Abstract
Logistics and transport have become an increasingly important topic in recent years. In this kind of scenario, being able to offer added value to users means an important improvement in the services offered by the different companies. Different actors take part in the process of sending, transportation and collection of the different products through roads, ports and airports. During this process different aspects of security must be taken into account, since an error in one of them can cause major problems for public health, nature or even the economy of a country. With all this in mind, this work proposes a new system that allows us, through the use of wireless technologies such as Radio Frequency Identification, Global Positioning System, Wi-Fi Direct and mobile communication technologies, to automate the process of authentication and tracking of different products and goods. The proposed scheme allows through the use of the cloud the creation of a ubiquitous communications system for monitoring, control and even automation of repositioning orders automatically. In addition, the use of a system based on blockchain allows to carry out the whole process in an optimal way that guarantees the privacy and immutability of the data referring to the transports and merchandise. This work allows to reduce costs and improve the quality of the processes of sending, transport and reception of products for the different companies involved in the supply chain.
1. Introduction
A typical problem of the companies in the transport and logistics industry is the automation of the supervision and control of products, the inventory, the management of the relationship with customers, the tracking of fleets, etc. In addition to this, the increase of Internet sales and a new tendency called Amazonization [1], makes the supply chain logistic more relevant for the companies and difficult to manage every day. The main objective of this work is to improve existing solutions through a ubiquitous proposal based on different types of communications and devices for the management of information about the transported goods.
The protection of information security in real time is essential for the proper functioning of any organization in the transport and logistics sector. In particular, the tracking of merchandise should cover the current and past locations of each item, including its arrival or departure, and the registration of the identification of each item, its location, time and status. These data can be very useful for both customers and owners. On the one hand, a system that provides these data allows to verify how customers obtain benefits by improving the use of resources, reducing storage costs, the risk of loss or theft, etc. On the other hand, such data would help design and manage the Supply Chain, adding security and interesting information that may be useful for product management, and offering a new customer service.
Business systems are paying increasing attention to the performance, design and analysis of the Supply Chain to reduce costs, improve efficiency and effectiveness, and launch new products with greater benefits. Company managers know that the competitiveness of their products is achieved not only by optimizing the manufacturing lines, but also by improving the supply chain. The RAPEX report [2] indicates that the traceability of consumer goods would reduce fraud in Europe and allow action to be taken against unsafe products. This would be possible through the control of the goods arriving at the borders of the countries, including details such as the date and place of entry, as well as the origin and destination of the products. In addition, that report emphasizes the importance of monitoring and control at any time and place, which can help reduce the effects of dangerous goods that could enter the borders and reduce thefts that may arise. In addition, effective supply chain for essential goods can mean the difference between life and death in some specific non-commercial situations, such as disasters and emergencies.
Many studies estimate large losses due to surplus inventories and problems of coordination between the elements of the supply chain. In order to have an efficient supply chain, a rapid supply system must respond to changes in customer demand and warn of any interruption. In addition, a supply chain must include distribution planning, warehouse management and transport fleet, and sales, operations, programming and production planning. The data collection in real time of the supply chain allows a better management and planning of the data.
In the transport and logistics industry, the automation of merchandise supervision and control, inventory, customer relationship management, fleet tracking, etc., is a typical problem that must be solved by the companies of the sector.
Furthermore, companies must adapt their solutions for the incoming technologies that will be extended the incoming years. One of the most relevant techno-solutions related with this topic is the autonomous driving of fleets [3]. Nowadays, many companies are working and improving their autonomous vehicles. Tesla, Google, Uber and many other car companies are working on their solutions and they are very advanced. This will be a must in the supply chain logistic because will allow to reduce cost, improve time of delivery, improve efficiency and avoid problems related with people involved in the supply chain. However, companies must adapt their current solutions to this new paradigm.
The main objective of this research is to improve these solutions making use of ubiquitous technologies, through the administration of information about the transported merchandise using the proposed system, which includes different types of communications and devices [4]. The current expansion of ubiquitous technologies is possible due to three different factors. The first factor is the miniaturization of the components of the computer, since, as they are getting smaller, it is easier to connect practically anything, anywhere, at any time. The second factor is overcoming the limitation of the mobile telephony infrastructure. Finally, the third factor is the proliferation of applications and services that use the large amount of information created.
Blockchain and Distributed Ledger Technologies (DLTs) are among the most promising areas of new developments for the information society. The fact that DLT allows network participants to transfer and update information or records, and that this is done reliably, safely and efficiently, carries enormous potential. Smart contracts are generic programs that run on the blockchain using a ledger data structure, which acts autonomously and can handle items of substantial value. They make the blockchain programmable and open it for generic applications. A large part of the industry today is investigating the application of blockchain and DLT from Financial Technology to logistics, supply chain, insurance and many more. All of them would involve simplifying operations when exchanging data or goods among entities through reducing trust in intermediaries.
