Exerting Qualitative Analytics and Blockchain Requirement-Engineering in Designing and Implementing a Luxury Products Authentication System
Abstract
:1. Introduction
- What are the important features of designing a digitized verification system for the authenticity verification of luxury accessories?
- What is the model representation for outlining the requirements of important features of blockchain applications for the verification of luxury accessories across their lifecycle?
- What are the architecture and relevant blockchain technologies for prototyping the requirements in the model representation of the proposed platform?
2. Materials and Methods
2.1. Related Literature Review
2.2. Blockchain Protocol Technologies
2.2.1. Decentralized Consensus
2.2.2. Decentralized Storage and Time Stamping
2.2.3. Public Key (PK) Infrastructure and Digital Signature
2.2.4. Smart Contracts and Tokenization
2.3. Research Method—Design Science Research
2.3.1. Qualitative Analytics
2.3.2. Blockchain Technologies and T-DM Methodology
2.3.3. Peer Debriefing Mapping of Requirements to Blockchain Technologies
2.4. Running Case
3. Results
3.1. Luxury Products Authentication and Associated Problems
3.1.1. Derived Process of Luxury Product Authentication
3.1.2. Problems in Luxury Product Authentications
- (a)
- Experts identified problems with luxury product authentications
- (b)
- Factors that cause problems in luxury product authentication
- (c) Additional derived problems from the AS-IS process of luxury authentication
- (d) Blockchain-based solution for luxury product authentication
3.2. Model Requirements of the LogisticsBDT Application
3.2.1. Stakeholders and Agents
3.2.2. Software Properties of the Designed Platform
3.2.3. Functional Requirements of the Proposed Platform
- (a)
- Register brand function: The platform verifies luxury brands that are allowed to mint luxury NFTs through a challenge and response system. The function provides brand details allows brands to provide their host address and email. With the function send encrypted random number, a random 2-byte token is sent to the address provided by the brand. The function add website to brand PK list links the wallet address of the user to the luxury brand on the condition that the user can provide the correct token sent. Hence, every luxury NFT minted by this user is linked to the brand host website.
- (b)
- Mint luxury NFT function: To mint a luxury NFT, the following functions are executed. The scan PID function allows the scanner to read the QR code (or RFID) information that contains the luxury product identification details (PID). The add metadata function enables the brand to provide information about the product such as name, color, image etc. The user signs the data with their wallet private key and sends it to the blockchain. On successful minting, the user is returned with the transaction details of the blockchain operation.
