STAR-RIS-Assisted Millimeter-Wave Secure Communication with Multiple Eavesdroppers
Abstract
1. Introduction
2. System Model
2.1. Signal Model
2.2. Channel State Information
3. Problem Formulation
4. System Sum Rate Maximization
4.1. Problem Transformation
4.2. Optimization Variable Decoupling
4.3. -Procedure
4.4. SCA- and SDR-Based Iterative Algorithm
| Algorithm 1: Main loop: SCA |
|
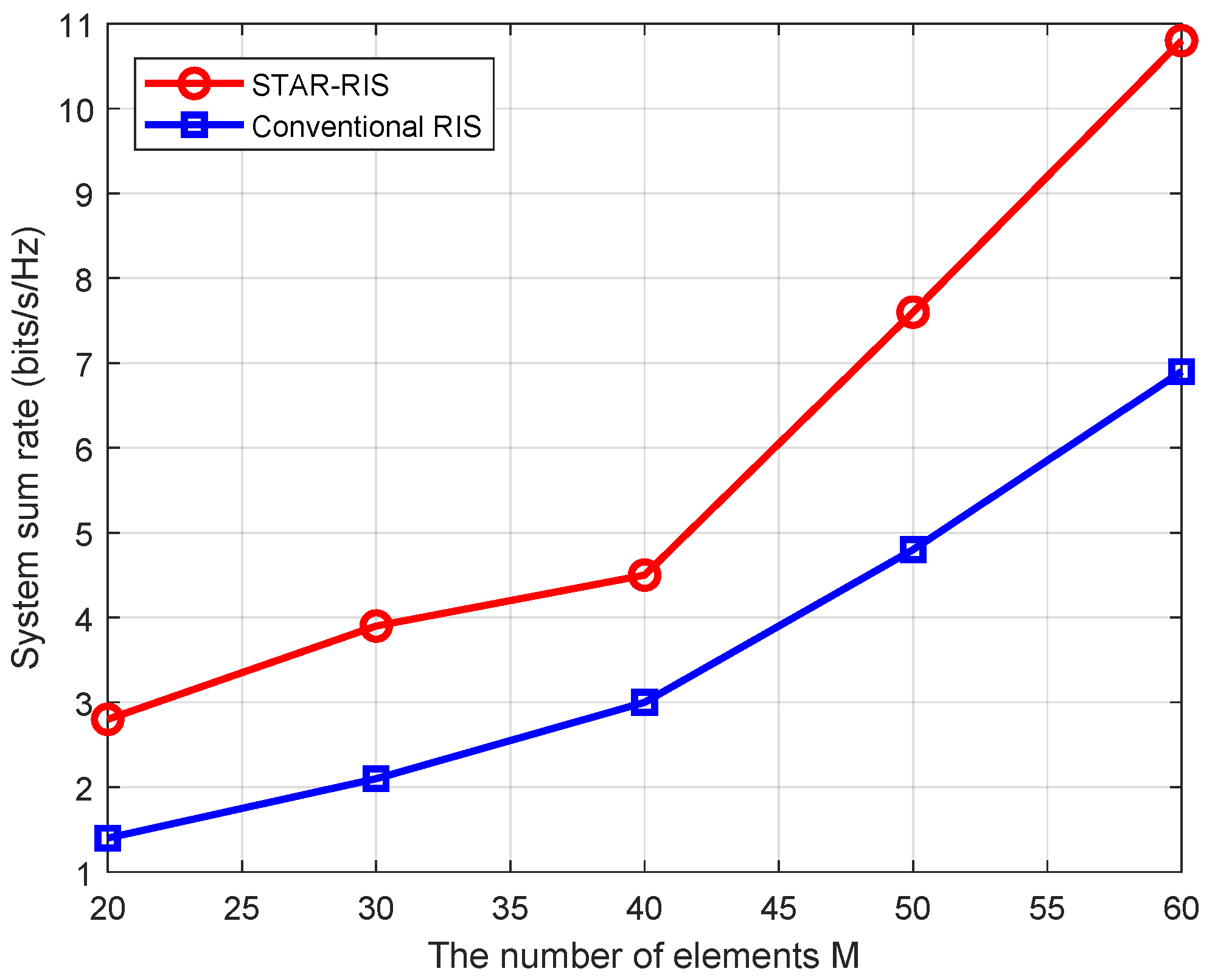
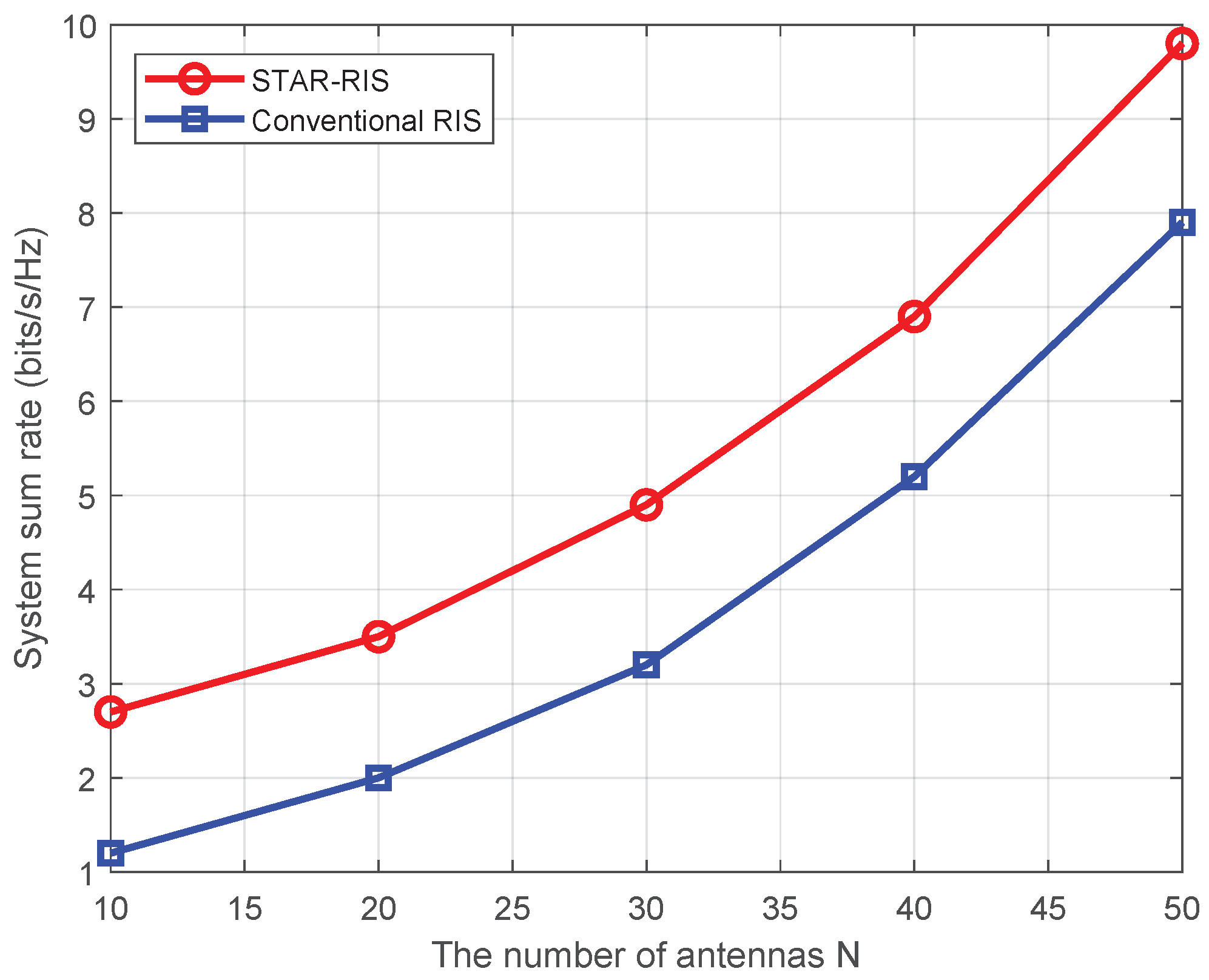
5. Simulation Results and Analysis
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Proof of Theorem 1
References
- Ghosh, A.; Thomas, T.A.; Cudak, M.C.; Ratasuk, R.; Moorut, P.; Vook, F.W.; Rappaport, T.S.; MacCartney, G.R.; Sun, S.; Nie, S. Millimeter-Wave Enhanced Local Area Systems: A High-Data-Rate Approach for Future Wireless Networks. IEEE J. Sel. Areas Commun. 2014, 32, 1152–1163. [Google Scholar] [CrossRef]
- Abari, O.; Bharadia, D.; Duffield, A.; Katabi, D. Enabling high-quality untethered virtual reality. In Proceedings of the 14th USENIX Symposium on Networked Systems Design and Implementation (NSDI 17), Boston, MA, USA, 27–29 March 2017; pp. 531–544. [Google Scholar]
- Tan, X.; Sun, Z.; Koutsonikolas, D.; Jornet, J.M. Enabling indoor mobile millimeter-wave networks based on smart reflect-arrays. In Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Honolulu, HI, USA, 15–19 April 2018; pp. 270–278. [Google Scholar]
- Nie, S.; Akyildiz, I.F. Beamforming in intelligent environments based on ultra-massive MIMO platforms in millimeter wave and terahertz bands. In Proceedings of the ICASSP 2020—2020 IEEE International Conference on Acoustics, Speech and Signal Processing, Barcelona, Spain, 4–8 May 2020; pp. 8683–8687. [Google Scholar]
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network: Joint Active and Passive Beamforming Design. In Proceedings of the 2018 IEEE Global Communications Conference (GLOBECOM), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Wu, Q.; Zhang, R. Towards Smart and Reconfigurable Environment: Intelligent Reflecting Surface Aided Wireless Network. IEEE Commun. Mag. 2020, 58, 106–112. [Google Scholar] [CrossRef]
