Abstract
Cryptography is one of the most important branches of information security. Cryptography ensures secure communication and data privacy, and it has been increasingly applied in healthcare and related areas. As a significant cryptographic method, the Hill cipher has attracted significant attention from experts and scholars. To enhance the security of the traditional Hill cipher (THC) and expand its application in medical image encryption, a novel dynamic Hill cipher with Arnold scrambling technique (DHCAST) is proposed in this work. Unlike the THC, the proposed DHCAST uses a time-varying matrix as its secret key, which greatly increases the security of the THC, and the new DHCAST is successfully applied in medical images encryption. In addition, the new DHCAST method employs the Zeroing Neural Network (ZNN) in its decryption to find the time-varying inversion key matrix (TVIKM). In order to enhance the efficiency of the ZNN for solving the TVIKM, a new fuzzy zeroing neural network (NFZNN) model is constructed, and the convergence and robustness of the NFZNN model are validated by both theoretical analysis and experiment results. Simulation experiments show that the convergence time of the NFZNN model is about 0.05 s, while the convergence time of the traditional Zeroing Neural Network (TZNN) model is about 2 s, which means that the convergence speed of the NFZNN model is about 400 times that of the TZNN model. Moreover, the Peak Signal to Noise Ratio (PSNR) and Number of Pixel Change Rate (NPCR) of the proposed DHCAST algorithm reach 9.51 and 99.74%, respectively, which effectively validates its excellent encryption quality and attack prevention ability.
MSC:
37M99; 68U07; 68U10
1. Introduction
Today, in the era of serious threats to information security, cryptography has become an indispensable part of the field of information security, especially in the information security of images [1,2,3,4,5,6,7,8,9,10] and videos [11,12,13,14]. In the field of medicine, more than 90% of medical images of patients are processed and stored in electronic devices due to the continuous development of magnetic resonance imaging (MRI), X-ray, and other scanning and imaging technologies [15]. However, unauthorized access to medical information on the internet leads to the violation of patients’ rights [16]. In order to ensure the security of information, cryptography has been extensively researched and widely applied in various fields, including artificial intelligence [17], data transmission [18,19], information confrontation [20], and image encryption [21,22,23,24,25,26,27,28,29]. In addition, matrix theory is useful in cryptography and is commonly employed in encryption algorithms, such as the Playfair cipher [30,31], the Knapsack cipher [32,33], the Chaos cipher [34,35], the Hill cipher [36,37], etc. Generally, most encryption algorithms consist of the following five main components: plaintext, secret key, ciphertext, encryption, and decryption. Encryption algorithms are constantly evolving with technological advancements and are widely used in image encryption.
Image encryption involves transforming ordinary images into random cryptographic images for transmission. The Arnold scrambling algorithm and the Hill cipher are two important encryption methods. The Arnold scrambling algorithm [38,39] performs a permutation operation on the coordinates of each pixel of the original image to obtain new coordinates, and these new coordinates are then repeated several times to complete the permutation and realize the encryption of the image. In addition, THC is based on an algebraic approach and uses a time-invariant key matrix for encryption, which results in a weak security algorithm. Moreover, THC lacks good robustness, and the encrypted image information inevitably encounters interference during its transmission process, which will result in significant differences between the decrypted image and the initial image after receiving the image at the receiver side. Therefore, the THC is not suitable for image encryption and transmission. In the medical arena, efficiently and securely encrypting medical images at the transmitter and quickly and robustly decrypting them at the receiver has become increasingly important. However, it is difficult to ensure the security and confidentiality of the medical images during their transmission by simply using the Arnold scrambling algorithm or the THC method alone.
To address the aforementioned issues and make the Arnold scrambling algorithm and the THC method above more suitable for medical image encryption, a novel DHCAST is proposed in this work. Compared with THC, the proposed DHCAST not only inherits the intrinsic THC advantages, but also makes the obtained image ciphertext matrix time-varying and performs joint encryption with Arnold scrambling, which greatly improves the security of the THC.
However, it is worth noting that it is necessary to guarantee the efficiency and accuracy of image decryption while ensuring security. The proposed DHCAST uses a time-varying matrix as its secret key to replace the time-invariant matrix key of the THC, which leads to the received image ciphertext at the receiver also being time-varying. With this in mind, how to quickly and effectively find the TVIKM of the DHCAST for the image ciphertext decryption at the receiver becomes another thorny problem.
With the advancement of technology, new types of neural network models and algorithms are also emerging [40,41,42,43,44,45,46,47,48,49,50]. As an effective algorithm for solving time-varying problems, ZNN is widely applied in scientific and industrial fields, such as robot manipulator control [51,52,53], time-varying linear systems [54,55], the synchronization of chaotic systems [56,57,58], and time-varying matrix inversion [59,60]. Unlike traditional numerical iterative algorithms, the ZNN sufficiently takes into account the velocity compensation of the time-varying coefficients, which renders it more advantageous in dealing with time-varying problems. At first, researchers used the linear activation function to construct a ZNN model to solve time-varying problems. However, with further research, it has been found that the activation function-based ZNN model has an infinite convergence time. Therefore, the sign-bi-power activation function-based ZNN model with finite-time convergence was designed. However, the convergence time of the finite-time convergence ZNN model is dependent on the system initial value, and the system initial value is unknown in many cases, which leads to uncertainty regarding the convergence time. Therefore, ZNN models with a fixed-time convergence have appeared, and the convergence time of the fixed-time convergence ZNN models is no longer depend on system initial values.
It should be noted that noise is unavoidable during digital image transmission, and thus image encryption and decryption algorithms with noise-resistant capability should also be considered. Based on the above analysis, ZNN models with both fixed-time convergence and robustness to noise are particularly important for the DHCAST decryption.
Fuzzy theory was proposed by Zadeh in 1965. It is a theory that deals with data uncertainty and imprecision. Traditional exact mathematical models usually require that the input and output relationships of a problem are exact and unambiguous. However, in many real situations, information is often vague and uncertain due to noises and interference, and precise mathematical models may not accurately describe the problem, while fuzzy theory can provide a more flexible and realistic representation. Fuzzy theory describes the fuzzy characteristics and laws of a problem in terms of fuzzy sets, fuzzy logic operations, and fuzzy reasoning, rather than a strict mathematical model, which enables it to become a excellent tool for handling uncertainty, ambiguity, and complexity. Due to its advantages, such as flexibility and uncertainty, fuzzy theory has been continuously developed in recent years and has been widely applied in various fields, including control systems [61], artificial intelligence [62], rock engineering [63], and other application [64].
Based on the above analysis, an NFZNN model with a fuzzy activation function is constructed to solve the TVIKM of the DHCAST. The NFZNN model exhibits superior convergence and robustness for quickly solving the TVIKM of the DHCAST.
The main contributions of this paper are as follows:
- The static time-invariant key of THC is replaced with a dynamic time-varying key, and a novel dynamic Hill cipher with stronger confidentiality is obtained.
- To further enhance the security of the novel dynamic Hill cipher, the Arnold scrambling algorithm is combined with it, and a novel DHCAST is proposed in this work.
- In order to quickly and effectively find the TVIKM of the DHCAST for the image ciphertext decryption at the receiver, a NFZNN model is designed, and both the theoretical analysis and simulation results indicate that the designed NFZNN model has superior convergence and robustness for quickly solving the TVIKM of the DHCAST.
The remainder of this paper is organized as follows: the proposed DHCAST for medical image encryption is presented in Section 2. The construction of the NFZNN model for quickly solving the TVIKM of the DHCAST decryption is illustrated in Section 3. Section 4 validates the fixed time convergence and robustness of the constructed NFZNN model for solving the TVIKM of the DHCAST decryption. In Section 5, comparative simulation results of the designed NFZNN model with other existing models for solving the TVIKM of the DHCAST decryption are presented to further illustrate superior convergence and robustness of the designed NFZNN model. In addition, the MRI and cardiac ultrasound medical image encryption and decryption experiments using the proposed DHCAST are also provided. Conclusions are drawn in Section 6.
In addition, for the convenience of reading and understanding, the abbreviations for all commonly used vocabulary are presented in Table 1.

Table 1.
Summary of the abbreviations.
2. THC and the Proposed DHCAST
2.1. THC
The THC is a classic symmetric encryption algorithm proposed by Lester S. Hill in 1929, and the encryption and decryption processes of the THC are introduced below.
2.1.1. THC Encryption
- Step 1:
- The original image is transformed and stored in the plaintext pixel matrix .
- Step 2:
- Design an invertible static matrix as the secret key.
- Step 3:
- The THC encryption is performed by , where M is the ciphertext matrix.
It should be noted that the designed secret key D must be an invertible matrix.
2.1.2. THC Decryption
- Step 1:
- Calculate the inversion matrix of the secret key matrix D.
- Step 2:
- The ciphertext matrix M is multiplied by the inversion matrix , and the plaintext matrix can be obtained .
- Step 3:
- Transform the plaintext matrix I to the original information.
