ECQV-Based Lightweight Revocable Authentication Protocol for Electric Vehicle Charging
Abstract
:1. Introduction
- Clean-fuel vehicles and initiatives to reduce carbon emissions should be encouraged: Saudi Arabia, the world’s leading oil producer, declared that at least 30% of the cars in its capital city will be electric by 2030. Similarly, China seeks 25% of all new cars to be electrified by 2025. The UK attempts to stop producing and selling fossil-fuel vehicles by 2030 [4].
- Resolve uncertainty for EV drivers: EV drivers still face uncertainty, even though more people are adopting the technology. As reported by the climate group EV100′s members, the most significant challenge that users are concerned about is the availability of EV charging stations (e.g., charging station location, EV parking space, and charge cost) [5,6]. As a result, charging stations need to be strategically positioned and used efficiently as the demand for EVs increases [7]. Because work was disrupted in major areas due to the COVID-19 pandemic, the installation of publicly available chargers increased by 45%, a slower rate than the 85% seen in 2019. The company also cited a persistent barrier as the lack of suitable vehicle types. The cost of buying an electric vehicle remains a significant barrier [5];
- Make EV charging a smooth experience: Remote control using smartphone applications is one of the features of smart EV charging. This feature makes EV charging faster as well as easier to use and, hence, more accessible to a wider variety of clients [3].
1.1. Problem Statement
1.2. Paper Motivation and Contribution
- Present an ECQV-based authentication solution that is more effective at preserving privacy and providing secure authentication for electric vehicle charging stations;
- Use Burrows–Abadi–Needham (BAN) logic and the AVISPA simulation tool to conduct a formal security study to demonstrate that the proposed scheme is secure against numerous attacks. In addition, we perform an informal security analysis to show the proposed protocol’s security;
- Compare the computational costs with other related work, to illustrate that the proposed techniques will perform better.
1.3. Paper Organization
2. Preliminaries
2.1. Solution Requirements
- Mutual authentication: The system must allow the parties to confirm one another’s identities and guarantee that communication is based on trust. To verify the EAG’s identification and registration with the trusted charging system operator (OP), the EV must authenticate the EAG. The EAG will verify the EV’s registration with the OP concurrently. The OP issues certificates for authentication, consequently reducing the likelihood of a masquerade attack [16];
- Anonymity: Anonymity is the capability to evade being recognized within a group of subjects. The EV’s true identity should not be revealed to the EAG while it is charging [17]. Un-traceability is the ability to keep the activities of a subject un-traceable. Eavesdroppers cannot guess or trace the EV’s activities [16];
- Un-linkability: Un-linkability is where the attacker cannot tell whether two actions are related. EVs during various charging sessions should not be linkable [17];
- Traceability: This characteristic guarantees that, if necessary, the trustworthy organization (OP) can determine or reveal a malicious EV’s real identity [18];
- Perfect forward security: If a long-lasting private key is exposed, the adversary cannot obtain a future session key [19];
- Perfect backward security: If a long-lasting private key is exposed, an adversary cannot obtain the old session key [19];
- Joint key control: The session key will be created using a random number that is contributed by both EAG and EV. As a result, no other party has access to or can acquire any session keys;
- Effective reauthentication: The process where the EAG reauthenticates the EV, causing an overhead. The EAG should, therefore, be able to verify the EV using the information given by a reliable third party (OP) during the initial encounter. Therefore, the EAG does not need to rely on the OP for future access because it can reauthenticate the EV;
- Revocation method: If a user’s registration is ended or the EAG/EV secret key is publicly disclosed, the corresponding information should be revoked. It is critical to grant a revocation mechanism for the system;
- Attack resistance: Adversaries may launch attacks during the communication between EAG and EV, as it is carried out in an insecure environment. Thus, the proposed scheme must be capable of thwarting attacks such as MITM attacks, replay attacks, impersonation attacks, etc.
2.2. ECQV Implicit Certificates
- (1)
- ECQV Basic Notations
- (2)
- ECQV Algorithms
- ECQV certificate request: A user generates an EC pair of keys and sends the public key together with the user’s ID to the CA;
- ECQV certificate generation: The CA validates the ID and creates data for public reconstruction that may be used to obtain the user’s public key. Next, ECQV certificate data are incorporated and contain both ID and public reconstruction information. The resulting ECQV certificate and the private key of the CA are then used to compute the user’s private reconstruction data. The user then receives the private reconstruction data and the ECQV certificate from the CA;
- ECQV certificate reception: The user creates a public/private-key pair using the first step’s private key, private reconstruction information, and ECQV certificate (acquired from CA). In order to confirm that the obtained certificate was indeed issued by the CA, the user then performs a verification process.
