Neural Attractor-Based Adaptive Key Generator with DNA-Coded Security and Privacy Framework for Multimedia Data in Cloud Environments
Abstract
1. Introduction
2. Related Works
- Neural–DNA–chaos permutation-based image encryption.
- Adaptive key generation based on plain image.
- Neural-based confusion of grey image.
- Establishment of a public cloud interface with the security framework.
- Validation of user authenticity to access the cloud-ciphered image.
- Improved protection for image sharing in multimedia communication.
3. Pre-Requisites
3.1. DNA Approach
3.2. Chaotic System
The Suitability of Chaotic Sequences for the Image Encryption Algorithm
3.3. Hyperchaotic HNN
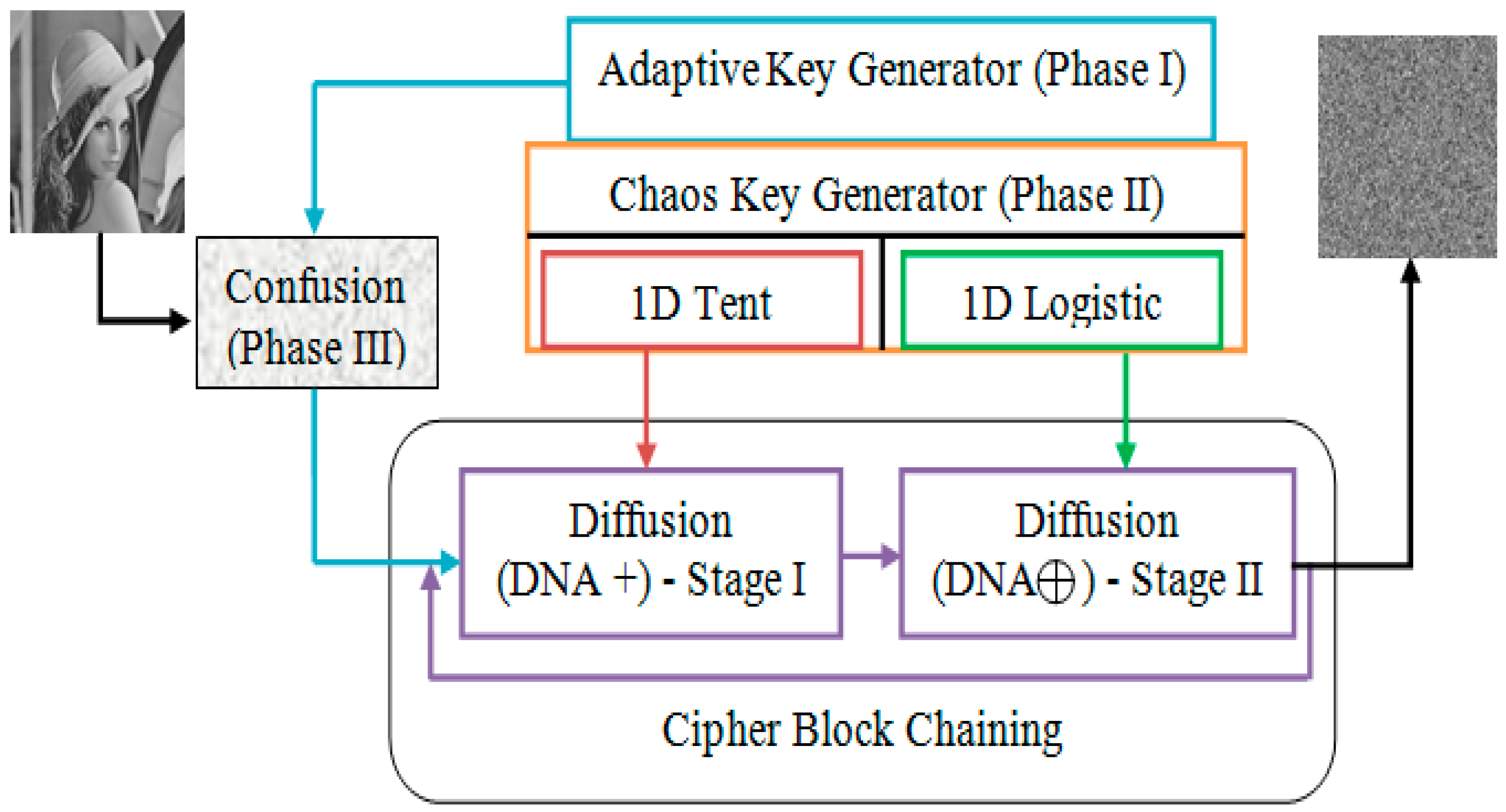
4. Proposed Approach
4.1. Image Ciphering and Deciphering Process
| Algorithm 1: Adaptive random sequence generation using discrete Hopfield attractor |
| Input: Multiplicative identity matrix (Β)[4,4], sampling rate Tw, random initiator h[1,4] Output: Nonlinear random sequence Ω Initialise wij ← [w w/2 σ − w; Ψ 2w 3w 0; 3w ϕ w 0; mw 0 0 nw] ← [1 0.5 −5 −1; −0.37 2 3 0; 3 −13 1 0; 100 0 0 170] Update the wij with new σ, Ψ, ϕ Get H(0) ← [h]T Repeat Set r ← r + 1 Until r ≤ (Image size/4) Initialise Ω ← {} for f ← 1 to 16,384 for i ← 1 to 4 Ω ((4 × (f − 1)) + i) = Dh(i) end end Return (Ω) |
| Algorithm 2: Chaos key generator |
| Input: Initial parameters (KLD(0), KT(0)) control parameters (γ, μ) and image size N 3.4 ≤ α2 ≤ 4; 0 ≤ γ ≤ 2; 0 ≤ KLD(0) and KT(0) ≤ 1 Output: Chaos sequence KLDM and KTM as key for size N and DNA rule selectors R1, R2 1D tent map-based sequence as key for Diffusion I Initialise KTM = { }; θ = 1/2 for i ← 1 to N do if KT(i − 1) ≥ θ then Set KT(i) ← (μ × (1 − KT(i − 1))) else Set KT(i) ← (μ × KT(i − 1)) Set KTM(i) ← mod (KT × 1014, 256) end Return (KTM) 1D logistic map-based sequence as key for Diffusion II Set KLD(1) ← (γ × KLD(0)) × (1 − KLD(0)) Initialise KLDM = { } for i ← 2 to N do Set KLD(i) ← (γ × KLD(i −1)) × (1- KLD(i − 1)) Set KLDM(i) ← mod (KLD × 1014, 256) end Return (KLDM) |
| Algorithm 3: Image encryption—Hopfield based permutation |
| Input: Original image I of size (X) [M, N], Nonlinear random sequence Ω Output: Scrambled image matrix C Get where R is the ascending order of key stream ; ∀ is the index of the sorted key stream Repeat Set Set j ← j + 1 Until j < (M × N) Return (C) |
| Algorithm 4: Image encryption—cipher block chaining process |
| Input: Shuffled image C, Key sequences KTM, KLDM, rule for DNA encoding R1, R2 and 8-bit secret key K1 Output: Encrypted image E Set E(1) ← C(1) ⊕ K1 for i← 2 to N do Cd(i) ← C(i) ⊕ E(i − 1) Diffusion Stage I: Set CdDNA(i) DNAEncode (Cd(i)) Set KTMDNA(i) DNAEncode (KTM(i)) Set List ← [0, 2, 4, 6] for j ← 1 to 4 do Set n ← List[j] Set Cd1(i)[n:n + 1] ← mod ((CdDNA(i) [n:n + 1] + KTMDNA (i) [n:n + 1]), 4); end Diffusion Stage II: Set Cd1DNA(i) DNAEncode (Cd1(i)) Set KLDMDNA(i) DNAEncode (KLDM(i)) Set List ← [0, 2, 4, 6] for j ← 1 to 4 do Set n ← List[j] Set E(i)[n:n + 1] ← Cd1DNA (i) [n:n + 1] ⊕ KLDMDNA (i) [n:n + 1] end end Return (E) |
| Algorithm 5: Authenticated cloud access process |
