The Data Privacy Protection Method for Hyperledger Fabric Based on Trustzone
Abstract
:1. Introduction
1.1. Related Works
1.2. Our Goal and Contribution
- Aiming at solving data confidentiality issues when applying Fabric blockchain on IoT devices, we propose a data-privacy protection method of Fabric blockchain based on Trustzone technology, using TEE to provide Fabric with encryption algorithm services to protect data privacy.
- According to the TEE standard specification, we store the key in the trusted execution environment by designing the directory file and key encryption file, which improves security of the key stored in the Fabric blockchain node.
- In order to reduce the impact of the trusted execution environment on the performance of data-encryption operations, we improve the data-copying stage, changing from data transfer to pointer transfer to optimize program performance.
2. Background
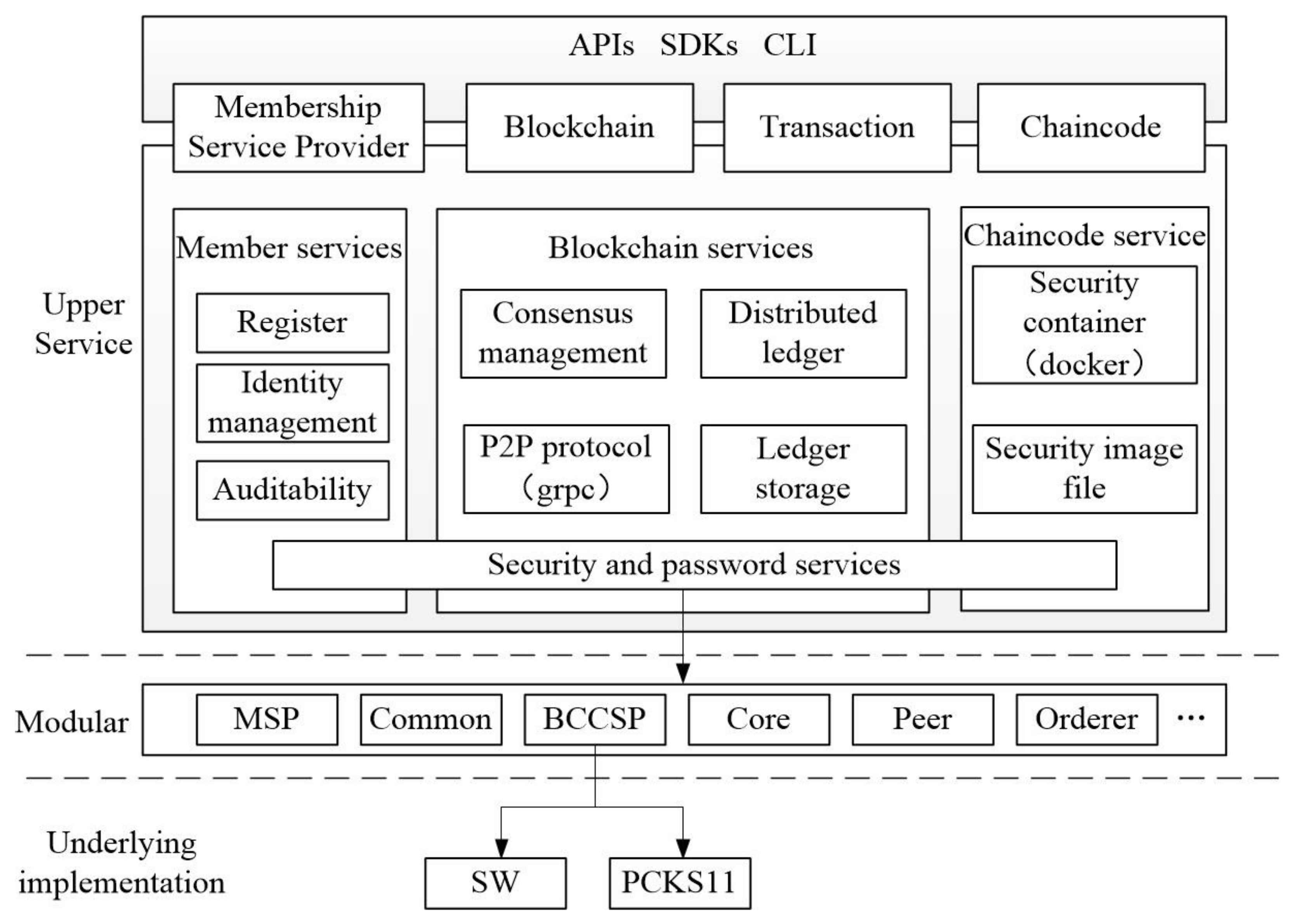
2.1. Hyperledger Fabric
2.2. Security and Cryptographic Services for Fabric Networks
2.3. Smart Contract
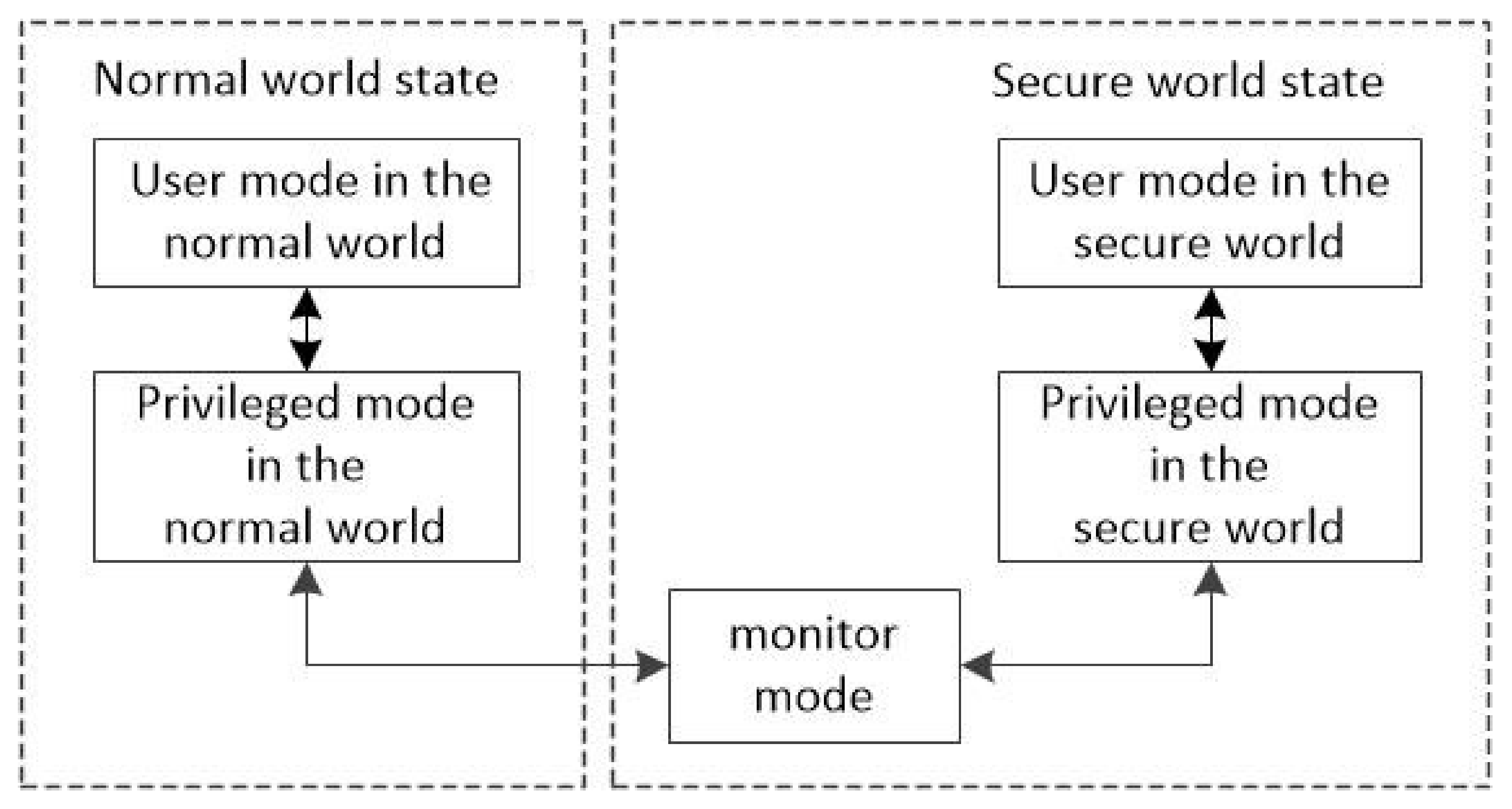
2.4. Trustzone Technology
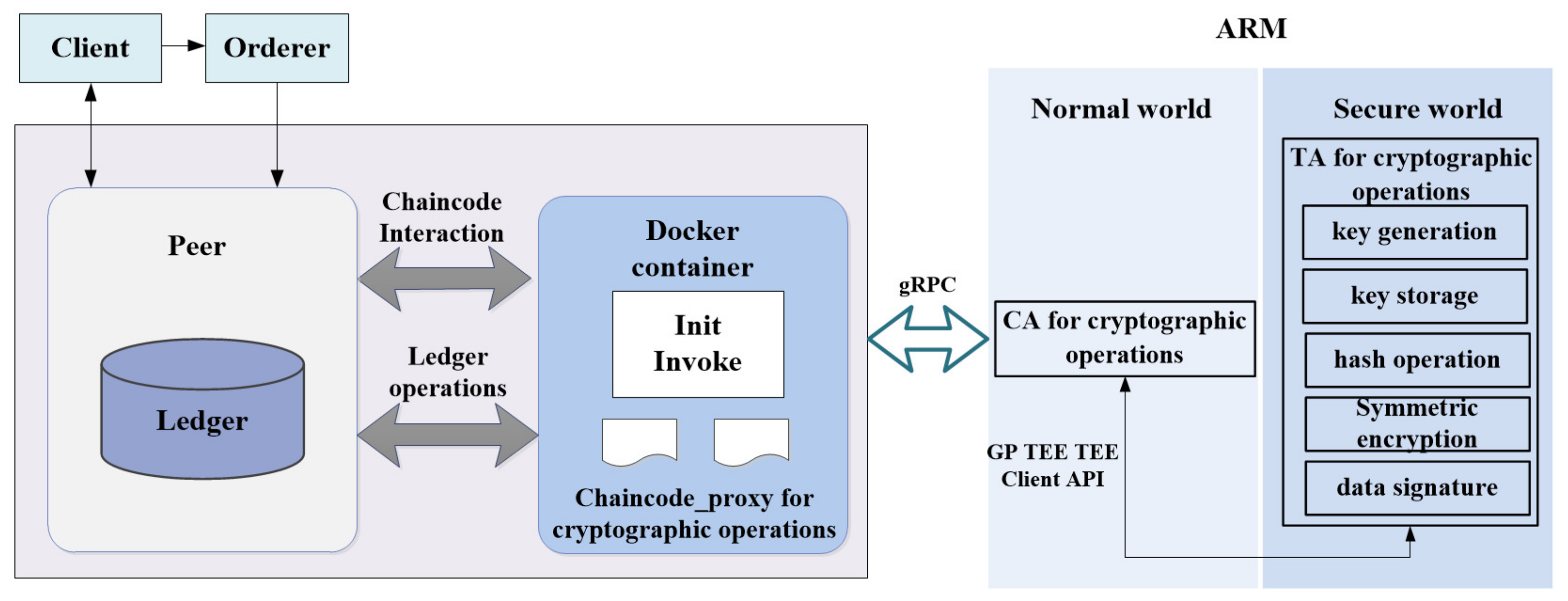
3. System Architecture
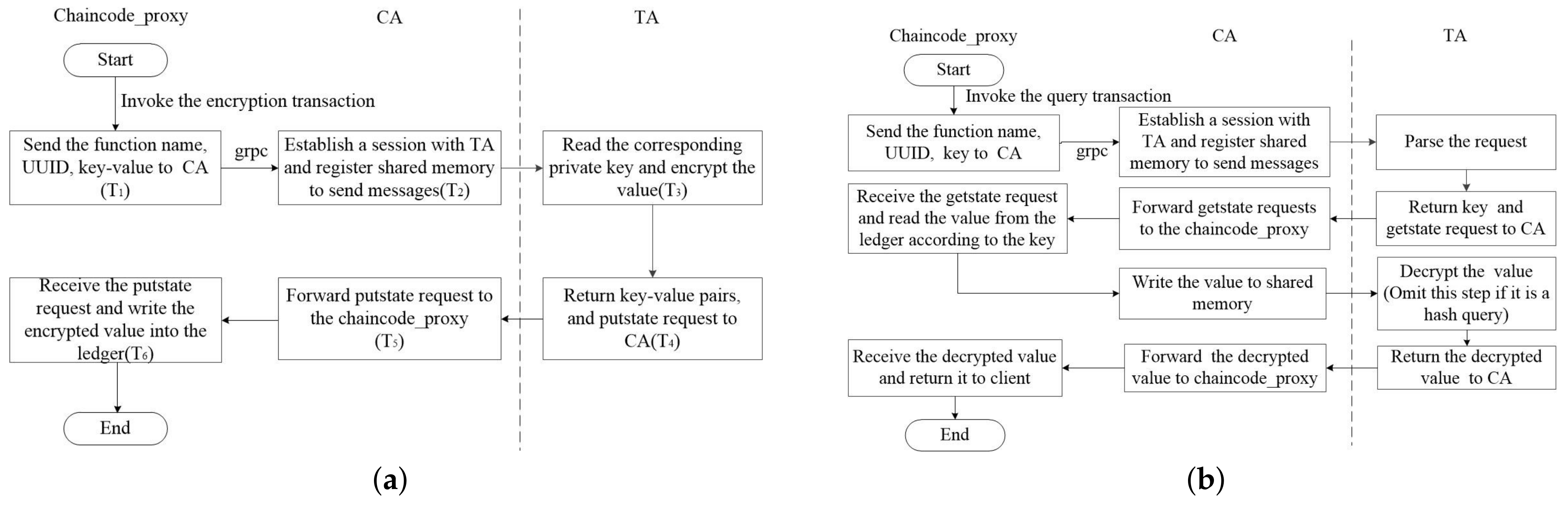
- Chaincode_proxy. The chaincode_proxy is installed and instantiated as a chaincode, which is deployed on Fabric network nodes, runs in an isolated sandbox (currently a Docker container), and interacts with corresponding peer nodes through the gRPC protocol to manipulate data in the distributed ledger. it is responsible for forwarding chaincode encryption request to the CA or receiving processing responses from CA. After installation and instantiation, the UUID corresponding to the TA must be passed to the chaincode_proxy so that it can communicate with the TA that provides cryptographic services.
- CA. The CA for cryptographic operations runs in the normal world REE and is used to forward messages between chaincode_proxy and TA. Communication between the chaincode_proxy and the CA is achieved through gRPC remote procedure calls and the session between the CA and the TA is achieved through the TEE Client API function.
- TA. The TA for cryptographic operations runs in the TEE secure world and is called by CA. It replaces the BCCSP module in Fabric to provide encryption services for Fabric, including key generation, key storage, symmetric encryption, hash calculation, digital signature and other modules.
