Abstract
Software trustworthiness is an important research field in software engineering. In order to appropriately evaluate it, some different measurement approaches have been proposed, which have important guiding significance for improving software trustworthiness. Recently, we have investigated attributes-based approaches. That is, how to maximize trustworthy degree of some software satisfying a given threshold by adjusting every attribute value such that the cost is minimal, i.e., the sum of all attribute values is as small as possible. The work is helpful to improve the software quality under the same cost. This paper continues this work and considers a reallocation approach to dealing with the problem that the threshold and the minimal constraints of every attribute values dynamically increase. In this process, the costs of trustworthiness improvement should be ensured to be minimal. For this purpose, we firstly define a reallocation model by mathematical programming. Then we introduce the notion of growth function. Based on this, a polynomial reallocation algorithm is designed to solve the above reallocation model. Finally, we verify our work on spacecraft softwares and the results show that this work is valid.
1. Introduction
Software trustworthiness is the ability of software to satisfy user expectation with its behaviors and results and to still provide continuous services by disturbances [1]. It can be characterized by many software attributes [1,2,3,4,5,6,7], which are called trustworthy attributes. Software trustworthiness measurement depicts how to calculate the trustworthy degree of software based on the given trustworthy attributes’ values and their weight values. It can provide a basis for guiding and improving the trustworthiness of design and implementation of software. Therefore, software trustworthiness measurement becomes one of the core scientific problems in researching software trustworthiness [1]. Many measures based on trustworthy attributes are established. In view of the use of more rigorous methods to evaluate software trustworthiness and theoretical validation of models, Tao et al. apply axiomatic approaches to assess software trustworthiness, present the desirable properties of software trustworthiness measures and establish a series of measures complying with these properties [8,9,10,11,12,13,14]. Ding et al. combine utility theory and evidence theory to measure software trustworthiness [15]. They use the utility values of expert scoring to assess the trustworthy attributes, and merge these values according to the Dempster synthesis rule in the evidence theory as software trustworthiness measurement result [15]. Hauke et al. present the requirements for robust probabilistic trust assessment by use of supervised learning, and apply a selection of estimators to a real-world data set to show the effectiveness of supervised methods [16]. Muhammad et al. use the scoring upon the completion of system testing execution to rate software trustworthiness. The rating strategy is based on multiple level calculations that produce a final rating, including test strategies imposed, completeness of system test execution, test iterations, test case priority and test case result for each iteration [17]. Based on trust theory in the field of humanities and sociology, Yang et al. propose a measurable Social-to-Software software trustworthiness framework, and present a whole metric solution for software trustworthiness, namely, the advanced J-M model based on power function, the time-loss rate for ability trustworthiness measurement and the fuzzy comprehensive evaluation model [18]. Wang et al. design and implement TRUSTIE to balance the crowd wisdom and software trustworthiness in a well-controlled way, and evaluate the trustworthiness of software development activities by considering different kinds of software evidences, such as development evidences, sharing evidences and application evidences. These evidences can directly or indirectly reflect trustworthiness attributes which include not only objective quality attributes like correctness, security, but also subjective attributes for example user evaluations [19]. The authors of Cho et al. propose a system-level trustworthiness metric framework that accommodates four submetrics, referred to as STRAM (Security, Trust, Resilience, and Agility Metrics), which gives a hierarchical ontology structure. Moreover, they proposes developing and incorporating metrics describing key assessment tools, including Vulnerability Assessment, Risk Assessment and Red Teaming, to provide additional evidence into the measurement and quality of trustworthy systems [20]. The research on trustworthiness evaluation for specific types of software or intermediate software products by attributes has also achieved fruitful results. Davide et al. elicit the factors that affect the open source software (OSS) trustworthiness through carrying out a survey, collect the objective measures on a sample of 22 Java and 22 C/C++ OSS products by means of the self-developed tool MacXim and subjective evaluations by means of more than 500 questionnaires, and correlate the objective measures to subjective evaluations with a multivariate regression model [21,22]. Han constructs a formal model for the workflow management system trustworthiness measurement and proposes a measurement algorithm from the software behaviour entropy of calculus operators through the principle of maximum entropy and the data mining method [23]. In consideration of the lack of the research on the trustworthiness measurement for software architecture, Jiang et al. establish a trustworthy attribute model of software architecture, and use the Principle of Maximum Entropy and Grey Decision-making Method as the trustworthiness evaluation method of a software architecture [24]. Gene et al. lay out a heuristic systematic model for assessing trust in code. The proposed model describes a five step process of how programmers perceive trust in computer code, including (1) acquisition, (2) initial viewing, (3) in depth look, (4) incorporation, and (5) reevaluation [25]. Wang et al. propose an updating model of software component trustworthiness, they compute the trustworthy degree of the software component based on users’ feedback, and determine the weight of updating by the number of users [26].
