Detour-RS: Reroute Attack Vulnerability Assessment with Awareness of the Layout and Resource †
Abstract
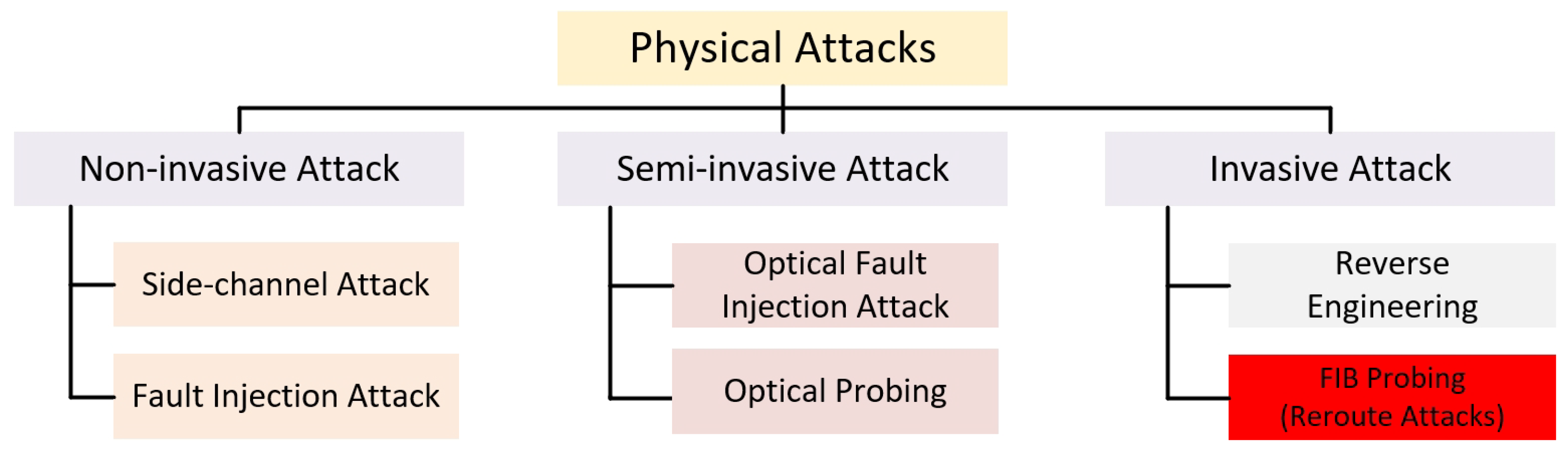
:1. Introduction
- Reverse engineering: When an adversary gains access to the physical IC, he/she may attempt to reverse engineer the design and functionality of the device using FIB-based techniques. This poses a threat to intellectual property and proprietary information.
- Counterfeiting and tampering: FIB-based probing can be employed to modify or tamper with the IC at the silicon level. This is a concern in applications where the integrity and authenticity of the IC are critical, such as in secure microcontrollers or cryptographic devices.
- Hardware security modules: In the context of hardware security modules, where sensitive cryptographic operations are performed, FIB-based attacks could potentially compromise the confidentiality and integrity of cryptographic keys.
- Defense and aerospace applications: In sectors like defense and aerospace, where security is paramount, unauthorized access to and tampering with ICs through FIB-based attacks could have severe consequences, including the compromise of mission-critical systems.
- We introduce an advanced and meticulously automated security assessment framework that operates with a keen awareness of layout intricacies. This framework is tailored to assess the vulnerabilities within design layouts when subjected to the latest FIB precision techniques. Our proposed solution stands at the forefront of automation, providing a comprehensive evaluation of layout vulnerabilities in the context of reroute attacks, aligning seamlessly with the state-of-the-art capabilities of FIB technology.
- Our research has resulted in the development of an innovative metric, the layout-aware added traces’ length. This metric quantifies the effort required for the reroute attacks. Our solution seamlessly integrates both linear and nonlinear programming techniques into our framework. It automates the identification of circuit edit locations within shield nets, forming the basis for reroute path establishment and streamlining the process.
- We conducted a comprehensive series of experiments using various physical design layouts for a system-on-chip (SoC) design, employing our Detour-RS framework. Our findings indicate that a two-layer shield structure offers greater resilience against reroute attacks compared to a single-layer design. Additionally, within the context of two-layer shield protection, an orthogonal configuration exhibited higher resistance than a parallel one. These insights underscore the potential benefits of particular layout choices for enhancing the security of intricate SoC designs.
