A Novel Auction Blockchain System with Price Recommendation and Trusted Execution Environment
Abstract
:1. Introduction
2. Background and Related Work
2.1. Online Auctions
- First Price Sealed Bidding Auction (FPSBA): The buyer seals the bid in an envelope and delivers it to the auctioneer. Subsequently, the auctioneer opens the envelope to determine the winner with the highest bid.
- Second Price Sealed Bidding Auction (Vickrey auction): It is similar to FPSBA except that the winner will pay the second-highest bid.
- Open Ascending Auction (English auction): Bidders make increasingly higher bids and stop bidding if they are unwilling to pay higher than the current highest bid.
- Open Descending Auction (Dutch auction): The auctioneer initially sets a high price and then gradually reduces it until any buyer decides to pay at the current price.
2.2. Winner’s Curse
2.3. Price Recommendation and Prediction
2.4. Blockchain
- Decentralized: The most basic feature of a blockchain is that the data do not rely on a centralized node but can be recorded and stored in a decentralized fashion.
- Transparent: The data can be updated on any nodes in the blockchain system, which is the main contributor to the blockchain’s trustworthiness.
- Open source: Most of the blockchain systems are open to the public for inspection, verification, and usage to create other applications.
- Autonomous: Based on the consensus algorithm, all nodes in the blockchain system can safely transmit and update data without intervention.
- Unchangeable: All records will be stored forever and cannot be changed unless one party occupies at least 51% of the nodes at the same time.
- Anonymous: A blockchain resolves the problem of trust between nodes, so data can be transmitted and traded in an anonymous manner, with only the blockchain address being known to each other.
2.5. Ethereum
2.6. Blockchain-Based E-Auction
2.7. Trusted Execution Environment
3. System Framework
3.1. System Environment
3.2. Roles
- Buyer/Bidder: The role with the capability of bidding on items in an online auction.
- Bidder of Decision Support: The role with bidding capability and price recommendations suggested by the system. The price predictions are based on data collected from past auctions.
- Seller: The role of publishing product auctions and collecting payments with the capability of specifying item auction price, auction time, and other information in detail.
- Auction Manager: The role of verifying information of the auctioned products or identities of all the other participating roles.
3.3. Auction Scenario
- The seller sends the system a request to list the auctioned item.
- Upon receipt of the seller’s listing request, the auction manager verifies the product information and checks if there is any missing information.
- Each buyer can pay for the registration to access the price recommendations before the auction starts.
- Buyers who paid for the registration are converted to the role of “bidders of price suggestions.”
- Bidders of price suggestions can request a price recommendation.
- The price recommendation request is sent to SGX for secure processing.
- The price recommendation is calculated and returned to the bidder of price suggestions.
- The auction manager starts the auction.
- The system takes bids from all buyers.
- The auction manager verifies the auction time and bid counts during the auction. The auction is closed at the end of auction time or if there exists a winner.
- The auction manager verifies the winner’s information.
- The winning buyer submits the payment.
- The seller verifies the payment.
