Integration of Privacy Protection and Blockchain-Based Food Safety Traceability: Potential and Challenges
Abstract
:1. Introduction
- Key data flows in the food traceability chain and the technical support covered.
- A comprehensive review of security issues in food traceability integration technologies and solutions to meet the requirements of food traceability at each step.
- Discusses how PP technologies can be integrated into the full food traceability process to meet all needs, presenting challenges and opportunities for solutions.
2. Background of Food Safety
2.1. Food Data Tracing
2.2. Technologies in Food Traceability
2.2.1. Internet of Things
2.2.2. Artificial Intelligence
2.2.3. Privacy Protection
3. Literature Review and Discussion
3.1. IoT Information Gathering
Identification
3.2. Traceability with Safety
3.3. Food Safety Management
3.3.1. Food Products Trust
3.3.2. Food Information Publication
3.4. Traceability System Management
3.5. Decision Support
4. Challenges
4.1. Gaps in Development
4.2. Technical Challenges
4.3. Sustainability and Transparency
4.4. Governance and Regulation
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Omarov, R.; Agarkov, A.; Rastovarov, E.; Shlykov, S. Modern methods for food safety. Eng. Rural Dev. Proc. 2017, 960–963. [Google Scholar] [CrossRef]
- Botcha, K.M.; Chakravarthy, V.V.; Anurag. Enhancing traceability in pharmaceutical supply chain using Internet of Things (IoT) and blockchain. In Proceedings of the 2019 IEEE International Conference on Intelligent Systems and Green Technology (ICISGT), Visakhapatnam, India, 29–30 June 2019; pp. 45–453. [Google Scholar]
- Nordhagen, S. Food safety perspectives and practices of consumers and vendors in Nigeria: A review. Food Control 2022, 134, 108693. [Google Scholar] [CrossRef]
- Gunders, D.; Bloom, J. Wasted: How America Is Losing up to 40 Percent of Its Food from Farm to Fork to Landfill. NRDC Issue Paper 2017, 1–26. [Google Scholar]
- Moldovan, M.-G.; Dabija, D.-C.; Pocol, C.B. Resources Management for a Resilient World: A Literature Review of Eastern European Countries with Focus on Household Behaviour and Trends Related to Food Waste. Sustainability 2022, 14, 7123. [Google Scholar] [CrossRef]
- Liu, C.; Jiang, H.; Badulescu, D.; Bac, D.P. Achieving Zero Hunger Goal through Minimizing Waste in Food Supply Chain: Evidence from Asian Emerging Region. Sustainability 2022, 14, 5930. [Google Scholar] [CrossRef]
- Liu, W.; Wei, S.; Wang, S.; Lim, M.K.; Wang, Y. Problem identification model of agricultural precision management based on smart supply chains: An exploratory study from China. J. Clean. Prod. 2022, 352, 131622. [Google Scholar] [CrossRef]
- Biegańska, M. Intelligent packaging as a tool in supply chain traceability in the food sector. In Current Trends in Quality Science–Consumer Behavior, Logistic, Product Management; Instytut Technologii Eksploatacji: Radom, Poland, 2022; pp. 226–236. Available online: https://ue.poznan.pl/pl/uniwersytet,c13/instytut-nauk-o-jakosci,c13079/konferencje,c14716/icqmsc-2021,c14717/monographs-current-trends-in-quality-sciences-2021,a105563.html (accessed on 22 July 2022).
- Fan, Y.; Lin, X.; Liang, W.; Wang, J.; Tan, G.; Lei, X.; Jing, L. TraceChain: A blockchain-based scheme to protect data confidentiality and traceability. Softw. Pract. Exp. 2022, 52, 115–129. [Google Scholar] [CrossRef]
- Marsden, T.; Banks, J.; Bristow, G. Food supply chain approaches: Exploring their role in rural development. Sociol. Rural 2000, 40, 424–438. [Google Scholar] [CrossRef]
- Chen, W.; Chen, C.-L.; Cao, Q.; Chiu, C.-H. Time course and epidemiological features of COVID-19 resurgence due to cold-chain food or packaging contamination. Biomed. J. 2022; in press. [Google Scholar] [CrossRef]
- Peng, X.; Zhang, X.; Wang, X.; Li, H.; Xu, J.; Zhao, Z. Multi-Chain Collaboration-Based Information Management and Control for the Rice Supply Chain. Agriculture 2022, 12, 689. [Google Scholar] [CrossRef]
- Liu, S.; Mu, T.; Xu, S.; He, G. Research on cross-chain method based on distributed Digital Identity. In Proceedings of the 2022 4th International Conference on Blockchain Technology, New York, NY, USA, 25–27 March 2022; pp. 59–73. [Google Scholar]
- Wu, X.; Li, Y.; Li, J.; Sun, Y. Research on the traceability coding of grain and oil products based on the EAN-UCC coding system. In Proceedings of the 2022 IEEE 2nd International Conference on Power, Electronics and Computer Applications (ICPECA), Shenyang, China, 21–23 January 2022. [Google Scholar]
- Prashar, D.; Jha, N.; Jha, S.; Lee, Y.; Joshi, G.P. Blockchain-based traceability and visibility for agricultural products: A decentralized way of ensuring food safety in india. Sustainability 2020, 12, 3497. [Google Scholar] [CrossRef] [Green Version]
- Yu, Z.; Jung, D.; Park, S.; Hu, Y.; Huang, K.; Rasco, B.A.; Wang, S.; Ronholm, J.; Lu, X.; Chen, J. Smart traceability for food safety. Crit. Rev. Food Sci. Nutr. 2022, 62, 905–916. [Google Scholar] [CrossRef]
- Qian, J.; Dai, B.; Wang, B.; Zha, Y.; Song, Q. Traceability in food processing: Problems, methods, and performance evaluations—A review. Crit. Rev. Food Sci. Nutr. 2022, 62, 679–692. [Google Scholar] [CrossRef]
- Manning, L.; Brewer, S.; Craigon, P.J.; Frey, J.; Gutierrez, A.; Jacobs, N.; Kanza, S.; Munday, S.; Sacks, J.; Pearson, S. Artificial intelligence and ethics within the food sector: Developing a common language for technology adoption across the supply chain. Trends Food Sci. Technol. 2022, 125, 33–42. [Google Scholar] [CrossRef]
- Wright, C.S. Bitcoin: A Peer-to-Peer Electronic Cash System. pp. 1–9. Available online: https://ssrn.com/abstract=3440802 (accessed on 22 July 2022). [CrossRef]
- Tan, A.; Gligor, D.; Ngah, A. Applying blockchain for halal food traceability. Int. J. Logist. Res. Appl. 2020, 25, 947–964. [Google Scholar] [CrossRef]
- Anwar, M.R.; Apriani, D.; Adianita, I.R. Hash Algorithm In Verification of Certificate Data Integrity And Security. Aptisi Trans. Technopreneurship 2021, 3, 181–188. [Google Scholar] [CrossRef]
- Zheng, W.; Zheng, Z.; Chen, X.; Dai, K.; Li, P.; Chen, R. Nutbaas: A blockchain-as-a-service platform. IEEE Access 2019, 7, 134422–134433. [Google Scholar] [CrossRef]
- Nair, P.R.; Dorai, D.R. Evaluation of Performance and Security of Proof of Work and Proof of Stake using Blockchain. In Proceedings of the 2021 Third International Conference on Intelligent Communication Technologies and Virtual Mobile Networks (ICICV), Tirunelveli, India, 4–6 February 2021; pp. 279–283. [Google Scholar]
- Creydt, M.; Fischer, M. Blockchain and more-Algorithm driven food traceability. Food Control 2019, 105, 45–51. [Google Scholar] [CrossRef]
- Nasir, M.H.; Arshad, J.; Khan, M.M.; Fatima, M.; Salah, K.; Jayaraman, R. Scalable blockchains—A systematic review. Future Gener. Comput. Syst. 2022, 126, 136–162. [Google Scholar] [CrossRef]