- We propose time and gas consumption metrics to evaluate the resource consumption of the reroute attackers. The results are demonstrated for different sets of target assets, and we also obtained the average resource cost for each single via, which provides another fair perspective to evaluate the reroute attacks.
- We methodically explored both independent and dependent scenarios, distinguishing mainly by whether circuit edits from reroute attacks are allowed to overlap or not. Our findings reveal a noteworthy observation: in the more practical dependent scenario, there is a nearly 50% increase in the demand for layout-aware added traces. Furthermore, we introduce a graphical tool that facilitates intuitive visualization of target asset exposure to reroute attacks, along with the associated statistical insights.
- Improved simplicity and accuracy: We extend our linear programming-based approach in [31] to a hybrid model covering both linear and nonlinear scenarios such that the vulnerabilities of reroute attacks within the target layout can be analyzed in a more comprehensive and accurate manner. Although the linear programming we utilized previously can be effective in reroute attack vulnerability assessment, the linear constraints increase exponentially with respect to targets and associated shield nets. As such, the linear programming-based implementation in our original solution (i.e., Detour) is very tricky and error-prone since the discontinuous constraints involved need to be deliberately analyzed and attached under various intrusion scenarios. Missing single-corner cases can easily lead to suboptimal results, e.g., over-/under-estimating the vulnerabilities. In contrast, employing a general optimization methodology that can handle both linear and nonlinear problems can be very beneficial to alleviate the cumbersomeness of constraint creation because we only need to define the entire problem scope for gradient-based search, making the analysis more reliable and accurate.
- Nonlinear problem coverage: As all linear programming problems are mathematically special cases of nonlinear problems, our hybrid model in Detour-RS can effectively address all cases of Detour (our conference version). In addition to the implementation perspective, we would like to highlight that using a hybrid model including nonlinear programming is not overkill in our case because the objective function, in some complicated scenarios, is better represented with a continuous, but nonlinear one. We present a specific example to illustrate how our extended hybrid model can address nonlinear scenarios in Section 5.1.
- Time and gas metrics: Almost all existing works regarding reroute attacks or micro-probing attack vulnerability assessment focus on the exploitable windows of FIB intrusions, e.g., the exposed area metric in our framework. However, other factors can also play important roles in practical attack determination. It is worth mentioning that FIB is extremely precise and expensive equipment; the required time and gas resource consumption of reroute attacks thus reflect the feasibility and difficulty, serving as a useful reference for threat evaluation.
2. Background
2.1. Basics of FIB-Based Micro-Probing
2.2. FIB-Aware Anti-Probing Physical Design Flow
2.3. Countermeasures
2.4. Exposed Area
- is the depth or distance from the shield layer to the target layer in the IC layout. This depth should be available in the process design kit (PDK) for the IC’s technology node.
- denotes the FIB aspect ratio (see Figure 2a), which can be found in FIB datasheets and, in the case of probing, represents the attacker’s capability.
- represents the nominal width of shield wires. The minimum wire width is a parameter that can be found in the PDK.
- is the process variation margin of shield wires.
- is the space required between the shield and hole to avoid shorts created by operator/FIB localization error. This parameter can be estimated by the FIB’s datasheets and empirical studies.
2.5. Threat Model
3. Detour-RS Framework
3.1. Overview
3.2. Probing Area Calculation
3.3. Shield and Other Obscuring Nets’ Extraction
| Algorithm 1: Shield nets’ extraction. | |
| Input: Layout—physical design layout | |
| Input: Tar—coordinates of target wires | |
| Input: —FIB aspect ratio | |
| Input: —technology parameters | |
| Output: of the target wire | |
| Output: MEA, EA—MEA and EA of the target wire | |
| Output: —coordinates of the shield nets | |
| Output: —metal layer of the shield nets | |
| 1 | Load the physical design layout Layout |
| 2 | Input RFIB, Techpara, and Tar, and identify the dfaredge |
| 3 | Apply the of the target wire, and identify its MEA |
| 4 | |
| 5 | {, } = — |
3.4. LP-Based Reroute Attack Effort Estimation
| Algorithm 2: Hybrid optimization in estimating reroute paths. |
 |
3.4.1. Independent Scenarios
- Stage 1: Initialization and processing (lines 1–9):
- Stage 2: Added trace length formulation and constraints (lines 7–21):
- Stage 3: Hybrid optimization for reroute attack efforts’ estimation (lines 22, 29, 30):
- The first set of constraints enforces that a certain distance between each segment of the added traces in the layout must be maintained to ensure the signals extracted from the target nets to be reliable, which are expressed asHere, we include the distance requirements between vias, between vias and metal wires, and between wires, to avoid consequences such as the short of the signals.