Software trustworthiness allocation is the reverse of the software trustworthiness measurement, which refers to the process of determining the trustworthy attribute values according to the minimum trustworthy degree that a given software must achieve, the minimum value which the trustworthy attributes must reach, and the trustworthy attribute weight values of the software. Software trustworthiness allocation is useful to increase the software trustworthiness by adjusting the trustworthy attribute values at the same cost. We have investigated the software trustworthiness allocation approach based on trustworthy attributes which allocates software trustworthiness to trustworthy attributes [27], and the software attribute trustworthiness allocation approach based on sub-attributes which allocates software attribute trustworthiness to sub-attributes [28]. Due to actual needs, the minimum trustworthy degree and the minimum value may be increased, then the software trustworthiness needs to be reallocated to improve the original trustworthy attribute values. Since the trustworthy attribute value is positively correlated with the software research and development cost. Therefore, it is hoped that the software trustworthiness reallocation can minimize the sum of the increases of all the trustworthy attribute values when the trustworthy degree of software is greater than or equal to and each trustworthy attribute value is more than or equal to . In order to resolve the above problem, in this paper we build a mathematical programming (MP) model to reallocate the trustworthy degree of software to its attributes appropriately, present a trustworthy attribute value growth function, and propose a reallocation algorithm for solving this MP based on the growth function. Moreover, trustworthiness reallocation of 11 spacecraft softwares are taken as research objects to show the significance and effectiveness of our work. ISO/IEC DIS 30754 standard aims to provide a consensus specification for software trustworthiness by collating good practice from the five main facets of trustworthiness, namely safety, reliability, availability, resilience and security [29]. They can enable an organization to improve operational effectiveness and efficiency. In addition to the trustworthy attributes mentioned in the ISO/IEC DIS 30754 standard, in our reallocation approach they can also contain other required facets; for example, maintainability. Our reallocation approach can determine the optimal degree of each trustworthy attribute value to be increased with the software trustworthiness improvement requirements satisfied, meanwhile, the trustworthy attribute value is positively correlated with the costs of R & D. Therefore, the adoption of our approach is beneficial to the improvement of enterprise efficiency and the reduction of cost, which is consistent with the goal of ISO/IEC DIS 30754 standard.
The rest of the paper is organized as follows. In Section 2, we describe the materials and methods, including reallocating procedure, software trustworthiness measurement model proposed in [14], a reallocation model for software trustworthiness, a reallocation algorithm and an example based on the trustworthiness reallocation of 11 spacecraft softwares. We present the discussion in Section 3. The conclusions and future work come in the last section.
2. Materials and Methods
The reason for software trustworthiness reallocation is that the software trustworthiness requirement is improved, therefore the software attribute value after reallocation should not be less than the corresponding software attribute value before reallocation. Either the software trustworthiness allocation method [27] or software attribute trustworthiness allocation method [28] can not deal with the above problem. Therefore, they can not be applied for software trustworthiness reallocation. For this reason, we establish a reallocation model based on mathematical programming, and give a polynomial time algorithm to solve the model.
2.1. Reallocating Procedure
The procedure for software trustworthiness reallocation consists of four steps as shown in Figure 1. In order to reallocate the software trustworthiness to attributes, we first need to give a software trustworthiness measurement model. It is used to determine the trustworthy degree of software based on the trustworthy attributes’ values and their weight values. Then the software trustworthiness improvement requirements are captured. They should include the minimum trustworthy degree that a given software must achieve and the minimum value which the trustworthy attributes must reach. The trustworthy attribute values and their weight values before reallocation are definitive in this requirements. In Step 3 a software trustworthiness reallocation model is established. It is applied to describe how to model the reallocation of software trustworthiness to trustworthy attributes according to the measurement model built in Step 1 and the requirements presented in Step 2. Finally, software trustworthiness reallocation algorithm is designed to resolve the reallocation model. Since the elements that need to be included in the software trustworthiness improvement requirements are specified in the Step 2, in the following of this section we will focus on the constructions of software trustworthiness measurement mode and software trustworthiness reallocation model and the design of the software trustworthiness reallocation algorithm.
