Cryptographic Techniques in Artificial Intelligence Security: A Bibliometric Review
Abstract
1. Introduction
2. Materials and Methods
3. Results
4. Discussion
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Workman, M. Validation of a biases model in strategic security decision making. Inf. Manag. Comput. Secur. 2012, 20, 52–70. [Google Scholar] [CrossRef]
- Li, F. The research on information safety problem of digital campus network. In Proceedings of the 2011 2nd International Conference on Artificial Intelligence, Management Science and Electronic Commerce (AIMSEC), Dengfeng, China, 8–10 August 2011; pp. 828–831. [Google Scholar]
- Al Kuwaiti, A.; Nazer, K.; Al-Reedy, A.; Al-Shehri, S.; Al-Muhanna, A.; Subbarayalu, A.V.; Al Muhanna, D.; Al-Muhanna, F.A. A review of the role of artificial intelligence in healthcare. J. Pers. Med. 2023, 13, 951. [Google Scholar] [CrossRef] [PubMed]
- Parmar, M. Xaisec-Explainable AI Security: An Early Discussion Paper on New Multidisciplinary Subfield in Pursuit of Building Trust in Security of AI Systems. 2021. Available online: https://osf.io/preprints/osf/rc92f_v1 (accessed on 3 March 2025).
- Cintas-Canto, A.; Kaur, J.; Mozaffari-Kermani, M.; Azarderakhsh, R. ChatGPT vs. Lightweight security: First work implementing the NIST cryptographic standard ASCON. arXiv 2023, arXiv:2306.08178. [Google Scholar]
- Ganji, K.; Afshan, N. A bibliometric review of Internet of Things (IoT) on cybersecurity issues. J. Sci. Technol. Policy Manag. 2024. Available online: https://www.emerald.com/insight/content/doi/10.1108/jstpm-05-2023-0071/full/html (accessed on 3 March 2025). [CrossRef]
- Kumar, S.; Lim, W.M.; Sivarajah, U.; Kaur, J. Artificial intelligence and blockchain integration in business: Trends from a bibliometric-content analysis. Inf. Syst. Front. 2023, 25, 871–896. [Google Scholar] [CrossRef]
- Perifanis, N.-A.; Kitsios, F. Investigating the influence of artificial intelligence on business value in the digital era of strategy: A literature review. Information 2023, 14, 85. [Google Scholar] [CrossRef]
- Nasar, W.; Da Silva Torres, R.; Gundersen, O.E.; Karlsen, A.T. The use of decision support in search and rescue: A systematic literature review. ISPRS Int. J. Geo-Inf. 2023, 12, 182. [Google Scholar] [CrossRef]
- Liu, X.; Wang, X.; Chang, J.; Zhang, H.; Cao, P. Landscape analysis and overview of the literature on oxidative stress and pulmonary diseases. Front. Pharmacol. 2023, 14, 1190817. [Google Scholar] [CrossRef]
- Gauffriau, M. Counting methods introduced into the bibliometric research literature 1970–2018: A review. Quant. Sci. Stud. 2021, 2, 932–975. [Google Scholar] [CrossRef]
- Jiang, W.; Sousa, P.S.; Moreira, M.R.; Amaro, G.M. Lean direction in literature: A bibliometric approach. Prod. Manuf. Res. 2021, 9, 241–263. [Google Scholar] [CrossRef]
- Donthu, N.; Kumar, S.; Mukherjee, D.; Pandey, N.; Lim, W.M. How to conduct a bibliometric analysis: An overview and guidelines. J. Bus. Res. 2021, 133, 285–296. [Google Scholar] [CrossRef]
- Bunjak, A.; Černe, M.; Schölly, E.L. Exploring the past, present, and future of the mindfulness field: A multitechnique bibliometric review. Front. Psychol. 2022, 13, 792599. [Google Scholar] [CrossRef] [PubMed]
- Fang, X.; Ren, H.; Gu, M. Orbital angular momentum holography for high-security encryption. Nat. Photonics 2020, 14, 102–108. [Google Scholar] [CrossRef]
- Taylor, P.J.; Dargahi, T.; Dehghantanha, A.; Parizi, R.M.; Choo, K.K.R. A systematic literature review of blockchain cyber security. Digit. Commun. Netw. 2020, 6, 147–156. [Google Scholar] [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutor. 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Khan, L.U.; Yaqoob, I.; Imran, M.; Han, Z.; Hong, C.S. 6G Wireless Systems: A Vision, Architectural Elements, and Future Directions. IEEE Access 2020, 8, 147029–147044. [Google Scholar] [CrossRef]
- Sharma, A.; Vanjani, P.; Paliwal, N.; Basnayaka, C.M.W.; Jayakody, D.N.K.; Wang, H.C.; Muthuchidambaranathan, P. Communication and networking technologies for UAVs: A survey. J. Netw. Comput. Appl. 2020, 168, 102739. [Google Scholar] [CrossRef]
