Abstract
We conduct a cryptanalysis of the Vehicle-to-Infrastructure (V2I) handover authentication protocol newly developed by Son et al., which incorporates blockchain technology for authentication purposes. Although this approach is notably efficient, our analysis reveals that the protocol is vulnerable to vehicle impersonation attacks, traceability attacks, and trusted authority (TA) circumvention attacks. To address these security vulnerabilities, we propose an enhanced protocol integrating Schnorr signature-based authentication, dynamically refreshed temporary identities, and TA-anchored credential mechanisms. We validate its security through heuristic analysis and formal verification using ProVerif. Furthermore, a comprehensive comparison with various related schemes confirms that the new protocol achieves a higher level of security while simultaneously maintaining satisfactory efficiency in both the computational and communication aspects.
Keywords:
vehicular ad hoc networks; Schnorr signatures; forward secrecy; low-latency authentication; ProVerif MSC:
94A60
1. Introduction
With the rapid progression of vehicle technologies, satellite communications [1], and Cyber–Physical Systems (CPSs), vehicles are increasingly becoming intelligent [2,3]. Among these advancements, Intelligent Transportation Systems (ITSs) have become a significant area of focus [4,5], garnering substantial interest from industry and academia alike. Vehicular Ad Hoc Networks (VANETs) are a critical component of future ITS development [6]. In VANETs, vehicles within ITS collect environmental data using On-Board Units (OBUs) and transmit this information to other vehicles and roadside infrastructure. Developments in edge computing, artificial intelligence, and advanced in-vehicle communication technologies further drive the growth of VANETs. The primary aim of VANETs is to establish an extensive, integrated network that allows intelligent vehicles to efficiently share data and resources. This integration enables a variety of vehicle applications, including safety, efficiency, and third-party entertainment services. Due to the high-speed dynamic properties of vehicles, the above information interaction process must ensure a stable and continuous connection between the vehicle and the Internet.
However, the inherently open nature of wireless communication channels in VANETs makes them susceptible to significant security threats, such as replay attacks, identity impersonation, and man-in-the-middle attacks [7]. In addition, as the vehicle travels, it will cross the communication range of several roadside infrastructures. Therefore, handover authentication mechanisms are also required to achieve stable and secure communication. This mechanism must ensure communication confidentiality and integrity while facilitating mutual authentication and key establishment, resisting typical protocol attacks, and maintaining high performance.
Blockchain technology has been introduced for VANET authentication due to its tamper-resistant and decentralized features [8,9]. The primary goal of employing blockchain for handover authentication is to enable Roadside Units (RSUs) to store historical access data for vehicle authentication. This storage allows RSUs to swiftly verify vehicle identities based on past access data, greatly streamlining the re-authentication process. This methodology offers numerous advantages, including reducing dependency on remote servers for vehicles that have been previously authenticated, lowering the number of authentication rounds, and decreasing computational and communication burdens. Moreover, it enhances the security of both RSUs and intelligent vehicles.
1.1. Related Work
Qu et al. [10] conducted a study utilizing Public Key Infrastructure (PKI) to manage security services in VANETs, focusing on entities with wireless access and communication mechanisms. Cui et al. [11] noted that PKI-based systems are advantageous for secure information exchange in VANETs, facilitating entity authentication and message integrity verification. Yang et al. [12] proposed a signature-based protocol for rapid handover authentication in VANETs, acknowledging the incompatibility of long authentication latencies with the high mobility of vehicles in VANET environments. This protocol reduces latency in identity verification by removing the need for multiple-party interactions. Ref. [13] discussed a novel authentication protocol for fog-enabled VANETs based on the multiple-trusted-authority model, which reduces the chance of service unavailability and single-point-of-failure.
Xu et al. [14] introduced an LTE-A anonymous handover authentication scheme for vehicular networks, acknowledging the necessity of concealing vehicle identities from message recipients due to mobility across different Roadside Units (RSUs). Anonymous handover ensures the confidentiality of vehicle identities, thwarting potential location tracking by attackers. Liu et al. [15] highlighted the inability of many handover authentication protocols to address serious threats such as unauthorized access and impersonation attacks. To counter these challenges, they suggested a decentralized and anonymous authentication scheme that supports seamless handover by incorporating blockchain technology.
Wang et al. [16] observed that vehicles entering new infrastructure coverage areas in VANETs face complex re-authentication processes. They recommended a scalable computation scheme aided by blockchain technology, facilitating vehicle handover authentication via secure ownership transfer mechanisms. Maria et al. [17] merged bilinear pairing technology with blockchain to expedite handover authentication between RSUs, significantly minimizing computational overhead. Su et al. [18] proposed a hybrid blockchain-based privacy-preserving authentication scheme, while a pre-authentication mechanism was used to accelerate the cross-domain authentication of vehicles.
1.2. This Work
In 2022, Son et al. [19] introduced a blockchain-based handover authentication protocol for VANETs, aiming to enhance system efficiency and security. Their protocol was validated for security using the well-established BAN Logic.
They claimed that the proposed protocol had resistance to various attacks and could ensure security properties such as perfect forward secrecy and anonymity. However, our analysis reveals vulnerabilities in their design. Despite the innovative design leveraging blockchain’s tamper-proof nature for computational and communication efficiency, our in-depth analysis of the protocol revealed several flaws, which make the protocol impractical for actual deployment. Therefore, we first demonstrate successful attacks against their protocol, then propose a security-enhanced handover authentication protocol to fix these issues. In the initial authentication stage, we implemented a strategy involving hiding fake identities. This method aims to protect the true identity of users from being disclosed. By updating the temporary identity, we ensure the anonymity of the identity throughout the entire switching authentication process. This design effectively prevents issues related to traceability and also prevents synchronization attacks. We adopted the well-known Schnorr signature mechanism, which can effectively resist various attacks, including vehicle impersonation attacks and TA bypass attacks. Finally, a thorough analysis of the security and operational performance of the improved protocol is presented.
The remainder of the paper is structured as follows. Section 2 introduces the system model and adversary model of the protocol. Section 3 reviews the protocol by Son et al. Our cryptanalysis of their protocol is detailed in Section 4. The enhanced protocol is presented in Section 5. Section 6 presents a security analysis of the improved protocol. Additionally, Section 8 presents a comprehensive analysis of the performance of the protocol. Finally, our conclusions are presented in Section 9.
2. Preliminaries
This section introduces elliptic curve cryptography and the Schnorr signature scheme, which we will use as building blocks for our new protocol. Here, we also outline the system models on which such authentication protocols are based and the adversary models used to explore their security.
2.1. Elliptic Curve Cryptography
ECC is a public-key cryptosystem based on the algebraic structure of elliptic curves over finite fields. Let denote a finite field of large prime order p. An elliptic curve E over is defined by the Weierstrass equation , where .
Definition 1
(Elliptic Curve Discrete Logarithm Problem). Given a base point and another point , it is computationally infeasible to determine the unique integer x.
Definition 2
(Elliptic Curve Computational Diffie–Hellman Problem). Given points and , it is computationally infeasible to compute the point in probabilistic polynomial time without the knowledge of either a or b.
2.2. Schnorr Signature
The Schnorr signature [20] is a digital signature scheme based on the discrete logarithm problems proposed by Schnorr in 1991. It has the characteristics of simplicity, efficiency, and security, and is widely used in many security protocols. The core of this algorithm is to generate a pair of signatures using the user’s private key and public key, which can prove that the sender of the message has the corresponding private key without exposing the private key itself. The algorithm consists of three main steps: the setup phase, signature generation, and verification.
- Setup: Assume group is a cyclic group of order n. The signer chooses a private signing key x from the set . The public verification key is .
- Signature generation: The signer selects a random number k, calculates the temporary public key , and then computes the hash values, and , to generate the signature pair , where g is a generator of the group , and k is an element of the set .
- Signature verification: The verifier confirms the validity of the signature by calculating the hash value and verifying whether is equal to R.