The solution for the supply chain management proposed here combines through a secure system many different ubiquitous technologies such as Long Term Evolution (LTE), Radio Frequency Identification (RFID), Wi-Fi Direct, Global Positioning System (GPS), Quick Response (QR) codes, Blockchain, etc. First, the proposed system can be used to compare the transported goods with the delivery note. In addition, the scheme allows to check, track and verify through the cloud, the goods transported from the origin to the destination. In addition, the system includes an interface that allows a quick verification of information relevant by the authorities. This information will benefit not only the authorities but also the company, because it can reduce time, control their products, guarantee their reliability, optimize transportation through the adaptive assignment of travel routes, and gain customers through the offer of added value. Finally, the use of blockchain allows that only authorized people can read the blocks, execute a smart contract and verify new blocks. This approach facilitates coordination among the supply chain management services and provides privacy, information integrity and traceability to the supply chain.
The organization of this work is as follows. Section 2 includes a brief review of some related work. Section 3 describes the methodology used to deal with information security aspects, and the most important risk factors of the proposed supply chain. Section 4 provides the details of the proposed ubiquitous system. Finally, Section 5 closes the document with some conclusions and open research lines.
2. Related Work
Given that the areas of transport and logistics, and of the supply chain management require addressing several problems related to reliability and security, ubiquitous technologies will be increasingly important in these sectors [5,6].
The work [7] includes a classification of several existing models to improve the supply chain, and explains the approaches studied for each model.
Most of the security problems existing in the supply chain are related to physical problems that can happen, such as regular scheduled stops, long nighttime stops, fencing breaks, stops near residential areas, unmanned trains and unlocked containers [8].
The main objective of this research is to improve the productivity and safety of the supply chain using the most advanced current ubiquitous technologies. In relation to this, the authors of [9] provide an analysis of efficiency and effectiveness after applying several strategies to improve supply chain. An extensive review of numerous papers related to the management of green supply chain is included in the work [10].
This work has taken into account the potential problem of the cloning of the used technology [11], since it would allow to alter the merchandise without being detected. To avoid this problem, we propose an ad-hoc solution for strong authentication based on Zero-Knowledge Proofs [12] and based on a previous solution presented in [13] which involved a ubiquitous system to automate the loading, unloading and checking during the route of merchandise. The company Agorabee [14] proposes a similar solution to this system but without some ad-hoc technologies involved and possibilities of connection with external entities.
In Google Play Store it is possible to find several applications to facilitate the tracking of products in the supply chain [15,16], which share some of the features proposed in this work. However, the solution proposed here is much wider than all of them since it allows, combining different advanced technologies, to track information of many operators through the web using any device such as a laptop, phone, tablet, etc., covering from the beginning, with the delivery note, and tracking the merchandise safely to the destination.
Regarding blockchain, one of the first applications of the concept can be found in [17] where a decentralized model was described to share information for finance. This proposal includes the concept of transaction. The design of the blockchain has been designed for the tracking of assets exchanged by different entities. Actually, in the most famous blockchain implementations no asset is exchanged and the property of a certain value is the result of the evaluation of the transaction. Finally, what is obtained is a list of the amount of assets exchanged between the various entities.
In [18] the authors rely on the use of publicly auditable contracts. The environment is deployed in a blockchain to improve the transparency of the data, to the access it and to usage it.
The use of RFID and blockchain as a whole is not a new solution, since the authors of [19] present the concept of using the mixture of these technologies to have a traceability of the agrifood supply chain. They present a theoretical scheme in order to be a solution to a complicated problem in China, food security. While it is true that this system uses RFID and blockchain, it only focuses on a specific use case, China’s agrifood industry. In addition, this work is a description of possible solutions to this particular case. Furthermore, the work [20] provides a solution of the supply chain focuses on business to business integration. Shipchain [14] is a startup company which solution helps to create a track and trace system across the entire supply chain by using blockchain. This solution has similarities with the proposed schema here, but lacks of connection possibilities with multiple entities and different automations with smart contracts that helps to avoid problems in the management of transported goods.
They referring to the electronic data exchanged over the internet, but just taking into account the exchange between the value-added service providers and the business partners.
3. Preliminaries
In this section, some terms and previous knowledge about used technologies, which are necessary for the correct understanding of the presented work, are addressed.
3.1. Blockchain
The definition of blockchain is based on the use of a data base in a distributed way. Each of the elements of this database has a temporary mark and a link to a previous document. From the moment in which a verified and sealed element is, it is theoretically impossible to modify it. This sealed in time is an operation called transaction. A transaction allows you to store information on which the system generates a temporary follow-up. In this way we can define that a blockchain is composed of a series of blocks that represent sets of confirmed transactions. In addition, each of the blocks of the system must contain, among other things, a code that links directly to the identifier of the previous block and some type of information related to the transaction itself, such as persons involved, number of cryptocurrencies, etc.). The link to the next block must also appear by means of its code that unequivocally identifies the next element of the chain. All the codes that unambiguously identify each block are calculated with a hash function used to generate a string.
