A Comprehensive Analytical Framework under Practical Constraints for a Cooperative NOMA System Empowered by SWIPT IoT
Abstract
:1. Introduction
1.1. Information Background
1.2. Related Works and Motivation
1.3. Contributions
- An innovative C-NOMA scheme custom-tailored for SWIPT-enabled IoT systems takes center stage. This scheme orchestrates power allocation for two users through a pivotal relay node (R) in the DF of signals from the B. It is essential to emphasize that R also performs the critical task of EH from the power beacon (PB). This holistic integration of power management, signal manipulation, and EH within a unified relay node represents a groundbreaking strategy, aimed at optimizing overall system efficiency. The scheme utilizes a TS receiver architecture, enabling R to simultaneously perform both EH and Information Processing (IP) tasks.
- EH Protocol Advancement: The paper introduces an advanced EH protocol with an HD-based TSR mechanism meticulously designed for SWIPT-based C-NOMA systems. This EH protocol assumes a pivotal role in the harnessing of energy from received signals, thereby bolstering the sustainability and autonomy of IoT devices interconnected within the network.
- In an effort to provide a comprehensive understanding of system performance, the paper derives precise closed-form expressions for critical metrics, including but not limited to OP and System Throughput (ST). These analytical expressions serve as essential tools for rigorously evaluating the proposed C-NOMA and EH schemes. Researchers and practitioners can use these insights to make informed decisions and assess the effectiveness of these systems in practical IoT deployments.
1.4. Organization and Notations
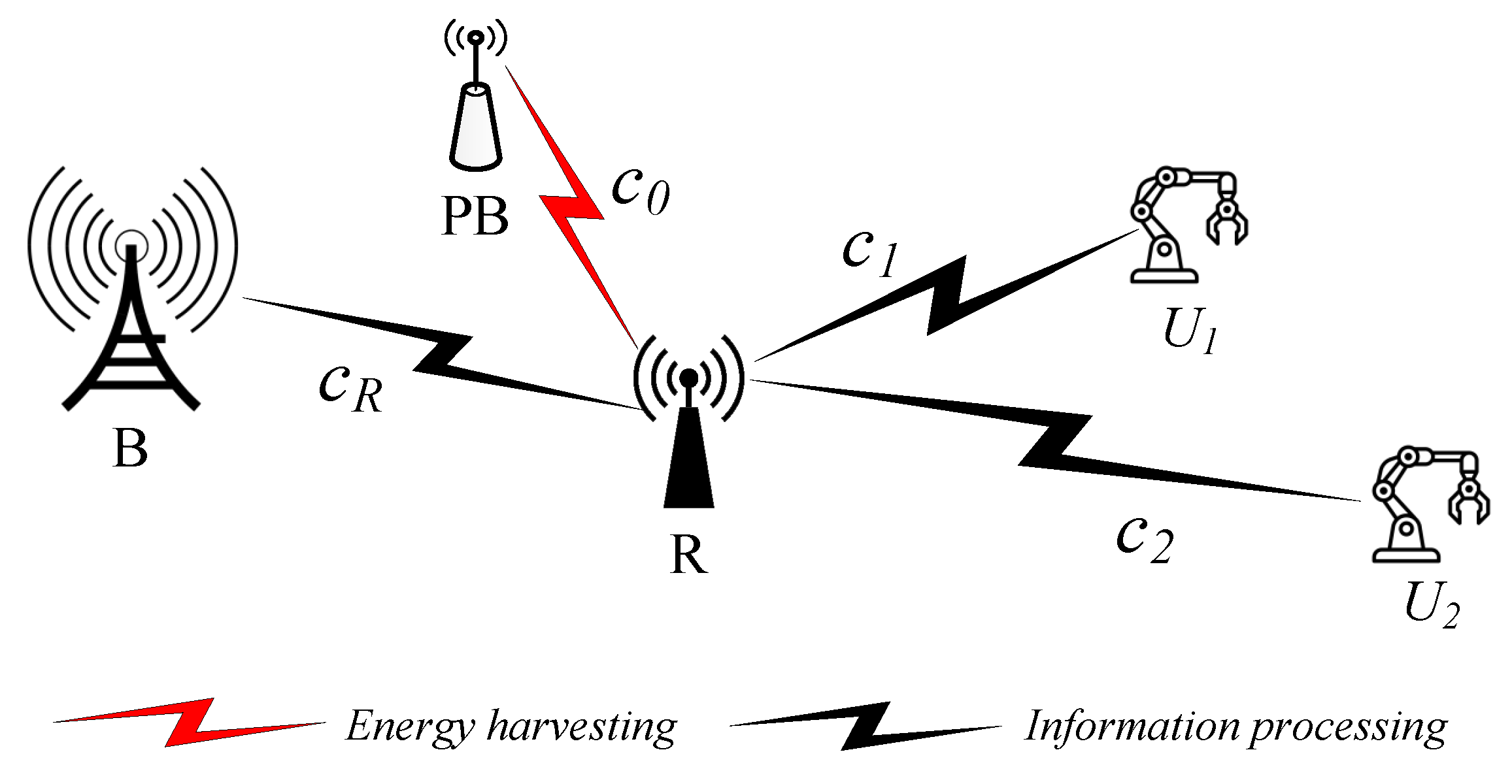
2. System Model
3. The TSR-Based Energy Harvesting of the Relay Node
3.1. The Energy Harvesting at the Relay Node
3.2. Phase: Energy Transfer
3.3. Phase: Data Transmission
3.3.1. Stage. 1: Communication
3.3.2. Stage. 2: Communication
4. Performance Assessment
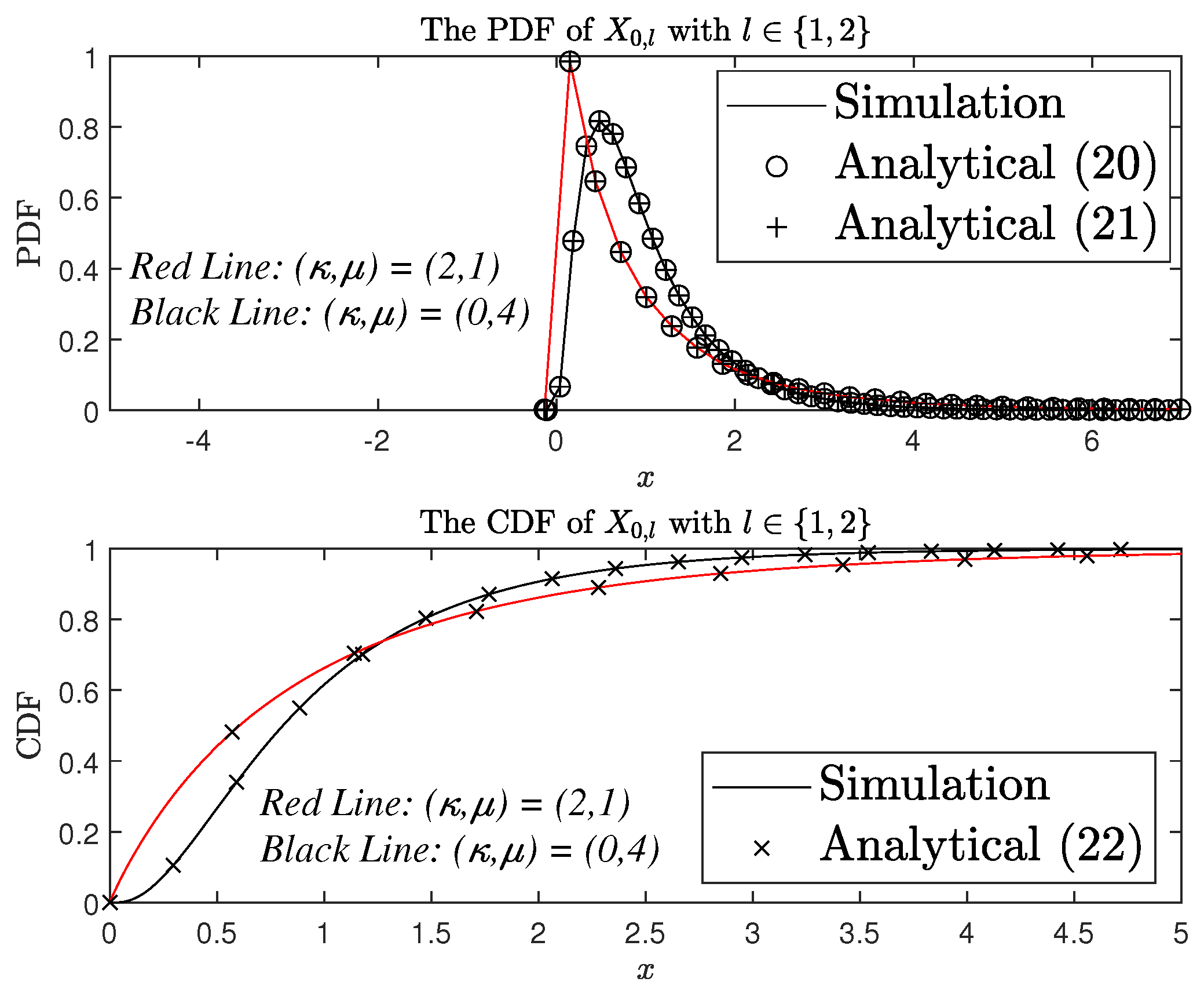
4.1. Channel Characteristics
4.2. The OP
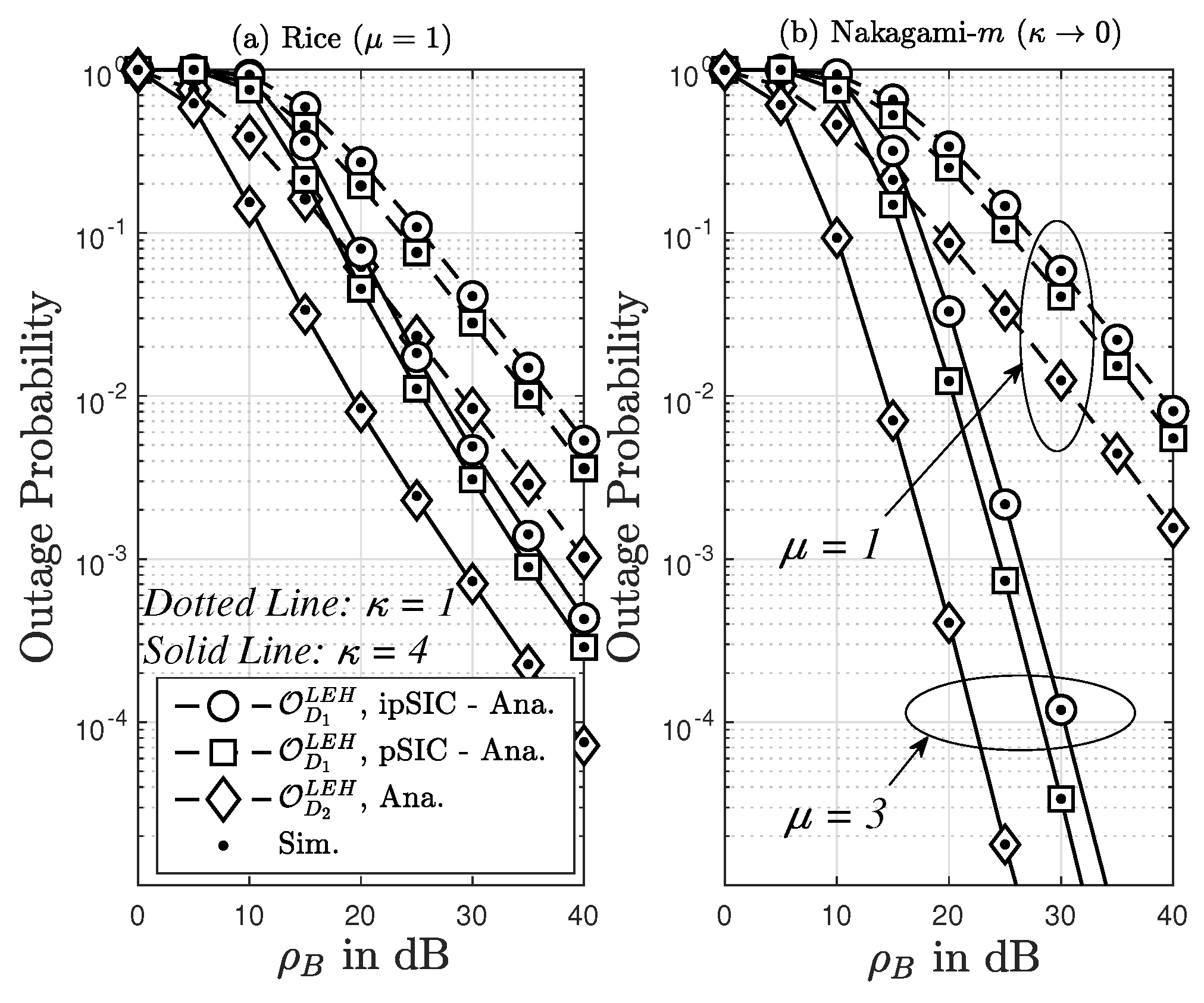
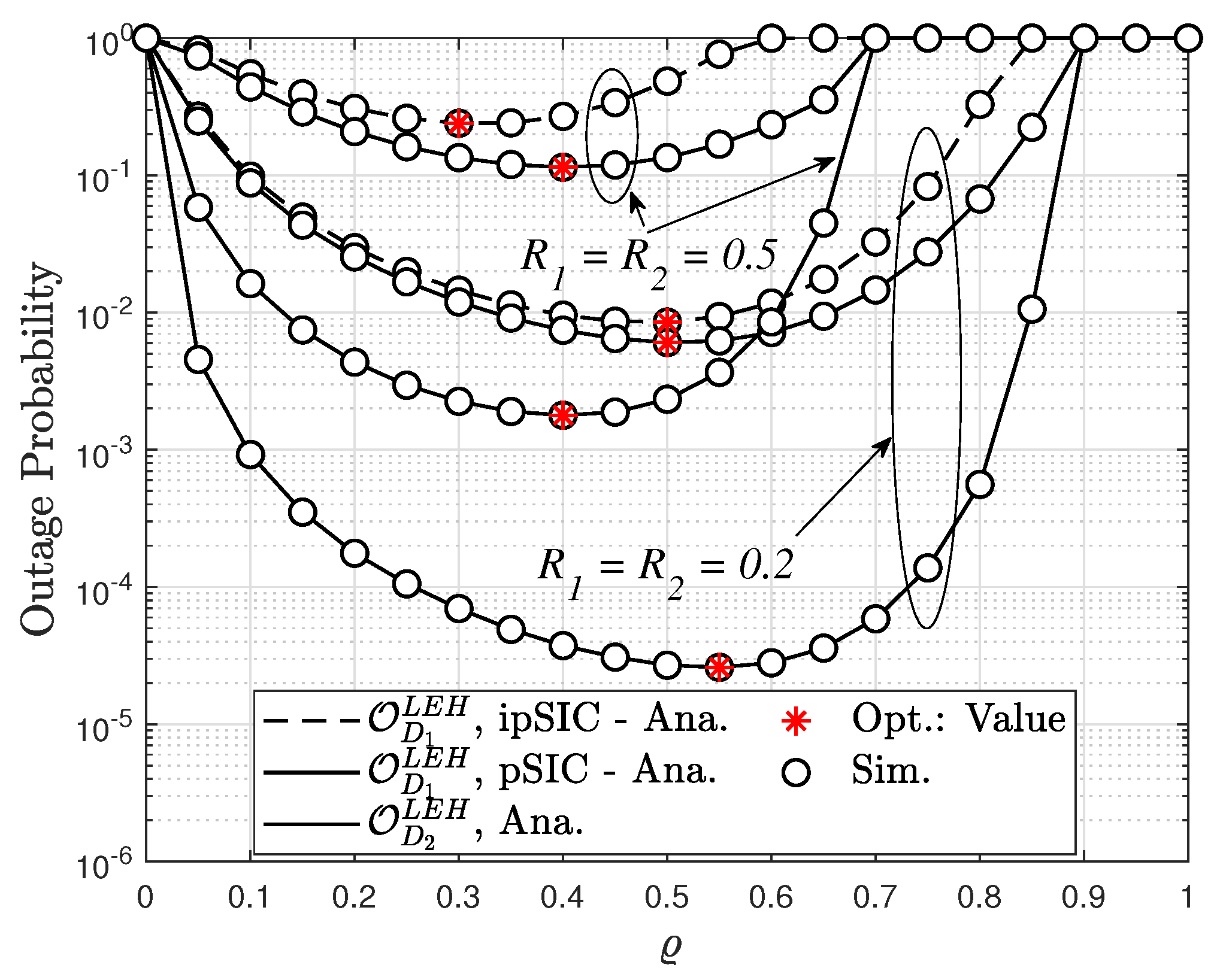