Based on the above THC encryption and decryption methods, it can be observed that the selection of the cipher key matrix D is very important. In addition, the secret key matrix D of THC is a time-invariant matrix, and when an attacker has a portion of the plaintext and the corresponding ciphertext, the key could be broken by comparing the ciphertext with the plaintext, and the probability of the encrypted image being cracked increases considerably, which leads to the fact that the THC is not commonly used for encrypting medical images due to its lack of sufficient confidentiality. Therefore, in order to enhance the confidentiality of THC, a novel DHCAST is proposed in this work. The proposed DHCAST not only replaces the time-invariant secret key matrix D of the THC with a time-varying secret matrix key , but also performs joint encryption with the Arnold scrambling algorithm to enhance the randomness of the cipher, which greatly improves the complexity of the cipher key and significantly increases its confidentiality. To facilitate the understanding of the proposed DHCAST, the Arnold scrambling encryption-decryption process is described in detail in the following subsections.
2.2. The Arnold Scrambling Algorithm
The Arnold scrambling algorithm was proposed by Vladimir Igorevich Arnold, and it has been widely used in image encryption. The Arnold scrambling algorithm is used to scramble the position of each pixel in the image to achieve encryption, and it is a kind of reversible scrambling. The two-dimensional Arnold scrambling algorithm with two parameters is presented as follows.
where a and b are the disorganization parameters, x and y denote the original position of an element in the pixel matrix of the image, and represent the position of the element after the pixel matrix disorganization, and N is the size of the matrix.
2.2.1. Arnold Scrambling Encryption
The above Formula (1) maps a pixel point of an image to a new coordinate . Repeating the above operation on the image can disrupt the positional information of the pixels and cause visual distortion and deformation of the original image. The detailed Arnold scrambling encryption is explained below.
- Step 1:
- Select the dislocation parameters a and b. Two-dimensional Arnold scrambling requires the determination of the dislocation parameters to control the position of the pixels in the image.
- Step 2:
- Extract the image pixels into the corresponding matrix, where n is the row and column size of the plaintext matrix.
- Step 3:
- According to Equation (1), two equations and can be derived, and then the position of each element in the image plaintext matrix is scrambled according to the above equation.
- Step 4:
- For the disordered pixel coordinates , perform Step 3 here to get the new pixel coordinates . Repeat this operation until the preset number of disorganization is reached.
- Step 5:
- Convert the disorganized pixel matrix to an encrypted image.
2.2.2. Arnold Scrambling Decryption
Arnold scrambling encryption is the process of scrambling and sorting the positional information of the pixels, while the Arnold scrambling decryption is the reversion of its encryption process. It is only necessary to perform the inverse operation on the obtained encrypted image to restore the disrupted position information to obtain the original image. Therefore, the pixel matrix of the encrypted image is extracted and restored to the original image by transforming it with the following equation:
These are the encryption and decryption processes of the Arnold scrambling algorithm.
In order to enhance the security and confidentiality of the transmitted images, the DHCAST, combining the advantages of the above THC and the Arnold scrambling algorithm, is proposed and introduced in the following subsection.
2.3. The Proposed DHCAST
2.3.1. DHCAST Encryption
- Step 1:
- The original image is transformed and stored in the plaintext pixel matrix .
- Step 2:
- The first ciphertext matrix M with scrambled pixels can be obtained by using the Arnold scramble technique. Here, the first ciphertext matrix M with scrambled pixels is time-invariant.
- Step 3:
- Choose an appropriate n-dimensional time-varying matrix as the dynamic time-varying secret key matrix for the encryption. Here, the secret key matrix is a dynamic matrix, and its element values change with time t.
- Step 4:
- The second ciphertext matrix can be obtained by . Here, the second ciphertext matrix is time-varying due to the selection of the dynamic time-varying secret key matrix .
2.3.2. DHCAST Decryption
- Step 1:
- Derive the time-varying inversion key matrix (TVIKM) of the dynamic time-varying key matrix .
- Step 2:
- Multiply the second ciphertext matrix by the above TVIKM , the first ciphertext matrix is obtained by .
- Step 3:
- The plaintext pixel matrix P can be obtained by performing the inverse transformation of Arnold permutation with the number of times set in the first ciphertext matrix obtained as in the previous subsection.
- Step 4:
- Turn the plaintext pixel matrix P into the image that the receiver side expects to obtain, and the DHCAST decryption is complete.
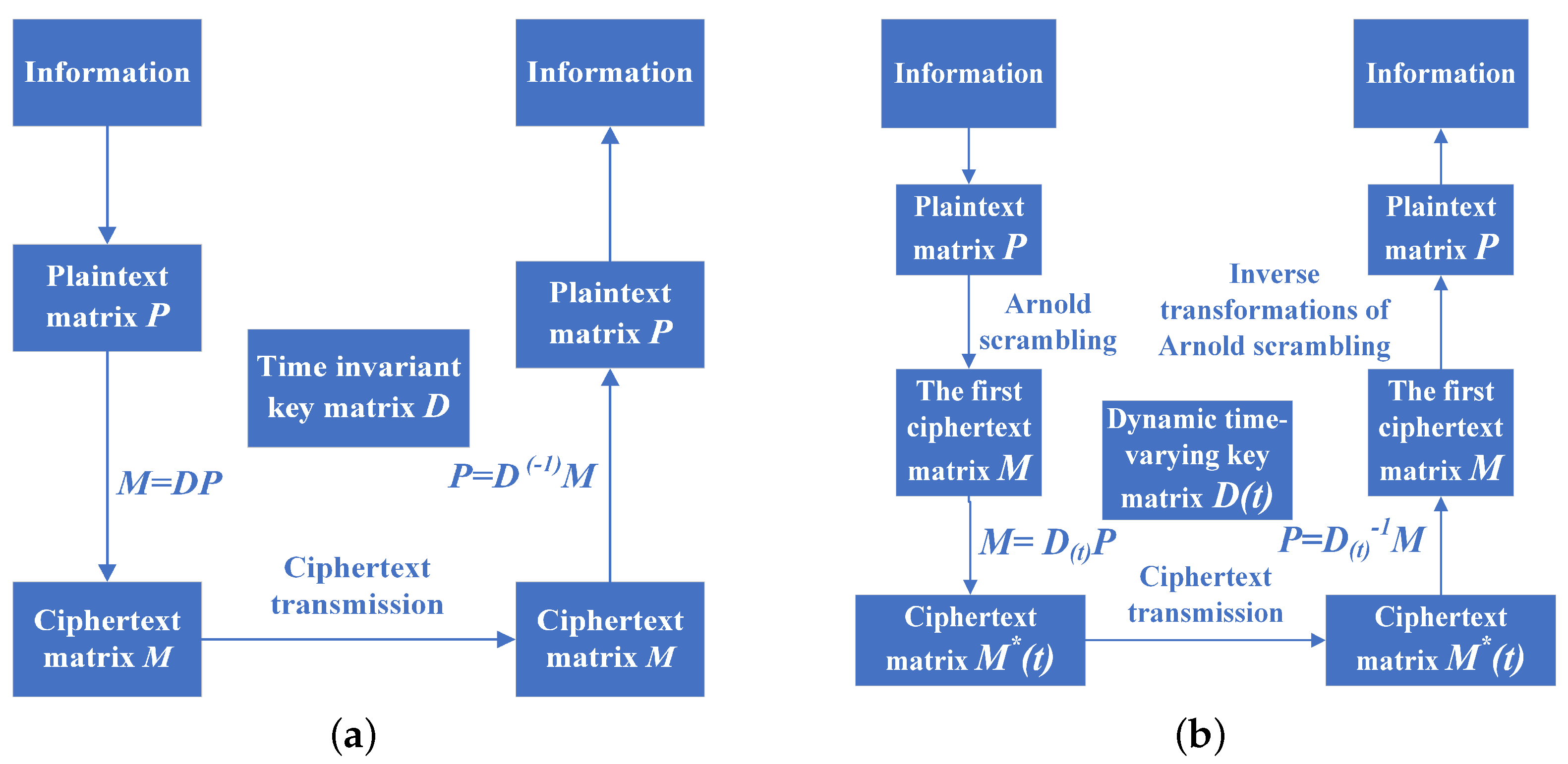
The flowcharts of the THC and the proposed DHCAST are all presented in Figure 1. From Figure 1, it can be clearly observed that the proposed DHCAST shares similar principles with the THC in terms of encryption and decryption operations; however, the static secret key matrix D of the THC is replaced with a time-varying secret matrix key in the proposed DHCAST, and the elements of the ciphertext pixel matrix of the DHCAST are time-varying. Moreover, the DHCAST performs joint encryption with the Arnold scrambling algorithm to enhance the randomness of the cipher, which greatly improves the complexity of the cipher key and significantly increases its confidentiality.
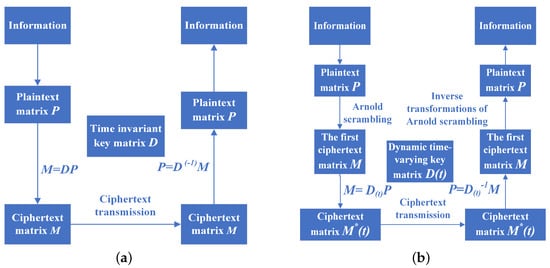
Figure 1.
The THC and proposed DHCAST. (a) The THC. (b) The proposed DHCAST.
Remark 1.
It should be noted that the proposed DHCAST uses a time-varying secret key matrix as its secret key to replace the time-invariant key matrix D of the THC, which leads to the received image pixel ciphertext matrix at the receiver also being time-varying. Thus, how to quickly and effectively find the TVIKM of the DHCAST for the image ciphertext decryption at the receiver becomes another thorny problem.