- The next constraint enforces that no traces cross in the same layer and is incorporated for the same reason as the first constraint. It can be stated as
- To avoid affecting the normal signal transmission of shield wires, a minimum space will be reserved between traces and the probing area of the target net, expressed as
3.4.2. Dependent Scenarios
4. Experimental Results
4.1. Experimental Setup
4.2. Evaluation
4.2.1. Independent Scenarios
- Design 1: the original CEP physical layout without any dedicated protection (shield nets) against probing or reroute attacks. Security resilience depends on non-shield obscuring nets.
- Design 2: the CEP physical layout with a one-layer single shield at the M6 layer.
- Design 3: the CEP physical layout with a two-layer orthogonal shield at the M6 and M7 layers.
- Design 4: the CEP physical layout with a two-layer parallel shield at the M6 and M8 layers.
4.2.2. Dependent Scenarios
4.2.3. Time and Gas Consumption
5. Discussion
5.1. Hybrid Model in Detour-RS vs. Linear Programming in Detour [15]
- ;
- ;
- ;
- ;
- ;
- ;
- ;
- ;
- ;
- .
5.2. Discussion of Metrics
- Exposed area: Exposed area refers to the exploitable space of a target wire for a micro-probing adversary. In other words, given the FIB configuration and precision, adversaries can place their probing points in the exposed area to access the target wire without cutting off any shield wires. Figure 5 illustrates the determination of the exposed area for the given target wire and covering metal wires, which are capable of providing protection to the milling exclusion area on the target wire. An adversary will tend to target the target wires with a larger exposed area since it implies easier reroute attacks. Therefore, in our framework, the exposed area is used to identify the target wire with the protected covering wires, where a reroute attack would be performed.
- Layout-aware added traces’ length: This metric refers to the length of metal traces added by the reroute attack adversaries, which are necessary for a successful reroute attack. The greater the length of the layout-aware added traces, the higher the resource cost for attackers to perform a reroute attack is. Therefore, the metric itself and its variants (e.g., layout-aware added vias and layout-aware added traces) can effectively quantify the adversarial efforts of reroute attacks. For example, we comprehensively assess the vulnerabilities of reroute attacks in Table 4 given different scenarios, designs, and sets of target wires using the metric.
- Time and gas consumption: When it comes to practical microprobing reroute attacks, the time and gas consumption of FIB are very important by reflecting the efficiency and cost of adversaries. The duration of the attack directly impacts its cost and feasibility. FIB systems are expensive to operate, with costs often billed by the hour. Therefore, an attack that takes less time is more cost-effective. Additionally, the availability of the FIB equipment might be limited, making time efficiency crucial. As for gas consumption, FIB systems use various gases for processes such as etching or deposition. The amount of gas consumed not only affects the operational cost, but also the feasibility of long operations. Efficient gas usage ensures that the attack can be sustained for the necessary duration without requiring excessive resources.
- Added traces’ length [14]: This metric was proposed to evaluate reroute attack difficulty on different shield structures based on the calculation of added traces’ length. It quantifies the cost to mill a fixed-size area on a shielded design by reroute attacks for different shield structures. However, the added traces’ length metric is limited by its focus on fixed shield structures and theoretical cost calculations, which rely on the ideal positioning of shield nets within the design layout. In practice, routing conditions often fluctuate, resulting in suboptimal routing of shield nets due to factors such as congestion and restricted space within the protected area. In other words, the added traces’ length metric in [14] is more of a theoretical estimation instead of being aware of layout information. In contrast, the layout-aware added traces’ length metric in our Detour-RS framework provides a more accurate estimation by taking into account the specific design layout, rather than depending on the overly optimistic assumptions associated with fixed shield structures.
- Target score [31]: This metric was used to quantify the likelihood of a net being targeted in a probing attack. The higher the target score is, the more sensitive information that the nets will carry. It can be used to identify the target nets and the shield nets that will provide protection. However, as the focus of our Detour-RS is vulnerability assessment, we do not need the target score metric at this stage, since it is designed for optimal countermeasure deployment.