4.2.1. The OP in the Scenario of LEH
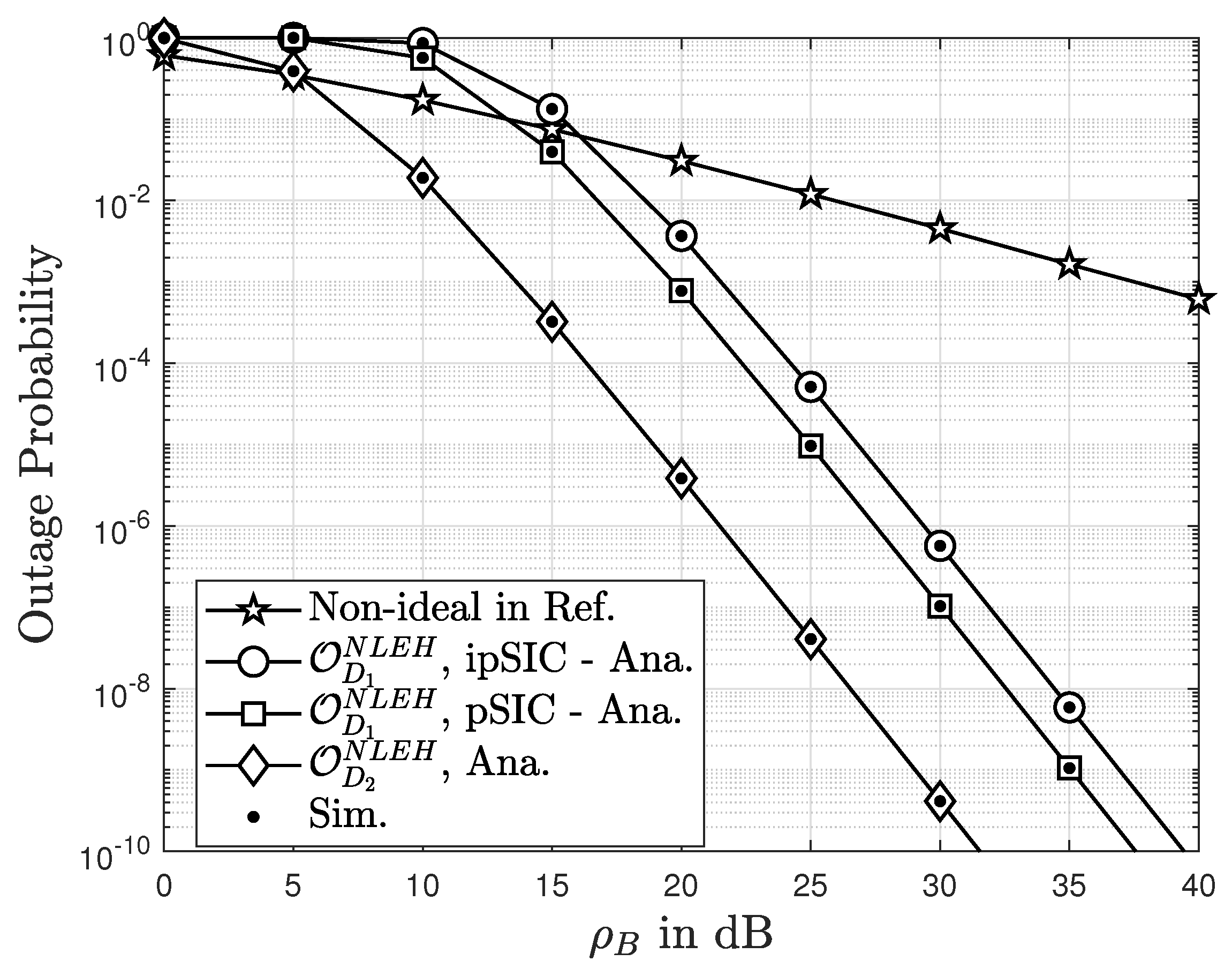
4.2.2. The OP in the Scenario of NLEH
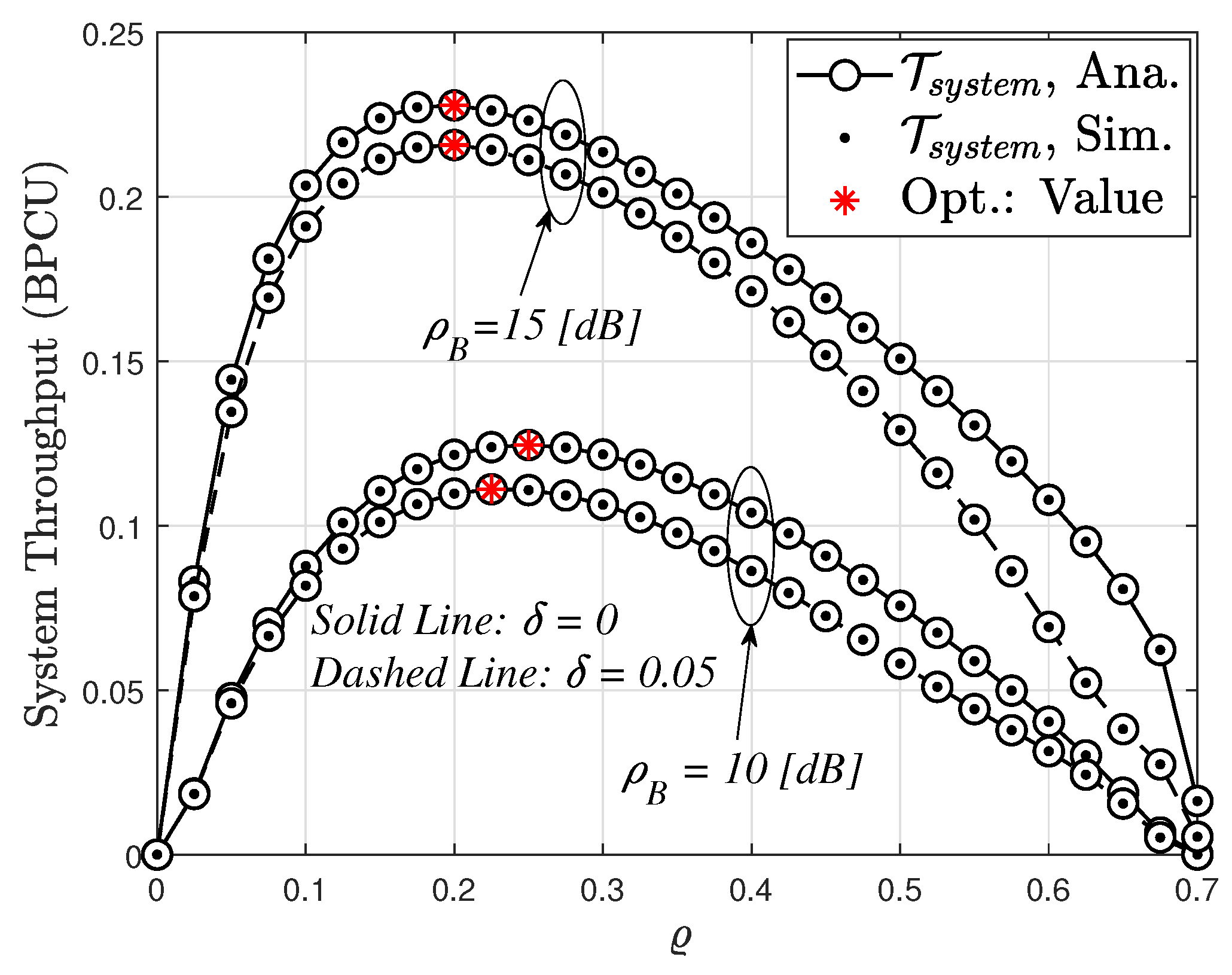
4.3. System Throughput Analysis (STA)
5. Pseudo Code
| Algorithm 1: The proposed method for Problem-Solving |
1. Initialization: 1.1 Set 1.2 Set 1.3 Set 1.4 Set 2. While Loop: 2.1 while do: 2.1.1 Set 2.1.2 Set 2.1.5 If then 2.1.5.1 Set else: 2.1.5.2 Set 2.1.6 end 2.2 End while 3. Return the Optimal : 3.1 Return |
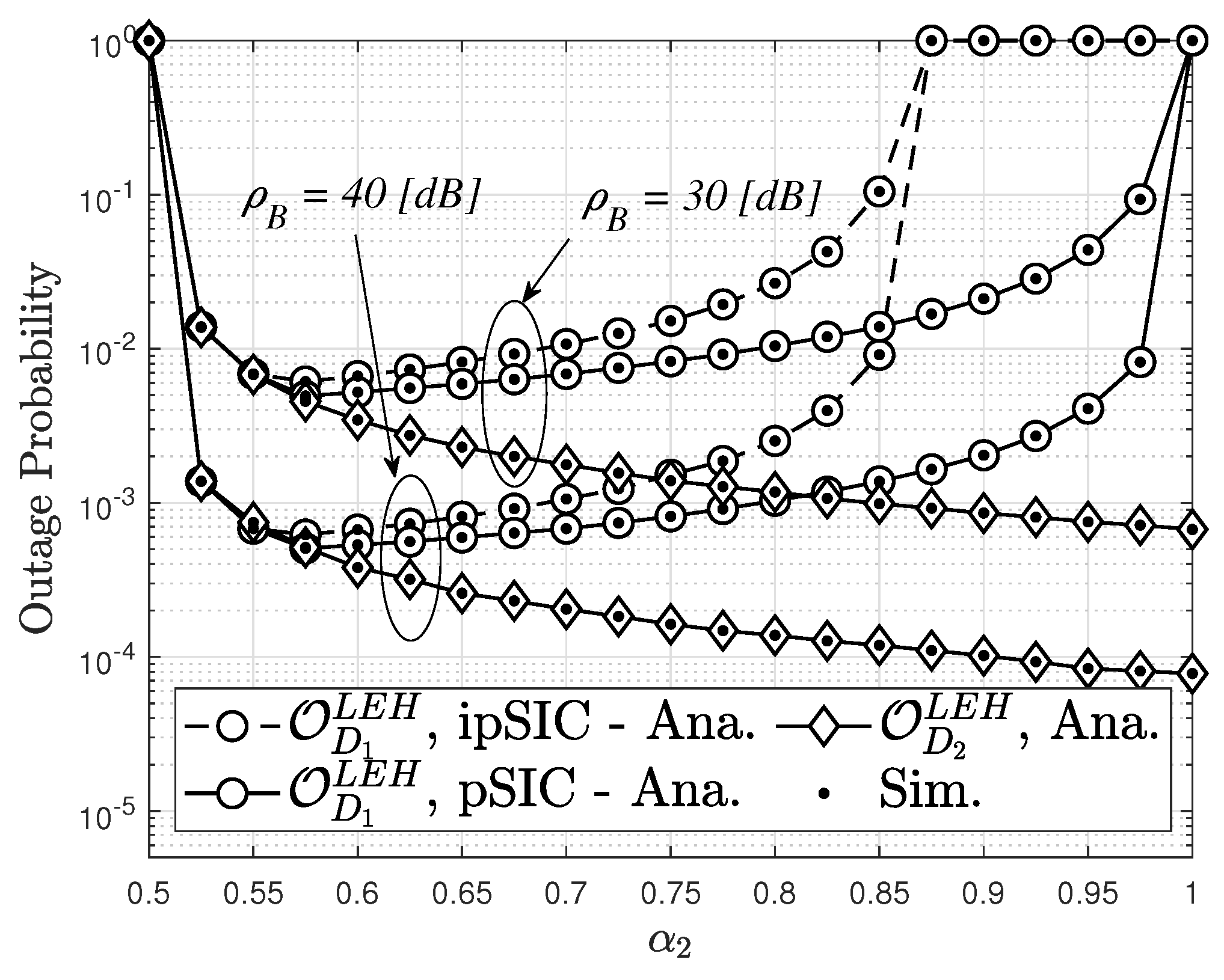
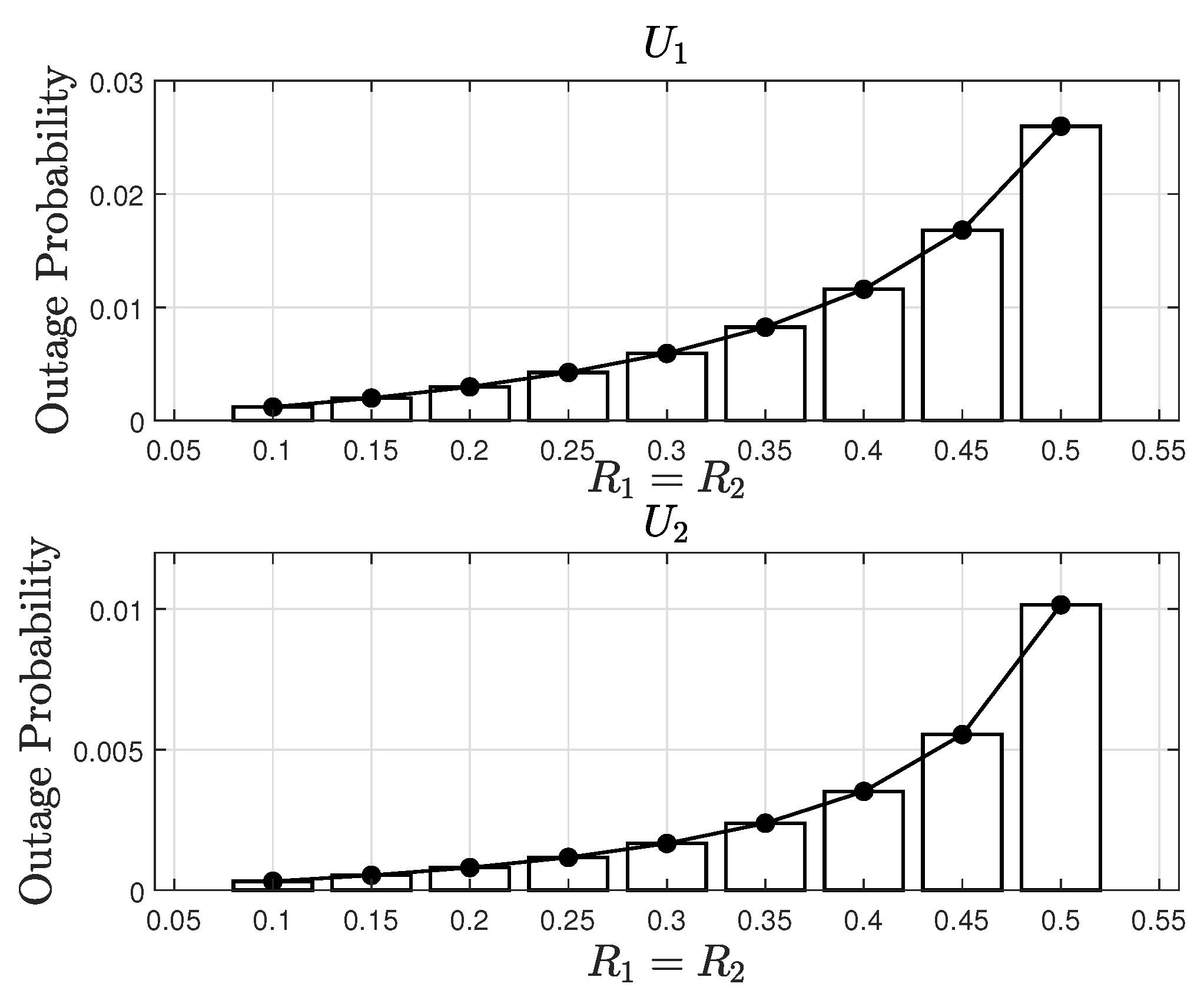
6. Optimization of the TS Factor to Minimize the OP for Users
7. Energy Efficiency
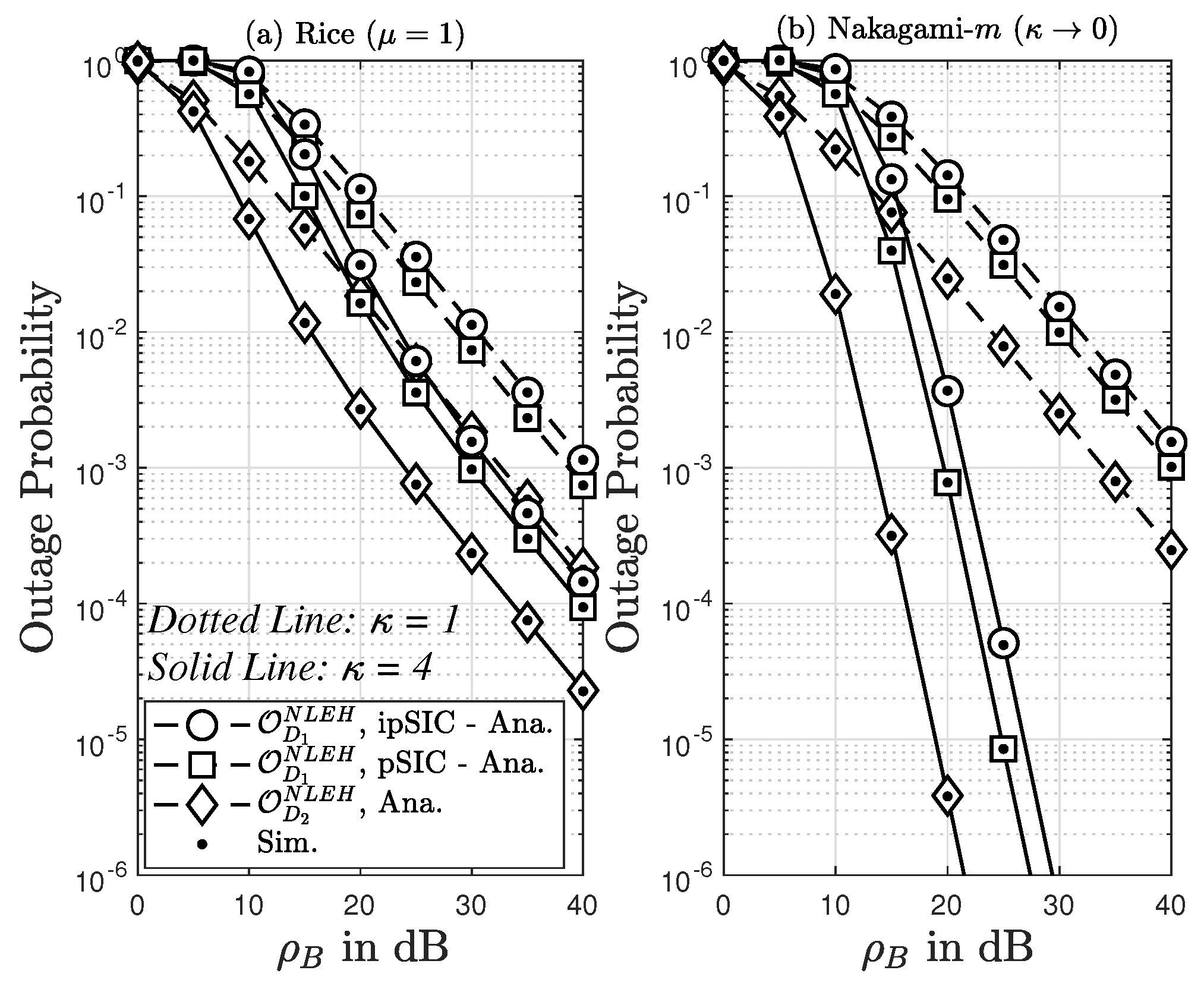
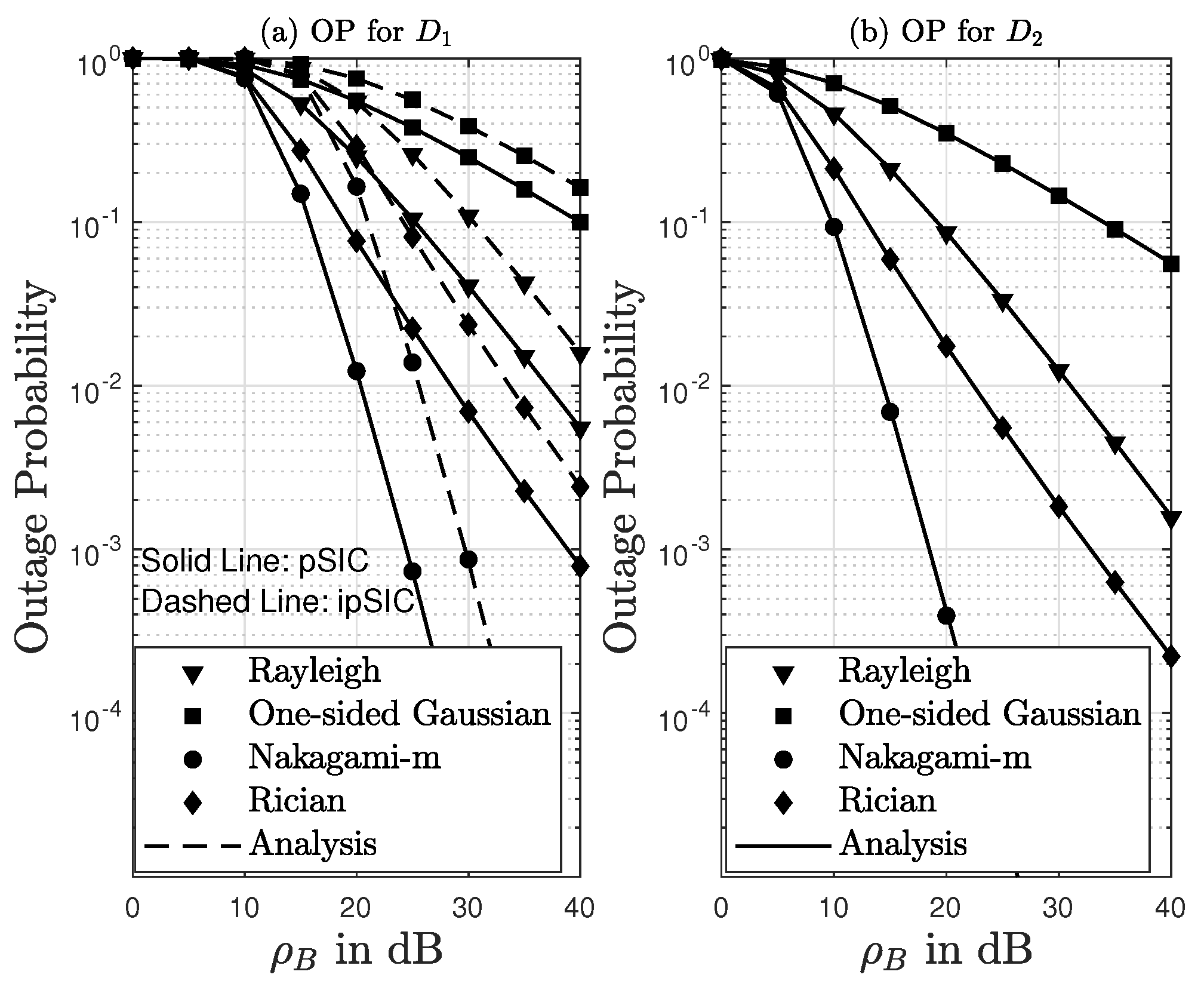
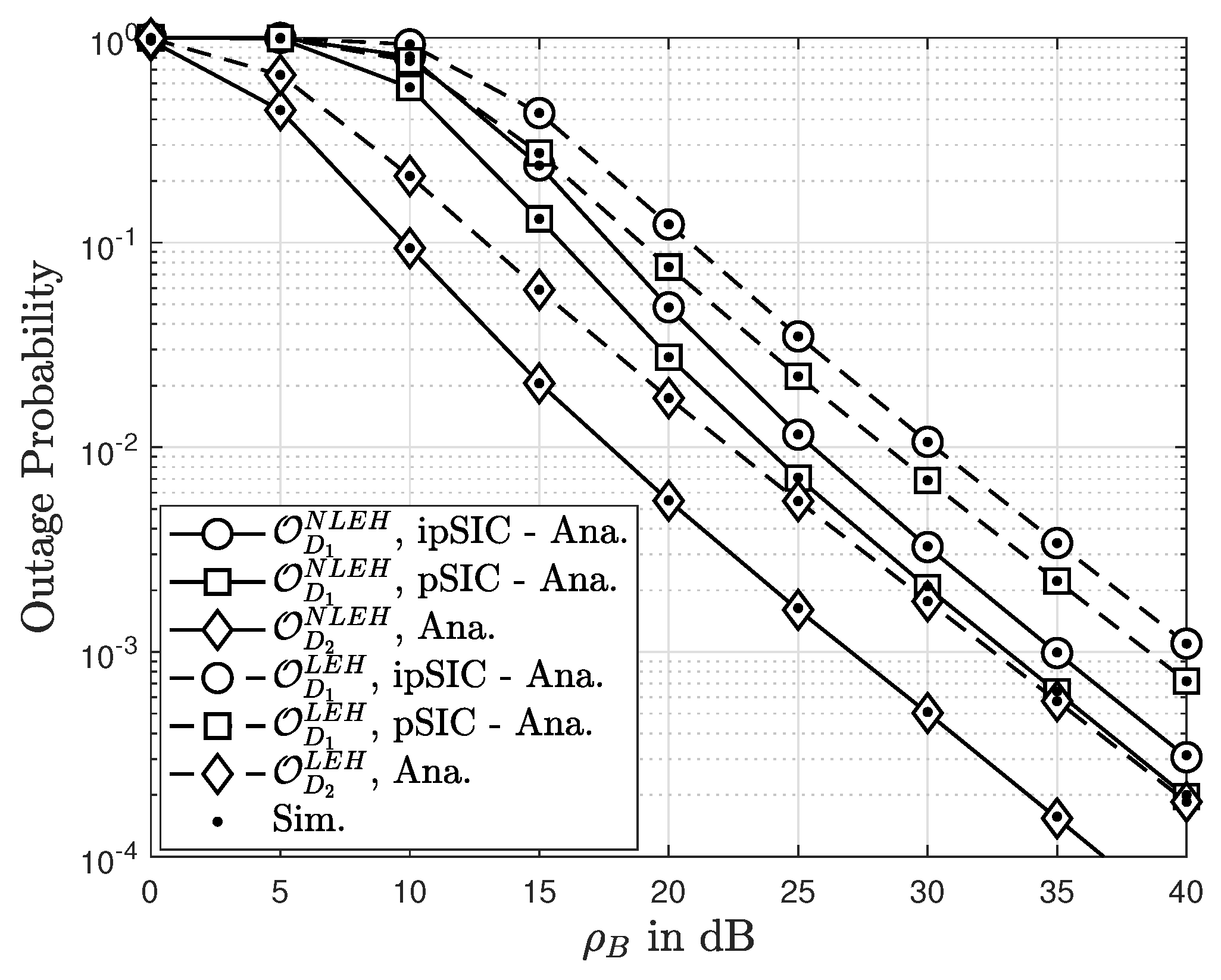
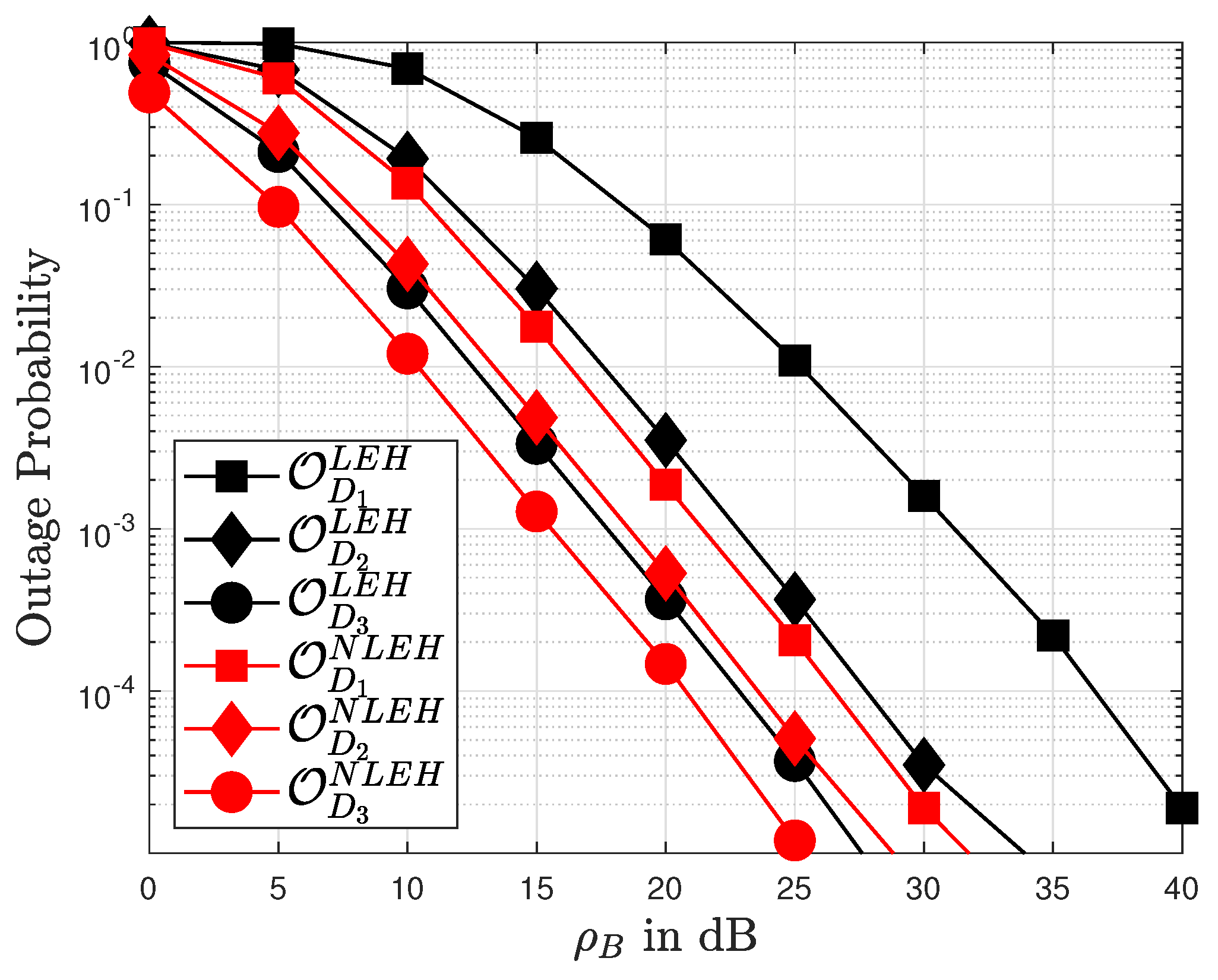
8. Simulation Results
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Equation (21)
References
- Dai, L.; Wang, B.; Ding, Z.; Wang, Z.; Chen, S.; Hanzo, L. A Survey of Non-Orthogonal Multiple Access for 5G. IEEE Commun. Surv. Tutor. 2018, 20, 2294–2323. [Google Scholar] [CrossRef]
- Makki, B.; Chitti, K.; Behravan, A.; Alouini, M.-S. A Survey of NOMA: Current Status and Open Research Challenges. IEEE Open J. Commun. Soc. 2020, 1, 179–189. [Google Scholar] [CrossRef]
- Al-habob, A.A.; Salhab, A.M.; Zummo, S.A. A Novel Time-Switching Relaying Protocol for Multi-user Relay Networks with SWIPT. Arab. J. Sci. Eng. 2019, 44, 2253–2263. [Google Scholar] [CrossRef]
- Tran, H.Q.; Phan, C.V.; Vien, Q.T. Power splitting versus time switching based cooperative relaying protocols for SWIPT in NOMA systems. Phys. Commun. 2020, 41, 101098. [Google Scholar] [CrossRef]
- Tran, H.Q.; Phan, C.V.; Vien, Q.T. Performance analysis of power-splitting relaying protocol in SWIPT based cooperative NOMA systems. EURASIP J. Wirel. Commun. Netw. 2021, 2021, 110. [Google Scholar] [CrossRef]
- Tran, H.Q.; Vien, Q.T. SWIPT-Based Cooperative NOMA for Two-Way Relay Communications: PSR versus TSR. Wirel. Commun. Mob. Comput. 2023, 2023, 3069999. [Google Scholar] [CrossRef]
- Alhamad, R.; Boujemaa, H. Non Orthogonal Multiple Access for Multi-carrier Code Division Multiple Access Systems with Energy Harvesting. Wirel. Pers. Commun. 2024, 134, 2121–2136. [Google Scholar] [CrossRef]