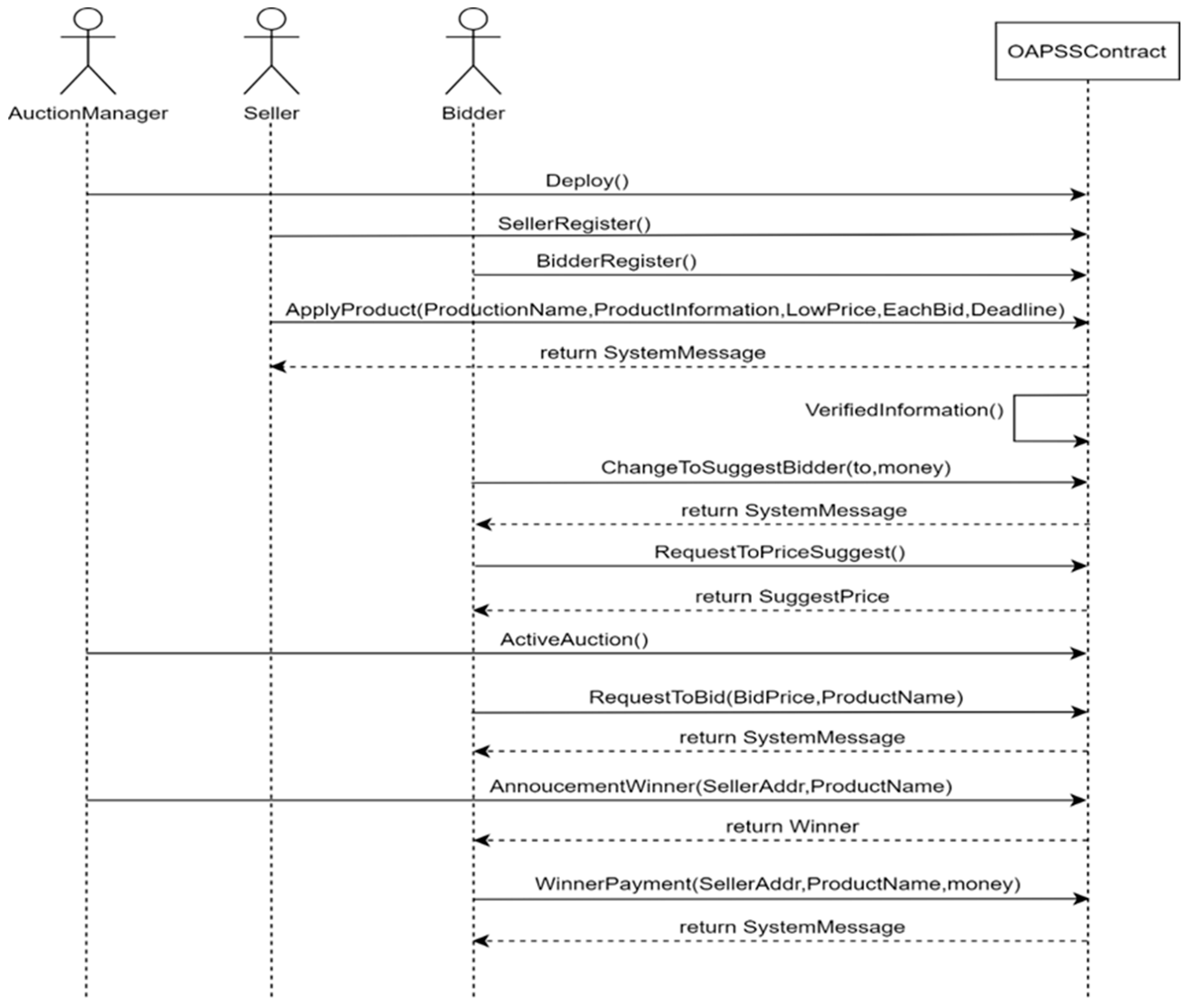
3.4. Ethereum Smart Contract
| Algorithm 1 ApplyProduct |
| Input: Ethereumaddress(EA) of SellerAddr |
| ProductName, AuctionLowPrice, AuctionStartTime, AuctionEndTime |
| 1. if SellerAddr = Seller Address then |
| 2. Add product information to ProductHashtable 3. Setting Auction Time 4. str = Identity verification success 5. else 6. str = Identity verification failed |
| 7. end |
| Algorithm 2 VerifiedProductInformation |
| Input: Ethereumaddress(EA) of AuctionManagerAddr |
| ProductName, AuctionLowPrice, AuctionTime |
| 1. if AuctionManagerAddr = AuctionManager Address then |
| 2. if Product Information <> null then 3. AuctionReadyState = true; 4. str = Product apply success 5. else 6. AuctionReadyState = false; 7. str = Product apply fail 8. else 9. str = Identity verification failed |
| 10. end |
| Algorithm 3 ChangeToSuggestionBidder |
| Input: Ethereumaddress(EA) of BidderAddr |
| Fee |
| 1. if BidderAddr = Bidder Address then 2. if Fee = true |
| 3. Add Bidder to SuggestionBidderArrayList 4. str = change to Suggestion Bidder is success 5. else 6. str = change to Suggestion Bidder is fail 7. end 8. else 9. str = Identity verification failed 10. end |
| Algorithm 4 RequestToPriceSuggest |
| Input: Ethereumaddress(EA) of BidderPriceSuggestionAddr |
| ProductName |
| 1. if BidderPriceSuggestionAddr = Bidder of price suggestion Address then 2. EnterSGXenclave |
| 3. collect product information 4. use α-Sutte indicator to predict price 5. return suggest price; 6. else 7. str = Identity verification failed 8. end |
| Algorithm 5 ActiveAuction |
| Input: Ethereumaddress(EA) of AuctionManagerAddr |
| ProductName, AuctionTime, AuctionReadyState |
| 1. if AuctionManagerAddr = AuctionManager Address then 2. if AuctionReadyState = true |
| 3. while AuctionActive = false 4. if AuctionStartime = now then 5. AuctionActive = true 6. str = Auction Start 7. else 8. AuctionActive = false 9. str = Auction time is not up yet 10. end 11. else 12. str = Auction not ready, please check product information 13. end 14. else 15. str = Identity verification failed |
| 16. end |
| Algorithm 6 RequestToBid |