- Anuradha, M.; Jayasankar, T.; Prakash, N.B.; Sikkandar, M.Y.; Hemalakshmi, G.R.; Bharatiraja, C.; Britto, A.S.F. IoT enabled cancer prediction system to enhance the authentication and security using cloud computing. Microprocess. Microsyst. 2021, 80, 103301. [Google Scholar] [CrossRef]
- Zaman, S.; Alhazmi, K.; Aseeri, M.A.; Ahmed, M.R.; Khan, R.T.; Kaiser, M.S.; Mahmud, M. Security Threats and Artificial Intelligence Based Countermeasures for Internet of Things Networks: A Comprehensive Survey. IEEE Access 2021, 9, 94668–94690. [Google Scholar] [CrossRef]
- Li, B.; Feng, Y.; Xiong, Z.; Yang, W.; Liu, G. Research on AI security enhanced encryption algorithm of autonomous IoT systems. Inf. Sci. 2021, 575, 379–398. [Google Scholar] [CrossRef]
- Sharma, P.; Jain, S.; Gupta, S.; Chamola, V. Role of machine learning and deep learning in securing 5G-driven industrial IoT applications. Ad Hoc Netw. 2021, 123, 102685. [Google Scholar] [CrossRef]
- Jan, M.A.; Khan, F.; Khan, R.; Mastorakis, S.; Menon, V.G.; Alazab, M.; Watters, P. Lightweight Mutual Authentication and Privacy-Preservation Scheme for Intelligent Wearable Devices in Industrial-CPS. IEEE Trans. Ind. Inform. 2021, 17, 5829–5839. [Google Scholar] [CrossRef]
- Razdan, S.; Sharma, S. Internet of Medical Things (IoMT): Overview, Emerging Technologies, and Case Studies. IETE Tech. Rev. (Inst. Electron. Telecommun. Eng. India) 2022, 39, 775–788. [Google Scholar] [CrossRef]
- Hasan, M.K.; Ghazal, T.M.; Saeed, R.A.; Pandey, B.; Gohel, H.; Eshmawi, A.A.; Abdel-Khalek, S.; Alkhassawneh, H.M. A review on security threats, vulnerabilities, and counter measures of 5G enabled Internet-of-Medical-Things. IET Commun. 2022, 16, 421–432. [Google Scholar] [CrossRef]
- Almaiah, M.A.; Hajjej, F.; Ali, A.; Pasha, M.F.; Almomani, O. An AI-Enabled Hybrid Lightweight Authentication Model for Digital Healthcare Using Industrial Internet of Things Cyber-Physical Systems. Sensors 2022, 22, 1448. [Google Scholar] [CrossRef]
- Abdel Hakeem, S.A.; Hussein, H.H.; Kim, H. Security Requirements and Challenges of 6G Technologies and Applications. Sensors 2022, 22, 1969. [Google Scholar] [CrossRef] [PubMed]
- Neelakandan, S.; Rene Beulah, J.; Prathiba, L.; Murthy, G.L.N.; Fantin Irudaya Raj, E.; Arulkumar, N. Blockchain with deep learning-enabled secure healthcare data transmission and diagnostic model. Int. J. Model. Simul. Sci. Comput. 2022, 13, 2241006. [Google Scholar] [CrossRef]
- Rajapaksha, S.; Kalutarage, H.; Al-Kadri, M.O.; Petrovski, A.; Madzudzo, G.; Cheah, M. AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey. ACM Comput. Surv. 2023, 55, 1–40. [Google Scholar] [CrossRef]
- Boualouache, A.; Engel, T. A Survey on Machine Learning-Based Misbehavior Detection Systems for 5G and Beyond Vehicular Networks. IEEE Commun. Surv. Tutor. 2023, 25, 1128–1172. [Google Scholar] [CrossRef]
- Friha, O.; Ferrag, M.A.; Benbouzid, M.; Berghout, T.; Kantarci, B.; Choo, K.K.R. 2DF-IDS: Decentralized and differentially private federated learning-based intrusion detection system for industrial IoT. Comput. Secur. 2023, 127, 103097. [Google Scholar] [CrossRef]
- Deebak, B.D.; Memon, F.H.; Khowaja, S.A.; Dev, K.; Wang, W.; Qureshi, N.M.F.; Su, C. A Lightweight Blockchain-Based Remote Mutual Authentication for AI-Empowered IoT Sustainable Computing Systems. IEEE Internet Things J. 2023, 10, 6652–6660. [Google Scholar] [CrossRef]
- Ein Shoka, A.A.; Dessouky, M.M.; El-Sayed, A.; El-Din Hemdan, E. An efficient CNN based epileptic seizures detection framework using encrypted EEG signals for secure telemedicine applications. Alex. Eng. J. 2023, 65, 399–412. [Google Scholar] [CrossRef]
- Almalawi, A.; Khan, A.I.; Alsolami, F.; Abushark, Y.B.; Alfakeeh, A.S. Managing Security of Healthcare Data for a Modern Healthcare System. Sensors 2023, 23, 3612. [Google Scholar] [CrossRef] [PubMed]
- Dhar Dwivedi, A.; Singh, R.; Kaushik, K.; Rao Mukkamala, R.; Alnumay, W.S. Blockchain and artificial intelligence for 5G-enabled Internet of Things: Challenges, opportunities, and solutions. Trans. Emerg. Telecommun. Technol. 2024, 35, e4329. [Google Scholar] [CrossRef]