3. Literature Review
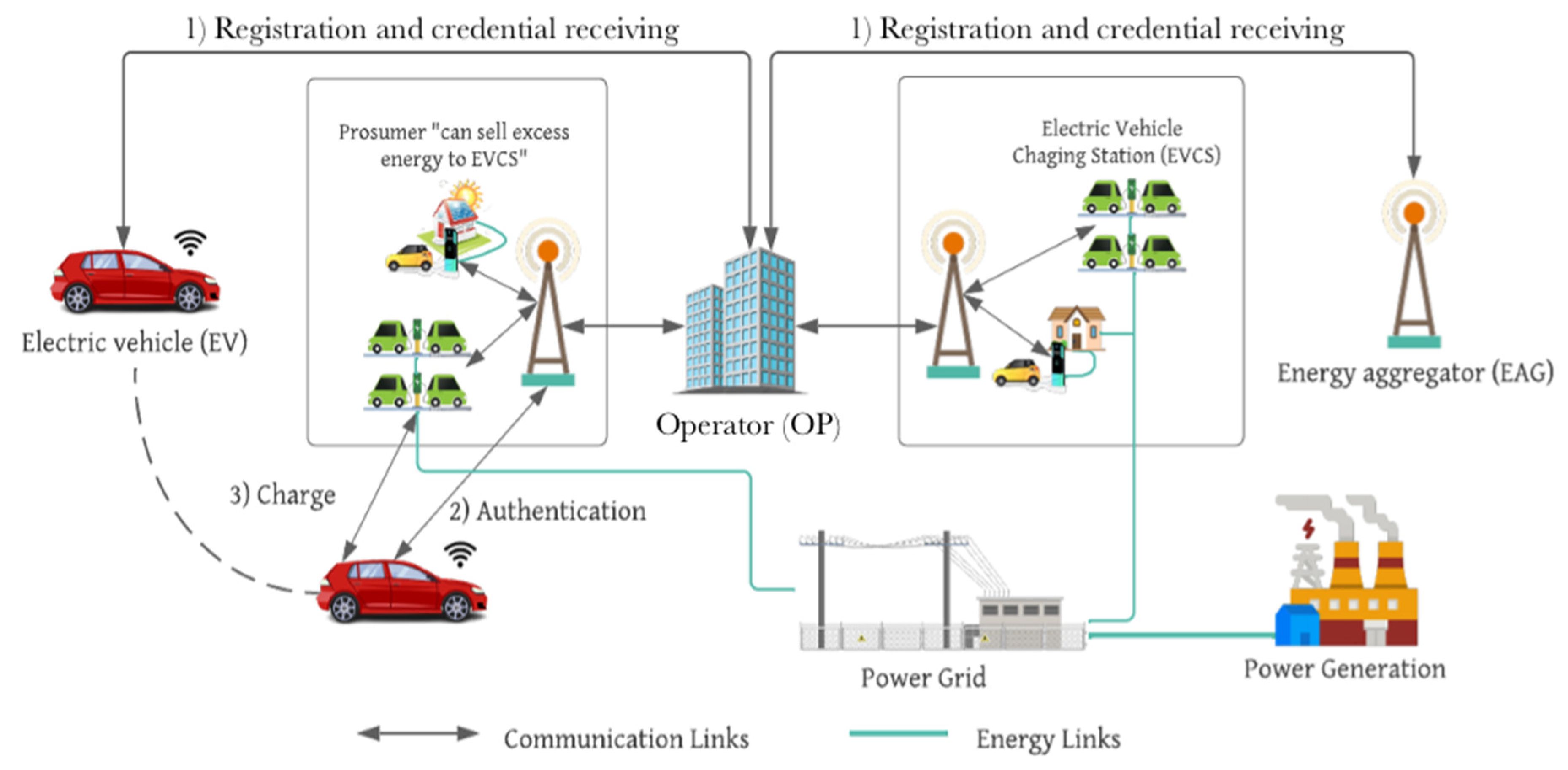
4. Proposed System
4.1. System Architecture
- Operator (OP): Any EV or EAG seeking to use the charging system must first register their identification information with the OP, where OP acts as the initializer for the proposed protocol. Authorized EVs can use the EAG’s services and develop trust with one another because the OP acts as a certificate generator (trusted third party). The OP can also identify malicious or misbehaving nodes by revealing their identities;
- Energy Aggregator (EAG): A data aggregator is a smart device or collection of smart devices that serves as a data aggregator of available EV power information while the EVs are charging and supplying power to the EVs via a number of EVCSs. To coordinate the charging, the EAG has an authentication mechanism to identify authorized EVs;
- Electric Vehicle (EV): It is a smart device that communicates charging requests to EAGs and mutually validates an EAG’s eligibility to use its service (charging).