3.2. Smart Contracts
As it is known, a contract in real life is nothing more or nothing less than an agreement between two or more parties. Within these you can find a series of requirements and conditions that are established by the participants that are part of it, all these participants must sign this agreement as verification of the execution of the contract. Until very recently the contracts have been written documents subject to the legal regulations of the laws.
3.3. Wi-Fi Direct
In this proposal Wi-Fi Direct is used to exchange information between devices, concretely between the RFID reader and smartphone. Wi-Fi Direct is an extension of Wi-Fi technology that adds new capabilities. One of its features the possibility of configuration of groups where a device, called Group Owner, is able to establish multiple P2P connections with different devices, called Group Clients. In this way, the Group Owner works as an access point and the other devices join the group as clients, with the possibility of establishing a unique P2P connection with the device playing the role of Group Owner.
The main advantage of Wi-Fi Direct compared with other similar technologies is that all necessary changes with respect to the traditional Wi-Fi are done at software level. This fact assures backward compatibility with all certified Wi-Fi devices, so this technology is being widespread easily.
4. Methodology
In this work we have taken into account a combination of international safety standards, best industrial practices, regional legislative documentation and related experience. With all this in mind, the proposed solutions provide security in the supply chain and prevent and limit the amount of cargo thefts, increasing visibility and efficiency.
There are several recommendations to protect supply chain systems, such as a set of minimum security requirements that are provided to all logistics partners. Some of them are: sealed containers with high security locks, products wrapped with non-descriptive plastic to confuse potential criminals, and implementation of an information security system to ensure that unauthorized personnel do not have access to the information of the product or transport routes.
The aforementioned theoretical recommendations must be applied in practice. Therefore, the security of the proposed system is also based on their application. While applying them, the proposed system allows improving the supply chain by providing information in real time, and setting up alarms in case of changes in goods containers in order to reduce thefts.
Not having a centralized supply chain management can negatively affect purchases, manufacturing and time to market in supply chain, which could generate problems in the financial strategy of the companies. The management of security risk is a fundamental part of the supply chain management system to ensure that risks are identified throughout the value chain and mitigated to meet financial objectives. In particular, the phases of the supply chain that the system must cover are especially manufacturing and distribution, suppliers, transport, retailers, arrivals at the central warehouse, container tracking at docks, cranes or vessels and a wholesale and retail distribution center.
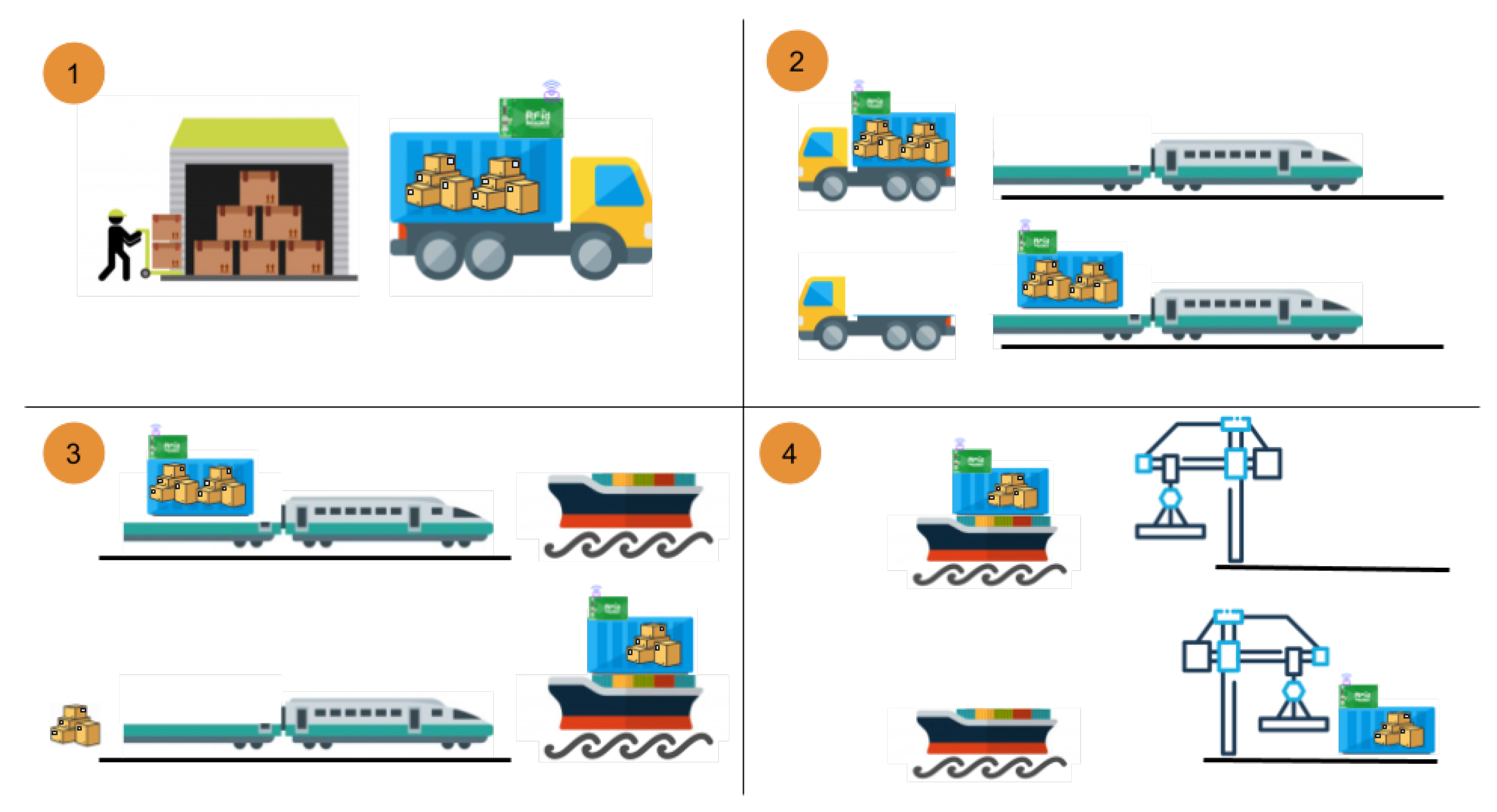
As it is known, different agents participate in the transfer of merchandises from the moment they leave the factory until they reach the final destination. An example can be observed in Figure 1, where multiple agents and types of transport are used (trucks, trains, ships, planes, etc.).
Figure 1.
Transportation System Proposal General View.
In traditional transportation systems if a merchandise or part of it is lost (like in Figure 1, Step 3), we can not know in which part of the supply chain it has happened. To avoid this problem, a new system is presented in this work. In the proposed system, the first step consists in put a RFID tag in every merchandise of the container (as it is shown in Figure 1, Step 1).
