Impact of Imbalanced Modulation on Security of Continuous-Variable Measurement-Device-Independent Quantum Key Distribution
Abstract
1. Introduction
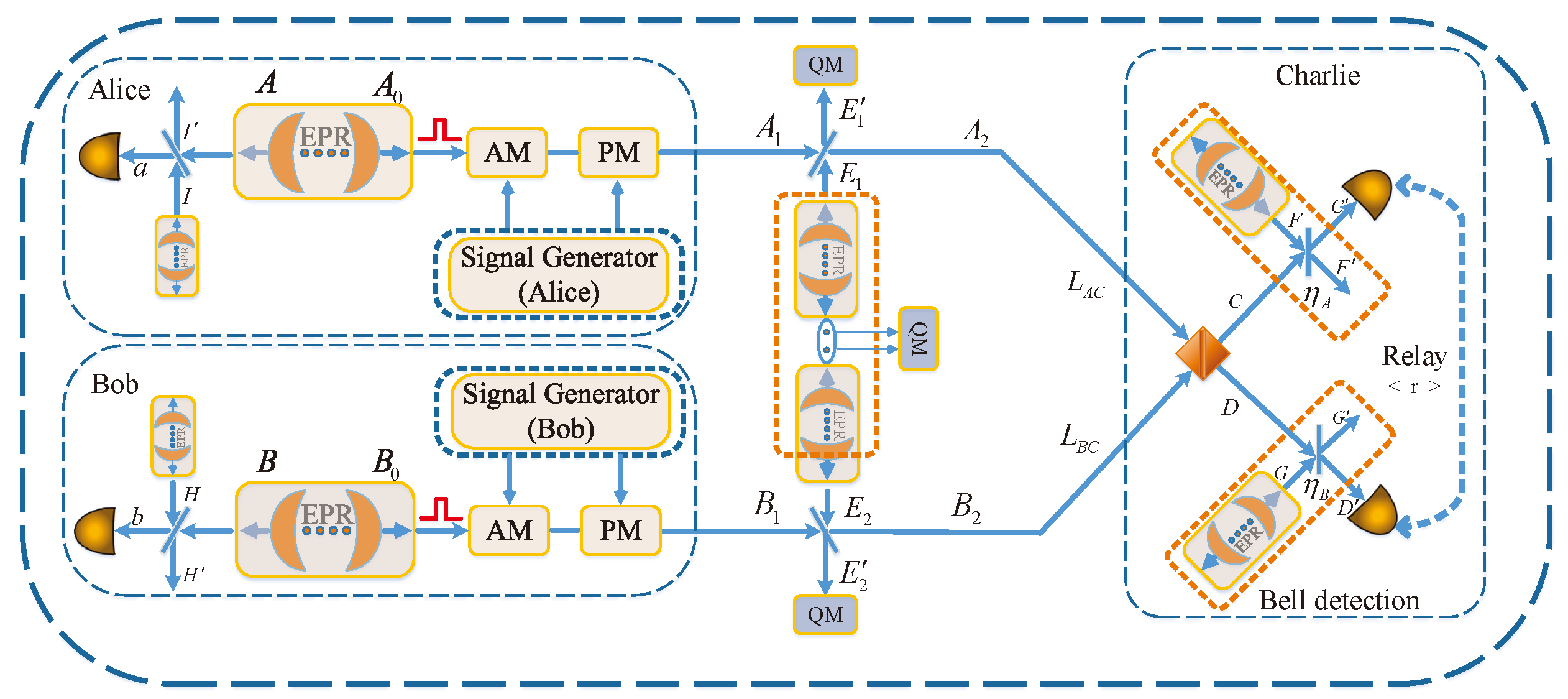
2. CV-MDI-QKD Protocol with Imbalanced Modulated Using Squeezed State and Coherent State
3. Imbalanced Modulation Influence on the Protocol under the Symmetric Distances
4. Imbalanced Modulation Influence on the Protocol under the Asymmetric Distances
5. Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145–195. [Google Scholar] [CrossRef]
- Scarani, V.; Bechmann-Pasquinucci, H.; Cerf, N.J.; Dušek, M.; Lütkenhaus, N.; Peev, M. The security of practical quantum key distribution. Rev. Mod. Phys. 2009, 81, 1301–1350. [Google Scholar] [CrossRef]
- Weedbrook, C.; Pirandola, S.; García-Patrón, R.; Cerf, N.J.; Ralph, T.C.; Shapiro, J.H.; Lloyd, S. Gaussian quantum information. Rev. Mod. Phys. 2012, 84, 621–669. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Tamaki, K. Secure quantum key distribution. Nat. Photon. 2014, 8, 595–604. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photon. 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Xu, F.H.; Ma, X.F.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Grosshans, F.; Van Assche, G.; Wenger, J.; Brouri, R.; Cerf, N.J.; Grangier, P. Quantum key distribution using gaussian-modulated coherent states. Nature 2003, 421, 238–241. [Google Scholar] [CrossRef]
- Lance, A.M.; Symul, T.; Sharma, V.; Weedbrook, C.; Ralph, T.C.; Lam, P.K. No-switching quantum key distribution using broadband modulated coherent light. Phys. Rev. Lett. 2005, 95, 180503. [Google Scholar] [CrossRef] [PubMed]
- Qi, B.; Huang, L.L.; Qian, L.; Lo, H.K. Experimental study on the Gaussian-modulated coherent-state quantum key distribution over standard telecommunication fibers. Phys. Rev. A 2007, 76, 052323. [Google Scholar] [CrossRef]
- Lodewyck, J.; Bloch, M.; García-Patrón, R.; Fossier, S.; Karpov, E.; Diamanti, E.; Debuisschert, T.; Cerf, N.J.; McLaughlin, S.W.; Grangier, P.; et al. Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phys. Rev. A 2007, 76, 042305. [Google Scholar] [CrossRef]
- Qi, B.; Zhu, W.; Qian, L.; Lo, H.K. Feasibility of quantum key distribution through a dense wavelength division multiplexing network. New J. Phys. 2010, 12, 103024. [Google Scholar] [CrossRef]
- Madsen, L.S.; Usenko, V.C.; Lassen, M.; Filip, R.; Andersen, U.L. Continuous variable quantum key distribution with modulated entangled states. Nat. Commun. 2012, 3, 1083. [Google Scholar] [CrossRef]
- Jouguet, P.; Kunz-Jacques, S.; Leverrier, A.; Grangier, P.; Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photon. 2013, 7, 378–381. [Google Scholar] [CrossRef]
- Kumar, R.; Hao, Q.; Alléaume, R. Coexistence of continuous variable QKD with intense DWDM classical channels. New J. Phys. 2015, 17, 043027. [Google Scholar] [CrossRef]
- Pirandola, S.; Ottaviani, C.; Spedalieri, G.; Weedbrook, C.; Braunstein, S.L.; Lloyd, S.; Gehring, T.; Jacobsen, C.S.; Andersen, U.L. High-rate measurement-device-independent quantum cryptography. Nat. Photon. 2015, 9, 397–403. [Google Scholar] [CrossRef]