4.2. Threat Model
4.3. Initialization Phase
- Step 1:
- A base point G of order is chosen by OP on the elliptic curve , where is a significant prime number. Select the curve coefficients and , field size , and cofactor , where is the number of points on the elliptic curve (these are the elliptic curve domain parameters);
- Step 2:
- Select an approved hash function . The OP and certificate requester (EV or EAG) specify the generator of random numbers to be used throughout the certificate request/creation procedures to generate the private keys;
- Step 3:
- OP obtains an EC-key pair (), which is associated with the elliptic curve domain parameters (established in the first step).
- Step 4:
- Both EV and EAG obtain, in an authentic manner, the EC domain parameters, , and (OP’s public key).
4.4. Registration Phase
4.4.1. EV Registration
- Step 1:
- EV selects its identity ; generate EC-key pair (), where and . Compute to ensure integrity. Then, send it to OP encrypted with (OP’s public key);
- Step 2:
- OP retrieves the content of the message using its private key and verifies . Then, choose and generate EV’s implicit certificate ; compute , , the private key construction data of EV. OP uses Formula (1) to create EV’s pseudo-identity and signs it using OP’s private key, where the real identity of EV is encrypted with to assure its anonymity and is agreed to be incremented sequentially () by EV itself every time it requests a service. Compute EV’s authenticator using Formula (2), which contains the issued with its time-life () signed using the private key of OP. Compute to ensure integrity. Compute registration key that is shared between OP and EV only. Then, send to EV encrypted with Lastly, OP destroys , , to prevent the possession of EV’s private key by an adversary;
- Step 3:
- EV calculates the shared registration key to retrieve and verify through OP’s public key and check . Compute to generate its private/public-key pair / using Formulas (3) and (4).
4.4.2. EAG Registration
- Step 1:
- EAG selects its identity ; generate EC-key pair (), where and . Compute to ensure integrity. Then, send it to OP encrypted with .
- Step 2:
- OP retrieves the content of the message using its private key and verifies ; choose and generate EAG’s implicit certificate ; compute , , the private key construction data of EAG. Compute the authenticator by Formula (8); it contains the issued , , its time-life () signed using the private key of OP. Then, compute to ensure integrity. Compute registration key that is shared between OP and EAG only. Then, send it to EAG encrypted with Lastly, OP destroys , , to prevent the possession of EAG’s private key by adversaries.
- Step 3:
- EAG computes the registration key to retrieve and verify the through OP’s public key and checks . Compute to generate its private/public-key pair / using Formulas (9) and (10).
4.5. Authentication Phase
4.5.1. Mutual Authentication Protocol
- Step 1:
- EV generates the charging request , where “” states the amount of power needed, “” specifies how much the EV is willing to pay for the service (to keep the location of the EV private), “” should specify how far it is from the local EAG, and “” states the time-life of the request. Then, EV sends to their local EAG;
- Step 2:
- The EAG sends its as a response to the EV charging request;
- Step 3:
- EV verifies through OP’s signature and checks if it is valid by the ; retrieve and compute to extract the EAG’s public key . Generate a random number , time stamp , and the master shared key using Formula (14). Increase the counter one at a time (by adding 1 to the previous EV’s pseudo-identification) to generate a new anonymous identity for the current session. This prevents linking between multiple sessions of an EV. Then, send to EAG encrypted with .
- Step 4:
- To decrypt the message, EAG employs its own private key and uses OP’s signature to confirm that is authentic, and checks to make sure the message is not being replayed. Compute to extract EV’s public key . Verify by OP’s signature and EV’s signature () that is included in it. Then, generate , the master shared key using Formula (15), and the authorization token by Formula (16), where are encrypted with . Moreover, generate the initial and session key using Formulas (17) and (18), receptively. Then, send to EV encrypted by , the EAG schedule charging service for EVs that is protected by .
- Step 5:
- EV generates by Formula (17) to retrieve and checks the validity of . Next, create the session key to be used during the charging session using Formula (18). EV stores the issued by EAG, and updates . By the end of this process, EV and EAG shall have both established trust between them, without having to depend on OP in the future for session authentication.
4.5.2. Lightweight Mutual Reauthentication Protocol
- Step 1:
- EV creates , and applies Formula (18) to determine the previous session key to be used in encryption. Increment the counter sequentially (add 1 to the EV’s previous pseudo-identity) to have a new anonymous identity for this session to maintain un-linkability. Then, EV sends , to EAG.
- Step 2:
- EAG validates the authenticity of via the signature using and . Decrypt the using to retrieve . EAG needs to compute in order to obtain , and confirm that the was transmitted by the authorized EV. Then, use , , , to generate the temporary key using Formula (19). Generate a fresh session key as in the Formula (20). EAG then sends encrypted by to EV. The EAG manages the EV charging service that is secured by .
- Step 3:
- EV generates the to retrieve and verifies . Then, use Formula (20) to create for the charging session; is updated.