- Ogundokun, R.O.; Awotunde, J.B.; Imoize, A.L.; Li, C.-T.; Abdulahi, A.T.; Adelodun, A.B.; Sur, S.N.; Lee, C.-C. Non-Orthogonal Multiple Access Enabled Mobile Edge Computing in 6G Communications: A Systematic Literature Review. Sustainability 2023, 15, 7315. [Google Scholar] [CrossRef]
- Islam, S.M.; Avazov, N.; Dobre, O.A.; Kwak, K.S. Power-Domain Non-Orthogonal Multiple Access (NOMA) in 5G Systems: Potentials and Challenges. IEEE Commun. Surv. Tutor. 2017, 19, 721–742. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; I, C.L.; Wang, Z. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Tran, H.Q.; Truong, P.Q.; Phan, C.V.; Vien, Q.T. On the energy efficiency of NOMA for wireless backhaul in multi-tier heterogeneous CRAN. In Proceedings of the 2017 International Conference on Recent Advances in Signal Processing, Telecommunications & Computing (SigTelCom), Da Nang, Vietnam, 9–11 January 2017; pp. 229–234. [Google Scholar] [CrossRef]
- Sur, S.N.; Kandar, D.; Silva, A.; Nguyen, N.D.; Nandi, S.; Do, D.-T. Hybrid Precoding Algorithm for Millimeter-Wave Massive MIMO-NOMA Systems. Electronics 2022, 11, 2198. [Google Scholar] [CrossRef]
- Ding, Z.; Lei, X.; Karagiannidis, G.K.; Schober, R.; Yuan, J.; Bhargava, V.K. A Survey on Non-Orthogonal Multiple Access for 5G Networks: Research Challenges and Future Trends. IEEE J. Sel. Areas Commun. 2017, 35, 2181–2195. [Google Scholar] [CrossRef]
- Tsiropoulos, G.I.; Yadav, A.; Zeng, M.; Dobre, O.A. Cooperation in 5G HetNets: Advanced Spectrum Access and D2D Assisted Communications. IEEE Wirel. Commun. 2017, 24, 110–117. [Google Scholar] [CrossRef]
- Zhang, Z.; Ma, Z.; Xiao, M.; Ding, Z.; Fan, P. Full-duplex device-to-device-aided cooperative nonorthogonal multiple access. IEEE Trans. Veh. Technol. 2017, 66, 4467–4471. [Google Scholar] [CrossRef]
- Wang, Z.; Yue, X.; Peng, Z. Full-duplex user relaying for NOMA system with self-energy recycling. IEEE Access 2018, 6, 67057–67069. [Google Scholar] [CrossRef]
- Yue, X.; Liu, Y.; Kang, S.; Nallanathan, A.; Ding, Z. Exploiting Full/Half-Duplex User Relaying in NOMA Systems. IEEE Trans. Commun. 2018, 66, 560–575. [Google Scholar] [CrossRef]