- Kadadha, M.; Otrok, H.; Mizouni, R.; Singh, S.; Ouali, A. On-chain behavior prediction Machine Learning model for blockchain-based crowdsourcing. Future Gener. Comput. Syst. 2022, 136, 170–181. [Google Scholar] [CrossRef]
- Tanya, R.; Chelliah, B.J. A Comprehensive Study on Cybersecurity Challenges and Solutions in an IoT Framework. In Towards a Wireless Connected World: Achievements and New Technologies; Springer: Berlin/Heidelberg, Germany, 2022; pp. 105–137. [Google Scholar]
- Hallak, J.C.; Tacsir, A. Traceability systems as a differentiation tool in agri-food value chains: A framework for public policies in Latin America. J. Agribus. Dev. Emerg. Econ. 2022; ahead-of-print. [Google Scholar] [CrossRef]
- Nandakumar, K.; Sumathi, P.; Sanjaykumar, S.; Radhakrishnan, P.; Vasanthi, N.; Sandhiya, S. Food Safety Transparency and Traceability System Based on ML Enabled Blockchain Using Design Thinking. J. Posit. Sch. Psychol. 2022, 6, 5414–5424. [Google Scholar]
- Naik, G.; Suresh, D.N. Challenges of creating sustainable agri-retail supply chains. IIMB Manag. Rev. 2018, 30, 270–282. [Google Scholar] [CrossRef]
- Tsang, Y.P.; Choy, K.L.; Wu, C.H.; Ho, G.T.S.; Lam, H.Y. Blockchain-driven IoT for food traceability with an integrated consensus mechanism. IEEE Access 2019, 7, 129000–129017. [Google Scholar] [CrossRef]
- Ashton, K. That ‘internet of things’ thing. RFID J. 2009, 22, 97–114. [Google Scholar]
- Yin, H.; Cao, Y.; Marelli, B.; Zeng, X.; Mason, A.J.; Cao, C. Soil Sensors and Plant Wearables for Smart and Precision Agriculture. Adv. Mater. 2021, 33, e2007764. [Google Scholar] [CrossRef]
- Urdampilleta, M.; Ayela, C.; Ducrot, P.-H.; Rosario-Amorin, D.; Mondal, A.; Rouzières, M.; Dechambenoit, P.; Mathonière, C.; Mathieu, F.; Dufour, I.; et al. Molecule-based microelectromechanical sensors. Sci. Rep. 2018, 8, 8016. [Google Scholar] [CrossRef]
- Sharmila, S.; Vijayarani, S. Machine to Machine (M2M), Radio-frequency Identification (RFID), and Software-Defined Networking (SDN): Facilitators of the Internet of Things. In Artificial Intelligence-Based Internet of Things Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 219–242. [Google Scholar]
- El Matbouly, H.; Nikbakhtnasrabadi, F.; Dahiya, R. RFID Near-field Communication (NFC)-Based Sensing Technology in Food Quality Control. In Biosensing and Micro-Nano Devices; Springer: Singapore, 2022; pp. 219–241. [Google Scholar]
- Ye, H.; Lee, C.-J.; Wu, T.-Y.; Yang, X.-D.; Chen, B.-Y.; Liang, R.-H. Body-Centric NFC: Body-Centric Interaction with NFC Devices through Near-Field Enabled Clothing. In Proceedings of the Designing Interactive Systems Conference, Online, 13–17 June 2022; pp. 1626–1639. [Google Scholar]
- Tan, W.C.; Sidhu, M.S. Review of RFID and IoT integration in supply chain management. Oper. Res. Perspect. 2022, 9, 100229. [Google Scholar] [CrossRef]
- Ariza, J.A.; Baez, H. Understanding the role of single-board computers in engineering and computer science education: A systematic literature review. Comput. Appl. Eng. Educ. 2022, 30, 304–329. [Google Scholar] [CrossRef]
- Aronson, J.K. Artificial Intelligence in Pharmacovigilance: An Introduction to Terms, Concepts, Applications, and Limitations. Drug Saf. 2022, 45, 407–418. [Google Scholar] [CrossRef]
- Ou, W.; Gao, W.; Li, Z.; Zhang, S.; Wang, Q. Application of keywords speech recognition in agricultural voice information system. In Proceedings of the 2010 Second International Conference on Computational Intelligence and Natural Computing, Wuhan, China, 13–14 September 2010; pp. 197–200. [Google Scholar]
- Tran, N.K.; Albahra, S.; May, L.; Waldman, S.; Crabtree, S.; Bainbridge, S.; Rashidi, H. Evolving applications of artificial intelligence and machine learning in infectious diseases testing. Clin. Chem. 2022, 68, 125–133. [Google Scholar] [CrossRef] [PubMed]
- Tian, H.; Wang, T.; Liu, Y.; Qiao, X.; Li, Y. Computer vision technology in agricultural automation—A review. Inf. Process. Agric. 2020, 7, 1–19. [Google Scholar] [CrossRef]
- Vasconez, J.P.; Kantor, G.A.; Cheein, F.A.A. Human–robot interaction in agriculture: A survey and current challenges. Biosyst. Eng. 2019, 179, 35–48. [Google Scholar] [CrossRef]
- Dewi, T.; Risma, P.; Oktarina, Y.; Muslimin, S. Visual servoing design and control for agriculture robot; a review. In Proceedings of the 2018 International Conference on Electrical Engineering and Computer Science (ICECOS), Pangkal Pinang, Indonesia, 2–4 October 2018; pp. 57–62. [Google Scholar]
- Debats, S.R.; Luo, D.; Estes, L.D.; Fuchs, T.J.; Caylor, K.K. A generalized computer vision approach to mapping crop fields in heterogeneous agricultural landscapes. Remote Sens. Environ. 2016, 179, 210–221. [Google Scholar] [CrossRef] [Green Version]
- Ingram, J.; Maye, D.; Bailye, C.; Barnes, A.; Bear, C.; Bell, M.; Cutress, D.; Davies, L.; de Boon, A.; Dinnie, L.; et al. What are the priority research questions for digital agriculture? Land Use Policy 2022, 114, 105962. [Google Scholar] [CrossRef]
- Wang, X. Managing Land Carrying Capacity: Key to Achieving Sustainable Production Systems for Food Security. Land 2022, 11, 484. [Google Scholar] [CrossRef]
- Feng, L.; Zhang, H.; Lou, L.; Chen, Y. A blockchain-based collocation storage architecture for data security process platform of WSN. In Proceedings of the 2018 IEEE 22nd International Conference on Computer Supported Cooperative Work in Design (CSCWD), Nanjing, China, 9–11 May 2018; pp. 75–80. [Google Scholar]
- Showail, A.; Tahir, R.; Zaffar, M.F.; Noor, M.H.; Al-Khatib, M. An Internet of Secure and Private Things: A Service-Oriented Architecture. Comput. Secur. 2022, 120, 102776. [Google Scholar] [CrossRef]
- Hyperledger Fabric Documentation. 2022. Available online: https://hyperledgerfabric.readthedocs.io/en/release-2.2/ (accessed on 22 July 2022).
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Differential privacy techniques for cyber physical systems: A survey. IEEE Commun. Surv. Tutor. 2020, 22, 746–789. [Google Scholar] [CrossRef] [Green Version]
- Inan, A.; Kantarcioglu, M.; Ghinita, G.; Bertino, E. Private record matching using differential privacy. In Proceedings of the 13th International Conference on Extending Database Technology, Lausanne, Switzerland, 20–26 March 2010; pp. 123–134. [Google Scholar]
- Mothukuri, V.; Parizi, R.M.; Pouriyeh, S.; Huang, Y.; Dehghantanha, A.; Srivastava, G. A survey on security and privacy of federated learning. Futur. Gener. Comput. Syst. 2021, 115, 619–640. [Google Scholar] [CrossRef]
- Triastcyn, A.; Faltings, B. Federated generative privacy. IEEE Intell. Syst. 2020, 35, 50–57. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, X.; Susilo, W.; Yang, G.; Jiang, Z.L.; Yiu, S.-M.; Wang, H. Generic server-aided secure multi-party computation in cloud computing. Comput. Stand. Interfaces 2022, 79, 103552. [Google Scholar] [CrossRef]
- Luongo, M.; Pon, C. The Keep Network: A Privacy Layer for Public Blockchains. 2018. Available online: https://static.coinpaprika.com/storage/cdn/whitepapers/448413.pdf (accessed on 22 July 2022).