| Input: Ethereumaddress(EA) of BidderAddr |
| ProductName, BidPrice, AuctionTime |
| 1. if BidderAddr = Bidder Address then 2. if BidPrice ≥ Base standard && BidPrice > CurrentHighestPrice then |
| 3. if now < AuctionEndTime then 4. CurrentHighestPrice = BidPrice 5. CurrentHighestBidder = Bidder 6. str = Bid success 7. else 8. str = Bid fail 9. end 10. else 11. str = Bid fail 12. end 13. else 14. str = Identity verification failed |
| 15.end |
| Algorithm 7 AnnoucementWinner |
| Input: Ethereumaddress(EA) of AuctionManagerAddr |
| 1. if AuctionManagerAddr = AuctionManager Address then 2. if now < AuctionEndTime then |
| 3. Get HighestBidder 4. Winner = HighestBidder 5. Add Winner to WinnerNoPayArrayList 6. Notify Winnerto payment 7. str = Auction End 8. else 9. str = Auction time is not up yet 10. end 11. else 12. str = Identity verification failed 13. end |
| Algorithm 8 WinnerPayment |
| Input: Ethereumaddress(EA) of BidderAddr |
| PaymentAmount |
| 1. if BidderAddr = WinnerNoPayArrayList then 2. if PaymentAmount = CurrentHighestPrice then |
| 3. transfer winner money to smart contract 4. str = wait to seller receive payment 5. else if PaymentAmount > CurrentHighestPrice then 6. return PaymentAmount - CurrentHighestPrice 7. str = wait to seller receive payment 8. else 9. str = Amount is enough 10. end 11. else 12. str = Identity verification failed 13. end |
4. Testing and Security Analysis
4.1. Deploy Results
4.1.1. Deploy Contracts
4.1.2. Winner Announcement
4.2. Experiment on Winner’s Curse
- Confirm the existence of the winner’s curse.
- Compare the difference between two scenarios, with and without the final transaction price prediction.
4.2.1. Framework and Methods
- Buyer: The buyers are divided into the experimental group (with price prediction) and the control group (without price prediction) for comparison before the auction stage. Detailed group descriptions are shown in Table 4.
- Auction Stage: Fifteen items of various types are introduced to each buyer group for the auctions. The auction procedure includes price recommendation, bidding, product acquisition, winner announcement, and final payment.