To address this issue, a NFZNN model for efficiently solving the TVIKM is constructed, and the NFZNN model will be introduced in the next section.
3. The NFZNN Model
Based on the above analysis, it is clear that efficiently solving the TVIKM is very important for the proposed DHCAST decryption. As an effective algorithm for time-varying problem-solving, a NFZNN model with considerable convergence and robustness is designed and constructed for solving the TVIKM of the proposed DHCAST.
3.1. ZNN Model
As previously stated, the ability to quickly and accurately solve the TVIKM is crucial for the successful application of the proposed DHCAST. In order to solve the TVIKM , we define the following Equation (3).
where represents a dynamic time-varying secret key matrix that is known, I is an n-dimensional unitary matrix, and is the required TVIKM matrix of the proposed DHCAST to be solved.
Generally, the ZNN model to solve the above in Equation (1) is constructed in three steps.
- Step 1:
- By analyzing Equation (3), the following error function is constructed.
- Step 2:
- After analyzing the appeal, the problem that needs to be solved now is how to make converge to 0 quickly. In order to solve this problem, we construct the following evolution formula.where > 0 is a fixed convergence factor, and and represent the activation function array and the derivatives of , respectively.
- Step 3:
- The ZNN model for solving the TVIKM matrix of the proposed DHCAST can be constructed by deriving both sides of Equation (4) simultaneously.where and represent the derivatives of and , respectively.
During the process of image decryption and transmission, external interference is inevitable. Therefore, the ZNN model used for decrypting images must have anti-interference capabilities to ensure successful image decryption and transmission under various conditions. The ZNN model with external noise is presented in Equation (7).
where is the external noise.
By analyzing previous works, it can be concluded that the activation function is an important function for the convergence of the ZNN model, and some recently reported models with commonly used activation functions are summarized in Table 2. It is worth mentioning that the constructed NFZNN model and the recently reported ZNN models in Table 2 will all be used to solve the TVIKM of the proposed DHCAST for the purpose of comparison in the the simulation experiments section. In addition, how the constructed NFZNN model will be used to solve the TVIKM will be explained in the next subsection.

Table 2.
Commonly used activation functions.
3.2. NFZNN Model
3.2.1. Fuzzy Logic System
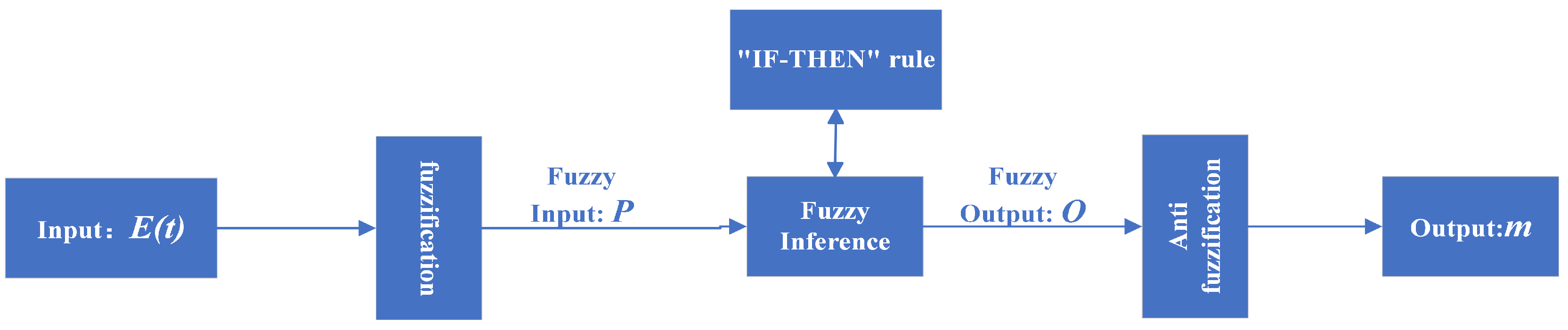
The fuzzy logic system (FLS) is widely used in the control field of nonlinear systems, and the structure of the FLS to generate the fuzzy parameter m is presented in Figure 2.
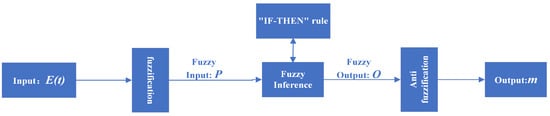
Figure 2.
The structure of FLS.
In Figure 2, the input of the FLS is a real-time variable closely related to noise, O is the real-time fuzzy output of the FLS, and m is the generated fuzzy parameter. The specific process is as follows:
- Step 1
- (Fuzzification): In a fuzzy logic system, fuzzification is the process of converting input variables from precise values to membership values in a fuzzy set. The method of fuzzification usually consists of establishing a fuzzy set, setting membership functions, calculating membership degrees, and generating several parts of the fuzzy set. In this article, a suitable fuzzy set is established, and the Gaussian membership function is used as the membership function of the FLS to transform input into fuzzy input P, thereby introducing uncertainty or fuzziness into the fuzzy logic system. The specific expression of the Gaussian membership function is as follows:
- Step 2
- (Matching fuzzy rules and conducting fuzzy inference): In this step, the main reliance is on the established Fuzzy Inference mechanism “IF-THEN” rule to infer different inputs and obtain the final inference. The relationship between fuzzy input P and fuzzy output O is defined as follows:where , , , and represent the error values of zero, small error, medium error, and large error, respectively. In addition, let , where . Then, it can be concluded that in the formula (), the symbol ⋄ represents a fuzzy operation.
- Step 3
- (Anti fuzzification): The fuzzy parameter m can be obtained by the following anti fuzzification operation.where , , , and the operation ∧ and operation ∨ denote the choice of minimum and maximum, respectively.
3.2.2. The NFAF and NFZNN Model
As mentioned in the ZNN model (7), the activation function is an important function for the convergence of the ZNN model. Therefore, a novel fuzzy activation function (NFAF) is designed below.
where m is the fuzzy parameter obtained from the above FLS, and , .
Then, the following NFZNN model (11) is realized according to the same steps employed in constructing the ZNN model (7).
4. Theoretical Analysis of the NFZNN Model
In this section, the convergence and robustness of NFZNN will be discussed in detail. To facilitate the analysis, the following Lemma 1 and two definitions are given in advance.
Lemma 1
([68]). If W(•): is a continuous radially unbounded function, and the following two conditions are fulfilled.
- (1)
- ⇔
- (2)
- Any in system (11) satisfieswhere , , and [0, +∞]. Then, the dynamic system (11) is stable within fixed-time
Definition 1.
If there exists a constant , when ∀, and , and the dynamic system (11) achieves finite-time stability, and is the settling time.
Definition 2.
If the following two conditions are satisfied:
- (1)
- The dynamic system (11) is finite-time stability;
- (2)
- For any , there exists a constant such that .
Then, dynamic system (11) achieves fixed-time stable.
Proof.
Let , and its derivative is
Then, Equation (15) can be rewritten as
From the above analysis, it can be observed that , and there always exists a constant . Let and for ∀. As a result of ⇔⇔, there exists a constant such that and for ∀. Therefore, system (12) satisfies Definition 1.
Then, taking the inverse of Equation (14) and integrating it yields
Next, Equation (18) will be discussed in the following two situations.
- (1)
- When
The following equation can be obtained through changing the integral upper limit of Equation (17).
For easy computation, let , and , then
Finally
- (2)
- When :
Let = . The derivation of the equation is = ; then, Equation (21) can transformed to the following form.
Finally
According to Definition 2, we can obtain that dynamic system (11) is stable in fixed-time
The Proof of Lemma 1 is completed. In the following subsections, the convergence and robustness of the NFZNN model will be analyzed according to Lemma 1. □
4.1. Convergence Analysis of the NFZNN Model
The following Theorem 1 guarantees the convergence of the NFZNN model (11).
Theorem 1.
If the inversion matrix of a dynamic time-varying secret key in Equation (3) exists, and the external noise , then the NFZNN model (11) will converge to the TVIKM matrix of the proposed DHCAST in fixed time .
where and is a fixed convergence factor.
Proof.
It should be noted that the NFZNN model (11) is derived from the evolutionary Formulation (5). Therefore, the fixed-time stable of evolution Formula (5) ensures the fixed-time convergence of the proposed NFZNN model (11). The evolution Formula (5) consists of n subsystems, and if all its subsystems have the aforementioned fixed-time stable property, then the proposed NFZNN model (11) is fixed-time convergence. The expression for the th subsystem of evolution Formula (5) is provided below.
The Lyapunov function is adopted to verify the fixed-time stable of the th subsystem.
By taking the derivation of the Lyapunov function , and substituting Equation (26) into the derived equation, we can obtain the follwoing Equation (27).
Because , we can obtain
Since the Lyapunov function , Equation (28) can be simplified as
Finally, according to Lemma 1, it is clear that the upper bound of convergence time of the th subsystem and the convergence time of NFZNN model (11) are
The proof of Theorem 1 is completed. □
4.2. Robustness Analysis of the NFZNN Model
It should be noted that noise is an inevitable occurrence during the proposed DHCAST decryption process. Therefore, the robustness of the NFZNN for solving the TVIKM matrix of the proposed DHCAST under different noise environments is analyzed in this subsection.