4.6. Revocation Protocol
- Step 1:
- EV creates the revocation request ; forward it to OP after being encrypted with OP’s public key .
- Step 2:
- OP decrypts the revocation request by its and verifies using and , which is within , and to avoid replay attack, OP checks to verify whether it is valid or not. Finally, OP updates the status as revoked. A fake revocation request cannot be produced by the adversary since EV’s signature is necessary.
- Step 1:
- EV uses Formula (21) to create the revocation request, which is subsequently sent to EAG after being partially encrypted using Formula (22).
- Step 2:
- EAG validates the through the signature using and decrypts internal part using its . Then, EAG uses , , to generate the revocation key using Formula (22) and retrieving the other part of the message. Verify the request belongs to the same by and using the retrieved , then check whether is valid or not. Finally, EAG updates status as revoked. The use of revoked leads to the rejection of EV’s charging service request. Furthermore, since the master key is used to construct the revocation key , an adversary cannot produce a fake revocation request.
5. Security Analysis
5.1. Formal Security Analysis BAN Logic
- Clearly state the goals to achieve;
- Form assumptions about the initial situation;
- Affirm the protocol in its idealized state;
- Utilize the logic to obtain associated party beliefs.
5.1.1. Analyzing Authentication Protocol
- Step 1:
- Goals. The analysis’ key goals, which comprise the secrecy of the exchanged session key, are listed below:
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Step 2:
- Assumptions. The proposed protocol’s preliminary assumptions are as follows:
- P1.
- EAG |≡ # ()
- P2.
- EV |≡ # ()
- P3.
- EAG |≡ # ()
- P4.
- EAG |≡)
- P5.
- EV |≡)
- P6.
- EAG |≡)
- P7.
- EV |≡)
- P8.
- EAG|≡ EV )
- P9.
- EV |≡ EAG )
- Step 3:
- Idealization. The following is an idealized version of the proposed protocol:
- M1.
- EV → EAG: )
- M2.
- EAG → EV:
- Step 4:
- Analysis. The beliefs that both the EV and EAG can obtain in the proposed protocol are derived here. Then, we investigate, based on BAN logic rules, which authentication goals can be met.
5.1.2. Analyzing Reauthentication Protocol
- Step 1:
- Goals. The analysis’ key goals, which comprise the secrecy of the exchanged session key, are listed below:
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
- Step 2:
- Assumptions. The proposed protocol’s preliminary assumptions are as follows:
- P1.
- EAG |≡ # ()
- P2.
- EAG |≡ # ()
- P3.
- EAG |≡ # ()
- P4.
- EV |≡ # ()
- P5.
- EAG |≡)
- P6.
- EV |≡)
- P7.
- EAG |≡)
- P8.
- EV |≡)
- P9.
- EAG|≡ EV )
- P10.
- EV |≡ EAG )
- Step 3:
- Idealization. The following is an idealized version of the proposed protocol:
- M1.
- EV → EAG:)
- M2.
- EAG → EV: )
- Step 4:
- Analysis. The beliefs that both the EV and EAG can obtain in the proposed protocol are derived here. Then, we investigate which authentication goals can be met.
5.2. Security Simulation with AVISPA Tool
5.2.1. Mutual Authentication HLPSL Specification of AVISPA Simulation
5.2.2. Mutual Authentication AVISPA Verification Results
5.2.3. Reauthentication HLPSL Specifications of AVISPA Simulation
5.2.4. Reauthentication AVISPA Verification Results
5.3. Informal Security Analysis
5.3.1. Mutual Authentication
5.3.2. Anonymity
5.3.3. Un-Linkability
5.3.4. Traceability
5.3.5. Forward/Backward Security
5.3.6. Joint Key Control
5.3.7. Effective Reauthentication
5.3.8. Revocation Functionality
5.3.9. Resist MITM/Replay Attack
5.3.10. Resist Impersonation Attack
5.3.11. Resist DOS Attack
6. Comparison with Related Schemes
6.1. Security and Functional Features Comparison
6.2. Computational Cost Comparison
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- US EPA. Sources of Greenhouse Gas Emissions. Available online: https://www.epa.gov/ghgemissions/sources-greenhouse-gas-emissions (accessed on 12 April 2022).
- Ahmadi, P. Environmental Impacts and Behavioral Drivers of Deep Decarbonization for Transportation through Electric Vehicles. J. Clean. Prod. 2019, 225, 1209–1219. [Google Scholar] [CrossRef]
- Acharya, S.; Dvorkin, Y.; Pandžić, H.; Karri, R. Cybersecurity of Smart Electric Vehicle Charging: A Power Grid Perspective. IEEE Access 2020, 8, 214434–214453. [Google Scholar] [CrossRef]
- Nereim, V. Saudi Arabia to Start Electric-Vehicle Push in Capital Riyadh. Available online: www.bloomberg.com/news/articles/2021-10-23/saudi-arabia-to-start-electric-vehicle-push-in-capital-riyadh (accessed on 23 October 2021).