| Input: Encrypted image E of size X, login credentials of AWS, identity and access management (IAM) key pairs Output: Uploaded encrypted image E in the cloud storage Set AWS login credentials: username ← “username” and password←“password” Set IAM key pairs: access key ← “AAAAAAA” and secret key ← “SSSSSSS” if (username = “username” && password = “password”) then if (access key = “AAAAAAA” && secret key = “SSSSSSS”) then captcha = randomgen (captcha) and user expect to type it on the screen if captcha matched then Access = “Access Granted” Push S3: Bucket ← Encrypted images else Return (“Invalid CAPTCHA”) else Return (“Invalid Credentials”) else Return (Access = “Access Denied”) |
| Algorithm 6: Image decryption—cipher block chaining process |
| Input: Encrypted image of size (E) [M, N], key sequences KTM, KLDM, rule for DNA encoding R1, R2 and 8-bit secret key K1 Output: Shuffled image C Diffusion Stage I: Set EDNA(i) DNAEncode (E(i)) Set KLDMDNA(i) DNAEncode (KLDM(i)) Set List ← [0, 2, 4, 6] for j ← 1 to 4 do Set n ← List[j] Set Cd1(i)[n:n + 1] ← EDNA (i) [n:n + 1] ⊕ KLDMDNA (i) [n:n + 1] end Diffusion Stage II: Set Cd1DNA(i) DNAEncode (Cdi(i)) Set KTMDNA(i) DNAEncode (KTM(i)) Set List ← [0, 2, 4, 6] for j ← 1 to 4 do Set n ← List[j] Set Cd(i)[n:n + 1] ← mod ((Cd1DNA (i) [n:n + 1] − KTMDNA (i) [n:n + 1]), 4) end Set C(1) ← Cd(1) ⊕ K1 for i ← 2 to N do Set C(i) ← Cd(i) ⊕ Cd(i − 1) end Return (C) |
| Algorithm 7: Image decryption—Hopfield-based reassembling |
| Input: Scrambled image matrix C of size (X) [M, N], nonlinear random sequence Ω Output: Original image I Get [R, A] ← sort (Ω, “ascend”) where R is the ascending order of key stream ; A is the index of the sorted key stream Repeat Set I (A(j)) ← C(j) Set j ← j + 1 Until j < (M × N) Return (I) |
4.2. Security Framework Interface with Public Cloud
5. Results and Discussion
5.1. Brute Force Attack
5.1.1. Keyspace Analysis
5.1.2. Key Sensitivity Analysis
5.2. Statistical Attack Analysis
5.2.1. Histogram Analysis
5.2.2. Neighbouring Pixel Correlation Analysis
5.2.3. Information Entropy
5.3. Encryption Quality Analysis
5.3.1. Chi-Square Test
5.3.2. Histogram Maximum Deviation
5.3.3. Irregular Deviation
5.3.4. Deviation from Ideality
5.4. Chosen Plaintext Attack
5.5. Bit Distribution Analysis at Plane Level
5.6. Computational Complexity
5.7. Discussion
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Singh, A.; Chatterjee, K. Cloud security issues and challenges: A survey. J. Netw. Comput. Appl. 2017, 79, 88–115. [Google Scholar] [CrossRef]
- Yang, R.; Xu, Q.; Au, M.H.; Yu, Z.; Wang, H.; Zhou, L. Position based cryptography with location privacy: A step for Fog Computing. Future Gener. Comput. Syst. 2018, 78, 799–806. [Google Scholar] [CrossRef]
- Shahzadi, S.; Iqbal, M.; Dagiuklas, T.; Qayyum, Z.U. Multi-access edge computing: Open issues, challenges and future perspectives. J. Cloud Comput. 2017, 6, 30. [Google Scholar] [CrossRef]
- Huh, J.H.; Seo, Y.S. Understanding edge computing: Engineering evolution with artificial intelligence. IEEE Access 2019, 7, 164229–164245. [Google Scholar] [CrossRef]
- Eom, S.; Huh, J.H. The opening capability for security against privacy infringements in the smart grid environment. Mathematics 2018, 6, 202. [Google Scholar] [CrossRef]