4. Implementation Details
4.1. Interactive Process
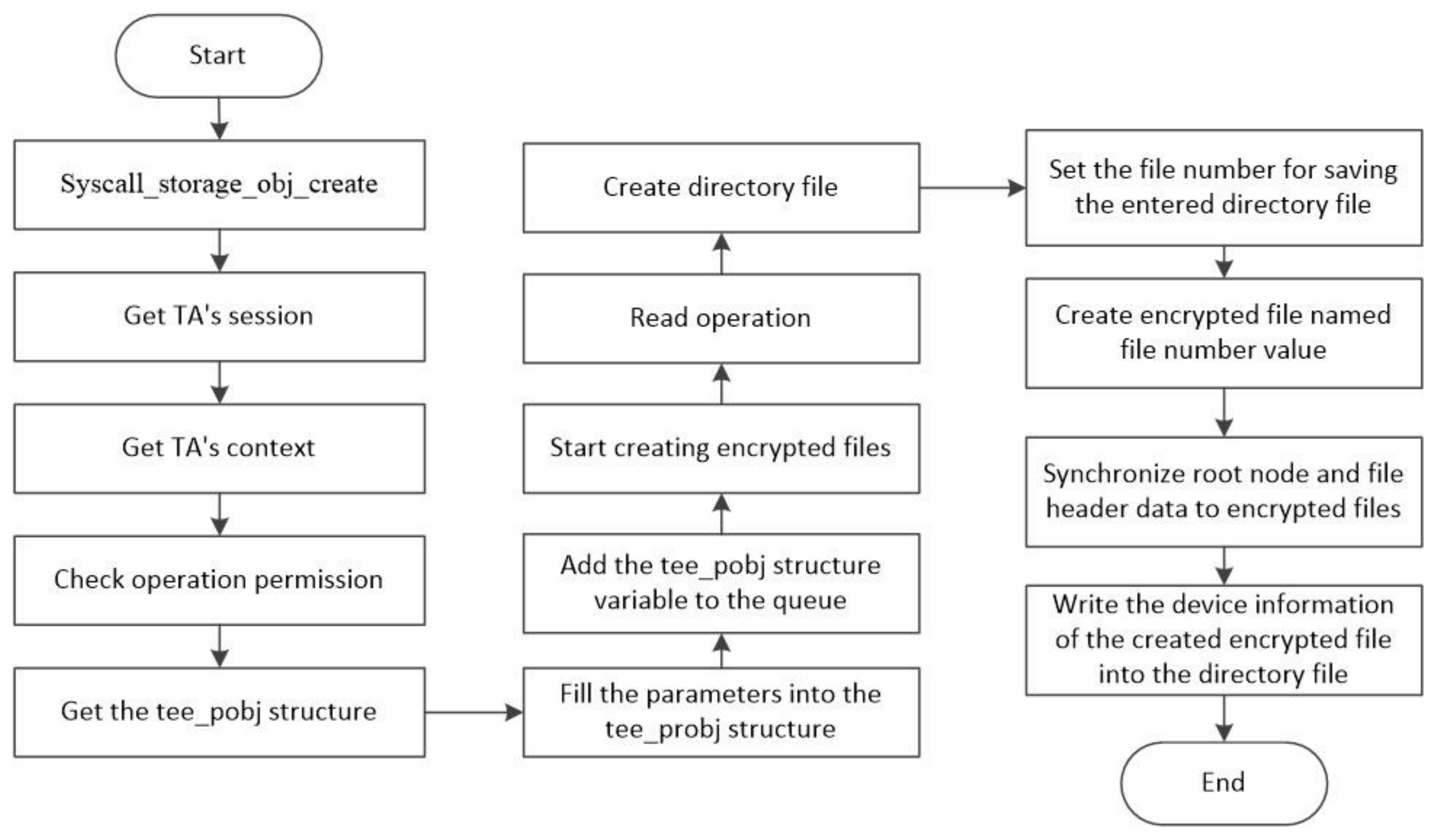
4.2. Key Storage Module in TA
4.2.1. Creation of Directory Files and Key Encrypted Files
4.2.2. Writing and Reading of Key Encryption File
4.3. Symmetric Encryption and Signature Module in TA
- When the TA receives the TEEC_InvokeCommand command request from the CA, it calls the TEE_AllocateOperation function to allocate an operation handle for cryptographic operations, and sets the algorithm type and mode to determine whether the cryptographic algorithm is encrypted or decrypted. Where the mode parameter is set to EN_MODE_CBC.
- Call the TEE_AllocateTransientObject function to allocate an uninitialized temporary space. After the allocation operation is successful, call the TEE_InitRefAttribute and TEE_PopulateTransientObject functions to set the key object parameters, and then call the TEE_SetOperationKey function to save the contents of the object storing the key to the operation handle.
- Call the TEE_CipherInit function to initialize the configuration.
- Call the TEE_CipherUpdate function interface to transmit the data to be calculated.
- Call the TEE_CipherDoFinal function to complete the AES encryption and decryption operation, and return the operation result.
4.4. Data Encryption and Signature Module in TA
- When a link is established between the TA and the CA through the OpenSession operation, the TEE_AllocateOperation function is called to specify the type of digest algorithm (for example: SHA-256, SHA-384, etc.)
- Call the TEE_DigestDoFinal function to send the data to be calculated (this function can be called continuously to send the data).
- Call the TEE_DigestUpdate function to perform the digest calculation operation, and feed the data back to the TA.
- Finally, the functions of CloseSession and FinalizeContext are called in turn to release resources and avoid resource occupation caused by data.