- (c)
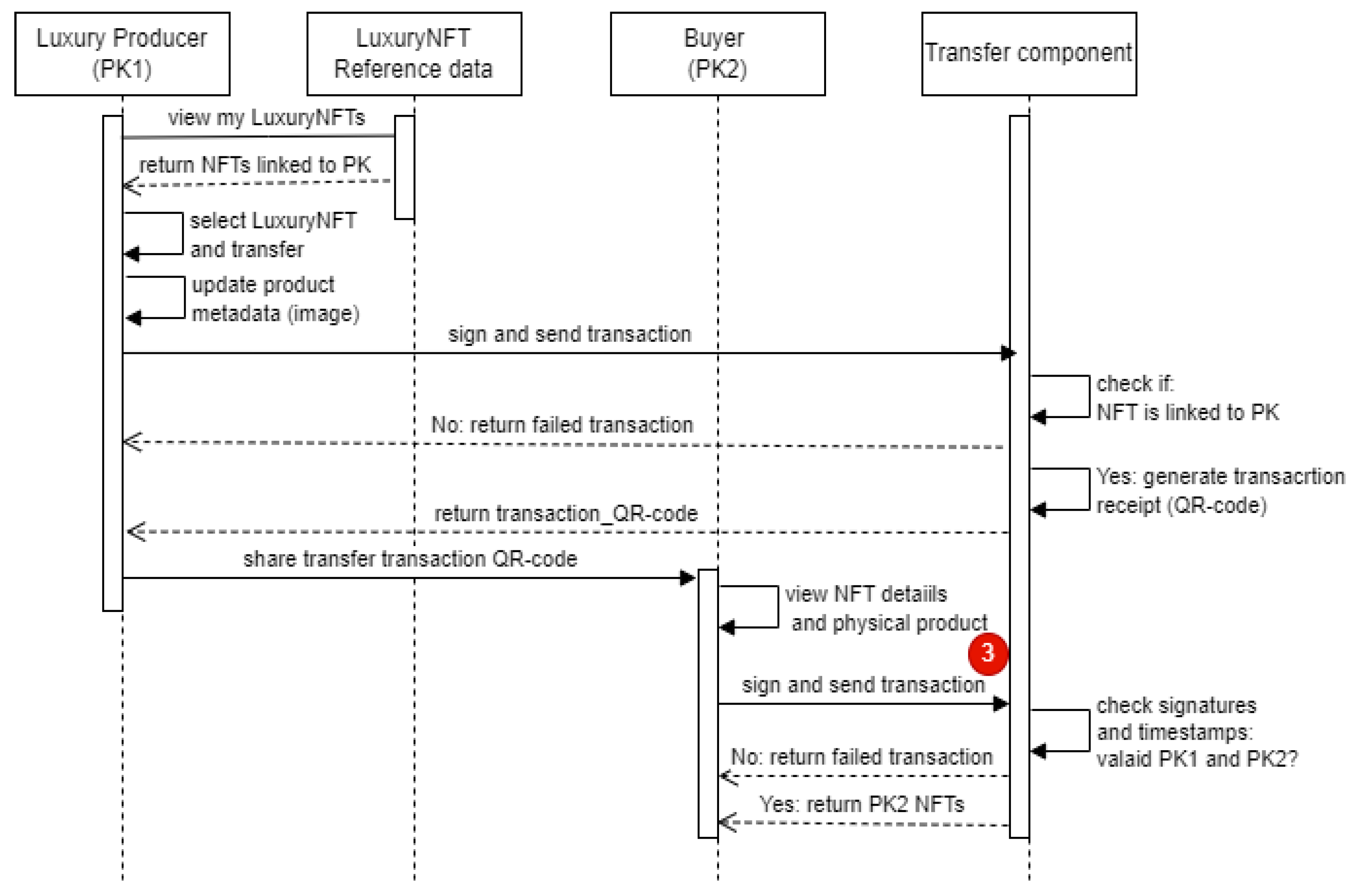
- Transfer ownership function: To transfer the ownership of an existing luxury product to a new owner, the following functions are performed. The scan/select function allows the system to collect the PID information of the product and first checks if the wallet address of the current owner matches the address of the user that initiated the transfer function. The add metadata function allows the current owner of a luxury product to update the metadata (image only), thereby providing a traceable history of physical changes in the product since when it was first minted as a luxury NFT. The data is then signed by the current owner. An automated agent generates a QR code that encodes the sign data. The scan QR code and decode data allow the new owner to decode the information contained in the signed data present in the QR code and then append his/her signature to the initially signed data. This makes a complete handshake, ensuring that two parties agree to complete a transfer operation of any given luxury accessories. The new owner submits the signed data to the blockchain. If the operation is successful, transaction details of the blockchain operation are returned to the new owner.
- (d)
- View luxury NFT function: Viewing the luxury NFT function allows users to see the historic ownership of a luxury product, timestamps, and public keys linked to them. The scan PID function enables the user to locate a PID linked to the product by scanning the product QR code, barcode, or RFID. The list of previous owners, their timestamps, and other related metadata describing the luxury NFT is returned to the user.
3.3. Blockchain Technologies for Implementing the Application Model
3.3.1. Architecture and Data Model of LogisticsBDT Platform
- (a)
- Brand registration component: Only a luxury brand represented as a producer and an automated software verification agent can interact with the brand registration component. The producer registers his brand details, while the software agent performs the challenge/response operation. The data generated from the brand registration is centrally stored in our database. In the future, we plan to decentralize the operation of brand registration using blockchain oracles and a configurable challenge–response system implemented in MFSSIA.
- (b)
- Minting component: The minting component of the application allows only verified luxury brands to mint a new luxury NFT. The PID scanner reads the product identification data from the physical product. The product input provides a form for adding metadata and
- (c)
- # an original image. The digital signature component allows the producer to assign a signature on the minted luxury NFT.