2.3. System Model
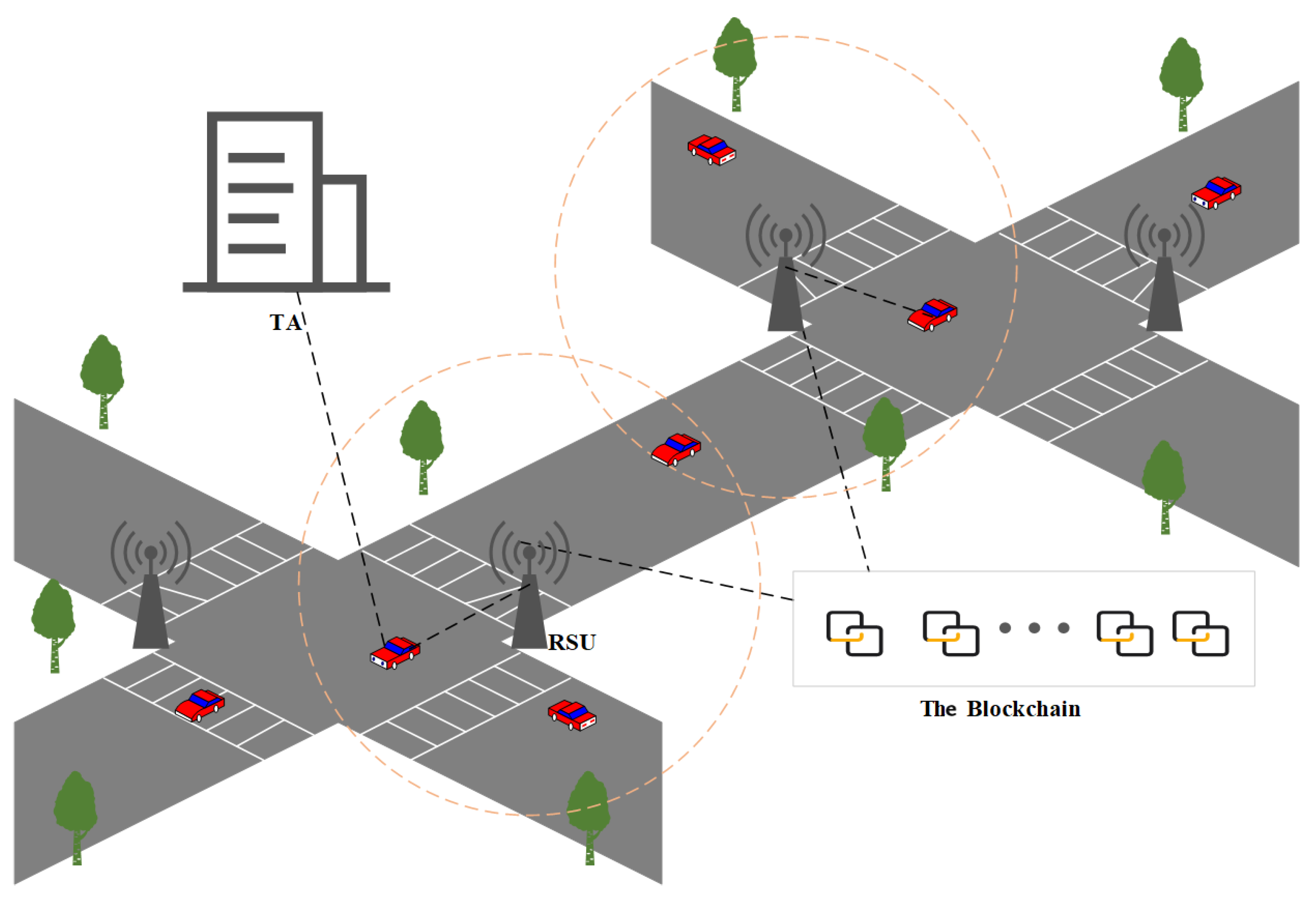
Figure 1 illustrates the blockchain-based handover authentication architecture within VANETs. This architecture includes four key components: the TA, RSUs, vehicles, and, finally, blockchain. Each component has a specific, well-defined role:
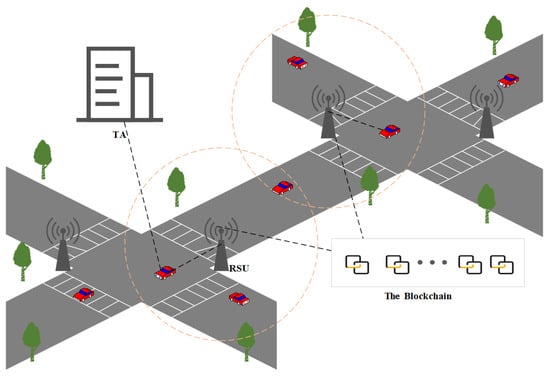
Figure 1.
Systematic architecture of proposed scheme.
- 1.
- TA: The TA disseminates vital public system parameters. During the registration phase, it selects identities and private keys for the RSUs and issues smart cards to vehicles.
- 2.
- RSUs: RSUs are crucial for vehicle authentication before establishing communication links. They have the computational capacity for authenticating in-zone vehicles and act as ledger guardians and transaction nodes on the blockchain. In handover scenarios, RSUs verify vehicle authenticity using blockchain data.
- 3.
- Vehicles: Vehicles, equipped with computationally limited OBUs, register with the TA and authenticate with RSUs to facilitate real-time traffic and entertainment data transmission.
- 4.
- Blockchain: RSUs function as active nodes in the blockchain. After successful vehicle-to-RSU authentication, RSUs upload key elements—temporary identity, randomized data, and vehicle hash—to the blockchain, enabling quick vehicle identity authentication using the stored information.
2.4. Adversary Model
To evaluate the security of the protocol, it is crucial to define the capabilities of potential attackers. The widely recognized Dolev–Yao threat model [21] is widely used for assessing the security of authentication protocols. In this model, the adversary, denoted as , has the following capabilities:
- has complete control over the public communication channel, which includes the ability to eavesdrop and to modify and delete messages exchanged between entities.
- is capable of conducting side-channel attacks to extract stored values from physical devices [22,23,24].
- has unrestricted access to the parameters of all entities, including their identities and public keys, as well as to unauthorized users.
3. Review of the Scheme of Son et al. [19]
This section reviews the protocol proposed by Son et al. [19], which involves three entities, i.e., vehicles, RSUs, and a TA, as key components. The protocol consists of five phases: system setup, vehicle registration, initial V2I authentication, blockchain-based handover authentication, and vehicle revocation. For clarity, Table 1 summarizes the notations used in the protocol.

Table 1.
Notation Guide.
3.1. System Setup
The system setup phase includes the following steps:
- Step 1:
- The TA initializes an elliptic curve , with P as its generator in . A secret master key , a one-way hash function , and a fuzzy verifier l () are chosen by the TA. Secret and shared keys are deployed to each RSU.
- Step 2:
- The TA generates a distinct identifier for , computed as and . The triplet is then shared with .
- Step 3:
- Upon receiving this information, calculates a public key and securely stores the values . This exchange occurs via a secure communication channel.
3.2. Vehicle Registration
Before authentication with an RSU, vehicle must register with the TA, which is carried out over a secure channel. The registration process involves the following steps:
- Step 1:
- generates a unique identity and password , along with a random . It calculates and , forwarding to the TA.
- Step 2:
- The TA checks ’s registration status and whether is revoked. If not, the TA randomly chooses , computes , and securely stores . The TA updates with , which is transmitted to , while is uploaded to the blockchain.
- Step 3:
- After receiving , performs computations: , , , and mod l). These values update as for future use.
3.3. Initial V2I Authentication
Following registration, begins authentication with . The initial V2I authentication process is as follows:
- Step 1:
- enters and into , triggering several computations. calculates , , , , and . Then, it verifies whether mod l).
- Step 2:
- selects a random and computes , , , and . It sends the computed values to .
- Step 3:
- checks the timestamp , calculates , and derives . It confirms the presence of in the blockchain and verifies , authenticating .
- Step 4:
- generates random values and and a timestamp . The RSU calculates , , , , , and . These values are sent to .
- Step 5:
- Upon receipt, calculates , determines as , and derives as . The RSU checks if equals . If so, uploads to the blockchain.
3.4. Blockchain-Enabled Handover Authentication
When transitions to from , a mutual authentication process between and occurs. The authentication phase consists of the following steps:
- Step 1:
- generates a random value , calculates , and computes . It then transmits these values to .
- Step 2:
- Upon receipt, retrieves the corresponding transaction from the blockchain. The RSU verifies the signature, computes , and checks if .
- Step 3:
- If the values are consistent, calculates and checks if . Upon successful verification, generates random and , then computes , , , , and . These values are then sent to .
- Step 4:
- upon receiving this information, calculates , , and . It verifies . The successful completion of these steps confirms mutual authentication between and . Additionally, appends to the blockchain.
3.5. Vehicle Revocation
During communication, RSUs can detect deviations in ’s behavior. In response, RSUs have the authority to revoke by invalidating via blockchain transactions. This action nullifies , preventing from communicating with other RSUs. This deterrence mechanism is strengthened by the shared blockchain transactions among RSUs, enabling the identification of unauthorized activities by . Furthermore, if attempts re-registration with the TA, it must submit . The TA can infer from and stored values, thereby rejecting ’s registration request.
4. Cryptanalysis of Son et al.’s [19] Protocol
Son et al. claim that their protocol fulfills the essential security properties required for a handover authentication scheme [19]. Nevertheless, our analysis exposes several crucial vulnerabilities in their protocol, such as susceptibility to vehicle impersonation, traceability, and susceptibility to TA circumvention attacks.These attacks can result in privacy violations and data tampering, and in severe cases, they may compromise system security, leading to crashes and system outages. To break through these vulnerabilities, the attacker initially needs to obtain secret data, and k, stored in , typically through power analysis attacks (like side channel attacks). As noted in [10], the remote placement of RSUs makes them vulnerable to physical attacks, allowing to capture and manipulate RSUs, extract cryptographic details, and even relocate tampered RSUs to facilitate further attacks.