Each container has a QR code associated with it, that can be read to know all the information of the container and its merchandises. Moreover, the container has a RFID reader that is the responsible of check if all the merchandise is in the container every time that the container is moved from the different transport means and every few minutes (see Figure 1, Steps 2 and 3).
Every time that the container is moved from the different transportation systems of the supply chain, this checking is done again and the result state is written in the blockchain. If the container has all the merchandise with which it left the factory, a correct exchange is made. But in case of detecting the lack of any of the labels this anomaly is captured in a blockchain. Finally, when the container reaches its final destination (see Figure 1, Step 4), it can always be checked before opening it if its content has been altered or is completely correct.
All the possible anomalies and the trace of everything that has happened in the supply chain is registered thanks to the use of smart contracts.
5. Smart Contract Proposal
The use of smart contracts is one of the fundamental points of the proposed system. The defined smart contract is used every time that the merchandise is exchanged by the different parts of the supply chain.
On the one hand, each container has an identifier and on the other hand, each container has a series of RFID tags that are responsible for identifying the items that are inside each container.
Every time a carrier exchange is made, the performance of this action is recorded by means of the smart contract defined. In this way, the container issuer is included in the contract with the information of the new person responsible for it, who will be the receiver and the location where this merchandise exchange takes place.
To estimate every time the status of the container, they are classified using a code in the contract. State represents the status of the container: Complete (refers to the state in which all the RFID Tags are inside the container), Incomplete (is used when one or more Tags are lost) and Finished (is the state used when a container is in the final destination and the journal has finished). Note that each user has an identification associated to his/her own address and also an entity to which he/she belongs.
Related to the merchandise exchange, the contract also includes when someone generates this action. If everything is right, that means all the container tags all inside the container the exchange is generated and the status of the container is Complete, otherwise the status of the container changes to Incomplete and the lost is stored on the blockchain. This update is made by using a function that is specifically defined.
Several functions exist related to the internal operation of the smart contract and the evolution of the exchange and the tracking. On the one hand, to know the status of a container at all times by means of its identifier, the function getContainerState() has been created. The information about the tags that a specific container contains is obtained by calling the function getTags(). On the other hand, in order to know in real time all the information about the location of a container and its state, function trackContainer() has been created. On the same way, to perform real-time tracking of one of the RFID tags, the trackTag() function has been created.
One of the contributions to highlight this contract is that at any time a supervisor of the operation or a police officer can check the status of the container. To achieve this, the event ContainerVerification() is used, in which the revision of the contents of a container by a specific supervisor is recorded. The result of this function will not only update the status of the container, but will also record the result of this verification in the chain of blocks.