- Abbasi, O.; Ebrahimi, A. Cooperative NOMA with full-duplex amplify-and-forward relaying. Trans. Emerg. Telecommun. Technol. 2018, 29, e3421. [Google Scholar] [CrossRef]
- Yang, Z.; Ding, Z.; Wu, Y.; Fan, P. Novel Relay Selection Strategies for Cooperative NOMA. IEEE Trans. Veh. Technol. 2017, 66, 10114–10123. [Google Scholar] [CrossRef]
- Duan, W.; Ju, J.; Hou, J.; Sun, Q.; Jiang, X.Q.; Zhang, G. Effective resource utilization schemes for decode-and-forward relay networks with NOMA. IEEE Access 2019, 7, 51466–51474. [Google Scholar] [CrossRef]
- Doan, T.B.; Nguyen, T.H. Exploiting SWIPT for Coordinated-NOMA Systems Under Nakagami-m Fading. IEEE Access. 2024, 12, 19216–19228. [Google Scholar] [CrossRef]
- Nasir, A.A.; Zhou, X.; Durrani, S.; Kennedy, R.A. Relaying Protocols for Wireless Energy Harvesting and Information Processing. IEEE Trans. Wirel. Commun. 2013, 12, 3622–3636. [Google Scholar] [CrossRef]
- Dubey, S.; Mehra, N.; Shakya, D.K. Time and relay shared full/half duplex cooperative NOMA with paired cell edge users. AEU-Int. J. Electron. Commun. 2024, 177, 155168. [Google Scholar] [CrossRef]
- Chu, T.M.C.; Zepernick, H.J. Performance of a Non-Orthogonal Multiple Access System with Full-Duplex Relaying. IEEE Commun. Lett. 2018, 22, 2084–2087. [Google Scholar] [CrossRef]
- Mohammadi, M.; Chalise, B.K.; Hakimi, A.; Suraweera, H.A.; Ding, Z. Joint Beamforming Design and Power Allocation for Full-Duplex NOMA Cognitive Relay Systems. In Proceedings of the 2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Guo, C.; Zhao, L.; Feng, C.; Ding, Z.; Wang, H.-M. Secrecy Performance of NOMA Systems With Energy Harvesting and Full-Duplex Relaying. IEEE Trans. Veh. Technol. 2020, 69, 12301–12305. [Google Scholar] [CrossRef]
- Guo, C.; Zhao, L.; Feng, C.; Ding, Z.; Chen, H.-H. Energy Harvesting Enabled NOMA Systems With Full-Duplex Relaying. IEEE Trans. Veh. Technol. 2019, 68, 7179–7183. [Google Scholar] [CrossRef]
- Singh, C.K.; Upadhyay, P.K. Overlay Cognitive IoT-Based Full-Duplex Relaying NOMA Systems With Hardware Imperfections. IEEE Internet Things J. 2022, 9, 6578–6596. [Google Scholar] [CrossRef]