4.1. Traceability Attacks
Ensuring vehicle untraceability in VANETs is crucial for protecting privacy. This means preventing attackers from tracing a specific vehicle’s route [25]. Specifically, an attacker should not be able to determine which RSUs a vehicle has passed.
It is generally assumed that RSU administrators/managers will not engage in “active” attacks. However, they may act as “honest-but-curious” adversaries and initiate “passive” attacks. To acquire a vehicle’s RID, we now present two methods through which can acquire a vehicle’s pseudo-identity RID:
Case1: With the secret key of and intercepted data from a public channel, calculates and the pseudo-identity .
Case2: Using the secret key k from a compromised RSU, accesses blockchain transaction data to extract . Then, computes , thus acquiring any vehicle’s pseudo-identity RID authenticated by an RSU.
This enables to associate specific s with a given pseudo-identity RID. Since each vehicle has a unique pseudo-identity, can then identify all RSUs (through their s) that a particular vehicle has encountered. Consequently, effectively compromises the trace privacy of vehicles.
4.2. Vehicle Impersonation Attacks
Vehicle impersonation attacks involve attackers disguising themselves as legitimate vehicles registered with the TA. These attacks pose serious risks, such as obtaining paid services under false pretenses or engaging in malicious activities to avoid detection and punishment, thereby compromising the security of VANETs [26].
Our scrutiny of Son et al.’s initial V2I authentication stage indicated the following major flaw: if an attacker acquires a vehicle’s pseudo-identity RID, they can convincingly impersonate that vehicle and pass the authentication checks of all RSUs. Worryingly, this could even apply to unregistered vehicles, highlighting the severity of this security breach. The vehicle impersonation attack proceeds as follows:
- Step 1:
- selects a random number and a timestamp .
- Step 2:
- Upon choosing the random number and timestamp, computes the following values from the acquired pseudo-identity as the vehicle enters the legitimate :
- Step 3:
- then creates a valid authentication request message .
- Step 4:
- authenticates the message , calculates , and forwards the message to .
- Step 5:
- receives the message and computes , , and .
- Step 6:
- Consequently, both and generate the session key and maintain it.
Through this attack, can convincingly impersonate a legitimate vehicle and gain access to .
4.3. TA Circumvention Attacks
In a secure VANET system, vehicles must register with the TA before accessing services. However, the following attack scenario demonstrates a vulnerability. An RSU administrator can impersonate a TA and complete the vehicle registration process independently. This breach is possible because the legitimate TA uses a shared secret key k with the RSU to verify the vehicle registration information uploaded to the blockchain. An RSU with knowledge of k can bypass the TA, create registration data, and upload it to the blockchain. The attack process unfolds as follows:
- Step 1:
- The vehicle selects and , computes and , and sends to the RSU, not the TA.
- Step 2:
- Upon receiving , the RSU generates and computes .
- Step 3:
- The RSU then uploads to the blockchain.
This process effectively completes the registration of the vehicle by the RSU, allowing the vehicle to authenticate interactions with all RSUs using their registered . Consequently, can launch attacks upon bypassing the TA.
5. Our Improved Protocol
In response to the security issues identified in Son et al.’s protocol, we propose specific enhancements and introduce our improved protocol. Firstly, to mitigate vehicle impersonation attacks, our protocol employs the Schnorr signature. Secondly, we address traceability attacks by reducing the size of parameters uploaded to the blockchain, opting for hashing over signatures. Lastly, to prevent circumvention attacks, we incorporate unique parameters from the TA. The effectiveness of these measures will be demonstrated in the subsequent section. Additionally, our design aims for the protocol to be lightweight.
It is important to note that our new protocol builds upon Son et al.’s framework. Therefore, the general process of both protocols remains similar. To provide a clear explanation and ensure completeness, we will reiterate the identical parts in our description.
5.1. System Setup
The TA establishes an elliptic curve , utilizing P as the generator within the group . Besides selecting a secret key y and its corresponding public key Y, the TA employs a one-way hash function and a fuzzy verifier l, adhering to the condition . The shared parameters k, private key , and identity are securely stored in the RSU following the same system initialization steps as Son’s scheme, where , and .
5.2. Vehicle Registration
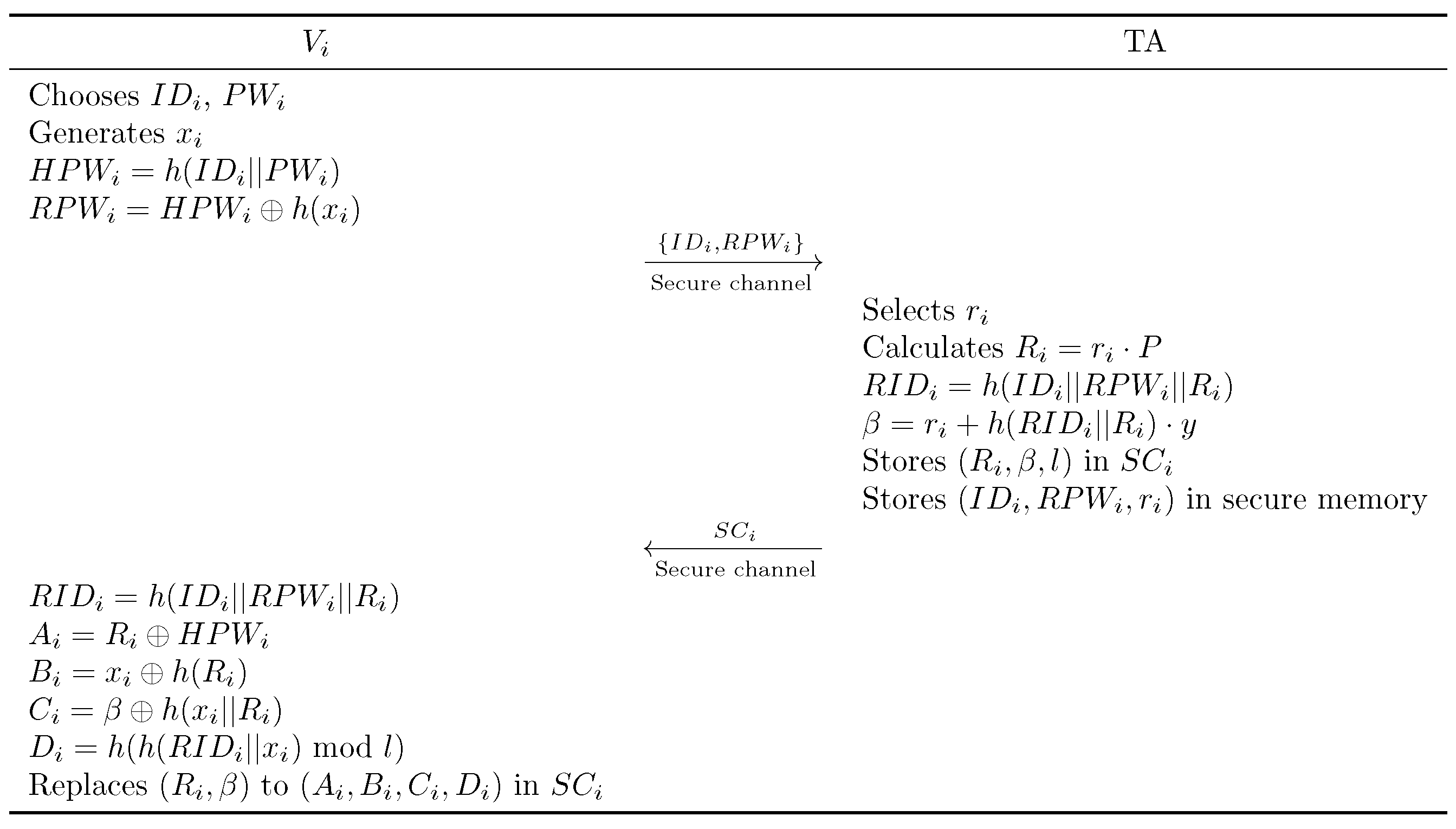
Prior to initiating authentication with an RSU, vehicle must register with the TA. The initial V2I authentication phase is depicted in Figure 2.
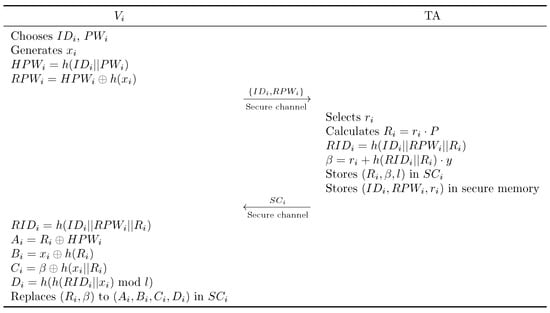
Figure 2.
Vehicle registration phase.
- Step 1:
- generates a unique identity and password , and selects a random number . It then computes and . transmits the values to the TA.
