Abstract
One promising paradigm for content-centric communication is Named Data Networking (NDN), which revolutionizes data delivery and retrieval. A crucial component of NDN, producer mobility, presents new difficulties and opportunities for network optimization. This article reviews simulation strategies designed to improve NDN producer mobility. Producer mobility strategies have developed due to NDN data access needs, and these methods optimize data retrieval in dynamic networks. However, assessing their performance in different situations is difficult. Moreover, simulation approaches offer a cost-effective and controlled setting for experimentation, making them useful for testing these technologies. This review analyzes cutting-edge simulation methodologies for NDN producer mobility evaluation. These methodologies fall into three categories: simulation frameworks, mobility models, and performance metrics. Popular simulation platforms, including ns-3, OMNeT++, and ndnSIM, and mobility models that simulate producer movement are discussed. We also examine producer mobility performance indicators, such as handover data latency, signaling cost, and total packet loss. In conclusion, this comprehensive evaluation will help researchers, network engineers, and practitioners understand NDN producer mobility modeling approaches. By knowing these methodologies’ strengths and weaknesses, network stakeholders may make informed NDN solution development and deployment decisions, improving content-centric communication in dynamic network environments.
Keywords:
named data networking; producer mobility; simulation methods; performance optimization; mobility models; ns-3; OMNeT++; ndnSIM; machine learning; artificial intelligence; performance metrics MSC:
68M10; 68M12; 68M20; 68R10; 90B10; 90B18
1. Introduction
Named Data Networking (NDN), alternatively referred to as “future network technology”, is anticipated to encounter heightened expectations due to the increasing demands of the digital age beyond the original vision of its inventors. Consequently, scholars and experts in academia and industry are currently focused on advancing the next-generation network, addressing the various limitations of the emerging Internet, and assuring its sustained progress [1]. The computer business encounters substantial obstacles in effectively handling the extensive content disseminated by solutions, which include the Internet of Things (IoT), Blockchain technology, Cloud-Edge technology, and Artificial Intelligence (AI). When combined with mobility support, these technologies present unique characteristics that must be addressed in distinct ways [2]. Based on statistical data, it is anticipated that the growth rate for mobility traffic consumers could surpass that of conventional data packets [3], and the proliferation of network devices necessitating constant and widespread accessibility is experiencing a significant surge. Communication networks necessitate the incorporation of dynamic mobility.
The Transmission Control Protocol over Internet Protocol (TCP/IP) protocol is a networking architecture that operates in a persistent session, increasing network latency during mobility events for reconnection requests to be sent for each interruption in a mobility scenario. Table 1 presents the comparison between traditional Internet Protocol (IP) networking with NDN. Note that NDN’s content-centric strategy enhances content retrieval efficiency by eliminating the requirement for specific host addresses. Consumers indicate interest in the material by name, allowing for detailed and adaptable data retrieval. Hence, in-network caching and content-based routing in NDN effectively enhance bandwidth utilization. The intrinsic caching mechanism eliminates duplication and enhances overall efficacy in content dissemination. Consequently, the scalability and adaptability of NDN are enhanced by its adaptive routing and forwarding mechanisms, as well as its utilization of content-based naming. The network adapts to fluctuating circumstances, optimizing the distribution of material and incorporating content signing and verification, making security an intrinsic feature. Therefore, trustworthiness is achieved using content-centric authentication, which offers a more resilient security framework than TCP/IP.

Table 1.
Comparison TCP/IP and NDN technology.
The NDN architecture handles the issue of producer mobility by continuously updating routing tables, making it particularly suitable for situations where content producers relocate inside the network. This is a notable improvement compared to TCP/IP, which might necessitate further techniques to ensure that effective content retrieval in mobile situations smoothly integrates with edge computing by facilitating the proximity of computation to the data source. Subsequently, this is accomplished by obtaining and analyzing data locally, decreasing the need for centralized data centers, and facilitating Quality of Service by allowing for the distribution of content in a prioritized manner according to the specific needs and preferences of the user. Consumers indicate interest in data with particular specifications, and the network adjusts its supply to optimize accordingly.
In contrast, NDN operates oppositely, as content is stored within the router, continuously eliminating the need to request content from a central server. Within NDN, mobility is categorized into two distinct forms: content consumer and producer mobility. This study emphasizes the advantages of an efficient NDN architecture by examining its uses in conventional and innovative contexts. The novel NDN technology optimizes performance by reducing cache ingestion and enhancing time consumption [4]. Furthermore, the NDN architecture enables the utilization of mechanisms not supported by traditional IP-addressing communication. The NDN architecture facilitates the retrieval of incomplete data, enables translucent failover, and allows for the restoration of consumer node content [5].
NDN has persistently advanced its affiliated protocols and explored several use cases for NDN applications, encompassing video streaming, online gaming, and social networking [6]. Moreover, several organizations and enterprises have also demonstrated interest in NDN and its possible applications. Cisco has expressed the view that NDN has the potential to offer answers to the most challenging networking issues currently being encountered [7]. In a scholarly publication in 2018, scholars affiliated with Huawei Technologies examined the potential of NDN in facilitating edge computing, with the researchers exploring how NDN may enhance the efficacy and security of data transfer within edge networks [8]. Consequently, NDN technology has garnered considerable attention within the computer industry, as it can mitigate some constraints associated with conventional IP-based networking. While still in its early stages and undergoing continuous development, this architectural approach has the potential to fundamentally reshape our understanding and methods of computer network design and implementation.
The concept of producer mobility assumes significance within the NDN framework due to its profound impact on the adaptability and operational efficiency of the network. Producer mobility refers to the capability of content creators to dynamically change their location within the network, thereby influencing the manner in which consumers access and retrieve content. This attribute becomes particularly crucial in scenarios where producers are not tethered to fixed locations, a common occurrence in contemporary dynamic and distributed computing environments. In modern applications and services, content is often generated dynamically in response to user demands or system triggers [9]. Producer mobility approaches guarantee customers can easily access the latest and most relevant material, regardless of the producer’s moving location. Furthermore, NDN is specifically built to accommodate growing numbers of users and producers without issues efficiently. Producer mobility strategies are essential for optimizing resource use, guaranteeing the network’s responsiveness and efficiency even during high usage [10].
Unanticipated occurrences, such as hardware malfunctions or network divisions, might arise in dynamic networking settings. Therefore, producer mobility strategies enhance the robustness of the NDN architecture by allowing producers to move to less crowded or healthier areas of the network [11]. This minimizes service disruptions and improves fault tolerance. Other than that, NDN can improve content delivery and enhance service quality by enabling adequate producer mobility [12]. Producers can strategically position themselves to minimize the delay, enhance data transmission efficiency, and guarantee prompt and user-friendly information retrieval.
NDN mobility refers to extending the NDN architecture, facilitating efficient and uninterrupted communication inside mobile and wireless contexts. Despite being specifically built to prioritize mobility, the NDN framework encounters many obstacles that necessitate resolution to offer comprehensive support for mobile devices and users within its network. Some of the issues that arise in this context pertain to the effective management of smooth handoffs [13], modifying routing and forwarding decisions to accommodate dynamic changes in device locations [14], addressing security measures (such as the management of cryptographic keys and the revocation of digital certificates [15]), adapting to constrained resources (such as low processing power and battery capacity [16]), and addressing limited interoperability between different NDN implementations [17]. Notwithstanding these issues, NDN continues to hold promise as a viable option for content-centric networking and mobility. However, it requires substantial technical enhancements to facilitate mobility inside its network effectively.
Much research has been conducted on NDN using name resolution services, rendezvous servers, resolution managers, anchor approaches, and anchorless techniques. Continuously querying interest prefixes and updating the most recent information for direct consumer submission is being carried out for the rendezvous [18]. Note that the anchor-based [19] technique possesses functionality comparable to a rendezvous. This approach involves the monitoring and updating of information within each rendezvous node. Nevertheless, a notable distinction is that this technique will select anchor nodes from a pool of many rendezvous options. The last technique is anchorless [20], which enhances the process of directing network traffic between different locations of producer and rendezvous servers. Each technique possesses its own set of pros and cons. Certain factors can lead to increased latency during the submission of interest, while others can result in excessive processing time due to the calculation of longer routing paths for forwarding. Given the circumstances, it is advantageous to perform a detailed study of the current state of these various procedures.
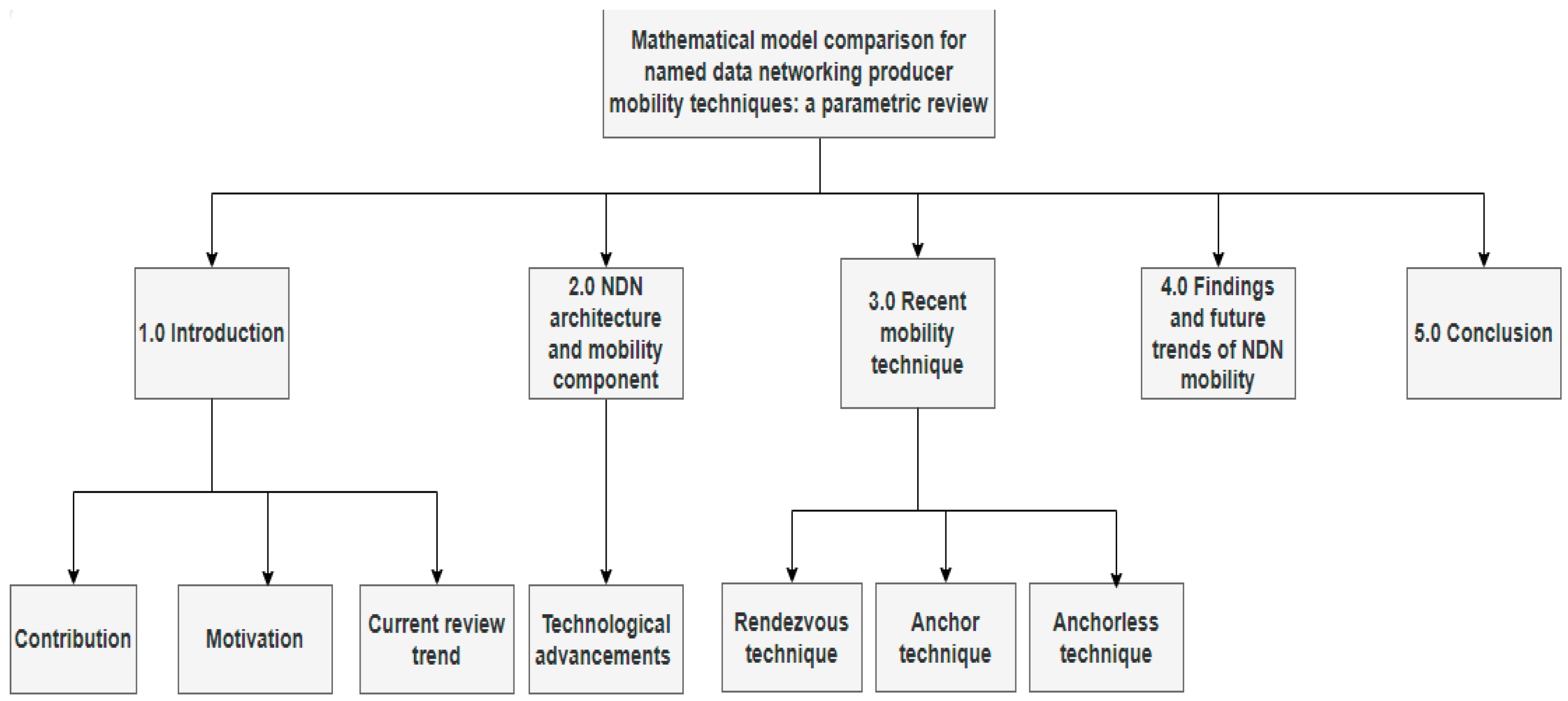
The manuscript comprises four primary portions, as illustrated in Figure 1. Section 1 provides an overview of the introduction to the NDN, encompassing its contribution and motivation, the methodology employed for selecting articles, and an outline of the manuscript. Meanwhile, Section 2 provides an exposition of the operational principles and methodologies of NDN mobility. This manuscript examines the underlying architecture and a comprehensive overview of consumer and producer mobility strategies. The following section explores critical contemporary NDN technologies, such as anchorless, dual-routing planes, locator-based, proactive handover, and rendezvous. Consequently, Section 4 explores the unresolved matters and difficulties of NDN mobility. Section 5 provides a conclusion and offers recommendations for future research.
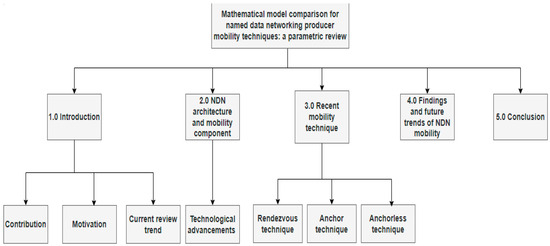
Figure 1.
Manuscript Taxonomy.
1.1. Contribution
Numerous review papers on NDN have been published that focus on various aspects of the NDN architecture, whereas mobility has yet to receive significant emphasis. Previous literature on NDN mobility primarily focused on examining NDN structure and characteristics while neglecting to explore NDN mobility resolutions and outstanding concerns. Over the past five years, a mere 50% of the reviews have addressed NDN mobility. Among the techniques considered, 33.4% pertain to anchor and anchorless approaches. Nevertheless, the scope of these mobility studies was primarily centered on consumer mobility. Therefore, the review papers in question did not address the topic of producer mobility. This article provides an overview of the NDN architecture and its operational aspects, followed by an examination of producers’ mobility strategies. The analysis is based on a review of research publications published from 2018 to 2024. This manuscript provides a complete analysis of the concerns and challenges.
The subsequent contributions of this manuscript:
- Insight into the most relevant recent review publications on mathematical models for NDN producer mobility.
- Highlighting the recent NDN mobility techniques: the Anchor technique, the Anchorless technique, and the Rendezvous technique.
- Discussing the findings and future trends of NDN hybrid mobility in aspects of architecture, features, and security.
1.2. Contribution
The NDN paradigm is a highly promising content-centric networking strategy for accommodating mobility. One primary obstacle in NDN is providing adequate mobility support for mobile devices transitioning between different locations while accessing content. Here, the rationale for developing NDN mobility is to facilitate uninterrupted access to content for mobile devices while they transition between different geographical locations. The primary objective of NDN mobility is to enhance the efficacy and effectiveness of content dissemination to mobile devices by mitigating the latency associated with content retrieval and minimizing the volume of content requiring retransmission when a mobile device traverses beyond the network’s coverage area. The next objective of NDN mobility is to facilitate effective discovery and retrieval procedures for content on mobile devices. Moreover, the NDN architecture offers enhanced support for content-centric mobility compared to the existing host-centric Internet, as content is assigned specific names and can be stored in several network locations, allowing for efficient caching. Additionally, it can enhance user satisfaction, decrease network congestion, and optimize resource allocation.
Another motivation relates to the need for a more extensive investigation of NDN producer mobility, which includes many approaches and considerations. Researchers, including Liu et al. [21] and Torres et al. [22], have examined concerns regarding cache handover and scalability solutions. Alternatively, the work by Saxena et al. [23], Shuja et al. [9], and Deebak et al. [24] solely focus on caching and scalability. Regarding mobility issues, the present NDN producer mobility approaches must be sufficient to resolve the cache, energy, handover, scalability, and security challenges connected with NDN producer mobility. Previous academic studies have recorded the impacts of enhancing the effectiveness of proposed strategies for NDN producer mobility; however, there needs to be more focus on improving the energy efficiency of transportation for NDN producers.