- Data Aggregation: The two sets of 15 final transaction prices and the highest bids obtained from both buyer groups are collected. There are three groups, which are with prediction price (PdP) help group, without prediction price (NPdP) help group, and past prices (PP). Each price in PP is the average of the past four final prices collected from eBay. Table 3 summarizes the data groups and their definitions.
- Data Analysis: We use analysis of variance (ANOVA) and Tukey’s post-analysis [24] to evaluate the differences between groups. The goal of this analysis is to verify our price predictions on the final transaction price and how it impacts the winner’s curse. The ANOVA analysis of this experiment is shown in Table 5 and Table 6.
4.2.2. Experimental Results
4.3. Cost Analysis
4.4. Security Analysis
- Reentrancy Vulnerability
- Replay Attack
- Access Restriction
- Timestamp Dependency
- Confidentiality
- Data Integrity
- Availability
- Authorization
- Non-repudiation
- Sybil Attack
- Double-Spend Attack
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Olaya, J.; Boehm, F. Corruption in Public Contracting Auctions: The Role of Transparency in Bidding Process. Ann. Public Coop. Econ. 2006, 77, 431–452. [Google Scholar]
- Amyx, D.A.; Luehlfing, M.S. Winner’s curse and parallel sales channels—Online auctions linked within e-tail websites. Inf. Manag. 2006, 43, 919–927. [Google Scholar] [CrossRef]
- Milgrom, P.R.; Weber, R.J. A Theory of Auctions and Competitive Bidding. Econometrica 1982, 50, 1089. [Google Scholar] [CrossRef]
- Klein, S.; O’Keefe, M. The Impact of the Web on Auctions: Some Empirical Evidence and Theoretical Considerations. Int. J. Electron. Commer. 1999, 3, 7–20. [Google Scholar] [CrossRef]
- Krishna, V. Auction Theory; Academic Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Capen, E.C.; Clapp, R.V.; Campbell, W.M. Competitive Bidding in High-Risk Situations. JPT J. Pet. Technol. 1971, 23, 641–653. [Google Scholar] [CrossRef]
- Bazerman, M.H.; Samuelson, W.F. I Won the auction but don’t want the prize. J. Confl. Resolut. 1983, 27, 618–634. [Google Scholar] [CrossRef] [Green Version]
- Goeree, J.; Offerman, T. Winner’s curse without overbidding. Eur. Econ. Rev. 2003, 47, 625–644. [Google Scholar] [CrossRef]
- Ahmar, A.S. A Comparison of α-Sutte Indicator and ARIMA methods in renewable energy forecasting in Indonesia. Int. J. Eng. Technol. 2018, 7, 20–22. [Google Scholar] [CrossRef] [Green Version]
- Ahmar, A.S. Sutte indicator: An approach to predict the direction of stock market movements. Songklanakarin J. Sci. Technol. 2018, 40, 1228–1231. [Google Scholar] [CrossRef]
- Bhowmik, M.; Chandana, T.S.S.; Rudra, B. Comparative Study of Machine Learning Algorithms for Fraud Detection in Blockchain. In Proceedings of the 2021 5th International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 8–10 April 2021; pp. 539–541. [Google Scholar]
- Cheema, M.A.; Ashraf, N.; Aftab, A.; Qureshi, H.K.; Kazim, M.; Azar, A.T. Machine Learning with Blockchain for Secure E-voting System. In Proceedings of the 2020 First International Conference of Smart Systems and Emerging Technologies (SMARTTECH), Riyadh, Saudi Arabia, 3–5 November 2020; pp. 177–182. [Google Scholar]
- Haber, S.; Stornetta, W.S. How to time-stamp a digital document. J. Cryptol. 1991, 3, 99–111. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Decentralized Bus. Rev. 2008, 21260. Available online: https://www.debr.io/article/21260.pdf (accessed on 1 December 2021).