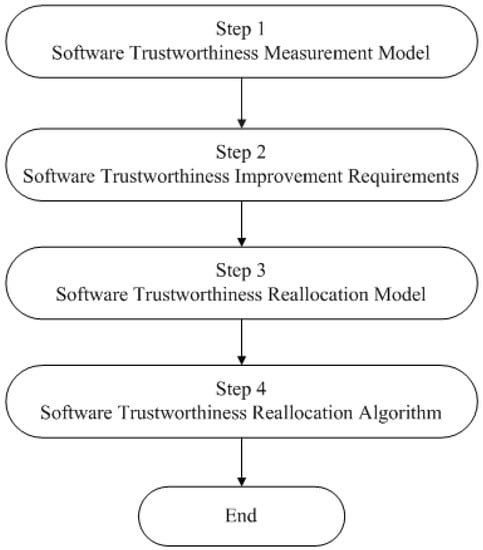
Figure 1.
Reallocating procedure for software trustworthiness.
2.2. Software Trustworthiness Measurement Model
We applied axiomatic approaches to measure software trustworthiness in the view of trustworthy attributes and presented four properties that software trustworthiness measures are required to have, including monotonicity, acceleration, sensitivity and substitutivity [8]. Three new properties were put forward to perfect the property set, i.e., expectability, non-negativity and proportionality [11,12]. And we constructed a software trustworthiness measurement model that satisfies the above properties [13]. Considering the particularities of spacecraft software, a simplified version as shown in Definition 1 was used to measure the spacecraft software trustworthiness [14].
Definition 1.
(Simplified Software Trustworthiness Measurement Model Used in [14])
where
- 1.
- T is the trustworthy degree of software;
- 2.
- n is the number of trustworthy attributes;
- 3.
- is the value of the trustworthy attribute such that , of which is the specified value that all of the trustworthy attributes must reach;
- 4.
- is the weight value of theattribute, with,.
This simplified measurement model not only complies with the properties mentioned above, but is also in agreement with the idea of Cannikin Law. Meanwhile, its effectiveness is validated by applying it to assess the trustworthiness of 23 spacecraft softwares whose total code is about 300,000 lines. The measurement results show that it is suitable for evaluating the spacecraft software trustworthiness, and can accurately detect the weak links in the development process, which is very important for the improvement of the development level of this type of software. In the next subsection, we will build a reallocation model for software trustworthiness according to this.
2.3. Reallocation Model for Software Trustworthiness
As previously described, software trustworthiness reallocation should not only minimize the sum of the increases of all the trustworthy attribute values, but also make sure that the trustworthy degree of software is not less than the required minimum degree and each trustworthy attribute value is more than or equal to the required minimum value. Therefore, a mathematical programming model is constructed as a reallocation model for software trustworthiness on the basis of the simplified measurement model given in the Definition 1.
Definition 2 (Reallocation Model for Software Trustworthiness).
Mathematical Programming (MP)
where
- 1.
- T is the trustworthy degree of software after reallocation;
- 2.
- is the new trustworthy degree that the software must achieve after reallocation;
- 3.
- n is the number of trustworthy attributes;
- 4.
- are the trustworthy attribute values after reallocation;
- 5.
- are the trustworthy attribute values before reallocation;
- 6.
- is the new value that all of the trustworthy attributes must reach after reallocation;
- 7.
- is the increased value of theattribute after reallocation;
- 8.
- is the weight value of theattribute, with,.
Sensitivity is used to describe the percentage change of the degree of software trustworthiness caused by the percentage changes of the values of trustworthy attributes. We perform a sensitivity analysis on the simplified software trustworthiness measurement model given in the Definition 1, it follows that for ,
Sensitivity analysis of this simplified model shows that the greater the attribute weight value is, the more important it is to improve the software trustworthiness. Therefore, it is necessary to increase the value of attribute with the most important weight value as much as possible. At the same time, considering that the trustworthy attribute value after reallocation should be greater than or equal to the trustworthy attribute value before reallocation and the reallocation process should be as simple as possible, the following trustworthy attribute value growth function is defined.