5. Experimental Configuration and Analysis
5.1. Experimental Environment
5.2. TCB Size
5.3. Security Analysis
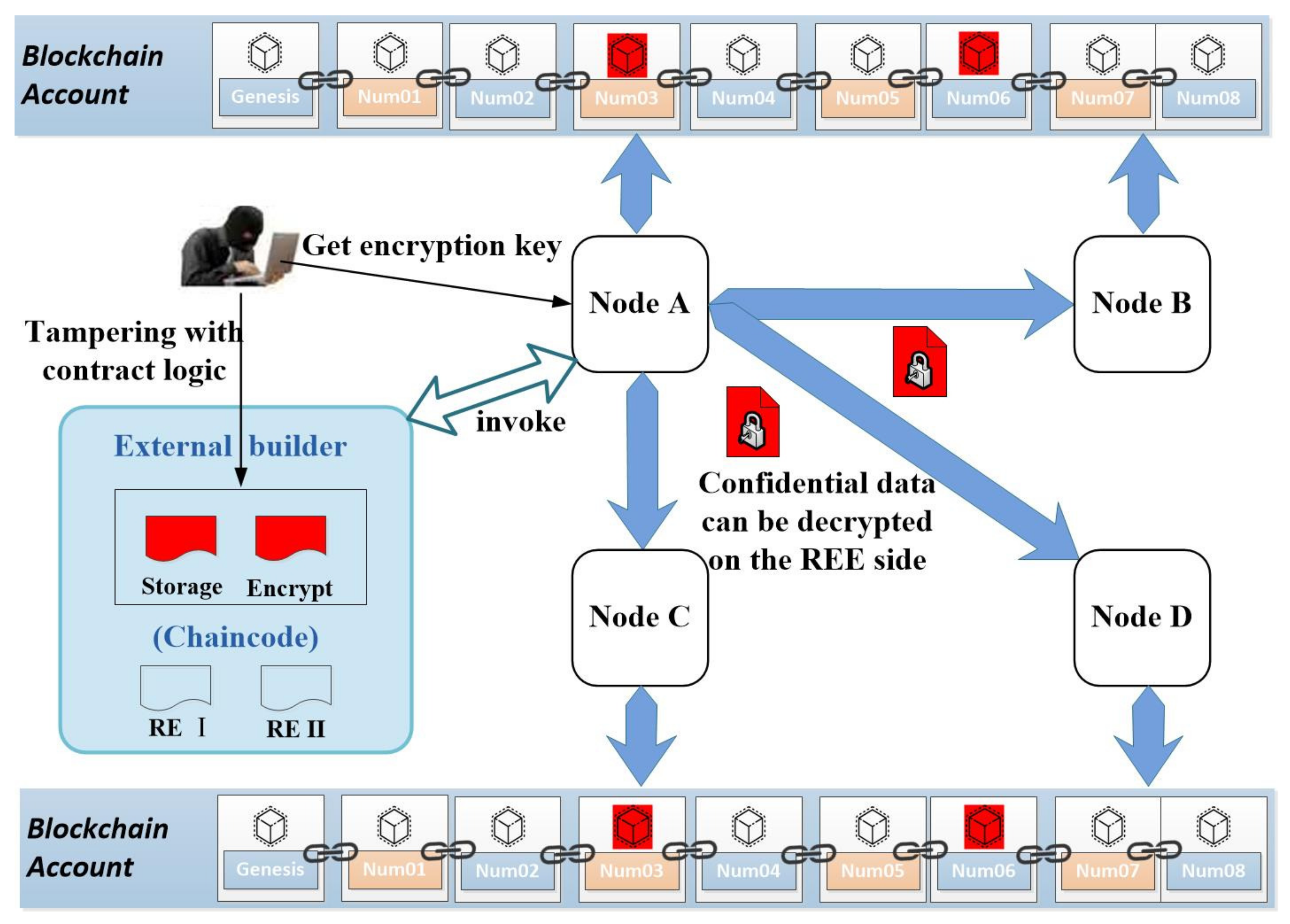
5.3.1. Analysis of Potential Attack Scenarios
- Key disclosure attack
- Privacy Stealing Attack
- Image Replacement Attack
5.3.2. Compared with E-Fabric
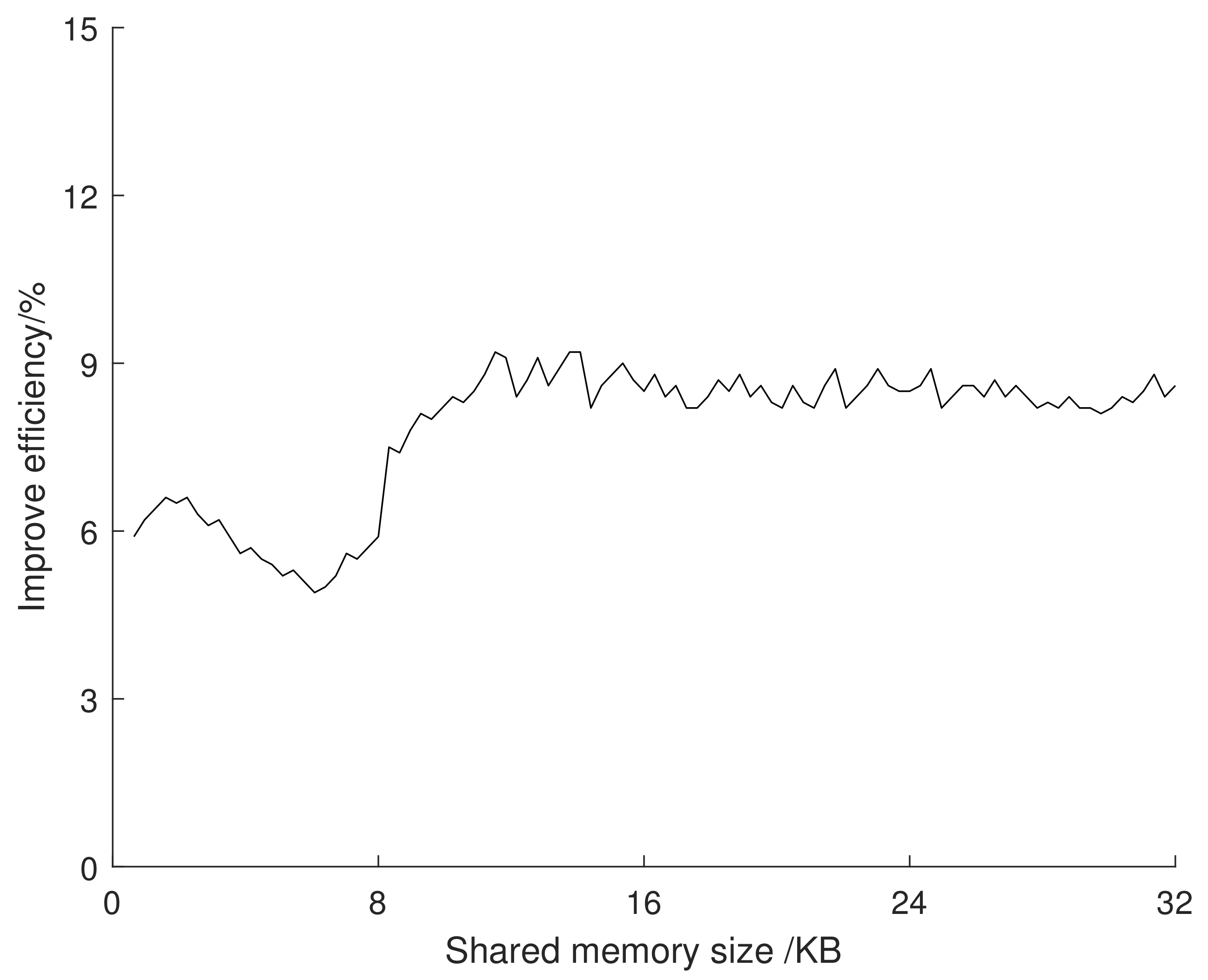
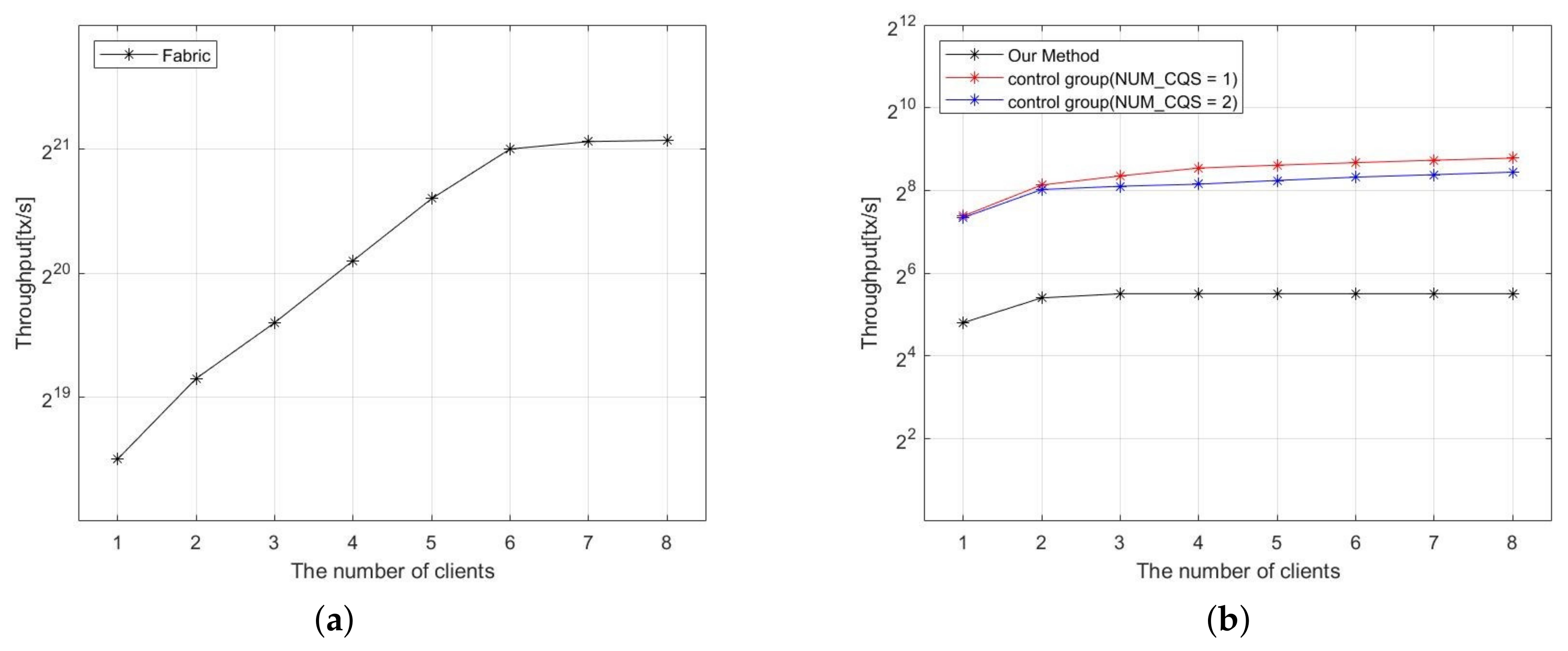
5.4. Performance Evaluation
5.4.1. Performance of Hash Operation Module
5.4.2. Read and Write Performance of Key Encrypted Files
5.4.3. Performance of Symmetric Encryption Module
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Sousa, J.; Bessani, A.; Vukolic, M. A byzantine fault-tolerant ordering service for the hyperledger fabric blockchain platform. In Proceedings of the 48th Annual IEEE/IFIP International Conference on Dependable Systems and Networks, Luxembourg, 25–28 June 2018; pp. 51–58. [Google Scholar]
- Wutthikarn, R.; Hui, Y.G. Prototype of blockchain in dental care service application based on hyperledger composer in hyperledger fabric framework. In Proceedings of the 22nd International Computer Science and Engineering Conference, Chiang Mai, Thailand, 21–24 November 2018; pp. 1–4. [Google Scholar]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain technologies for the internet of things: Research issues and challenges. IEEE Internet Things J. 2019, 6, 2188–2204. [Google Scholar] [CrossRef] [Green Version]
- Brandenburger, M.; Cachin, C.; Kapitza, R. Trusted computing meets blockchain: Rollback attacks and a solution for hyperledger fabric. In Proceedings of the 38th Symposium on Reliable Distributed Systems (SRDS), Lyon, France, 1–4 October 2019; pp. 32400–32409. [Google Scholar]
- Brandenburger, M.; Cachin, C.; Kapitza, R.; Sorniotti, A. Blockchain and trusted computing: Problems, pitfalls, and a solution for hyperledger fabric. arXiv 2018, arXiv:1805.08541. [Google Scholar]