6. Proposed System
The system designed to control the products from its manufacture to its delivery to the final client through the use of ubiquitous technologies presented here facilitates the work to the customs authorities and to all the people involved in the transit of merchandise.
The new system allows to verify if the merchandise collected is correct by detecting possible errors in the delivery process. In addition, it provides an online verification mechanism and stores a complete history of freight transport. This whole process is carried out taking into account the security requirements involved in the supply chain process through the use of cryptographic algorithms to prevent unauthorized reading, writing or modification of labeling merchandise, and to detect falsified information.
The proposed scheme has a minimal cost, since it is based on affordable and common devices such as low-cost RFID and smartphones, so it reduces the economic costs through the use of low-cost passive tags.
RFID technology is currently exploited by most companies related to the logistics of supply chain [21,22] because it allows them to validate information about products and locate them easily and quickly within any container.
Normally, most supply chains are formed by five types of participants: supplier, manufacturer, distributor, retailer and customer. The proposed scheme has different parts according to the five stages in the supply chain, including the generation and extraction of QR data of container goods, the RFID validation of goods, the web service for fleet tracking, the Wi-Fi P2P application for customs verification and the blockchain and smart contracts for the guarantee the traceability of the merchandise.
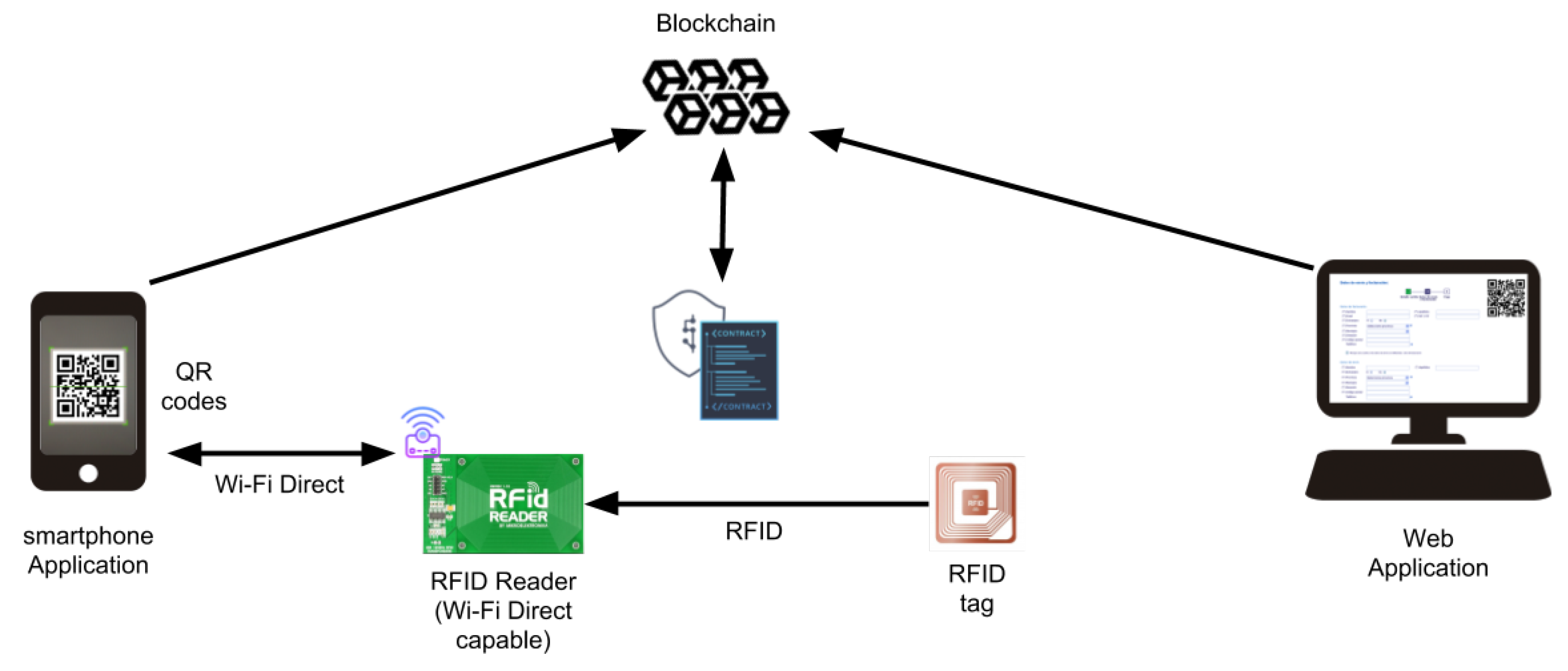
The complete flow of technologies used in the proposal is shown in Figure 2. In this Figure, the communication of the different parts of the system is shown with the arrows, that indicates an information flow. Some communications, like the smartphone and web application query to the blockchain using the oracle, can be made in a parallel way, allowing that more than one user or authority can verify the correctness and trace of the container and his merchandise.