- Rauniyar, A.; Engelstad, P.E.; Østerbø, O.N. On the Performance of Bidirectional NOMA-SWIPT Enabled IoT Relay Networks. IEEE Sens. J. 2021, 21, 2299–2315. [Google Scholar] [CrossRef]
- Sixtus J, R.J.; Muthu, T. Investigations on IoT with SWIPT-NOMA Combination in Wireless Sensor Networks. In Proceedings of the 2022 International Conference on Inventive Computation Technologies (ICICT), Lalitpur, Nepal, 20–22 July 2022; pp. 688–693. [Google Scholar] [CrossRef]
- Shaheen, E.M.; Soleymani, M.R. Performance Analyses of SWIPT-NOMA Enabled IoT Relay Networks. In Proceedings of the 2022 International Symposium on Networks, Computers and Communications (ISNCC), Shenzhen, China, 19–22 July 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Al-Obiedollah, H.; Salameh, H.B.; Gharaibeh, A.; Cumanan, K.; Ding, Z.; Dobre, O.A. Harvested Power Fairness-Based Multi-Carrier NOMA IoT Networks With SWIPT. IEEE Wirel. Commun. Lett. 2023, 12, 381–385. [Google Scholar] [CrossRef]
- Do, D.-T.; Le, C.-B.; Afghah, F. Enabling Full-Duplex and Energy Harvesting in Uplink and Downlink of Small-Cell Network Relying on Power Domain Based Multiple Access. IEEE Access 2020, 8, 142772–142784. [Google Scholar] [CrossRef]
- Do, D.-T.; Le, C.-B.; Le, A.-T. Joint of full-duplex relay, non-linear energy harvesting and multiple access in performance improvement of cell-edge user in heterogeneous networks. Wirel. Netw. 2020, 26, 6253–6266. [Google Scholar] [CrossRef]
- Babaei, M.; Aygolu, U.; Basar, E. Cooperative AF relaying with energy harvesting in Nakagami- fading channel. Phys. Commun. 2019, 34, 105–113. [Google Scholar] [CrossRef]
- Li, X.; Huang, M.; Zhang, C.; Deng, D.; Rabie, K.M.; Ding, Y.; Du, J. Security and Reliability Performance Analysis of Cooperative Multi-Relay Systems With Nonlinear Energy Harvesters and Hardware Impairments. IEEE Access 2019, 7, 102644–102661. [Google Scholar] [CrossRef]
- Le, A.-T.; Tran, D.-H.; Le, C.-B.; Tin, P.T.; Nguyen, T.N.; Ding, Z.; Poor, H.V.; Voznak, M. Power Beacon and NOMA-Assisted Cooperative IoT Networks With Co-Channel Interference: Performance Analysis and Deep Learning Evaluation. IEEE Trans. Mob. Comput. 2024, 23, 7270–7283. [Google Scholar] [CrossRef]