- Tao, M.; Ota, K.; Dong, M. Ontology-based data semantic management and application in IoT- and cloud-enabled smart homes. Future Gener. Comput. Syst. 2017, 76, 528–539. [Google Scholar] [CrossRef]
- Asadi, S.; Nilashi, M.; Husin, A.R.C.; Yadegaridehkordi, E. Customers perspectives on adoption of cloud computing in banking sector. Inf. Technol. Manag. 2017, 18, 305–330. [Google Scholar] [CrossRef]
- Singh, S.; Jeong, Y.S.; Park, J.H. A survey on cloud computing security: Issues, threats, and solutions. J. Netw. Comput. Appl. 2016, 75, 200–222. [Google Scholar] [CrossRef]
- Kumari, M.; Gupta, S.; Sardana, P. A Survey of Image Encryption Algorithms. 3D Res. 2017, 8, 37. [Google Scholar] [CrossRef]
- Wang, B.; Xie, Y.; Zhou, C.; Zhou, S.; Zheng, X. Evaluating the permutation and diffusion operations used in image encryption based on chaotic maps. Optik 2016, 127, 3541–3545. [Google Scholar] [CrossRef]
- Alsaedi, M. Colored image encryption and decryption using multi-chaos 2D quadratic strange attractors and matrix transformations. Multimed. Tools Appl. 2017, 76, 24527–24547. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Pun, C.M.; Chen, C.L.P. 2D Sine Logistic modulation map for image encryption. Inf. Sci. 2015, 297, 80–94. [Google Scholar] [CrossRef]
- Diaconu, A.V. Circular inter-intra pixels bit-level permutation and chaos-based image encryption. Inf. Sci. 2016, 355–356, 314–327. [Google Scholar] [CrossRef]
- Ponuma, R.; Amutha, R. Compressive sensing based image compression-encryption using novel 1D-chaotic map. Multimed. Tools Appl. 2018, 77, 19209–19234. [Google Scholar] [CrossRef]
- Abbas, N.A. Image encryption based on Independent Component Analysis and Arnold’s Cat Map. Egypt. Inform. J. 2016, 17, 139–146. [Google Scholar] [CrossRef]
- Wang, X.; Liu, L.; Zhang, Y. A novel chaotic block image encryption algorithm based on dynamic random growth technique. Opt. Lasers Eng. 2015, 66, 10–18. [Google Scholar] [CrossRef]
- Belazi, A.; Abd El-Latif, A.A.; Belghith, S. A novel image encryption scheme based on substitution-permutation network and chaos. Signal Process. 2016, 128, 155–170. [Google Scholar] [CrossRef]
- Huang, X.; Ye, G. An image encryption algorithm based on irregular wave representation. Multimed. Tools Appl. 2018, 77, 2611–2628. [Google Scholar] [CrossRef]
- Broumandnia, A. Designing digital image encryption using 2D and 3D reversible modular chaotic maps. J. Inf. Secur. Appl. 2019, 47, 188–198. [Google Scholar] [CrossRef]
- Duan, C.F.; Zhou, J.; Gong, L.H.; Wu, J.Y.; Zhou, N.R. New color image encryption scheme based on multi-parameter fractional discrete Tchebyshev moments and nonlinear fractal permutation method. Opt. Lasers Eng. 2022, 150, 106881. [Google Scholar] [CrossRef]
- Zhang, Q.; Liu, L.; Wei, X. Improved algorithm for image encryption based on DNA encoding and multi-chaotic maps. AEU Int. J. Electron. Commun. 2014, 68, 186–192. [Google Scholar] [CrossRef]
- Wang, X.Y.; Zhang, Y.Q.; Bao, X.M. A novel chaotic image encryption scheme using DNA sequence operations. Opt. Lasers Eng. 2015, 73, 53–61. [Google Scholar] [CrossRef]
- Hu, T.; Liu, Y.; Gong, L.H.; Guo, S.F.; Yuan, H.M. Chaotic image cryptosystem using DNA deletion and DNA insertion. Signal Process. 2017, 134, 234–243. [Google Scholar] [CrossRef]