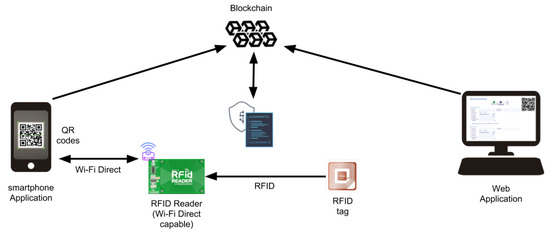
Figure 2.
Relationship between technologies for the ubiquitous supply chain system.
The operation of the proposed system starts with this first phase, which is the generation of the bill of goods, which includes relevant information about the products that are inside the container, apart from other information. This receipt has a specific format consisting on related enterprises and carriers, origin and destination places and corresponding dates, receipt ID, 13-character codes identifying the products and quantity of each product, and other relevant information.
The second stage is executed by the carrier through the transport-tracking app. The smartphone reads the QR code using the app and its content is decrypted with the shared key that was previously stored in the device. After reading the code, the driver has all the data of the QR bill of goods stored in his/her smartphone.
The development of the reading of QR codes in the Android platform was done by using a library called Zxing.
Later, information is stored in the local device into an SQLite database. All the information related to origin and destinations can be also seen in the device by using Google Maps Android API. At this moment, the information is written in the developed blockchain as a new block to provide a new security layer to prevent possible data modification of the information.
To begin with the process of tracking the container and its contents, a first exchange with the already named smart contract is generated. The generation of the smart contract is needed for the next steps of the proposed system in the supply chain. In the smart contract there are some relations. On the on hand, the association between the tags and the container itself (containderID). On the other hand, the initialization of the first owner of the container from the moment it leaves the factory (from the senderID to the receiverID).
This stage is especially interesting not only in the loading of merchandise in the container, but also in every delivery of merchandise to reduce possible errors. Furthermore, by using RFID readers in the container it is also possible to know the approximate position where a product is.
Moreover, using the blockchain system in combination with the periodic product check, the owners can know where a product is and which is the involved carrier with quite precision.
Secondly, specific details about the path of the merchandise can be discovered with traceability, allowing the detection of possible bottlenecks to improve the next parts of the route. Every time a carrier exchange is made, the performance of this action is recorded in the blockchain so that the users can check this information.