- Shield security [31]: This metric was proposed to identify the optimal metal layer where the shield and target nets will be routed, which will vary with different technology and FIB parameters. It will assist in providing the maximum protection to the target nets. Similar to the target score, shield security is also a countermeasure-oriented metric that could be utilized at the subsequent protection stage instead of the vulnerability assessment phase of our Detour-RS.
5.3. Scalability Evaluation of Detour-RS
6. Conclusions and Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Volya, D.; Zhang, T.; Alam, N.; Tehranipoor, M.; Mishra, P. Towards Secure Classical-Quantum Systems. In Proceedings of the 2023 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 1–4 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 283–292. [Google Scholar]
- Zhang, T.; Park, J.; Tehranipoor, M.; Farahmandi, F. PSC-TG: RTL power side-channel leakage assessment with test pattern generation. In Proceedings of the 2021 58th ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 5–9 December 2021; IEEE: Piscataway, NJ, USA, 2021; pp. 709–714. [Google Scholar]
- Zhang, T.; Rahman, M.L.; Kamali, H.M.; Azar, K.Z.; Tehranipoor, M.; Farahmandi, F. FISHI: Fault Injection Detection in Secure Heterogeneous Integration via Power Noise Variation. In Proceedings of the 2023 IEEE 73rd Electronic Components and Technology Conference (ECTC), Orlando, FL, USA, 30 May–2 June 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 2188–2195. [Google Scholar]
- Tajik, S.; Lohrke, H.; Seifert, J.P.; Boit, C. On the power of optical contactless probing: Attacking bitstream encryption of FPGAs. In Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, Dallas, TX, USA, 30 October–3 November 2017; pp. 1661–1674. [Google Scholar]
- Zhang, T.; Tehranipoor, M.; Farahmandi, F. BitFREE: On Significant Speedup and Security Applications of FPGA Bitstream Format Reverse Engineering. In Proceedings of the 2023 IEEE European Test Symposium (ETS), Venezia, Italy, 22–26 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 1–6. [Google Scholar]
- Zhang, T.; Wang, J.; Guo, S.; Chen, Z. A comprehensive FPGA reverse engineering tool-chain: From bitstream to RTL code. IEEE Access 2019, 7, 38379–38389. [Google Scholar] [CrossRef]
- Gao, M.; Forte, D. iPROBE-O: FIB-aware Place and Route for Probing Protection Using Orthogonal Shields. In Proceedings of the 2022 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Singapore, 14–16 December 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Gao, M.; Rahman, M.S.; Varshney, N.; Tehranipoor, M.; Forte, D. iPROBE: Internal Shielding Approach for Protecting Against Front-side and Back-side Probing Attacks. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2023, 42, 4541–4554. [Google Scholar] [CrossRef]
- Helfmeier, C.; Boit, C.; Nedospasov, D.; Seifert, J.P. Cloning Physically Unclonable Functions. In Proceedings of the 2013 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, TX, USA, 2–3 June 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Ray, V. Freud applications of fib: Invasive fib attacks and countermeasures in hardware security devices. In Proceedings of the East-Coast Focused Ion Beam User Group Meeting, Washington, DC, USA, 23 February 2009. [Google Scholar]
- Cioranesco, J.M.; Danger, J.L.; Graba, T.; Guilley, S.; Mathieu, Y.; Naccache, D.; Ngo, X.T. Cryptographically secure shields. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 25–31. [Google Scholar]
- Ling, M.; Wu, L.; Li, X.; Zhang, X.; Hou, J.; Wang, Y. Design of monitor and protect circuits against FIB attack on chip security. In Proceedings of the 2012 Eighth International Conference on Computational Intelligence and Security, Guangzhou, China, 17–18 November 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 530–533. [Google Scholar]
- Manich, S.; Wamser, M.S.; Sigl, G. Detection of probing attempts in secure ICs. In Proceedings of the 2012 IEEE International Symposium on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 3–4 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 134–139. [Google Scholar]
- Wang, H.; Shi, Q.; Forte, D.; Tehranipoor, M.M. Probing Assessment Framework and Evaluation of Antiprobing Solutions. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2019, 27, 1239–1252. [Google Scholar] [CrossRef]
- Gao, M.; Forte, D. Detour: Layout-aware Reroute Attack Vulnerability Assessment and Analysis. In Proceedings of the 2023 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 1–4 May 2023; IEEE: Piscataway, NJ, USA, 2023; pp. 122–132. [Google Scholar]