- Qiao, J.; Alouini, M.-S. Secure Transmission for Intelligent Reflecting Surface-Assisted mmWave and Terahertz Systems. IEEE Wirel. Commun. Lett. 2020, 9, 1743–1747. [Google Scholar] [CrossRef]
- Qiao, J.; Zhang, C.; Dong, A.; Bian, J.; Alouini, M.-S. Securing Intelligent Reflecting Surface Assisted Terahertz Systems. IEEE Trans. Veh. Technol. 2022, 71, 8519–8533. [Google Scholar] [CrossRef]
- Mei, W.; Zhang, R. Cooperative beam routing for multi-IRS aided communication. IEEE Wirel. Commun. Lett. 2021, 10, 426–430. [Google Scholar] [CrossRef]
- Xu, J.; Liu, Y.; Mu, X.; Dobre, O.A. STAR-RISs: Simultaneous Transmitting and Reflecting Reconfigurable Intelligent Surfaces. IEEE Commun. Lett. 2021, 25, 3134–3138. [Google Scholar] [CrossRef]
- Lin, Z.; Lin, M.; Champagne, B.; Zhu, W.-P.; Al-Dhahir, N. Secure and Energy Efficient Transmission for RSMA-Based Cognitive Satellite-Terrestrial Networks. IEEE Wirel. Commun. Lett. 2021, 10, 251–255. [Google Scholar] [CrossRef]
- Niu, H.; Chu, Z.; Zhou, F.; Zhu, Z.; Zhang, M.; Wong, K.-K. Weighted Sum Secrecy Rate Maximization Using Intelligent Reflecting Surface. IEEE Trans. Commun. 2021, 69, 6170–6184. [Google Scholar] [CrossRef]
- Chu, Z.; Hao, W.; Xiao, P.; Mi, D.; Liu, Z.; Khalily, M.; Kelly, J.R.; Feresidis, A.P. Secrecy Rate Optimization for Intelligent Reflecting Surface Assisted MIMO System. IEEE Trans. Inf. Forensics Secur. 2021, 16, 1655–1669. [Google Scholar] [CrossRef]
- Niu, H.; Chu, Z.; Zhou, F.; Zhu, Z. Simultaneous Transmission and Reflection Reconfigurable Intelligent Surface Assisted Secrecy MISO Networks. IEEE Commun. Lett. 2021, 25, 3498–3502. [Google Scholar] [CrossRef]
- Zhang, Z.; Wang, Z.; Liu, Y.; He, B.; Lv, L.; Chen, J. Security Enhancement for Coupled Phase-Shift STAR-RIS Networks. IEEE Trans. Veh. Technol. 2023, 72, 8210–8215. [Google Scholar] [CrossRef]