Another interesting option of the system is the use of the short-distance interface to facilitate authorities work and merchandise management and checking.
In order to do that, the app has an interface that the identified agents or a supervisor of the operation can use to examine the content of every container without looking inside.
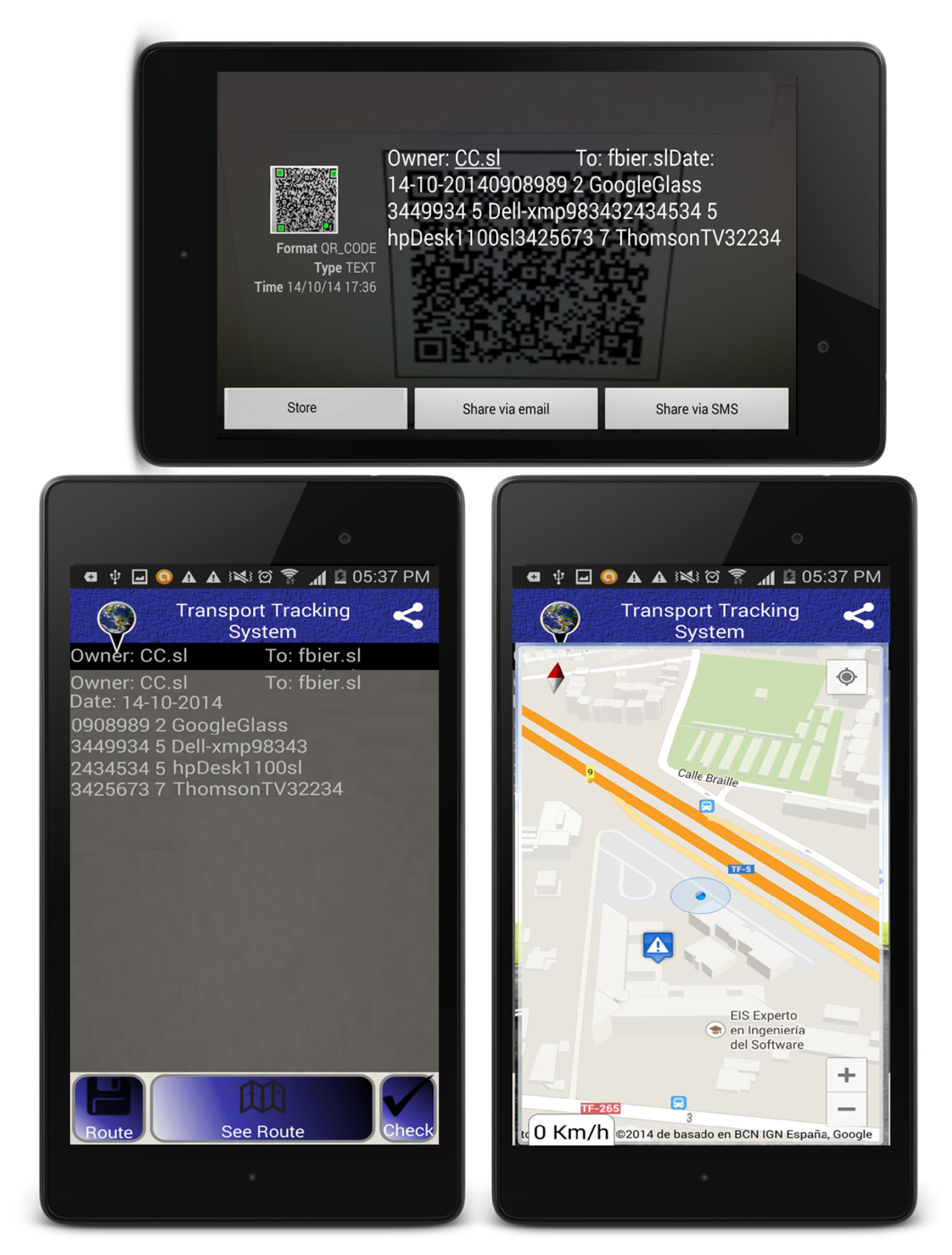
A mobile application has been developed that provides real-time tracking of containers as well as communication with the blockchain (it is shown in Figure 3).
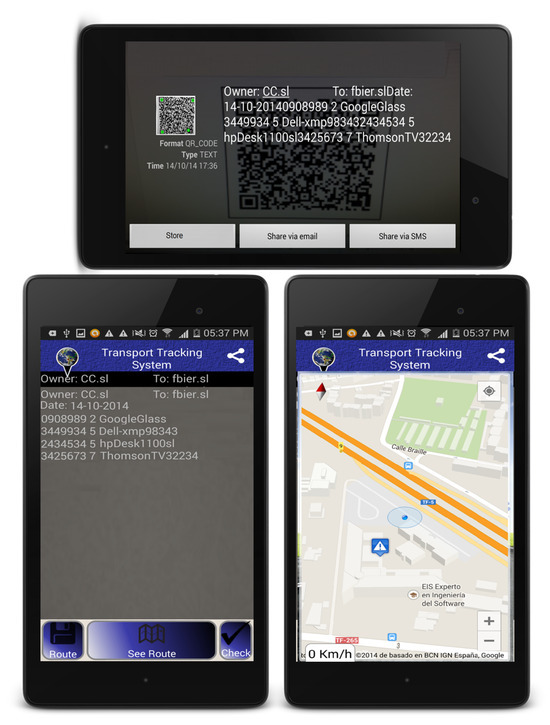
Figure 3.
Android implementation of the supply chain tool.
The server in the cloud is secured to to guarantee data privacy and security. The Web Platform has been implemented by using a NodeJS server with Firebase for data and Express framework to create the web services for NodeJS. For the responsive front-end, Bootstrap framework and GMaps API have been used.
7. Conclusions
In this work, a new system has been proposed to solve different problems that usually appears in logistic. The use of new ubiquitous technologies in logistics management allows to improve the efficiency and security of the Supply Chain.
The developed system offers a new tracking system that allows to verify the charge of the container not only in the moments of loading and delivery, which is when most of the problems generally occur, but also at any time and place.
The use of a blockchain system guarantee the integrity of all the information in the supply chain. Moreover, the use of smart contracts in addition to the blockchain allows to automatize some frequent task in the system, as could be a periodic scan to check if the merchandise is in the container, or the control of the goods by the authorities in personalized areas. In combination with this, the use of an interface to control the products allows faster and easier control by part of the authorities. The different tools implemented in this work are in a prototype phase and new features can be added in the future.
Funding
This research was funded by the Government of the Canary Islands grant number TESIS2015010102 and TESIS-2015010106, the University of La Laguna, and the CajaCanarias Foundation under Project DIG02-INSITU.
Acknowledgments
Research supported by TESIS2015010102, TESIS2015010106, RTC-2014-1648-8, TEC2014-54110-R, MTM-2015-69138-REDT and DIG02-INSITU.
Conflicts of Interest
The authors declare no conflict of interest. The founding sponsors had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, and in the decision to publish the results.
References
- Golumbia, D. The Amazonization of Everything. Jacobin, August 2015. Available online: http://blogs.ubc.ca/politicalgeography/files/2015/09/The-Amazonization-of-Everything.pdf (accessed on 1 November 2019).
