1. Introduction
It is important to study how to improve funding of companies, as [
1] exposed a strong positive relationship between access to finance and job growth. Overall, firms with access to a loan exhibit employment growth between 1 to 3 percentage points larger than firms with no access to finance. In the case of SME (Small and Medium Enterprises), they are the top job creators, but they suffer from a lack of funding and late payments to their invoices. No wonder the global market of invoice discounting will grow at a steady rate over the next few years [
2]. Invoice discounting represents 10% of banks’ provided credit, a major source of working capital finance globally [
3]. It seems it will become even greater in the next crisis, due to their cyclical nature. In particular, invoice discounting is an effective way to help companies troubled by late payments (when invoices are paid in one to three months). Over the recent decades, in the European Union alone, the factoring market has surpassed loans and other forms of funding [
3]. Moreover, invoice discounting has another benefit, in that the customer (debtor) is not informed that the supplier (creditor) is being financed. From the suppliers’ point of view, this confidentiality is good for easing negotiations, as they hide the weakness of using working capital finance.
According to [
4], small companies in the financial market are not being adequately served, despite the recognition that this market has the potential to meet their liquidity needs. The difficulty lies in assessing the authenticity of the parties involved in the invoice marketplace and determining whether an invoice has already been factored. These challenges make it easy for fraudulent activities, such as double pledging or selling non-existent invoices, to take place. Such fraudulent practices can cause problems for buyers who may be contacted by fraudulent factors demanding payments for invoices that have already been factored by legitimate sellers. Moreover, even in the absence of fraud, paying the invoice to the wrong organization can lead to several problems.
A possible solution to this problem could be a centralized system where all invoices could be stored and verified by interested parties. However, despite the factoring market’s existence for centuries, no such entities have emerged due to the need for confidentiality. Buyers, factors, and sellers are reluctant to share information about past invoices, as disclosing them can work against you for a number of reasons. The study presented in [
4] proposes a third-party solution to address the shortcomings of centralized systems. As mentioned in [
5], preventing an invoice from being factored twice is a crucial feature of a factoring system. Blockchain technology has the potential to revolutionize various financial processes such as inter-company transactions, procure-to-pay, order-to-cash, rebates, warranties, and financing (including trade finance, letters of credit, and invoice factoring). Recent surveys such as [
6,
7,
8,
9,
10] suggest that wherever paper-based systems are prevalent, blockchain can offer a promising alternative.
1.1. Invoice Discounting and Factoring
Invoice discounting provides the advantage of accelerating cash flow from customers to suppliers, as suppliers receive advance payments from the bank rather than waiting for customer payment. This allows businesses to invest in growth and expansion. However, faster invoice discounting services need to be provided while preventing double spending and minimizing risk. Blockchain frameworks have the potential to address these issues and transform the invoice discounting process by providing increased transparency and reducing risk for all parties involved, including suppliers, customers, and financial institutions.
Factoring is a financial transaction where a business sells its accounts receivable (i.e., invoices) to a third party at a discount to meet its immediate cash needs. Factoring faces issues related to inter-mediation and trade finance and supply chain, where decentralized finances offer potential solutions. Several studies [
11,
12,
13,
14,
15] have explored promising approaches to tackle these challenges.
This paper aims to delve into novel alternative approaches to invoice discounting or factoring by radically decentralizing how invoices are utilized. Instead of storing all invoices on a ledger, we plan to develop solutions that leverage algorithms implemented as dApps or smart contracts to score companies, decentralize crowd funding, and introduce byppay, a new solution to invoice compensation with debt-soothing effects. Our approach will only declare invoices related to the clients and suppliers of an actor on a ledger, using a full mechanism of Proof of Existence (PoE). The inherent benefits of such a decentralized approach to invoice compensation are bolstered, as discussed in [
12,
16].
1.2. State of the Art of Blockchain for Funding
Discounters can benefit from decentralization and the adoption of blockchain in several ways [
17,
18,
19]. Firstly, there is an immutable and time-stamped record of every invoice emitted by a company, including the debtor’s receipt and verification against which a discounter would fund. As a result, the overall invoice discounting process is streamlined. Secondly, the trust and security mechanisms of blockchain enable the elimination of on-site audits of receivables, debtors, notification, and month-end reconciliation processes. Additionally, blockchain facilitates fast and cost-effective value transfer, particularly for cross-border payments [
20].
Furthermore, the debtor’s verification of invoice validity and receipt of goods and services significantly reduces the risk of dispute and non-payment. The debtor also has an incentive to acknowledge and confirm invoices promptly, since their confirmation record is visible to their suppliers on the blockchain, which can influence payment terms and contract prices. Moreover, blockchain technology’s immutable nature helps to prevent invoice fraud by eliminating the consensus for double invoicing transactions. Finally, time stamping an invoice has legal value, protecting the first assignee from subsequent assignees who try to assign the same invoice more than once without notice, thereby safeguarding the assignee’s value.
1.3. Proof of Existence
The paper cited in [
2] presented evidence suggesting that the adoption of distributed ledger-based approaches could enhance the invoice discounting service. However, in our view, the current approaches, using blockchain, remain centralized in nature, relying on a full declaration of invoices made available online for graph analysis. We propose a different approach: a bottom-up, agent-based implementation that is more suitable for decentralized implementation and which fits pretty well with Blockchain/Distributed Ledger Technologies (DLTs).
Distributed intelligence algorithms and multi-agent paradigms require a proper framework that the computing and ledger possibilities of DLT platforms such as Ethereum or Polygon, Polkadot, BitcoinSV, and Binance Smart Chain, among others, are ideal for developing such intelligence. Many distributed bottom-up behaviors and strategies are open for research, including coalition formation techniques and distributed autonomous organizations that require the proper platforms and environments to develop fully. Actors such as [
21] that use the BitcoinSV platform or [
22] that use blockchain to enhance the PoE.