- Lin, I.-C.; Liao, T.-C. A survey of blockchain security issues and challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Foti, M.; Vavalis, M. Blockchain based uniform price double auctions for energy markets. Appl. Energy 2019, 254, 113604. [Google Scholar] [CrossRef]
- Desai, H.; Kantarcioglu, M.; Kagal, L. A Hybrid blockchain architecture for privacy-enabled and accountable auctions. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 34–43. [Google Scholar]
- Wang, D.; Zhao, J.; Mu, C. Research on Blockchain-Based E-Bidding System. Appl. Sci. 2021, 11, 4011. [Google Scholar] [CrossRef]
- Jiao, Y.; Wang, P.; Niyato, D.; Suankaewmanee, K. Auction mechanisms in cloud/fog computing resource allocation for public blockchain networks. IEEE Trans. Parallel Distrib. Syst. 2019, 30, 1975–1989. [Google Scholar] [CrossRef] [Green Version]
- Braghin, C.; Cimato, S.; Damiani, E.; Baronchelli, M. Designing smart-contract based auctions. In International Conference on Security with Intelligent Computing and Big-Data Services; Springer: Cham, Switzerland, 2019; pp. 54–64. [Google Scholar]
- McKeen, F.; Alexandrovich, I.; Berenzon, A.; Rozas, C.V.; Shafi, H.; Shanbhogue, V.; Savagaonkar, U.R. Innovative instructions and software model for isolated execution. In Proceedings of the HASP’13: The Second Workshop on Hardware and Architectural Support for Security and Privacy, Tel-Aviv, Israel, 23–24 June 2013; p. 1. [Google Scholar] [CrossRef] [Green Version]
- Sun, J.; Huang, S.; Zheng, C.; Wang, T.; Zong, C.; Hui, Z. Mutation testing for integer overflow in ethereum smart contracts. Tsinghua Sci. Technol. 2022, 27, 27–40. [Google Scholar] [CrossRef]
- Magalhães, F.A.; Souza, T.R.; Araújo, V.L.; Oliveira, L.M.; de Paula Silveira, L.; de Melo Ocarino, J.; Fonseca, S.T. Comparison of the rigidity and forefoot—Rearfoot kinematics from three forefoot tracking marker clusters during walking and weight-bearing foot pronation-supination. J. Biomech. 2020, 98, 109381. [Google Scholar] [CrossRef]
- Harb, H.; Makhoul, A.; Couturier, R. An enhanced K-means and ANOVA-based clustering approach for similarity aggregation in underwater wireless sensor networks. IEEE Sens. J. 2015, 15, 5483–5493. [Google Scholar] [CrossRef] [Green Version]
- Luu, L.; Narayanan, V.; Zheng, C.; Baweja, K.; Gilbert, S.; Saxena, P. A Secure sharding protocol for open blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 17–30. [Google Scholar]
- Omar, I.A.; Jayaraman, R.; Debe, M.S.; Salah, K.; Yaqoob, I.; Omar, M. Automating procurement contracts in the healthcare supply chain using blockchain smart contracts. IEEE Access 2021, 9, 37397–37409. [Google Scholar] [CrossRef]
- Xiong, W.; Xiong, L. Data Trading Certification Based on Consortium Blockchain and Smart Contracts. IEEE Access 2021, 9, 3482–3496. [Google Scholar] [CrossRef]
- Karpinski, M.; Kovalchuk, L.; Kochan, R.; Oliynykov, R.; Rodinko, M.; Wieclaw, L. Blockchain Technologies: Probability of Double-Spend Attack on a Proof-of-Stake Consensus. Sensors 2021, 21, 6408. [Google Scholar] [CrossRef]