- Cheng, R.; Zhang, F.; Kos, J.; He, W.; Song, D. Ekiden: A Platform for Confidentiality-Preserving, Trustworthy, and Performant Smart Contracts. In Proceedings of the 2019 IEEE European Symposium on Security and Privacy, Stockholm, Sweden, 17–19 June 2019; pp. 185–200. [Google Scholar]
- Fan, J.; Chen, J.; Shen, R. Sgx-based approach for blockchain transactions security and privacy protection. J. Appl. Sci. 2021, 39, 17–28. [Google Scholar]
- Zhou, L.; Wang, L.; Ai, T.; Sun, Y. BeeKeeper 2.0: Confidential blockchain-enabled IoT system with fully homomorphic computation. J. Abbr. 2008, 10, 142–149. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Dai, W.; Wang, Q.; Wang, Z.; Lin, X.; Jin, H. Trustzone-based secure lightweight wallet for hyperledger fabric. J. Parallel And Distrib. Comput. 2021, 149, 66–75. [Google Scholar] [CrossRef]
- Müller, C.; Brandenburger, M.; Cachin, C.; Felber, P.; Gttel, C.; Schiavoni, V. Tz4fabric: Executing Smart Contracts with ARM TrustZone. In Proceedings of the 2020 International Symposium on Reliable Distributed Systems, Shanghai, China, 21–24 September 2020; pp. 31–40. [Google Scholar]
- Yannick, K.; Yi, W.; Wang, J. A lightweight trusted execution environment construction method for fabric chaincode based on sgx. Netinfo Secur. 2022, 22, 73–83. [Google Scholar]
- Zhu, Y.; Song, W.; Wang, D.; Ma, D.; Chu, C. Ta-spesc: Toward asset-driven smart contract language supporting ownership transaction and rule-based generation on blockchain. IEEE Trans. Reliab. 2021, 99, 1255–1270. [Google Scholar] [CrossRef]
- Sharma, A.; Schuhknecht, F.M.; Agrawal, D.; Dittrich, J. Blurring the lines between blockchains and database systems: The case of hyperledger fabric. In Proceedings of the 2019 International Conference on Management of Data, Amsterdam, The Netherlands, 1–5 July 2019; pp. 105–122. [Google Scholar]