1.4. On Collateral
Our solution requires no third parties and no collateral (but invoices are the basic asset) and is anti-cyclical, similarly to the complementary currencies such as WIR Bank (
https://www.wir.ch, accessed on 15 September 2022) [
23]. In fact, currencies are the oldest information system of humanity, and today we have the means to create a new information systems using new forms of payment that will complete the strength of the currencies.
However, using collateral and liquidity pools will indeed boost the invoice discounting, factoring or byppay adoption. Thus, this project covers the areas of distributing intelligence with a DLT, and adopts new DeFi (Decentralized Finances) to cover risks or enhance liquidity of the invoices as assets, real-world assets, which are tokenized on a ledger. Instead of transacting with a counterparty, following the logic of conventional financial operations, DeFi users interact with software programs that pool the resources of other DeFi users [
24].
The DeFi implementation is backed by the ideas of value in the Internet of Value (IoV), where tokenized invoices back the value and their rights are traded among peers (invoices as a type of real assets as considered in [
8]). With the proposed implementation of collateral, some of the IoV systemic risks are solved, remarkably the over-collateralization will not be necessary, as stated in our contributions to the recent reports of [
9,
25].
1.5. Liquidity Pools
Regarding liquidity pools for crowd funding of factoring, there are decentralized Protocols for Loanable Funds (PLF) that enable users to borrow or lend digital assets [
26,
27,
28]. Automated smart contracts act as intermediaries by locking the assets deposited by the lender and providing borrowers with liquidity in exchange for collateral. These smart contracts are also known as Lending Pools [
29]. In the state of the art, Lending Pools lock a pair of tokens, a loanable token, and a collateral token. Lenders earn interest rates based on the supply and demand of the provided liquidity. However, as there is no guarantee of repayment, borrowers must over-collateralize their position. Additionally, when returning the borrowed amount, the borrowers must pay an interest rate, which is proportionally divided among the lenders and the governance token. Furthermore, borrowers will be charged an extra fee when they are liquidated [
26].
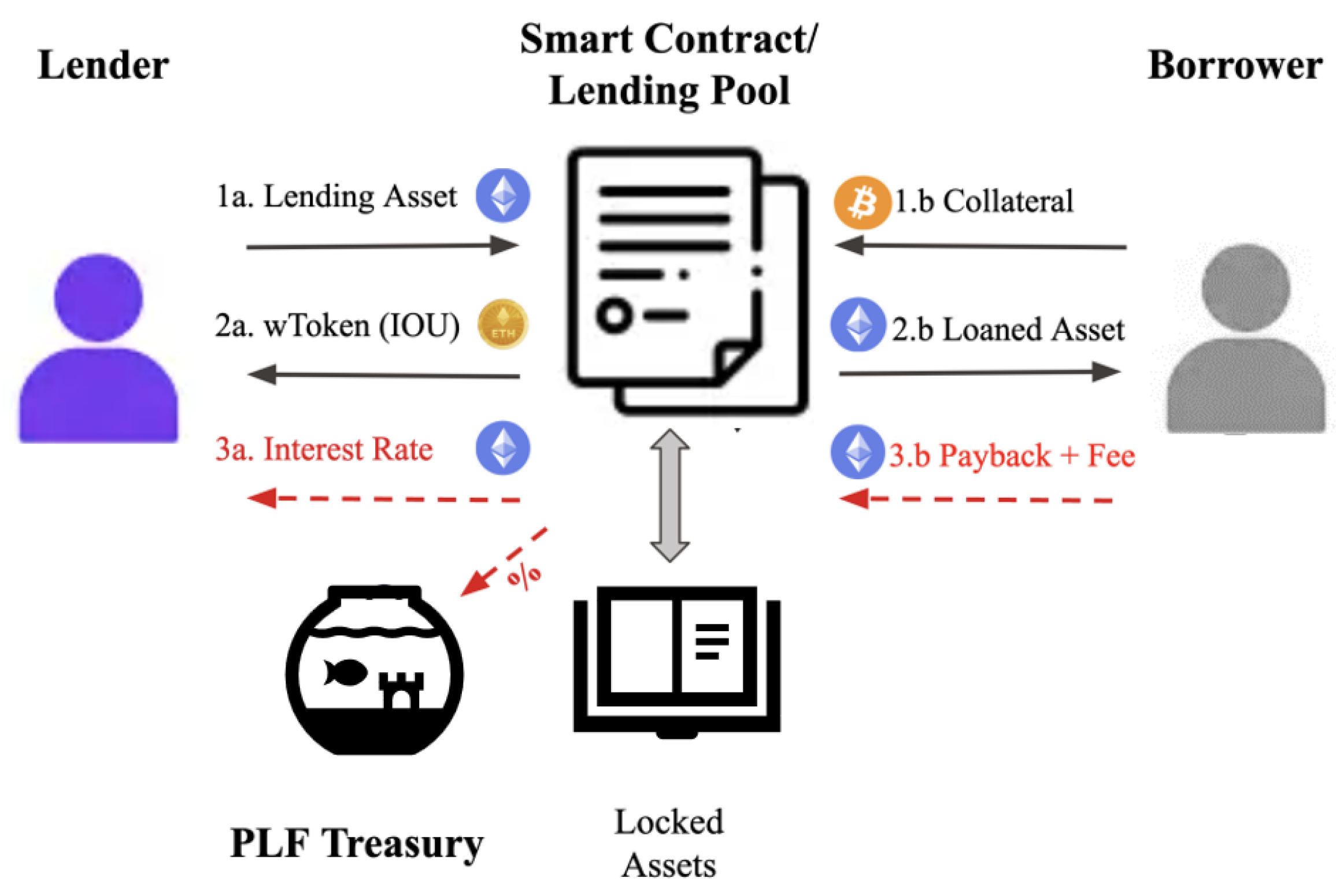
Figure 1 shows a graphic schematic of the process. Starting from the left, Lenders deposit their crypto-assets, such as Ethereum, to earn additional profits. They receive a wrapped token or IOU from the PLF as proof of their deposit. The smart contract acts as a middleman and manages the deposited assets, loans, and liquidations. Borrowers are required to deposit collateral before obtaining a loan. At the end of the loan term, the borrower is obligated to return the borrowed amount plus an interest rate. This interest rate is split pro rata among all lenders, while the remaining interest generated is revenue for the PLF.