- Gill, S.S. Quantum and blockchain based Serverless edge computing: A vision, model, new trends and future directions. Internet Technol. Lett. 2024, 7, e275. [Google Scholar] [CrossRef]
- Alqaralleh, B.A.Y.; Vaiyapuri, T.; Parvathy, V.S.; Gupta, D.; Khanna, A.; Shankar, K. Blockchain-assisted secure image transmission and diagnosis model on Internet of Medical Things Environment. Pers. Ubiquitous Comput. 2024, 28, 17–27. [Google Scholar] [CrossRef]
- Pleshakova, E.; Osipov, A.; Gataullin, S.; Gataullin, T.; Vasilakos, A. Next gen cybersecurity paradigm towards artificial general intelligence: Russian market challenges and future global technological trends. J. Comput. Virol. Hacking Tech. 2024, 20, 429–440. [Google Scholar] [CrossRef]
- Fang, W.; Zhu, C.; Zhang, W. Toward Secure and Lightweight Data Transmission for Cloud-Edge-Terminal Collaboration in Artificial Intelligence of Things. IEEE Internet Things J. 2024, 11, 105–113. [Google Scholar] [CrossRef]
- Ishtaiwi, A.; Al Khaldy, M.A.; Al-Qerem, A.; Aldweesh, A.; Almomani, A. Artificial Intelligence in Cryptographic Evolution: Bridging the Future of Security. In Innovations in Modern Cryptography; IGI Global: Hershey, PA, USA, 2024; pp. 31–54. [Google Scholar]
- Radanliev, P. Artificial intelligence and quantum cryptography. J. Anal. Sci. Technol. 2024, 15, 4. [Google Scholar] [CrossRef]
- Sagar, R.; Jhaveri, R.; Borrego, C. Applications in security and evasions in machine learning: A survey. Electronics 2020, 9, 97. [Google Scholar] [CrossRef]
- Pramanik, S.; Ghosh, R.; Ghonge, M.M.; Narayan, V.; Sinha, M.; Pandey, D.; Samanta, D. A novel approach using steganography and cryptography in business intelligence. In Integration Challenges for Analytics, Business Intelligence, and Data Mining; IGI Global Scientific Publishing: Hershey, PA, USA, 2021; pp. 192–217. [Google Scholar]
- Dai, D.; Boroomand, S. A review of artificial intelligence to enhance the security of big data systems: State-of-art, methodologies, applications, and challenges. Arch. Comput. Methods Eng. 2022, 29, 1291–1309. [Google Scholar] [CrossRef]
- Al-Suqri, M.N.; Gillani, M. A comparative analysis of information and artificial intelligence toward national security. IEEE Access 2022, 10, 64420–64434. [Google Scholar] [CrossRef]
- Gulo, T.R.; Dwiastuti, I. The rising US trade protectionism under Donald Trump and its implication on China’s artificial intelligence advancement. AEGIS J. Int. Relat. 2022, 5. [Google Scholar] [CrossRef]
- Pise, A.A.; Almuzaini, K.K.; Ahanger, T.A.; Farouk, A.; Pant, K.; Pareek, P.K.; Nuagah, S.J. Enabling artificial intelligence of things (AIoT) healthcare architectures and listing security issues. Comput. Intell. Neurosci. 2022, 2022, 8421434. [Google Scholar] [CrossRef]
- Hegde, S.B.; Srivastav, S.; Ks, N.B. A Comparative study on state of art Cryptographic key distribution with quantum networks. In Proceedings of the 2022 IEEE 3rd Global Conference for Advancement in Technology (GCAT), Bangalore, India, 7–9 October 2022; pp. 1–7. [Google Scholar]
- Mao, B.; Kawamoto, Y.; Kato, N. AI-Based Joint Optimization of QoS and Security for 6G Energy Harvesting Internet of Things. IEEE Internet Things J. 2020, 7, 7032–7042. [Google Scholar] [CrossRef]
- Kim, A.; Park, M.; Lee, D.H. AI-IDS: Application of Deep Learning to Real-Time Web Intrusion Detection. IEEE Access 2020, 8, 70245–70261. [Google Scholar] [CrossRef]
- Yu, W.; Dillon, T.; Mostafa, F.; Rahayu, W.; Liu, Y. A global manufacturing big data ecosystem for fault detection in predictive maintenance. IEEE Trans. Ind. Inform. 2020, 16, 183–192. [Google Scholar] [CrossRef]
- Yusuf, S.O.; Echere, A.Z.; Ocran, G.; Abubakar, J.E.; Paul-Adeleye, A.H.; Owusu, P. Analyzing the efficiency of AI-powered encryption solutions in safeguarding financial data for SMBs. World J. Adv. Res. Rev. 2024, 23, 2138–2147. [Google Scholar] [CrossRef]
- Olasehinde, T. Real-Time Data Encryption and Decryption Using AI in Cloud Security. 2024. Available online: https://www.researchgate.net/publication/386178125_Real-Time_Data_Encryption_and_Decryption_Using_AI_in_Cloud_Security (accessed on 3 March 2025).