Definition 3 (Trustworthy Attribute Value Growth Function).
where
- 1.
- n is the number of trustworthy attributes;
- 2.
- are the trustworthy attribute values after reallocation;
- 3.
- are the trustworthy attribute values before reallocation;
- 4.
- is the new value that all of the trustworthy attributes must reach after reallocation;
- 5.
- is the weight value of theattribute with,,;
- 6.
- k is the growth rate of the trustworthy attribute value, which follows.
Since for a given software, , , are fixed, substituting the trustworthy attribute value growth function into the objective function in the reallocation model for software trustworthiness, it follows that
Therefore, by substituting the trustworthy attribute value growth function into the reallocation model for software trustworthiness, we can obtain the following reallocation model for software trustworthiness based on trustworthy attribute value growth function.
Definition 4 (Reallocation Model for Software Trustworthiness Based on Trustworthy Attribute Value Growth Function).
Mathematical Programming (MP)
where
- 1.
- k is the growth rate of the trustworthy attribute value, which follows;
- 2.
- n is the number of trustworthy attributes;
- 3.
- is the new value that all of the trustworthy attributes must reach after reallocation, of which;
- 4.
- are the trustworthy attribute values before reallocation such that;
- 5.
- is the weight value of theattribute with,,;
- 6.
- is the new trustworthy degree that the software must achieve after reallocation.
2.4. Reallocation Algorithm for Software Trustworthiness
Let , , , . For the reallocation model for software trustworthiness based on trustworthy attribute value growth function:
- Since for , , and , then for any , it follows that
- (1)
- For , notice that and , then for any , we can derive
- (2)
- For , since and , then from the inequality , we have
In summary, from the inequality constraint in the reallocation model presented in Definition 4
we can obtain
Software trustworthiness allocation allocates trustworthiness to trustworthy attributes according to weight values of trustworthy attributes, so does software trustworthiness reallocation. On the other hand, since , then they are already the maximum value that the trustworthy attribute can take and cannot be increased in the process of trustworthiness reallocation. Therefore, software trustworthiness reallocation based on trustworthy attribute value growth function is actually to find the minimum k satisfying within , where .
The solution process of the MP given in Definition 4:
- When , it is easy to prove that is the optimal solution, and all of the trustworthy attribute values after the reallocation are equal to .
- When ,
- (1)
- if , it is easy to show that is the optimal solution, and all of the trustworthy attribute values after the reallocation are equal to too.
- (2)
- if , letTaking as the initial value of the iteration, Newton iteration method is used to find the approximate root k that satisfies . If , then the trustworthy attribute values are calculated by substituting k into the trustworthy attribute value growth function. For different , and , k solved by Newton iteration method satisfying may be out of the above range. In this case, bringing k into the trustworthy attribute value growth function will cause some trustworthy attribute values to exceed 10. To solve this problem, is modified towhere is a set whose initial value is the empty set ⌀. Substituting the k obtained by the Newton iteration method into the trustworthy attribute value growth function, if there exist trustworthy attribute values which are more than 10, the set of the subscripts of the trustworthy attributes whose values exceed 10 is incorporated into , and the newly obtained set is still recorded as . The trustworthy attributes whose subscripts are in are sorted in descending order according to their weight values, and the values of the attributes with the largest weight value are set to , the values of the attributes with the second largest weight value are set to , the values of the attributes with the third largest weight value are set to , and so on. However, it is necessary to ensure that the trustworthy attribute values satisfy in the process of setting the trustworthy attribute values. Because the software trustworthiness is reallocated according to the weight values of trustworthy attributes, the smaller the attribute weight value is, the smaller the trustworthy attribute value is reallocated. Therefore, the step size is set to for decreasing values, and the step size can be modified according to the specific situation. The initial value of the attribute with the largest weight value can also be changed as needed. In the next round of calculation, Newton iterative method is used to find the new approximate root k that satisfies , and the similar method is applied to update the value of and the values of trustworthy attributes whose subscripts are in . When the set is no longer updated, values of trustworthy attributes whose subscripts are in are calculated by the trustworthy attribute value growth function, values of trustworthy attributes whose subscripts are in are obtained according to the above setting rules, and values of trustworthy attributes whose subscripts are in are equal to 10.00. At this time, the trustworthy attribute values obtained are the reallocation results.