- Chai, X.; Chen, Y.; Broyde, L. A novel chaos-based image encryption algorithm using DNA sequence operations. Opt. Lasers Eng. 2017, 88, 197–213. [Google Scholar] [CrossRef]
- Enayatifar, R.; Abdullah, A.H.; Isnin, I.F.; Altameem, A.; Lee, M. Image encryption using a synchronous permutation-diffusion technique. Opt. Lasers Eng. 2017, 90, 146–154. [Google Scholar] [CrossRef]
- Wang, S.; Peng, Q.; Du, B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt. Laser Technol. 2022, 148, 107753. [Google Scholar] [CrossRef]
- Alarood, A.A.; Alsolami, E.; Al-Khasawneh, M.A.; Ababneh, N.; Elmedany, W. IES: Hyper-chaotic plain image encryption scheme using improved shuffled confusion-diffusion. Ain Shams Eng. J. 2022, 13, 101583. [Google Scholar] [CrossRef]
- Zhou, W.; Wang, X.; Wang, M.; Li, D. A new combination chaotic system and its application in a new Bit-level image encryption scheme. Opt. Lasers Eng. 2022, 149, 106782. [Google Scholar] [CrossRef]
- Pavithran, P.; Mathew, S.; Namasudra, S.; Srivastava, G. A novel cryptosystem based on DNA cryptography, hyperchaotic systems and a randomly generated Moore machine for cyber physical systems. Comput. Commun. 2022, 188, 1–12. [Google Scholar] [CrossRef]
- Yousif, S.F.; Abboud, A.J.; Alhumaima, R.S. A new image encryption based on bit replacing, chaos and DNA coding techniques. Multimed. Tools Appl. 2022, 81, 27453–27493. [Google Scholar] [CrossRef]
- Qin, Z.; Weng, J.; Cui, Y.; Ren, K. Privacy-Preserving Image Processing in the Cloud. IEEE Cloud Comput. 2018, 5, 48–57. [Google Scholar] [CrossRef]
- Chidambaram, N.; Raj, P.; Thenmozhi, K.; Rajagopalan, S.; Amirtharajan, R. A cloud compatible DNA coded security solution for multimedia file sharing & storage. Multimed. Tools Appl. 2019, 78, 33837–33863. [Google Scholar]
- Zhang, Y.; He, Q.; Xiang, Y.; Zhang, L.Y.; Liu, B.; Chen, J.; Xie, Y. Low-Cost and Confidentiality-Preserving Data Acquisition for Internet of Multimedia Things. IEEE Internet Things J. 2018, 5, 3442–3451. [Google Scholar] [CrossRef]
- Bigdeli, N.; Farid, Y.; Afshar, K. A robust hybrid method for image encryption based on Hopfield neural network. Comput. Electr. Eng. 2012, 38, 356–369. [Google Scholar] [CrossRef]
- Lakshmi, C.; Thenmozhi, K.; Rayappan, J.B.B.; Amirtharajan, R. Hopfield attractor-trusted neural network: An attack-resistant image encryption. Neural Comput. Appl. 2020, 32, 11477–11489. [Google Scholar] [CrossRef]
- Lakshmi, C.; Thenmozhi, K.; Venkatesan, C.; Seshadhri, A.; Rayappan, J.B.B.; Amirtharajan, R. Mutated cleavages of images for stealth disclosure: A hopfield neural network attractor (HNNA) approach. Neural Process. Lett. 2021, 53, 907–928. [Google Scholar] [CrossRef]
- Lakshmi, C.; Thenmozhi, K.; Rayappan, J.B.B.; Rajagopalan, S.; Amirtharajan, R.; Chidambaram, N. Neural-assisted image-dependent encryption scheme for medical image cloud storage. Neural Comput. Appl. 2021, 33, 6671–6684. [Google Scholar] [CrossRef]
- Dhall, S.; Pal, S.K.; Sharma, K. A chaos-based probabilistic block cipher for image encryption. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 1533–1543. [Google Scholar] [CrossRef]