- Global EV Outlook 2021—Analysis. IEA. Available online: https://www.iea.org/reports/global-ev-outlook-2021 (accessed on 2 November 2021).
- Yi, T.; Zhang, C.; Lin, T.; Liu, J. Research on the Spatial-Temporal Distribution of Electric Vehicle Charging Load Demand: A Case Study in China. J. Clean. Prod. 2020, 242, 118457. [Google Scholar] [CrossRef]
- Fu, Z.; Dong, P.; Ju, Y. An Intelligent Electric Vehicle Charging System for New Energy Companies Based on Consortium Blockchain. J. Clean. Prod. 2020, 261, 121219. [Google Scholar] [CrossRef]
- Gorenflo, C.; Golab, L.; Keshav, S. Mitigating Trust Issues in Electric Vehicle Charging Using a Blockchain. In Proceedings of the Tenth ACM International Conference on Future Energy Systems; e-Energy ’19. Association for Computing Machinery: New York, NY, USA, 2019; pp. 160–164. [Google Scholar] [CrossRef]
- Al-Ogaili, A.S.; Tengku Hashim, T.J.; Rahmat, N.A.; Ramasamy, A.K.; Marsadek, M.B.; Faisal, M.; Hannan, M.A. Review on Scheduling, Clustering, and Forecasting Strategies for Controlling Electric Vehicle Charging: Challenges and Recommendations. IEEE Access 2019, 7, 128353–128371. [Google Scholar] [CrossRef]
- Nedyalkov, I.; Arnaudov, D. Attacks and Security Measures of the Exchanged Information in the Charging Infrastructure for Electromobiles. In Proceedings of the IEEE XXVIII International Scientific Conference Electronics (ET), Sozopol, Bulgaria, 12–14 September 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Wang, X.; Hou, X.; Rios, R.; Tippenhauer, N.O.; Ochoa, M. Constrained Proximity Attacks on Mobile Targets. ACM Trans. Priv. Secur. 2022, 25, 20. [Google Scholar] [CrossRef]
- Kilari, V.T.; Yu, R.; Misra, S.; Xue, G. Robust Revocable Anonymous Authentication for Vehicle to Grid Communications. IEEE Trans. Intell. Transp. Syst. 2020, 21, 4845–4857. [Google Scholar] [CrossRef]
- Zhang, X.; Liu, C.; Chai, K.K.; Poslad, S. A Privacy-Preserving Consensus Mechanism for an Electric Vehicle Charging Scheme. J. Netw. Comput. Appl. 2021, 174, 102908. [Google Scholar] [CrossRef]
- ElHussini, H.; Assi, C.; Moussa, B.; Atallah, R.; Ghrayeb, A. A Tale of Two Entities: Contextualizing the Security of Electric Vehicle Charging Stations on the Power Grid. ACM Trans. Internet Things 2021, 2, 9. [Google Scholar] [CrossRef]
- Baroutis, N.; Younis, M. Location Privacy in Wireless Sensor Networks. In Mission-Oriented Sensor Networks and Systems: Art and Science: Volume 1: Foundations; Ammari, H.M., Ed.; Studies in Systems, Decision and Control; Springer International Publishing: Cham, Switzerland, 2019; pp. 669–714. [Google Scholar] [CrossRef]
- Saxena, N.; Grijalva, S.; Chukwuka, V.; Vasilakos, A.V. Network Security and Privacy Challenges in Smart Vehicle-to-Grid. IEEE Wirel. Commun. 2017, 24, 88–98. [Google Scholar] [CrossRef]
- Hansen, M.; Jensen, M.; Rost, M. Protection Goals for Privacy Engineering. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 159–166. [Google Scholar] [CrossRef]
- Mundhe, P.; Verma, S.; Venkatesan, S. A Comprehensive Survey on Authentication and Privacy-Preserving Schemes in VANETs. Comput. Sci. Rev. 2021, 41, 100411. [Google Scholar] [CrossRef]
- Zhang, J.; Cui, J.; Zhong, H.; Chen, Z.; Liu, L. PA-CRT: Chinese Remainder Theorem Based Conditional Privacy-Preserving Authentication Scheme in Vehicular Ad-Hoc Networks. IEEE Trans. Dependable Secure Comput. 2021, 18, 722–735. [Google Scholar] [CrossRef]
- Brown, D.R.L.; Gallant, R.; Vanstone, S.A. Provably Secure Implicit Certificate Schemes. In Financial Cryptography; Syverson, P., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2002; pp. 156–165. [Google Scholar] [CrossRef]
- Campagna, M. Sec 4: Elliptic Curve Qu-Vanstone Implicit Certificate Scheme (ECQV). Standards for Efficient Cryptography, Version. 2013; 1. Available online: www.secg.org/sec4-1.0.pdf (accessed on 24 November 2021).