- Wu, H.; Stern, L.; Xia, D.; Ferranti, D.; Thompson, B.; Klein, K.; Gonzalez, C.; Rack, P. Focused helium ion beam deposited low resistivity cobalt metal lines with 10 nm resolution: Implications for advanced circuit editing. J. Mater. Sci. Mater. Electron. 2014, 25, 587–595. [Google Scholar] [CrossRef]
- Sidorkin, V.; van Veldhoven, E.; van der Drift, E.; Alkemade, P.; Salemink, H.; Maas, D. Sub-10-nm nanolithography with a scanning helium beam. J. Vac. Sci. Technol. Microelectron. Nanometer Struct. Process. Meas. Phenom. 2009, 27, L18–L20. [Google Scholar] [CrossRef]
- Boit, C.; Helfmeier, C.; Kerst, U. Security risks posed by modern IC debug and diagnosis tools. In Proceedings of the 2013 Workshop on Fault Diagnosis and Tolerance in Cryptography, Los Alamitos, CA, USA, 20 August 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 3–11. [Google Scholar]
- Shi, Q.; Asadizanjani, N.; Forte, D.; Tehranipoor, M.M. A layout-driven framework to assess vulnerability of ICs to microprobing attacks. In Proceedings of the 2016 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), McLean, VA, USA, 3–5 May 2016; pp. 155–160. [Google Scholar] [CrossRef]
- Immler, V.; Obermaier, J.; Ng, K.K.; Ke, F.X.; Lee, J.; Lim, Y.P.; Oh, W.K.; Wee, K.H.; Sigl, G. Secure physical enclosures from covers with tamper-resistance. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2019, 2019, 51–96. [Google Scholar] [CrossRef]
- Isaacs, P.; Morris, T., Jr.; Fisher, M.J.; Cuthbert, K. Tamper proof, tamper evident encryption technology. In Proceedings of the Pan Pacific Symposium, Maui, HI, USA, 22–24 January 2013. [Google Scholar]
- Trippel, T.; Shin, K.G.; Bush, K.B.; Hicks, M. T-TER: Defeating A2 Trojans with Targeted Tamper-Evident Routing. In Proceedings of the Proceedings of the 2023 ACM Asia Conference on Computer and Communications Security, Melbourne, Australia, 10–14 July 2023; pp. 746–759. [Google Scholar]
- Skorobogatov, S. Physical attacks and tamper resistance. In Introduction to Hardware Security and Trust; Springer: Berlin/Heidelberg, Germany, 2011; pp. 143–173. [Google Scholar]
- Wilton, S.J.; Kafafi, N.; Wu, J.C.; Bozman, K.A.; Aken’Ova, V.O.; Saleh, R. Design considerations for soft embedded programmable logic cores. IEEE J. Solid-State Circuits 2005, 40, 485–497. [Google Scholar] [CrossRef]
- Schulze, T.E.; Kwiat, K.; Kamhoua, C.; Chang, S.C.; Shi, Y. RECORD: Temporarily randomized encoding of combinational logic for resistance to data leakage from hardware trojan. In Proceedings of the 2016 IEEE Asian Hardware-Oriented Security and Trust (AsianHOST), Yilan, Taiwan, 19–20 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Schulze, T.E.; Beetner, D.G.; Shi, Y.; Kwiat, K.A.; Kamhoua, C.A. Combating data leakage trojans in commercial and ASIC applications with time-division multiplexing and random encoding. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2018, 26, 2007–2015. [Google Scholar] [CrossRef]
- Ho, W.G.; Chong, K.S.; Kim, T.T.H.; Gwee, B.H. A secure data-toggling SRAM for confidential data protection. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66, 4186–4199. [Google Scholar] [CrossRef]
- Pathak, S.K.; Nirmala Devi, M. Preventing Data Leakage by Trojans in Commercial and ASIC Applications Using TDM and DES Encryption and Decryption. In Proceedings of the International Conference on Signal Processing and Integrated Networks, Noida, India, 25–26 August 2022; Springer: Berlin/Heidelberg, Germany, 2022; pp. 95–110. [Google Scholar]
- Ray, S.; Jin, Y. Security policy enforcement in modern SoC designs. In Proceedings of the 2015 IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Austin, TX, USA, 2–6 November 2015; pp. 345–350. [Google Scholar] [CrossRef]
- Backer, J.; Hely, D.; Karri, R. Secure and flexible trace-based debugging of systems-on-chip. ACM Trans. Des. Autom. Electron. Syst. (TODAES) 2016, 22, 31. [Google Scholar] [CrossRef]
- Wang, H.; Shi, Q.; Nahiyan, A.; Forte, D.; Tehranipoor, M.M. A Physical Design Flow Against Front-Side Probing Attacks by Internal Shielding. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2020, 39, 2152–2165. [Google Scholar] [CrossRef]
- Zhang, T.; Rahman, F.; Tehranipoor, M.; Farahmandi, F. Fpga-chain: Enabling holistic protection of fpga supply chain with blockchain technology. IEEE Des. Test 2022, 40, 127–136. [Google Scholar] [CrossRef]
- Common Evaluation Platform v4.2. Available online: https://github.com/mit-ll/CEP (accessed on 14 January 2023).