The reallocation algorithm for software trustworthiness is shown in Algorithm 1. Steps 6–7 are used to find the approximate root k satisfying by the Newton iteration method. It takes , where m represents the maximum number of iterations that the designer wishes to perform. Steps 5–32 are a triple nested loop, which are used to reallocate software trustworthiness to trustworthy attributes whose subscripts are in . Since , of which n is the number of trustworthy attributes, the number of loops in the outmost loop is . Steps 9–14 are a for loop, which calculate the values of trustworthy attributes whose subscripts are in according to the trustworthy attribute value growth function. Similarly, because , the number of loops in this for loop is . Steps 19–30 are a double nested loop, which are applied to set the values of trustworthy attributes whose subscripts are in . Since , it follows that , then the number of loops in this double nested loop is . Step 33 is used to reallocate software trustworthiness to trustworthy attributes whose subscripts are in . Due to , Step 33 takes . Thus, the time complexity of Algorithm 1 is . m is usually set to a constant, such as , hence the time complexity of Algorithm 1 is .
| Algorithm 1 Algorithm for reallocating software trustworthiness: for given trustworthy attribute values before reallocation, trustworthy attribute weight values , that the software must achieve after reallocation and that all of the trustworthy attributes must reach after reallocation, output the reallocated trustworthy attribute values |
|
2.5. Example of Software Trustworthiness Reallocation
The simplified software trustworthiness measurement model given in Definition 1 was applied to evaluate the trustworthiness of 23 spacecraft softwares [14]. The trustworthy attributes of spacecraft software are composed of 9 attributes, including (1) overall planning and implementation, (2) analysis and design, (3) test verification, (4) reliability and safety, (5) software technology status change, (6) quality problem close loop, (7) configuration management, (8) software development environment, (9) third party evaluation situation, and their values before reallocation are respectively denoted by . The weight values of these 9 attributes are , which are calculated by the method presented in [9]. The spacecraft software’s trustworthy degree before reallocation computed on the basis of the simplified model is denoted by . The trustworthy attribute values, trustworthy degrees and trustworthy ranks of 11 representative spacecraft softwares are shown in Table 1 [14]. The ranks of 11 representative spacecrafts are obtained according to the software trustworthiness classification model, as shown in the Table 2 [14]. In this classification model, software trustworthiness is divided into five ranks. Rank V is the highest level, which requires that the trustworthy degree of software is at least , and the trustworthy attribute value is at least . Rank I is the lowest level, which requires that the trustworthy degree of software is at least , the trustworthy attribute value is at least .

Table 1.
Trustworthy attribute values, trustworthy degrees and trustworthy ranks of 11 representative spacecraft softwares.

Table 2.
Software trustworthiness classification model.
We have implemented our reallocation algorithm on a PC with Intel(R) Core (TM) i7-6500 CPU @ 2.50 GHz 2.59 GHz and 8 GB of main memory running Windows 10 64-bit operating system. The IDE is PyCharm with Python 3.6.1. Assuming that the trustworthy rank of each of these 11 representative softwares needs to be improved by one level, in the following we will show how to use Algorithm 1 to reallocate their trustworthiness according to the classification model given in Table 2.
The process of trustworthiness reallocation of software no. 4 from rank II to rank III is as follows. Because , then let . Substituting into the trustworthy attribute value growth function , we can get the following reallocation result
The change of each attribute value caused by trustworthiness reallocation of spacecraft software from rank II to rank III is shown in the Table 3.

Table 3.
Changes of trustworthy attribute values caused by trustworthiness reallocation of spacecraft software from rank II to rank III.
The following is the process of trustworthiness reallocation of software whose number is 7 from rank III to rank IV. First, initialize , , , and is obtained.
Because and , the first outermost loop of the outermost else part is executed, it follows that
Taking as the initial iterative value, as the maximum number of iterations and as the error, the approximate solution of is obtained by Newton iterative method, which exceeds the range of . Bringing into the trustworthy attribute value growth function , we can get
of which , update and let .
Since , the second outermost loop of the outermost else part is executed, it follows that
Taking as the initial iterative value, as the maximum number of iterations and as the error, the approximate solution of is obtained by Newton iterative method. Bringing into the trustworthy attribute value growth function to calculate the values of attributes whose subscripts are in , the values of attributes whose subscripts are in are obtained from the settings in the previous round of outermost loop of the outermost else part, then we have
All of the trustworthy attribute values are less than or equal to , the set is no longer updated, the outmost loop is jumped out of and the algorithm is stopped. The above trustworthy attribute values are the reallocation result.