Table 1 presents a comparison between DLF and other DeFi protocols such as Decentralized Exchanges and and Yield Aggregators.
1.6. From Over-Collateralization to Risk Appraisal
The current initiatives involve liquidity pools and related DeFi implementations, where any tokenized asset (i.e., insurances, factoring, lending, guaranties of service, and more) is backed by collateral in the search of collateralizing the risk, by means of any of the new digital assets or virtual currencies [
25]. Their drawback lies in the over-collateralization, and the volatility caused by new forms of inter-dependency at an unprecedented level is a systemic risk in the future internet of value.
In our opinion, the over-collateralization does not fit properly with invoices risk management, as they are assets with value already appraised in a currency and their risk is related to their liquidity. The euros that will be paid through an invoice are a sort of a stable coin—invoice-euro, for example—so the conversion invoice-euro is pegged to the euro at a discount; say 0.5, 1, or 2 percent or more according to the mora or invoice non-payment rates. It is not a monetary risk, nor a crazy market valuation, but pure risk management that is well known in financial markets which use sophisticated tools.
Unlike the solutions of liquidity pools in the state of the art that use crowd source and oracle approaches to rate risk, we look for alternative formulas that appraise the risk in a fully automated way.
In this reality, there is room to study partly collateralized invoices novel mechanisms using risk management tools that are worthy of exploration and creation in a decentralized implementation that should avoid over-collateralization. These techniques, including the Black–Scholes or the Kelly Criterion [
30], are currently studied for their implementation in risk appraisal and management. The work proposed here is interested in the Kelly Criterion for calculating the optimal diversification of investments for creating a portfolio, given a volume of money available for investment, and given some known risk, as it forecasts the optimal benefit achievable.
In the case of decentralized markets with liquidity pools for invoices, provided that we know the volume of money in advance, because it is the liquidity pool’s amount of money, we chose to reformulate the Kelly Criterion so that one might decide whether a given invoice that is partly collateralized can be accepted to be fully collateralized by the liquidity pool, and at what benefit to collect from to compensate the risk. This benefit will be the premium required as a fee for every invoice accepted in the liquidity pool. As this is a new usage of the Kelly Criterion, we named it the Reverse Kelly Criterion as a new formula that calculates the premium to be granted given an invoice with some collateral, as we will see in the following section containing all the details. So this is the goal of our paper: to invent a resilient PLF mechanism that does not require over-collateralization. Let us see how we can do it.
2. Reverse Kelly AMM (rkAMM) Design
Electronic markets use algorithms that decide the price and the amount of liquidity supplied in markets. However, this automation is not complete, as algorithms are managed by humans who intervene to improve their design, or turn them off entirely if conditions become unfavorable, leading to liquidity withdrawals that can exacerbate market volatility. Instead, an Automated Market Maker (AMM) is a type of market that employs a single algorithm to facilitate trades. It is a straightforward, fixed, and predictable approach [
31]. AMMs use a constant product rule to swap assets: the product of the reserves of the two assets must remain the same before and after any currency exchange or swap occurs. This concept of holding the value of a function, such as the product of asset reserves during exchanges, evolved into the concept of constant function market making. The fundamental design of constant function market makers was established in [
32]. Then, a simple formula,
, set prices and quantities for thousands of different assets using few hundreds lines of code. The AMM today [
31] executes upwards of USD 50bn per month in digital assets. The most popular AMM, Uniswap, uses a year of data acquired directly from the public Ethereum blockchain containing over 39 million transactions.
In an AMM, anyone can become a Liquidity Provider (LP) by transferring their digital assets to pools. Fund liquidity can be increased, thus increasing the pool size or creating new ones. In exchange, they receive revenue from a fixed fee on trades (called swaps) by those who demand liquidity from the AMM. Fee revenue is shared equally among LPs in proportion to their investment—so LP returns vary based on the amount of liquidity in a pool (or the pool’s volume or size). LPs can only add or remove liquidity, and prices are set by the AMM algorithm, unlike traditional market makers that can also vary in terms of prices [
31].
An algorithm has been conceived following the main guidelines of an AMM for the full collateralization of invoices. As previously stated, AMM were designed to trade two assets by their balance
x and
y in a liquidity pool to keep up a constant
k, as
, so that incoming
x means withdrawing
y to keep the
constant at
k. There are several variants of the same scheme [
33] to add resilience and utility to the AMM implementation, which must follow their axioms.
In our implementation, we also have liquidity providers that contribute and withdraw their funds at a fee, so that the liquidity pool has some volume V to grant the remaining collateral demanded by the invoices to become fully funded, and premium is required in exchange to compensate the risk aiming at some benefit. From this point of view, it works as a standard community fund for securing risk of participants, but with liquidity providers instead and securing particular assets, such as invoices, that are backed by some collateral. Thus, collateral is added to the pool along with the premium p and, in exchange, the remaining collateral exits, , meaning that the constant k is recalculated by the Kelly criterion. Thus, k changes with the new liquidity volume V, and thus with the premium collected.
As briefly introduced, we use the Kelly criterion to calculate the premium contribution to the liquidity pool for missing collateral for a 100% backing invoice, after acknowledging that it is partially backed by some collateral. It is named rkAMM: Reverse Kelly AMM. Performance curves for the rkAMM have been simulated with streams of hundreds of invoices and subsequently analyzed. In its implementation, we have considered the minting of NFTs with the inclusion of terms such as “backing %” of the invoices, risk, and elaboration, which are useful for applying the Kelly Criterion investment formula, among other considerations.