- Ha, D.A.; Nguyen, K.T.; Zao, J.K. Efficient Authentication of Resource-Constrained IoT Devices Based on ECQV Implicit Certificates and Datagram Transport Layer Security Protocol. In Proceedings of the Seventh Symposium on Information and Communication Technology, Ho Chi Minh City, Vietnam, 8–9 December 2016; SoICT ’16. Association for Computing Machinery: New York, NY, USA, 2016; pp. 173–179. [Google Scholar] [CrossRef]
- Khan, A.G.; Basharat, S.; Riaz, M.U. Analysis of Asymmetric Cryptography in Information Security Based on Computational Study to Ensure Confidentiality during Information Exchange. Int. J. Sci. Eng. Res. 2018, 9, 992–999. [Google Scholar]
- Bokhari, M.U.; Shallal, Q.M. A Review on Symmetric Key Encryption Techniques in Cryptography. Int. J. Comput. Appl. 2016, 147, 43–48. [Google Scholar]
- Li, H.; Dán, G.; Nahrstedt, K. Portunes+: Privacy-Preserving Fast Authentication for Dynamic Electric Vehicle Charging. IEEE Trans. Smart Grid 2017, 8, 2305–2313. [Google Scholar] [CrossRef]
- Huang, X.; Xu, C.; Wang, P.; Liu, H. LNSC: A Security Model for Electric Vehicle and Charging Pile Management Based on Blockchain Ecosystem. IEEE Access 2018, 6, 13565–13574. [Google Scholar] [CrossRef]
- Kim, M.; Park, K.; Yu, S.; Lee, J.; Park, Y.; Lee, S.-W.; Chung, B. A Secure Charging System for Electric Vehicles Based on Blockchain. Sensors 2019, 19, 3028. [Google Scholar] [CrossRef]
- ElGhanam, E.; Ahmed, I.; Hassan, M.; Osman, A. Authentication and Billing for Dynamic Wireless EV Charging in an Internet of Electric Vehicles. Future Internet 2021, 13, 257. [Google Scholar] [CrossRef]
- Babu, P.R.; Amin, R.; Reddy, A.G.; Das, A.K.; Susilo, W.; Park, Y. Robust Authentication Protocol for Dynamic Charging System of Electric Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 11338–11351. [Google Scholar] [CrossRef]
- Rabieh, K.; Wei, M. Efficient and Privacy-Aware Authentication Scheme for EVs Pre-Paid Wireless Charging Services. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Gunukula, S.; Sherif, A.B.T.; Pazos-Revilla, M.; Ausby, B.; Mahmoud, M.; Shen, X.S. Efficient Scheme for Secure and Privacy-Preserving Electric Vehicle Dynamic Charging System. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Roman, L.F.A.; Gondim, P.R.L. Authentication Protocol in CTNs for a CWD-WPT Charging System in a Cloud Environment. Ad Hoc Netw. 2020, 97, 102004. [Google Scholar] [CrossRef]
- Fuchsbauer, G.; Vergnaud, D. Fair Blind Signatures without Random Oracles. In Progress in Cryptology—AFRICACRYPT 2010; Bernstein, D.J., Lange, T., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2010; pp. 16–33. [Google Scholar] [CrossRef]
- Li, F.; Xin, X.; Hu, Y. Efficient Certificate-Based Signcryption Scheme from Bilinear Pairings. Int. J. Comput. Appl. 2008, 30, 129–133. [Google Scholar] [CrossRef]
- Xia, Z.; Fang, Z.; Gu, K.; Wang, J.; Tan, J.; Wang, G. Effective Charging Identity Authentication Scheme Based on Fog Computing in V2G Networks. J. Inf. Secur. Appl. 2021, 58, 102649. [Google Scholar] [CrossRef]
- Roman, L.F.A.; Gondim, P.R.L.; Lloret, J. Pairing-Based Authentication Protocol for V2G Networks in Smart Grid. Ad Hoc Netw. 2019, 90, 101745. [Google Scholar] [CrossRef]
- Kumar, G.; Saha, R.; Rai, M.K.; Buchanan, W.J.; Thomas, R.; Geetha, G.; Hoon-Kim, T.; Rodrigues, J.J.P.C. A Privacy-Preserving Secure Framework for Electric Vehicles in IoT Using Matching Market and Signcryption. IEEE Trans. Veh. Technol. 2020, 69, 7707–7722. [Google Scholar] [CrossRef]
- Vaidya, B.; Mouftah, H.T. Multimodal and Multi-Pass Authentication Mechanisms for Electric Vehicle Charging Networks. In Proceedings of the International Wireless Communications and Mobile Computing (IWCMC), Limassol, Cyprus, 15–19 June 2020; pp. 371–376. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Hasbullah, I.H.; Manickam, S. Survey of Authentication and Privacy Schemes in Vehicular Ad Hoc Networks. IEEE Sens. J. 2021, 21, 2422–2433. [Google Scholar] [CrossRef]