- Ojo, B.; Aghaunor, C.T. AI-driven cybersecurity solutions for real-time threat detection in critical infrastructure. Int. J. Sci. Res. Arch. 2024, 12, 1716–1726. [Google Scholar]
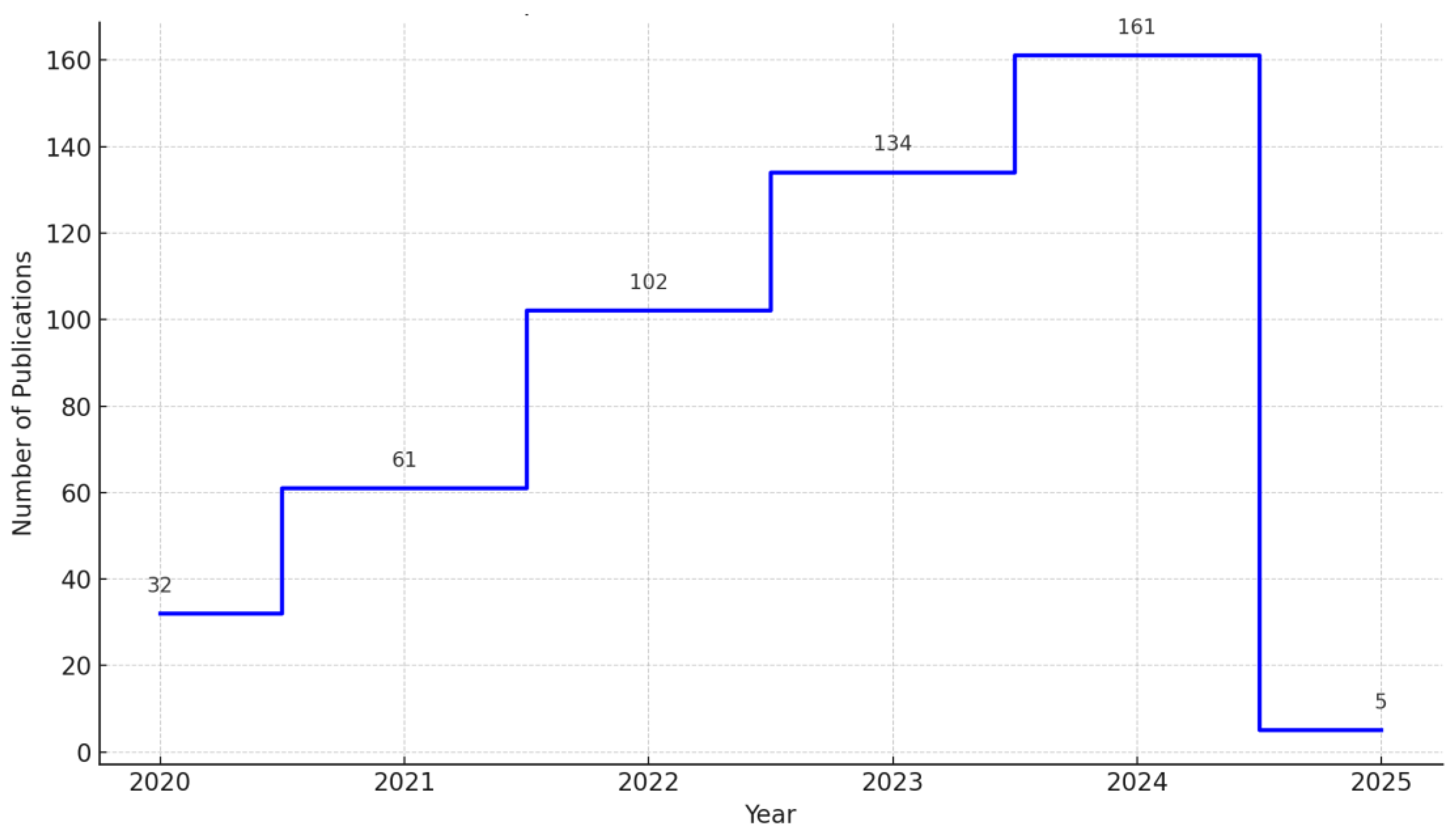
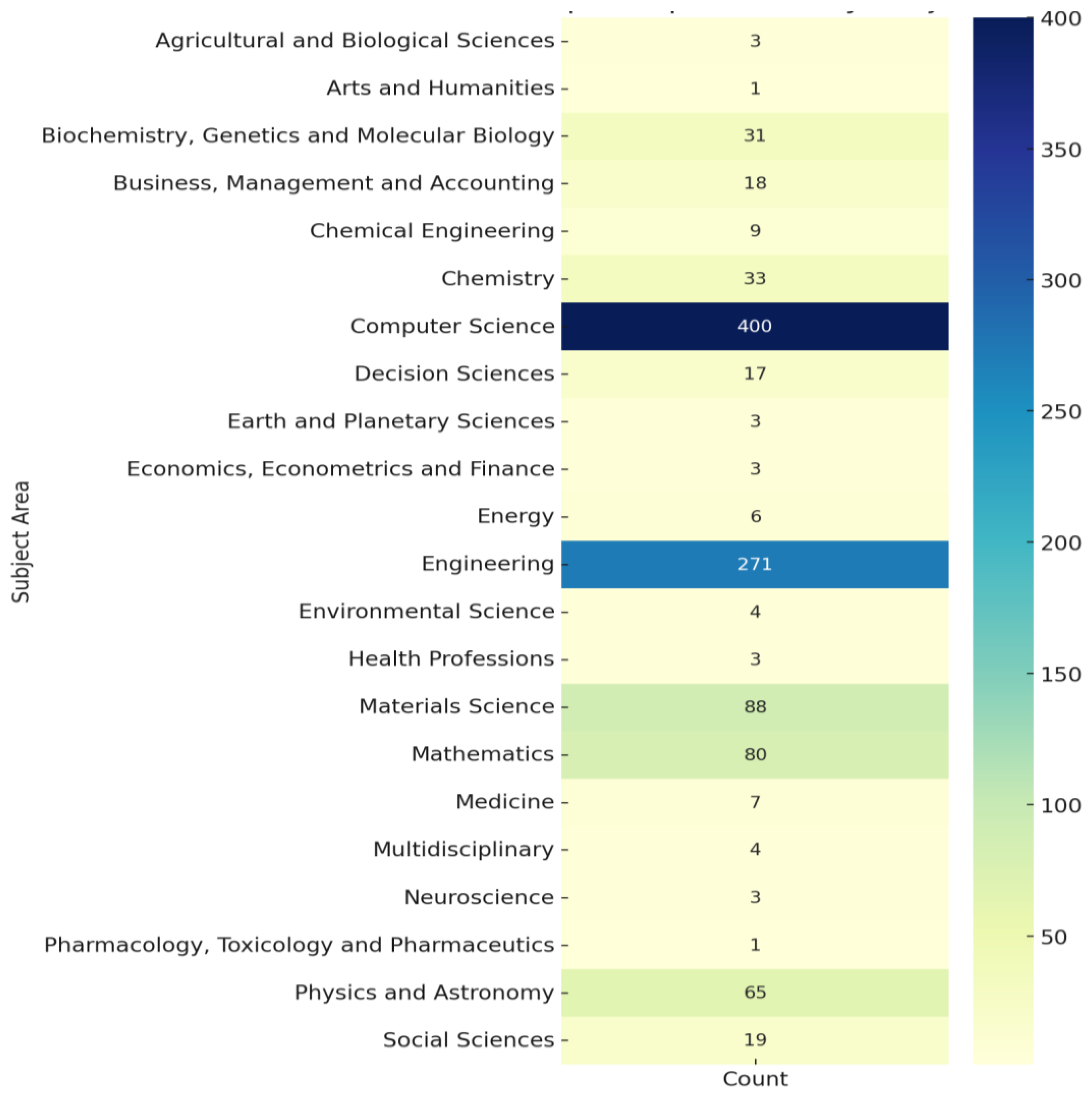
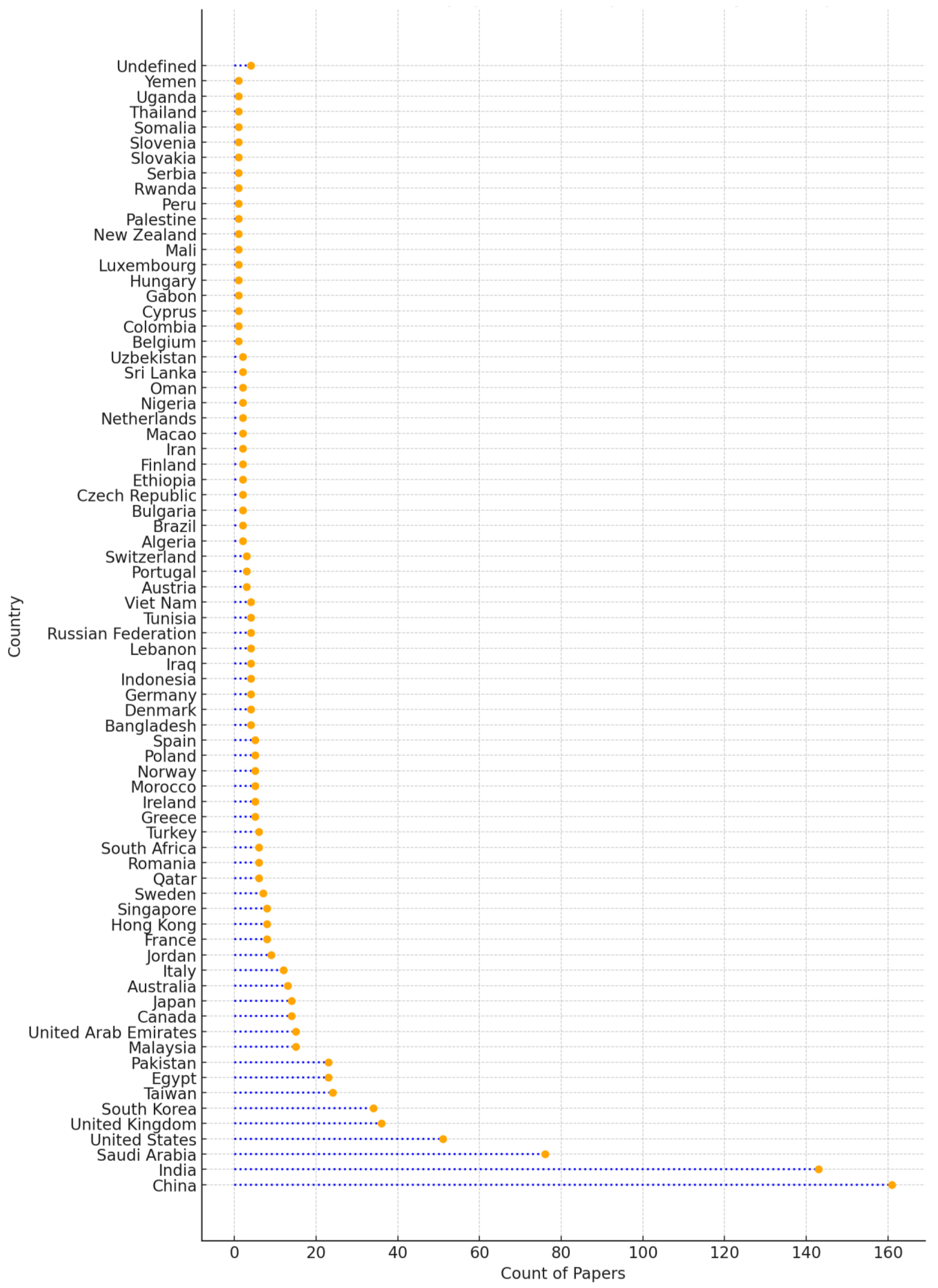
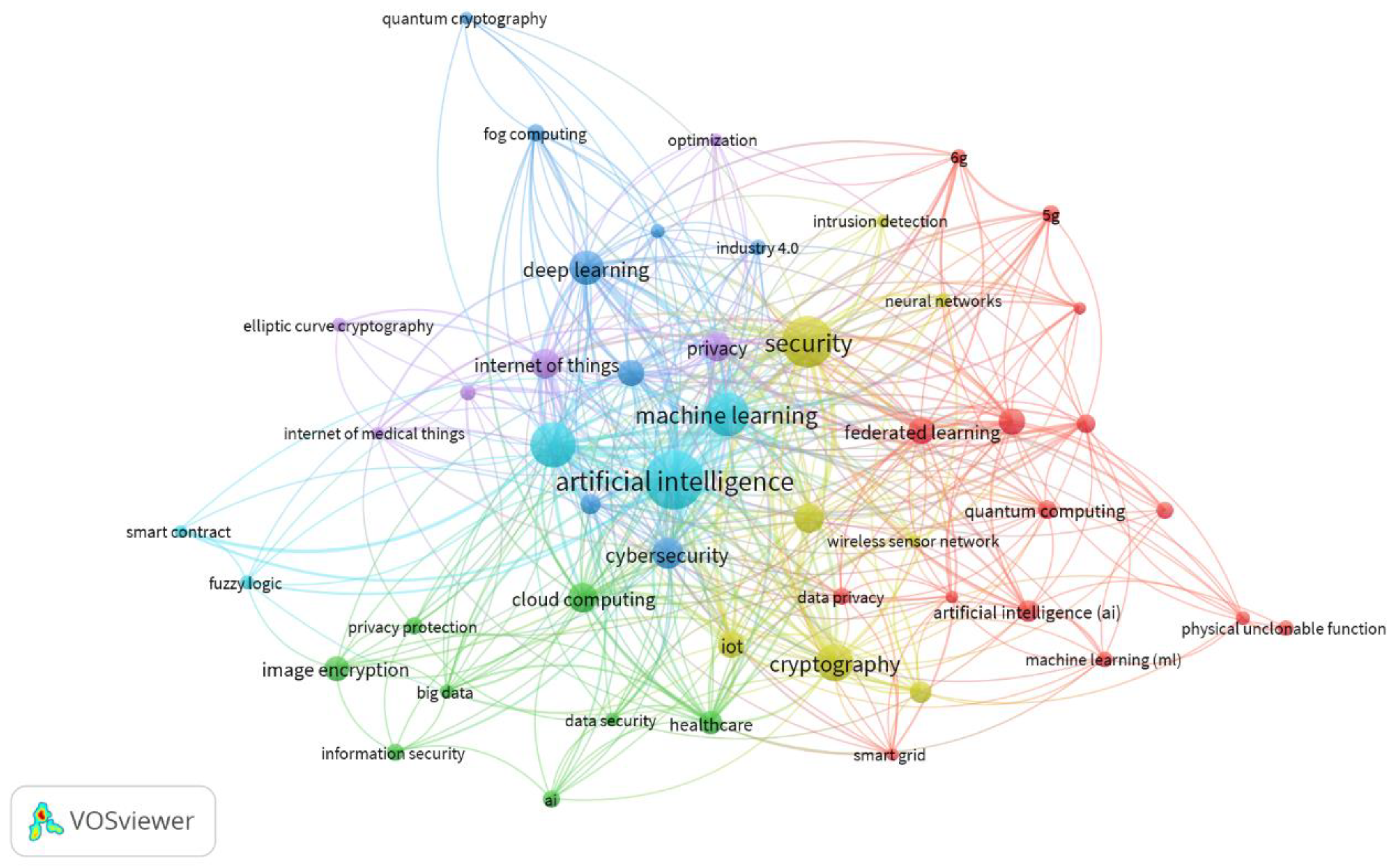
| Affiliation | Number of Publications |
|---|---|
| King Abdulaziz University | 13 |
| King Saud University | 12 |
| Taif University | 12 |
| Chinese Academy of Sciences | 10 |
| SRM Institute of Science and Technology | 9 |
| Prince Sattam Bin Abdulaziz University | 9 |
| Peng Cheng Laboratory | 9 |
| Beijing University of Posts and Telecommunications | 8 |
| University of Petroleum and Energy Studies | 8 |
| Ministry of Education of the People’s Republic of China | 7 |
| Vellore Institute of Technology | 7 |
| Nirma University | 7 |
| Author | Number of Publications |
|---|---|
| Das, A.K. | 7 |
| Tanwar, S. | 7 |
| Vijayakumar, P. | 6 |
| Jadav, N.K. | 5 |
| Alshehri, M.D. | 4 |
| Dev, K. | 4 |
| Gupta, D. | 4 |
| Gupta, R. | 4 |
| Kumar, N. | 4 |
| Shankar, K. | 4 |
| Veeravalli, B. | 4 |
| Wazid, M. | 4 |
| Journal | Number of Publications |
|---|---|
| IEEE Access | 47 |
| Sensors | 21 |
| IEEE Internet Of Things Journal | 14 |
| Wireless Personal Communications | 10 |
| Multimedia Tools and Applications | 8 |
| Security And Communication Networks | 8 |
| Computers Materials and Continua | 7 |
| IEEE Transactions on Information Forensics and Security | 7 |
| Wireless Communications and Mobile Computing | 7 |