- Patel, S.; Thanikaiselvan, V.; Pelusi, D.; Nagaraj, B.; Arunkumar, R.; Amirtharajan, R. Colour image encryption based on customised neural network and DNA encoding. Neural Comput. 2021, 33, 14533–14550. [Google Scholar] [CrossRef]
- Jiang, Z.; Liu, X. Image Encryption Algorithm Based on Discrete Quantum Baker Map and Chen Hyperchaotic System. Int. J. Theor. Phys. 2023, 62, 22. [Google Scholar] [CrossRef]
- Wang, W.T.; Sun, J.Y.; Zhang, H.; Zhang, J. Quantum cryptosystem and circuit design for color image based on novel 3D Julia-fractal chaos system. Quantum Inf. Process. 2023, 22, 64. [Google Scholar] [CrossRef]
- Wang, H.K.; Xu, G.B.; Jiang, D.H. Quantum grayscale image encryption and secret sharing schemes based on Rubik’s Cube. Physica A Stat. Mech. Its Appl. 2023, 612, 128482. [Google Scholar] [CrossRef]
- Hao, W.; Zhang, T.; Chen, X.; Zhou, X. A hybrid NEQR image encryption cryptosystem using two-dimensional quantum walks and quantum coding. Signal Process. 2023, 205, 108890. [Google Scholar] [CrossRef]
- Mahalingam, H.; Veeramalai, T.; Menon, A.R.; S., S.; Amirtharajan, R. Dual-Domain Image Encryption in Unsecure Medium—A Secure Communication Perspective. Mathematics 2023, 11, 457. [Google Scholar] [CrossRef]
- Zhu, S.; Deng, X.; Zhang, W.; Zhu, C. Image Encryption Scheme Based on Newly Designed Chaotic Map and Parallel DNA Coding. Mathematics 2023, 11, 231. [Google Scholar] [CrossRef]
- Song, X.; Chen, G.; Abd El-Latif, A.A. Quantum Color Image Encryption Scheme Based on Geometric Transformation and Intensity Channel Diffusion. Mathematics 2022, 10, 3038. [Google Scholar] [CrossRef]
- Zhong, H.; Li, G.; Xu, X.; Song, X. Image Encryption Algorithm Based on a Novel Wide-Range Discrete Hyperchaotic Map. Mathematics 2022, 10, 2583. [Google Scholar] [CrossRef]
- Mansoor, S.; Sarosh, P.; Parah, S.A.; Ullah, H.; Hijji, M.; Muhammad, K. Adaptive Color Image Encryption Scheme Based on Multiple Distinct Chaotic Maps and DNA Computing. Mathematics 2022, 10, 2004. [Google Scholar] [CrossRef]
- Mfungo, D.E.; Fu, X.; Wang, X.; Xian, Y. Enhancing Image Encryption with the Kronecker xor Product, the Hill Cipher, and the Sigmoid Logistic Map. Appl. Sci. 2023, 13, 4034. [Google Scholar] [CrossRef]
- Chen, C.; Zhu, D.; Wang, X.; Zeng, L. One-Dimensional Quadratic Chaotic System and Splicing Model for Image Encryption. Electronics 2023, 12, 1325. [Google Scholar] [CrossRef]
- Chen, X.; Wang, Q.; Fan, L.; Yu, S. A Novel Chaotic Image Encryption Scheme Armed with Global Dynamic Selection. Entropy 2023, 25, 476. [Google Scholar] [CrossRef] [PubMed]
- Chang, H.; Wang, E.; Liu, J. Research on Image Encryption Based on Fractional Seed Chaos Generator and Fractal Theory. Fractal Fract. 2023, 7, 221. [Google Scholar] [CrossRef]
- Zhao, J.; Wang, S.; Zhang, L. Block Image Encryption Algorithm Based on Novel Chaos and DNA Encoding. Information 2023, 14, 150. [Google Scholar] [CrossRef]








| Binary Stream (DNA Rules) | 00 | 01 | 10 | 11 |
|---|---|---|---|---|
| I | A | C | G | T |
| II | A | G | C | T |
| III | T | G | C | A |
| IV | T | C | G | A |
| V | C | A | T | G |
| VI | C | T | A | G |
| VII | G | A | T | C |
| VIII | G | T | A | C |
| Test Images | Method | Correlation Direction | ||
|---|---|---|---|---|