- (d)
- Transfer component: The transfer component of the application provides all users access to transferring their luxury NFTs to new owners. The product update component allows the inclusion of the current image of the luxury NFT. The PID scanner provides the reading capability of the product data, and the QR-encoder decoder provides the possibility of generating an intermediate asset that can be signed by the second party who is the new owner. The digital signature provides the signing functionality and the data generated is stored in a decentralized database with the timestamp and hash stored on a blockchain.
- (e)
- Viewer component: The viewer component of the application allows anyone with physical access to a luxury accessory already minted as an NFT to view the history of ownership of the product. The PID scanner reads the identification data, while the product details component presents the luxury NFT information to the user. To get the data, the PID read from the physical product is referenced in the data storage containing the transaction hash of the data on the blockchain. Searching the hash data on a blockchain returns the content identification details of the product metadata. This detailed information is then returned to the user showing the historical timestamps connected to the product.
3.3.2. Assessment of Selected Blockchain Technologies
- (a)
- Brand registration technology stack: Brand registration is proposed to be implemented using a simple HTML form and a software agent for challenge–response verification. The challenge–response verification provides a checking method for ensuring that a particular user is part of the organization represented by the brand host address. A simple JavaScript is proposed for generating the challenge and verifying the response from the user.
- (b)
- The minting technology stack: In the LogisticsBDT minting implementation, the PID scanner is proposed to first support QR codes and barcodes. Support for RFID-attached products will be added later. Product input for adding the metadata and original image of the product is implemented using a simple HTML form. The digital signature is proposed to be implemented on Polkadot technology (Polkadot scalable, interoperable and secure blockchain technology for web: https://polkadot.network/technology/ (accessed on 22 December 2022).
- (c)
- The transferring technology stack: In LogisticsBDT transfer, the product update is proposed to be implemented using an HTML form for uploading a new image. The multi-signature that simulates a secured handshake between buyer and seller for a digital signature is implemented with the Polkadot blockchain.
- (d)
- The viewer technology stack: For the LogisticsBDT Viewer, the PID scanner works only on QR codes and barcodes. The metadata containing product details of a luxury NFT is displayed as HTML.
- (e)
- On-chain components technology stack: The on-chain properties of the platform are proposed to be implemented on the Robonomics blockchain (Robonomics blockchain for physical internet: https://robonomics.network/ (accessed on 22 December 2022) and the Inter-planetary file system (IPFS) (Inter-planetary file system network: https://ipfs.tech/ (accessed on 22 December 2022)). The IPFS provides decentralized storage for the metadata and images associated with a given luxury NFT. The timestamping shows the historical occurrences of transactions on a given luxury NFT and is also implemented on the Robonomics platform.
- (f)
- Peer debriefing validation of proposed technology stacks: Three peers working in the field of blockchain application development research are presented with the proposed technologies described above for realizing the architecture of the LogisticsBDT application. They provide a ranking to show the suitability of each technology in the realization of a particular component. A simple average score of the results from the peers is used to generate a ranking for the suitability of the listed technologies. The PD scores for the suitability ranking of the technologies for realizing the mapped architecture of the platform are shown in the last column of Table 2.