- Step 2:
- The TA verifies whether is already registered and if the corresponding is on the revocation list. If not, TA selects randomly and computes , , , and . TA securely stores and stores in , which is then forwarded to .
- Step 3:
- , upon receiving , performs the following computations: , , , , and . The values in are then replaced with , concluding this phase.
5.3. Initial V2I Authentication
Following the registration phase, the authentication process between and is outlined in Figure 3. The process includes the following steps:

Figure 3.
Initial V2I authentication phase.
- Step 1:
- inputs and into . calculates various values, including , , , , , and . then verifies mod l).
- Step 2:
- If verification is successful, selects a random number and calculates , , , , , and . sends to .
- Step 3:
- On receipt, verifies the timestamp and computes , , and . The RSU retrieves and calculates , where Y is the public key of the TA. It verifies , indicating successful vehicle authentication. The integrity of is also verified by checking if .
- Step 4:
- Subsequently, generates random numbers and and a timestamp . It calculates , , , , , and . transmits to .
- Step 5:
- Upon receiving the message, calculates , , , and verifies . Following successful mutual authentication, uploads to the blockchain.
5.4. Blockchain-Based Handover Authentication
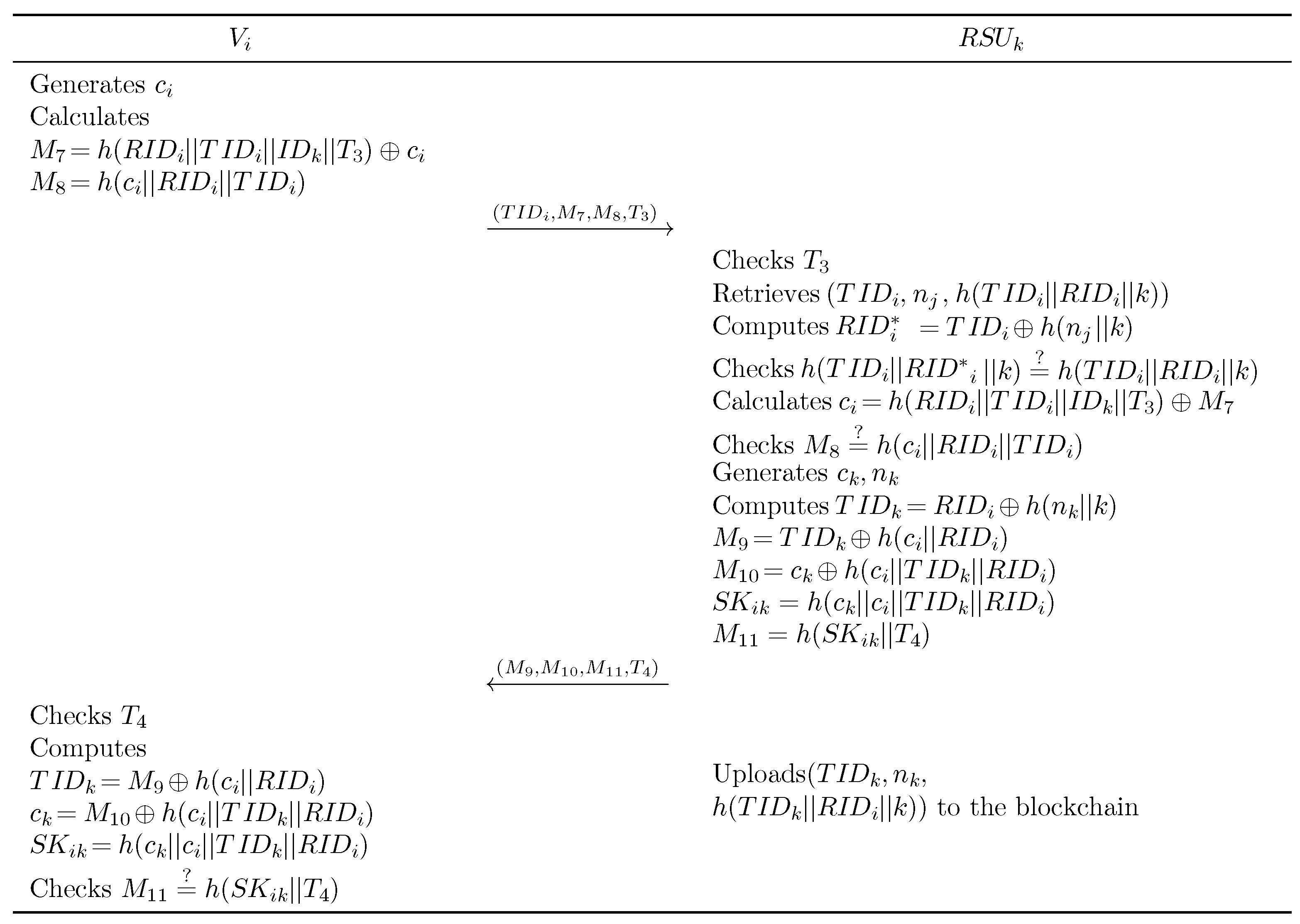
When vehicle successfully authenticates with and enters the coverage area of , it is essential to initiate a new round of mutual authentication between and . The blockchain-based handover authentication procedure is illustrated in Figure 4 and proceeds as follows:
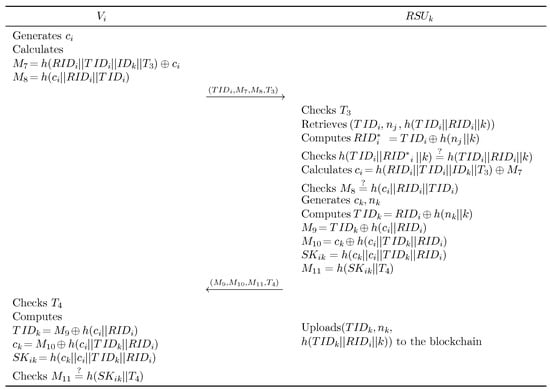
Figure 4.
Blockchain-based handover authentication phase.
- Step 1:
- generates a random value and computes , along with . then transmits to .
- Step 2:
- On receiving this message, retrieves the transaction from the blockchain. It then calculates and verifies whether .
- Step 3:
- If the verification is successful, computes and checks if . Upon confirmation, generates random values and , and calculates , , , , and . then transmits to .
- Step 4:
- Upon receipt, calculates , , and . then verifies if . The successful completion of these steps confirms mutual authentication between and , after which uploads to the blockchain.
5.5. Vehicle Revocation
During communication, if exhibits any inappropriate behavior, it can be detected by RSUs. In response, an RSU can upload a transaction to the blockchain that invalidates the corresponding entry . This action effectively nullifies the validity of , preventing from engaging in further communication with other RSUs. As RSUs collectively access blockchain records, they can quickly identify and flag any unauthorized activities of . Moreover, if attempts to re-register with the TA, it is required to provide during the registration phase. The TA, utilizing along with securely stored data, can derive , enabling it to conclusively reject any registration requests from .
6. Security Analysis of the Improved Protocol
In this section, we first present our design goals related to security features and then offer both heuristic and formal security analyses to demonstrate that our proposed scheme successfully achieves all these design goals.
Security Goals
Our design goals include identity privacy, confidentiality, message integrity, and resistance to common attacks, which are detailed as follows:
- Identity privacy: The proposed protocol should enable vehicle users to authenticate without revealing their identity and ensure that their activities and actions cannot be traced.
- Confidentiality: The proposed protocol needs to ensure that all data and information on public transmission channels remain private and prevent unauthorized access and leakage.
- Message integrity: The proposed protocol needs to ensure that the data transmitted during the authentication process have not been tampered with.
- Resistance to common attacks: The proposed protocol is designed to effectively counter a range of potential security threats, including but not limited to replay attacks and impersonation attacks.
7. Heuristic Security Analysis
The heuristic security analysis of our proposed scheme is outlined as follows:
7.1. Anonymity and Untraceability
In the authentication phase, the vehicle’s real identity is concealed, utilizing the pseudonym . This approach ensures that adversaries cannot determine the actual identity of the vehicle, thereby maintaining anonymity. Moreover, the information uploaded to the blockchain by RSUs, , only serves to verify the vehicle’s RID without revealing the RSU details. The dynamic temporary identity updates via blockchain, and refreshed values using RSU-specific nonces break long-term pseudonym linkage. With being refreshed during each handover authentication, it becomes impossible for adversaries to track the vehicle’s movement across RSUs, ensuring untraceability.
7.2. Mutual Authentication
The improved protocol establishes robust mutual authentication through a bidirectional verification framework. Throughout the authentication phase, both and can deduce the vehicle’s pseudonymous RID from the transmitted vehicle data. In the initial authentication, the vehicle sends and , enabling the RSUs to verify the legitimacy of its pseudonymous RID using the TA’s public key, Y. The RSU cryptographically validates vehicle registration credentials using the TA’s public key through elliptic curve operations, while the vehicle authenticates the RSU by verifying timestamped session key hashes. This step ensures the authentication of by the RSUs. Also, in both the initial and handover authentication phases, the vehicle receives and , respectively. By verifying the source of these messages as being from and , in handover scenarios, infrastructure nodes authenticate vehicles through blockchain-stored identity records, while vehicles confirm RSU legitimacy via temporary identity decryption and session key verification. The protocol achieves mutual authentication.