| International Journal of Advanced Computer Science and Applications | 6 |
| Authors | Title | Year | Source Title | Cited by |
|---|---|---|---|---|
| Fang et al. [15] | Orbital angular momentum holography for high-security encryption | 2020 | Nature Photonics | 586 |
| Taylor et al. [16] | A systematic literature review of blockchain cyber security | 2020 | Digital Communications and Networks | 417 |
| Tange et al. [17] | A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities | 2020 | IEEE Communications Surveys and Tutorials | 302 |
| Khan et al. [18] | 6G Wireless Systems: A Vision, Architectural Elements, and Future Directions | 2020 | IEEE Access | 259 |
| Sharma et al. [19] | Communication and networking technologies for UAVs: A survey | 2020 | Journal of Network and Computer Applications | 229 |
| Anuradha et al. [20] | IoT enabled cancer prediction system to enhance the authentication and security using cloud computing | 2021 | Microprocessors and Microsystems | 112 |
| Zaman et al. [21] | Security Threats and Artificial Intelligence-Based Countermeasures for Internet of Things Networks: A Comprehensive Survey | 2021 | IEEE Access | 94 |
| Li et al. [22] | Research on AI security enhanced encryption algorithm of autonomous IoT systems | 2021 | Information Sciences | 83 |
| Sharma et al. [23] | Role of machine learning and deep learning in securing 5G-driven industrial IoT applications | 2021 | Ad Hoc Networks | 83 |
| Jan et al. [24] | Lightweight Mutual Authentication and Privacy-Preservation Scheme for Intelligent Wearable Devices in Industrial-CPS | 2021 | IEEE Transactions on Industrial Informatics | 81 |