We assumed that for an invoice of amount X, the collateral q is a percentage of X, and the remaining non-collateralized amount is . We will show how these assumptions have been worked out in the rkAMM.
The Kelly criterion, sometimes referred to as the Kelly strategy or Kelly bet, is a mathematical formula that determines the optimal size for a bet when the expected returns are known. It involves maximizing the expected value of the logarithm of wealth or expected geometric growth rate, as described in [
30]. Due to its ability to produce higher wealth compared to any other strategy in the long run (when the number of bets can be infinite), the criterion is also known as the scientific gambling method. The formula has been practically demonstrated in gambling and used to explain diversification in investment management. Rediscovered for its usage in multiple portfolios [
34], in the case of digital assets, it was proposed to be used today for risk assessment of derivative products [
35]. Here, we saw the opportunity to use the Kelly criterion for “assessing” the liquidity pools for invoice funding.
We use the Kelly criterion to calculate how much premium should be required to contribute to a liquidity pool of size
V for an invoice amount of
X with a collateral of
p, thus demanding the remaining
collateral out of the rkAMM, as depicted in
Figure 2.
We plan to use the rkAMM connected to Byppay [
36] because byppay is a system that curates invoices in the sense that groups of three companies acknowledge each other’s rights (invoices) and swap the rights among players to compensate said invoices. Whenever a Byppay among three companies A, B, and C is created, where C invoiced B and B invoiced A so that the chain of payments happened to be from A to B and B to C, schematically A > B > C. In a byppay A > C, that means that A pays directly to C and compensates the A > B and B > C payments. The Proof of Existence (PoE) of the invoices involved in the Byppay considers the mutual knowledge among A and C through B, the common acquaintance of A and C. This PoE and A rating must be sufficient for most of the Byppay cases that require no early payments. This Byppay flow is shown in
Figure 3.
If the Byppay is open to third parties other than A, B, and C, then some collateral might be required to B to enhance the PoE and stake of the AB invoice, and the collateralization flow might let the door open to third parties that trust B, or trust A, or trust both, to add collateral to that invoice, privately or openly as a marketplace.
Everyone contributing with collateral will receive some fees; say, a 2% fee out of his piece of contribution to the collateral of the invoices being byppaid. Invoices will be paid some time later, usually in one to three months on average; therefore, the contributed collateral pays off an annual percentage yield (APY) average of 8% to 24%. Contributors of collateral will have advance knowledge of the due date of the invoices to calculate their benefits. Additionally, the greater the connection and knowledge of A and B, the more oracles they would need to rate/score companies, which might fit well on this stage of the byppay flow.
The byppayable invoices with strong collateralization (say, from 50% collateral) are eligible for the rkAMM, and the C will secure the remaining collateral by means of premium to be contributed to said liquidity pool, and then C will receive the full AB amount in advance, while the full amount of the AB invoice will be paid by A to the liquidity pool on the due date.
Whenever A pays, all collateral from the marketplace is returned to the liquidity providers with an additional 2%, and the rkAMM liquidity pool retrieves the collateral provided again with an additional 2%, while B obtains the collateral he might have contributed at the 2% extra, deductible from the fees and bonuses that could have released for the entire Byppay process.
2.1. rkAMM Definition
As introduced, a model inspired by an AMM is proposed to automatically comply with invoice compensation. It is an underlying protocol to conduct exchanges in a decentralized manner through an autonomous trading mechanism. This allows users to exchange their assets without involving centralized financial authorities. Kelly’s formula risk assessment criteria will be used.
The following two assets will be considered:
The reserve for collateral allocated in the AMM as a liquidity pool, known as Q.
The reserve of premium collected in the AMM, known as .
The collateral serves as a liquidity asset used to complete the compensation of invoices to pay while, in general terms, the premium serves as a protection mechanism of the AMM against the loss of lent collateral and, hopefully, some benefit. Thus, the premium is considered the amount to be paid based on the risk the AMM assumes when lending collateral.
These assets (
Q and
) are exchanged among agents by interacting with the AMM. Agents withdraw liquidity
Q at a premium
P to compensate the non-collateralized amount of their invoices. This premium contributed by agents is used to compensate the losses the AMM may experience during its operation. The steady remaining premium will be the benefit attributed to the intrinsic performance of the AMM. Additionally, the liquidity providers are enabled to deposit liquidity into the AMM, which allows them to receive a proportional profit out of the accumulated premium based on their shares on the AMM liquidity pool
Q according to proposals of [
37]. Different premium withdrawal policies and periods are discussed in later sections.
In case there is no liquidity available to collateralize an invoice, the AMM will cover the collateralization of the invoice with the premium collected. Once invoices are fully paid, the remaining premium as profit is expected to be withdrawn in different percentages and periods that will be decided in this paper after several simulations to seek the best withdrawal policy.
2.2. rkAMM Formula
Let us explain the formula of collateral and premium exchanges. To do this, we start with Kelly’s investment formula (Equation (
1)):
The following assumptions are made:
f is the ratio between the amount of collateral requested and the total volume of the rkAMM. The total volume of the rkAMM is computed as the sum of the available collateral Q and, eventually, the accumulated premium at the time.
p is the collateralized percentage of an invoice. We chose that p is the probability of the invoice to be paid.
q is the non-collateralized percentage of an invoice amount. We assumed that q is the probability of the invoice to be unpaid.
given that q is the lack of collateral of an invoice to be fully collateralized by the rkAMM, we interpreted it as the amount of money that could be lost; that is, a, which is known as the partial loss in Kelly’s investment formula.
From the above:
b in Kelly’s investment formula is defined as the partial win. We interpreted this value as the ratio between potential profit and potential loss.