- Longo, R.; Podda, A.S.; Saia, R. Analysis of a Consensus Protocol for Extending Consistent Subchains on the Bitcoin Blockchain. Computation 2020, 8, 67. [Google Scholar] [CrossRef]
- Cui, Z.; Fei XU, E.; Zhang, S.; Cai, X.; Cao, Y.; Zhang, W.; Chen, J. A hybrid blockchain-based identity authentication scheme for multi-WSN. IEEE Trans. Serv. Comput. 2020, 13, 241–251. [Google Scholar] [CrossRef]
- Abu-Elezz, I.; Hassan, A.; Nazeemudeen, A.; Househ, M.; Abd-Alrazaq, A. The benefits and threats of blockchain technology in healthcare: A scoping review. Int. J. Med. Inform. 2020, 142, 104246. [Google Scholar] [CrossRef] [PubMed]
- Ahmar, A.S.; del Val, E.B. SutteARIMA: Short-term forecasting method, a case: Covid-19 and the stock market in Spain. Sci. Total Environ. 2020, 729, 138883. [Google Scholar] [CrossRef]




| Parameter | Value |
|---|---|
| OS | Windows 10 |
| CPU | 8-Core Intel(R) i7 |
| RAM | 32 GB |
| TEE | Intel SGX |
| Language | Solidity |
| IDE | Remix IDE |
| Function | Smart Contract Algorithm |
|---|---|
| Deploy the contract. | Deploy() |
| Register the seller. | SellerRegister() |
| Register the buyer. | BidderRegister() |
| List an auctioned item. | ApplyProduct() |
| Verify the auctioned item. | VerifiedProductInformation() |
| Register the buyer for a price suggestion. | ChangeToSuggestBidder() |
| The buyer requests a price suggestion. | RequestToPriceSuggest() |
| Start the auction. | ActiveAuction() |
| Bid on an item. | RequestToBid() |
| Announce the winner. | AnnoucementWinner() |
| The winner pays the seller. | Winner Payment() |
| Account | Address |
|---|---|
| B | 0xAb8483F64d9C6d1EcF9b849Ae677dD3315835cb2 |
| BP | 0x4B20993Bc481177ec7E8f571ceCaE8A9e22C02db |
| S | 0x78731D3Ca6b7E34aC0F824c42a7cC18A495cabaB |
| AM | 0x5B38Da6a701c568545dCfcB03FcB875f56beddC4 |
| Groups | Abbreviation | Definitions |
|---|---|---|
| Average of the past four final prices | PP (past price) | The past four final transaction prices for each of the 15 auctioned items from eBay |
| Experimental group | PdP (with prediction price help) | The final price and highest biddings with buyers using price recommendations for each of the 15 auctioned items |
| Control group | NPdP (without prediction price help) | The final price and highest biddings without price recommendations for each of the 15 auctioned items |
| N | Avg | Std | Min | Max | |
|---|---|---|---|---|---|
| PP | 15 | 4699.85 | 5165.55 | 634.25 | 21,301.5 |
| PdP | 15 | 6220.67 | 3942.58 | 1690 | 15,060 |
| NPdP | 15 | 6942 | 4867.39 | 1010 | 15,510 |
| N | Avg | Std | Min | Max | |
|---|---|---|---|---|---|
| PP | 15 | 4699.85 | 5165.56 | 634.25 | 21,301.5 |
| PdP | 15 | 7468 | 5266.40 | 1800 | 20,000 |
| NPdP | 15 | 10,434.67 | 5866.46 | 2700 | 20,000 |
| Sum of Squares | F | Sig. | |
|---|---|---|---|
| Comparison between the transaction prices | 39,302,208.67 | 0.894 | 0.417 |