- Walk, N.; Hosseini, S.; Geng, J.; Thearle, O.; Haw, J.Y.; Armstrong, S.J.; Assad, S.M.; Janousek, J.; Ralph, T.C.; Symul, T.; et al. Experimental demonstration of Gaussian protocols for one-sided device-independent quantum key distribution. Optica 2016, 3, 634–642. [Google Scholar] [CrossRef]
- Li, Y.M.; Wang, X.Y.; Bai, Z.L.; Liu, W.Y.; Yang, S.S.; Peng, K.C. Continuous variable quantum key distribution. Chin. Phys. B 2017, 26, 040303. [Google Scholar] [CrossRef]
- Liu, W.Y.; Wang, X.Y.; Wang, N.; Du, S.N.; Li, Y.M. Imperfect state preparation in continuous-variable quantum key distribution. Phys. Rev. A 2017, 96, 042312. [Google Scholar] [CrossRef]
- Liu, W.Y.; Cao, Y.X.; Wang, X.Y.; Li, Y.M. Continuous-variable quantum key distribution under strong channel polarization disturbance. Phys. Rev. A 2020, 102, 032625. [Google Scholar] [CrossRef]
- Tian, Y.; Wang, P.; Liu, J.Q.; Du, S.; Liu, W.Y.; Lu, Z.G.; Wang, X.Y.; Li, Y.M. Experimental demonstration of continuous-variable measurement-device-independent quantum key distribution over optical fiber. Optica 2022, 9, 492–500. [Google Scholar] [CrossRef]
- Karinou, F.; Brunner, H.H.; Fung, C.H.F.; Comandar, L.C.; Bettelli, S.; Hillerkuss, D.; Kuschnerov, M.; Mikroulis, S.; Wang, D.; Xie, C.S.; et al. Toward the Integration of CV Quantum Key Distribution in Deployed Optical Networks. IEEE Photon. Tech. Lett. 2018, 30, 650–653. [Google Scholar] [CrossRef]
- Huang, D.; Lin, D.K.; Wang, C.; Liu, W.Q.; Fang, S.H.; Peng, J.Y.; Huang, P.; Zeng, G.H. Continuous-variable quantum key distribution with 1 Mbps secure key rate. Opt. Express 2015, 23, 17511–17519. [Google Scholar] [CrossRef]
- Kleis, S.; Steinmayer, J.; Derksen, R.H.; Schaeffer, C.G. Experimental investigation of heterodyne quantum key distribution in the S-band or L-band embedded in a commercial C-band DWDM system. Opt. Express 2019, 27, 16540–16549. [Google Scholar] [CrossRef]
- Eriksson, T.A.; Hirano, T.; Puttnam, B.J.; Rademacher, G.; Luis, R.S.; Fujiwara, M.; Namiki, R.; Awaji, Y.; Takeoka, M.; Wada, N.; et al. Wavelength division multiplexing of continuous variable quantum key distribution and 18.3 Tbit/s data channels. Commun. Phys. 2019, 2, 9. [Google Scholar] [CrossRef]
- Jouguet, P.; Kunz-Jacques, S.; Diamanti, E.; Leverrier, A. Analysis of imperfections in practical continuous-variable quantum key distribution. Phys. Rev. A 2012, 86, 032309. [Google Scholar] [CrossRef]
- Huang, D.; Huang, P.; Li, H.S.; Wang, T.; Zhou, Y.M.; Zeng, G.H. Field demonstration of a continuous-variable quantum key distribution network. Opt. Lett. 2016, 41, 3511–3514. [Google Scholar] [CrossRef]
- Zhang, Y.C.; Li, Z.Y.; Chen, Z.Y.; Weedbrook, C.; Zhao, Y.J.; Wang, X.Y.; Huang, Y.D.; Xu, C.C.; Zhang, X.X.; Wang, Z.Y.; et al. Continuous-variable QKD over 50 km commercial fiber. Quantum Sci. Technol. 2019, 4, 035006. [Google Scholar] [CrossRef]
- Sun, S.H.; Xu, F.H. Security of quantum key distribution with source and detection imperfections. New J. Phys. 2021, 23, 023011. [Google Scholar] [CrossRef]