Simplifying the Equation (
1) using the assumptions above:
For our purpose, the variable to clear is
b, which is the ratio of potential profit and potential loss. Thus, solving
b from Equation (
2):
The good news is that, in an invoice, the ratio
f and probabilities
p and
q are always known.
The potential loss is known, since it is the amount of collateral that the rkAMM lends to the user, which is equal to the non-collateralized amount. Then, the potential profit is what we have called the . So far, all the variables are known, except for the .
The variable to clear is the potential profit, which is the premium, since it is the amount the rkAMM can earn if the user repays the collateral and the invoice in full. That is why it is a potential profit, because the rkAMM is assuming a risk based on an amount, which is compensated by a premium, which will not be repaid but kept for the collateral and liquidity providers who assumed the risk.
So, we can formulate the following equation of
b, whose value is known from solving Equation (
3):
Clearing the
variable:
In summary, we have the following values on Equation (
6):
: variable to calculate.
b: calculated from Equation (
3) since
f and
q are known.
q: known since it is the amount to be collateralized.
: known as an invoice parameter.
2.3. Illustrative Example
Firs, the rkAMM initial condition is presented in
Table 2.
Then, an invoice that has a
p collateral and is demanding
q over the total amount is applying for the rkAMM service. This scenario is contemplated in
Table 3.
Using Equation (
4), the value of
f is:
Since .
Then, from Equation (
3), the value of
b is:
Recall that is proportional but essentially different from q because with p, q, and b and a, we are working with probabilities and ratios.
From Equation (
5), we have:
Clearing premium from the previous equation as in Equation (
6):
Finally, the rkAMM goes on as follows and the intermediate situation can be seen in
Table 4.
At this point, collateral is withdrawn from the pool and has been deposited. What will happen if the payer does not repay the invoice will be matter of study with several scenarios that will be covered in the next section.
So, following this example, at some point, the user or his client will repay the collateral, which is EUR 800. Finally, the rkAMM situation is shown in
Table 5:
The rkAMM has made a profit because it has assumed the risk by supporting the non-collateralized amount of the invoice for some time in between the collateral provided by the rkAMM; the collateral is later repaid at the invoice due date, sooner or later.
3. Simulations Setup
A set of simulations have been developed based on five scenarios to study typical situations that may occur. Invoices used in the scenarios have the structure shown in
Table 6:
Key attributes such as invoice amounts or the percentages of collateral or nonpayment are modified at each scenario to analyze the behavior of the rkAMM. The complete set of attributes used to simulate the scenarios is shown in
Table 7.
In this research, neither predictive nor classification models are used, since the rkAMM does not need to predict future behavior of invoice sets and does not need to classify them. Simulations only intend to study the final outcome of the rkAMM based on sets of invoices generated randomly through uniform distribution.
At every scenario, many sets (from 100 sets) of invoices are generated to obtain solid statistical ground.
3.1. Scenarios
The five scenarios for the simulations are:
Scenario 1—Here, we experiment with the growing contribution of collateral by liquidity providers (LP) on a growing rate of the volume of collateral (Q) in the rkAMM, in the pool. As the Probability of Contribution is fixed at 50% every day, the Range of Liquidity contribution is being experimented in three conditions: 1% of initial Q at every contribution for scenario 1.1 (Very Low), 5% of initial Q for case 1.2 (Low), 10% of initial Q for case 1.3 (Medium), and 25% of initial Q for case 1.4 (Max).
Scenario 2—Here, we experiment with sets of non-payments back to the rkAMM. The attribute changed in this scenario is the non-payment probability, in three cases: 2% of invoices for case 2.1 (Low), 5% for case 2.2 (Medium), and 20% for case 2.3 (Max).
Scenario 3—Here, we experiment with Increasing Delay in invoice payments. The payment period ranges from what is considered short to long. Payment period ranges are: 30–60 days for case 3.1 (Short), 60–90 days for case 3.2 (Medium), and 90–120 days for case 3.3 (Long).
Scenario 4—Here, we experiment with the to be collateralized, which will depend on a variable percentage of the initial volume of collateral () in the rkAMM. The Demanded collateral to the pool is in three cases: 1% of initial for case 4.1 (Low), 10% of initial for case 4.2 (Medium), and 25% of initial for case 4.3 (Max).
Scenario 5—Different % to be collateralized. This is slightly different from scenario 4, as here, we work with the percentage only and not with the amount to be collateralized. Although they are, of course, directly related, the sensitivity of the pool to the amount of collateral comes out with different outputs. The range of % collateral p of invoices is set to three cases. Range of % collateral p: 55% for case 5.1 (Low), 75% for case 5.2 (Medium), and 90% for case 5.3 (Max).
In addition to the scenarios proposed above, there is an additional set consisting of those situations in which there are malicious actors trying to take advantage of the rkAMM operation. These scenarios foresee a hack of the rkAMM; that is, there is a high number of false, bogus invoices. A false invoice is considered one for which the collateral given away by the rkAMM will never be paid back. The purpose of this hack from the attacker’s point of view is to drain the rkAMM liquidity.
Hack scenario—To hack the rkAMM, the following attributes from the default scenario are modified to produce a set of hacking cases:
Range of % from invoices to collateralize: 49% (Max), 30% (Medium), and 10% (Low)
Non-payment probability: 10% (Low), 50% (Medium), and 100% (Max) crossed with all the ranges of % from invoices to collateralize.
3.2. Technical Description of the Simulator
The simulator has been developed in Python. For the analysis and presentation of the experiment metrics, common analysis and data visualization libraries have been used.
The invoices have been structured in a list of dictionaries to execute the simulations. Each invoice is defined by a dictionary of seven keys and values, and this dictionary in turn occupies a position in a list of invoices.