- Mu, C.; Ding, T.; Sun, Y.; Huang, Y.; Li, F.; Siano, P. Energy Block-based Peer-to-Peer Contract Trading with Secure Multi-party Computation in Nanogrid. IEEE Trans. Smart Grid 2022, 8, 19410–19432. [Google Scholar] [CrossRef]
- Peng, S.; Cai, Z.; Liu, W.; Wang, W.; Li, G.; Sun, Y.; Zhu, L. Blockchain Data Secure Transmission Method Based on Homomorphic Encryption. Comput. Intell. Neurosci. 2022, 2022, 3406228. [Google Scholar] [CrossRef]
- Hellwig, D.P.; Huchzermeier, A. Distributed ledger technology and fully homomorphic encryption: Next-generation information-sharing for supply chain efficiency. In Innovative Technology at the Interface of Finance and Operations; Springer: Berlin/Heidelberg, Germany, 2022; pp. 31–49. [Google Scholar]
- Akram, M.; Sen, A. A case study Evaluation of Blockchain for digital identity verification and management in BFSI using Zero-Knowledge Proof. In Proceedings of the 2022 International Conference on Decision Aid Sciences and Applications (DASA), Chiangrai, Thailand, 23–25 March 2022; pp. 1295–1299. [Google Scholar]
- Wen, X.-J.; Chen, Y.-Z.; Fan, X.-C.; Zhang, W.; Yi, Z.-Z.; Fang, J.-B. Blockchain consensus mechanism based on quantum zero-knowledge proof. Opt. Laser Technol. 2022, 147, 107693. [Google Scholar] [CrossRef]
- Yang, K.; Wang, X.; Non-Interactive Zero-Knowledge Proofs to Multiple Verifiers. Cryptology ePrint Archive. 2022, pp. 1–55. Available online: https://eprint.iacr.org/2022/063 (accessed on 22 July 2022).
- Xu, J.; Gu, B.; Tian, G. Review of agricultural IoT technology. Artif. Intell. Agric. 2022, 6, 10–22. [Google Scholar] [CrossRef]
- Kuznetsov, A.; Poluyanenko, N.; Kiian, A.; Poliakova, O. Application of Bluetooth, Wi-Fi and GPS Technologies in the Means of Contact Tracking. In Information Security Technologies in the Decentralized Distributed Networks; Springer: Berlin/Heidelberg, Germany, 2022; pp. 33–69. [Google Scholar]
- Kang, J.; Xiong, Z.; Niyato, D.; Ye, D.; Kim, D.I.; Zhao, J. Toward secure blockchain-enabled internet of vehicles: Optimizing consensus management using reputation and contract theory. IEEE Trans. Veh. Technol. 2019, 68, 2906–2920. [Google Scholar] [CrossRef] [Green Version]
- Kuhn, M.; Funk, F.; Zhang, G.; Franke, J. Blockchain-based application for the traceability of complex assembly structures. J. Manuf. Syst. 2021, 59, 617–630. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Enyeart, D.; Ferris, C.; Laventman, G.; Manevich, Y.; et al. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, New York, NY, USA, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Zyskind, G.; Nathan, O. Decentralizing privacy: Using blockchain to protect personal data. In Proceedings of the Security and Privacy Workshops (SPW), San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar]
- Wang, L.; He, Y.; Wu, Z. Design of a Blockchain-Enabled Traceability System Framework for Food Supply Chains. Foods 2022, 11, 744. [Google Scholar] [CrossRef]
- Pateriya, R.K.; Sharma, S. Te evolution of RFID security and privacy: A research survey. In Proceedings of the 2011 International Conference on Communication Systems and Network Technologies, Jammu, India, 3–5 June 2011; pp. 115–119. [Google Scholar]
- Juels, A.; Rivest, R.L.; Szydlo, M. The blocker tag: Selective blocking of RFID tags for consumer privacy. In Proceedings of the 10th ACM conference on Computer and Communications Security, Singapore, 14 April–17 March 2015; pp. 103–111. [Google Scholar]
- Yuvaraj, N.; Raja, R.A.; Karthikeyan, T.; Kousik, N.V. Improved privacy preservation framework for cloud-based internet of things. In Internet of Things; CRC Press: Boca Raton, FL, USA, 2020; pp. 165–174. [Google Scholar]
- Shrestha, R.; Kim, S. Integration of IoT with blockchain and homomorphic encryption: Challenging issues and opportunities. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 2019; Volume 115, pp. 293–331. [Google Scholar]
- Gervais, A.; Karame, G.O.; Wüst, K.; Glykantzis, V.; Ritzdorf, H.; Capkun, S. On the security and performance of proof of work blockchains. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 3–16. [Google Scholar]
- Mirabelli, G.; Solina, V. Blockchain and agricultural supply chains traceability: Research trends and future challenges. Procedia Manuf. 2020, 42, 414–421. [Google Scholar] [CrossRef]
- Lavelli, V.; Beccalli, M.P. Cheese whey recycling in the perspective of the circular economy: Modeling processes and the supply chain to design the involvement of the small and medium enterprises. Trends Food Sci. Technol. 2022, 126, 86–98. [Google Scholar] [CrossRef]
- Syed, N.F.; Shah, S.W.; Trujillo-Rasua, R.; Doss, R. Traceability in supply chains: A Cyber security analysis. Comput. Secur. 2022, 112, 102536. [Google Scholar] [CrossRef]
- Sun, W. Application of Blockchain Technology in the Supply Chain Finance. In Proceedings of the IEEE International Conference on Cloud Computing and Big Data Analysis (ICCCBDA), Chengdu, China, 22–24 April 2022; pp. 205–209. [Google Scholar]
- Huang, S.; Wang, G.; Yan, Y.; Fang, X. Blockchain-based data management for digital twin of product. J. Manuf. Syst. 2020, 54, 361–371. [Google Scholar] [CrossRef]
- Tian, H.; Jian, Y.; Ge, X. Blockchain-based AMI framework for data security and privacy protection. Sustain. Energy Grids Netw. 2022, 32, 100807. [Google Scholar] [CrossRef]
- Zhou, P.; Wang, K.; Guo, L.; Gong, S.; Zheng, B. A Privacy-Preserving Distributed Contextual Federated Online Learning Framework with Big Data Support in Social Recommender Systems. IEEE Trans. Knowl. Data Eng. 2021, 33, 824–838. [Google Scholar] [CrossRef]
- Zhang, X.; Sun, P.; Xu, J.; Wang, X.; Yu, J.; Zhao, Z.; Dong, Y. Blockchain-based safety management system for the grain supply chain. IEEE Access 2020, 8, 36398–36410. [Google Scholar] [CrossRef]
- Truex, S.; Baracaldo, N.; Anwar, A.; Steinke, T.; Ludwig, H.; Zhang, R.; Zhou, Y. A hybrid approach to privacy-preserving federated learning. In Proceedings of the 12th ACM Workshop on Artificial Intelligence and Security, London, UK, 15 November 2019; ACM: New York, NY, USA, 2019; pp. 1–11. [Google Scholar] [CrossRef]
- Hua, J.; Wang, X.; Kang, M.; Wang, H.; Wang, F.-Y. Blockchain Based Provenance for Agricultural Products: A Distributed Platform with Duplicated and Shared Bookkeeping. In Proceedings of the 2018 IEEE Intelligent Vehicles Symposium (IV), Changshu, China, 26–30 June 2018; pp. 97–101. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Prieto, J.; De la Prieta, F.; Corchado, J.M. How blockchain improves the supply chain: Case study alimentary supply chain. Procedia Comput. Sci. 2018, 134, 393–398. [Google Scholar] [CrossRef]
- Wortmann Felix, C.M.; Andreas, B.; Dominik, B.; Elgar, F. Blockchain for the IoT: Privacy-Preserving Protection of Sensor Data. J. Assoc. Inf. Syst. 2019, 20, 1274–1309. [Google Scholar]
- Pincheira, C.; Miguel; Salek, A.; Muhammad; Vecchio, M.; Giaffreda, R. Blockchain-based traceability in Agri-Food supply chain management: A practical implementation. In Proceedings of the 2018 IoT Vertical and Topical Summit on Agriculture—Tuscany (IOT Tuscany), Tuscany, Italy, 8–9 May 2018; 9 May 2018; pp. 1–4. [Google Scholar]
- Kim, M.; Hilton, B.; Burks, Z.; Reyes, J. Integrating Blockchain, Smart Contract-Tokens, and IoT to Design a Food Traceability Solution. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 335–340. [Google Scholar]
- Baralla, G.; Ibba, S.; Marchesi, M.; Tonelli, R.; Missineo, S. A Blockchain Based System to Ensure Transparency and Reliability in Food Supply Chain. In European Conference on Parallel Processing; Springer: Cham, Switzerland, 2018; pp. 379–391. [Google Scholar]