Similarly, the trustworthiness of the rest of rank III softwares and rank IV softwares which need to be improved by one level can be reallocated to trustworthy attributes by Algorithm 1. The reallocation results are shown in Table 4 and Table 5.

Table 4.
Changes of trustworthy attribute values caused by trustworthiness reallocation of spacecraft softwares from rank III to rank IV.

Table 5.
Changes of trustworthy attribute values caused by trustworthiness reallocation of spacecraft softwares from rank IV to rank V.
The last rows of Table 3, Table 4 and Table 5 separately give the sum of the increases of all the trustworthy attribute values of 11 representative spacecraft softwares. Since we assume that the trustworthy attribute values are positively correlated with the software development costs, these rows reflect to some extent the research and development costs required to improve the software trustworthiness by one level. From Table 4, it can be found that the trustworthy degrees of all of software no. 2, no. 6, no.7, no. 9, no. 20, no. 21 and no. 22 after reallocation calculated by the model presented in the Definition 1 are , which is exactly the lowest trustworthy degrees required for rank IV. The reason is that all of their trustworthy degrees before reallocation satisfy and . It can be found from Table 5 that all of software no. 18, no. 19 and no.23 have similar results.
3. Discussion
We defined an allocation model for software trustworthiness based on the simplified model as shown in Definition 1 [27] and an allocation model for software attribute trustworthiness based on a model that used the same computational model as the simplified model [28]. The allocation model for software trustworthiness gives the procedure of determining the value of each attribute with the given trustworthy degree of a software. It requires a feasible solution that minimizes the sum of all the trustworthy attribute values when the software trustworthiness requirements are satisfied. We provide an attribute-based allocation algorithm to get the allocation results using Newton iterative method. The allocation model for software attribute trustworthiness describes the process of computing the value of each sub-attribute according to the given value of trustworthy attribute. It requires a solution that not only maximizes the value of the attribute but also minimizes the sum of all its sub-attribute values. We design a sub-attribute-based allocation algorithm to obtain the allocation results by solving a group of indefinite equations. The reallocation mode for software trustworthiness presents how to reallocate software trustworthiness to attributes with the improvement requirements of software trustworthiness satisfied. It requires a solution that minimizes the sum of the increases of all the trustworthy attribute values. We also give an attribute-based reallocation algorithm to get the reallocation results with the help of Newton iterative method. Compared with the allocation models, the reallocation model has different objective functions and more constraints. The reallocation model needs to ensure that each software attribute value after reallocation is not less than the corresponding software attribute value before reallocation. The software trustworthiness allocation method and software attribute trustworthiness allocation method given by us can not guarantee this, so neither of them can be used for software trustworthiness reallocation.
4. Conclusions and Future Work
In this paper, we have established a mathematical programming model to reallocate the trustworthy degree of software to its attribute appropriately. In order to solve this mathematical programming, a trustworthy attribute value growth function is given. A polynomial time algorithm is designed to compute the optimal solution of this mathematical programming based on the trustworthy attribute value growth function. In addition, this algorithm is implemented and its effectiveness is validated by applying it to reallocate the trustworthiness of 11 spacecraft softwares which need to be improved by one level. We also highlight how the time line of our research has evolved from the findings of our previous study and explain their differences. The results obtained here are useful to minimize the costs of software trustworthiness improvement.
There are several problems that are worthy of further study. First, for the sake of simplicity, we assume that all attributes have the same trustworthy growth rate in the trustworthy attribute value growth function. If their trustworthy growth rates are not the same, the question of how to solve the corresponding reallocation model is important. Furthermore, in this paper, it is assumed that the trustworthy attribute value growth function is a linear function. If it is another type of function, how should the corresponding reallocation model be solved? Third, we will extend the reallocation approach given in this paper to reallocate software trustworthiness based on other software trustworthiness measurement models, and study the reallocation approach for software attribute trustworthiness on the basis of the reallocation approach proposed here. We will also research how to select the trustworthy attributes by implementing a learning approach based on reinforcement learning method. Finally, we will study the quantitative relationship between trustworthy attribute values and the costs of R & D to further evaluate the economic benefits of our approach.