- Gorenflo, G.; Lee, S.; Golab, L.; Keshav, S. FastFabric: Scaling hyperledger fabric to 20000 transactions per second. In Proceedings of the 2019 IEEE International Conference on Blockchain and Cryptocurrency (ICBC), Seoul, Korea, 14–17 May 2019; pp. 455–463. [Google Scholar] [CrossRef] [Green Version]
- Wan, S.; Li, M.; Liu, G.; Wang, C. Recent advances in consensus protocols for blockchain: A survey. Wirel. Netw. 2020, 26, 5579–5593. [Google Scholar] [CrossRef]
- Guo, Q.; Zhang, D.; Liang, C.; Liu, X.; Song, J. Design and implementation of proxy-protected proxy signature based on sm2. Chin. J. Netw. Inf. Secur. 2017, 3, 47–54. [Google Scholar]
- Androulaki, E.; Manevich, Y.; Muralidharan, S.; Murthy, C.; Laventman, G. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portugal, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Badruddoja, S.; Dantu, R.; He, Y.; Upadhayay, K.; Thompson, M. Making smart contracts smarter. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, New York, NY, USA, 24–28 October 2016; pp. 254–269. [Google Scholar]
- Vacca, A.; Sorbo, A.D.; Visaggio, C.A.; Canfora, G. A systematic literature review of blockchain and smart contract development: Techniques, tools, and open challenges. J. Syst. Softw. 2020, 174, 110891. [Google Scholar] [CrossRef]
- Hei, X.; Gao, W.; Wang, Y.; Zhu, L.; Ji, W. From hardware to operating system: A static measurement method of android system based on TrustZone. Wirel. Commun. Mob. Comput. 2020, 4, 8816023. [Google Scholar] [CrossRef]
- Shepherd, C.; Arfaoui, G.; Gurulian, I.; Lee, R.P.; Markantonakis, K.; Akram, R.N.; Sauveron, D.; Conchon, E. Secure and trusted execution: Past, present, and future-a critical review in the context of the internet of things and cyber-physical systems. In Proceedings of the 2016 IEEE Trustcom/BigDataSE/ISPA, 2, Tianjin, China, 3–26 August 2016; pp. 168–177. [Google Scholar]
- Linaro, Op-Tee Documentation. Available online: https://optee.readthedocs.io/ (accessed on 27 December 2022).