- Peng, X.; Zhang, X.; Wang, X.; Li, H.; Xu, J.; Zhao, Z.; Wang, Y. Research on the Cross-Chain Model of Rice Supply Chain Supervision Based on Parallel Blockchain and Smart Contracts. Foods 2022, 11, 1269. [Google Scholar] [CrossRef]
- Tse, D.; Zhang, B.; Yang, Y.; Cheng, C.; Mu, H. Blockchain application in food supply information security. In Proceedings of the 2017 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Singapore, 10–13 December 2017; pp. 1357–1361. [Google Scholar]
- Shaik, C. Preventing counterfeit products using cryptography, qr code and webservice. Comput. Sci. Eng. Int. J. (CSEIJ) 2021, 11, 1–11. [Google Scholar] [CrossRef]
- Carter, C.A.; Zhong, F.; Zhu, J. Advances in Chinese agriculture and its global implications. Appl. Econ. Perspect. Policy 2012, 34, 1–36. [Google Scholar] [CrossRef]
- Kevorchian, C.; Gavrilescu, C.; Hurduzeu, G. A Peer-to-Peer (p2p) Agricultural Insurance Approach Based on Smart Contracts in Blockchain Ethereum. Agric. Econ. Rural Dev. New Ser. 2020, 1, 29–45. [Google Scholar]
- Singh, M. Can Blockchain Technology Support Agricultural Sustainability? Authorea Preprints 2022, 1–44. [Google Scholar]
- Kim, H.M.; Laskowski, M. Agriculture on the blockchain: Sustainable solutions for food, farmers, and financing. In Supply Chain Revolution, Barrow Books; AMACOM: New York, NY, USA, 2018. [Google Scholar]
- Shen, M.; Tang, X.; Zhu, L.; Du, X.; Guizani, M. Privacy-preserving support vector machine training over blockchain-based encrypted IoT data in smart cities. IEEE Internet Things J. 2019, 6, 7702–7712. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-based data sharing for electronic medical records in cloud environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Hassan, M.U.; Rehmani, M.H.; Chen, J. Privacy preservation in blockchain based IoT systems: Integration issues, prospects, challenges, and future research directions. Future Gener. Comput. Syst. 2019, 97, 512–529. [Google Scholar] [CrossRef]
- Rahman, M.A.; Hossain, M.S.; Islam, M.S.; Alrajeh, N.A.; Muhammad, G. Secure and provenance enhanced internet of health things framework: A blockchain managed federated learning approach. IEEE Access 2020, 8, 205071–205087. [Google Scholar] [CrossRef]
- George, R.V.; Harsh, H.O.; Ray, P.; Babu, A.K. Food quality traceability prototype for restaurants using blockchain and food quality data index. J. Clean. Prod. 2019, 240, 118021. [Google Scholar] [CrossRef]
- Zheng, M.; Zhang, S.; Zhang, Y.; Hu, B. Construct Food Safety Traceability System for People’s Health Under the Internet of Things and Big Data. IEEE Access 2021, 9, 70571–70583. [Google Scholar] [CrossRef]
- Masudin, I.; Ramadhani, A.; Restuputri, D.P.; Amallynda, I. The effect of traceability system and managerial initiative on indonesian food cold chain performance: A COVID-19 pandemic perspective. Glob. J. Flex. Syst. Manag. 2021, 22, 331–356. [Google Scholar] [CrossRef]
- Katsikouli, P.; Wilde, A.S.; Dragoni, N.; Høgh-Jensen, H. On the benefits and challenges of blockchains for managing food supply chains. J. Sci. Food Agric. 2021, 101, 2175–2181. [Google Scholar] [CrossRef]
- Köhler, S.; Pizzol, M. Technology assessment of blockchain-based technologies in the food supply chain. J. Clean. Prod. 2020, 269, 122193. [Google Scholar] [CrossRef]
- Cozzolino, D. Recent trends on the use of infrared spectroscopy to trace and authenticate natural and agricultural food products. Appl. Spectrosc. Rev. 2012, 47, 518–530. [Google Scholar] [CrossRef]
- Lyu, D.; Zhou, L.; Ma, X. Income-increasing effect of e-commerce of agricultural products based on IT absorptive theory. Wirel. Netw. 2022, 28, 2337–2344. [Google Scholar] [CrossRef]
- Chao, S. Construction Model of E-Commerce Agricultural Product Online Marketing System Based on Blockchain and Improved Genetic Algorithm. Secur. Commun. Netw. 2022, 2022, 4055698. [Google Scholar] [CrossRef]
- Demestichas, K.; Peppes, N.; Alexakis, T.; Adamopoulou, E. Blockchain in agriculture traceability systems: A review. Appl. Sci. 2020, 10, 4113. [Google Scholar] [CrossRef]
- Dabholkar, A.; Saraswat, V. Ripping the fabric: Attacks and mitigations on hyperledger fabric. In Applications and Techniques in Information Security, Proceedings of the 10th International Conference, ATIS 2019, Thanjavur, India, 22–24 November 2019; Springer: Singapore, 2019; pp. 300–311. [Google Scholar]
- Tang, C.; Ma, Y.; Yu, X. Design and Implementation of Port Video Terminals Security Access Authentication System Using Blockchain Technology. In E3S Web of Conferences; EDP Sciences: Les Ulis, France, 2021; p. 03086. [Google Scholar]
- Davda, Y.; Sunitha, R.; Honnavalli, P.B. Design of Hash Algorithm for Blockchain Security; EasyChair: Bangalore, India, 2022; pp. 1–8. [Google Scholar]
- Devika, K.N.; Bhakthavatchalu, R. Parameterizable FPGA implementation of SHA-256 using blockchain concept. In Proceedings of the 2019 International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 4–6 April 2019; pp. 370–374. [Google Scholar]
- Sankar, L.S.; Sindhu, M.; Sethumadhavan, M. Survey of consensus protocols on blockchain applications. In Proceedings of the 2017 4th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 January 2017; pp. 1–5. [Google Scholar]
- Bouraga, S. A taxonomy of blockchain consensus protocols: A survey and classification framework. Expert Syst. Appl. 2021, 168, 114384. [Google Scholar] [CrossRef]
- Chen, D.; Orekondy, T.; Fritz, M. Gs-wgan: A gradient-sanitized approach for learning differentially private generators. arXiv 2020, arXiv:2006.08265.2020. [Google Scholar]
- Lan, S.; Hong, J.; Chen, J.; Cai, J.; Wang, Y. Equation Chapter 1 Section 1 Differentially Private High-Dimensional Binary Data Publication via Adaptive Bayesian Network. Wirel. Commun. Mob. Comput. 2021, 2021, 8693978. [Google Scholar] [CrossRef]
- Wang, J.; Ling, X.; Le, Y.; Huang, Y.; You, X. Blockchain-enabled wireless communications: A new paradigm towards 6G. Natl. Sci. Rev. 2021, 8, nwab069. [Google Scholar] [CrossRef]
- Akbar, N.A.; Muneer, A.; ElHakim, N.; Fati, S.M. Distributed Hybrid Double-Spending Attack Prevention Mechanism for Proof-of-Work and Proof-of-Stake Blockchain Consensuses. Future Internet 2021, 13, 285. [Google Scholar] [CrossRef]
- Gerrits, L.; Samuel, C.N.; Kromes, R.; Verdier, F.; Glock, S.; Guitton-Ouhamou, P. Experimental Scalability Study of Consortium Blockchains with BFT Consensus for IoT Automotive Use Case. In Proceedings of the 19th ACM Conference on Embedded Networked Sensor Systems, Coimbra, Portugal, 15–17 November 2021; pp. 492–498. [Google Scholar] [CrossRef]
- Pandey, M.; Agarwal, R.; Shukla, S.K.; Verma, N.K. Reputation-based PoS for the Restriction of Illicit Activities on Blockchain: Algorand Usecase. arXiv 2021, arXiv:2112.11024. [Google Scholar] [CrossRef]
- Zhao, H.; Deng, S.; Liu, Z.; Xiang, Z.; Yin, J.; Dustdar, S.; Zomaya, A. Dpos: Decentralized, privacy-preserving, and low-complexity online slicing for multi-tenant networks. IEEE Trans. Mob. Comput. 2021. [Google Scholar] [CrossRef]
- Yasir, A.I.; Kusuma, G.P. Deep Deterministic Policy Gradients for Optimizing Simulated PoA Blockchain Networks Based on Healthcare Data Characteristics. Adv. Sci. Technol. Eng. Syst. J. 2021, 6, 757–764. [Google Scholar] [CrossRef]
- Yuan, R.; Yu-Bin, X.; Chen, H.-B.; Bin-Yu, Z.; Xie, J. Shadoweth: Private smart contract on public blockchain. J. Comput. Sci. Technol. 2018, 33, 542–556. [Google Scholar] [CrossRef]
- Kalodner, H.; Goldfeder, S.; Chen, X.; Weinberg, S.M.; Felten, E.W. Arbitrum: Scalable, Private Smart Contracts; USENIX Association: Baltimore, MD, USA, 2018; pp. 1353–1370. Available online: https://www.usenix.org/conference/usenixsecurity18/presentation/kalodner (accessed on 22 July 2022).