Author Contributions
Conceptualization, H.T. and Y.C.; methodology, H.T. and Y.C.; algorithm, H.T., Y.C. and H.W.; software, H.T.; writing—original draft preparation, H.T.; writing—review and editing, H.W.; funding acquisition, H.T. All authors have read and agreed to the published version of the manuscript.
Funding
This work was financially supported by the National Natural Science Foundation of China (91118007), Doctoral Research Fund of Zhengzhou University of Light Industry (2016BSJJ037) and Science and Technology Project of Henan Province (182102210617).
Conflicts of Interest
The authors declare no conflict of interest.
References
- He, J.F.; Shan, Z.G.; Wang, J.; Pu, G.G.; Fang, Y.F.; Liu, K.; Zhao, R.Z.; Zhang, Z.T. Review of the Achievements of Major Research Plan of Trustworthy Software. Bull. Natl. Nat. Sci. Found. China 2018, 32, 291–296. [Google Scholar] [CrossRef]
- Fenton, N.; Littlewood, B.; Neil, M.; Strigini, L.; Sutclife, A.; Wright, D. Assessing Dependability of Safety Critical Systems Using Diverse Evidence. IEEE Proc. Softw. 1998, 145, 35–39. [Google Scholar] [CrossRef]
- Steffen, B.; Wilhelm, H.; Alexandra, P.; Marko, B.; Heiko, K.; Jan, P.; Abhishek, D.; Henrik, L.; Matthias, R.; Daniel, W.; et al. Trustworthy Software Systems: A Discussion of Basic Concepts and Terminology. ACM SIGSOFT Softw. Eng. Notes 2006, 31, 1–18. [Google Scholar] [CrossRef]
- Hasselbring, W.; Reussner, R. Toward Trustworthy Software Systems. IEEE Trans. Comput. 2006, 39, 91–92. [Google Scholar] [CrossRef]
- Bianco, V.D.; Lavazza, L.; Morasca, S.; Taibi, D. A Survey On Open Source Sofware Trustworthiness. IEEE Sofw. 2011, 28, 67–75. [Google Scholar] [CrossRef]
- Tao, H.W.; Chen, Y.X. A Survey of Software Trustworthiness Measurement Validation. Int. J. Perform. Eng. 2018, 14, 2056–2065. [Google Scholar] [CrossRef]
- Tao, H.W.; Chen, Y.X.; Wu, H.Y.; Deng, R.M. A Survey of Software Trustworthiness Measurements. Int. J. Perform. Eng. 2019, 15, 2364–2372. [Google Scholar] [CrossRef]
- Tao, H.W.; Chen, Y.X. A Metric Model For Trustworthiness of Softwares. In Proceedings of the 2009 IEEE/WIC/ACM International Joint Conference on Web Intelligence and Intelligent Agent Technology, Milan, Italy, 15–18 September 2009; pp. 69–72. [Google Scholar] [CrossRef]
- Tao, H.W.; Chen, Y.X. A New Metric Model for Trustworthiness of Softwares. Telecommun. Syst. 2012, 51, 95–105. [Google Scholar] [CrossRef]
- Zhang, L.W.; Chen, Y.X.; Zhou, Y.; Zhang, M.; Zhang, J.Y. Stability of Software Trustworthiness Measurements Models. In Proceedings of the IEEE 7th International Conference on Software Security and Reliability Companion, Gaithersburg, MD, USA, 18–20 June 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Tao, H.W.; Chen, Y.X.; Pang, J.M. Axiomatic Approaches Based Software Trustworthiness Measures. In Proceedings of the International Conference on Applied System Innovation (ICASI 2015), Osaka, Japan, 22–26 May 2015; pp. 135–142. [Google Scholar] [CrossRef]
- Tao, H.W.; Zhou, J. An Improved Attribute-Based Software Trustworthiness Metric Model. J. Wuhan Univ. (Nat. Sci. Ed.) 2017, 63, 151–157. [Google Scholar] [CrossRef]
- Tao, H.W.; Chen, Y.X. A Software Trustworthiness Measure Based on the Decompositions of Trustworthy Attributes and its Validation. In Proceedings of the Industrial Engineering, Management Science and Applications 2015, Tokyo, Japan, 26–28 May 2015; pp. 981–990. [Google Scholar] [CrossRef]