1.3. Current Review Trend
As presented in Table 2, 31peer-reviewed papers on NDN involving many methods have been published from 2017 to 2023. In 2017, a single paper by [25] reviewed Information Centric Networking (ICN) security and privacy for the purpose of devising possible mitigation techniques. As the years continued into 2018, three peer reviewed NDNs focused on energy, architecture, security, and vehicular. A review cover on energy conversation Host Centric Networking (HCN) focused on MANET [26], and a profound explanation of the architecture of IoT cover by [27] focused on consumer caching algorithm using the Random Replacement policy (consequently, reviewing security and vehicular [28] involved the security parameter for vehicular NDN also being discussed). The last review article from 2018 covered energy, architecture, and security [29,30,31,32,33].
Continuing into the year 2019, a combination area of energy that discusses content routing, as well as the architecture of ICN from an IoT perspective, ref. [34,35,36] and introducing linear topology for calculating memory and computation overhead [37]. An energy review paper discussed NDN MANET congestion control [38] in the year 2020 following a review by NDN over vehicular research [39,40]. It mainly covered window size for a profound explanation of vehicle parameter use. Subsequently, a single review paper on data dissemination schemes [41] focused on vehicular NDN in 2021. This review paper has discussed many parameters, such as vehicular speeds, delivery delay, transmission range, and the distance between two vehicles. A review paper on cache [42] covered implementing cache over NDN.
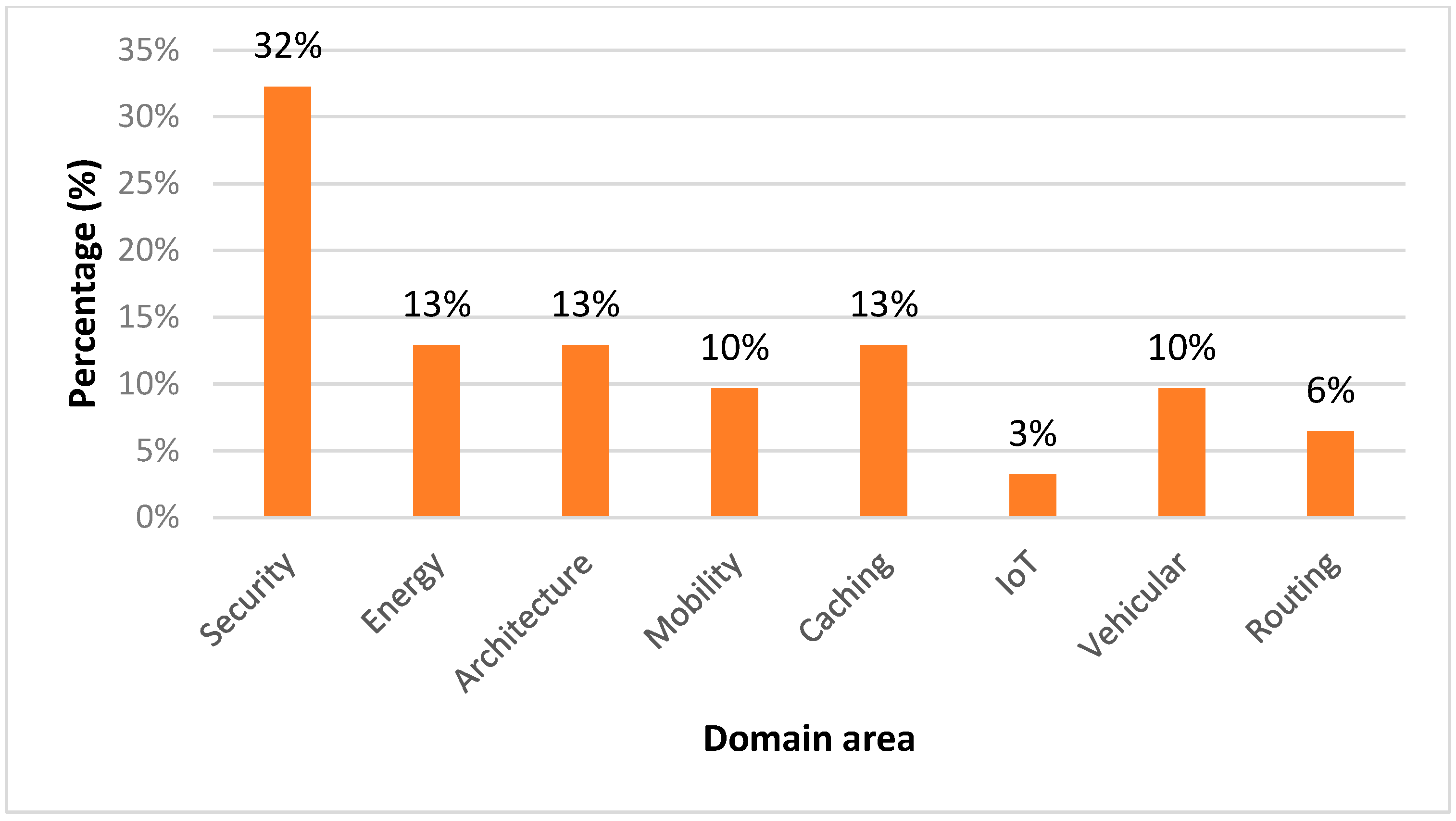
In the year 2022 there was a variety of review research from different perspectives, especially regarding vehicular NDN [43,44], security and privacy over NDN [45,46], mobility on NDN [47], as well as forwarding and routing on NDN [48]. There were significant discussions on routing, caching, and security mechanisms. Note that the latest review in 2023 was on new discussions on NDN architecture [49], application of NDN [50], technology updates over NDN [51], security and privacy concerns about NDN [52], and caching with NDN [53]. Figure 2 illustrates the percentage of review papers based on the selective domain of NDN.
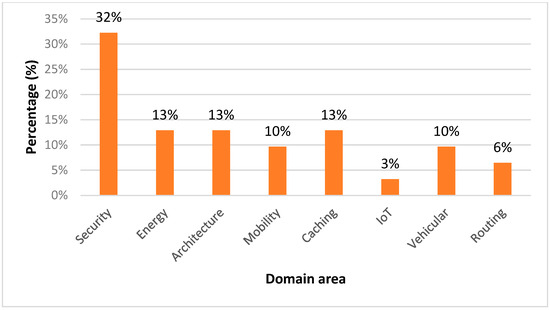
Figure 2.
Percentage review paper based on selective domain/focus area.

Table 2.
NDN review paper based on method and parameter.
Table 2.
NDN review paper based on method and parameter.
| Year | Domain/Focus Area | Reference | Simulation Tools | Method | Parameter |
|---|---|---|---|---|---|
| 2017 | security | [25] | Omnet++, SUMO, and Veins | Review | Security and privacy |
| 2018 | energy | [26] | ndnSIM and Matlab | HCN | energy |
| architecture | [27] | ndnSIM | Random-replacement (RR) policy and consumer-cache caching algorithm | Cache | |
| Security and vehicular | [28] | Review | Security | ||
| Energy, architecture, and security | [29,30,31,32] | Review | Security and privacy | ||
| 2019 | Energy, security, routing, and IoT | [34,35,36,37] | ndnSIM | Linear topology | Memory and computation overhead |
| 2020 | Energy, vehicular, cache | [38,39,40] | ndnSIM | routing | Windows size |
| 2021 | Vehicular, cache | [41,42] | ndnSIM | Mobility, bloom filter | Speed, delivery delay, transmission range, and distance between vehicles |
| 2022 | Vehicular, security, mobility, forwarding | [43,44,45,46,47,48,54,55,56,57] | Omnet++, SUMO, and Veins | Routing, caching, and security | Cache |
| 2023 | Architecture, application, technology, security, caching | [49,50,51,52,53,58] | ndnSIM | Security, caching | Interest flooding attack |
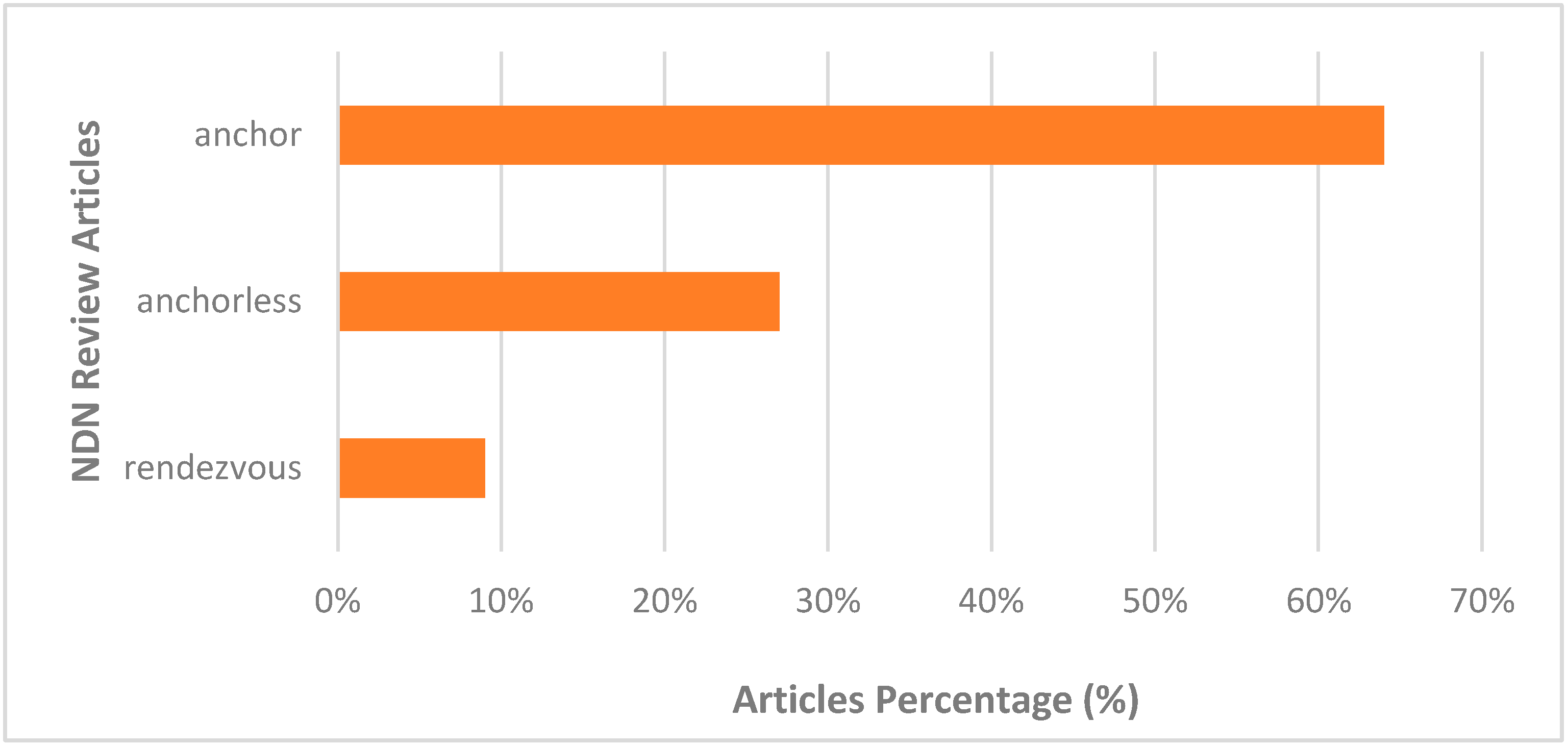
Figure 3 depicts the percentage of the NDN review articles. Based on the figure, the anchor technique is the most popular topic for discussion in a journal, reaching almost 62%, while the anchorless technique is at 29%. Fewer papers are published on the rendezvous technique, covering 9%. Therefore, the solution is to study more rendezvous techniques to determine the limitations and gaps.
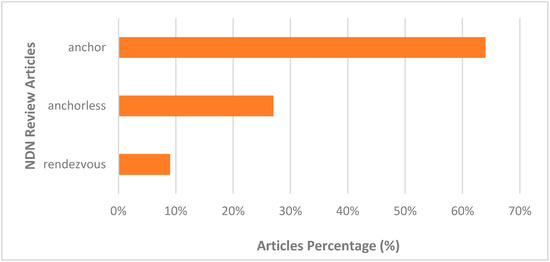
Figure 3.
NDN review article percentages.
2. NDN Architecture and Mobility Component
NDN has a distinct methodology compared to IP, prioritizing data over hosts, rendering it a more suitable choice for numerous IoT and content-centric scenarios. Within the NDN architecture, consumers transmit interest messages to producers to request specific data explicitly. If a data packet is absent in the local Content Store (CS), the interest is transmitted around the NDN network until the producer can supply the required data. Subsequently, the received data packet is stored in the CS of the NDN routers along the route for future utilization. The NDN architecture offers a versatile and effective method for retrieving and disseminating data across the Internet. Similar to the basic NDN, NDN mobility generally has consumer and producer mobility. Additionally, it offers improved security functionalities, including cryptographic signatures and a naming structure, simplifying access control and data privacy implementation. NDN mobility, like its simple counterpart, encompasses consumer and producer mobility.
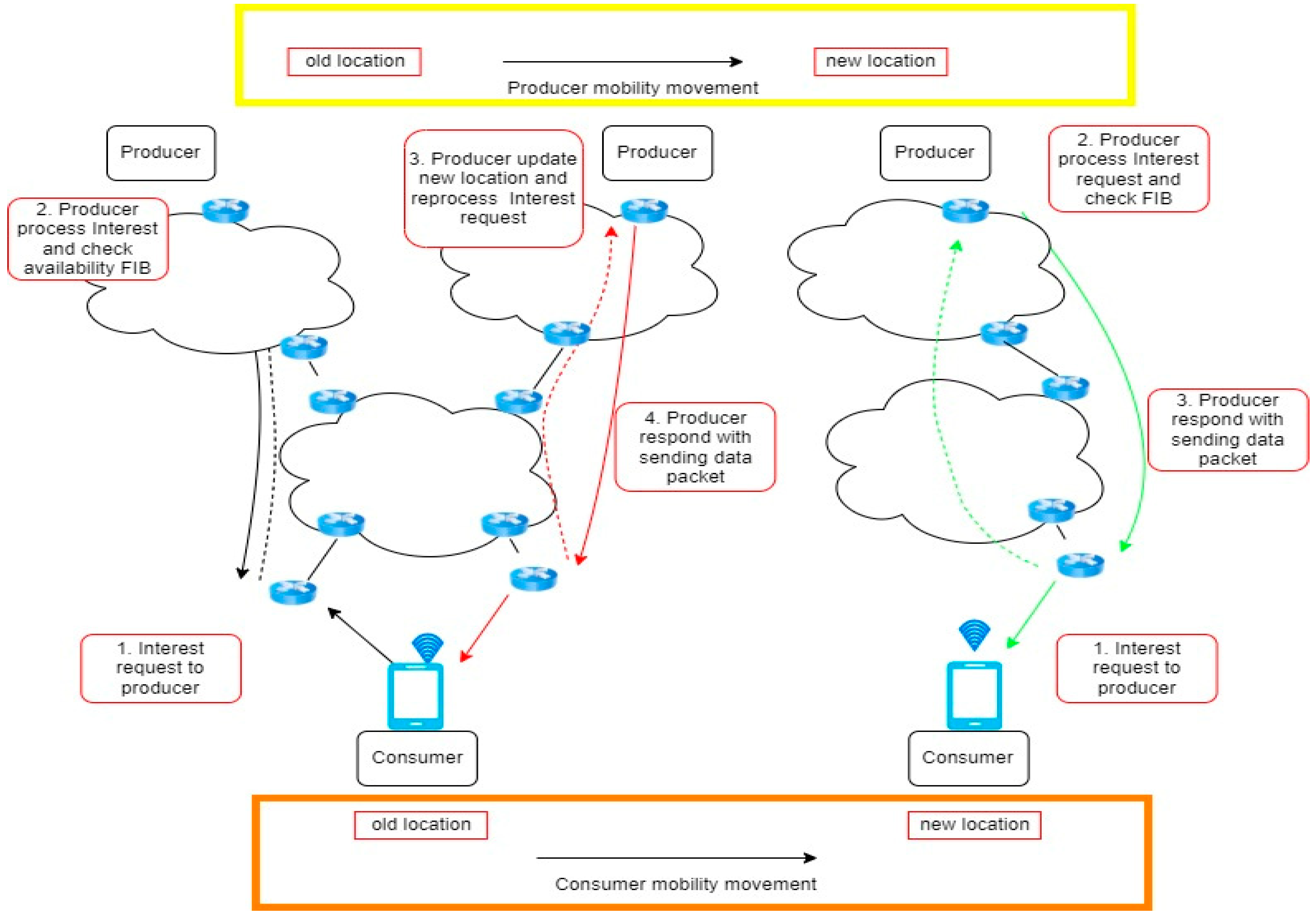
Moreover, it offers improved security functionalities, including cryptographic signatures and a naming structure, simplifying access control and data privacy implementation. NDN mobility, like its simple counterpart, encompasses consumer and producer mobility. Figure 4 illustrates the operational procedure of consumer mobility and the support provided for producer mobility.