- Sánchez, D.C. Raziel: Private and verifiable smart contracts on blockchains. arXiv 2018, arXiv:1807.09484. [Google Scholar]
- Atzei, N.; Bartoletti, M.; Cimoli, T. Atzei, N.; Bartoletti, M.; Cimoli, T. A survey of attacks on ethereum smart contracts (sok). In International Conference on Principles of Security and Trust; Springer: Berlin/Heidelberg, Germany, 2017; Bartoletti, M.; Volume 10204, pp. 164–186. [Google Scholar]
- Wen, Q.; Gao, Y.; Chen, Z.; Wu, D. A blockchain-based data sharing scheme in the supply chain by IIoT. In Proceedings of the 2019 IEEE International Conference on Industrial Cyber Physical Systems (ICPS), Taipei, Taiwan, 6–9 May 2019; pp. 695–700. [Google Scholar]
- Lin, Q.; Wang, H.; Pei, X.; Wang, J. Food safety traceability system based on blockchain and EPCIS. IEEE Access 2019, 7, 20698–20707. [Google Scholar] [CrossRef]
- Lin, C.; He, D.; Huang, X.; Xie, X.; Choo, K.-K.R. Ppchain: A privacy-preserving permissioned blockchain architecture for cryptocurrency and other regulated applications. IEEE Syst. J. 2020, 15, 4367–4378. [Google Scholar] [CrossRef]
- Pooja, S.; Mundada, M.R. Analysis of agricultural supply chain management for traceability of food products using blockchain-ethereum technology. In Proceedings of the 2020 IEEE International Conference on Distributed Computing, VLSI, Udupi, India, 30–31 October 2020, Electrical Circuits and Robotics (DISCOVER); pp. 127–132.
- Majdalawieh, M.; Nizamuddin, N.; Alaraj, M.; Khan, S.; Bani-Hani, A. Blockchain-based solution for Secure and Transparent Food Supply Chain Network. Peer-Peer Netw. Appl. 2021, 14, 3831–3850. [Google Scholar] [CrossRef]
- Koval, M. Blockchain in Dairy Supply Chains: A Literature Review. Master’s Thesis, University of Twente, Enschede, The Netherlands, 2022. [Google Scholar]
- Guo, J.; Li, C.; Luo, Y. Blockchain-assisted caching optimization and data storage methods in edge environment. J. Supercomput. 2022, 1–33. [Google Scholar] [CrossRef]
- Daulatrao, B.C.; Nandkumar, D.P.; Atmaram, J.G.; Dattatray, P.Y.; Mohanrao, S.S. Agri Food Supply Chain Using Ethereum Smart Contract. Int. J. Mod. Dev. Eng. Sci. 2022, 1, 11–16. [Google Scholar]
- Marchesi, L.; Mannaro, K.; Marchesi, M.; Tonelli, R. Automatic Generation of Ethereum-Based Smart Contracts for Agri-Food Traceability System. IEEE Access 2022, 10, 50363–50383. [Google Scholar] [CrossRef]
- Hayati, H.; Nugraha, I.G.B.B. Blockchain based traceability system in food supply chain. In Proceedings of the 2018 International Seminar on Research of Information Technology and Intelligent Systems (ISRITI), Yogyakarta, Indonesia, 21–22 November 2018; pp. 120–125. [Google Scholar]
- Mohan, T. Improve Food Supply Chain Traceability Using Blockchain. Master’s Thesis, The Pennsylvania State University, State College, PA, USA, 2018. [Google Scholar]
- Baralla, G.; Pinna, A.; Corrias, G. Ensure traceability in European food supply chain by using a blockchain system. In Proceedings of the 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain (WETSEB), Montreal, QC, Canada, 27–27 May 2019; pp. 40–47. [Google Scholar]
- Chan, K.Y.; Abdullah, J.; Khan, A.S. A framework for traceable and transparent supply chain management for agri-food sector in malaysia using blockchain technology. Int. J. Adv. Comput. Sci. Appl. 2019, 10, 149–156. [Google Scholar] [CrossRef] [Green Version]
- Bumblauskas, D.; Mann, A.; Dugan, B.; Rittmer, J. A blockchain use case in food distribution: Do you know where your food has been? Int. J. Inf. Manag. 2020, 52, 102008. [Google Scholar] [CrossRef]
- Pincheira, M.; Vecchio, M.; Giaffreda, R. Benchmarking Constrained IoT Devices in Blockchain-Based Agri-Food Traceability Applications. Int. Congress Blockchain Appl. 2021, 320, 212–221. [Google Scholar] [CrossRef]
- Wisessing, K.; Vichaidis, N. IoT Based Cold Chain Logistics with Blockchain for Food Monitoring Application. In Proceedings of the 2022 7th International Conference on Business and Industrial Research (ICBIR), Bangkok, Thailand, 19–20 May 2022; pp. 359–363. [Google Scholar]
- Mohit, M.; Kaur, S.; Singh, M. Design and implementation of transaction privacy by virtue of ownership and traceability in blockchain based supply chain. Cluster Comput. 2022, 25, 2223–2240. [Google Scholar] [CrossRef]
- Wan, J.; Li, J.; Imran, M.; Li, D. A blockchain-based solution for enhancing security and privacy in smart factory. IEEE Trans. Ind. Inform. 2019, 15, 3652–3660. [Google Scholar] [CrossRef]
- Sahai, S.; Singh, N.; Dayama, P. Enabling Privacy and Traceability in Supply Chains using Blockchain and Zero Knowledge Proofs. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; pp. 134–143. [Google Scholar]
- Balasubramanian, S.; Akila, I.S. Blockchain implementation for agricultural food supply Chain using hyperledger fabric. J. Intell. Fuzzy Syst. 2022; pre-press. [Google Scholar] [CrossRef]
- Balamurugan, S.; Ayyasamy, A.; Joseph, K.S. IoT-Blockchain driven traceability techniques for improved safety measures in food supply chain. Int. J. Inf. Tecnol. 2022, 14, 1087–1098. [Google Scholar] [CrossRef]
- Lu, Y.; Li, P.; Xu, H. A Food anti-counterfeiting traceability system based on Blockchain and Internet of Things. Procedia Comput. Sci. 2022, 199, 629–636. [Google Scholar] [CrossRef]
- Gallo, P.; Daidone, F.; Sgroi, F.; Avantaggiato, M. AgriChain: Blockchain Syntactic and Semantic Validation for Reducing Information Asymmetry in Agri-Food. In Proceedings of the 2022: 4th Distributed Ledger Technology Workshop, Rome, Italy, 20 June 2022; pp. 1–3166. Available online: http://ceur-ws.org/Vol-3166/paper08.pdf (accessed on 22 July 2022).