3.3.3. Prototype Implementation of Luxury Product Authentication Platform
- (a)
- Brand verification algorithm challenge–response algorithm
| Algorithm 1: Brand registration |
| Initialize variables: x = ∅; x is a set of verified luxury brands, initialized as empty H = f(s,r); H is host url function of subdomain(s) and root-domain(r) E = f(u,r); E is an email function of username(u) and root-domain(r) Pk = user Public key z = the user input for each user T = 16-bit Token Begin algorithm: T = randomToken(16 bit) send(T,Ez) IF: (Ezf(r) == Hzf(r)) ∧ (Tz == T) → x = x ∪ {(Pkz,Hz)} → Store(x) ESLE: x = x |
- (b)
- Luxury NFT minting algorithm
| Algorithm 2: Minting Luxury NFT |
| Initialize variables: NFT = hash(PID) + M PID = Product ID of luxury product (in RFID, barcode or qrcode) M = Meta data of luxury product y = {(PID1 + M1), (PID2 + M2),..,(PIDn + Mn)}; y is a set of minted luxury NFTs x = {(Pk1,H1), (Pk2,H2),…(Pkn,Hn)}; x is a set of verified luxury brands Pk = user Public key H = Brand hostname z = the user input for each user Begin algorithm: Read(PIDz) IF: PIDz ∈ y → Return: PIDz + Mz ESLE: ¬ NFTz = hash(PIDz) + Mz Sign(NFTz, Pkz) IF: Pkz ∈ y → Mz = Mz + (Hz + Pkz) → Store(PIDz + Mz) Return: NFTz ELSE: ‘fail’ |
- (c)
- Luxury NFT transfer algorithm
| Algorithm 3: Transferring Luxury NFT |
| Initialize variables: T_N = transaction on an NFT ΣT_N = the total transactions on an NFT T_N = Sign(NFT, Pk); transaction on NFT is signed by a user public key D = signed transfer data z1 = the user that initiates the transfer z2 = the user that receives the NFT i = a sample of an NFT Begin algorithm: Transferz1(NFTi) ΣT_Ni = count{Sign(NFT1,Pk1), Sign(NFT2,Pk2),…, Sign(NFTn,Pkn)} ΣT_N = count(T_N1, T_N2,…,T_Nn} Decode(T_Nn) IF: PKz1 == PKn → Dz1 = signTransfer(NFTi, PKz1) → Send(Dz1) → Receive(Dz1) → Decode(Dz1) IF: PKz1 ∈ Dz1 == PKn ∈ ΣT_N → Dz2 = signTransfer(Dz1) → ΣT_Ni = Dz2 ∪ count{T_N1, T_N2,… T_Nn} → Store(ΣT_Ni) ELSE: ‘fail’ ELSE: ‘fail’ |
3.3.4. User Interfaces of the LogisticsBDT DApp
4. Evaluation and Discussions
4.1. Simulation and Evaluation of the Luxury Product Authentication Platform
4.1.1. Simulation Objective and Experiment Set-Up
4.1.2. Simulation Results
4.2. Discussions
4.2.1. Implications of the Evaluation Results on the Problems of Luxury Products Authentication
4.2.2. Implication of the Developed Blockchain-Based Luxury Product Authentication with Similar Works
4.2.3. Implications of the Research Contributions of This Work for Retailers and Consumers of Luxury Products
5. Conclusions
5.1. Limitations
5.2. Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Bundgaard, A.M.; Huulgaar, R.D. Luxury products for the circular economy? A case study of Bang & Olufsen. Bus. Strategy Environ. 2019, 28, 699–709. [Google Scholar]
- Hennigs, N.; Wiedmann, K.P.; Klarmann, C.; Behrens, S. Sustainability as part of the luxury essence: Delivering value through social and environmental excellence. J. Corp. Citizsh. 2013, 52, 25–35. [Google Scholar] [CrossRef]
- Abtan, O.; Ducasse, P.; Finet, L.; Gardet, C.; Gasc, M.; Salaire, S. Why Luxury Brands Should Celebrate the Preowned Boom. BCG. 2019. Available online: https://www.bcg.com/publications/2019/luxury-brands-should-celebrate-preowned-boom.aspx (accessed on 22 December 2022).