4.2.1. Time-Variant Bounded Vanishing Noise
Theorem 2.
If the inversion matrix of a dynamic time-varying secret key in Equation (3) exists, and the external noise satisfies the following inequality , then the NFZNN model (11) will converge to the TVIKM matrix of the proposed DHCAST in fixed time .
Proof.
Similarly, the th subsystem of evolution Formula (5) with time-variant bounded vanishing noise is provided below.
Construct the Lyapunov function , and the detailed proof of Theorem 2 is given below.
Firstly, the Lyapunov function is derived to obtain the following equation.
Because is a positive number, and according to the NFAF in Equation (10), we can obtain the following equation
Next, the following formula replacement is used to simplify the calculation process.
In addition, let us make the following substitutions.
Let , and the above equation can be simplified to
Then, the derivative of is obtained as
Based on the above equation, it is clear that when , and when , which means is monotonically decreasing at and monotonically increasing at , Equation (38) achieves its minimum value at , and the minimum value can be obtained by .
In accordance with Theorem 2, it follows that takes values in the range (0,), and the minimum value of is . Thus, in Equation (35), since the value of is always less than , the function is always a negative number. In bringing the Lyapunov function into the equation, then Equation (34) can be further simplified as
Finally, according to Lemma 1, it is clear that the upper bound of convergence time of the th subsystem and the convergence time of NFZNN model (11) are
The above is the theoretical Proof of Theorem 2. □
4.2.2. Time-Variant Vounded No-Vanishing Noise
Theorem 3.
If the inversion matrix of a dynamic time-varying secret key in Equation (3) exists, and the external noise satisfies the following inequality , then the NFZNN model (11) will converge to the TVIKM matrix of the proposed DHCAST in fixed time .
Proof.
Similar to the Proof of Theorem 2, the th subsystem of evolution Formula (5) with time-variant bounded vanishing noise is provided below.
Here, the Lyapunov function is chosen, and we can obtain Equation (43) following the same steps in the Proof of Theorem 2.
Because and , which leads to the fact that the value of is always a non-positive number, the above equation is further deformed, after which in the final transformed form is replaced by the Lyapunov function
According to Lemma 1, it is clear that the upper bound of convergence time of the th subsystem and the convergence time of NFZNN model (11) are
The above section is the Proof of Theorem 3. □
In this section, the above three Theorems strongly illustrate that the constructed NFZNN model with superior robustness and convergence can be theoretically applied to solve the TVIKM matrix of the proposed DHCAST.
5. Simulation Experiments of the NFZNN Model and the Proposed DHCAST
In this section, the simulation experiments of the NFZNN model and the proposed DHCAST are all provided.
Firstly, the comparative simulation results of the constructed NFZNN model with other existing models in Table 1 for solving the TVIKM matrix of the proposed DHCAST are provided. In the state diagrams, the red dashed curve represents the theoretical solution of the TVIKM matrix , and the rest of the curves represent the transient neural state solutions of the models.
Then, the simulation experiments of the proposed DHCAST for encrypting and decrypting the MRI and cardiac ultrasound images are provided to demonstrate the effectiveness and reliability of the proposed DHCAST in medical image encryption and decryption.
5.1. Two-Dimensional Time-Varying Inversion Key Matrix (TVIKM) Solving
In this subsection, comparative simulation results of the constructed NFZNN model with other existing models for solving the two-dimensional TVIKM matrix of the proposed DHCAST are provided.
Assume the following two-dimensional dynamic matrix is the time-varying key of the proposed DHCAST, and the constructed NFZNN model and other existing models are all used to find the TVIKM for the proposed DHCAST decryption.
According to in Equation (4), is the unknown TVIKM matrix of the proposed DHCAST to be solved, and this work uses the ZNN model to find the .
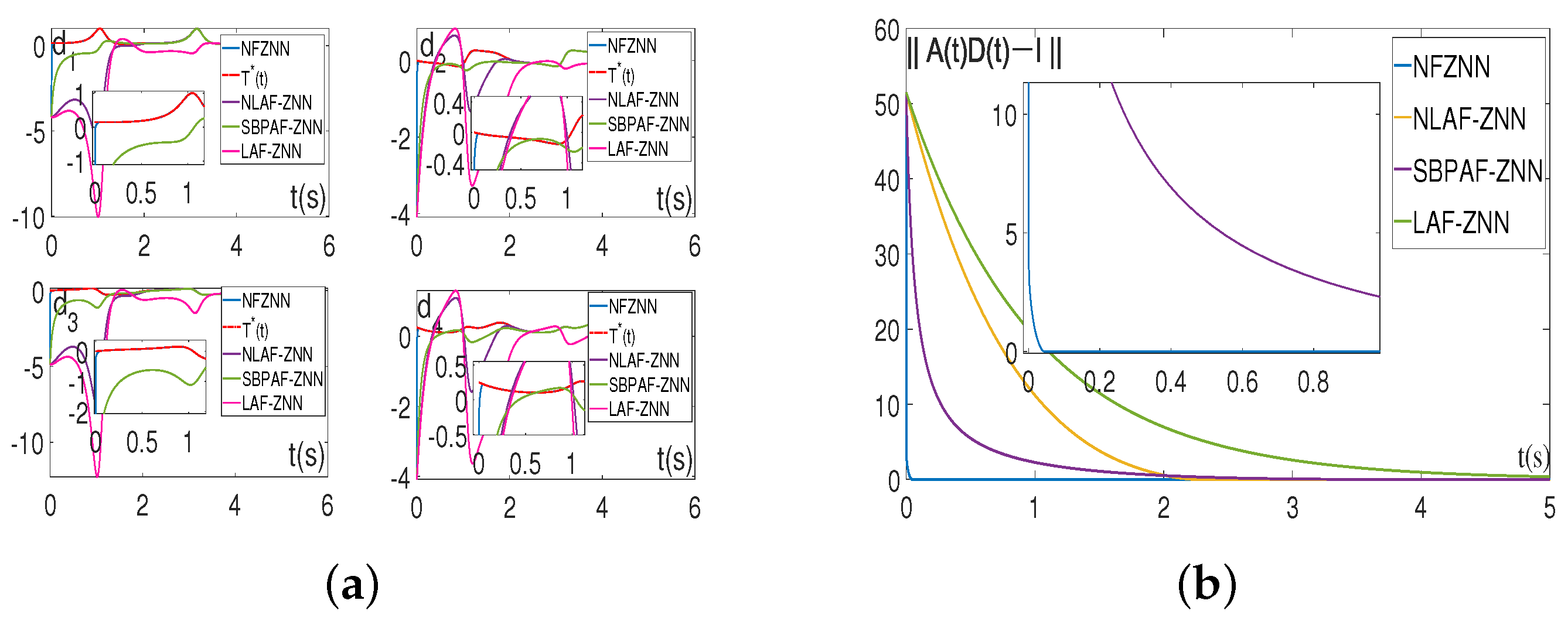
The simulation results of NFZNN and other existing models for solving the above two-dimensional TVIKM matrix under the ideal environment without noise are shown in Figure 3. Figure 3a is the state solution of all the models for solving the TVIKM matrix , and it can be intuitively observed that all the color lines are constantly approaching the red dashed line over time, from which it can be inferred that all the models can solve Equation (4) in ideal no noise environment, but the constructed NFZNN model spends the least time to find the TVIKM matrix among all the models.
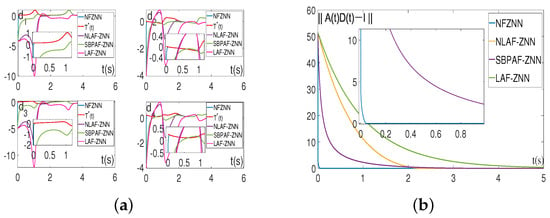
Figure 3.
State solutions and residual errors of the NFZNN and other models for solving the TVIKM without noise. (a) State solutions of the models without noise. (b) Residual errors of the models without noise.
Figure 3b shows the residual errors of all the models. Based on Figure 3b, it can be observed that the blue solid line representing the residual error of the NFZNN model converges to 0 very fast (about 0.05 s), while the errors of other models take much longer to converge to 0, which indicates that the NFZNN model has superior convergence compared to other models for solving the two-dimensional TVIKM matrix in the absence of interference.
Furthermore, noise is inevitable in the proposed DHCAST decryption, and the robustness to noise of the models should be considered. Next, the robustness of the constructed NFZNN model will be verified to ensure the successful DHCAST decryption under various noise interference situations.