- Ravi, D.; Ramachandran, S.; Vignesh, R.; Falmari, V.R.; Brindha, M. Privacy preserving transparent supply chain management through Hyperledger Fabric. Blockchain Res. Appl. 2022, 3, 100072. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhu, D.; Ren, X.; Shen, Y.; Cao, X.; Liu, H.; Li, J. Quality changes and shelf-life prediction model of postharvest apples using partial least squares and artificial neural network analysis. Food Chem. 2022, 394, 133526. [Google Scholar] [CrossRef]
- Himthani, P.; Dubey, G.P.; Sharma, B.M.; Taneja, A. Big Data Privacy and Challenges for Machine Learning. In Proceedings of the 2020 Fourth International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 7–9 October 2020; pp. 707–713. [Google Scholar]
- Onal, A.C.; Berat Sezer, O.; Ozbayoglu, M.; Dogdu, E. Weather data analysis and sensor fault detection using an extended IoT framework with semantics, big data, and machine learning. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2037–2046. [Google Scholar]
- Liu, B.; Ding, M.; Shaham, S.; Rahayu, W.; Farokhi, F.; Lin, Z. When machine learning meets privacy: A survey and outlook. ACM Comput. Surv. 2021, 54, 1–36. [Google Scholar] [CrossRef]
- Ryffel, T.; Trask, A.; Dahl, M.; Wagner, B.; Mancuso, J.; Rueckert, D.; Passerat-Palmbach, J. A generic framework for privacy preserving deep learning. arXiv 2018, arXiv:1811.04017. [Google Scholar]
- Hang, L.; Ullah, I.; Kim, D.-H. A secure fish farm platform based on blockchain for agriculture data integrity. Comput. Electron. Agric. 2020, 170, 105251. [Google Scholar] [CrossRef]
- Ajagbe, S.A.; Awotunde, J.B.; Adesina, A.O.; Achimugu, P.; Kumar, T.A. Internet of Medical Things (IoMT): Applications, Challenges, and Prospects in a Data-Driven Technology. Intell. Healthc. 2022, 299–319. [Google Scholar] [CrossRef]
- Takatsuji, T.; Watanabe, H.; Yamashita, Y. Blockchain technology to visualize the metrological traceability. Precis. Eng. 2019, 58, 1–6. [Google Scholar] [CrossRef]
- Kshetri, N. The Economics of Blockchain-Based Supply Chain Traceability in Developing Countries. Computer 2021, 54, 98–103. [Google Scholar] [CrossRef]
- Wan, L.; Eyers, D.; Zhang, H. Evaluating the impact of network latency on the safety of blockchain transactions. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 194–201. [Google Scholar]
- Zhao, C.; Zhang, S.; Wang, T.; Liew, S.C. Bodyless Block Propagation: TPS Fully Scalable Blockchain with Pre-Validation. arXiv 2022, arXiv:2204.08769. [Google Scholar]
- Sezer, B.B.; Topal, S.; Nuriyev, U. TPPSUPPLY: A traceable and privacy-preserving blockchain system architecture for the supply chain. J. Inf. Secur. Appl. 2022, 66, 103116. [Google Scholar] [CrossRef]
- Li, H.; Han, D.; Tang, M. A privacy-preserving storage scheme for logistics data with assistance of blockchain. IEEE Internet Things J. 2021, 9, 4704–4720. [Google Scholar] [CrossRef]
- Islam, M.; Rehmani, M.H.; Chen, J. Differential Privacy-based Permissioned Blockchain for Private Data Sharing in Industrial IoT. arXiv 2021, arXiv:2102.09857. [Google Scholar]
- Liang, W.; Ji, N. Privacy challenges of IoT-based blockchain: A systematic review. Clust. Comput. 2021, 25, 2203–2221. [Google Scholar] [CrossRef]
- Wu, G.; Wang, S.; Ning, Z.; Zhu, B. Privacy-Preserved EMR Information Publishing and Sharing: A Blockchain-Enabled Smart Healthcare System. IEEE J. Biomed. Health Inform. 2021, 26, 1917–1927. [Google Scholar] [CrossRef]
- Zhou, P.; Kortoçi, P.; Yau, Y.-P.; Finley, B.; Wang, X.; Braud, T.; Lee, L.-H.; Tarkoma, S.; Kangasharju, J.; Hui, P. AICP: Augmented Informative Cooperative Perception. IEEE Trans. Intell. Transp. Syst. 2022, 1–14. [Google Scholar] [CrossRef]
- Pang, G. The AI Chip Race. IEEE Intell. Syst. 2022, 37, 111–112. [Google Scholar] [CrossRef]
- Ahmed, W.A.; MacCarthy, B.L. Blockchain technology in the supply chain: Learning from emerging ecosystems and industry consortia. In Handbook on Digital Business Ecosystems; Edward Elgar Publishing: Cheltenham, UK, 2022; pp. 367–386. [Google Scholar]
- Salim, A.M.; Dabous, S.A. A review of critical success factors for solar home system implementation in public housing. Int. J. Energy Sect. Manag. 2022; ahead-of-print. [Google Scholar] [CrossRef]
- Cai, L.; Sun, Y.; Zheng, Z.; Xiao, J.; Qiu, W. Blockchain in China. Commun. ACM 2021, 64, 88–93. [Google Scholar] [CrossRef]
- Coad, A.; Harasztosi, P.; Pál, R.; Teruel, M.; others. Policy instruments for high-growth enterprises. Quest. Entrep. State 2022, 53, 273. [Google Scholar]
- Benyam, A.A.; Soma, T.; Fraser, E. Digital agricultural technologies for food loss and waste prevention and reduction: Global trends, adoption opportunities and barriers. J. Clean. Prod. 2021, 323, 129099. [Google Scholar] [CrossRef]
- Marin, M.-P.; Marin, I.; Vidu, L. Learning about the reduction of food waste using blockchain technology. arXiv 2021, arXiv:2101.02026. [Google Scholar]
- Trollman, H.; Garcia-Garcia, G.; Jagtap, S.; Trollman, F. Blockchain for Ecologically Embedded Coffee Supply Chains. Logistics 2022, 6, 43. [Google Scholar] [CrossRef]