- Sun, J.J.; Bellezza, S.; Pahari, N. Buy less, buy luxury: Understanding and overcoming product durability neglect for sustainable consumption. J. Mark. 2021, 85, 28–43. [Google Scholar] [CrossRef]
- Brandão, C.; Pinto, A.M.; Gadeka, M. The Counterfeit Market and the Luxury Goods. In Fashion Industry-An Itinerary between Feelings and Technology; BoD–Books on Demand: Norderstedt, Germany, 2019. [Google Scholar]
- OECD/EUIPO. Trends in Trade in Counterfeit and Pirated Goods, Illicit Trade; OECD Publishing: Paris, France, 2019. [CrossRef]
- Ting, M.-S.; Goh, Y.-N.; Is, S.M. Determining consumer purchase intentions toward counterfeit luxury goods in Malaysia. Asia Pac. Manag. Rev. 2016, 21, 219–230. [Google Scholar] [CrossRef]
- Staake, T.; Thiesse, F.; Fleisch, E. The emergence of counterfeit trade: A literature review. Eur. J. Market. 2009, 43, 320–349. [Google Scholar] [CrossRef]
- Peng, J.; Zou, B.; Zh, C. Combining external attention GAN with deep convolutional neural networks for real–fake identification of luxury handbags. Vis. Comput. 2022, 1–12. [Google Scholar] [CrossRef]
- De Boissieu, E.; Kondrateva, G.; Baudier, P.; Ammi, C. The use of blockchain in the luxury industry: Supply chains and the traceability of goods. J. Enterp. Inf. Manag. 2021. ahead-of-print. [Google Scholar] [CrossRef]
- Kolev, G.V.; Neligan, A. Effects of a Supply Chain Regulation: Survey-Based Results on the Expected Effects of the German Supply Chains Act; No. 8/2022. IW-Report, Nr. 8; Institut der Deutschen Wirtschaft Köln: Köln, Germany, 2022. [Google Scholar]
- Felbermayr, G.; Langhammer, R.; Sandkamp, A.; Herrmann, C.; Trapp, P. Economic Evaluation of a Due Diligence Law; IfW Kiel Institute for the World Economy: Kiel, Germany, 2021. [Google Scholar]
- Swan, M. Blockchain: Blueprint for a New Econom; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Udokwu, C.; Kormiltsyn, A.; Thangalimodzi, K.; Norta, A. The state of the art for blockchain-enabled smart-contract applications in the organization. In Proceedings of the 2018 Ivannikov Ispras Open Conference (ISPRAS), Moscow, Russia, 22–23 November 2018; pp. 137–144. [Google Scholar]
- Gayialis, S.P.; Kechagias, E.; Papadopoulos, G.A.; Konstantakopoulos, G.D. Design of a blockchain-driven system for product counterfeiting restraint in the supply chain. In Proceedings of the IFIP International Conference on Advances in Production Management Systems, Austin, TX, USA, 1 September 2019; Springer: Cham, The Netherlands, 2019; pp. 474–481. [Google Scholar]
- Chen, C.L.; Guo, L.H.; Zhou, M.; Tsaur, W.J.; Sun, H.; Zhan, W.; Li, C.T. Blockchain-Based Anti-Counterfeiting Management System for Traceable Luxury Products. Sustainability 2022, 14, 12814. [Google Scholar] [CrossRef]
- Ugochukwu, N.A.; Goyal, S.B.; Rajawat, A.S.; Islam, S.M.; He, J.; Aslam, M. An Innovative Blockchain-Based Secured Logistics Management Architecture: Utilizing an RSA Asymmetric Encryption Method. Mathematics 2022, 10, 4670. [Google Scholar] [CrossRef]
- Casado-Vara, R.; Prieto, J. How blockchain improves the supply chain: Case study alimentary supply chain. Procedia Comput. Sci. 2018, 134, 393–398. [Google Scholar] [CrossRef]
- Chiacchio, F.; D’Urso, D.; Oliveri, L.M.; Spitaleri, A.; Spampinato, C.; Giordano, D. A Non-Fungible Token Solution for the Track and Trace of Pharmaceutical Supply Chain. Appl. Sci. 2022, 12, 4019. [Google Scholar] [CrossRef]
- Musamih, A.; Salah, K.; Jayaraman, R.; Arshad, J.; Debe, M.; Al-Hammadi, Y.; Ellahham, S. A blockchain-based approach for drug traceability in healthcare supply chain. IEEE Access 2021, 9, 9728–9743. [Google Scholar] [CrossRef]
- Biswas, K.; Muthukkumarasamy, V.; Tan, W.L. Blockchain based wine supply chain traceability system. In Future Technologies Conference (FTC); The Science and Information Organization: New York, NY, USA, 2017; pp. 56–62. [Google Scholar]