- Jain, N.; Chin, H.M.; Mani, H.; Lupo, C.; Nikolic, D.S.; Kordts, A.; Pirandola, S.; Pedersen, T.B.; Kolb, M.; Ömer, B.; et al. Practical continuous-variable quantum key distribution with composable security. Nat. Commun. 2022, 13, 4740. [Google Scholar] [CrossRef]
- García-Patrón, R.; Cerf, N.J. Unconditional optimality of Gaussian attacks against continuous-variable QKD. Phys. Rev. Lett. 2006, 97, 190503. [Google Scholar] [CrossRef]
- Navascués, M.; Grosshans, F.; Acín, A. Optimality of Gaussian attacks in continuous-variable quantum cryptography. Phys. Rev. Lett. 2006, 97, 190502. [Google Scholar] [CrossRef]
- Wolf, M.M.; Giedke, G.; Cirac, J.I. Extremality of Gaussian quantum states. Phys. Rev. Lett. 2006, 96, 080502. [Google Scholar] [CrossRef]
- Renner, R.; Cirac, J.I. de Finetti representation theorem for infinite-dimensional quantum systems and applications to quantum cryptography. Phys. Rev. Lett. 2009, 102, 110504. [Google Scholar] [CrossRef]
- Leverrier, A.; Grosshans, F.; Grangier, P. Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 2010, 81, 062343. [Google Scholar] [CrossRef]
- Leverrier, A. Composable security proof for continuous-variable quantum key distribution with coherent states. Phys. Rev. Lett. 2015, 114, 070501. [Google Scholar] [CrossRef]
- Diamanti, E.; Lo, H.K.; Qi, B.; Yuan, Z.L. Practical challenges in quantum key distribution. NPJ Quantum Inf. 2016, 2, 16025. [Google Scholar] [CrossRef]
- Braunstein, S.L.; Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 2012, 108, 130502. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Wang, Q.; Wang, X.B. Efficient implementation of the decoy-state measurement-device-independent quantum key distribution with heralded single-photon sources. Phys. Rev. A 2013, 88, 052332. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, T.Y.; Wang, L.J.; Liang, H.; Shentu, G.L.; Wang, J.; Cui, K.; Yin, H.L.; Liu, N.L.; Li, L.; et al. Experimental Measurement-Device-Independent Quantum Key Distribution. Phys. Rev. Lett. 2013, 111, 130502. [Google Scholar] [CrossRef]
- Hu, X.L.; Cao, Y.; Yu, Z.W.; Wang, X.B. Measurement-device-independent quantum key distribution over asymmetric channel and unstable channel. Sci. Rep. 2018, 8, 17634. [Google Scholar] [CrossRef] [PubMed]
- Liu, H.; Wang, W.Y.; Wei, K.J.; Fang, X.T.; Li, L.; Liu, N.L.; Liang, H.; Zhang, S.J.; Zhang, W.J.; Li, H.; et al. Experimental demonstration of high-rate measurement-device-independent quantum key distribution over asymmetric channels. Phys. Rev. Lett. 2019, 122, 160501. [Google Scholar] [CrossRef]
- Li, Z.Y.; Zhang, Y.C.; Xu, F.H.; Peng, X.; Guo, H. Continuous-variable measurement-device-independent quantum key distribution. Phys. Rev. A 2014, 89, 052301. [Google Scholar] [CrossRef]
- Ma, X.C.; Sun, S.H.; Jiang, M.S.; Gui, M.; Liang, L.M. Gaussian-modulated coherent-state measurement-device-independent quantum key distribution. Phys. Rev. A 2014, 89, 042335. [Google Scholar] [CrossRef]
- Wang, P.; Wang, X.Y.; Li, Y.M. Continuous-variable measurement-device-independent quantum key distribution using modulated squeezed states and optical amplifiers. Phys. Rev. A 2019, 99, 042309. [Google Scholar] [CrossRef]