- Gopalakrishnan, P.K.; Hall, J.; Behdad, S. Cost analysis and optimization of Blockchain-based solid waste management traceability system. Waste Manag. 2021, 120, 594–607. [Google Scholar] [CrossRef]
- Sunny, J.; Undralla, N.; Pillai, V.M. Supply chain transparency through blockchain-based traceability: An overview with demonstration. Comput. Ind. Eng. 2020, 150, 106895. [Google Scholar] [CrossRef]
- Ferlay, J.; Colombet, M.; Soerjomataram, I.; Mathers, C.; Parkin, D.M.; Piñeros, M.; Znaor, A.; Bray, F. Estimating the global cancer incidence and mortality in 2018: GLOBOCAN sources and methods. Int. J. Cancer 2019, 144, 1941–1953. [Google Scholar] [CrossRef] [Green Version]
- Garcia-Torres, S.; Albareda, L.; Rey-Garcia, M.; Seuring, S. Traceability for sustainability–literature review and conceptual framework. Supply Chain. Manag. Int. J. 2019, 24, 85–106. [Google Scholar] [CrossRef]
- Gomiero, T.; Pimentel, D.; Paoletti, M.G. Is there a need for a more sustainable agriculture? Crit. Rev. Plant Sci. 2011, 30, 6–23. [Google Scholar] [CrossRef]
- Kaur, P.; Parashar, A. A systematic literature review of blockchain technology for smart villages. Arch. Comput. Methods Eng. 2021, 29, 2417–2468. [Google Scholar] [CrossRef] [PubMed]
- Kamilaris, A.; Fonts, A.; Prenafeta-Boldu, F.X. The rise of blockchain technology in agriculture and food supply chains. Trends Food Sci. Technol. 2019, 91, 640–652. [Google Scholar] [CrossRef] [Green Version]
- Funk, E.; Riddell, J.; Ankel, F.; Cabrera, D. Blockchain technology: A data framework to improve validity, trust, and accountability of information exchange in health professions education. Acad. Med. 2018, 93, 1791–1794. [Google Scholar] [CrossRef] [PubMed]
- Singh, S.; Sharma, P.K.; Yoon, B.; Shojafar, M.; Cho, G.H.; Ra, I.-H. Convergence of blockchain and artificial intelligence in IoT network for the sustainable smart city. Sustain. Cities Soc. 2020, 63, 102364. [Google Scholar] [CrossRef]
- Blanco, C.; Wall, M.M.; Olfson, M. Data needs and models for the opioid epidemic. Mol. Psychiatry 2021, 27, 787–792. [Google Scholar] [CrossRef]
- Goldfeder, S.; Kalodner, H.; Reisman, D.; Narayanan, A. When the cookie meets the blockchain: Privacy risks of web payments via cryptocurrencies. arXiv 2017, arXiv:1708.04748. [Google Scholar] [CrossRef] [Green Version]

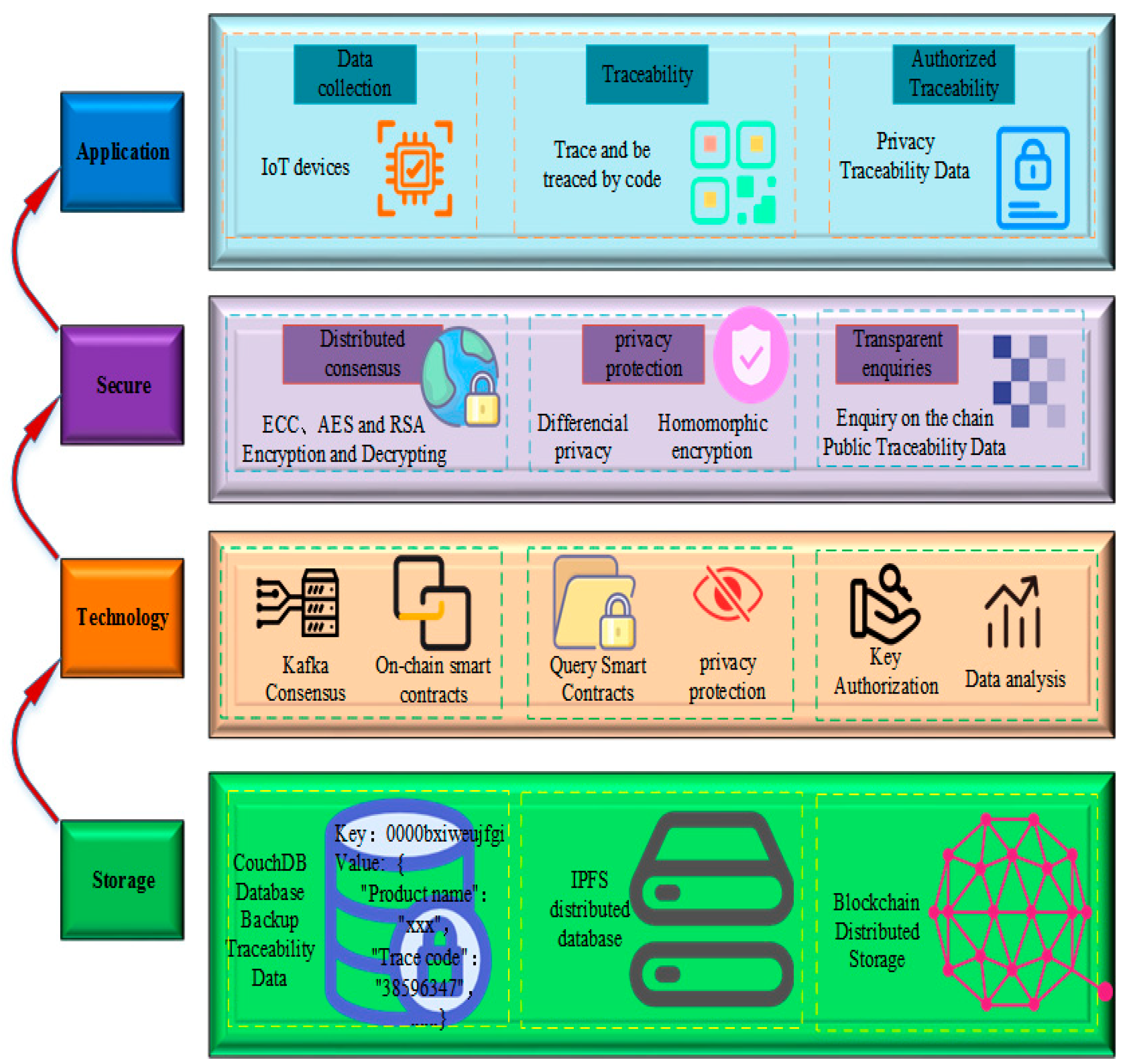
| Requirements | Description |
|---|---|
| R1 | Unique and the uniform identification of food products. |
| R2 | Transparent and authentic traceability data for food products. |
| R3 | Secure and uniform protection of private data that is not publicly available. |
| R4 | Real-time monitoring of food quality and safety during production, storage, and logistics. |
| R5 | Decision support for resource allocation and product quality assessment. |
| Requirements | Technologies | |||
|---|---|---|---|---|
| IoT | AI | PP | BC | |
| R1 | √ | √ | ||
| R2 | √ | √ | √ | |
| R3 | √ | |||
| R4 | √ | √ | ||
| R5 | √ | √ | ||
| R6 | √ | √ | ||
| Technologies | Application | Consumption | Transmission Distance | Advantage |
|---|---|---|---|---|
| Wireless WAN (GPRS/4G/5G/WiFi) | Voice, data | High | Long distance | Large coverage, high flexibility |
| Bluetooth (3.0/4.0/5.0) | Media, cable | Low | Within 10 m | Cheaper and simple configuration |
| ZigBee (1.0/2.0/3.0) | Monitoring, sensors | Low | Between 10 to 100 m | Low power, flexible network-topology |
| Lora | Data transparent transmission | Low | Long distance | Low power, stable operation |
| Categories | Attack Types |
|---|---|
| Data-based attacks | Data leakage, Unreal data injection attack, Database leakage, Cryptographic-based attacks |
| Network-based attacks | DoS/DDoS, Communication protocol attack, Side channel attack |
| Application-based attacks | Phishing websites, Script viruses, DoS/DDoS |
| BC-based attacks | Third-party attacks, Software update attacks, Interception attacks, Replay attacks, state-fork attacks, Consensus-based attacks, SC-based attacks |
| IoT-based attacks | Sensor incidents, Sensor weakening, Untrusted node, System hijacking |
| other attacks | Virus attacks, Supply chain attacks, Man-in-the-middle attacks, Social engineering analysis, Malware attacks |
| Name | Description |
|---|---|
| Differential privacy | Adding noise make it impossible for a malicious attacker to get one piece of real data out of many private messages. |
| Federated learning | Combine multiple data sources to model and provide model inference and prediction services without local data from all parties. |
| Secure multiparty computation | Techniques and systems for the secure calculation of agreed functions where participants do not share their data and where there are no trusted third parties. |
| Homomorphic encryption | Data can be transferred, analyzed, and returned between different participants and the cloud without being viewed and in clear text. |
| Zero-knowledge proof | The sender proves the authenticity of the data to the verifier, then completes the verification without revealing the real transmitted data. |
| Questions | Description |
|---|---|
| Q1 | How do PP and IoT help food traceability monitor storage status in real-time traceability? |