| Horizontal | Vertical | Diagonal | ||
| Lena | Plain | 0.9106 | 0.9507 | 0.8849 |
| Proposed | 0.0003 | 0.0042 | −0.0049 | |
| Ref. [12] | 0.0011 | 0.0098 | −0.0227 | |
| Ref. [13] | 0.00352 | 0.00648 | 0.00355 | |
| Ref. [16] | −0.0066 | −0.0089 | 0.0424 | |
| Ref. [17] | −0.0048 | −0.0112 | −0.0045 | |
| Ref. [19] Arnold Cat Map | 0.0003 | 0.0145 | 0.0841 | |
| Ref. [19] 2D Modular Chaotic Map | 0.0287 | 0.0217 | 0.0179 | |
| Ref. [19] 3D Modular Chaotic Map | 0.0269 | 0.0038 | 0.0094 | |
| Ref. [25] | 0.0023 | 0.0019 | 0.0011 | |
| Ref. [28] | 0.0028 | −0.0027 | −0.0032 | |
| Ref. [39] | −0.0287 | 0.0071 | 0.0007 | |
| Ref. [40] | 0.0054 | −0.0073 | 0.0021 | |
| Ref. [41] | − 0.0126 | − 0.0048 | 0.0054 | |
| Ref. [42] | 0.0070 | −0.0180 | −0.0033 | |
| Ref. [43] | −0.0042 | -0.0028 | 0.0027 | |
| Ref. [44] | −0.002153 | −0.0000901 | −0.0006059 | |
| Ref. [45] | 0.0090266 | −0.0059255 | 0.0055227 | |
| Ref. [46] | −0.0067 | −0.0038 | 0.0063 | |
| Ref. [47] | 0.001348 | 0.00016 | 0.002236 | |
| Ref. [48] | 0.0018 | 0.0028 | 0.0016 | |
| Ref. [49] | 0.0049 | −0.0022 | −0.0042 | |
| Ref. [50] | 0.0015 | −0.0021 | −0.0020 | |
| Ref. [51] | 0.0016 | −0.0034 | −0.0032 | |
| Ref. [52] | 0.0003 | −0.0021 | −0.0030 | |
| Ref. [53] | 0.000033 | −0.000295 | −0.000085 | |
| Baboon | Plain | 0.8423 | 0.8213 | 0.7408 |
| Proposed | 0.0050 | 0.0022 | −0.0048 | |
| Ref. [13] | 0.00083 | 0.00660 | 0.00159 | |
| Ref. [14] | 0.0003 | −0.0162 | 0.0134 | |
| Ref. [25] | 0.0059 | 0.0041 | 0.0028 | |
| Cameraman | Plain | 0.9303 | 0.9590 | 0.9048 |
| Proposed | −0.0055 | 0.0073 | −0.0072 | |
| Ref. [12] | −0.0047 | −0.0195 | 0.0279 | |
| Ref. [13] | 0.00954 | 0.01908 | 0.00568 | |
| Ref. [16] | 0.0063 | −0.0142 | 0.0168 | |
| Ref. [17] | −0.0095 | −0.0170 | −0.0119 | |
| Ref. [25] | 0.0198 | 0.0132 | 0.0032 | |
| Barbara | Plain | 0.8319 | 0.9483 | 0.7880 |
| Proposed | −0.0072 | 0.0002 | 0.0088 | |
| Ref. [12] | −0.0187 | −0.0016 | 0.0001 | |
| Ref. [16] | −0.0212 | −0.0161 | −0.0110 | |
| Ref. [17] | −0.0033 | −0.0269 | −0.0121 | |
| House | Plain | 0.9782 | 0.9529 | 0.9361 |
| Proposed | 0.0062 | −0.0014 | 0.0074 | |
| Ref. [12] | −0.0339 | 0.0186 | −0.0001 | |
| Ref. [13] | 0.01659 | 0.01531 | 0.00034 | |
| Ref. [16] | 0.0023 | −0.0187 | −0.0225 | |
| Ref. [17] | −0.0095 | −0.0259 | −0.0094 | |
| Test Images | Lena | Peppers | Baboon | Boat | Cameraman | Barbara | House | |
|---|---|---|---|---|---|---|---|---|
| Plain | 7.48183 | 7.60129 | 7.23399 | 7.26437 | 7.12881 | 7.51504 | 6.49614 | |
| Cipher | Proposed | 7.9970 | 7.9973 | 7.9976 | 7.9972 | 7.9977 | 7.9973 | 7.9973 |
| Ref. [12] | 7.9965 | 7.9958 | NA | 7.9959 | 7.9964 | 7.9957 | 7.9952 | |
| Ref. [13] | 7.99802 | 7.99852 | 7.99712 | NA | 7.99662 | NA | 7.99781 | |
| Ref. [16] | 7.9951 | 7.9965 | NA | 7.9960 | 7.9955 | 7.9937 | 7.9978 | |
| Ref. [25] | 7.9975 | 7.9958 | 7.9938 | 7.9941 | 7.9939 | NA | NA | |
| Ref. [28] | NA | NA | 7.9972 | 7.9962 | 7.9972 | 7.9969 | NA | |
| Ref. [31] | 7.9975 | 7.9972 | NA | NA | 7.9973 | NA | 7.9973 | |
| Ref. [32] | 7.9973 | 7.9972 | 7.9972 | 7.9972 | 7.9974 | 7.9972 | 7.9970 | |
| Ref. [39] | 7.9914 | NA | 7.9914 | NA | NA | NA | 7.9914 | |
| Test Image | Plain | Cipher | ||
|---|---|---|---|---|