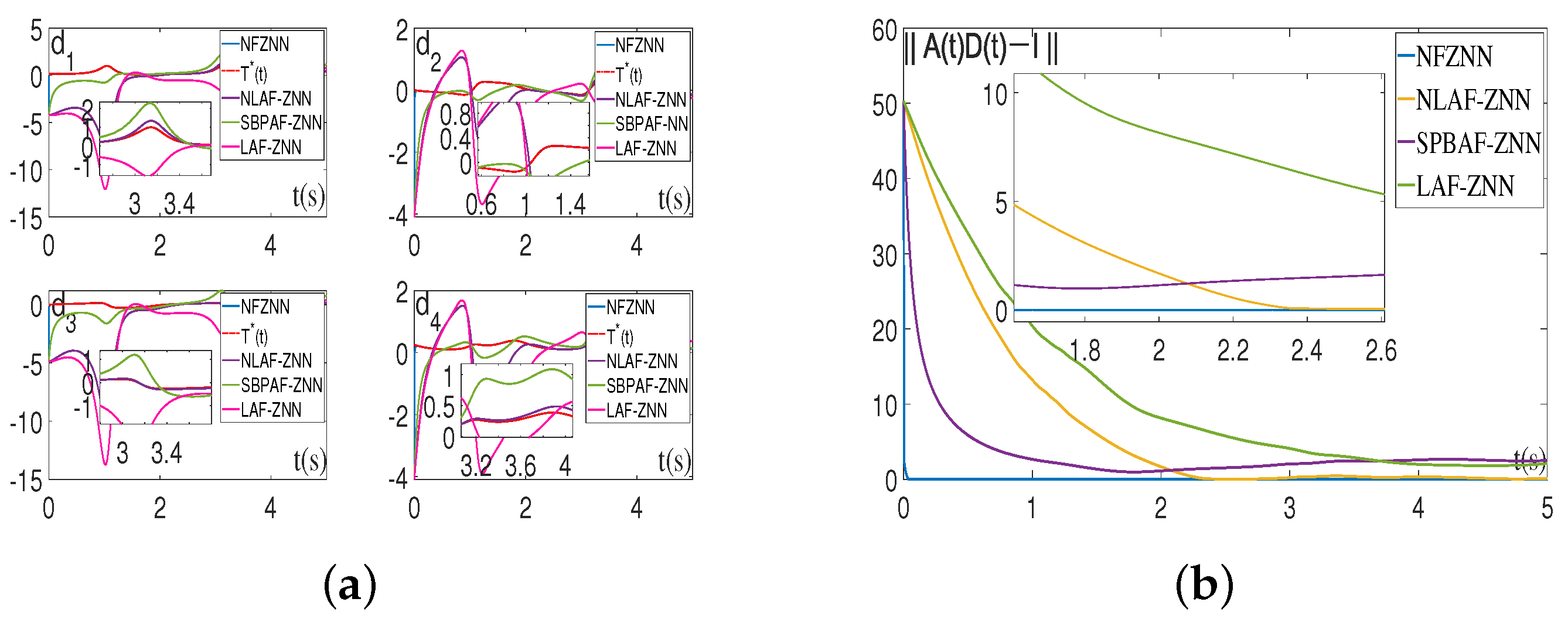
Figure 4 shows the simulation results of the NFZNN model and other existing models for solving the above two-dimensional TVIKM matrix under the combined noise . It can be clearly observed that only the neural state solutions (blue solid curves) generated by the NFZNN model quickly and robustly converge to the TVIKM matrix under the combined noise , and other solid curves representing the neural state solutions of other existing models fluctuate back and forth near the theoretical solutions or cannot approach the theoretical solution of the TVIKM matrix due to noise.
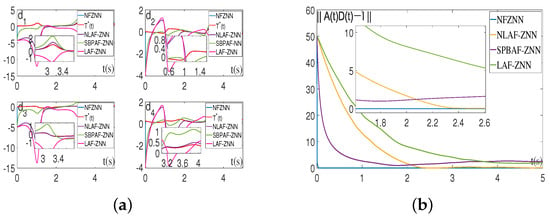
Figure 4.
State solutions and residual errors of the NFZNN model and other models for solving the TVIKM matrix with combined noises. (a) State solutions of the models with combined noises. (b) Residual errors of the models with combined noises.
Based on the above simulation results, it can be observed that the constructed NFZNN model efficiently and robustly solves the TVIKM matrix of the proposed DHCAST in various situations, and its efficiency and robustness are validated by both theoretical analysis and simulation experiments.
5.2. DHCAST Encryption and Decryption Experiments on Medical Images
The images can be divided into grayscale images and color images, and these two types of images are very common in the medical field. For example, the CT and MRI images are grayscale images, and the ultrasound images are color images. In this section, this paper uses ultrasound images from Ref. [69] and head MRI images from Ref. [70] as encrypted color and grayscale images. Afterwards, the proposed DHCAST will encrypt and decrypt these two images.
A color image usually consists of the three channels, and it can be regarded as a three-dimensional spatial matrix. For example, in a color image, the two 528s represent the pixel information in the picture, the 3 implies that the picture has the three channels, and each channel is a matrix. Similar to the color images, a grayscale image only has one channel, and the lightness and darkness of the grayscale image are depicted by the pixel values in its channel matrix.
Generally, the pixel information contained in the image is regarded as the plaintext information to be encrypted, and the encryption of a color image can be realized by encrypting its three sets of RGB channel pixel information separately. The three RGB pixel channels of the color image are extracted as the plaintext matrices , , and , while the grayscale image has only one channel to be encrypted.
In our DHCAST, the following matrices are adopted for the DHCAST time-varying keys. It is clear that the key matrices of the DHCAST are time-varying, and the element values of the key matrices will change with time. The DHCAST encryption and decryption simulation results for the ultrasound cardiology color image using these time-varying key matrices are presented in Figure 5.
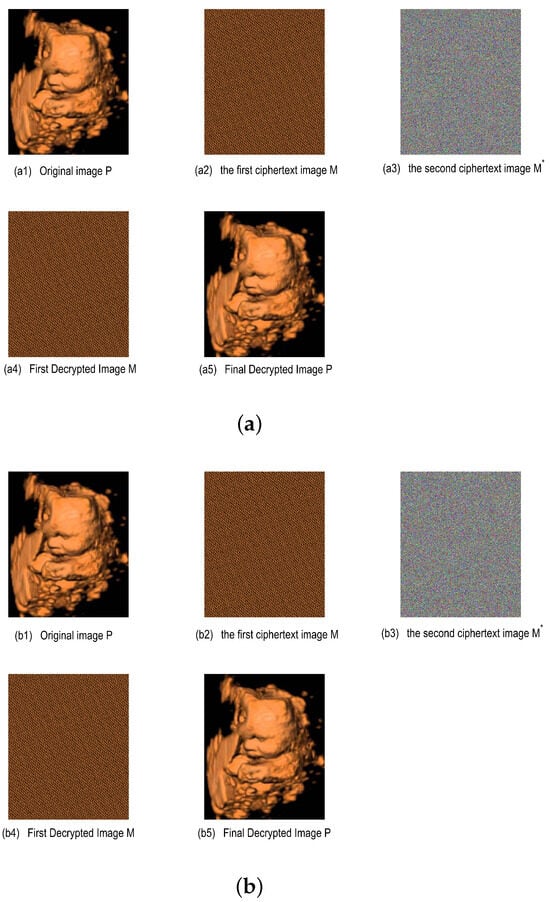
Figure 5.
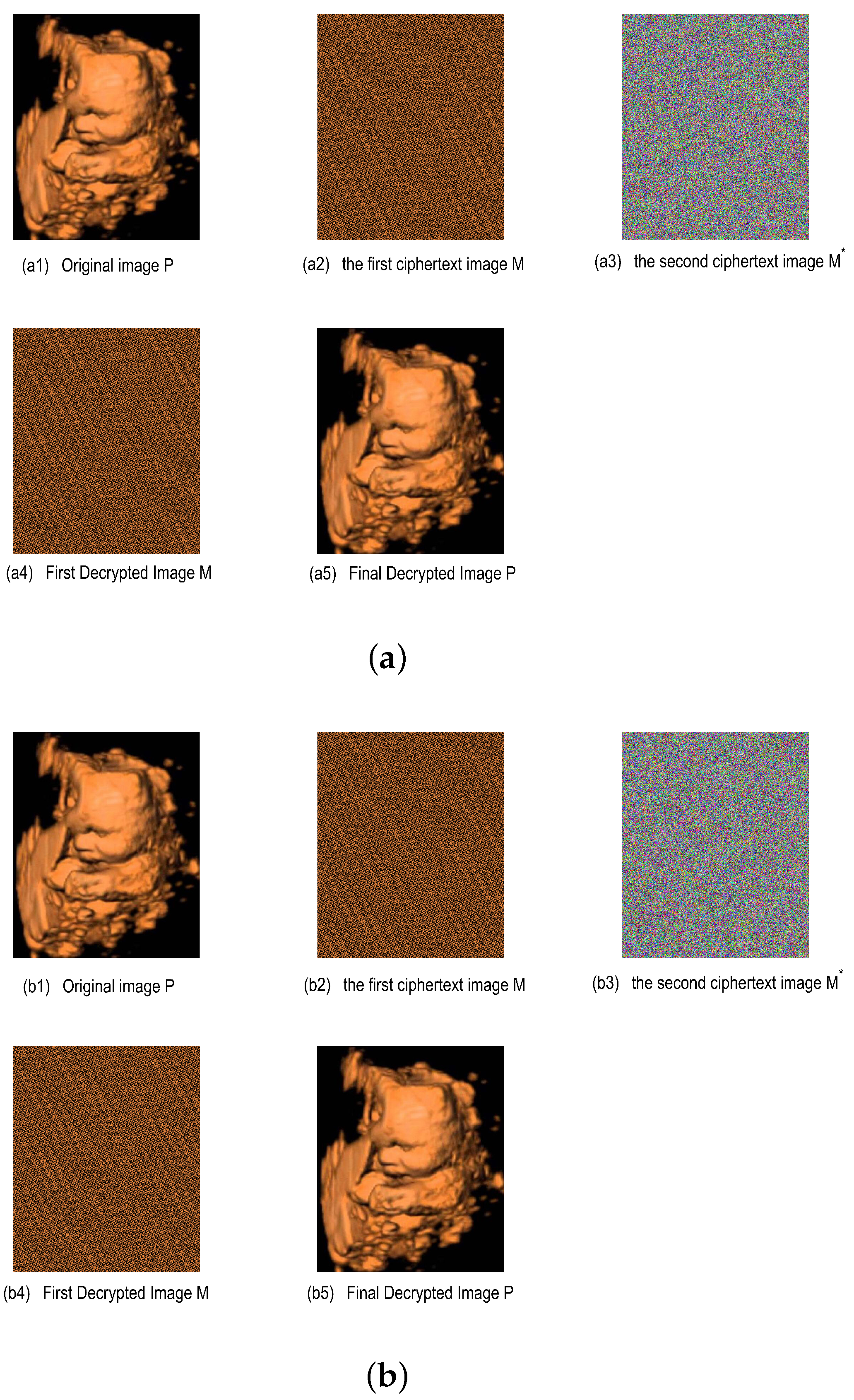
The DHCAST encryption and decryption simulation results for an ultrasound cardiology color image . (a) Key time s. (b) Key time s.