- Braeken, A.; Touhafi, A. AAA—Autonomous Anonymous User Authentication and Its Application in V2G. Concurr. Comput. Pract. Exp. 2018, 30, e4303. [Google Scholar] [CrossRef]
- Lu, Z.; Qu, G.; Liu, Z. A Survey on Recent Advances in Vehicular Network Security, Trust, and Privacy. IEEE Trans. Intell. Transp. Syst. 2019, 20, 760–776. [Google Scholar] [CrossRef]
- Baee, M.A.R.; Simpson, L.; Foo, E.; Pieprzyk, J. Broadcast Authentication in Latency-Critical Applications: On the Efficiency of IEEE 1609.2. IEEE Trans. Veh. Technol. 2019, 68, 11577–11587. [Google Scholar] [CrossRef]
- Almuhaideb, A.M. Re-AuTh: Lightweight Re-Authentication with Practical Key Management for Wireless Body Area Networks. Arab. J. Sci. Eng. 2021, 46, 8189–8202. [Google Scholar] [CrossRef]
- Almuhaideb, A.M.; Algothami, S.S. Efficient Privacy-Preserving and Secure Authentication for Electric-Vehicle-to-Electric-Vehicle-Charging System Based on ECQV. J. Sens. Actuator Netw. 2022, 11, 28. [Google Scholar] [CrossRef]
- Burrows, M.; Abadi, M.; Needham, R.M. A Logic of Authentication. Proc. R. Soc. Lond. Math. Phys. Sci. 1989, 426, 233–271. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Das, A.K. 2PAKEP: Provably Secure and Efficient Two-Party Authenticated Key Exchange Protocol for Mobile Environment. IEEE Access 2018, 6, 30225–30241. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Lee, K.; Park, K.; Park, Y. Secure Authentication Protocol for Wireless Sensor Networks in Vehicular Communications. Sensors 2018, 18, 3191. [Google Scholar] [CrossRef]
- Park, K.; Park, Y.; Park, Y.; Goutham Reddy, A.; Das, A.K. Provably Secure and Efficient Authentication Protocol for Roaming Service in Global Mobility Networks. IEEE Access 2017, 5, 25110–25125. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K.; Choo, K.-K.R.; Kumar, N.; Park, Y. Efficient and Secure Time-Key Based Single Sign-On Authentication for Mobile Devices. IEEE Access 2017, 5, 27707–27721. [Google Scholar] [CrossRef]
- Armando, A.; Basin, D.; Cuellar, J.; Rusinowitch, M.; Viganò, L. AVISPA: Automated Validation of Internet Security Protocols and Applications. Available online: https://www.ercim.eu/publication/Ercim_News/enw64/armando.html (accessed on 11 April 2022).
- SPAN—Security Protocol Animator for AVISPA. Available online: http://people.irisa.fr/Thomas.Genet/span/ (accessed on 11 April 2022).
- Von Oheimb, D. The High-Level Protocol Specification Language HLPSL Developed in the EU Project AVISPA. Proceedings of APPSEM 2005 Workshop, Frauenchiemsee, Germany, 12–15 September 2005; pp. 1–17. [Google Scholar]
- Turuani, M. The CL-Atse Protocol Analyser. In Term Rewriting and Applications; Pfenning, F., Ed.; Springer: Berlin/Heidelberg, Germany, 2006; pp. 277–286. [Google Scholar] [CrossRef]
- Basin, D.; Mödersheim, S.; Viganò, L. OFMC: A Symbolic Model Checker for Security Protocols. Int. J. Inf. Secur. 2005, 4, 181–208. [Google Scholar] [CrossRef]
- Juels, A.; Brainard, J. Client Puzzles: A Cryptographic Countermeasure Against Connection Depletion Attacks. In Proceedings of the Networks and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 1 January 1999. [Google Scholar]
- Kilinc, H.H.; Yanik, T. A Survey of SIP Authentication and Key Agreement Schemes. IEEE Commun. Surv. Tutor. 2014, 16, 1005–1023. [Google Scholar] [CrossRef]















| Notations | Meaning |
|---|---|
| EC private key for entity | |
| EC public key for entity | |
| [1,…, n − 1] | integer, a random value between 1 to n − 1 |
| G | Base point in with order |
| Elliptic curve (EC) over a finite field with being a significant prime number | |
| One-way hash function | |
| Private reconstruction data | |
| Public reconstruction data | |
| Identity of entity | |
| Hash of certificate | |
| Certificates of entity |
| Notations | Meaning |
|---|---|
| EV | Electric vehicle |