| Razdan and Sharma [25] | Internet of Medical Things (IoMT): Overview, Emerging Technologies, and Case Studies | 2022 | IETE Technical Review (Institution of Electronics and Telecommunication Engineers, India) | 188 |
| Hasan et al. [26] | A review on security threats, vulnerabilities, and counter measures of 5G enabled Internet-of-Medical-Things | 2022 | IET Communications | 140 |
| Almaiah et al. [27] | An AI-Enabled Hybrid Lightweight Authentication Model for Digital Healthcare Using Industrial Internet of Things Cyber-Physical Systems | 2022 | Sensors | 109 |
| Abdel Hakeem et al. [28] | Security Requirements and Challenges of 6G Technologies and Applications | 2022 | Sensors | 102 |
| Neelakandan et al. [29] | Blockchain with deep learning-enabled secure healthcare data transmission and diagnostic model | 2022 | International Journal of Modeling, Simulation, and Scientific Computing | 75 |
| Rajapaksha et al. [30] | AI-Based Intrusion Detection Systems for In-Vehicle Networks: A Survey | 2023 | ACM Computing Surveys | 79 |
| Boualouache and Engel [31] | A Survey on Machine Learning-Based Misbehavior Detection Systems for 5G and Beyond Vehicular Networks | 2023 | IEEE Communications Surveys and Tutorials | 55 |
| Friha et al. [32] | 2DF-IDS: Decentralized and differentially private federated learning-based intrusion detection system for industrial IoT | 2023 | Computers and Security | 53 |
| Deebak et al. [33] | A Lightweight Blockchain-Based Remote Mutual Authentication for AI-Empowered IoT Sustainable Computing Systems | 2023 | IEEE Internet of Things Journal | 52 |