| Q2 | How can blockchain securely verify and share food data on the traceability chain? |
| Q3 | How does the combination of IoT and blockchain ensure the identification of traceable food and resources? |
| Q4 | How can IoT, PP, and AI ensure the secure storage of traceability data without tampering? |
| Q5 | How do AI and PP help traceability systems make effective and intelligent decisions? |
| Platforms | Paper Working & Ref. |
|---|---|
| Ethereum | Fully decentralized AgriBlockIoT, a solution for agri-food supply chain man Agement [88] |
| A food safety traceability system based on the blockchain and the EPC Information Services using enterprise-level smart contract to prevent data tampering and sensitive information disclosure [130] | |
| A permissioned blockchain structure that protects privacy, using group signatures and broadcast encryption for privacy protection of data, and a PBFT for network-wide verification [136] | |
| An agricultural supply chain system model ensures security and trust and simplifies transactions and administrative procedures [137] | |
| A transparent, reliable, and tamper-proof framework for the food supply chain using smart contracts to develop [138] | |
| Double systems (Hyperledger Sawtooth & Ethereum) to develop dairy supply chain [139] | |
| Data is stored in the Interstellar File Storage System (IPFS), then returns a hash of the data stored on the blockchain which ensures a secure solution [140] | |
| A comprehensive solution for the agri-food supply chain. Ensures delivery mechanisms for the agri-food industry supply chain (IPFS stored data) [141] | |
| A customized smart contract semi-automatic system designed for the agri-food industry sector (honey as an example) [131] | |
| Hyperledger Sawtooth | FoodTrail deepens the advantages in terms of access, security, and accuracy [132] |
| Be used to provide greater asset traceability in today’s food supply chains [142] | |
| The proposed system allows consumers to reconstruct the history of a product down to its origin for verification of health and quality with a simple QR code scan [143] | |
| An agri-food blockchain technology in Malaysia (pepper), especially extends transparency and traceability in permissioned blockchain [144] | |
| The goal is to track egg products from farm to fork using blockchain and internet of things (IoT) enabled technologies [145] | |
| Focus on assessing the impact that a blockchain traceability system may have on constrained sensing devices. (test on Ethereum and Hyperledger Sawtooth) [146] | |
| The concept of using IoT devices in combination with a cold chain (Hyperledger Sawtooth) system [147] | |
| A traceability system, introducing product code and timestamps to protect privacy, as well as using asymmetric encryption algorithms for verification and signatures [133] | |
| Hyperledger Fabric | Customizes the existing Hyperledger architecture and adds a PP module based on DP to its smart contract [134] |
| Combining ZKP technology to ensure privacy and traceability in the food supply chain [148] | |
| A decentralized application (DApp) to verify food quality and the agricultural supply chain because of its high involvement and transparency [149] | |
| A platform ensures data availability and traceability. The identification of unsafe food can be prevented from entering and enhances food safety and reduces manual errors [150] | |
| The system ensures the uniqueness of food products, and the authenticity and reliability of the blockchain source data are ensured through IoT [151] | |
| A platform that combats information asymmetry and collusive relationships and provides a dual mechanism for validating crowd-sensing data [152] | |
| Help the development of the supply chain industry and the refinement of other blockchain systems, striking a balance between privacy protection and security and public blockchain [135] | |
| A framework for a supply chain traceability system based on Hyperledger Fabric and passive RFID [70] |
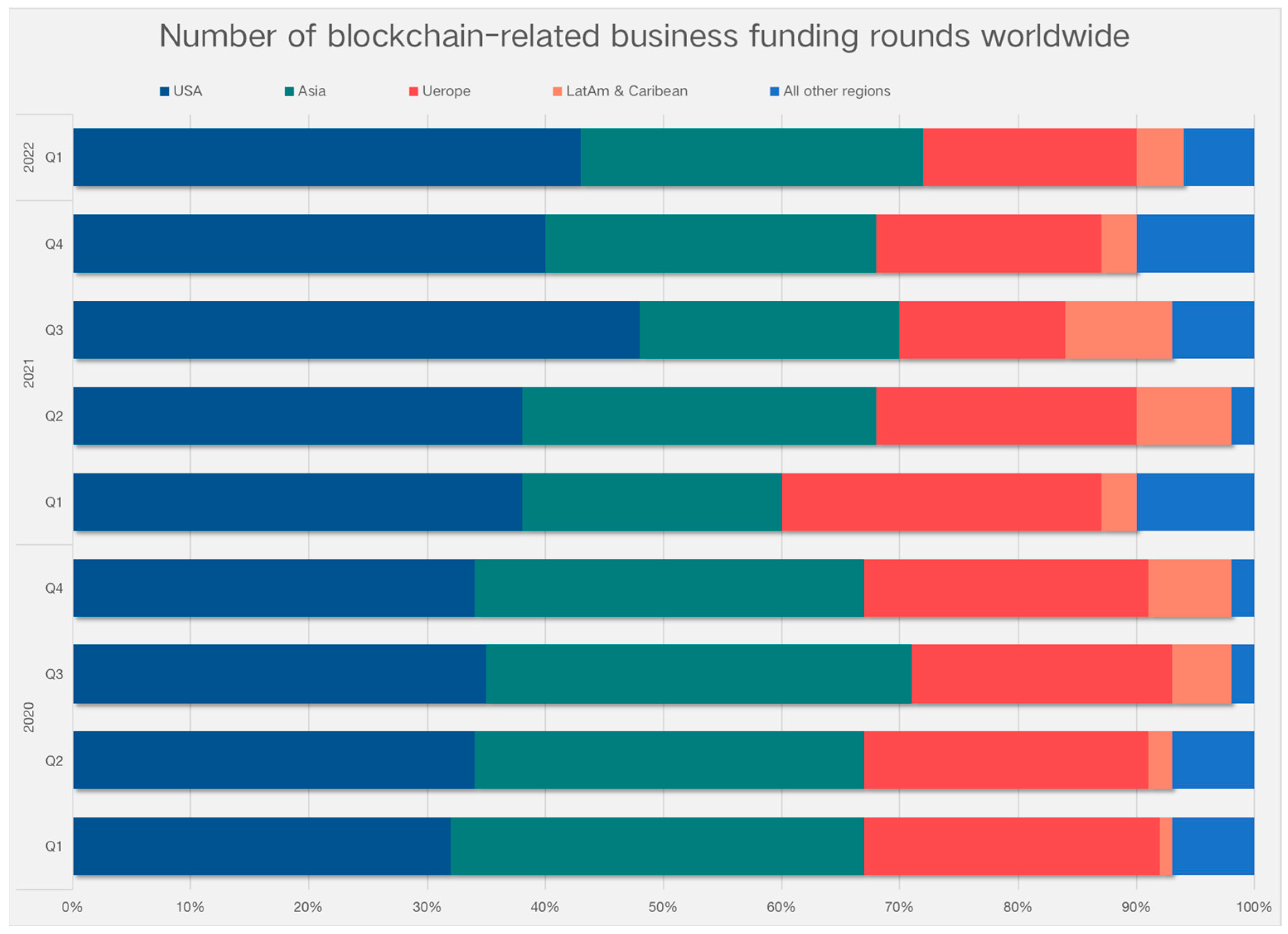
| Company Name | Round Amount | Country |
|---|---|---|
| Fireblocks | $550 M | USA |
| ConsenSys | $450 M | USA |
| Yuga Labs | $450 M | USA |
| FTX | $400 M | Bahamas |
| Animoca Brands | $359 M | Hong Kong |
| OpenSea | $300 M | USA |
| Blockdaemon | $207 M | USA |
| The Graph | $205 M | USA |
| Alchemy | $200 M | USA |
| Aleo | $200 M | USA |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lei, M.; Xu, L.; Liu, T.; Liu, S.; Sun, C. Integration of Privacy Protection and Blockchain-Based Food Safety Traceability: Potential and Challenges. Foods 2022, 11, 2262. https://doi.org/10.3390/foods11152262
Lei M, Xu L, Liu T, Liu S, Sun C. Integration of Privacy Protection and Blockchain-Based Food Safety Traceability: Potential and Challenges. Foods. 2022; 11(15):2262. https://doi.org/10.3390/foods11152262
Chicago/Turabian StyleLei, Moyixi, Longqin Xu, Tonglai Liu, Shuangyin Liu, and Chuanheng Sun. 2022. "Integration of Privacy Protection and Blockchain-Based Food Safety Traceability: Potential and Challenges" Foods 11, no. 15: 2262. https://doi.org/10.3390/foods11152262