7.3. Offline Password Guessing Resistance
In the event that an adversary obtains , they might try an offline dictionary attack with a list of identity–password pairs. However, even if they use and to access , verifying the correctness of becomes impossible due to the fuzzy verifier l. The likelihood of accurately guessing is about , which is extremely low and can be considered negligible.
7.4. Impersonation Attack Resistance
In our scheme, only authorized vehicles can input and to generate and create . By integrating Schnorr signatures with Trusted Authority (TA) key binding, we introduce the parameter by integrating Schnorr signatures with TA key binding, where the TA’s private key y cryptographically binds the vehicle registration to authentication processes. This ensures that only TA-registered vehicles can generate valid messages, as forging would require solving the Elliptic Curve Discrete Logarithm Problem (ECDLP), a mathematically intractable task under standardized security assumptions, which RSUs then validate using the TA’s public key. This validation indicates successful registration with the TA, effectively preventing impersonation attacks.
7.5. TA Circumvention Attack Resistance
Our scheme requires vehicles to register with the TA to acquire , uniquely generated by the TA as . Without the TA’s private key, adversaries cannot mimic the registration process, safeguarding against TA circumvention attacks. This process creates an unforgeable trust chain, ensuring all vehicles must undergo legitimate TA registration. Malicious RSUs cannot autonomously provision unauthorized entities. These coordinated measures establish a multi-layered defense architecture that balances security robustness with operational efficiency.
7.6. Replay Attack Resistance
Our approach incorporates timestamps and random numbers to defend against replay attacks. During authentication, the freshness of the timestamp is checked first. The random values and are utilized in establishing the session key, providing a solid defense against replay attacks.
7.7. Perfect Forward Security
Even with access to keys like and k, adversaries cannot calculate the session key due to the inclusion of in the initial authentication phase. Since the necessary random numbers and for the computation of are beyond the reach of adversaries, determining is infeasible. This unavailability also extends to the required for subsequent handover authentication, ensuring our scheme’s provision of perfect forward security.
7.8. Formal Security Analysis Using ProVerif
ProVerif [27] is an automated tool used to analyze and verify the security of cryptographic protocols. It can check properties such as confidentiality, authentication, and resistance to various attacks by formalizing protocols and using logical reasoning. It supports a wide range of protocols, including those based on symmetric and asymmetric encryption. In this section, we utilize ProVerif to evaluate the security of our proposed scheme.
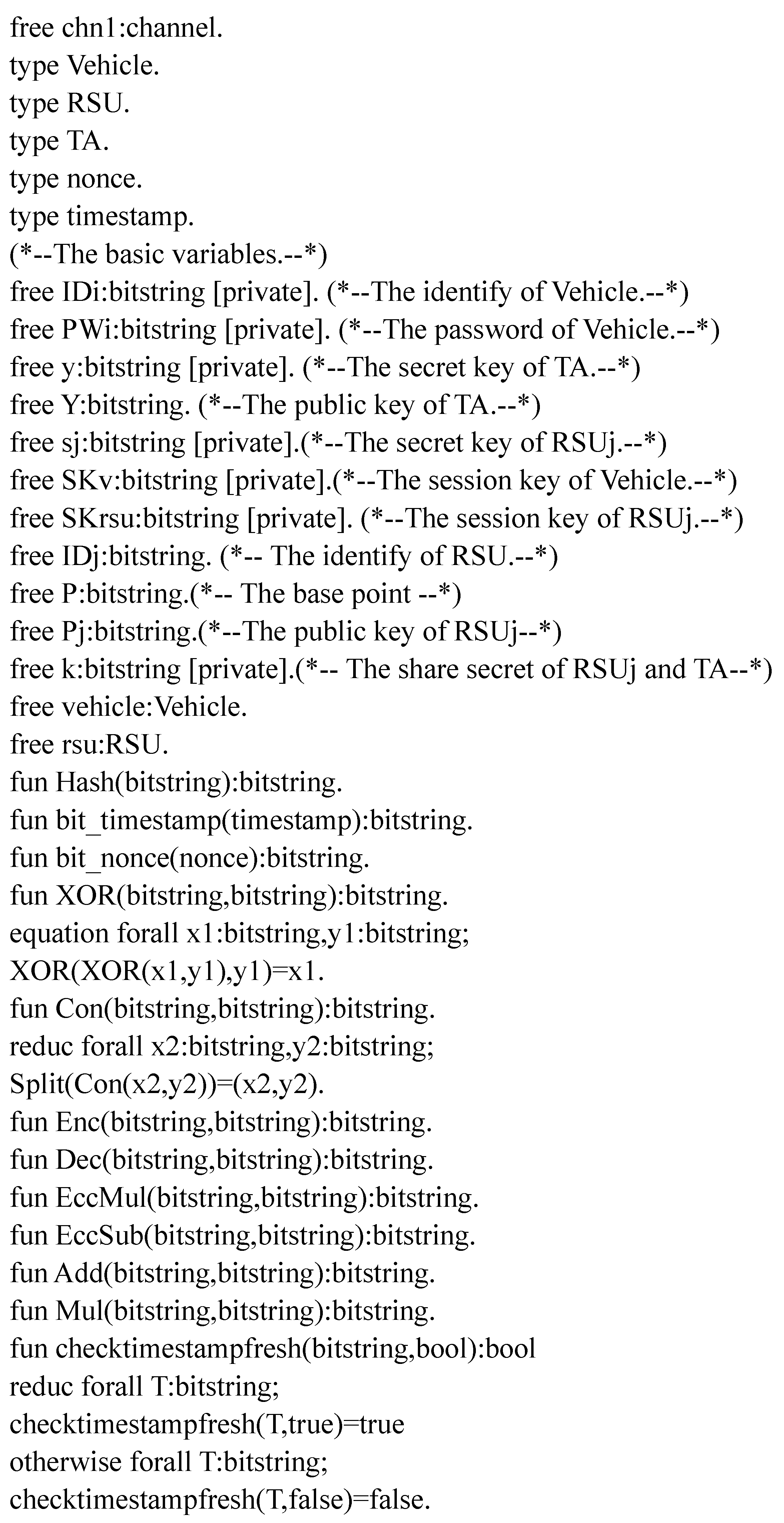
The initial part of the analysis involves the declaration of elements related to our scheme. This includes channels for message transmission, constants, variables, functions, and events, as depicted in Figure 5. Here, we define a public communication channel, ch1, for vehicle–RSU node interactions. Additionally, we establish constants, variables, a hash function , various connection functions, and XOR and ECC operations. The attacker model and associated events are illustrated primarily in Figure 6.

Figure 5.
Definition and function declaration.

Figure 6.
Events and queries.