- Zhang, Z.; Chen, J.; Liu, Y.; Wu, Q.; He, B.; Yang, L. On the Secrecy Design of STAR-RIS Assisted Uplink NOMA Networks. IEEE Trans. Wirel. Commun. 2022, 21, 11207–11221. [Google Scholar] [CrossRef]
- Gao, Q.; Liu, Y.; Mu, X.; Jia, M.; Li, D.; Hanzo, L. Joint Location and Beamforming Design for STAR-RIS Assisted NOMA Systems. IEEE Trans. Commun. 2023, 71, 2532–2546. [Google Scholar] [CrossRef]
- Li, X.; Zheng, Y.; Zeng, M.; Liu, Y.; Dobre, O.A. Enhancing Secrecy Performance for STAR-RIS NOMA Networks. IEEE Trans. Veh. Technol. 2023, 72, 2684–2688. [Google Scholar] [CrossRef]
- Ayach, O.E.; Rajagopal, S.; Abu-Surra, S.; Pi, Z.; Heath, R.W. Spatially sparse precoding in millimeter wave MIMO systems. IEEE Trans. Wirel. Commun. 2014, 13, 1499–1513. [Google Scholar] [CrossRef]
- Wu, Q.; Zhang, R. Intelligent Reflecting Surface Enhanced Wireless Network via Joint Active and Passive Beamforming. IEEE Trans. Wirel. Commun. 2019, 18, 5394–5409. [Google Scholar] [CrossRef]
- Faisal, M.M.A.; Nabil, M.; Kamruzzaman, M. Design and simulation of a single element high gain microstrip patch antenna for 5G wireless communication. In Proceedings of the 2018 International Conference on Innovations in Science, Engineering and Technology (ICISET), Chittagong, Bangladesh, 27–28 October 2018; pp. 290–293. [Google Scholar]
- Akdeniz, M.R.; Liu, Y.; Samimi, M.K.; Sun, S.; Rangan, S.; Rappaport, T.S.; Erkip, E. Millimeter wave channel modeling and cellular capacity evaluation. IEEE J. Sel. Areas Commun. 2014, 32, 1164–1179. [Google Scholar] [CrossRef]
- Li, R.; Wei, Z.; Yang, L.; Ng, D.W.K.; Yuan, J.; An, J. Resource allocation for secure multi-UAV communication systems with multi-eavesdropper. IEEE Trans. Commun. 2020, 68, 4490–4506. [Google Scholar] [CrossRef]
- Zhao, P.; Zhang, M.; Yu, H.; Luo, H.; Chen, W. Robust beamforming design for sum secrecy rate optimization in MU-MISO networks. IEEE Trans. Inf. Forensics Secur. 2015, 10, 1812–1823. [Google Scholar] [CrossRef]