- Solanki, S.; Upadhyay, P.K.; da Costa, D.B.; Ding, H.; Moualeau, J.M. Performance analysis of piece-wise linear model of energy harvesting-based multiuser overlay spectrum sharing networks. IEEE Open J. Commun. Soc. 2020, 1, 1820–1836. [Google Scholar] [CrossRef]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series and Products, 7th ed.; Academic: San Diego, CA, USA, 2007. [Google Scholar]
- Karagiannidis, G.K.; Sagias, N.C.; Mathiopoulos, P.T. N–Nakagami: A novel stochastic model for cascaded fading channels. IEEE Trans. Commun. 2007, 55, 1453–1458. [Google Scholar] [CrossRef]
- Nadarajah, S. Exact distribution of the product of m gamma and n Pareto random variables. J. Comput. Appl. Math. 2011, 235, 4496–4512. [Google Scholar] [CrossRef]
- Simon, M.K.; Alouini, M.-S. Digital Communication over Fading Channels; John Wiley & Sons: Hoboken, NJ, USA, 2005. [Google Scholar]
- Weisstein, E. Regularized Hypergeometric Function, 3rd ed.; Wolfram Research, Inc.: Champaign, IL, USA, 2003. [Google Scholar]
- Rauniyar, A.; Engelstad, P.; Østerbø, O.N. RF energy harvesting and information transmission in IoT relay systems based on time switching and NOMA. In Proceedings of the 2018 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 21–23 November 2018; pp. 1–7. [Google Scholar] [CrossRef]
- Rauniyar, A.; Engelstad, P.E.; Østerbø, O.N. Performance analysis of RF energy harvesting and information transmission based on NOMA with interfering signal for IoT relay systems. IEEE Sens. J. 2019, 19, 7668–7682. [Google Scholar] [CrossRef]
- Pei, L.; Yang, Z.; Pan, C.; Huang, W.; Chen, M.; Elkashlan, M.; Nallanathan, A. Energy-efficient D2D communications underlaying NOMA-based networks with energy harvesting. IEEE Commun. Lett. 2018, 22, 914–917. [Google Scholar] [CrossRef]
- Le-Thanh, T.; Ho-Van, K. Performance Analysis of Wireless Communications with Nonlinear Energy Harvesting under Hardware Impairment and κ−μ Shadowed Fading. Sensors 2023, 23, 3619. [Google Scholar] [CrossRef]
- Paris, J.F. Statistical Characterization of κ−μ Shadowed Fading. IEEE Trans. Veh. Technol. 2014, 63, 518–526. [Google Scholar] [CrossRef]