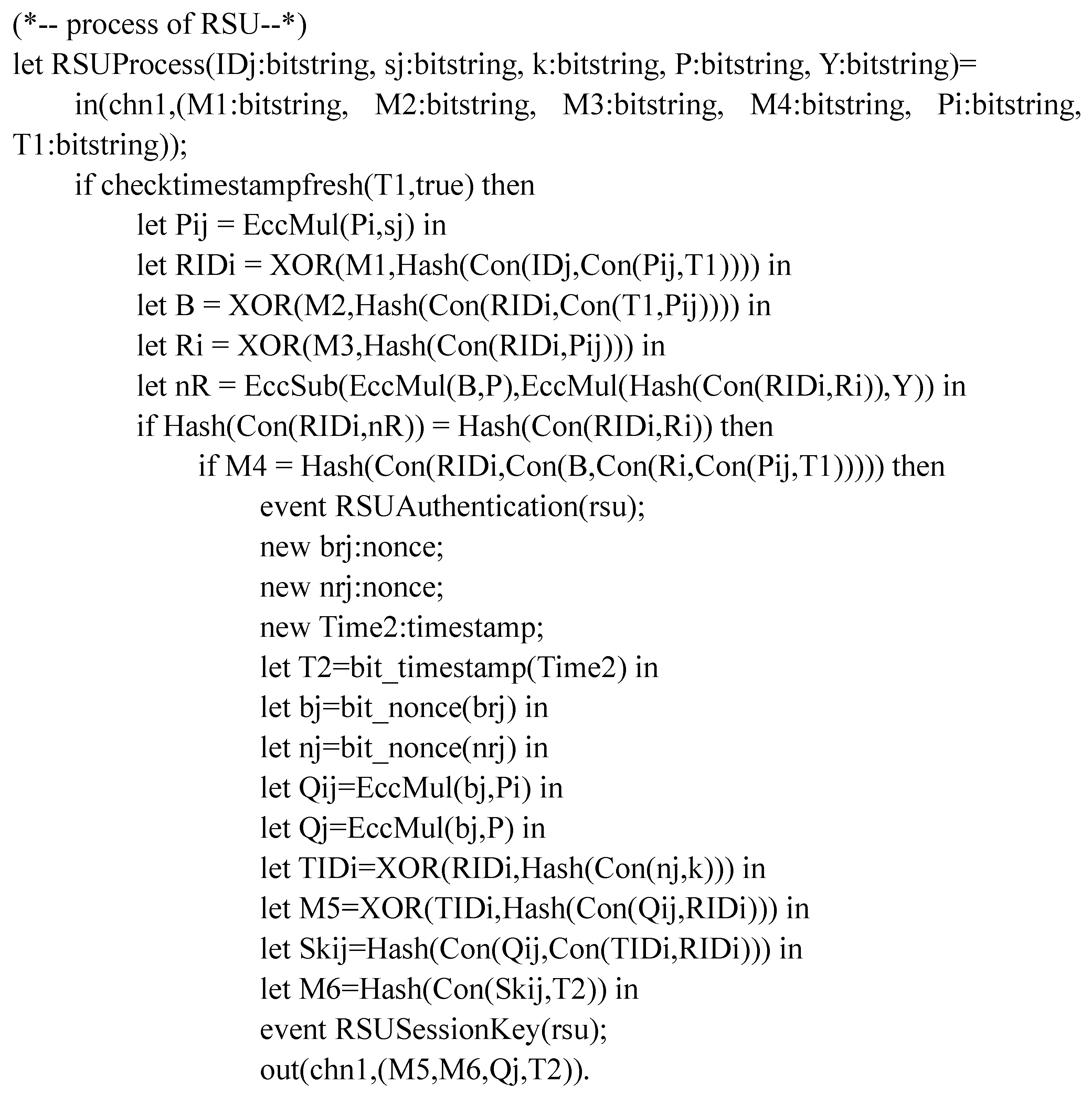
In the next part of the analysis, the focus shifts to the role of vehicles in the authentication process, shown in Figure 7. This process involves vehicles accessing SC-stored data, transmitting an authentication message to the RSU, and formulating a session key based on the information provided by the RSU. The RSU’s role is detailed in Figure 8, which includes decrypting messages using its private key, verifying vehicle identities using the TA’s public key, generating temporary identities and session keys, and securely transmitting these to the vehicle.

Figure 7.
Vehicle authentication process.

Figure 8.
RSU authentication process.
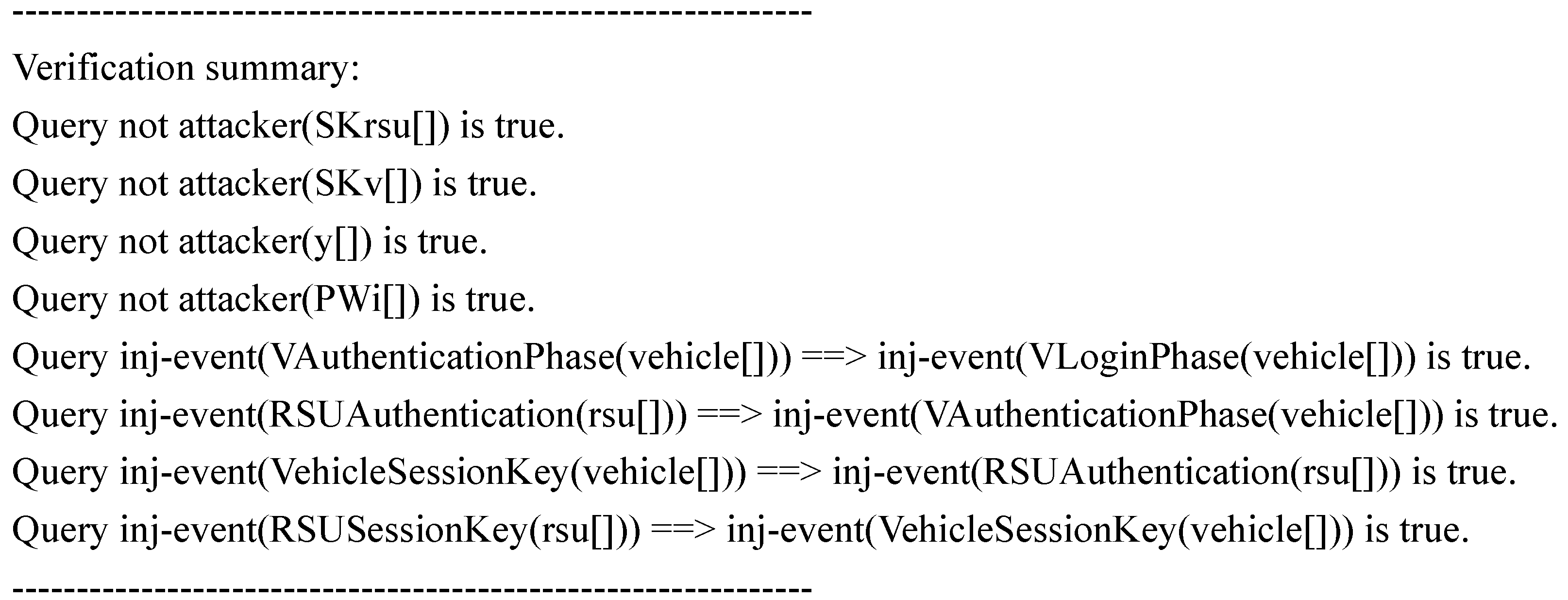
Figure 9 presents the results obtained from ProVerif’s analysis of our scheme. The findings confirm that adversaries are unable to obtain the critical parameters necessary for session key computation, thereby establishing the security robustness of our proposed scheme.
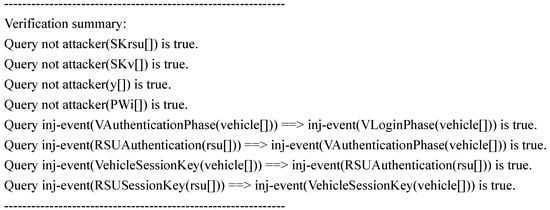
Figure 9.
Results.
8. Performance Comparison
This section presents a detailed performance evaluation of our proposed scheme, focusing on computation, communication, and security aspects. Our performance analysis is based on a comparison between the new protocol and some of the most relevant existing protocols., specifically those detailed in [14,19,28,29].
8.1. Computation Cost
Table 2 offers a comparative analysis of computational costs, contrasting our proposed scheme with those referenced. The evaluations were conducted using a personal computer equipped with an Intel(R) Core(TM) i5-1035G1 CPU @ 1.00 GHz, 1.19 GHz, 16.0 GB RAM, and a Windows 10 64-bit operating system. We denote the computation times for cryptographic one-way hash functions, elliptic curve point operations, and symmetric encryption/decryption functions as , , and , respectively, with respective durations of 0.056 ms, 2.806 ms, and 0.062 ms.

Table 2.
Comparison of computation cost.