- Yu, X.; Xu, D.; Sun, Y.; Ng, D.W.K.; Schober, R. Robust and secure wireless communications via intelligent reflecting surfaces. IEEE J. Sel. Areas Commun. 2020, 38, 2637–2652. [Google Scholar] [CrossRef]
- Ng, D.W.K.; Schober, R. Secure and green SWIPT in distributed antenna networks with limited backhaul capacity. IEEE Trans. Wireless Commun. 2015, 14, 5082–5097. [Google Scholar] [CrossRef]
- Zhou, F.; Chu, Z.; Sun, H.; Hu, R.Q.; Hanzo, L. Artificial noise aided secure cognitive beamforming for cooperative MISO-NOMA using SWIPT. IEEE J. Sel. Areas Commun. 2018, 36, 918–931. [Google Scholar] [CrossRef]
- Qin, H.; Chen, X.; Sun, Y.; Zhao, M.; Wang, J. Optimal power allocation for joint beamforming and artificial noise design in secure wireless communications. In Proceedings of the 2011 IEEE International Conference on Communications Workshops (ICC), Kyoto, Japan, 5–9 June 2011; pp. 1–5. [Google Scholar]
- Luo, Z.-Q.; Sturm, J.F.; Zhang, S. Multivariate nonnegative quadratic mappings. SIAM J. Optim. 2004, 14, 1140–1162. [Google Scholar] [CrossRef]
- Hu, C.; Dai, L.; Han, S.; Wang, X. Two-timescale channel estimation for reconfigurable intelligent surface aided wireless communications. IEEE Trans. Commun. 2021, 69, 7736–7747. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qian, B.; Qiao, J.; Zhang, C. STAR-RIS-Assisted Millimeter-Wave Secure Communication with Multiple Eavesdroppers. Mathematics 2024, 12, 2259. https://doi.org/10.3390/math12142259
Qian B, Qiao J, Zhang C. STAR-RIS-Assisted Millimeter-Wave Secure Communication with Multiple Eavesdroppers. Mathematics. 2024; 12(14):2259. https://doi.org/10.3390/math12142259
Chicago/Turabian StyleQian, Binghui, Jingping Qiao, and Chuanting Zhang. 2024. "STAR-RIS-Assisted Millimeter-Wave Secure Communication with Multiple Eavesdroppers" Mathematics 12, no. 14: 2259. https://doi.org/10.3390/math12142259
APA StyleQian, B., Qiao, J., & Zhang, C. (2024). STAR-RIS-Assisted Millimeter-Wave Secure Communication with Multiple Eavesdroppers. Mathematics, 12(14), 2259. https://doi.org/10.3390/math12142259