- Wang, J.; Chen, Y.X.; Gu, B.; Guo, X.Y.; Wang, B.H.; Jin, S.Y.; Xu, J.; Zhang, J.Y. An Approach to Measuring and Grading Software Trust for Spacecraft Software. Sci. Sin. Technol. 2015, 45, 221–228. [Google Scholar] [CrossRef]
- Ding, S.; Yang, S.L.; Fu, C. A Novel Evidential Reasoning Based Method for Software Trustworthiness Evaluation Under the Uncertain and Unreliable Environment. Exp. Syst. Appl. 2012, 39, 2700–2709. [Google Scholar] [CrossRef]
- Hauke, S.; Biedermann, S.; Muhlhauser, M.; Heider, D. On the Application of Supervised Machine Learning to Trustworthiness Assessment. In Proceedings of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, VIC, Australia, 16–18 July 2013; pp. 525–534. [Google Scholar] [CrossRef]
- Muhammad, D.M.S.; Fairul, R.F.; Loo, F.A.; Nur, F.A.; Norzamzarini, B. Rating of Software Trustworthiness Via Scoring of System Testing Results. Int. J. Dig. Enterp. Technol. 2018, 1, 121–134. [Google Scholar] [CrossRef]
- Yang, X.; Jabeen, G.; Luo, P.; Zhu, X.L.; Liu, M.H. A Unified Measurement Solution of Software Trustworthiness Based on Social-to-Software Framework. J. Comput. Sci. Technol. 2018, 33, 603–620. [Google Scholar] [CrossRef]
- Wang, H.M. Harnessing the Crowd Wisdom for Software Trustworthiness: Practices in China. ACM SIGSOFT Softw. Eng. Notes 2018, 43, 6–11. [Google Scholar] [CrossRef]
- Cho, J.H.; Xu, S.H.; Hurley, P.M.; Mackay, M.; Benjamin, T.; Beaumont, M. STRAM: Measuring the Trustworthiness of Computer-Based Systems. ACM Comput. Surv. 2019, 51, 1–47. [Google Scholar] [CrossRef]
- Davide, T. Towards a Trustworthiness Model for Open Source Software. Ph.D. Thesis, University of Insubria, Lombardy, ON, Canada, 2010. [Google Scholar]
- Vieri, D.B.; Luigi, L.; Sandro, M.; Davide, T. Quality of Open Source Software: The Qualipso Trustworthiness Model. In Proceedings of the 5th IFIP WG 2.13 International Conference on Open Source Systems (OSS 2009), Skövde, Sweden, 3–6 June 2009; pp. 199–212. [Google Scholar] [CrossRef]
- Han, Q. Trustworthiness Measurement Algorithm for TWfMS Based on Software Behaviour Entropy. Entropy 2018, 20, 195. [Google Scholar] [CrossRef]
- Jiang, R. A Trustworthiness Evaluation Method for Software Architectures Based on the Principle of Maximum Entropy (POME) and the Grey Decision-Making Method (GDMM). Entropy 2014, 16, 4818–4838. [Google Scholar] [CrossRef]
- Gene, M.A.; Tyler, J.R. Trustworthiness Perceptions of Computer Code: A Heuristic-Systematic Processing Model. In Proceedings of the 51st Hawaii International Conference on System Sciences, Waikoloa Village, HI, USA, 3–6 January 2018; pp. 5384–5393. [Google Scholar] [CrossRef]
- Wang, B.H.; Chen, Y.X.; Zhang, S.; Wu, H.Y. Updating Model of Software Component Trustworthiness Based on Users Feedback. IEEE Acess 2019, 7, 60199–60205. [Google Scholar] [CrossRef]
- Ma, Y.J.; Chen, Y.X.; Gu, B. An Attributes-Based Allocation Approach of Software Trustworthy Degrees. In Proceedings of the 2015 IEEE International Conference on Software Quality, Reliability and Security Companion, Vancouver, BC, Canada, 3–5 August 2015; pp. 89–94. [Google Scholar] [CrossRef]
- Tao, H.W.; Wu, H.Y.; Chen, Y.X. An Approach of Trustworthy Measurement Allocation Based on Sub-Attributes of Software. Mathematics 2019, 7, 237. [Google Scholar] [CrossRef]
- International Organization for Standardization (ISO). ISO/IEC DIS 30754 Information Technology–Software Trustworthiness–Governance and Management–Specification; ISO: Geneva, Switzerland, 2016. [Google Scholar]
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).