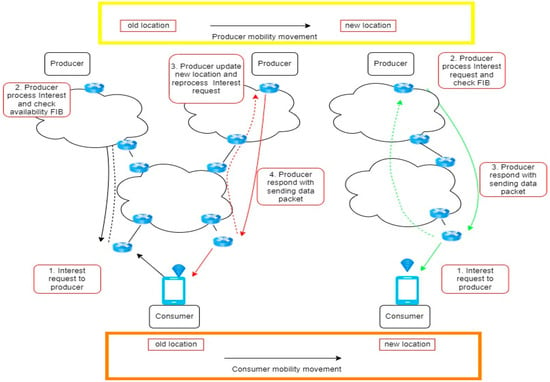
Figure 4.
Producer and consumer mobility in the NDN network.
The impact of NDN data access requirements on producer mobility strategies is significant. Consumers can efficiently retrieve content by indicating their interest in data through content names, thereby influencing the need for producer mobility solutions to enable continued access to content as producers move within the network. Effective caching solutions play a crucial role in minimizing latency and optimizing network resource utilization by storing content along the data stream. Consequently, producer mobility plans should consider the caching’s impact on content availability and the efficiency of accessing cached material. An evaluation of routing algorithms and tactics is essential to enhancing the efficiency of data packet forwarding by considering content names. This evaluation influences the design of producer mobility strategies, enabling dynamic adjustment of routing tables based on changing content source locations. Furthermore, simulation of dynamic network conditions is necessary to assess NDN’s responsiveness to changes in topology, producer mobility, and fluctuating demand patterns. Given the ever-changing nature of network conditions, producer mobility methods must adapt effectively to ensure uninterrupted access to content.
Technological Advancement NDN Producer Mobility Strategies
Recent research has focused on examining the tactics employed by producers to enhance their mobility. The Real-Time Adaptive Mobility (RAM) system implements a dynamic strategy to alter producer mobility in response to real-time changes in network conditions [59]. Other than that, it fulfills changing data access requirements by offering a dynamic and flexible approach to producer mobility in real-time situations. Machine Learning-Powered Mobility Forecasting (MLBMP) applies Machine Learning (ML) methods to forecast producer actions and enhance routing for more efficient content retrieval [60]. This proposes an intelligent method for improving the movement of producers, utilizing predictive analytics to optimize efficiency in accessing material. The study [61] examines techniques for producer mobility that prioritize energy efficiency, considering the effects on content retrieval and network resource usage. The authors acknowledge the importance of sustainability in NDN by connecting producer mobility strategies with energy-conscious concerns.
As illustrated in Figure 4, two mobility phases on NDN, for red arrow involve of producer mobility on NDN while for green arrow refer as consumer mobility on NDN. Producer mobility in NDN networks refers to moving producers from their previous positions to new places. During this process, the consumer initiates a direct request for interest from the manufacturer. Next, the producer handles the request for interest and verifies the availability of the FIB. Subsequently, the manufacturer relocates to a different site, updating the existing location and reprocessing the interest request. Upon reprocessing the request, the producer transmits the requested interest to the consumer. Concerning consumer mobility in the NDN network, the consumer transitions from one location to another remain unchanged. However, the notable distinction is that the producer handles the consumer interest request while the consumer is in motion.
NDN enables users to access the NDN network without needing specific approaches through utilizing in-network caching to deliver mobility functions. When a customer moves, the requested NDN duplicates the cache on each NDN router [62]. A study by Guo et al. [63] proposed two forwarding systems, namely flooding and smart flooding, which entail disseminating communications by sending interest packets to all active interfaces throughout the flooding process. Flooding is a direct method in which content is disseminated to all nodes in the network. This simplicity facilitates effortless implementation and reduces the need for extensive setting. Note that the decentralized character of flooding confers advantages to dynamic networks, as it prevents the need for a centralized infrastructure. Flooding inherently generates duplication, enhancing the accessibility and dependability of data. Nevertheless, this duplication could result in elevated network congestion and utilization of resources, hence affecting overall effectiveness. The primary disadvantage of flooding is the possibility of significant network congestion caused by the broadcast nature of the method. These consequences include higher latency, lower quality of service, and excessive resource usage, which diminishes its suitability for large-scale networks. Nonetheless, flooding is vulnerable to security concerns such as content contamination and unauthorized entry. Without adequate security measures, the network is susceptible to evil actions, which can jeopardize the integrity and confidentiality of data. Therefore, smart flooding frequently utilizes adaptive algorithms to react to dynamic network conditions effectively. The network’s adaptability enhances its resilience, enabling it to function effectively in dynamic contexts and under diverse workloads. As smart flooding utilizes sophisticated algorithms to distribute content intelligently, the heightened intricacy may present difficulties regarding execution, upkeep, and potential compromises with computing efficacy. Other than that, smart flooding employs adaptive decision-making mechanisms to optimize content delivery. The efficacy of bright flooding relies on the precision of these decisions, and any mistakes could impact the overall performance.
A Cluster Base Routing (CBR) model [64] has also created a method applicable to traffic situations with a high delay rate. Interest packets will be distributed periodically in congested traffic conditions with delays. Nevertheless, this method is exclusively applicable to flooding scenarios in regard to maintaining the vitality of NDN forwarding interest packets. CBR improves scalability by partitioning the network into clusters, lowering the intricacy of routing decisions, and handling a larger amount of data traffic. This clustering method effectively manages more extensive networks, enhancing scalability in NDN systems. Note that CBR minimizes control traffic in the network by limiting routing decisions to specific clusters. The reduced amount of control traffic helps mitigate congestion problems, resulting in enhanced network performance as a whole while boosting the efficiency of data retrieval by employing cluster-based architectures. This strategy enhances resource utilization by routing queries inside clusters, decreasing latency, and enhancing bandwidth efficiency. Nevertheless, the initial establishment of clusters incurs additional costs in communication and coordination. This additional cost may negatively affect the network’s effectiveness, especially during the initial setup stage, and must be handled cautiously. Hence, introducing or removing nodes in a cluster while keeping the membership dynamic adds more intricacy. The efficacy of CBR depends on resilient mechanisms for managing dynamic alterations in cluster membership while maintaining network stability as a whole. Consequently, load balancing is essential for distributing workloads evenly across clusters, reducing congestion in certain areas and guaranteeing fair allocation of resources. The effectiveness of CBR relies on its capacity to efficiently disperse workload. Therefore, load-balancing techniques must be meticulously crafted and assessed. Clustering can create weaknesses, including the risk of targeted assaults on specific clusters. Thus, strong security measures are necessary to protect against potential risks, guaranteeing the reliability and privacy of data within and between clusters.
A method for acquiring the necessary data has been implemented to enable NDN consumers to seek interest from the NDN network [6]. When a match is determined, an NDN router receives the name of the interest packet from the CS and then sends the contents back to the consumer. If there is no outcome, the router will store and enhance the packets of interest in the PIT using a forwarding method that relies on the routing and data planes. During the Pending Interest Table (PIT) stage, the NDN router initiates reverse-path procedures to retrieve the requested content. The NDN design enables customer mobility by ensuring that data packets are sent back along the path specified by the consumer interest packet. When the past and current locations coincide, the interest packet is either retransmitted from the NDN router cache or merged with previous interests without additional propagation. Correspondingly, NDN lacks any prior occurrence and fundamentally differs from the stateful data plane used in IP routing [65].
Producer mobility employs mapping-based methodologies within the NDN technology to deliver user-requested content based on location attributes [66]. This method is also employed in IP mobility technology to ascertain packet transport and consumer location. DNS servers and NDN broadcasts must detect name content based on the CN utilized. Interest packets are distributed to all user interfaces for NDN broadcast scenarios. If the broadcast function is inaccessible within the NDN network, the producer mobility will execute the latest location update and inform the closest DNS server. NDN possesses a broadcasting feature and can interface with wireless network technology. In the above case, when several users request identical data, a singular interest packet is distributed to all of them.
Nevertheless, this approach prioritizes the DNS function to mitigate the broadcast problem. Some methods, like the locator-free technique in NDN, employ DNS as a mechanism but implement it distinctly [67]. The level of complexity in NDN mobility is like that of IP mobility.
Flood-based strategies entail the distribution of material by transmitting it to every node inside the network. Although this strategy is uncomplicated and distributed, it has the potential to result in excessive repetition and congestion. When developing mathematical models for flood-based mobility, optimizing the dissemination process to minimize unnecessary costs and enhance the network’s overall efficiency is essential. Hence, the evaluation criteria should encompass scalability, latency, and bandwidth utilization [68]. Multicast-based methodologies strive to reach particular consumer groups selectively, optimizing the distribution of material to individuals who share an interest in the same information [69]. Meanwhile, mobile-centric strategies prioritize adjusting to the ever-changing motion of producers within the network [70].
Designing efficient congestion management systems is crucial to mitigating network congestion, packet loss, and overall performance deterioration due to the increasing data traffic. Congestion control optimizes resource allocation, boosts network stability, and optimizes the quality of service for customers. Here, the Interest Rate Estimation (IRE) is suggested as an adequate congestion control strategy in NDN. Considering the current network conditions, the IRE algorithm automatically adapts the rate at which interests are transmitted to avoid congestion. It uses feedback from routers to determine the network’s capacity and adapt the rate of interest expression accordingly [71]. Other than that, it also seeks to prevent congestion by adjusting the interest expression rate before network conditions change.
Integrating IRE into the NDN architecture can improve congestion control capabilities. The adaptability of IRE is in line with the content-centric nature of NDN, where interests are expressed based on content names rather than IP addresses. The dynamic adjustment of interest rates in support of NDN’s focus on efficient content retrieval is a key feature. IRE’s proactive rate adjustment helps alleviate congestion by aligning interest expression rates with network capacity, thereby reducing packet drops and the need for retransmissions. Consequently, congestion control strategies like IRE contribute to improved Quality of Service (QoS) for NDN users. Future research endeavors involve comparing IRE’s performance with conventional congestion control strategies in IP-based networks, evaluating its effectiveness in various network settings, considering factors like producer mobility and content popularity, and addressing potential implementation challenges, such as scalability issues and conflicts with other NDN functionalities. These efforts aim to refine and optimize IRE as a congestion management technique within the evolving landscape of NDN.
In contrast, NDN obtains data instead of routing packets to a mobile node. It is necessary to support producer mobility to accommodate the data generated by a mobile producer. The mobility technique employed by rendezvous, often referred to as mobile producer chasing, is utilized to ascertain the location of a mobile producer. Note that a mobile producer’s primary function is to extract data from a mobile network. An additional option is to utilize the rendezvous technique to enhance the identification of mobile data. This recently developed technique can use NDN data-centric nature in two distinct manners. Each data packet in NDN possesses distinct identification and is secure, enabling its extraction from the initial mobile producer to transmit data to a reliable and conveniently reachable location. Data rendezvous can be decoupled from the mobile producer for applications that generate data in a particular location. These strategies vary in their approach to managing the locator and optimizing the operation of mobile host handover. NDN mobility encompasses several solutions: anchor-based, anchorless-based, and rendezvous approaches.
3. Recent Mobility Techniques
Currently, there are only a limited number of NDN mobility strategies available. However, most interest in producer mobility pertains to rendezvous, anchor, and anchorless operations. Therefore, it is imperative to emphasize these three methodologies and their potential for future study adaptation. This section provides a complete description of the topology situation, forwarding method, mobility parameters of handover, and signaling cost.
Handover in the context of mobility refers to the seamless transfer of mobile transmission from an old base station to a new one, ensuring minimal disruption. It is essential, as it facilitates the establishment of data sessions between mobile devices. Moreover, handover latency and failure are prominent concerns in mobility, as they impede and interrupt service. On the other hand, the signaling cost parameter refers to the level of traffic demand that occurs when transmitting content and sending signaling messages. Consequently, ref. [72] stated that the handover rate refers to the likelihood that a consumer will transition to the next place during a single mobility time.
Handover data latency is the period that elapses between the start of a handover procedure, such as when a producer changes location, and the successful transmission of material to the consumer. It encompasses the duration required for interest packets to reach the new producer, the duration for the new producer to handle the request, and the duration for the data to travel over the network. The measurement commences at the onset of the handover procedure, usually when the consumer perceives the necessity for a handover. Correspondingly, the measurement is complete once the consumer receives the new producer’s specified content. It is essential to record time stamps at different stages of the handover process to conduct a detailed analysis. The assessment of latency’s impact should consider the fluctuating network conditions across different scenarios.
On the other hand, signaling cost refers to the additional expenses incurred due to the transmission of messages during handovers or other network events. In the context of NDN, this may encompass interest, data, or control packets explicitly associated with signaling. It examines the quantity and dimensions of signaling packets interchanged between entities throughout the handover procedure. Subsequently, it quantifies the number of signaling packets (such as interests and control messages) transmitted throughout the handover process. It also assesses the magnitude of each signaling packet to ascertain the overall amount of data linked to signaling.
Total packet loss measures the percentage or exact count of packets that fail to reach their intended destination during the handover procedure. It includes both interest and data packets that could be lost due to network circumstances or inefficiencies in the handover mechanism. Other than that, it determines the proportion of lost packets concerning the overall number of packets transmitted during the handover. Note that researchers use several simulators of mobility solutions for NDN experiments. The most popular simulator that supports NDN architecture and library is ndnSIM, which is a network simulator framework specifically developed to support study and experimentation in the NDN field. NDN is a developing network architecture that changes communication from the conventional host-centric method employed in the current Internet to a data-centric approach. Moreover, ndnSIM is constructed upon the NS-3 (Network Simulator version 3) foundation, enhancing its capabilities to simulate NDN-based communication scenarios.
Comparisons of current simulation frameworks for NDN, their constraints, and particular requirements for data access were developed. Notably, ndnSIM is an open-source simulator for NDN that seamlessly integrates with the commonly utilized ns-3 network simulator. The software offers a comprehensive implementation of the NDN protocol stack. It is compatible with various NDN-related scenarios, including precise and comprehensive implementation of the NDN protocol and integration into ns-3 for authentic network simulations. On the other hand, OMNeT++ is a framework for simulating discrete events, and the INET framework expands its capabilities to simulate networking protocols.