- GlobalPlatform Device Specifications: Trusted Execution Environment. Available online: https://globalplatform.org/ (accessed on 27 December 2022).
- Foschini, L.; Gavagna, A.; Martuscelli, G.; Montanari, R. Hyperledger fabric blockchain: Chaincode performance analysis. In Proceedings of the 2020 IEEE International Conference on Communications, Guangxi, China, 28–31 October 2020; pp. 1–6. [Google Scholar]
- Developers, G. Protocol Buffers. Available online: https://developers.google.com/protocol-buffers/ (accessed on 27 December 2022).
- Brandenburger, M.; Cachin, C.; Lorenz, M.; Kapitza, R. Rollback and forking detection for trusted execution environments using lightweight collective memory. In Proceedings of the 47th Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN), Denver, CO, USA, 31 October 2017; pp. 157–168. [Google Scholar]



| Scheme | Research Work | Resistance to Attacks |
|---|---|---|
| SGX | Brandenburger et al. [4,5] | Privacy stealing and rollback attack |
| Cheng et al. [6] | Privacy stealing and key disclosure attack | |
| Fan et al. [7] | Privacy stealing and replay attack | |
| Yannick et al. [11] | Privacy stealing, key disclosure, image replacement and MITM attack | |
| Trustzone | Dai et al. [9] Müller et al. [10] | Key disclosure attack Privacy stealing attack |
| This work | Privacy stealing, key disclosure, image replacement attack |
| Environment | Version | Notes |
|---|---|---|
| operating system | Ubuntu 18.04 server x64 | - |
| blockchain network | Hyperledger Fabric1.4.3 | Open source blockchain architecture |
| gRPC | v.1.20.0 | For remote procedure calls |
| OP-TEE | v3.8.0 | Provide the trusted environment |
| Go language | Go 1.14.6 | Smart contract development language |
| Go | C | C++ | Protocol Buffer | Total | |
|---|---|---|---|---|---|
| chaincode_proxy | 191 | 0 | 0 | 40 | 231 |
| CA | 0 | 0 | 388 | 40 | 428 |
| TA | 0 | 896 | 0 | 0 | 896 |
| Feature | E-Fabric | Our Scheme |
|---|---|---|
| Technology | Intel SGX | ARM Trustzone |
| Resist root attacker | √ | √ |
| Chaincode confidentiality | √ | √ |
| Remote attestation | √ | × |
| Data encryption | √ | √ |
| Key safety storage | × | √ |
| Average (ms) | Min (ms) | Max (ms) | |
|---|---|---|---|
| 9.46 | 7.37 | 13.24 | |
| + | 30.36 | 26.13 | 34.24 |
| 1.61 | 1.52 | 1.68 | |
| 0.02 | 0.02 | 0.02 | |
| 0.47 | 0.41 | 0.61 | |
| sum | 41.92 | — | — |
| Key Size | Writing (ms) | Reading (ms) |
|---|---|---|
| 128 B | 58.27 | 36.61 |
| 192 B | 61.33 | 38.07 |
| 256 B | 65.15 | 39.36 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gao, W.; Hei, X.; Wang, Y. The Data Privacy Protection Method for Hyperledger Fabric Based on Trustzone. Mathematics 2023, 11, 1357. https://doi.org/10.3390/math11061357
Gao W, Hei X, Wang Y. The Data Privacy Protection Method for Hyperledger Fabric Based on Trustzone. Mathematics. 2023; 11(6):1357. https://doi.org/10.3390/math11061357
Chicago/Turabian StyleGao, Wen, Xinhong Hei, and Yichuan Wang. 2023. "The Data Privacy Protection Method for Hyperledger Fabric Based on Trustzone" Mathematics 11, no. 6: 1357. https://doi.org/10.3390/math11061357
APA StyleGao, W., Hei, X., & Wang, Y. (2023). The Data Privacy Protection Method for Hyperledger Fabric Based on Trustzone. Mathematics, 11(6), 1357. https://doi.org/10.3390/math11061357