| Ein Shoka et al. [34] | An efficient CNN-based epileptic seizures detection framework using encrypted EEG signals for secure telemedicine applications | 2023 | Alexandria Engineering Journal | 48 |
| Almalawi et al. [35] | Managing Security of Healthcare Data for a Modern Healthcare System | 2023 | Sensors | 48 |
| Dhar Dwivedi et al. [36] | Blockchain and artificial intelligence for 5G-enabled Internet of Things: Challenges, opportunities, and solutions | 2024 | Transactions on Emerging Telecommunications Technologies | 61 |
| Gill [37] | Quantum and blockchain-based Serverless edge computing: A vision, model, new trends and future directions | 2024 | Internet Technology Letters | 41 |
| Alqaralleh et al. [38] | Blockchain-assisted secure image transmission and diagnosis model on Internet of Medical Things Environment | 2024 | Personal and Ubiquitous Computing | 30 |
| Pleshakova et al. [39] | Next gen cybersecurity paradigm towards artificial general intelligence: Russian market challenges and future global technological trends | 2024 | Journal of Computer Virology and Hacking Techniques | 19 |
| Fang et al. [40] | Toward Secure and Lightweight Data Transmission for Cloud-Edge-Terminal Collaboration in Artificial Intelligence of Things | 2024 | IEEE Internet of Things Journal | 19 |
| Study | Cryptographic Technique Used | Application Context | Key Findings |
|---|---|---|---|
| Pramanik et al. [44] | Steganography + Cryptography | Business intelligence security | Faster and more accurate than existing methods |