- Wang, J.; Guo, S.; Chen, Z.; Zhang, T. A benchmark suite of hardware trojans for on-chip networks. IEEE Access 2019, 7, 102002–102009. [Google Scholar] [CrossRef]
- Zhang, T.; Rahman, M.L.; Kamali, H.M.; Azar, K.Z.; Farahmandi, F. SiPGuard: Run-Time System-in-Package Security Monitoring via Power Noise Variation. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2023, 32, 305–318. [Google Scholar] [CrossRef]



















| Wire Name | Path_15_18553 | Path_15_18554 | Path_15_18557 |
|---|---|---|---|
| Exposed Area (μm2) | 10.086 | 0 | 12.722 |
| Ratio | 49% | 0 | 40% |
| Notation | Definition |
|---|---|
| Distance between vias and probing area | |
| Distance between vias | |
| Distance between traces and probing area | |
| Distance between traces |
| No. | Shield Type | Description |
|---|---|---|
| 1 | Original Design (No Shield) | Conventional physical design |
| 2 | One-Layer Single Shield | Shield on M6 |
| 3 | Two-Layer Orthogonal Shield | Shield on M6 and M7 |
| 4 | Two-Layer Parallel Shield | Shield on M6 and M8 |
| Scenarios | Design No. | AES Enc. Key | Data Bus | Obf. Key | AES-Sensitive Signals | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Vias | Traces | Length (mm) | Vias | Traces | Length (mm) | Vias | Traces | Length (mm) | Vias | Traces | Length (mm) | ||
| Wang et al. [14] | 2 | 494 | 247 | 93 | 2140 | 1070 | 1739 | 594 | 297 | 134 | N/A | N/A | N/A |
| 3 | 990 | 495 | 279 | 4280 | 2140 | 5217 | 1190 | 595 | 403 | N/A | N/A | N/A | |
| 4 | 744 | 372 | 233 | 3210 | 1605 | 4347 | 894 | 447 | 337 | N/A | N/A | N/A | |
| No shield nets [15] | 1 | 374 | 169 | 122 | 1726 | 997 | 1798 | 567 | 266 | 135 | N/A | N/A | N/A |
| Only shield nets [15] | 2 | 427 (−13.6%) | 208 (−15.8%) | 84 (−9.7%) | 2167 (+1.3%) | 998 (−6.7%) | 1679 (−3.4%) | 580 (−2.4%) | 279 (−6.1%) | 127 (−5.2%) | N/A | N/A | N/A |
| 3 | 921 (−7.0%) | 536 (+8.2%) | 264 (−5.4%) | 4150 (−3.0%) | 2042 (−4.6%) | 5170 (−0.9%) | 1220 (+2.5%) | 570 (−4.2%) | 399 (−1.0%) | N/A | N/A | N/A | |
| 4 | 699 (−6.0%) | 331 (−11.0%) | 232 (−0.4%) | 3147 (−2.0%) | 1489 (−7.2%) | 4279 (−1.6%) | 869 (−2.8%) | 466 (+4.3%) | 310 (−8.0%) | N/A | N/A | N/A | |
| Shield nets + Other nets [15] | 2 | 556 (+12.55%) | 316 (+27.9%) | 160 (+72.4%) | 2777 (−29.8%) | 1221 (+14.1%) | 2299 (+32.2%) | 652 (+9.8%) | 316 (+6.4%) | 182 (+35.8%) | N/A | N/A | N/A |
| 3 | 1048 (+5.9%) | 699 (+41.2%) | 379 (+35.8%) | 4980 (+16.3%) | 2556 (+19.5%) | 5797 (+11.1%) | 1466 (+23.2%) | 676 (+13.6%) | 527 (+30.8%) | N/A | N/A | N/A | |