Existing simulation frameworks may have difficulties simulating large-scale NDN networks due to computational and memory constraints and presenting restrictions. The restricted scalability could impede the evaluation of NDN performance in situations involving many nodes and elements of content. Hence, simulations may need help in correctly capturing the intricate and dynamic nature of real-world networks. Simulation results may not adequately represent the challenges and complexities of NDN implementation in dynamic, heterogeneous contexts. Subsequently, specific simulation frameworks may need more complete implementation of all developing NDN protocol stack components. There needs to be more implementation of the protocol to allow for the investigation of specific scenarios and characteristics pertinent to the most recent advancements in NDN. Simulating NDN protocols may result in increased overhead, which can affect the precision of the simulation outcomes. Therefore, the outcomes derived from simulations may not accurately reflect the actual performance of NDN in real-world implementations.
Particular requirements for accessing data in NDN efficient mechanisms enable consumers to access material from producers in a content-centric manner. To evaluate the effectiveness of NDN in delivering requested material, simulation frameworks must precisely replicate content retrieval scenarios, as well as efficient caching mechanisms for evaluating the influence of caching on latency reduction and network resource optimization. Simulation frameworks should offer comprehensive models for caching strategies, encompassing probabilistic, collaborative, and adaptive policies. Dynamic network conditions are modeled to evaluate NDN’s ability to respond to changes in topology, producer mobility, and fluctuating demand patterns. Simulations should include scenarios with changing conditions to assess the resilience and agility of NDN.
Constraints and disadvantages in regard to using ns3, OMNeT++, and ndnSIM while enacting NDN simulations: Simulating extensive NDN scenarios can provide difficulties regarding computational resources and memory use. The limited scalability of NDN may hinder evaluating its performance in cases involving many nodes and intricate network topologies. Simulations conducted with NS-3, OMNeT++, and ndnSIM can be computationally demanding, necessitating substantial computer resources and memory. Moreover, the computational limits of practicality may restrict the scale and complexity of experiments that can be undertaken due to the high resource requirements of simulations. The learning curve for these simulation tools is relatively high, particularly for users unfamiliar with simulation environments or lacking network simulation experience. Other than that, the learning curve may impede the acquisition of these technologies, especially for academics or practitioners with simulation competence. The level of NDN protocol implementation in simulation tools can vary, and certain features or parts of the protocol may need to be adequately depicted.
Note that insufficient protocol support may restrict the investigation of particular scenarios or characteristics pertinent to the most recent advancements in NDN. The design and architecture of simulation tools may incorporate biases or assumptions that impact the authenticity of the simulated scenarios. Biases have the potential to affect the applicability of simulation findings and may not accurately capture the complexities of actual NDN deployments. Simulations conducted using NS-3, OMNeT++, and ndnSIM have the potential to operate at a significantly accelerated pace compared to real-time. This accelerated pace can affect the precision of time-sensitive events or protocols. Furthermore, the disparity between the duration of the simulation and actual time might impact the accuracy of outcomes, particularly in situations where time is of utmost importance. Simulations may need help in effectively capturing the dynamic characteristics of real-world networks by accurately capturing the complexities and intricacies of deploying NDN in dynamic and diverse situations.
The availability of updates, bug fixes, and community support may differ for this simulation software. Nevertheless, the stability and functionality of the simulation tools may be affected by a lack of community support or the use of outdated software versions. Therefore, modifying models or incorporating novel components into simulations can be intricate and time-intensive. Researchers need help when trying to simulate particular facets or experimental circumstances, which restricts the adaptability of the simulation system. Attaining interoperability among various simulation tools might pose challenges, hindering the integration of distinct models or the execution of cross-tool analysis. Consequently, the absence of smooth interoperability may impede joint research endeavors and the ability to compare outcomes across various simulation environments.
Researchers frequently utilize ndnSIM to examine mobility scenarios to evaluate the performance of the NDN architecture in dynamic situations. There are several examples of research focusing on mobility techniques, including dynamic routing strategies [45], vehicular communication [39,73], content caching [74], and forwarding strategies [75].
3.1. Rendezvous Technique
In the context of rendezvous in NDN, the term “topology situation” pertains to the organization and interconnection of nodes, explicitly emphasizing the positions of Rendezvous Points (RPs). Rendezvous stations are centralized hubs facilitating efficient data interchange between content creators and consumers. Note that implementing RPs and their strategic positioning throughout the network is vital; hence, examining various methods for choosing RPs, such as proximity-based or load-balancing techniques, can influence the effectiveness of content retrieval. Comprehending the impact of the entire network structure on the choice and effectiveness of RPs is also significant for optimizing the rendezvous model.
The forwarding mechanism in rendezvous governs transmitting material from producers to consumers through rendezvous stations. The process entails the methods via which data packets traverse the network, utilizing rendezvous sites to optimize the routing and delivery of content. It is essential to assess the efficacy of various forwarding techniques, such as direct forwarding, rendezvous-based forwarding, or a hybrid approach. An analysis of how these techniques manage the distribution of material, improve latency, and adjust to dynamic network conditions deepens our comprehension of rendezvous in NDN.
The mobility parameters of handover in rendezvous refer to how the model handles the movement of producers or consumers throughout the network. This encompasses factors such as the velocity of producer movement, the frequency of transfers, and the methods for ensuring uninterrupted content delivery during mobility events.
The signaling cost in rendezvous refers to the additional expenses of transmitting control messages to manage RPs, facilitate handovers, and coordinate between producers and consumers. Assessing the efficiency of rendezvous in NDN requires a crucial evaluation of the signaling cost. Hence, efficiently reducing the additional costs related to signaling while guaranteeing the appropriate selection of RPs and good handover management is crucial for optimizing the model’s performance. Examining the influence of signaling on network resources, latency, and scalability yields valuable information on the overall effectiveness of the rendezvous strategy.
When examining the rendezvous model in NDN, it is crucial to recognize particular constraints and establish specific assumptions to define the extent of its suitability. The limitations include scalability, dependency on RPs, management of dynamic network conditions, security and privacy implications, stable RPs, predictable behavior of producers and consumers, sufficient network connectivity, centralized coordination, and a homogeneous network environment.
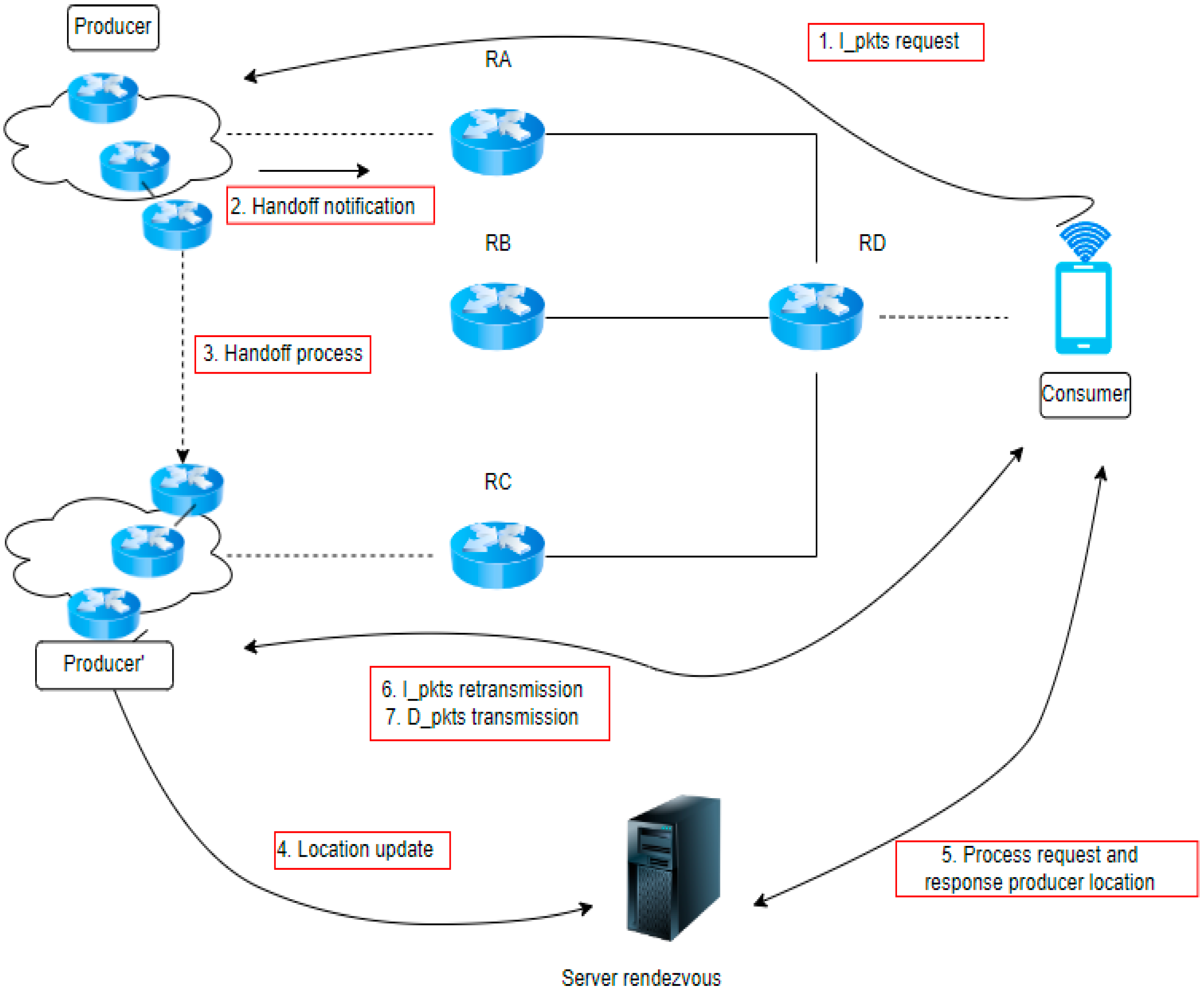
Figure 5 illustrates that the rendezvous server technology uses a mapping system, like the current DNS, to segregate the control and data planes. The initial connection between the consumer and the producer is stored in the DNS in order to match their correspondence precisely. However, the process varies when a mobile consumer or producer saves the current DNS state, as the original router cannot transfer the data update to a new router position. In such cases, a rendezvous server is required to maintain the current state of the new location.
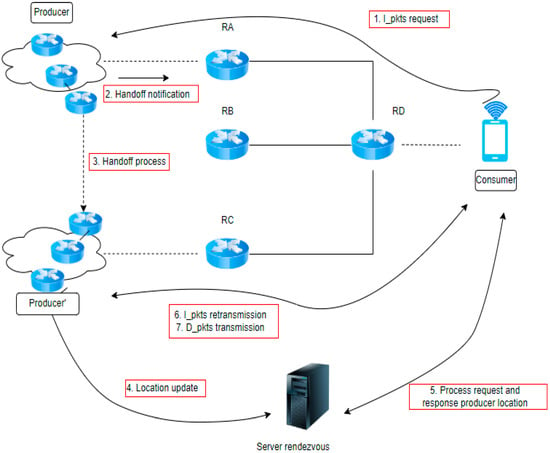
Figure 5.
NDN rendezvous technique.
Algorithm 1 outlines the rendezvous technique regarding a routing forwarding mechanism for producer mobility. The incoming customer interest is sent to the closest node in a queuing state. Assuming there is no packet loss, a NACK packet will be issued if the interest packet is not sent to the nearest node. Consequently, the producer will generate a NACK packet if the forward receives the interest packet. If there are no other loops to submit for the next-hop node currently available, receiving a data packet from the consumer is necessary.
| Algorithm 1: Algorithm to Transmit Interest Using Rendezvous Technique | |||
| Input: Interest Packet with Prefix pt Process For Consumer Request | |||
| Output: A packet send to consumer,cs | |||
| 1 | if node is the Producer then return Data; | ||
| 2 | if first time receiving Interest then return NACK; | ||
| 3 | FIFO_Q Outgoing_Q = [ ]; | ||
| 4 | foreach ⟨ ƿ, n → ɋ ⟩ in the FIB in descending order of length (ƿ) do | ||
| 5 | if ƿ is the prefix of ƿt and ɋ ≠ ςs then | ||
| 6 | enqueue (Outgoing_Q, ɋ); | ||
| 7 | while OutgoingQ ≠ [ ] do | ||
| 8 | ɋ ← dequeue (Outgoing_Q); | ||
| 9 | forward I through ɋ; | ||
| 10 | while router get a Interest do | ||
| 11 | case Data for I from ɋ do return Data; | ||
| 12 | case NACK for I from ɋ do continue; | ||
| 13 | case I from node k ≠ ɋ do send NACK to k; repeat Line 10 | ||
| 14 | return NACK; | ||
Signaling cost is defined by Equation (1), handover latency for the rendezvous strategy is described by Equation (2), and Table 3 displays the metrics associated with these equations.
δrendz = Σ (δProduser + δRA + δRB + δRC + δRD + δConsumer + δProduser′)
= ϨINT × (α + ç) + Ϩdata × (α + ç),
= ϨINT × (α + ç) + Ϩdata × (α + ç),
£rendz = ((ÞT ÞT + (lpn/v)) + (1 − (ÞT ÞT + (lpn/v)))) × (lpn + α × dwlrendz + 2ç × dwlrendz + α × dwlint + ç × dwint).

Table 3.
Rendezvous equation metrics.
3.2. Anchor Technique
In the context of anchor in NDN, the topology situation refers to the organization and interconnection of nodes, explicitly emphasizing the positions of anchor points. Anchor points function as pivotal hubs that streamline the process of retrieving content by overseeing the exchange of information between creators and users. Hence, analyzing the strategic placement of anchor points in the network is essential. The overall efficiency of information distribution can be influenced by various strategies for picking anchor points, such as hierarchical or distributed approaches. Other than that, comprehending the impact of network topology on the choice and effectiveness of anchor points aids in optimizing the anchor model.
The forwarding technique in anchor specifies how content is transmitted from producers to consumers via the anchor points. The process entails the methods by which data packets navigate the network, utilizing anchor points to route and deliver content effectively. It is essential to assess the efficacy of various forwarding techniques, such as direct forwarding, anchor-based forwarding, or hybrid approaches. Gaining insight into how these techniques manage data dissemination, improve response time, and adjust to fluctuations in network conditions improves comprehension of an anchor in NDN.
The mobility characteristics of handover in anchor pertain to the model’s ability to handle the migration of producers or consumers within the network. This encompasses factors such as the velocity of producer movement, the frequency of transitions, and the methods for ensuring uninterrupted content delivery during mobility events. It is essential to analyze how the anchor adjusts to dynamic changes in the locations of producers and consumers. This entails assessing the time it takes to transfer control from one system to another, the capability to choose suitable reference points during movement instances, and the influence of movement parameters on the effectiveness of retrieving content.
The signaling cost in anchor refers to the additional expenses from transmitting control messages to manage anchor points, facilitate handovers, and coordinate between producers and consumers. Assessing the efficiency of anchors in NDN requires a crucial evaluation of the signaling cost. Optimizing the model’s performance requires minimizing the signaling overhead while guaranteeing good anchor point selection and handover management. Examining the influence of signaling on network resources, latency, and scalability yields valuable information on the overall effectiveness of the anchor method.
When examining the anchor model in NDN, it is crucial to recognize particular constraints and establish specific assumptions to define the scope of its applicability. The system’s limitations include static anchor points, dependency on anchor points, handling dynamic network conditions, scalability concerns, and security and privacy implications. On the other hand, the system assumes stable anchor points, predictable producer and consumer behavior, adequate network connectivity, centralized coordination, and a homogeneous network environment.