| Dai and Boroomand [45] | AI-Enhanced Security Models | Big Data security | Evaluated security threats and defense strategies |
| Al-Suqri and Gillani [46] | Cryptographic Security Models | National security | Emphasized AI’s role in mitigating cyber threats |
| Gulo et al. [47] | Cryptographic AI Protection | Economic and security contexts | Highlighted AI security risks in geopolitical trade wars |
| Pise et al. [48] | AIoT Cryptographic Protocols | Healthcare security | Addressed privacy and integrity concerns in AIoT healthcare |
| Hegde et al. [49] | Quantum Cryptography | Secure communication | Compared classic vs. quantum cryptographic techniques |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Taherdoost, H.; Le, T.-V.; Slimani, K. Cryptographic Techniques in Artificial Intelligence Security: A Bibliometric Review. Cryptography 2025, 9, 17. https://doi.org/10.3390/cryptography9010017
Taherdoost H, Le T-V, Slimani K. Cryptographic Techniques in Artificial Intelligence Security: A Bibliometric Review. Cryptography. 2025; 9(1):17. https://doi.org/10.3390/cryptography9010017
Chicago/Turabian StyleTaherdoost, Hamed, Tuan-Vinh Le, and Khadija Slimani. 2025. "Cryptographic Techniques in Artificial Intelligence Security: A Bibliometric Review" Cryptography 9, no. 1: 17. https://doi.org/10.3390/cryptography9010017
APA StyleTaherdoost, H., Le, T.-V., & Slimani, K. (2025). Cryptographic Techniques in Artificial Intelligence Security: A Bibliometric Review. Cryptography, 9(1), 17. https://doi.org/10.3390/cryptography9010017