Regarding the functions of the simulation, those that allow modification of the volumes of liquidity, collateral, and premium have been defined. In addition, a function has been developed to calculate the premium based on the requested collateral, as explained in
Section 2.2 of this document.
To implement the simulation, there is a main function that randomly generates a set of invoices based on the previously defined parameters in
Table 6. The flow of invoices is steady at one invoice per day of any random amount and collateral within the range of parameters described for the simulations in
Table 7. When they are accepted in the liquidity pool, then premium is contributed, and collateral is withdrawn on the same day. Otherwise, when they are not accepted, they are simply discarded, and the next day comes for the next invoice.
The simulation also performs daily synchronization of the liquidity contributions of random amounts in the range established by the parameters. The invoices that are repaid achieve this with a random day within a minimum number of days (often 30 days are chosen) and a maximum of 120 days. On the other hand, invoices that are not repaid are programmed for a delay large enough for a due date well after the simulation, with a maximum delay of 100,000, since Python 3 int does not have a maximum size and using math.inf may impact the efficiency of our code.
Then, the number of days for each simulation is the number of the stream of invoices (one invoice per day), plus the maximum delay of 120 days and an additional number of few extra days. For instance, for a stream of 500 invoices, a maximum delay of 120 days, and 30 extra days, the limit is days per simulation.
Every scenario is defined by the parameters mentioned in
Table 7. A batch of 100 simulations per scenario are run; thus, the metrics are calculated as an average per batch.
To simulate several scenarios of unpaid invoices, a random number of invoices will be chosen not to be repaid, so that they pay the premium to be accepted in the rkAMM and obtain collateral that is, however, never returned to the rkAMM. The rkAMM will try to compensate the losses by means of the premium, and we will see how resilient it is at the end of the run of all simulations.
The rkAMM also contemplates the possibility of withdrawing the premium collected: the withdrawal period and the premium percentage to be withdrawn can be set up.
Last, but not least, the hack of the system, consisting of extenuating the rkAMM by a flow of bogus invoices, is intentionally left unpaid. This is achieved by increasing the hack probability that is directly proportional to the non-payment probability of invoices.
3.3. Repository of the rkAMM
4. Results
Several batches of simulations of the behavior of the rkAMM based on the scenarios defined in
Section 3.1 of this document were performed. Each batch is a case in a scenario, and performances will be analyzed. The plots of the liquidity and the premium will be presented for the most relevant scenarios.
4.1. Limitations
As stated, in the event that the rkAMM does not have liquidity nor premium to collateralize an invoice, this invoice is discarded, a day passes through, and the next invoice will be evaluated. When the rkAMM regains the collateral granted to a former collateralized invoice or the amount to be collateralized for a new invoice is less than the available liquidity in the rkAMM, the invoice might be granted for collateralization.
In the simulations, the profit percentage shows the result of the rkAMM. This benefit will be distributed among those LPs that have deposited liquidity into the rkAMM, so it is expected that this will have an impact on the rkAMM profit.
After inspecting the scenarios, our proposal of the rkAMM implies that the invoice percentage to collateralize is advised to never be greater than 49% or lower than 5%.
4.2. Metrics
A set of metrics is defined to describe the behavior of the rkAMM and analyse the results of the simulations: plots of the volume of the rkAMM, the premium collected, the premium withdrawn, and the resulting liquidity as an addition of the volume and the remaining premium. To better understand the metrics,
Table 8 shows an example. At the end of a batch of 100 simulations of the three cases of scenario 5, we have the averaged measures.
The set of
Table 9,
Table 10,
Table 11,
Table 12,
Table 13 and
Table 14 show results for all scenarios, which will be discussed in the next section. The result plots are also presented for a better understanding of the results. To avoid overloading this section and to facilitate reading, only the plots from scenario 5 with a Premium withdrawal period of 30 days are presented, since it is considered the most relevant and frequent scenario to occur in the rkAMM deployment. The plots for the other scenarios are summarized in the
Appendix A section. The results on mean average over a 100 runs batch per every case and scenario are less than 0.7% standard error on the rkAMM profit measure. We think this is reasonably sound for backing the conclusions over the discussion of the results.
In addition to the scenarios results of the tables presented above and the curves from scenario 5 shown in
Figure 4, in the following
Figure 5 and
Figure 6, there is a comparative analysis of the rkAMM profit of all the scenarios.
Figure 5 shows a comparison between the rkAMM profit when there is no premium withdrawal, and when there is premium withdrawn but, depending on the frequency, the premium is withdrawn.
Figure 6 shows the rkAMM percentage of profit difference between scenarios in which the premium is withdrawn and where it is not. Premium withdrawal intervals are 1, 30 and 90 days.
One can see that the rkAMM profit is not affected by the premium withdrawal in the majority of the scenarios. It can even be concluded that the frequency with which the premium is withdrawn does not have a significant impact either, except for the scenarios in which the premium is withdrawn every day.
Surprisingly, only the daily premium withdrawal causes the rkAMM profit to be only a few points lower than the rkAMM profit when there is no premium withdrawal, while in the other scenarios with lower frequency (of +30 days), even the performance is boosted in some cases.
Figure 7 shows the overall profit of rkAMM taking into account all possible scenarios and premium withdrawal periods.
As in the other scenarios, besides the hack scenarios tables,
Figure 8 illustrates the curves of that simulation.
Figure 9 shows that practically one-third of the scenarios is affected to a greater extent by the premium withdrawal, and therefore the rkAMM profit is altered. Further, this impact turns out to be positive and the performance of the AMM for this set of scenarios is better when premium is withdrawn periodically, especially with invoices collateralized at 51%. The best cases are those in which the invoices are collateralized at 51%, although the rkAMM profit decreases as the hack probability increases.