Figure 5a exhibits the proposed DHCAST encryption and decryption experiments for the ultrasound cardiology color image at time s, and Figure 5b is the proposed DHCAST encryption and decryption experiments for the ultrasound cardiology color image at time s. Figure 5a,b have the same DHCAST encryption and decryption processes; the only differences are their encryption and decryption time. Here, Figure 5a is used for detailed explanation of the proposed DHCAST.
According to the proposed DHCAST in Figure 1, Figure 5(a1) is the plaintext pixel matrices , , and ; Figure 5(a2) is the first ciphertext matrices , and after the Arnold scrambling technique; Figure 5(a3) is the second ciphertext matrices , , and . Here, the second ciphertext matrices , , and are all time-varying ciphertext matrices due to the adoption of the time-varying key matrices , , and , which greatly enhances the security of the THC.
Figure 5(a4) is the decrypted first ciphertext matrices , , and . Here, the TVKI matrices , , and are solved by the constructed NFZNN model in Section 3. Figure 5(a5) is the plaintext pixel matrices , , and , realized by performing the inverse transformation of the Arnold scrambling technique.
The proposed DHCAST encryption and decryption of grayscale images is similar to the DHCAST encryption and decryption of the RGB color images. However, there is a single channel in the grayscale image, and thus the DHCAST encryption and decryption of grayscale images is easier than the RGB color images. Figure 6 is the DHCAST encryption and decryption of the grayscale MRI images at s and s. It employs the same principles as the DHCAST encryption and decryption of RGB color images, and thus is not explained in detail here.
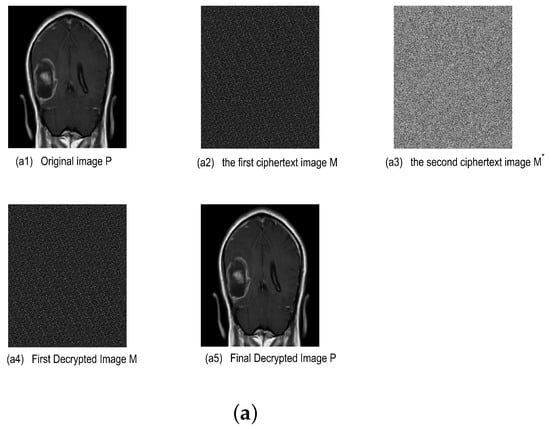

Figure 6.
The DHCAST encryption and decryption simulation results of MRI grayscale image . (a) Key time s. (b) Key time s.
Based on the experimental results in Figure 5 and Figure 6, it can be observed that the medical images can be efficiently encrypted by using DHCAST encryption, and the corresponding information from the original image can be hidden effectively after DHCAST encryption. Moreover, the corresponding information from the original image can also be effectively decrypted after the DHCAST decryption. It also should be emphasized that the proposed DHCAST not only replaces the time-invariant secret key matrix D of the THC with a time-varying secret matrix key , but also performs joint encryption with the Arnold scrambling algorithm to enhances the randomness of the ciphertext, which greatly improves the security and confidentiality of the medical images during their transmission.
5.3. Performance Comparison Analysis
In this subsection, comparative simulation results of the proposed DHCAST with other recently reported related work have been presented to demonstrate the superiority of the DHCAST algorithm.
5.3.1. Number of Pixel Change Rate (NPCR) and Uniform Average Changing Intensity (UACI)
The NPCR and UACI are important indicators for measuring the impact of encryption algorithms on pixel changes in sensitivity analysis. The specific expression of the NPCR and UACI are as follows.
where M and N are the width and height of the encrypted images, respectively. The function is defined as follows
where , are two different encrypted images of the same original image with different keys.
where M and N are the width and height of the encrypted images, and , are the pixel positions of the original image and the encrypted image, respectively.
The NPRC and UACI of the proposed DHCAST and the related work in Ref. [69] for image encryption are presented in Table 3.

Table 3.
NPCR and UACI comparison.
Based on Table 3, it can be observed that the NPCR and UACI of the proposed DHCAST algorithm reach 99.74% and 33.64%, respectively. The NPCR and UACI of the proposed DHCAST algorithm are larger than the related work in Ref. [69], which indicates that the DHCAST encryption algorithm is more sensitive to keys and has higher security.
5.3.2. Mean Square Error (MSE) and Peak Signal-to-Noise Ratio (PSNR)
The MSE and PSNR are used to evaluate the reliability of the proposed DHCAST algorithm and the quality of encrypted images. Generally, the MSE indicates the difference in pixel values between the encrypted image and the original image. The larger the MSE value, the stronger the protection ability of the encryption algorithm against brute-force cracking of encrypted images. The PSNR evaluates the quality of the encrypted image, and the smaller the PSNR value, the higher the security of the encrypted image.
The expressions of MSE and PSNR are as follows
where M and N denote the width and height of the image, and Z and E denote the original and encrypted images, respectively.
where is the maximum pixel value.
The MSE and PSNR of the proposed DHCAST and other recently reported algorithms are summarized in Table 4.

Table 4.
MSE and PSNR comparison.
Based on Table 4, it can be observed that the proposed DHCAST algorithm has a larger MSE value and a smaller PSNR compared to other algorithms, which indicates that the probability of brute force cracking risk of the proposed DHCAST is lower than other recently reported algorithms. Thus, it offers superior security for encrypted images.
6. Conclusions
In the field of cryptography, the main quest for information secrecy relates to the efficiency and security of encryption, and research on encryption is mainly focused on the improvement and refinement of the secret key contained in the cipher. In this work, a new DHCAST with a dynamic time-varying key is proposed. Unlike existing THC, the ciphertext of the DHCAST encrypts image changes with time t, which effectively prevents the possibility of password cracking and enhances the security of the transmitted information. In order to quickly solve the TVIKM matrix for the proposed DHCAST decryption, a NFZNN model is constructed. The effectiveness and robustness of the constructed NFZNN model for deriving the TVIKM matrix of the proposed DHCAST are validated by rigorous mathematical analysis and comparative simulation results. The simulation experiment results demonstrate that the constructed NFZNN model can quickly solve the TVIKM problem within 0.5 s in various complex environments. Afterwards, the proposed DHCAST with the NFZNN model is successfully applied in both MRI grayscale image and ultrasound color image encryption and decryption.
In our future work, the extension of the proposed DHCAST image encryption and decryption algorithm to other practical fields of image transmission is the main research direction. In addition, a ZNN model with superior convergence and robustness to noise should also be considered.
Author Contributions
Conceptualization, J.J. and F.Y.; methodology, Y.X.; software, Y.X. and Y.N.; validation, Y.X., Y.N. and J.J.; formal analysis, Y.X.; investigation, J.J.; resources, J.J.; data curation, Y.X.; writing—original draft preparation, Y.X., J.J. and F.Y.; writing—review and editing, Y.X., J.J. and F.Y.; visualization, Y.N.; supervision, J.J.; project administration, J.J.; funding acquisition, J.J. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by National Natural Science Foundation of China under Grant 62273141.