- European Rapex Reports. Available online: http://ec.europa.eu/consumers/safety/rapex/ (accessed on 1 November 2019).
- Geiger, A.; Lenz, P.; Urtasun, R. Are we ready for autonomous driving? the kitti vision benchmark suite. In Proceedings of the 2012 IEEE Conference on Computer Vision and Pattern Recognition, Providence, RI, USA, 16–21 June 2012; IEEE: Piscataway, NJ, USA, 2012; pp. 3354–3361. [Google Scholar]
- Angeles, R. RFID Technologies: Supply-Chain Applications and Implementation Issues. Inf. Syst. Manag. 2005, 22, 51–65. [Google Scholar] [CrossRef]
- Simchi-Levi, D.; Kaminsky, P.; Simchi-Levi, E.; Shankar, R. Designing and Managing the Supply Chain: Concepts, Strategies and Case Studies; Tata McGraw-Hill Education: New York, NY, USA, 2008. [Google Scholar]
- Christopher, M. Logistics And Supply Chain Management: Creating Value-Adding Networks; Pearson Education: London, UK, 2005. [Google Scholar]
- Beamon, B.M. Supply Chain Design and Analysis: Models and Methods. Int. J. Prod. Econ. 1998, 55, 281–294. [Google Scholar] [CrossRef]
- Lee, H.L.; Whang, S. Higher supply chain security with lower cost: Lessons from total quality management. Int. J. Prod. Econ. 2005, 96, 289–300. [Google Scholar] [CrossRef]
- Turker, D.; Altuntas, C. Sustainable supply chain management in the fast fashion industry, An analysis of corporate reports. Eur. Manag. J. 2014, 32, 837–849. [Google Scholar] [CrossRef]
- Srivastava, S.K. Green supply chain management: A state-of-the-art literature review. Int. J. Manag. Rev. 2007, 9, 53–80. [Google Scholar] [CrossRef]
- Ranasinghe, D.C.; Devadas, S.; Cole, P.H. A Low Cost Solution to Cloning and Authentication Based on a Lightweight Primitive. In Networked RFID Systems and Lightweight Cryptography, Part IV; Springer: Berlin/Heidelberg, Germany, 2008; pp. 289–309. [Google Scholar]
- Caballero-Gil, P.; Caballero-Gil, C.; Molina-Gil, J.; Hernandez-Goya, C. Self-Organized Authentication Architecture for Mobile Ad-hoc Networks. In Proceedings of the 6th International Symposium on Modeling and Optimization in Mobile, Ad-Hoc, and Wireless Networks, Berlin, Germany, 1–3 April 2008; pp. 217–224. [Google Scholar]
- Caballero-Gil, C.; Molina-Gil, J.; Caballero-Gil, P.; Quesada-Arencibia, A. IoT application in the supply chain logistics. In Proceedings of the International Conference on Computer Aided Systems Theory, Las Palmas de Gran Canaria, Spain, 10–15 February 2013; pp. 55–62. [Google Scholar]
- ECN Europe. RFID-Style Fleet Tracking Solution ‘10x Cheaper’ than Current GPS Alternatives. Posted on 7 November 2011.. Available online: https://ecneurope.wordpress.com/2011/11/07/rfid-style-fleet-tracking-solution-’10x-cheaper’-than-current-gps-alternatives/ (accessed on 1 November 2019).
- Package Buddy. Available online: play.google.com (accessed on 1 November 2019).
- Package Tracker Pro. Available online: play.google.com (accessed on 1 November 2019).
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Working Paper. 2009. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 1 November 2019).
- Neisse, R.; Steri, G.; Nai-Fovino, I. A blockchain-based approach for data accountability and provenance tracking. In Proceedings of the 12th International Conference on Availability, Reliability and Security, Reggio Calabria, Italy, 29 August–1 September 2017; ACM: New York, NY, USA, 2017. [Google Scholar]
- Feng, T. An agri-food supply chain traceability system for China based on RFID & blockchain technology. In Proceedings of the 2016 13th International Conference on Service Systems and Service Management (ICSSSM); Kunming, China, 24–26 June 2016, IEEE: Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar]
- Korpela, K.; Hallikas, J.; Dahlberg, T. Digital supply chain transformation toward blockchain integration. In Proceedings of the 50th Hawaii International Conference on System Sciences, Hilton Waikoloa Village, HI, USA, 4–7 January 2017. [Google Scholar]
- Bouet, M.; Santos, A.L.D. RFID Tags: Positioning Principles and Localization Techniques. In Proceedings of the 1st IFIP Wireless Days, Dubai, UAE, 24–27 November 2008; pp. 1–5. [Google Scholar]
- King, B.; Zhang, X. Securing the pharmaceutical supply chain using RFID. In Proceedings of the International Conference on Multimedia and Ubiquitous Engineering, Seoul, Korea, 26–28 April 2007; pp. 26–28. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).