As for the percentage difference with respect to withdrawing premium or not shown in
Figure 10, the scenarios in which premium is withdrawn every 30 days with 51% collateralized invoices present an improvement of 5%, 89% and 249% with hacking probabilities of 10%, 50%, and 100%, respectively. Regarding daily withdrawals, the only favorable case is found when invoices are collateralized at 51% with a hacking probability of 10%. Finally, for premium withdrawals every 90 days, the most remarkable case is that in which invoices are collateralized at 51%, with a hack probability of 50%. The rest of the scenarios have presented a worse performance when there is a periodic premium withdrawal.
All of the above is summarized in
Figure 11 where it can be seen the overall profit of rkAMM taking into account all possible scenarios and premium withdrawal periods.
5. Withdrawn Premium Analysis
In this section, a detailed analysis of the results of the previous section is carried out.
First, it must be taken into account that the rkAMM also grants collateral of invoices from the premium if it does not have sufficient liquidity. This happens for all scenarios and positively affects both the final premium values and the total volume of the rkAMM.
Considering the results, the more adverse the scenario, the lower the premium withdrawn from the rkAMM will be. The same happens with the remaining premium in the rkAMM: the worse the scenario, the lower the amount available. This is because the rkAMM will try to collateralize with the premium due to lack of liquidity, which is expected behavior in adverse scenarios. However, this general rule has some exceptions.
Scenario 1: The greater the increase in liquidity shows nearly a 100% match of the results when no premium is withdrawn.
As liquidity increases, the difference rises from an approximate −50% to a −1% difference on accepted/paid invoices increases. In all cases, all collateralized invoices are paid.
When there is a greater liquidity contribution, the total covered is increased. However, in the worst case of liquidity contribution (scenario 1.1), there is a 60% difference in terms of the total collateral covered. This difference is drastically reduced in the 1.4 case, where it is only 1%.
Concerning the premium managed by the rkAMM in these cases, it is increasing as more liquidity is provided, which was to be expected, given that a larger number of invoices are collateralized.
Regarding the benefit of the rkAMM, the greater the contribution of liquidity, the greater the profit rkAMM. However, the withdrawal of premium does not affect the benefit of the premium by itself, since there are scenarios in which premium is withdrawn and a larger benefit is obtained (even if only 1%) than those in which there is no withdrawal of premium. This is because in cases where there is no premium withdrawal, less premium is collected than in the cases where premium is withdrawn.
Scenario 2: Facing an increase in unpaid invoices, the scenarios with premium withdrawal and those without have the same shape, although the absolute values are affected and the results are worse in the cases of the highest numbers of unpaid invoices.
The number of collateralized invoices decreases. The same happens for the amount of collateral covered and the rkAMM profit.
Regarding the losses resulting from unpaid invoices, the relationship between scenarios is maintained despite the increase in the number of these invoices.
Scenario 3: The larger the delay in the payment of the invoices, the lower the premium that can be withdrawn and the lower the remaining premium in the case where the premium is not withdrawn. The shorter the payment term, the better the liquidity of the rkAMM.
The number of collateralized invoices will be lower, but the relationship between the scenarios with premium withdrawal and those without is variable, and it worsens in the scenarios where there are greater delays in the invoice payments. The same happens for the amount of collateral covered.
The rkAMM profit is lower, along with a growing delay in the payment of invoices.
Scenario 4: The greater the amount to be collateralized, the better the results of the rkAMM are in terms of its performance, since more liquidity is collateralized. Therefore, a higher premium is obtained and the larger the benefit of the rkAMM. In summary, better results are achieved the higher the risk assumed by rkAMM.
The number of collateralized invoices decreases, but the relationship between the scenarios with premium withdrawal and those without is variable, and it worsens in scenarios in which there are increasingly large invoices (of larger amounts). Despite the fact that the collateral is covered and the rkAMM profit increases, the two scenarios have the same behavior.
Scenario 5: Same pattern as scenario 4. The higher the percentage to be collateralized, the worse the results of the rkAMM. It can also be determined that the higher the percentage of collateralization of the invoices, the more similar the results between scenarios where premium is withdrawn and where it is not.
The number of collateralized invoices decreases; however, the relationship between the scenarios in which premium is withdrawn and those in which it is not decreases until it is almost equal to the scenario in which the invoices are almost completely collateralized. The same happens for the amount of collateral covered and profit rkAMM as the amount to be collateralized increases.
Hack Scenario: The larger the hack probability and the amount to collateralise, the worse the results of the AMM in terms of its performance. However, in some cases, premium withdrawal performs better in terms of AMM profit for withdrawal periods of 30 and 90 days.
Losses due to unpaid invoices, as expected, increase as the probability of hacking increases. On the contrary, the amount of collateral covered decreases as the probability of hacking and the amount to be collateralized increases. The same happens for the profit rkAMM.
Finally, as a conclusion to this section:
Withdrawing the premium can give better results in scenarios with larger liquidity (those with less payment terms or more liquidity contribution) and with higher risk (fewer guarantees or larger defaulting).
Thus, we find ourselves with an “aseptic” measure, withdrawing the benefits to improve the performance of rkAMM. The policy of premium withdrawal affects the design and performance of the rkAMM, and the following could be recommended:
- 1.
Not sharing profits (i.e., not having any premium withdrawal) is not an adequate policy for the operation of the rkAMM.
- 2.
Make a withdrawal variable policy based on liquidity, defaulting, and payment terms.
Additionally, distributing benefits early is expected to have a bandwagon effect on the demand for rkAMM products with more and more liquidity providers.
DeFi and rkAMM aim to automate as much as possible through smart contracts, but this approach has introduced or increased risks, as noted in [
38]. However, rkAMM premium collection/withdrawal solutions offer a solution that provides additional trust without the need for any rating or scoring, thanks to the involvement of byppay.
6. Discussion
The following comments and considerations relate to the six scenarios analyzed in terms of parameters other than benefits: the impact on accepted invoices, unpaid invoices, average losses, collateral covered, and remaining and withdrawn premium. The comments apply to both premium withdrawal and non-withdrawal cases.