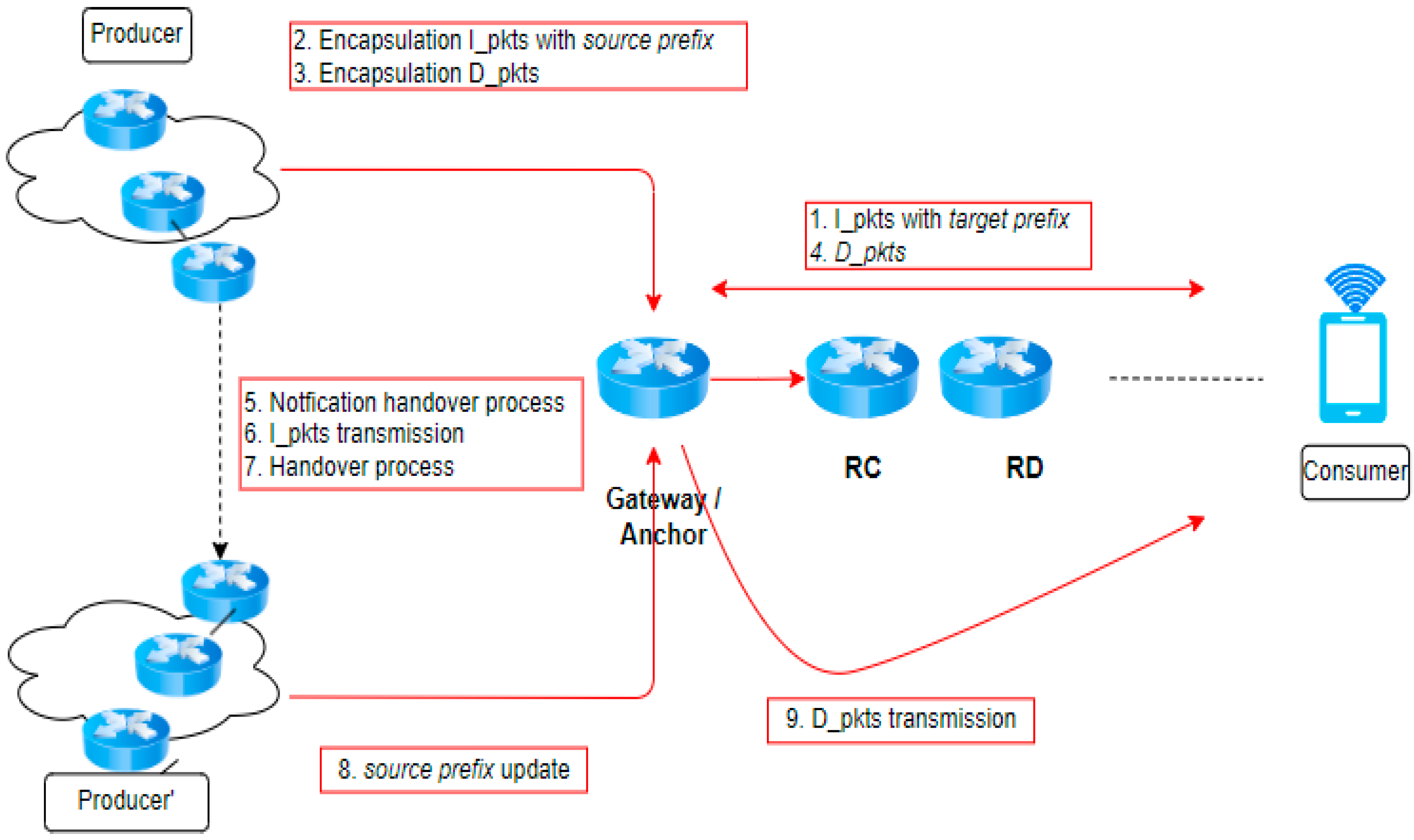
Figure 6 illustrates that a fixed point from the producer serves as the anchor node to monitor the producer’s movement. Compared to a DNS-based approach, the anchor transmits interest directly to the producer, resulting in cost, energy, and time savings. Although the interest was initially directed toward the anchor before the producer movement, the producer might still receive it after their shift to the new site. The interest was then retransmitted to overcome any miscommunication or lost connection.
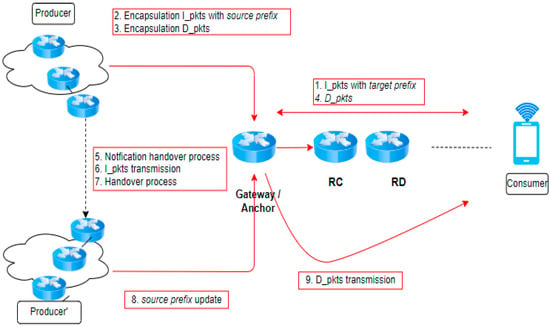
Figure 6.
NDN Anchor technique.
Algorithm 2 demonstrates the process of forwarding using the anchor approach. The characteristics are like the rendezvous technique, but a specific anchor is selected as the gateway. Note that the transmission begins by delivering an interest packet to the consumer, encapsulating the interest packet, and preparing to encapsulate the data packet. During the producer relocation, the packet will be dispatched to the gateway, and the handover process will be utilized to provide the notification. Once the handover process is completed, the prefix of interest will be updated. Finally, once the producer has assumed its new position, the data packet and acknowledgment (ACK) packet are transmitted through the consumer.
| Algorithm 2: Algorithm to Transmit Interest Using Anchor Technique | |||
| Input: Interest Packet with Prefix pt Process For Consumer Request | |||
| Output: A packet send to consumer,cs | |||
| 1 | if node is the Producer then return Data; | ||
| 2 | if first time receiving Interest then return ACK; | ||
| 3 | FIFO_Q OutgoingQ = [ ]; | ||
| 4 | foreach ⟨ þ, n → ð ⟩ in the FIB in ascending order of length (þ) do | ||
| 5 | if þ is the prefix of þt and þ ≠ cs then | ||
| 6 | enqueue (OutgoingQ, ð); | ||
| 7 | while OutgoingQ ≠ [ ] do | ||
| 8 | ð ← dequeue (OutgoingQ); | ||
| 9 | forward I through ð; | ||
| 10 | when switch receive a packet do | ||
| 11 | case Data for I from ð do return Data; | ||
| 12 | case ACK for I from ð do continue; | ||
| 13 | case I from node k ≠ ð do send ACK to k; repeat Line 10 | ||
| 14 | return ACK; | ||
Equation (3) specifies the cost associated with signaling, Equation (4) characterizes the delay experienced during handover for the anchor mobility approach, and Table 4 presents the metrics corresponding to the equation.
δanchor = Σ (δProduser + δRC + δRD + δConsumer + δProduser′)
= Ϩint × (α + 2ç) + Ϩdata × (α + ç),
= Ϩint × (α + 2ç) + Ϩdata × (α + ç),
£anchor = ((ÞT ÞT + (l/v)) + (1 − (ÞT ÞT + (l/v)))) × (lpn + α × LwlInt + 2ç × LwlInt + α × LwlInt + c × Lwint).

Table 4.
Anchor mobility equation metrics.
FIB/BIT method: KITE [67] employed a Pending Interest Table (PIT) instead of Forwarding Information Base (FIB) to redirect interest packets from the gateway to the consumer. This work is concluded by introducing diverse interests, encompassing connection and mapping. Once the handover process is over, the mobile host sends a traced interest to either the gateway or the replying host. Instead of transmitting data, the gateway or the relevant host provides a tracing request. Similar to data packets, tracking interest mirrors the consumer tracking interest while creating fresh avenues for the producer material. Additionally, the expenses associated with updating the location are assessed and contrasted analytically with the Network Mobility Support Protocol [76].
Dual-routing plane method: The router utilized in MobiCCN provides a virtual coordinate and a hyperbolic space allocation as a locator. When the Virtual Circuit (VC) inputs the content name (CN) of the object of interest, it is regarded as the destination address. Routers determine the optimal paths for mobile users by monitoring the number of hops a virtual circuit has in the network, resolving the scalability problem. Consequently, the consumer will alert the gateway about every new attachment point, and the router will generate a new FIB entry based on the virtual circuit and inbound interface details. Note that potential issues arise when dealing with substantial user traffic in Internet access routing aggregation, hindering the transmission of material to another producer. The work of [77] proposes a cache-aware social-based QoS routing system to enhance network performance and optimize routing methods.
Proactive handover method: Upon receiving this communication, the present access router will collaborate with the subsequent access router that the consumer will connect to, facilitating the mobile host in completing the handover operation in advance. Upon completion of the handover process, the access router will promptly inform the consumer and migrate to the new location. Once connected to the current router, the mobile consumer transmits an interest packet immediately to the new locators, originating from its previous location. The present and preceding access routers transmit accurate data to the mobile host, which returns it.
3.3. Anchorless Technique
In the context of anchorless NDN, the term “topology situation” pertains to the organization and interconnection of nodes without the need for predetermined anchor locations. This model exhibits decentralization and dynamism, enabling a highly adaptable and variable topology; therefore, comprehending the process by which nodes autonomously organize and establish connections without stationary anchor points is paramount. Examining the effects of topology modifications on the network’s efficiency and adaptability is also crucial for optimizing the anchorless model.
The forwarding mechanism in anchorless NDN pertains to the content transmission process without pre-established anchor sites. The nodes in the network engage collaboratively to facilitate the forwarding process, where they independently make judgments on distributing content within their local area. Hence, assessing the efficacy of advancing techniques in a context without anchors is of utmost importance. It involves evaluating how nodes collectively judge forwarding, adjust to dynamic changes, and optimize content retrieval without relying on central anchor points. Therefore, comprehending the influence of forwarding decisions on latency and network efficiency is essential.
The mobility characteristics of handover in anchorless NDN refer to how the model handles the movement of producers or consumers within the network. This encompasses factors such as the velocity of producer movement, the frequency of transitions, and the methods for ensuring uninterrupted content delivery during mobility events. Examining how anchorless NDN adjusts to the dynamic variations in the positions of producers and consumers is crucial. This entails assessing the time it takes for handover to occur, the capability to make localized decisions while experiencing mobility events, and the influence of mobility parameters on the efficiency of retrieving content in a decentralized setting.
The signaling cost in anchorless NDN primarily concerns the additional expenses associated with decentralized node communication and coordination. This encompasses transmitting signals to facilitate content finding, updating routing information, and coordinating actions without depending on stationary reference points. Consequently, assessing the efficiency of anchorless NDN requires a vital evaluation of the signaling cost. This is to minimize signaling overhead while maintaining efficient communication and collaboration across nodes, which is crucial to optimizing the model’s performance. Examining the influence of signaling on network resources, latency, and scalability yields valuable information on the overall effectiveness of the anchorless method.
When examining the anchorless model in NDN, it is important to recognize particular constraints and establish specific assumptions to define the scope of its applicability. The limitations include dynamic network conditions, the potential for increased latency, scalability challenges, and security and privacy concerns. On the other hand, the assumptions are node collaboration, predictable producer and consumer behavior, adequate network connectivity, decentralized decision-making, and a homogeneous network environment.
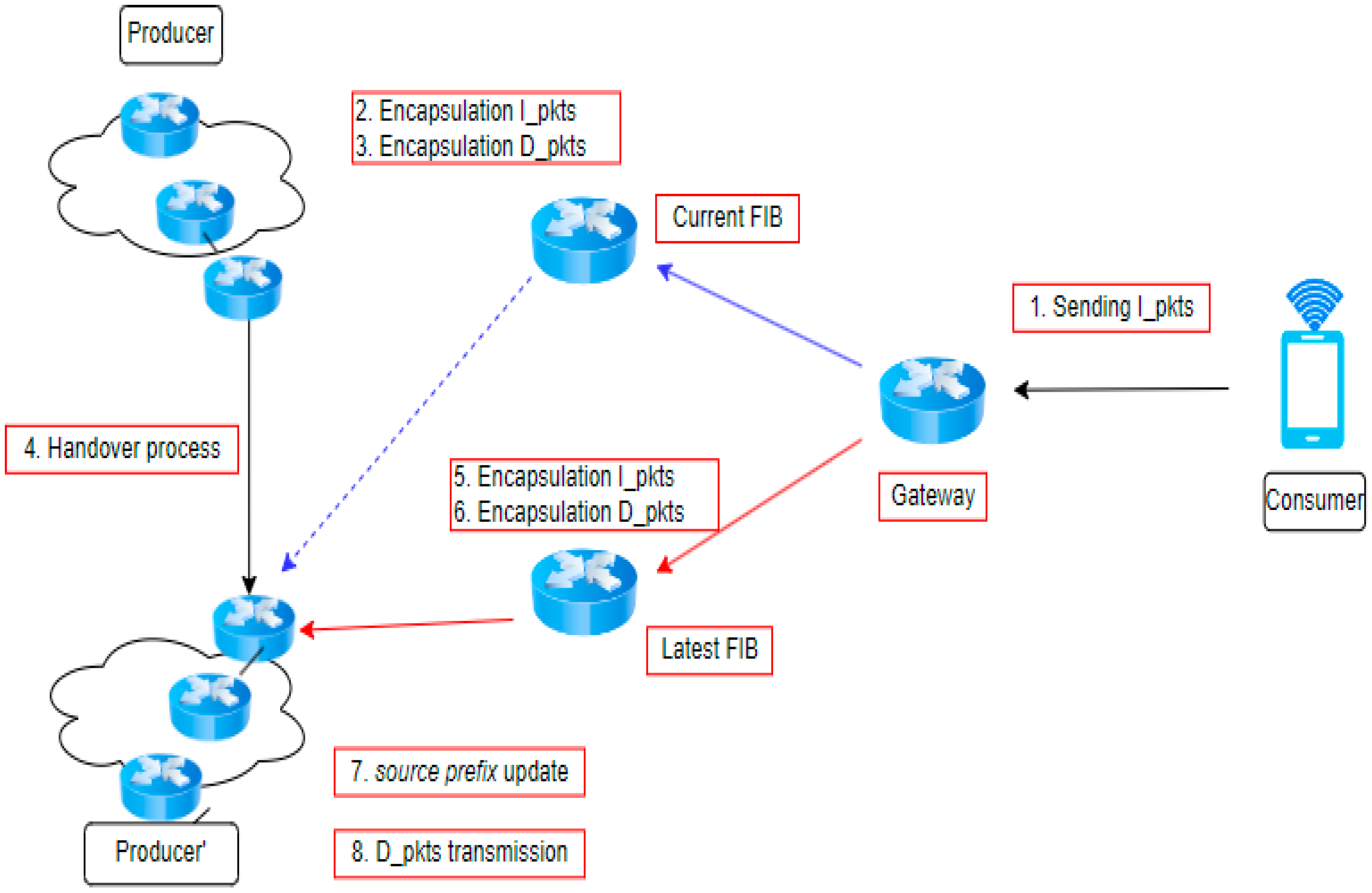
An anchorless version of producer mobility refers to a scenario where routers do not require designated nodes to receive interest updates. The FIB records for content relocation have been changed to replicate the new facial features, as depicted in Figure 7. The MAP-Me technique in NDN is a recent anchorless approach, as described by [78]. Note that MAP-Me depends on interest updates provided by cell phone manufacturers. None of the previous mobility solutions utilize the data from the producer or the routers that store it. Table 5 presents a comparison of the different options for NDN producer mobility. An alternative approach regarding anchorless models is to address the Core of Address modifications, which will affect the handoff process and mobility management [79].