| Comparison between highest bids | 246,759,438.67 | 4.167 | 0.022 * |
| (I) Group | (J) Group | Mean Difference (I–J) | Sig. |
|---|---|---|---|
| PP | PdP | −1520.82 | 0.650 |
| NPdP | −2242.15 | 0.398 | |
| PdP | PP | 1520.82 | 0.650 |
| NPdP | −721.33 | 0.907 | |
| NPdP | PP | 2242.15 | 0.398 |
| PdP | 721.33 | 0.907 |
| (I) Group | (J) Group | Mean Difference (I–J) | Sig. |
|---|---|---|---|
| PP | PdP | −2768.15 | 0.354 |
| NPdP | −5734.81 * | 0.017 * | |
| PdP | PP | 2768.15 | 0.354 |
| NPdP | −2966.67 | 0.304 | |
| NPdP | PP | 5734.82 * | 0.017 * |
| PdP | 2966.67 | 0.304 |
| Function Name | Transaction Cost | Execution Cost | USD |
|---|---|---|---|
| Deploy Contract | 2,982,237 | 2,220,393 | 4.61 |
| SellerRegister() | 63,787 | 42,515 | 0.10 |
| BidderRegister() | 45,034 | 23,762 | 0.07 |
| ApplyProduct() | 195,003 | 170,787 | 0.30 |
| VerifiedInformation() | 33,802 | 11,122 | 0.05 |
| ChangeToSuggestionBidder() | 99,075 | 76,203 | 0.15 |
| RequestToPriceSuggest() | 44,350 | 21,926 | 0.07 |
| ActiveAuction() | 33,078 | 40,654 | 0.05 |
| RequestToBid() | 102,525 | 79,909 | 0.16 |
| AnnoucementWinner() | 104,576 | 110,744 | 0.16 |
| WinnerPayment() | 38,580 | 14,556 | 0.06 |
| [27] | [28] | [31] | Our Study | |
|---|---|---|---|---|
| Confidentiality | ✓ | ✓ | ✓ | ✓ |
| Data integrity | ✓ | ✓ | - | ✓ |
| Availability | ✓ | - | ✓ | - |
| Authorization | ✓ | ✓ | ✓ | ✓ |
| Non-repudiation | ✓ | ✓ | ✓ | ✓ |
| Scalability | ✗ | ✓ | ✓ | ✗ |
| Sybil attack | ✗ | ✗ | ✓ | ✓ |
| Double-spend attack | ✓ | ✓ | ✓ | ✓ |
| Man in the middle attack | ✓ | ✗ | ✓ | ✓ |
| [17] | [18] | [21] | Our Study | |
|---|---|---|---|---|
| Environment setup | Ethereum | Hybrid blockchain architecture | Ethereum | Ethereum |
| Privacy protection | ✓ | ✓ | ✓ | ✓ |
| Decentralization | ✓ | ✓ | ✓ | ✓ |
| Scalability | ✓ | ✓ | ✗ | ✗ |
| Cost analysis | ✓ | ✓ | ✓ | ✓ |
| Final price recommendation | ✗ | ✗ | ✗ | ✓ |
| Trusted execution environment | ✗ | ✗ | ✗ | ✓ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shih, D.-H.; Wu, T.-W.; Shih, M.-H.; Tsai, W.-C.; Yen, D.C. A Novel Auction Blockchain System with Price Recommendation and Trusted Execution Environment. Mathematics 2021, 9, 3214. https://doi.org/10.3390/math9243214
Shih D-H, Wu T-W, Shih M-H, Tsai W-C, Yen DC. A Novel Auction Blockchain System with Price Recommendation and Trusted Execution Environment. Mathematics. 2021; 9(24):3214. https://doi.org/10.3390/math9243214
Chicago/Turabian StyleShih, Dong-Her, Ting-Wei Wu, Ming-Hung Shih, Wei-Cheng Tsai, and David C. Yen. 2021. "A Novel Auction Blockchain System with Price Recommendation and Trusted Execution Environment" Mathematics 9, no. 24: 3214. https://doi.org/10.3390/math9243214
APA StyleShih, D.-H., Wu, T.-W., Shih, M.-H., Tsai, W.-C., & Yen, D. C. (2021). A Novel Auction Blockchain System with Price Recommendation and Trusted Execution Environment. Mathematics, 9(24), 3214. https://doi.org/10.3390/math9243214