The rkAMM can accept more invoices if the liquidity stream flows into the LP with constant contribution probability (scenario 1). Otherwise, if there is no liquidity stream, the rkAMM liquidity gradually depletes, and it collateralizes invoices using the remaining premium until liquidity is replenished with premium or invoices are repaid. The best results for the number of accepted invoices are seen in scenarios in which there are small invoices or there are invoices with a high percentage to be collateralized.
Only scenario 2 shows positive results regardless of unpaid invoices, as unpaid invoices are intentionally included to be processed by the rkAMM. Hack scenarios result in losses, and these losses increase significantly when the invoice amount to be collateralized is greater.
The highest values of collateral covered are achieved in scenarios in which the LPs provide liquidity contributions, allowing the rkAMM more resources to cover collateral. However, the values of collateral covered obtained do not generally reach the values described in scenario 1. Similar collateral coverage values are achieved for cases 3.1 and 5.1 when there is no premium withdrawal.
Scenarios with greater collateral coverage result in a greater amount of premium withdrawn. The fact of making premium withdrawals in increasingly longer periods means that the premium withdrawn is lower. When there is no premium withdrawal, the remaining premium is in constant circulation and is used for collateralizing invoices.
All scenarios, except for some hacking ones, achieve a positive profit. The scenarios with the best performance in average (more profit, more invoices funded) are the ones where premium is withdrawn every 30 days.
In the case of hack scenarios, the rkAMM is resilient and can withstand an attack in scenarios with a small hack probability and a low percentage of invoice collateralization, specifically from 49% to a maximum of 30%. The scenarios in which the premium is withdrawn every 30 or 90 days with a 100% probability of hacking when the invoices are 51% collateralized are also resilient.
The optimal attack is to send bogus invoices with the highest percentage to collateralize, which is 90% in our experiments. It is worth noting that mechanisms such as checking invoices, enhancing KYC, and retaining collateral in custody could resist the hack by imposing a penalty of collateral loss. Further research is needed to investigate these mechanisms.
As future work, withdrawing profit from the rkAMM without harming its operation and long-term sustainability needs to be explored further in future research as well as calculate more exhaustively the optimal ranges of collateral and withdrawal policies, develop self tuning algorithms for demanded collateral and withdrawal policy for restoring resilience against hacks, and research into z-discrete formulations of the dynamics of the liquidity pool to stabilize the risk and volume of the rkAMM with our without using newly developed stable-coins for invoice discounting and the highest resilience of the state of the art.
Comparison with the State of the Art
Comparing our solution to the state of the art, we have the following benefits:
- 1.
Undercollateralization: The premium in cases in which the invoice has collateral of 49% is lower than the remaining 51% of the invoice amount, very different from the common overcollateralization required in the state of the art [
26,
27,
28,
29]. This is because the other Lending Pools lock a pair of tokens, a loanable token, and a collateral token. Lenders earn interest rates based on the supply and demand of the provided liquidity. However, as there is no guarantee of repayment, borrowers of those pools must over-collateralize their position.
- 2.
Risk measure: This is the only liquidity pool in state of the art that uses the Kelly criterion, which measures and mitigates the risk.
- 3.
Resiliency: This is the first exhaustive study of resiliency in the state of the art, with several cases in the hack scenarios of bogus invoices and many cases in the scenarios of non payment or growing delay in due time.
- 4.
Less demanding KYC: There is less need for KYC when a pool is accepting invoices from a byppay, as the byppay collects the collateral from the three parties that know each other in a byppay agreement. It is a great advantage to the Liquidity pools of the state of the art.
- 5.
Yet more decentralized: As a ancillary benefit, our solution does not require all invoices to be uploaded on the chain for their PoE, as [
22] that use blockchain to enhance the PoE, but only those involved in a byppay.
7. Conclusions
Our work is significant because we have developed liquidity pools or PLF that do not require over-collateralized assets. In our approach, invoices are only partly collateralized, with a portion consisting of pure collateral and a premium calculated using the reverse Kelly formula. Thus, this collateral and premium do not cover the full value of the invoice. Despite this, our unique approach, which uses the optimal return calculated by the Kelly criterion, does not result in losses, even when there is a 20% chance of non-payment.
To ensure proper operation of our rkAMM, we conducted experiments to fine-tune it. Our findings suggest that the optimal operation mode of our rkAMM involves invoices of collateral p over 50–70%, which provides strong resilience even in scenarios of up to 10% bogus invoices, 30–120 days of due time delay, and 5% non-payment. In addition, we recommend an approach with periodic withdrawals of 30 days in the event of a premium withdrawal policy. This approach benefits the acceptance and viability of the rkAMM by allowing LP to receive partial returns in advance, despite the risks and liquidity needs of the rkAMM.
Under these conditions, it may be possible to incorporate mechanisms of PoE to verify bogus invoices or double factor invoicing on the blockchain to work alongside our rkAMM, such as crowd collateralization, verifiable credentials, on-chain scoring, or own byppay referral among groups of three actors. It is true that, despite the resilience of the rkAMM, it should not be left on its own without proper protection, as it only buys time to detect any attack or hack, and a fraction of collateral is still necessary as the stake that hackers will lose when detected.
Furthermore, the rkAMM was originally designed to operate with invoices from byppay.com, as it is a negotiation system for invoice compensation, where trust among players who invoice each other is sound for the needs of the rkAMM, which lowers hacking possibilities. Other hack-hostile systems that the rkAMM might work with are other debt compensation systems, including Netting or Barter clubs such as RES.be, Wir.ch, or Sardex.it, as they all curate invoices properly with partial payments in their complementary currencies that might work similarly to collateral.
Based on our experiences with several hack scenarios, we recommend that the percentage of invoice collateralization with our rkAMM should never exceed 49% or be lower than 5%.