and efficient ciphertext-policy attribute-based signcryption for personal health records sharing in cloud computing. Future Gener. Comput. Syst. 2017, 67, 133–151. [Google Scholar] [CrossRef]
- Au, M.H.; Yuen, T.H.; Liu, J.K. A general framework for secure sharing of personal health records in cloud system. J. Comput. Syst. Sci. 2017, 90, 46–62. [Google Scholar] [CrossRef]
- Bösch, C.; Hartel, P.; Jonker, W. A survey of provably secure searchable encryption. ACM Comput. Surv. (CSUR) 2014, 47, 1–51. [Google Scholar] [CrossRef]
- Xhafa, L.; Li, J.; Zhao, G.; Li, J.; Chen, X.; Wong, D. Designing cloud-based electronic health record system with attribute-based encryption. Multimed. Tools Appl. 2015, 74, 3441–3458. [Google Scholar] [CrossRef]
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: New York, NY, USA, 2004; pp. 506–522. [Google Scholar]
- Yau, W.C.; Heng, S.H.; Goi, B. Off-Line keyword guessing attacks on recent public key encryption with keyword search schemes. In International Conference on Autonomic and Trusted Computing; Springer: New York, NY, USA, 2008. [Google Scholar]
- Ma, S.; Huang, Q. A new framework of IND-CCA secure public key encryption with keyword search. Comput. J. 2020, 63, 1849–1858. [Google Scholar] [CrossRef]
- Khader, D. Public key encryption with keyword search based on K-resilient IBE. In Proceedings of the International Conference on Computational Science and Its Applications (ICCSA 2006), Glasgow, UK, 8–11 May 2006; pp. 298–308. [Google Scholar]
- Yang, G.M.; Tan, C.H.; Huang., Q.; Wong, D.S. Probabilistic public key encryption with equality test. In Proceedings of the Topics in Cryptology-CT-RSA 2010: The Cryptographers’ Track at the RSA Conference 2010, San Francisco, CA, USA, 1–5 March 2010; Springer: Berlin/Heidelberg, Germany; pp. 119–131. [Google Scholar]
- Tang, Q. Towards public key encryption scheme supporting equality test with fine-grained authorization. In Australasian Conference on Information Security and Privacy; Springer: New York, NY, USA, 2011; pp. 389–406. [Google Scholar]
- Ling, Y.H.; Ma, S.; Huang, Q.; Li, X.; Ling, Y.Z. Group public key encryption with equality test against offline message recovery attack. Inf. Sci. 2020, 510, 16–32. [Google Scholar] [CrossRef]
- Tang, Q. Public key encryption supporting plaintext equality test and user-specified authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef]
- Ma, S.; Zhang, M.; Huang, Q.; Yang, B. Public key encryption with delegated equality test in a multi-user setting. Comput. J. 2015, 58, 986–1002. [Google Scholar] [CrossRef] [Green Version]
- Huang, K.; Tso, R.; Chen, Y.C.; Rahman, S.; Alomgren, A.; Alamri, A. PKE-AET: Public Key Encryption with Authorized Equality Test. Comput. J. 2015, 58, 2686–2697. [Google Scholar] [CrossRef]
- Jae, H.S. Short Signatures from Diffie-Hellman, revisited: Sublinear Public Key, CMA security, and tighter reduction. Cryptol. ePrint Arch. 2014. Available online: https://eprint.iacr.org/2014/138 (accessed on 1 December 2022).
- Ma, S.; Huang, Q.; Zhang, M.; Yang, B. Efficient public key encryption with equality test supporting flexible authorization. IEEE Trans. Inf. Forensics Secur. 2014, 10, 458–470. [Google Scholar] [CrossRef]
- Lin, H.; Zhao, F.; Gao, F.; Susilo, W.; Shi, Y. Lightweight public key encryption with equality test supporting partial authorization in cloud storage. Comput. J. 2020, 64, 1226–1238. [Google Scholar] [CrossRef]




Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, Z.; Zeng, S.; Cheng, S.; Hao, F. Efficient and Privacy-Preserving Categorization for Encrypted EMR. Mathematics 2023, 11, 754. https://doi.org/10.3390/math11030754
Zhao Z, Zeng S, Cheng S, Hao F. Efficient and Privacy-Preserving Categorization for Encrypted EMR. Mathematics. 2023; 11(3):754. https://doi.org/10.3390/math11030754
Chicago/Turabian StyleZhao, Zhiliang, Shengke Zeng, Shuai Cheng, and Fei Hao. 2023. "Efficient and Privacy-Preserving Categorization for Encrypted EMR" Mathematics 11, no. 3: 754. https://doi.org/10.3390/math11030754
APA StyleZhao, Z., Zeng, S., Cheng, S., & Hao, F. (2023). Efficient and Privacy-Preserving Categorization for Encrypted EMR. Mathematics, 11(3), 754. https://doi.org/10.3390/math11030754