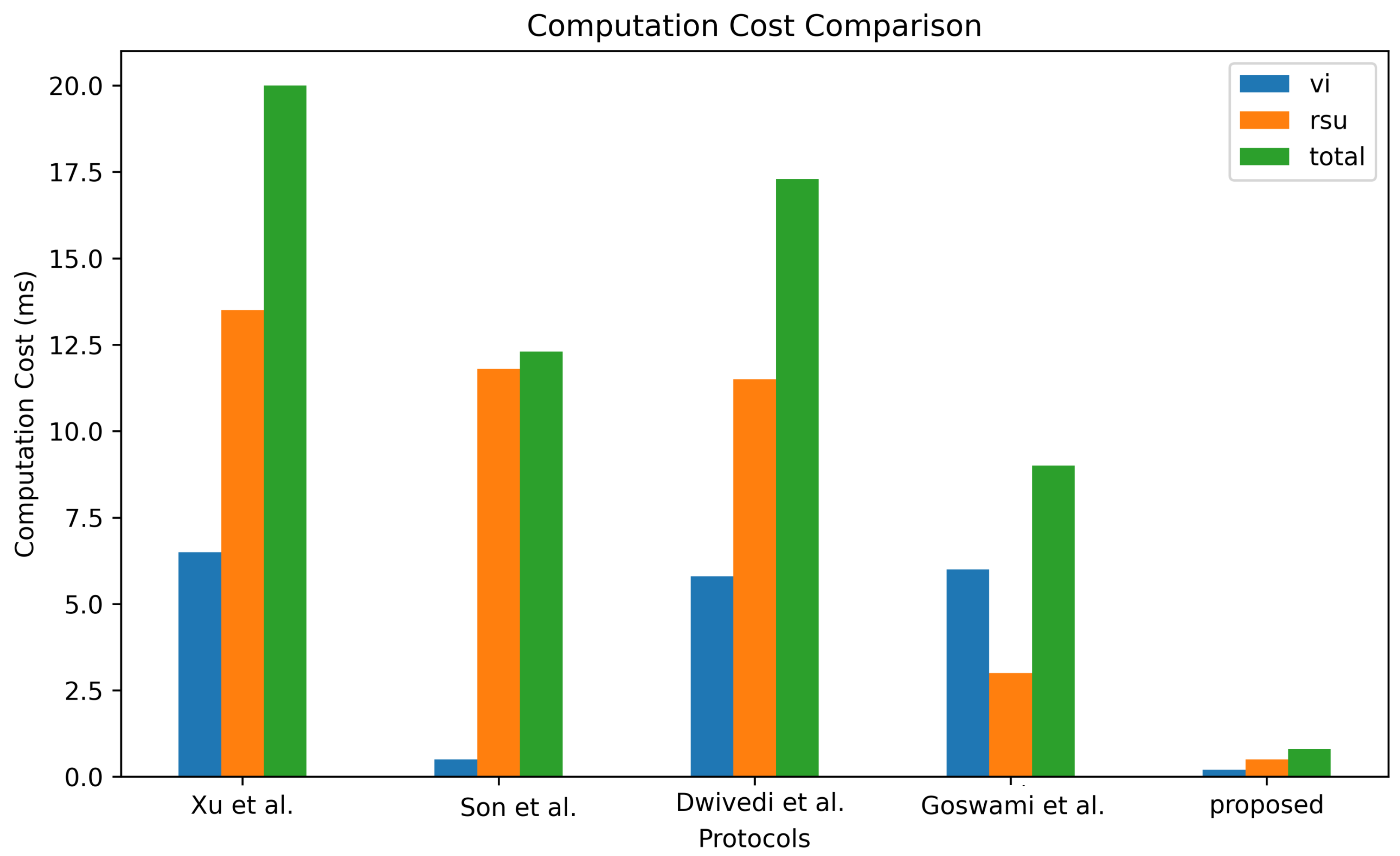
Notably, the initial authentication in our scheme is a one-time occurrence, followed by successive handover authentications. Thus, our analysis primarily focuses on the handover authentication overhead for comparison. In our scheme, the computation cost for vehicles is quantified as 6, and for the RSU nodes, it is 10. The total computation cost for our scheme, therefore, is approximately ms. In contrast, the total computation costs for the schemes in [14,19] are approximately 20.508 ms and 12.12 ms, respectively. Moreover, the schemes described in [28,29] entail computation times of approximately 17.284 ms and 9.034 ms, respectively. These findings, graphically represented in Figure 10, highlight the lower computational overhead of our proposed scheme compared to the aforementioned alternatives.
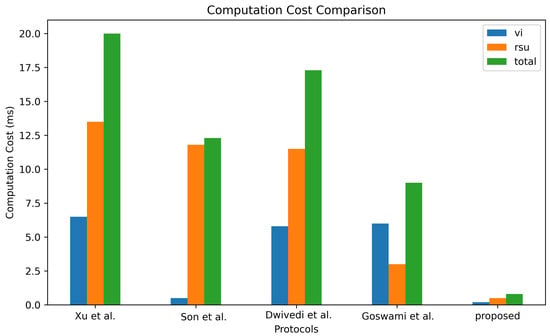
Figure 10.
Comparison of computation cost [14,19,28,29].
8.2. Communication Cost
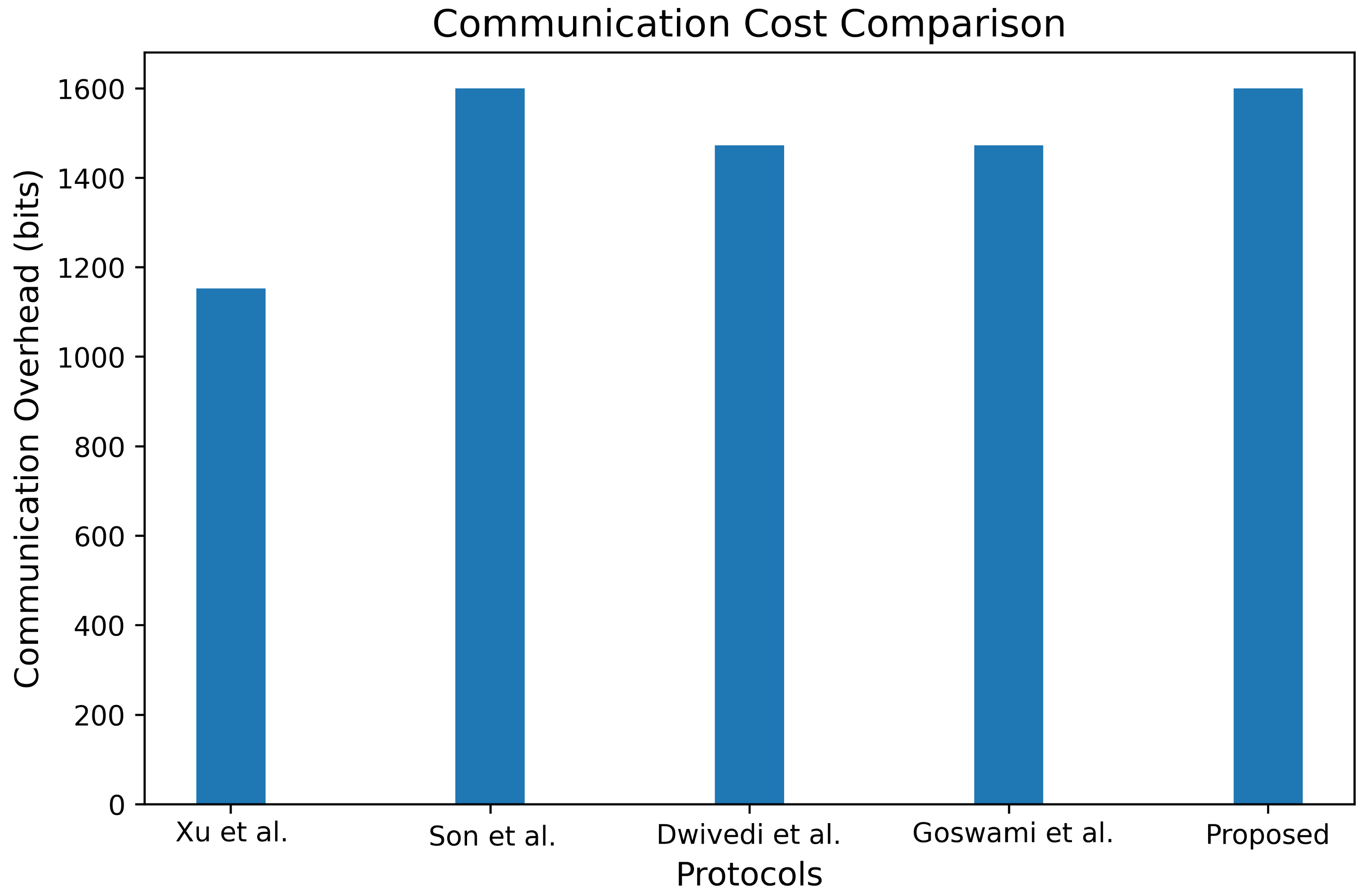
Table 3 provides a comparative analysis of communication costs, contrasting our proposed scheme with referenced alternatives. This assessment specifically evaluates the communication costs incurred during the authentication phase of our scheme. For this analysis, we assume the following sizes: the timestamps, identities, and random numbers are set to 32 bits, 160 bits, and 160 bits, respectively; the encryption/decryption processes utilize 256 bits; and the hash function output is set at 256 bits. The size of the elliptic curve point, represented as , is established at 320 bits. In our scheme, the communication overhead required in the first authentication is 2240 bits. The communication overhead required in the handover authentication process is 1600 bits. Hence, the total communication of our scheme is 3840 bits.

Table 3.
Comparison of communication costs.
For comparison, the communication costs of the schemes presented in [14,19,28] and [29] are 7264 bits, 3618 bits, 4416 bits, and 1440 bits, respectively. Figure 11 visually demonstrates that the communication overhead of the proposed protocol is much smaller than [14,28]. This juxtaposition highlights that our proposed scheme achieves competitive communication costs in relation to the other referenced schemes. Our protocol balances security and efficiency through optimized cryptographic design. Introducing 159 bits of additional computation addresses four high-risk vulnerabilities while ensuring robust anonymity and forward secrecy.
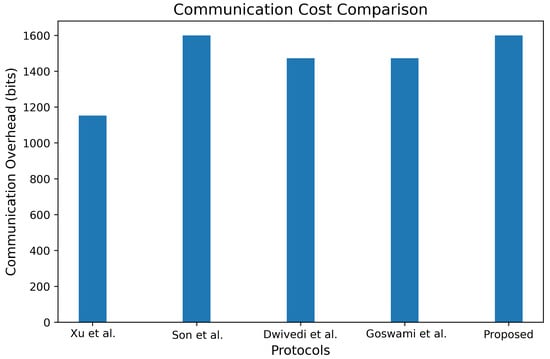
Figure 11.