| 4 | 866 (+16.4%) | 456 (+22.6%) | 352 (+51.1%) | 3971 (+23.7%) | 2020 (+25.9%) | 4929 (+13.4%) | 1010 (+13.0%) | 592 (+32.4%) | 420 (+24.6%) | N/A | N/A | N/A | |
| No shield nets | 1 | 380 | 190 | 122 | 2002 | 1001 | 1800 | 490 | 245 | 134 | 886 | 443 | 531 |
| Only shield nets | 2 | 440 (−10.9%) | 220 (−10.9%) | 140 (+50.5%) | 1688 (−21.2%) | 844 (−21.2%) | 1769 (−1.7%) | 416 (−30.0%) | 208 (−30.0%) | 144 (+7.5%) | 1042 | 521 | 792 |
| 3 | 980 (−1.0%) | 490 (−1.0%) | 321 (+15.0%) | 3976 (−7.1%) | 1988 (−7.1%) | 4162 (−20.2%) | 1048 (−11.9%) | 524 (−11.9%) | 391 (−3.0%) | 2478 | 1239 | 1562 | |
| 4 | 760 (+2.2%) | 380 (+2.2%) | 299 (+28.3%) | 3242 (+0.9%) | 1621 (+0.9%) | 3569 (−17.9%) | 960 (+7.4%) | 480 (+7.4%) | 335 (−0.6%) | 1958 | 979 | 1119 | |
| Shield nets + Other nets | 2 | 640 (+30.0%) | 320 (+30.0%) | 158 (+70.0%) | 2398 (+12.1%) | 1199 (+12.1%) | 2160 (+24.2%) | 632 (+6.4%) | 316 (+6.4%) | 162 (+20.9%) | 1268 | 634 | 961 |
| 3 | 1232 (+24.5%) | 616 (+24.5%) | 355 (+27.2%) | 4770 (+11.45%) | 2385 (+11.45%) | 5653 (+8.4%) | 1300 (+9.2%) | 650 (+9.2%) | 478 (+18.6%) | 2972 | 1486 | 2190 | |
| 4 | 906 (+21.8%) | 453 (+21.8%) | 347 (+48.9%) | 3732 (+16.3%) | 1866 (+16.3%) | 4777 (+9.9%) | 1180 (+32.0%) | 590 (+39.2%) | 399 (+18.4%) | 2026 | 1013 | 1546 | |
| Algorithm | Scenario | Target Assets | |||
|---|---|---|---|---|---|
| Enc. Keys | Data Bus | Obf. Key | Total | ||
| Linear | Independent | 310 | 2670 | 390 | 3370 |
| Dependent | 774 | 8997 | 860 | 10,631 | |
| Hybrid | Independent | 344 | 3438 | 454 | 4236 |
| Dependent | 796 | 10,227 | 929 | 11,952 | |
| Enc. Key | Data Bus | Obf. Key | Average | |
|---|---|---|---|---|
| Time | 146 | 1012 | 222 | 0.189 |
| Gas | 960 | 8916 | 982 | 1.487 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Gao, M.; Biswas, L.K.; Asadi, N.; Forte, D. Detour-RS: Reroute Attack Vulnerability Assessment with Awareness of the Layout and Resource. Cryptography 2024, 8, 13. https://doi.org/10.3390/cryptography8020013
Gao M, Biswas LK, Asadi N, Forte D. Detour-RS: Reroute Attack Vulnerability Assessment with Awareness of the Layout and Resource. Cryptography. 2024; 8(2):13. https://doi.org/10.3390/cryptography8020013
Chicago/Turabian StyleGao, Minyan, Liton Kumar Biswas, Navid Asadi, and Domenic Forte. 2024. "Detour-RS: Reroute Attack Vulnerability Assessment with Awareness of the Layout and Resource" Cryptography 8, no. 2: 13. https://doi.org/10.3390/cryptography8020013
APA StyleGao, M., Biswas, L. K., Asadi, N., & Forte, D. (2024). Detour-RS: Reroute Attack Vulnerability Assessment with Awareness of the Layout and Resource. Cryptography, 8(2), 13. https://doi.org/10.3390/cryptography8020013