Data Availability Statement
The data generated and analyzed in this study are included in this published article or are available from the corresponding author upon request.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Feng, W.; Zhang, J.; Chen, Y.; Qin, Z.; Zhang, Y.; Ahmad, M.; Woźniak, M. Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Syst. Appl. 2024, 246, 123190. [Google Scholar] [CrossRef]
- Yu, F.; Zhang, W.; Xiao, X.; Yao, W.; Cai, S.; Zhang, J.; Wang, C.; Li, Y. Dynamic analysis and field-programmable gate array implementation of a 5D fractional-order memristive hyperchaotic system with multiple coexisting attractors. Fractal Fract. 2024, 8, 271. [Google Scholar] [CrossRef]
- Lai, Q.; Yang, L.; Hu, G.; Guan, Z.H.; Iu, H.H.C. Constructing Multiscroll Memristive Neural Network with Local Activity Memristor and Application in Image Encryption. IEEE Trans. Cybern. 2024, 54, 4039–4048. [Google Scholar] [CrossRef] [PubMed]
- Jin, J.; Lei, X.; Chen, C.; Li, Z. A fuzzy activation function based zeroing neural network for dynamic Arnold map image cryptography. Math. Comput. Simul. 2024, in press. [Google Scholar] [CrossRef]
- Yu, F.; Kong, X.; Yao, W.; Zhang, J.; Cai, S.; Lin, H.; Jin, J. Dynamics analysis, synchronization and FPGA implementation of multiscroll Hopfield neural networks with non-polynomial memristor. Chaos Solitons Fractals 2024, 179, 114440. [Google Scholar] [CrossRef]
- Deng, Q.; Wang, C.; Sun, Y.; Deng, Z.; Yang, G. Memristive Tabu Learning Neuron Generated Multi-Wing Attractor with FPGA Implementation and Application in Encryption. IEEE Trans. Circuits Syst. I Regul. Pap. 2024, 1–12. [Google Scholar] [CrossRef]
- Ma, X.; Wang, Z.; Wang, C. An Image Encryption Algorithm Based on Tabu Search and Hyperchaos. Int. J. Bifurc. Chaos 2024, 34, 2450170. [Google Scholar] [CrossRef]
- Yu, F.; Xu, S.; Lin, Y.; Gracia, Y.M.; Yao, W.; Cai, S. Dynamic Analysis, Image Encryption Application and FPGA Implementation of a Discrete Memristor-Coupled Neural Network. Int. J. Bifurc. Chaos 2024, 34, 2450068. [Google Scholar] [CrossRef]
- Feng, W.; Wang, Q.; Liu, H.; Ren, Y.; Zhang, J.; Zhang, S.; Qian, K.; Wen, H. Exploiting newly designed fractional-order 3D Lorenz chaotic system and 2D discrete polynomial hyper-chaotic map for high-performance multi-image encryption. Fractal Fract. 2023, 7, 887. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y. Cryptanalysis of an image encryption algorithm using quantum chaotic map and DNA coding. Expert Syst. Appl. 2024, 237, 121514. [Google Scholar] [CrossRef]
- Yu, F.; Wu, C.; Xu, S.; Yao, W.; Xu, C.; Cai, S.; Wang, C. Color video encryption transmission in IoT based on memristive hopfield neural network. Signal Image Video Process. 2024, 19, 77. [Google Scholar] [CrossRef]
- Dhingra, D.; Dua, M. Medical video encryption using novel 2D Cosine-Sine map and dynamic DNA coding. Med. Biol. Eng. Comput. 2024, 62, 237–255. [Google Scholar] [CrossRef] [PubMed]
- Yu, F.; Lin, Y.; Yao, W.; Cai, S.; Lin, H.; Li, Y. Multiscroll hopfield neural network with extreme multistability and its application in video encryption for IIoT. Neural Netw. 2024, 182, 106904. [Google Scholar] [CrossRef] [PubMed]
- Gao, S.; Iu, H.H.C.; Wang, M.; Jiang, D.; El-Latif, A.A.A.; Wu, R.; Tang, X. Design, Hardware Implementation, and Application in Video Encryption of the 2-D Memristive Cubic Map. IEEE Internet Things J. 2024, 11, 21807–21815. [Google Scholar] [CrossRef]
- Jiang, L.; Chen, L.; Giannetsos, T.; Luo, B.; Liang, K.; Han, J. Toward practical privacy-preserving processing over encrypted data in IoT: An assistive healthcare use case. IEEE Internet Things J. 2019, 6, 10177–10190. [Google Scholar] [CrossRef]
- Ding, Y.; Wu, G.; Chen, D.; Zhang, N.; Gong, L.; Cao, M.; Qin, Z. DeepEDN: A deep-learning-based image encryption and decryption network for internet of medical things. IEEE Internet Things J. 2020, 8, 1504–1518. [Google Scholar] [CrossRef]
- Radanliev, P. Artificial intelligence and quantum cryptography. J. Anal. Sci. Technol. 2024, 15, 4. [Google Scholar] [CrossRef]
- Varghese, F.; Sasikala, P. A detailed review based on secure data transmission using cryptography and steganography. Wirel. Pers. Commun. 2023, 129, 2291–2318. [Google Scholar] [CrossRef]
- Ostad-Sharif, A.; Arshad, H.; Nikooghadam, M.; Abbasinezhad-Mood, D. Three party secure data transmission in IoT networks through design of a lightweight authenticated key agreement scheme. Future Gener. Comput. Syst. 2019, 100, 882–892. [Google Scholar] [CrossRef]
- Sedlmeir, J.; Rieger, A.; Roth, T.; Fridgen, G. Battling disinformation with cryptography. Nat. Mach. Intell. 2023, 5, 1056–1057. [Google Scholar] [CrossRef]
- Kong, X.; Yu, F.; Yao, W.; Cai, S.; Zhang, J.; Lin, H. Memristor-induced hyperchaos, multiscroll and extreme multistability in fractional-order HNN: Image encryption and FPGA implementation. Neural Netw. 2024, 171, 85–103. [Google Scholar] [CrossRef] [PubMed]
- Zhang, S.; Chen, C.; Zhang, Y.; Cai, J.; Wang, X.; Zeng, Z. Multidirectional Multidouble-Scroll Hopfield Neural Network with Application to Image Encryption. IEEE Trans. Syst. Man Cybern. Syst. 2024, 1–12. [Google Scholar] [CrossRef]
- Sun, J.; Li, C.; Wang, Z.; Wang, Y. A Memristive Fully Connect Neural Network and Application of Medical Image Encryption Based on Central Diffusion Algorithm. IEEE Trans. Ind. Informatics 2024, 20, 3778–3788. [Google Scholar] [CrossRef]
- Yu, F.; Xu, S.; Lin, Y.; He, T.; Wu, C.; Lin, H. Design and Analysis of a Novel Fractional-Order System with Hidden Dynamics, Hyperchaotic Behavior and Multi-Scroll Attractors. Mathematics 2024, 12, 2227. [Google Scholar] [CrossRef]
- Lin, H.; Deng, X.; Yu, F.; Sun, Y. Grid Multibutterfly Memristive Neural Network with Three Memristive Systems: Modeling, Dynamic Analysis, and Application in Police IoT. IEEE Internet Things J. 2024, 11, 29878–29889. [Google Scholar] [CrossRef]
- Zhu, J.; Jin, J.; Chen, C.; Wu, L.; Lu, M.; Ouyang, A. A New-Type Zeroing Neural Network Model and Its Application in Dynamic Cryptography. IEEE Trans. Emerg. Top. Comput. Intell. 2024, 1–16. [Google Scholar] [CrossRef]
- Feng, W.; Zhao, X.; Zhang, J.; Qin, Z.; Zhang, J.; He, Y. Image encryption algorithm based on plane-level image filtering and discrete logarithmic transform. Mathematics 2022, 10, 2751. [Google Scholar] [CrossRef]
- Lin, H.; Deng, X.; Yu, F.; Sun, Y. Diversified Butterfly Attractors of Memristive HNN with Two Memristive Systems and Application in IoMT for Privacy Protection. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2024, 1. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y. Cryptanalyzing an image cipher using multiple chaos and DNA operations. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101612. [Google Scholar] [CrossRef]
- Das, A.K.; Das, N. Enhancement of 3D-Playfair algorithm using dual key. Int. J. Adv. Intell. Paradig. 2020, 15, 405–416. [Google Scholar] [CrossRef]
- Albahrani, E.A.; Maryoosh, A.A.; Lafta, S.H. Block image encryption based on modified playfair and chaotic system. J. Inf. Secur. Appl. 2020, 51, 102445. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Mohamed, R.; ELkomy, O.M. Knapsack Cipher-based metaheuristic optimization algorithms for cryptanalysis in blockchain-enabled internet of things systems. Ad Hoc Netw. 2022, 128, 102798. [Google Scholar] [CrossRef]
- Vambol, A. Polynomial-Time Plaintext-Recovery Attack on the Matrix-Based Knapsack Cipher. Int. J. Comput. 2020, 19, 474–479. [Google Scholar] [CrossRef]
- Dhall, S.; Pal, S.K.; Sharma, K. A chaos-based probabilistic block cipher for image encryption. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 1533–1543. [Google Scholar] [CrossRef]
- Bezerra, J.I.M.; de Almeida Camargo, V.V.; Molter, A. A new efficient permutation-diffusion encryption algorithm based on a chaotic map. Chaos Solitons Fractals 2021, 151, 111235. [Google Scholar] [CrossRef]
- Prasad, K.; Mahato, H. Cryptography using generalized Fibonacci matrices with Affine-Hill cipher. J. Discret. Math. Sci. Cryptogr. 2022, 25, 2341–2352. [Google Scholar] [CrossRef]