- Rossi, M.; Mueller-Bloch, C.; Thatcher, J.B.; Beck, R. Blockchain research in information systems: Current trends and an inclusive future research agenda. J. Assoc. Inf. Syst. 2019, 20, 14. [Google Scholar] [CrossRef]
- Ullah, A.; Siddiquee, S.S.; Hossain, M.A.; Ray, S.K. thereumeum blockchain-based prototype for data security of regulated electricity market. Inventions 2020, 5, 58. [Google Scholar] [CrossRef]
- Hugo, B.; Caceres, C.; Abarzúa, L.Á. “Utility Tokens.” The Emerald Handbook on Cryptoassets: Investment Opportunities and Challenges; Emerald Publishing Limited: Bingley, UK, 2023; pp. 79–92. [Google Scholar]
- Hevner, A.R.; March, S.T.; Park, J.; Ram, S. Design science in information systems research. MIS Q. 2004, 28, 75–105. [Google Scholar] [CrossRef]
- Ritchie, J.; Spence, L. Qualitative Data Analysis for Applied Policy Research. Analyzing Qualitative Data; Routledge: Cambridge, UK, 2002; pp. 187–208. [Google Scholar]
- Zimmermann, R.; Udokwu, C.; Kompp, R.; Brandtner, P.; Norta, A. Authentication of Luxury Products–Identifying Key Requirements from a Seller and Consumer Perspective. In Proceedings of the International Conference on Future Data and Security Engineering, Ho Chi Minh City, Vietnam, 23–25 November 2022; Springer: Singapore, 2022; pp. 195–209. [Google Scholar]
- Udokwu, C.; Anyanka, H.; Nort, A. Evaluation of approaches for designing and developing decentralized applications on blockchain. In Proceedings of the 2020 4th International Conference on Algorithms, Computing and Systems, Berlin, Germany, 6–8 January 2020. [Google Scholar]
- Udokwu, C.; Nort, A. Deriving and formalizing requirements of decentralized applications for inter-organizational collaborations on blockchain. Arab. J. Sci. Eng. 2021, 46, 8397–8414. [Google Scholar] [CrossRef]
- Sterling, L.; Taveter, K. The Art of Agent-Oriented Modelling; MIT Press: Cambridge, MA, USA, 2009. [Google Scholar]
- Miller, T.; Pedell, S. Emotion-led modelling for people-oriented requirements engineering: The case study of emergency systems. J. Syst. Softw. 2015, 105, 54–71. [Google Scholar] [CrossRef]
- Janesick, V. Peer Debriefing. The Blackwell Encyclopedia of Sociology; Wiley Online library: Hoboken, NJ, USA, 2007; Available online: https://onlinelibrary.wiley.com/doi/abs/10.1002/9781405165518.wbeosp014.pub2 (accessed on 22 December 2022).
- Green, R.T.; Smit, T. Executive insights: Countering brand counterfeiters. J. Int. Mark. 2002, 10, 89–106. [Google Scholar] [CrossRef]
- Udokwu, C.; Brandtner, P.; Norta, A.; Kormiltsyn, A.; Matulevičius, R. Implementation and evaluation of the DAOM framework and support tool for designing blockchain decentralized applications. Int. J. Inf. Technol. 2021, 13, 2245–2263. [Google Scholar] [CrossRef]
- Randhawa, P.; Calantone, R.J.; Voorhee, C.M. The pursuit of counterfeited luxury: An examination of the negative side effects of close consumer–brand connections. J. Bus. Res. 2015, 68, 2395–2403. [Google Scholar] [CrossRef]
- Ting, S.L.; Tsan, A.H. A two-factor authentication system using radio frequency identification and watermarking technology. Comput. Ind. 2013, 64, 268–279. [Google Scholar] [CrossRef] [Green Version]
- Udokwu, C.J. A Modelling Approach for Building Blockchain Applications That Enables Trustable Inter-Organizational Collaborations. Doctoral Dissertation, Lappeenranta University of Technology, Lappeenranta, Finland, 2022. [Google Scholar]
- Norta, A.; Kormiltsyn, A.; Udokwu, C.; Dwivedi, V.; Aroh, S.; Nikolajev, I. A Blockchain Implementation for Configurable Multi-Factor Challenge-Set Self-Sovereign Identity Authentication. In Proceedings of the 2022 IEEE International Conference on Blockchain (Blockchain), Espoo, Finland, 22 August 2022; pp. 455–461. [Google Scholar]






| ID | Questions | Most Repeated Themes | ||
|---|---|---|---|---|
| 1 | 2 | 3 | ||
| 1 | Are used goods repurchased? | Yes (4) | No (4) | - |
| 2 | How does the process of repurchasing work? | Trade-in by previous owners (3) | Direct sale to consumers (2) | Sale on commission (2) |