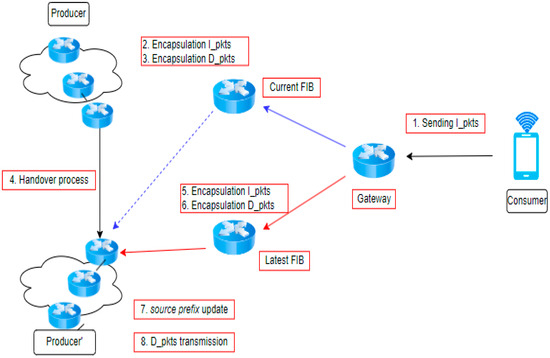
Figure 7.
NDN anchorless technique.

Table 5.
Anchorless mobility equation metric.
Algorithm 3 implements the anchorless approach, which utilizes a routing forwarding mechanism to transport the interest packet. The blue arrow mentions the current request to current FIB while sending interest to Producer before handover process, while red arrow show the process of requesting latest data packet on latest FIB while handover process done. The goal of sending interest to a neighbor is to disseminate the packet to the corresponding node. Ultimately, the interest packet is relocated to a different position, and the FIB will identify the current interest using the suitable sequence and transmit it to the closest point of attachment. Note that the discovery phase is crucial for identifying the valid next hop, eliminating the need to alert the router. This method ensures that the consumer will securely receive the data packet.
| Algorithm 3: Algorithm to Transmit Interest Using Anchorless Technique | |||
| Input: Interest Packet with Prefix pt Process For Consumer Request | |||
| Output: A packet send to consumer,cs | |||
| 1 | if ɛ ← FIB.LPM(I) | ||
| 2 | return | ||
| 3 | if I.s = [ ] then | ||
| 4 | if has valid Interface (ɛ,NextHop) then | ||
| 5 | BestRouteForwardingStrategy (I.ɛ) | ||
| 6 | else | ||
| 7 | I.seq ← ɛ.seq; send to Neighbor(I) | ||
| 8 | else | ||
| 9 | if has ProducerInterface (ɛ,NextHop) then | ||
| 10 | BestRouteForwardingStrategy (I.ɛ) | ||
| 11 | else if | ||
| 12 | ɛ.seq ≥ I.seq ∧ ∈ ɛ.FIB then | ||
| 13 | I.seq ← ɛ.seq; send to Neighbor(I) | ||
Equation (5) specifies the cost associated with signaling, Equation (6) characterizes the delay in handover for the anchorless mobility approach, and Table 5 presents the metrics corresponding to the equation.
δanchorless = Σ (δProduser + δGateway + δCurrent FIB + δLatest F + δConsumer + δProduser′)
= ϨInt × (2α + 2ç) + Ϩdata × (2α + 2),
= ϨInt × (2α + 2ç) + Ϩdata × (2α + 2),
£anchorless = ((ÞT ÞT + (l/v)) + (1 − (ÞT ÞT + (l/v)))) × (lpn + α × Lwlup + 2ɛ × Lwtrç + a × LwltrçɛInt + 2ɛ × Lwtrçɛdata).
Producer mobility strategies are essential for optimizing content retrieval in dynamic situations. Ensuring uninterrupted and dependable access to information is crucial, particularly in mobile devices, IoT devices, and changing network topologies. To achieve this, it is essential to address the mobility of producers. Flood-based producers inundate the network with content interest messages, assuring widespread data dissemination to all possible customers. Application scenario: Streaming live events that attract concurrent interest from different consumers was employed [80]. Meanwhile, ad hoc networks are characterized by frequent and unpredictable producer migration. Based on multi-casting, content is distributed to targeted consumer groups by multicast, which minimizes duplication compared to indiscriminate flooding [81]. In the application scenario of simultaneous video broadcasting to multiple consumers with shared interests, collaborative applications serve as platforms where users exchange and share data collectively. The system adapts to producer mobility by continuously updating routing and forwarding tables. In vehicular networks, which include content providers and moving cars, mobile sensors operate within dynamic IoT contexts [82].
Illustrative case study and exemplification: within the VNDN system, cars are producers, actively generating and distributing content; thus, adapting to the dynamic nature of vehicle networks requires using mobility-based approaches. Illustration: A group of interconnected automobiles exchanging real-time traffic information, utilizing mobility-based methods to guarantee prompt content delivery despite ongoing motion. Amidst natural disasters, there is often a frequent movement of producers due to the ever-changing circumstances. Hence, utilizing mobility-based strategies in NDN facilitates the effective delivery of content. An illustration: Emergency response teams utilize NDN to distribute information on disaster situations [83]. Consequently, the use of mobility-based approaches guarantees dependable communication, even in a dynamic setting. Mobile sensors serve as content producers in IoT applications, and mobility-based solutions are crucial for smooth data retrieval. Alternatively, agricultural IoT sensors are installed on mobile drones to gather and distribute crop data. However, examining scalability becomes difficult, particularly for flood-based techniques, as the number of producers and consumers grows.
Further investigation is required to enhance the ability to scale up in ever-changing settings. Therefore, utilizing mobility-based solutions may give rise to apprehensions regarding security and privacy. The research topic of guaranteeing secure and confidential communication in situations, such as vehicular networks or disaster response, is paramount. Ensuring uniformity and compatibility in producer mobility approaches is essential for universal acceptance. Research endeavors should prioritize the establishment of standardized methods and mechanisms (Table 6).

Table 6.
Mathematical simulation for NDN producer mobility techniques.
4. Findings and Future Trends of NDN Mobility
A recent study indicates that NDN mobility can decrease latency and enhance data retrieval performance by enabling data to be obtained from any node within the network rather than a designated place [92]. Furthermore, implementing caching and content retrieval algorithms in NDN mobility can enhance data accessibility and minimize duplication in mobile networks [93]. Note that NDN mobility enhances security and privacy in mobile networks by utilizing encryption and name-based access control techniques, which provide secure and detailed data access [94].
NDN in-network mobility management has garnered interest, with recent studies focusing on developing a scalable and adaptable virtual network overlay. NDN mobility research also incorporates other emerging technologies like edge computing and blockchain. Other than that, it entails relocating computing resources near devices, enhancing performance and reducing communication overhead. Blockchain technology can guarantee the genuineness and uncorrupted nature of the content, which is essential in a mobile setting where devices may lack reliability. Moreover, this technique is thoroughly implemented and tested using the ns3 and ndnSIM simulation tools. Table 7 displays the characteristics of NDN hybrid mobility and its associated benefits.

Table 7.
Technology and application based on NDN hybrid mobility.
NDN mobility research is expected to focus on incorporating IoT devices, which typically have restricted resources and sporadic connectivity. Researchers are also investigating cross-layer optimization techniques to enhance the performance of NDN mobility, which involves integrating NDN mobility with other layers of the networking stack, such as the transport and physical layers. Furthermore, integrating NDN mobility with Software-Defined Networking (SDN) can facilitate the implementation of real-time network adjustments and data flow optimization.
NDN diverges from conventional IP-based networking by embracing a content-centric methodology. It employs a naming and addressing system, directly identifying and referring to content, redirecting attention from the source and destination IP addresses to the content. This paradigm shift enables data retrieval to be more efficient and adaptable. Consequently, producers disseminate content while consumers manifest interest in content based on its name, enabling content-centric networking to incorporate caching and in-network storage as a fundamental component of its architecture. The content is stored in a cache along the route, allowing for efficient retrieval in future requests. Here, caching minimizes the repetition of data transfer, optimizes the utilization of bandwidth, and improves the speed of content delivery. NDN’s caching method greatly enhances network efficiency in frequent content requests and utilizes adaptive forwarding and routing techniques, allowing for real-time adjustments based on network conditions and user requirements.
This flexibility is especially applicable in situations with fluctuating network density and dynamics. Dynamic routing optimizes data transmission in high-density networks by adjusting routing patterns in response to real-time conditions. Moreover, NDN can adjust to varying network structures, guaranteeing effective content retrieval even in intricate and ever-changing network environments. It tackles the issue of producer mobility by employing sophisticated methods that automatically change routing tables in response to the migration of content producers. NDN producer mobility techniques guarantee uninterrupted and adequate content access in intricate and crowded networks with mobile producers. This flexibility enhances the efficiency of data transmission, especially in situations where network topologies are constantly changing.
Name-Based Producer Mobility (NPM) is a strategy employed in NDN to tackle the difficulties linked to the movement of content producers in ever-changing network settings. Traditional host-centric networking architectures in NDN encounter challenges when content producers, also known as data publishers, alter their locations or relocate inside the network. Nevertheless, NPM implements techniques that allow for flexible adjustment to the movements of content producers without depending on static IP addresses. This enhances the efficiency of retrieving content in situations involving mobile producers. The critical components of NPM include dynamic binding, interest forwarding updates, interest forwarding state maintenance, and proactive notification.
The performance implications of NPM in NDN are related to enhancing content retrieval efficiency, particularly in situations involving mobile producers. NPM guarantees consumer access to content by continuously changing routing and forwarding tables in response to producer moves. Therefore, the favorable performance impact results in improved content retrieval and decreased latency in dynamic network conditions, reducing the delay caused by the movement of content creators. Moreover, consumers can obtain material from the closest producer location, minimizing the producer mobility’s effect on response times. Decreased latency enhances the overall responsiveness of the network, particularly in situations involving frequent moves by producers, facilitating dynamic routing and forwarding by leveraging the real-time positions of content creators. This flexibility enhances the efficiency of transmitting information in networks that have constantly changing structures. The network can effectively adjust to changes in its structure, guaranteeing that content is delivered using the most efficient routes, even when the structure changes often enhance scalability by enabling the network to accommodate more mobile producers and consumers. Other than that, the inherent flexibility of NPM allows the network to expand more efficiently in dynamic settings. Enhanced scalability guarantees that the NDN architecture maintains its efficiency and responsiveness, even when the number of producers and consumers grows. It ensures that content retrieval is aligned with consumer preferences and the current locations of providers, maintaining QoS. The combination of proactive notifications and dynamic binding ensures a consistent QoS. Ensuring consistent QoS guarantees consumers receive material with the intended performance attributes, enhancing the overall user experience.
In contrast with conventional methods, in conventional IP-based networking, the issue of mobility is typically tackled by methods such as mobile IP, which may entail intricate handover processes and supplementary signaling. IP-based systems may need help adjusting to changing network structures and ensuring effective material retrieval when producers frequently change locations. Thus, NPM streamlines mobility management by directly linking content names with the present positions of producers, obviating the necessity for intricate handover methods. The content-centric nature of NDN, paired with NPM, provides a more efficient and flexible solution for content retrieval in dynamic situations.
Possibilities for incorporating a hierarchical naming scheme: Enables routers to make routing decisions based on the prefix, minimizing the search scope and enhancing performance. It facilitates effective routing by directing requests to content replicas or sources situated in proximity, minimizing latency. Furthermore, it improves routing efficiency by allowing routers to make decisions based on the recency or relevancy of content.
Impacts of caching strategies to reduce network overhead and improve content delivery: Minimizes the time it takes to obtain content by serving it from adjacent cache locations, lowering overall latency. Note that content obtained via caches decreases the demand for network traffic, optimizing resource utilization. Network resources are employed more efficiently by probabilistically caching content, focusing on popular or often visited content. Strategic caching decreases the chances of cache pollution with less-relevant items. Hence, adaptability guarantees that caching algorithms fit with dynamic network conditions, ensuring optimal content delivery in evolving scenarios. By adjusting to shifting demand patterns, adaptive caching strategies boost the possibility of serving content from caches, improving hit ratios. Material is cached closer to consumers, lowering the time it takes to obtain material, especially in cases with location-based naming schemes. Meanwhile, location-based caching contributes to scalable content delivery by optimizing content placement in the network. Caching decreases the need for repeated transfers of the same content, reducing overall bandwidth consumption. Collaborative caching improves the possibility of serving content from shared caches, boosting overall hit ratios. Thus, distributing caching responsibilities across several entities contributes to a better balanced and diversified network load.
Name-based forwarding is a routing mechanism where content names are organized in a hierarchical structure, similar to a file path. This structure enables efficient and organized routing decisions to be made, and it conforms to NDN’s content-centric paradigm by employing content names for routing, preventing the need for IP addresses. Routers maintain a forwarding table that keeps track of the state of network connections. This database is updated in real-time by exchanging interest and data packets. Name-based forwarding streamlines and expedites the process of retrieving content by directly linking interest packets with precise content names. It facilitates flexible adjustment to network changes, facilitating the movement of producers and optimizing routing in dynamic settings.
On the other hand, interest aggregation refers to combining or consolidating individual interests or preferences into a collective or group decision. It detects and removes duplicate interest packets, preventing the producer from receiving multiple requests for the same content. Meanwhile, routers function as consolidation points, merging comparable interests into a unified request before transmitting it upstream. It also optimizes the management of interest packets to reduce network and content producer workload. Interest aggregation decreases repetitive queries, reducing bandwidth usage and enhancing network efficiency. Additionally, it optimizes the processing of interest packets by aligning with NDN’s content-centric nature and focusing on content names.
NDN hybrid mobility has gained an appeal due to its ability to enhance the performance and efficiency of mobile and wireless networks by incorporating other technologies and applications. It addresses problems such as inconsistent network addressing, limited application utilization, data archiving, replication issues, and content durability. Hence, integrating mobility methods and techniques to create hybrid techniques effectively resolves the problems. To address the challenges related to hybrid mobility, we can utilize ndnSIM for simulation purposes. This involves configuring the topology to facilitate the execution of the hybrid simulation. Figure 8 illustrates a concise overview of the NDN hybrid mobility taxonomy, whereas Table 8 categorizes the hybrid NDN approaches. The subsequent sections delineate some potential hybrid methodologies. Table 9 presents the potential challenges and limitations of NDN in network optimization.
Figure 8.
NDN Hybrid Mobility Taxonomy.

Table 8.
Categorization of NDN hybrid.

Table 9.
Potential Challenges and Limitations of NDN in Network Optimization.
5. Conclusions
This article explores the performance-optimized simulation techniques employed to assess producer mobility alternatives in NDN. NDN’s content-centric communication design poses challenges in facilitating data provider mobility. The significance and potential consequences of employing producer mobility techniques in NDN encompass various aspects, including enabling dynamic access to content, optimizing the utilization of resources, supporting the IoT and vehicular networks, enhancing reliability in emergency scenarios, and facilitating edge computing. Further investigation should prioritize improving the scalability of producer mobility methods, particularly in extensive NDN implementations. Hence, exploring more efficient methods for dynamic routing and forwarding is imperative. Continuous research efforts are necessary to tackle security and privacy challenges related to mobility-based approaches. Other than that, providing robust methods for ensuring secure communication in constantly changing contexts is crucial. Future research should focus on establishing uniformity and compatibility among methods used to enhance producer mobility. Implementing standardized protocols will ease the NDN installations into becoming widely adopted and compatible with one another.
Author Contributions
Supervision: A.H.M.A.; validation: H.S. and K.A.; visualization and writing of original draft: W.M.H.A.; review and editing: A.H.M.A., H.S., K.A. and M.S. All authors have read and agreed to the published version of the manuscript.