Comparison of communication costs [14,19,28,29].
8.3. Security Features
Table 4 presents a detailed comparison of security features between our proposed protocol and other existing protocols. This evaluation covers essential attributes such as A1: “Anonymity and Non-traceability Preservation”; A2: “Mutual Authentication”; A3: “Offline Password Guessing Attack Resistance”; A4: “Impersonation Attack Resistance”; A5: “TA circumvention Attack Preservation”; A6: “Replay Attack Resistance”; and A7: “Perfect Forward Secrecy”. As discussed in Section 7, our protocol successfully maintains these security features. In contrast, we analyze the security of the related protocols. The schemes [14,28] achieve the security goal, but their solution consumes a huge amount of computing and communication overhead. We analyzed Son et al. [19]’s protocol and found it to have some security flaws, such as traceability, impersonation attacks, and TA bypass attacks. The requirements of anonymity and traceability are not met by the scheme [29], and it is vulnerable to off-line password guessing attacks and impersonation attacks. Compared with these protocols, our solution is more suitable for VANETs.

Table 4.
Comparison of security features.
9. Conclusions
We identified security vulnerabilities in the blockchain-based handover authentication protocol proposed by Son et al., specifically the vulnerabilities related to vehicle impersonation, traceability, and TA circumvention attacks. Subsequently, we proposed an enhanced blockchain-based protocol. Our protocol effectively mitigates the identified vulnerabilities while maintaining desirable security properties. Through a comprehensive security analysis and a detailed comparison with related protocols, we demonstrated the relative superiority of our protocol in terms of computational efficiency. Although communication efficiency remains an area for potential improvement, we also envision extending this work to address emerging quantum threats. Future iterations could incorporate post-quantum cryptographic primitives such as lattice-based signatures or hash-based commitments to enhance resistance against quantum computing attacks.
Author Contributions
Conceptualization, S.W., B.H. and Y.W.; methodology, S.W. and Y.W.; software, S.W. and K.W.; validation, S.W., K.W. and X.Z.; formal analysis, S.W. and Q.X.; investigation, S.W. and Y.W.; resources, S.W., Y.W. and K.W.; writing—original draft preparation, S.W. and Y.W.; writing—review and editing, S.W. and Y.W.; visualization, S.W., B.H. and X.Z.; supervision, B.H. and Q.X. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Hangzhou Joint Fund of the Zhejiang Provincial Natural Science Foundation of China under Grant No. LHZSZ24F020002 and the National Natural Science Foundation of China under Grant U21A20466.
Data Availability Statement
Data are contained within the article.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Li, F.; Lam, K.Y.; Liu, X.; Wang, J.; Zhao, K.; Wang, L. Joint pricing and power allocation for multibeam satellite systems with dynamic game model. IEEE Trans. Veh. Technol. 2017, 67, 2398–2408. [Google Scholar] [CrossRef]
- Hussain, R.; Zeadally, S. Autonomous cars: Research results, issues, and future challenges. IEEE Commun. Surv. Tutor. 2018, 21, 1275–1313. [Google Scholar] [CrossRef]
- Sun, Y.; Song, H. Secure and Trustworthy Transportation Cyber-Physical Systems; Springer: Berlin/Heidelberg, Germany, 2017. [Google Scholar] [CrossRef]
- Sharma, S.; Kaushik, B. A survey on internet of vehicles: Applications, security issues & solutions. Veh. Commun. 2019, 20, 100182. [Google Scholar] [CrossRef]
- Dai, Y.; Xu, D.; Maharjan, S.; Qiao, G.; Zhang, Y. Artificial intelligence empowered edge computing and caching for internet of vehicles. IEEE Wirel. Commun. 2019, 26, 12–18. [Google Scholar] [CrossRef]
- Arthurs, P.; Gillam, L.; Krause, P.; Wang, N.; Halder, K.; Mouzakitis, A. A taxonomy and survey of edge cloud computing for intelligent transportation systems and connected vehicles. IEEE Trans. Intell. Transp. Syst. 2021, 23, 6206–6221. [Google Scholar] [CrossRef]
- Garg, T.; Kagalwalla, N.; Churi, P.; Pawar, A.; Deshmukh, S. A survey on security and privacy issues in IoV. Int. J. Electr. Comput. Eng. 2020, 10, 5409–5419. [Google Scholar] [CrossRef]
- Mollah, M.B.; Zhao, J.; Niyato, D.; Guan, Y.L.; Yuen, C.; Sun, S.; Lam, K.Y.; Koh, L.H. Blockchain for the Internet of Vehicles Towards Intelligent Transportation Systems: A Survey. IEEE Internet Things J. 2021, 8, 4157–4185. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Liang, K. BPAS: Blockchain-assisted privacy-preserving authentication system for vehicular ad hoc networks. IEEE Trans. Ind. Inform. 2019, 16, 4146–4155. [Google Scholar] [CrossRef]
- Qu, F.; Wu, Z.; Wang, F.Y.; Cho, W. A security and privacy review of VANETs. IEEE Trans. Intell. Transp. Syst. 2015, 16, 2985–2996. [Google Scholar] [CrossRef]
- Cui, J.; Wei, L.; Zhang, J.; Xu, Y.; Zhong, H. An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2018, 20, 1621–1632. [Google Scholar] [CrossRef]
- Yang, A.; Weng, J.; Yang, K.; Huang, C.; Shen, X. Delegating authentication to edge: A decentralized authentication architecture for vehicular networks. IEEE Trans. Intell. Transp. Syst. 2020, 23, 1284–1298. [Google Scholar] [CrossRef]
- Pankaj, K.; Hari, O. Multi-TA model-based conditional privacy-preserving authentication protocol for fog-enabled VANET. Veh. Commun. 2024, 47, 100785. [Google Scholar] [CrossRef]
- Xu, C.; Huang, X.; Ma, M.; Bao, H. An anonymous handover authentication scheme based on LTE-A for vehicular networks. Wirel. Commun. Mob. Comput. 2018, 2018, 6251219. [Google Scholar] [CrossRef]
- Liu, X.; Yang, A.; Huang, C.; Li, Y.; Li, T.; Li, M. Decentralized anonymous authentication with fair billing for space-ground integrated networks. IEEE Trans. Veh. Technol. 2021, 70, 7764–7777. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.F.; Liu, J. B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Maria, A.; Pandi, V.; Lazarus, J.D.; Karuppiah, M.; Christo, M.S. BBAAS: Blockchain-based anonymous authentication scheme for providing secure communication in VANETs. Secur. Commun. Netw. 2021, 2021, 1–11. [Google Scholar] [CrossRef]
- Su, H.; Dong, S.; Zhang, T. A hybrid blockchain-based privacy-preserving authentication scheme for Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2024, 73, 17059–17072. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of Blockchain-Based Lightweight V2I Handover Authentication Protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Chen, X.; Yang, A.; Tong, Y.; Weng, J.; Weng, J.; Li, T. A multisignature-based secure and OBU-friendly emergency reporting scheme in VANET. IEEE Internet Things J. 2022, 9, 23130–23141. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Randolph, M.; Diehl, W. Power side-channel attack analysis: A review of 20 years of study for the layman. Cryptography 2020, 4, 15. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A privacy-preserving and scalable authentication protocol for the internet of vehicles. IEEE Internet Things J. 2020, 8, 1123–1139. [Google Scholar] [CrossRef]
- Liang, Y.; Luo, E.; Liu, Y. Physically secure and conditional-privacy authenticated key agreement for VANETs. IEEE Trans. Veh. Technol. 2023, 72, 7914–7925. [Google Scholar] [CrossRef]
- Xu, Z.; Li, X.; Xu, J.; Liang, W.; Choo, K.K.R. A secure and computationally efficient authentication and key agreement scheme for internet of vehicles. Comput. Electr. Eng. 2021, 95, 107409. [Google Scholar] [CrossRef]
- Wang, C.; Huang, R.; Shen, J.; Liu, J.; Vijayakumar, P.; Kumar, N. A novel lightweight authentication protocol for emergency vehicle avoidance in VANETs. IEEE Internet Things J. 2021, 8, 14248–14257. [Google Scholar] [CrossRef]
- Abadi, M.; Blanchet, B.; Comon-Lundh, H. Models and Proofs of Protocol Security: A Progress Report. In Computer Aided Verification; Bouajjani, A., Maler, O., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 35–49. [Google Scholar] [CrossRef]
- Dwivedi, S.K.; Amin, R.; Vollala, S.; Khan, M.K. B-HAS: Blockchain-Assisted Efficient Handover Authentication and Secure Communication Protocol in VANETs. IEEE Trans. Netw. Sci. Eng. 2023, 10, 3491–3504. [Google Scholar] [CrossRef]
- Goswami, A.; Rana, S.; Chhikara, D. An efficient blockchain assisted dynamic authentication scheme for geo-spatial enabled vehicular network. Telecommun. Syst. 2023, 83, 241–251. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).