- Wen, H.; Lin, Y.; Yang, L.; Chen, R. Cryptanalysis of an image encryption scheme using variant Hill cipher and chaos. Expert Syst. Appl. 2024, 250, 123748. [Google Scholar] [CrossRef]
- Wei, Y.; Li, H.s.; Liu, K.; Zhao, S. Quantum video encryption based on bitplanes and improved Arnold scrambling. Quantum Inf. Process. 2024, 23, 67. [Google Scholar] [CrossRef]
- Bhatti, U.A.; Yu, Z.; Li, J.; Nawaz, S.A.; Mehmood, A.; Zhang, K.; Yuan, L. Hybrid watermarking algorithm using Clifford algebra with Arnold scrambling and chaotic encryption. IEEE Access 2020, 8, 76386–76398. [Google Scholar] [CrossRef]
- Elmoznino, E.; Bonner, M.F. High-performing neural network models of visual cortex benefit from high latent dimensionality. PLoS Comput. Biol. 2024, 20, e1011792. [Google Scholar] [CrossRef]
- Wan, Q.; Yang, Q.; Liu, T.; Chen, C.; Shen, K. Single direction, grid and spatial multi-scroll attractors in Hopfield neural network with the variable number memristive self-connected synapses. Chaos Solitons Fractals 2024, 189, 115584. [Google Scholar] [CrossRef]
- Luo, D.; Wang, C.; Deng, Q.; Sun, Y. Dynamics in a memristive neural network with three discrete heterogeneous neurons and its application. Nonlinear Dyn. 2024, 1–14. [Google Scholar] [CrossRef]
- Yao, W.; Fang, J.; Yu, F.; Xiong, L.; Tang, L.; Zhang, J.; Sun, Y. Electromagnetic radiation control for nonlinear dynamics of Hopfield neural networks. Chaos Interdiscip. J. Nonlinear Sci. 2024, 34, 073149. [Google Scholar] [CrossRef] [PubMed]
- Zhang, S.; Yao, W.; Xiong, L.; Wang, Y.; Tang, L.; Zhang, X.; Yu, F. A Hindmarsh–Rose neuron model with electromagnetic radiation control for the mechanical optimization design. Chaos Solitons Fractals 2024, 187, 115408. [Google Scholar] [CrossRef]
- Mou, J.; Cao, H.; Zhou, N.; Cao, Y. An FHN-HR Neuron Network Coupled with a Novel Locally Active Memristor and Its DSP Implementation. IEEE Trans. Cybern. 2024, 54, 7333–7342. [Google Scholar] [CrossRef]
- Zhu, R.; Zhong, G.Y.; Li, J.C. Forecasting price in a new hybrid neural network model with machine learning. Expert Syst. Appl. 2024, 249, 123697. [Google Scholar] [CrossRef]
- Zhang, S.; Li, Y.; Lu, D.; Li, C. A novel memristive synapse-coupled ring neural network with countless attractors and its application. Chaos Solitons Fractals 2024, 184, 115056. [Google Scholar] [CrossRef]
- Xu, Q.; Wang, K.; Feng, C.; Fan, W.; Wang, N. Dynamical effects of low-frequency and high-frequency current stimuli in a memristive Morris–Lecar neuron model. Chaos Solitons Fractals 2024, 189, 115646. [Google Scholar] [CrossRef]
- Wang, J.; Liu, Y.; Rao, S.; Zhou, X.; Hu, J. A novel self-adaptive multi-strategy artificial bee colony algorithm for coverage optimization in wireless sensor networks. Ad Hoc Netw. 2023, 150, 103284. [Google Scholar] [CrossRef]
- Li, J.; Wang, C.; Deng, Q. Symmetric multi-double-scroll attractors in Hopfield neural network under pulse controlled memristor. Nonlinear Dyn. 2024, 112, 14463–14477. [Google Scholar] [CrossRef]
- Zhang, Z.; Guo, J.; Chen, S.; Xu, S.; Zhang, M.; Teruo, N.; Wang, H.; Pei, Y. A Real-Time 3-D Visual Detection-Based Soft Wire Avoidance Scheme for Industrial Robot Manipulators. IEEE Trans. Syst. Man Cybern. Syst. 2024, 54, 827–840. [Google Scholar] [CrossRef]
- Jin, J.; Chen, W.; Chen, C.; Chen, L.; Tang, Z.; Chen, L.; Wu, L.; Zhu, C. A predefined fixed-time convergence ZNN and its applications to time-varying quadratic programming solving and dual-arm manipulator cooperative trajectory tracking. IEEE Trans. Ind. Inform. 2022, 19, 8691–8702. [Google Scholar] [CrossRef]
- Jin, J.; Zhu, J.; Zhou, L.; Chen, C.; Wu, L.; Lu, M.; Zhu, C.; Chen, L.; Zhao, L.; Li, Z. A Complex-Valued Variant-Parameter Robust Zeroing Neural Network Model and its Applications. IEEE Trans. Emerg. Top. Comput. Intell. 2024, 8, 1303–1321. [Google Scholar] [CrossRef]
- Jin, J.; Zhu, J.; Zhao, L.; Chen, L.; Chen, L.; Gong, J. A robust predefined-time convergence zeroing neural network for dynamic matrix inversion. IEEE Trans. Cybern. 2023, 53, 3887–3900. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Z.; Li, Z.; Yang, S. A barrier varying-parameter dynamic learning network for solving time-varying quadratic programming problems with multiple constraints. IEEE Trans. Cybern. 2021, 52, 8781–8792. [Google Scholar] [CrossRef]
- Chen, W.; Jin, J.; Chen, C.; Yu, F.; Wang, C. A disturbance suppression zeroing neural network for robust synchronization of chaotic systems and its FPGA implementation. Int. J. Bifurc. Chaos 2022, 32, 2250210. [Google Scholar] [CrossRef]
- Jin, J.; Chen, W.; Ouyang, A.; Yu, F.; Liu, H. A time-varying fuzzy parameter zeroing neural network for the synchronization of chaotic systems. IEEE Trans. Emerg. Top. Comput. Intell. 2024, 8, 364–376. [Google Scholar] [CrossRef]
- Jin, J.; Fang, J.; Chen, C.; Li, Z.; Yu, F. A complex-valued time varying zeroing neural network model for synchronization of complex chaotic systems. Nonlinear Dyn. 2024, 1–21. [Google Scholar] [CrossRef]
- Liao, B.; Han, L.; Cao, X.; Li, S.; Li, J. Double integral-enhanced Zeroing neural network with linear noise rejection for time-varying matrix inverse. CAAI Trans. Intell. Technol. 2024, 9, 197–210. [Google Scholar] [CrossRef]
- Liao, B.; Han, L.; He, Y.; Cao, X.; Li, J. Prescribed-time convergent adaptive ZNN for time-varying matrix inversion under harmonic noise. Electronics 2022, 11, 1636. [Google Scholar] [CrossRef]
- Feng, S.; Wu, H.N. Hybrid robust boundary and fuzzy control for disturbance attenuation of nonlinear coupled ODE-beam systems with application to a flexible spacecraft. IEEE Trans. Fuzzy Syst. 2016, 25, 1293–1305. [Google Scholar] [CrossRef]
- Jin, J.; Chen, W.; Chen, C.; Wu, L. Fixed-time solution of inequality constrained time-varying linear systems via zeroing neural networks. J. Frankl. Inst. 2024, 361, 106870. [Google Scholar] [CrossRef]
- Samimi Namin, F.; Rouhani, M.M. A Review: Applications of Fuzzy Theory in Rock Engineering. Indian Geotech. J. 2024, 1–18. [Google Scholar] [CrossRef]
- Jin, J.; Chen, W.; Ouyang, A.; Liu, H. Toward Fuzzy Activation Function Activated Zeroing Neural Network for Currents Computing. IEEE Trans. Circuits Syst. II-Express Briefs 2023, 70, 4201–4205. [Google Scholar] [CrossRef]
- Xiao, L.; Song, W.; Jia, L.; Li, X. ZNN for time-variant nonlinear inequality systems: A finite-time solution. Neurocomputing 2022, 500, 319–328. [Google Scholar] [CrossRef]
- Zeng, Y.; Xiao, L.; Li, K.; Li, J.; Li, K.; Jian, Z. Design and analysis of three nonlinearly activated ZNN models for solving time-varying linear matrix inequalities in finite time. Neurocomputing 2020, 390, 78–87. [Google Scholar] [CrossRef]
- Xiao, L.; Zhang, Y.; Dai, J.; Li, J.; Li, W. New noise-tolerant ZNN models with predefined-time convergence for time-variant Sylvester equation solving. IEEE Trans. Syst. Man, Cybern. Syst. 2019, 51, 3629–3640. [Google Scholar] [CrossRef]
- Chen, C.; Li, L.; Peng, H.; Yang, Y.; Mi, L.; Zhao, H. A new fixed-time stability theorem and its application to the fixed-time synchronization of neural networks. Neural Netw. 2020, 123, 412–419. [Google Scholar] [CrossRef]
- Kaur, M.; AlZubi, A.A.; Singh, D.; Kumar, V.; Lee, H.N. Lightweight Biomedical Image Encryption Approach. IEEE Access 2023, 11, 74048–74057. [Google Scholar] [CrossRef]
- Prabhavathi, K.; Anandaraju, M.; Kiran. An efficient medical image encryption algorithm for telemedicine applications. Microprocess. Microsyst. 2023, 101, 104907. [Google Scholar] [CrossRef]
- Younas, I.; Khan, M. A new efficient digital image encryption based on inverse left almost semi group and Lorenz chaotic system. Entropy 2018, 20, 913. [Google Scholar] [CrossRef]
- Khan, H.; Jamal, S.S.; Hazzazi, M.M.; Khan, M.; Hussain, I. New image encryption scheme based on Arnold map and cuckoo search optimization algorithm. Multimed. Tools Appl. 2023, 82, 7419–7441. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).