- Yacoub, M. The κ−μ distribution and the η−μ distribution. IEEE Antennas Propag. Mag. 2007, 49, 68–81. [Google Scholar] [CrossRef]


| Our Scheme | [33] | [34] | [4] | [5] | [6] | [35] | [36] | [37] | |
|---|---|---|---|---|---|---|---|---|---|
| NOMA | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | X | X | ✓ |
| Multiple Relay | X | X | X | X | X | X | X | ✓ | X |
| Energy harvesting | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Generalized channels | ✓ | X | X | X | X | X | X | X | X |
| Full-Duplex | X | ✓ | ✓ | X | X | X | X | X | X |
| Power beacon | ✓ | X | X | X | X | X | X | ✓ | ✓ |
| AF | X | X | X | X | X | X | ✓ | X | X |
| DF | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| Outage Probability | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| Throughput | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | X | ✓ | ✓ |
| Optimization | ✓ | X | ✓ | X | X | X | X | X | ✓ |
| Acronym | Definition |
|---|---|
| 6G | Six-generation |
| AF | Amplify and decode |
| AWGN | Additive white gaussian noise |
| CDF | Cumulative distribution function |
| C-NOMA | Cooperative non-orthogonal multiple access |
| CSST | Cooperative spectrum-sharing transmission |
| D2D | Device to device |
| DF | Decode and forward |
| DLT | Delay-limited transmission |
| EH | Energy harvesting |
| FD | Full-duplex |
| HD | Half-duplex |
| IoT | Internet of things |
| IP | Information processing |
| ipSIC | Imperfect SIC |
| LEH | Linear energy harvesting |
| NLEH | Nonlinear energy harvesting |
| OFDM | Orthogonal frequency division multiple access |
| OFDMA | Orthogonal frequency division multiple access |
| OMA | Orthogonal multiple access |
| OP | Outage probability |
| Probability density function | |
| pSIC | Perfect SIC |
| QoS | Quality of service |
| RMS | Root-mean-square |
| RVs | Random variables |
| SC | Superimposed coding |
| SIC | Successive interference cancellation |
| ST | System throughput |
| SINR | signal-to-plus-noise ratio |
| SNR | signal-to-noise ratio |
| SWIPT | Simultaneous wireless information and power transfer |
| TSR | Time-switching receiver |
| Parameters | Description |
|---|---|