- Zheng, Y.; Shi, H.B.; Pan, W.; Wang, Q.T.; Mao, J.H. Security Analysis of Continuous-Variable Measurement-Device-Independent Quantum Key Distribution Systems in Complex Communication Environments. Entropy 2022, 24, 127. [Google Scholar] [CrossRef]
- Song, T.T.; Wen, Q.Y.; Guo, F.Z.; Tan, X.Q. Finite-key analysis for measurement-device-independent quantum key distribution. Phys. Rev. A 2012, 86, 022332. [Google Scholar] [CrossRef]
- Curty, M.; Xu, F.H.; Gui, W.; Lim, C.C.W.; Tamaki, K.; Lo, H.K. Finite-key analysis for measurement-device-independent quantum key distribution. Nat. Commun. 2014, 5, 3732. [Google Scholar] [CrossRef] [PubMed]
- Papanastasiou, P.; Ottaviani, C.; Pirandola, S. Finite-size analysis of measurement-device-independent quantum cryptography with continuous variables. Phys. Rev. A 2017, 96, 042332. [Google Scholar] [CrossRef]
- Ma, X.F.; Fung, C.H.F.; Razavi, M. Statistical fluctuation analysis for measurement-device-independent quantum key distribution. Phys. Rev. A 2012, 86, 052305. [Google Scholar] [CrossRef]
- Yu, Z.W.; Zhou, Y.H.; Wang, X.B. Statistical fluctuation analysis for measurement-device-independent quantum key distribution with three-intensity decoy-state method. Phys. Rev. A 2015, 91, 032318. [Google Scholar] [CrossRef]
- Wang, C.; Yin, Z.Q.; Wang, S.; Chen, W.; Guo, G.C.; Han, Z.F. Measurement-device-independent quantum key distribution robust against environmental disturbances. Optica 2017, 4, 1016–1023. [Google Scholar] [CrossRef]
- Zang, Y.C.; Li, Z.Y.; Yu, S.; Gu, W.Y.; Peng, X.; Guo, H. Continuous-variable measurement-device-independent quantum key distribution using squeezed states. Phys. Rev. A 2014, 90, 052325. [Google Scholar] [CrossRef]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2009, 42, 114014. [Google Scholar] [CrossRef]
- Fossier, S.; Diamanti, E.; Debuisschert, T. Improvement of continuous-variable quantum key distribution systems by using optical preamplifiers. J. Phys. B At. Mol. Opt. 2009, 42, 114014. [Google Scholar] [CrossRef]






Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, W.; Liu, Z.; Bai, J.; Jie, Q.; Zhang, G.; Tian, Y.; Jin, J. Impact of Imbalanced Modulation on Security of Continuous-Variable Measurement-Device-Independent Quantum Key Distribution. Photonics 2024, 11, 649. https://doi.org/10.3390/photonics11070649
Liu W, Liu Z, Bai J, Jie Q, Zhang G, Tian Y, Jin J. Impact of Imbalanced Modulation on Security of Continuous-Variable Measurement-Device-Independent Quantum Key Distribution. Photonics. 2024; 11(7):649. https://doi.org/10.3390/photonics11070649
Chicago/Turabian StyleLiu, Wenyuan, Zehui Liu, Jiandong Bai, Qi Jie, Guangwei Zhang, Yan Tian, and Jingjing Jin. 2024. "Impact of Imbalanced Modulation on Security of Continuous-Variable Measurement-Device-Independent Quantum Key Distribution" Photonics 11, no. 7: 649. https://doi.org/10.3390/photonics11070649
APA StyleLiu, W., Liu, Z., Bai, J., Jie, Q., Zhang, G., Tian, Y., & Jin, J. (2024). Impact of Imbalanced Modulation on Security of Continuous-Variable Measurement-Device-Independent Quantum Key Distribution. Photonics, 11(7), 649. https://doi.org/10.3390/photonics11070649