Funding
Fakulti Teknologi dan Sains Maklumat, Universiti Kebangsaan Malaysia: TT-2022-31 005.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Gbadamosi, S.A.; Hancke, G.P.; Abu-Mahfouz, A.M. Building upon NB-IoT networks: A roadmap towards 5G new radio networks. IEEE Access 2020, 8, 188641–188672. [Google Scholar] [CrossRef]
- Wang, X.; Cai, S. Mobility Management in Vehicular Named Data Networking. IEEE Sens. Lett. 2021, 5, 7500804. [Google Scholar] [CrossRef]
- Din, I.U.; Hassan, S.; Almogren, A.; Ayub, F.; Guizani, M. PUC: Packet Update Caching for energy efficient IoT-based Information-Centric Networking. Future Gener. Comput. Syst. 2020, 111, 634–643. [Google Scholar] [CrossRef]
- Karim, F.A.; Hafizah, A.; Aman, M. Named Data Networking: A Survey on Routing Strategies. IEEE Access 2022, 10, 90254–90270. [Google Scholar] [CrossRef]
- Aboodi, A.; Wan, T.C.; Sodhy, G.C. Survey on the Incorporation of NDN/CCN in IoT. IEEE Access 2019, 7, 71827–71858. [Google Scholar] [CrossRef]
- Afanasyev, A.; Burke, J.; Refaei, T.; Wang, L.; Zhang, B.; Zhang, L. A Brief Introduction to Named Data Networking. In Proceedings of the IEEE Military Communications Conference MILCOM, Los Angeles, CA, USA, 29–31 October 2018; pp. 605–611. [Google Scholar]
- Cisco. Mobile Video Delivery with Hybrid ICN IP-Integrated ICN Solution for 5G. Cisco White Pap. 2017, 1–14. Available online: https://www.cisco.com/c/dam/en/us/solutions/collateral/service-provider/ultra-services-platform/mwc17-hicn-video-wp.pdf (accessed on 15 July 2023).
- Mtibaa, A.; Tourani, R.; Misra, S.; Burke, J.; Zhang, L. Towards edge computing over named data networking. In Proceedings of the 2018 IEEE International Conference on Edge Computing (EDGE), San Francisco, CA, USA, 2–7 July 2018; pp. 117–120. [Google Scholar]
- Shuja, J.; Bilal, K.; Alasmary, W.; Sinky, H.; Alanazi, E. Applying machine learning techniques for caching in next-generation edge networks: A comprehensive survey. J. Netw. Comput. Appl. 2021, 181, 103005. [Google Scholar] [CrossRef]
- Chen, C.; Jiang, J.; Fu, R.; Chen, L.; Li, C.; Wan, S. An Intelligent Caching Strategy Considering Time-Space Characteristics in Vehicular Named Data Networks. IEEE Trans. Intell. Transp. Syst. 2021, 23, 19655–19667. [Google Scholar] [CrossRef]
- Baranski, S.; Konorski, J. Mitigation of fake data content poisoning attacks in NDN via blockchain. In Proceedings of the 2020 30th International Telecommunication Networks and Applications Conference (ITNAC), Melbourne, Australia, 25–27 November 2020. [Google Scholar] [CrossRef]
- Tsai, P.H.; Zhang, J.B.; Tsai, M.H. An Efficient Probe-Based Routing for Content-Centric Networking. Sensors 2022, 22, 341. [Google Scholar] [CrossRef]
- Islam, S.; Abdalla, A.H.; Mohd Isa, F.N.; Hasan, M.K. Performance evaluation of multi-interfaced fast handoff scheme for PNEMO environment. Elektron. Elektrotech. 2018, 24, 80–85. [Google Scholar] [CrossRef]
- Li, X.; Wang, S.; Wu, W.; Chen, X.; Xiao, B. Interest tree based information dissemination via vehicular named data networking. In Proceedings of the 2018 27th International Conference on Computer Communication and Networks (ICCCN), Hangzhou, China, 30 July–2 August 2018. [Google Scholar]
- Buragohain, M.; Nandi, S. Quality of Service provisioning in Named Data Networking via PIT entry reservation and PIT replacement policy. Comput. Commun. 2020, 155, 166–183. [Google Scholar] [CrossRef]
- Manzo, G.; Kalogeiton, E.; Di Maio, A.; Braun, T.; Palattella, M.R.; Turcanu, I.; Souas, R.; Rizzo, G. DeepNDN: Opportunistic Data Replication and Caching in Support of Vehicular Named Data. In Proceedings of the 2020 IEEE 21st International Symposium on “A World of Wireless, Mobile and Multimedia Networks” (WoWMoM), Cork, Ireland, 31 August–3 September 2020; pp. 234–243. [Google Scholar]
- Abou-Nassar, E.M.; Iliyasu, A.M.; El-Kafrawy, P.M.; Song, O.Y.; Bashir, A.K.; Abd El-Latif, A.A. DITrust Chain: Towards Blockchain-Based Trust Models for Sustainable Healthcare IoT Systems. IEEE Access 2020, 8, 111223–111238. [Google Scholar] [CrossRef]
- Hussaini, M.; Naeem, M.A.; Kim, B.S.; Maijama’a, I.S. Efficient Producer Mobility Management Model in Information-Centric Networking. IEEE Access 2019, 7, 42032–42051. [Google Scholar] [CrossRef]
- Kim, D.; Ko, Y.B. On-demand anchor-based mobility support method for named data networking. In Proceedings of the 2017 19th International Conference on Advanced Communication Technology (ICACT), PyeongChang, Republic of Korea, 19–22 February 2017; pp. 19–23. [Google Scholar]
- Ahmed, M.Z.; Hashim, A.H.A.; Ramli, H.A.M.; Khalifa, O.O.; Alkali, A.H.; Adamu, Z.M. Simulation of handoff algorithm for NDN producer’s mobility. J. Adv. Res. Dyn. Control Syst. 2020, 12, 2242–2251. [Google Scholar] [CrossRef]
- Liu, D.; Huang, C.; Chen, X.; Jia, X. Space-terrestrial integrated mobility management via named data networking. Tsinghua Sci. Technol. 2018, 23, 431–439. [Google Scholar] [CrossRef]
- Torres, J.V.; Alvarenga, I.D.; Boutaba, R.; Duarte, O.C.M.B. Evaluating CRoS-NDN: A comparative performance analysis of a controller-based routing scheme for named-data networking. J. Internet Serv. Appl. 2019, 10, 20. [Google Scholar] [CrossRef]
- Saxena, D.; Raychoudhury, V. Scalable, Memory-efficient Pending Interest Table of Named Data Networking. In Proceedings of the International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Delhi, India, 10–13 December 2020; pp. 1–8. [Google Scholar]
- Deebak, B.D.; Al-Turjman, F.; Aloqaily, M.; Alfandi, O. IoT-BSFCAN: A smart context-aware system in IoT-Cloud using mobile-fogging. Future Gener. Comput. Syst. 2020, 109, 368–381. [Google Scholar] [CrossRef]
- Ngai, E.; Ohlman, B.; Tsudik, G.; Uzun, E.; Wählisch, M.; Wood, C.A. Can We Make a Cake and Eat it Too? A Discussion of ICN Security and Privacy. ACM SIGCOMM Comput. Commun. Rev. 2017, 47, 49–54. [Google Scholar] [CrossRef]
- Muchtar, F.; Abdullah, A.H.; Hassan, S.; Masud, F. Energy conservation strategies in Host Centric Networking based MANET: A review. J. Netw. Comput. Appl. 2018, 111, 77–98. [Google Scholar] [CrossRef]
- Meddeb, M.; Dhraief, A.; Belghith, A.; Monteil, T.; Drira, K.; Al-Ahmadi, S. Named Data Networking: A Promising Architecture for the Internet of Things (IoT). Int. J. Semant. Web Inf. Syst. 2018, 14, 86–112. [Google Scholar] [CrossRef]
- Khelifi, H.; Luo, S.; Nour, B.; Shah, S.C. Security and privacy issues in vehicular named data networks: An overview. Mob. Inf. Syst. 2018, 2018, 5672154. [Google Scholar] [CrossRef]
- Chatterjee, T.; Ruj, S.; Bit, S.D. Security Issues in Named Data Networks. Computer 2018, 51, 66–75. [Google Scholar] [CrossRef]
- Mick, T.; Tourani, R.; Misra, S. LASeR: Lightweight Authentication and Secured Routing for NDN IoT in Smart Cities. IEEE Internet Things J. 2018, 5, 755–764. [Google Scholar] [CrossRef]
- Rainer, B.; Petscharnig, S. Challenges and opportunities of named data networking in vehicle-to-everything communication: A review. Information 2018, 9, 264. [Google Scholar] [CrossRef]
- Zhang, Z.; Yu, Y.; Zhang, H.; Newberry, E.; Mastorakis, S.; Li, Y.; Afanasyev, A.; Zhang, L. An Overview of Security Support in Named Data Networking. IEEE Commun. Mag. 2018, 56, 62–68. [Google Scholar] [CrossRef]
- Azamuddin, W.M.H.; Aman, A.H.M.; Hassan, R.; Abdali, T.A.N. Named Data Networking Mobility: A Survey; Springer International Publishing: Berlin/Heidelberg, Germany, 2022; Volume 1548 CCIS, ISBN 9783030972547. [Google Scholar]
- Farkhana, M.; Abdul Hanan, A.; Suhaidi, H.; Ahamad Tajudin, K.; Kamal Zuhairi, Z. Energy conservation of content routing through wireless broadcast control in NDN based MANET: A review. J. Netw. Comput. Appl. 2019, 131, 109–132. [Google Scholar] [CrossRef]
- Kumar, N.; Singh, A.K.; Aleem, A.; Srivastava, S. Security Attacks in Named Data Networking: A Review and Research Directions. J. Comput. Sci. Technol. 2019, 34, 1319–1350. [Google Scholar] [CrossRef]
- Nour, B.; Sharif, K.; Li, F.; Biswas, S.; Moungla, H.; Guizani, M.; Wang, Y. A survey of Internet of Things communication using ICN: A use case perspective. Comput. Commun. 2019, 142–143, 95–123. [Google Scholar] [CrossRef]
- Li, Z.; Xu, Y.; Zhang, B.; Yan, L.; Liu, K. Packet Forwarding in Named Data Networking Requirements and Survey of Solutions. IEEE Commun. Surv. Tutor. 2019, 21, 1950–1987. [Google Scholar] [CrossRef]
- Muchtar, F.; Abdullah, A.H.; Al-Adhaileh, M.; Zamli, K.Z. Energy conservation strategies in Named Data Networking based MANET using congestion control: A review. J. Netw. Comput. Appl. 2020, 152, 102511. [Google Scholar] [CrossRef]
- Khelifi, H.; Luo, S.; Nour, B.; Moungla, H.; Faheem, Y.; Hussain, R.; Ksentini, A. Named Data Networking in Vehicular Ad Hoc Networks: State-of-the-Art and Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 320–351. [Google Scholar] [CrossRef]
- Chen, C.; Wang, C.; Qiu, T.; Atiquzzaman, M.; Wu, D.O. Caching in Vehicular Named Data Networking: Architecture, Schemes and Future Directions. IEEE Commun. Surv. Tutor. 2020, 22, 2378–2407. [Google Scholar] [CrossRef]
- Al-Omaisi, H.; Sundararajan, E.A.; Alsaqour, R.; Abdullah, N.F.; Abdelhaq, M. A survey of data dissemination schemes in vehicular named data networking. Veh. Commun. 2021, 30, 100353. [Google Scholar] [CrossRef]
- Nayak, S.; Patgiri, R.; Borah, A. A survey on the roles of Bloom Filter in implementation of the Named Data Networking. Comput. Netw. 2021, 196, 108232. [Google Scholar] [CrossRef]
- da Silva, E.T.; Costa, A.L.D.; de Macedo, J.M.H. On the realization of VANET using named data networking: On improvement of VANET using NDN-based routing, caching, and security. Int. J. Commun. Syst. 2022, 35, e5348. [Google Scholar] [CrossRef]
- Shah, M.S.M.; Leau, Y.B.; Yan, Z.; Anbar, M. Hierarchical Naming Scheme in Named Data Networking for Internet of Things: A Review and Future Security Challenges. IEEE Access 2022, 10, 19958–19970. [Google Scholar] [CrossRef]
- Ahed, K.; Benamar, M.; Lahcen, A.A.; Ouazzani, R. El Forwarding strategies in vehicular named data networks: A survey. J. King Saud Univ.—Comput. Inf. Sci. 2022, 34, 1819–1835. [Google Scholar] [CrossRef]
- Lee, R.T.; Leau, Y.B.; Park, Y.J.; Anbar, M. A Survey of Interest Flooding Attack in Named-Data Networking: Taxonomy, Performance and Future Research Challenges. IETE Tech. Rev. 2022, 39, 1027–1045. [Google Scholar] [CrossRef]
- Gundoǧan, C.; Amsuss, C.; Schmidt, T.C.; Wahlisch, M. Content Object Security in the Internet of Things: Challenges, Prospects, and Emerging Solutions. IEEE Trans. Netw. Serv. Manag. 2022, 19, 538–553. [Google Scholar] [CrossRef]
- Naeem, M.A.; Nguyen, T.N.; Ali, R.; Cengiz, K.; Meng, Y.; Khurshaid, T. Hybrid Cache Management in IoT-Based Named Data Networking. IEEE Internet Things J. 2022, 9, 7140–7150. [Google Scholar] [CrossRef]
- Azamuddin, W.M.H.; Aman, A.H.M.; Sallehuddin, H.; Abualsaud, K.; Mansor, N. The Emerging of Named Data Networking: Architecture, Application and Technology. IEEE Access 2023, 11, 23620–23633. [Google Scholar] [CrossRef]
- Benmoussa, A.; Kerrache, C.A.; Lagraa, N.; Mastorakis, S.; Lakas, A.; Tahari, A.E.K. Interest Flooding Attacks in Named Data Networking: Survey of Existing Solutions, Open Issues, Requirements, and Future Directions. ACM Comput. Surv. 2023, 55, 1–37. [Google Scholar] [CrossRef]
- Alubady, R.; Salman, M.; Mohamed, A.S. A review of modern caching strategies in named data network: Overview, classification, and research directions. Telecommun. Syst. 2023, 84, 581–626. [Google Scholar] [CrossRef]
- Asaf, K.; Rehman, R.A.; Kim, B.S. Blockchain technology in Named Data Networks: A detailed survey. J. Netw. Comput. Appl. 2020, 171, 102840. [Google Scholar] [CrossRef]
- Aldaoud, M.; Al-Abri, D.; Awadalla, M.; Kausar, F. Leveraging ICN and SDN for Future Internet Architecture: A Survey. Electronics 2023, 12, 1723. [Google Scholar] [CrossRef]
- Jeet, R.; Kumar, P.A.R. A survey on interest packet flooding attacks and its countermeasures in named data networking. Int. J. Inf. Secur. 2022, 21, 1163–1187. [Google Scholar] [CrossRef]
- Azamuddin, W.M.H.; Aman, A.H.M.; Hassan, R.; Mansor, N. Comparison of Named Data Networking Mobility Methodology in a Merged Cloud Internet of Things and Artificial Intelligence Environment. Sensors 2022, 22, 6668. [Google Scholar] [CrossRef]
- Singh, K.K.; Dudeja, R.K. Hybrid Information Placement in Named Data Networking-Internet of Things System. In Proceedings of the 2022 8th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 25–26 March 2022; pp. 593–601. [Google Scholar] [CrossRef]
- Iqbal, S.M.A. Cache-MCDM: A hybrid caching scheme in Mobile Named Data Networks based on multi-criteria decision making. Future Gener. Comput. Syst. 2024, 154, 344–358. [Google Scholar] [CrossRef]
- Bilgili, S.; Demir, A.K.; Alam, S. IfNot: An approach towards mitigating interest flooding attacks in named data networking of things. Internet Things 2024, 25, 101076. [Google Scholar] [CrossRef]
- Cao, K.; Xu, G.; Zhou, J.; Wei, T.; Chen, M.; Hu, S. QoS-adaptive approximate real-time computation for mobility-aware IoT lifetime optimization. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2018, 38, 1799–1810. [Google Scholar] [CrossRef]