| χ2 Value | H0 Test | χ2 Value | H0 Test | |
| Airplane | 168,463 | Fail | 258.172 | Pass |
| Baboon | 58,247.8 | Fail | 213.781 | Pass |
| Barbara | 35,001.2 | Fail | 242.57 | Pass |
| Boat | 85,621.8 | Fail | 255.305 | Pass |
| Cameraman | 97,215.8 | Fail | 212.992 | Pass |
| Girl | 93,817.1 | Fail | 240.836 | Pass |
| House | 300,852 | Fail | 242.477 | Pass |
| Lena | 37,973 | Fail | 276.633 | Pass |
| Peppers | 30,024.6 | Fail | 248.867 | Pass |
| Splash | 86,407.1 | Fail | 269.953 | Pass |
| Test Image/Method | Histogram Maximum Deviation | ||||
|---|---|---|---|---|---|
| Barbara | Boat | Cameraman | Lena | Peppers | |
| Proposed | 40,694.5 | 53,452.5 | 60,413 | 40,921.5 | 36,169 |
| Ref. [12] | 17,944 | 25,367 | 16,674 | 20,811 | 22,648 |
| Ref. [16] | 19,384 | 25,193 | 16,803 | 19,931 | 22,966 |
| Ref. [17] | 18,148 | 25,442 | 18,007 | 21,339 | 22,935 |
| Ref. [28] | NA | NA | 64,119 | 41,458 | 36,391 |
| Ref. [31] | 158,258 | 148,597 | 64,300 | NA | NA |
| Test Image/Method | Irregular Deviation | ||||
|---|---|---|---|---|---|
| Barbara | Boat | Cameraman | Lena | Peppers | |
| Proposed | 43,446 | 46,218 | 39,020 | 44,748 | 41,394 |
| Ref. [12] | 42,556 | 36,124 | 39,380 | 40,820 | 34,824 |
| Ref. [16] | 43,014 | 36,220 | 39,414 | 40,768 | 34,706 |
| Ref. [17] | 42,708 | 36,226 | 39,244 | 40,480 | 35,088 |
| Ref. [28] | NA | NA | 38,959 | 44,465 | 41,184 |
| Ref. [31] | 129,765 | 137,793 | 39,668 | NA | NA |
| Test Image/Method | Deviation from Ideality | |||||
|---|---|---|---|---|---|---|
| Barbara | Boat | Cameraman | House | Lena | Peppers | |
| Proposed | 0.04834 | 0.05002 | 0.04437 | 0.04889 | 0.05182 | 0.04916 |
| Ref. [12] | 0.0928 | 0.0985 | 0.092 | 0.0994 | 0.0934 | 0.0977 |
| Ref. [16] | 0.1012 | 0.0995 | 0.1065 | 0.1141 | 0.1001 | 0.0979 |
| Ref. [17] | 0.0976 | 0.0958 | 0.0942 | 0.0882 | 0.0994 | 0.0917 |
| Ref. [28] | NA | NA | NA | 0.0485 | 0.0468 | 0.0496 |
| Ref. [31] | 0.0522 | 0.0528 | 0.0502 | NA | NA | NA |
| Planes Test Images | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | |
|---|---|---|---|---|---|---|---|---|---|
| Airplane | P | 50.383 | 49.817 | 49.355 | 51.842 | 53.865 | 24.394 | 78.969 | 81.544 |
| E | 50.191 | 50.134 | 49.817 | 50.22 | 49.763 | 50.531 | 50.034 | 49.969 | |
| Baboon | P | 50.247 | 50.075 | 50.378 | 50.563 | 53 | 55.841 | 44.63 | 53.096 |
| E | 49.834 | 50.006 | 50.09 | 49.844 | 50.102 | 50.092 | 49.715 | 49.782 | |
| Barbara | P | 49.928 | 49.916 | 50.075 | 50.272 | 48.856 | 48.956 | 47.932 | 35.727 |
| E | 50.041 | 50.259 | 49.825 | 50.356 | 50.066 | 49.71 | 49.623 | 50.128 | |
| Boat | P | 49.924 | 50 | 49.974 | 49.364 | 50.856 | 39.584 | 22.548 | 67.471 |
| E | 49.889 | 50.281 | 49.783 | 50.168 | 49.977 | 49.974 | 49.911 | 49.98 | |
| Cameraman | P | 49.841 | 49.379 | 50.844 | 52.199 | 42.644 | 50.958 | 18.71 | 60.005 |
| E | 50.145 | 49.895 | 49.931 | 49.965 | 49.867 | 50.336 | 49.782 | 50.058 | |
| Girl | P | 50.175 | 50.787 | 50.722 | 49.904 | 46.37 | 50.824 | 26.7 | 8.197 |
| E | 49.586 | 49.832 | 49.916 | 49.887 | 49.77 | 50.003 | 50.111 | 49.713 | |
| House | P | 50.035 | 49.631 | 52.985 | 65.085 | 67.981 | 71.492 | 52.217 | 48.505 |
| E | 49.921 | 50.359 | 50.259 | 49.77 | 49.988 | 50.05 | 49.829 | 50.122 | |