| 3 | How do they check the authenticity of these used luxury products? | Serial number/certificate (5) | Product visual inspection (3) | - |
| 4 | Who is responsible for verifying the authenticity of resold products? | Seller (7) | Producer (4) | Consumer (3) |
| 5 | What options are there (currently) for verifying the authenticity of luxury products? | Visual inspection using specialized equipment (8) | Knowledge-based and experience (8) | Warranty checks (2) |
| 6 | What digital options are there (should be used) for verifying the authenticity of products? | Qr code for identifying luxury products (4) | Blockchain for interoperable storage of luxury product data (3) | - |
| 7 | Where do you see deficits in the methods/processes (current) you mentioned for authenticating luxury products? | Traceability and document verification problems (2) | Effort and difficulty of the verification tasks (2) | - |
| 8 | What factors cause these deficits? | Lack of knowledge and complexity of implementation (of verification) (4) | Too expensive (2) | 100% authenticity can’t be guaranteed (2) |
| 9 | Who do they think should pay for? additional authentication services? | Consumer (5) | Seller (4) | Producer (3) |
| 10 | What features/capabilities would you like to see for luxury product authentication? | Certification seal with a digital service book (4) | Multi-vendor database storage (for luxury products’ data) (3) | A high ease of use and fast verification (2) |
| 11 | Experts’ ratings on (the blockchain-specific) features: product identification, transfer of ownership, product purchase with cryptocurrency and product ownership history (scale: 1–5) | Product ownership history (3) | Transfer of ownership (2) | Product identification (2) |
| Component Tech-Stack Mapping | |||
|---|---|---|---|
| Component | Sub-Component | Tech-Stack | PD- Validation |
| Brand registration | Brand input | HTML text Form | 5 |
| Brand validation | Challenge-set host-email authentication | 4 | |
| LuxuryNFT minting | PID scanner | QR-Code | 4 |
| Bar-Code | 4 | ||
| RFID/NFC | 4 | ||
| Product input | HTML text/image Form | 4 | |
| Digital signature | Polkadot wallet (single-signature) | 4 | |
| LuxuryNFT transfer | Product update | HTML image form | 4 |
| PID scanner | QR-Code | 4 | |
| Bar-Code | 4 | ||
| RFID/NFC | 4 | ||
| Product update | HTML image Form | 5 | |
| Digital signature | Polkadot wallet (multi-signature) | 3 | |
| LuxuryNFT viewer | PID scanner | QR-Code | 4 |
| Bar-Code | 4 | ||
| RFID/NFC | 4 | ||
| Product details | HTML/CSS | 4 | |
| On-chain | Storage | IPFS | 5 |
| Time-stamping | Robonomics blockchain | 4 | |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Udokwu, C.; Zimmermann, R.; Norta, A.; Brandtner, P.; Kormiltsyn, A.; Aroh, S.M. Exerting Qualitative Analytics and Blockchain Requirement-Engineering in Designing and Implementing a Luxury Products Authentication System. Inventions 2023, 8, 49. https://doi.org/10.3390/inventions8010049
Udokwu C, Zimmermann R, Norta A, Brandtner P, Kormiltsyn A, Aroh SM. Exerting Qualitative Analytics and Blockchain Requirement-Engineering in Designing and Implementing a Luxury Products Authentication System. Inventions. 2023; 8(1):49. https://doi.org/10.3390/inventions8010049
Chicago/Turabian StyleUdokwu, Chibuzor, Robert Zimmermann, Alexander Norta, Patrick Brandtner, Alexandr Kormiltsyn, and Sunday Melitus Aroh. 2023. "Exerting Qualitative Analytics and Blockchain Requirement-Engineering in Designing and Implementing a Luxury Products Authentication System" Inventions 8, no. 1: 49. https://doi.org/10.3390/inventions8010049
APA StyleUdokwu, C., Zimmermann, R., Norta, A., Brandtner, P., Kormiltsyn, A., & Aroh, S. M. (2023). Exerting Qualitative Analytics and Blockchain Requirement-Engineering in Designing and Implementing a Luxury Products Authentication System. Inventions, 8(1), 49. https://doi.org/10.3390/inventions8010049