| The target rate is set at , where i belongs to the set . | |
| ’s information | |
| ’s threshold rate. | |
| Power allocation coefficients at . | |
| & | The AWGN term was succeeded by . |
| Transmit power at BS. | |
| Transmit power at R | |
| T | The total time used for EH and IP. |
| Time-switching factor. | |
| The EH efficiency. | |
| e | Subindex for defining the RV. Here, |
| The ratio of the dispersed waves to the total power of the dominant components. | |
| An extension utilizing real values that are linked to the quantity of multipath clusters. | |
| The root-mean-square (RMS) value of the received signal envelope. | |
| The average value of the received signal envelope. | |
| The instantaneous signal-to-noise ratio (SNR). | |
| The average SNR. | |
| The shaping parameter refers to a crucial aspect of a Nakagami-m RV. | |
| The rate parameter (also known as the inverse scale parameter) represents an optimistic measure of a Gamma RV. |
| Parameters | Notations | Values |
|---|---|---|
| Power splitting factors | ||
| Threshold data rate at | Bit/s/Hz | |
| Threshold data rate at | Bit/s/Hz | |
| Time-switching factor | ||
| Coherence time block | T | 1 |
| Interference factor | ||
| Energy conversion efficiency | ||
| Monte-Carlo sample | − |
| Channels | Distribution Parameters |
|---|---|
| Rayleigh | , |
| One-sided Gaussian | , |
| Nakagami-m | , |
| Rician with parameter K | , |
| , |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tran, H.Q.; Sur, S.N.; Lee, B.M. A Comprehensive Analytical Framework under Practical Constraints for a Cooperative NOMA System Empowered by SWIPT IoT. Mathematics 2024, 12, 2249. https://doi.org/10.3390/math12142249
Tran HQ, Sur SN, Lee BM. A Comprehensive Analytical Framework under Practical Constraints for a Cooperative NOMA System Empowered by SWIPT IoT. Mathematics. 2024; 12(14):2249. https://doi.org/10.3390/math12142249
Chicago/Turabian StyleTran, Huu Q., Samarendra Nath Sur, and Byung Moo Lee. 2024. "A Comprehensive Analytical Framework under Practical Constraints for a Cooperative NOMA System Empowered by SWIPT IoT" Mathematics 12, no. 14: 2249. https://doi.org/10.3390/math12142249