| Lena | P | 50.009 | 50.108 | 49.728 | 49.901 | 49.777 | 50.337 | 41.794 | 51.187 |
| E | 50.247 | 49.968 | 49.486 | 49.768 | 50.113 | 50.005 | 50.536 | 50.444 | |
| Peppers | P | 49.979 | 49.715 | 49.796 | 49.933 | 53.462 | 46.248 | 44.778 | 47.327 |
| E | 49.925 | 50.201 | 49.954 | 50.281 | 49.966 | 49.78 | 50.204 | 50.194 | |
| Parameters | Tool Used for Implementation | System Configuration | Proposed Approach | Execution Time (s) | |
|---|---|---|---|---|---|
| Existing Work | |||||
| Ref. [17] | MATLAB | Intel Core i3-3227U 1.9 CPU and 4 GB of RAM | LFT-based S-box using a new chaotic map, P-S network | 0.095 | |
| Ref. [18] | MATLAB R2011b | Intel(R) Core (TM) i3–2350, 2.30 GHz CPU | Plain image-dependent keystream using 2D logistic map | 0.0343 | |
| Ref. [19] | MATLAB R2017a | Intel Core i7–7500 U, 3.5 GHz CPU, 4GB RAM | 3D modular chaotic map permutation process for image encryption | 0.8271 | |
| Ref. [25] | MATLAB 8 | Intel Core i7, 2.3 GHz CPU, 8 GB RAM | Logistic chaos system, DNA encoding and operations. | 0.281 | |
| Ref. [30] | MATLAB 2013a | Intel Core i3, 2.4 GHz CPU and 4 GB RAM | Bit-level permutation and diffusion using DNA addition | 0.54 | |
| Ref. [32] | Virtual instrumentation tool | Core i5, 2.5 GHz CPU, 4 GB RAM | Chaos-based key generation system, DNA encoding and operations for secure image storage in the cloud | 0.2188 | |
| Ref. [33] | MATLAB2011b | AMD A6-3420M and 2 GB RAM | Secure sampling through cascade chaotic map followed by confusion using Arnold transform and single-stage XOR-based diffusion | 1.663661 | |
| Proposed | Virtual instrumentation tool | Core i5, 2.5 GHz CPU, 4 GB RAM | Neural attractor-based image-specific key generation and chaos key generation for image scrambling and DNA-based diffusion | 0.2195 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mahalingam, H.; Velupillai Meikandan, P.; Thenmozhi, K.; Moria, K.M.; Lakshmi, C.; Chidambaram, N.; Amirtharajan, R. Neural Attractor-Based Adaptive Key Generator with DNA-Coded Security and Privacy Framework for Multimedia Data in Cloud Environments. Mathematics 2023, 11, 1769. https://doi.org/10.3390/math11081769
Mahalingam H, Velupillai Meikandan P, Thenmozhi K, Moria KM, Lakshmi C, Chidambaram N, Amirtharajan R. Neural Attractor-Based Adaptive Key Generator with DNA-Coded Security and Privacy Framework for Multimedia Data in Cloud Environments. Mathematics. 2023; 11(8):1769. https://doi.org/10.3390/math11081769
Chicago/Turabian StyleMahalingam, Hemalatha, Padmapriya Velupillai Meikandan, Karuppuswamy Thenmozhi, Kawthar Mostafa Moria, Chandrasekaran Lakshmi, Nithya Chidambaram, and Rengarajan Amirtharajan. 2023. "Neural Attractor-Based Adaptive Key Generator with DNA-Coded Security and Privacy Framework for Multimedia Data in Cloud Environments" Mathematics 11, no. 8: 1769. https://doi.org/10.3390/math11081769
APA StyleMahalingam, H., Velupillai Meikandan, P., Thenmozhi, K., Moria, K. M., Lakshmi, C., Chidambaram, N., & Amirtharajan, R. (2023). Neural Attractor-Based Adaptive Key Generator with DNA-Coded Security and Privacy Framework for Multimedia Data in Cloud Environments. Mathematics, 11(8), 1769. https://doi.org/10.3390/math11081769