| EAG | Energy aggregator |
| OP | Electricity operator |
| Elliptic curve (EC) over a finite field, with being a significant prime integer | |
| G | base point with order |
| EV/EAG’s true identity | |
| Pair of EC keys for entity | |
| Data used to construct entity ‘s private key | |
| Entity ’s certificate | |
| Message is signed by entity using ’s private key | |
| Using entity public key, entity encrypts message | |
| Entity ’s authenticator | |
| Hash of entity ’s authenticator | |
| Time stamp produced by | |
| TL | Time-life |
| Certificate hash | |
| Entity ’s Public/Private-key pair | |
| RK, RK’ | EV and OP/EAG and OP registration key |
| anonymous identity established by OP | |
| counter that is incremented by EV | |
| Nonce by | |
| EV’s authorization token, generated by EAG | |
| EV and EAG shared symmetric master key | |
| EV and EAG shared symmetric initial key | |
| EV and EAG shared symmetric temporary key | |
| EV and EAG shared symmetric session key | |
| One-way hash function | |
| Concatenation operation |
| Notations | Description |
|---|---|
| P|≡ X | Principal P believes statement X is true. |
| #(X) | Statement X is fresh. |
| X | P has jurisdiction over statement X. |
| X | P sees X, indicating that P has received statement X and could read it. |
| X | P once said the statement X. |
| (X, Y) | The formula (X, Y) includes the terms X or Y. |
| X combined with Y. | |
| The key K is used to encrypt either X or Y. | |
| The key K is used to hash X or Y. | |
| K is a secret parameter that P and Q share (or will share). Entity X’s public key. |
| Feature/Approach | Li et al. [25] | Rabieh and Wei [30] | Gunukula et al. [31] | Huang et al. [26] | Roman et al. [36] | Kim et al. [27] | Roman and Gondim [32] | Vaidya and Mouftah [38] | Kumar et al. [37] | ElGhanam et al. [28] | Xia et al. [35] | Proposed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2016 | 2017 | 2017 | 2018 | 2019 | 2019 | 2019 | 2020 | 2020 | 2021 | 2021 | 2022 | |
| Mutual Authentication | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | × | × | ✓ | ✓ | ✓ |
| Forward security | × | × | × | ✓ | ✓ | ✓ | ✓ | × | ✓ | ✓ | × | ✓ |
| Anonymity | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ | ✓ |
| Resist replay attack | ✓ | ✓ | × | ✓ | ✓ | ✓ | ✓ | × | ✓ | ✓ | ✓ | ✓ |
| Resist impersonation attack | × | × | × | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Resist MITM attack | ✓ | × | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
| Backward security | × | × | × | × | ✓ | × | × | × | × | × | × | ✓ |
| Un-linkability | × | ✓ | ✓ | × | × | × | ✓ | × | × | ✓ | × | ✓ |
| Traceability | × | × | × | × | × | × | × | × | × | × | ✓ | ✓ |
| Effective Reauthentication | × | × | × | × | × | × | × | × | × | × | × | ✓ |
| Revocation method | × | ✓ | × | × | × | × | ✓ | × | × | ✓ | × | ✓ |
| Joint key control | × | ✓ | × | ✓ | ✓ | ✓ | × | × | × | × | × | ✓ |
| Number of Messages (EV) | 2 | 2 | 5 | 3 | 2 | 2 | 5 | 3 | 1 | 2 | 1 | 2 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almuhaideb, A.M.; Algothami, S.S. ECQV-Based Lightweight Revocable Authentication Protocol for Electric Vehicle Charging. Big Data Cogn. Comput. 2022, 6, 102. https://doi.org/10.3390/bdcc6040102
Almuhaideb AM, Algothami SS. ECQV-Based Lightweight Revocable Authentication Protocol for Electric Vehicle Charging. Big Data and Cognitive Computing. 2022; 6(4):102. https://doi.org/10.3390/bdcc6040102
Chicago/Turabian StyleAlmuhaideb, Abdullah M., and Sammar S. Algothami. 2022. "ECQV-Based Lightweight Revocable Authentication Protocol for Electric Vehicle Charging" Big Data and Cognitive Computing 6, no. 4: 102. https://doi.org/10.3390/bdcc6040102
APA StyleAlmuhaideb, A. M., & Algothami, S. S. (2022). ECQV-Based Lightweight Revocable Authentication Protocol for Electric Vehicle Charging. Big Data and Cognitive Computing, 6(4), 102. https://doi.org/10.3390/bdcc6040102