- Tang, Y.; Cheng, N.; Wu, W.; Wang, M.; Dai, Y.; Shen, X. Delay-minimization routing for heterogeneous VANETs with machine learning based mobility prediction. IEEE Trans. Veh. Technol. 2019, 68, 3967–3979. [Google Scholar] [CrossRef]
- Khalid, A.; Rehman, R.A.; Burhan, M. CBILEM: A novel energy aware mobility handling protocol for SDN based NDN-MANETs. Ad Hoc Netw. 2023, 140, 103049. [Google Scholar] [CrossRef]
- Mascarenhas, D.M.; Moraes, I.M. PIF and ReCiF: Efficient interest-packet forwarding mechanisms for named-Data Wireless Mesh Networks. Information 2018, 9, 243. [Google Scholar] [CrossRef]
- Guo, X.; Yang, S.; Cao, L.; Wang, J.; Jiang, Y. A new solution based on optimal link-state routing for named data MANET. China Commun. 2021, 18, 213–229. [Google Scholar] [CrossRef]
- Vaiyapuri, T.; Parvathy, V.S.; Manikandan, V.; Krishnaraj, N.; Gupta, D.; Shankar, K. A Novel Hybrid Optimization for Cluster-Based Routing Protocol in Information-Centric Wireless Sensor Networks for IoT Based Mobile Edge Computing. Wirel. Pers. Commun. 2021, 127, 39–62. [Google Scholar] [CrossRef]
- Alhowaidi, M.; Nadig, D.; Hu, B.; Ramamurthy, B.; Bockelman, B. Cache management for large data transfers and multipath forwarding strategies in Named Data Networking. Comput. Netw. 2021, 199, 108437. [Google Scholar] [CrossRef]
- Rui, L.; Yang, S.; Huang, H. A producer mobility support scheme for real-time multimedia delivery in named data networking. Multimed. Tools Appl. 2018, 77, 4811–4826. [Google Scholar] [CrossRef]
- Zhang, Y.; Xia, Z.; Mastorakis, S.; Zhang, L. KITE: Producer mobility support in named data networking. In Proceedings of the 5th ACM Conference on Information-Centric Networking, Boston, MA, USA, 21–23 September 2018; ACM: New York, NY, USA, 2018; pp. 125–136. [Google Scholar]
- Fei, Y.; Zhu, H.; Yin, J. Modeling and verifying NLSR protocol of NDN for CPS using UPPAAL. J. Softw. Evol. Process 2023, 35, e2384. [Google Scholar] [CrossRef]
- Westerhoff, L.; Reinhardt, S.; Schafer, G.; Wolisz, A. Security analysis and concept for the multicast-based handover support architecture MOMBASA. In Proceedings of the IEEE Global Telecommunications Conference, Dallas, TX, USA, 29 November–3 December 2004; Volume 4, pp. 2201–2207. [Google Scholar]
- Abrar, A.; Arif, A.S.C.M.; Zaini, K.M. Producer mobility support in information-centric networks: Research background and open issues. Int. J. Commun. Netw. Distrib. Syst. 2022, 28, 312–336. [Google Scholar] [CrossRef]
- Li, H. PFECC: A precise feedback-based explicit congestion control algorithm in nameddata networking. Turkish J. Electr. Eng. Comput. Sci. 2021, 29, 1124–1138. [Google Scholar] [CrossRef]
- Sadr, S.; Adve, R.S. Handoff rate and coverage analysis in multi-tier heterogeneous networks. IEEE Trans. Wirel. Commun. 2015, 14, 2626–2638. [Google Scholar] [CrossRef]
- Hou, R.; Zhou, S.; Cui, M.; Zhou, L.; Zeng, D.; Luo, J.; Ma, M. Data Forwarding Scheme for Vehicle Tracking in Named Data Networking. IEEE Trans. Veh. Technol. 2021, 70, 6684–6695. [Google Scholar] [CrossRef]
- Ayaz, M.; Iqbal, J.; Adnan, M.; Hussain, S.S.; Alabrah, A.; Amin, N.U.; Al-Hadhrami, S.; Mizanur Rahman, S.M. A Content Dissemination Technique Based on Priority to Improve Quality of Service of Vehicular Ad Hoc Networks. J. Adv. Transp. 2022, 2022, 6903450. [Google Scholar] [CrossRef]
- Ahmed, M.Z.; Hashim, A.H.A.; Hassan, A.M.; Khalifa, O.O.; Alkali, A.H.; Ahmed, A.M. Performance evaluation of best route and broadcast strategy for NDN producer’s mobility. Int. J. Eng. Adv. Technol. 2019, 9, 3671–3677. [Google Scholar] [CrossRef]
- Islam, S.; Abdalla, A.H.; Khalifa, M.K.H.O.O.; Mahmoud, O.; Saeed, R.A. Macro mobility scheme in NEMO to support seamless handoff. In Proceedings of the 2012 International Conference on Computer and Communication Engineering, ICCCE 2012, Kuala Lumpur, Malaysia, 3–5 July 2012; pp. 234–238. [Google Scholar]
- Qu, D.; Wang, X.; Huang, M.; Li, K.; Das, S.K.; Wu, S. A cache-aware social-based QoS routing scheme in Information Centric Networks. J. Netw. Comput. Appl. 2018, 121, 20–32. [Google Scholar] [CrossRef]
- Auge, J.; Carofiglio, G.; Grassi, G.; Muscariello, L.; Pau, G.; Zeng, X. MAP-Me: Managing Anchor-Less Producer Mobility in Content-Centric Networks. IEEE Trans. Netw. Serv. Manag. 2018, 15, 596–610. [Google Scholar] [CrossRef]
- Ahmed, M.Z.; Hassan, A.M.; Alkali, A.H.; Hashim, A.H.A.; Khalifa, O.O.; Ramli, H.A.B.M. Performance Evaluation of Scenerio-aware Protocol for Producer Mobility Support in NDN. In Proceedings of the 2019 7th International Conference on Mechatronics Engineering (ICOM), Putrajaya, Malaysia, 30–31 October 2019. [Google Scholar] [CrossRef]
- Wu, F.; Yang, W.; Ren, J.; Lyu, F.; Yang, P.; Zhang, Y.; Shen, X. NDN-MMRA: Multi-Stage Multicast Rate Adaptation in Named Data Networking WLAN. IEEE Trans. Multimed. 2020, 23, 3250–3263. [Google Scholar] [CrossRef]
- Wang, X.; Cai, S. An Efficient Named-Data-Networking-Based IoT Cloud Framework. IEEE Internet Things J. 2020, 7, 3453–3461. [Google Scholar] [CrossRef]
- Alduayji, S.; Belghith, A.; Gazdar, A.; Al-Ahmadi, S. PF-ClusterCache: Popularity and Freshness-Aware Collaborative Cache Clustering for Named Data Networking of Things. Appl. Sci. 2022, 12, 6706. [Google Scholar] [CrossRef]
- Zhang, J.; Liu, P.; Zhang, F.; Iwabuchi, H.; De Moura, A.A.D.H.E.A.; De Albuquerque, V.H.C. Ensemble Meteorological Cloud Classification Meets Internet of Dependable and Controllable Things. IEEE Internet Things J. 2021, 8, 3323–3330. [Google Scholar] [CrossRef]
- Jahanian, M.; Chen, J.; Ramakrishnan, K.K. Graph-based namespaces and load sharing for efficient information dissemination in disasters. In Proceedings of the 2019 IEEE 27th International Conference on Network Protocols (ICNP), Chicago, IL, USA, 8–10 October 2019. [Google Scholar]
- Zhang, Y.; Xia, Z.; Afanasyev, A.; Zhang, L. A note on routing scalability in named data networking. In Proceedings of the 2019 IEEE International Conference on Communications Workshops (ICC Workshops), Shanghai, China, 20–24 May 2019. [Google Scholar] [CrossRef]
- Wilhelm, G.; Ayaida, M.; Fouchal, H. A secure cloud approach for intelligent transport systems. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019. [Google Scholar] [CrossRef]
- Kim, H.; Ko, N. A Scalable Pub/Sub System for NDN. In Proceedings of the 2020 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 21–23 October 2020; pp. 1067–1069. [Google Scholar] [CrossRef]
- Ahmed, M.Z.; Hashim, A.H.A.; Khalifa, O.O.; Alsaqour, R.A.; Saeed, R.A.; Alkali, A.H. Queuing Theory Approach for NDN Mobile Producer’s Rate of Transmission Using Network Coding. In Proceedings of the 2021 International Congress of Advanced Technology and Engineering, ICOTEN 2021, Online, 4–5 July 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmed, M.Z.; Hashim, A.H.A.; Khalifa, O.O.; Saeed, R.A.; Alsaqour, R.A.; Alkali, A.H. Connectivity Framework for Rendezvous and Mobile Producer Nodes Using NDN Interest Flooding. In Proceedings of the 2021 International Congress of Advanced Technology and Engineering, ICOTEN 2021, Online, 4–5 July 2021. [Google Scholar] [CrossRef]
- Ramani, S.K.; Afanasyev, A. Rapid establishment of transient trust for NDN-based vehicular networks. In Proceedings of the 2020 IEEE International Conference on Communications Workshops (ICC Workshops), Dublin, Ireland, 7–11 June 2020. [Google Scholar] [CrossRef]
- Luo, J.; He, C.; Wang, J.; Deng, L.; Ran, Y. Anchored Secret Sharing for Access Control with Fast Revocation in Named Data Networking. In Proceedings of the 2021 4th International Conference on Hot Information-Centric Networking (HotICN), Nanjing, China, 25–27 November 2021; pp. 51–56. [Google Scholar] [CrossRef]
- Wang, X.; Cai, S. Efficient Road Safety Data Retrieval in VNDN. IEEE Syst. J. 2021, 15, 996–1004. [Google Scholar] [CrossRef]
- Saranya, N.; Geetha, K.; Rajan, C. Data replication in mobile edge computing systems to reduce latency in internet of things. Wirel. Pers. Commun. 2020, 112, 2643–2662. [Google Scholar] [CrossRef]
- Hasan, M.K.; Islam, S.; Sulaiman, R.; Khan, S.; Hashim, A.H.A.; Habib, S.; Islam, M.; Alyahya, S.; Ahmed, M.M.; Kamil, S.; et al. Lightweight Encryption Technique to Enhance Medical Image Security on Internet of Medical Things Applications. IEEE Access 2021, 9, 47731–47742. [Google Scholar] [CrossRef]
- Zhang, X.; Gong, L.; Xun, Y.; Piao, X.; Leit, K. Centaur: A evolutionary design of hybrid NDN/IP transport architecture for streaming application. In Proceedings of the 2016 IEEE 7th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference, UEMCON 2016, New York, NY, USA, 20–22 October 2016. [Google Scholar]
- Hu, Y.; Serban, C.; Wang, L.; Afanasyev, A.; Zhang, L. PLI-Sync: Prefetch Loss-Insensitive Sync for NDN Group Streaming. In Proceedings of the ICC 2021-IEEE International Conference on Communications, Montreal, QC, Canada, 14–23 June 2021; pp. 1–6. [Google Scholar]
- Thomas, Y.; Fotiou, N.; Toumpis, S.; Polyzos, G.C. Improving mobile ad hoc networks using hybrid IP-Information Centric Networking. Comput. Commun. 2020, 156, 25–34. [Google Scholar] [CrossRef]
- Yan, Z.; Park, Y.J.; Leau, Y.B.; Ren-Ting, L.; Hassan, R. Hybrid Network Mobility Support in Named Data Networking. In Proceedings of the International Conference on Information Networking, Barcelona, Spain, 7–10 January 2020; pp. 16–19. [Google Scholar]
- Li, Z.; Liu, K.; Liu, D.; Shi, H.; Chen, Y. Hybrid wireless networks with FIB-based Named Data Networking. Eurasip J. Wirel. Commun. Netw. 2017, 2017, 54. [Google Scholar] [CrossRef]
- Gündoğan, C.; Kietzmann, P.; Schmidt, T.C.; Wählisch, M. Hopp: Robust and resilient publish-subscribe for an information-centric internet of things. In Proceedings of the 2018 IEEE 43rd Conference on Local Computer Networks (LCN), Chicago, IL, USA, 1–4 October 2018; pp. 331–334. [Google Scholar]
- Deng, G.; Xie, X.; Shi, L.; Li, R. Hybrid information forwarding in VANETs through named data networking. In Proceedings of the IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, PIMRC, Hong Kong, China, 30 August–2 September 2015; pp. 1940–1944. [Google Scholar]
- Paranjothi, A.; Tanik, U.; Wang, Y.; Khan, M.S. Hybrid-Vehfog: A robust approach for reliable dissemination of critical messages in connected vehicles. Trans. Emerg. Telecommun. Technol. 2019, 30, e3595. [Google Scholar] [CrossRef]
- Aldahlan, B.; Fei, Z. A geographic routing strategy with DTN support for vehicular named data networking. In Proceedings of the 2019 IEEE International Conference on Computational Science and Engineering (CSE) and IEEE International Conference on Embedded and Ubiquitous Computing (EUC), CSE/EUC 2019, New York, NY, USA, 1–3 August 2019; pp. 361–366. [Google Scholar]
- Russell, K.; Simon, R. Evaluation of a Geo-region Based Architecture for Information Centric Disruption Tolerant Networks. In Proceedings of the 2019 International Conference on Computing, Networking and Communications, ICNC 2019, Honolulu, HI, USA, 18–21 February 2019; pp. 911–917. [Google Scholar]
- Wu, F.; Yang, W.; Lu, J.L.; Lyu, F.; Ren, J.; Zhang, Y.X. RLSS: A Reinforcement Learning Scheme for HD Map Data Source Selection in Vehicular NDN. IEEE Internet Things J. 2022, 9, 10777–10791. [Google Scholar] [CrossRef]
- Aboud, A.; Touati, H.; Hnich, B. Hybrid 802.11 p-cellular architecture for NDN-based VANET. Int. J. Commun. Syst. 2022, 36, e5393. [Google Scholar] [CrossRef]
- Quang Minh, N.; Yamamoto, R.; Ohzahata, S.; Kato, T. Performance evaluation of MANET based on named data networking using hybrid routing mechanism. J. Commun. 2019, 14, 819–825. [Google Scholar] [CrossRef]
- Gameiro, L.; Senna, C.; Luís, M. Ndniot-fc: Iot devices as first-class traffic in name data networks. Future Internet 2020, 12, 207. [Google Scholar] [CrossRef]
- Javaheri, A.; Hashemi, S.N.S.; Bohlooli, A. Hybrid Naming Scheme Based PURSUIT Architecture for Smart City. In Proceedings of the 2020 4th International Conference on Smart City, Internet of Things and Applications (SCIOT), Mashhad, Iran, 16–17 September 2020; pp. 33–38. [Google Scholar] [CrossRef]
- Majed, A.-q.; Wang, X.; Yi, B. Name lookup in named data networking: A review. Information 2019, 10, 85. [Google Scholar] [CrossRef]
- Chen, Z.; Kim, J.; Lee, M. Named-Data Network based secure communication strategy for smart cities. Internet Technol. Lett. 2021, 4, e211. [Google Scholar] [CrossRef]
- Hlaing, H.H.; Funamoto, Y.; Mambo, M. Performance Comparison of Hybrid Encryption-based Access Control Schemes in NDN. In Proceedings of the 2021 17th International Conference on Mobility, Sensing and Networking (MSN), Exeter, UK, 13–15 December 2021; pp. 622–627. [Google Scholar]
- Hussain, S.; Ullah, S.S.; Gumaei, A.; Al-Rakhami, M.; Ahmad, I.; Arif, S.M. A Novel Efficient Certificateless Signature Scheme for the Prevention of Content Poisoning Attack in Named Data Networking-Based Internet of Things. IEEE Access 2021, 9, 40198–40215. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).