A Lightweight Authentication Protocol for UAVs Based on ECC Scheme
Abstract
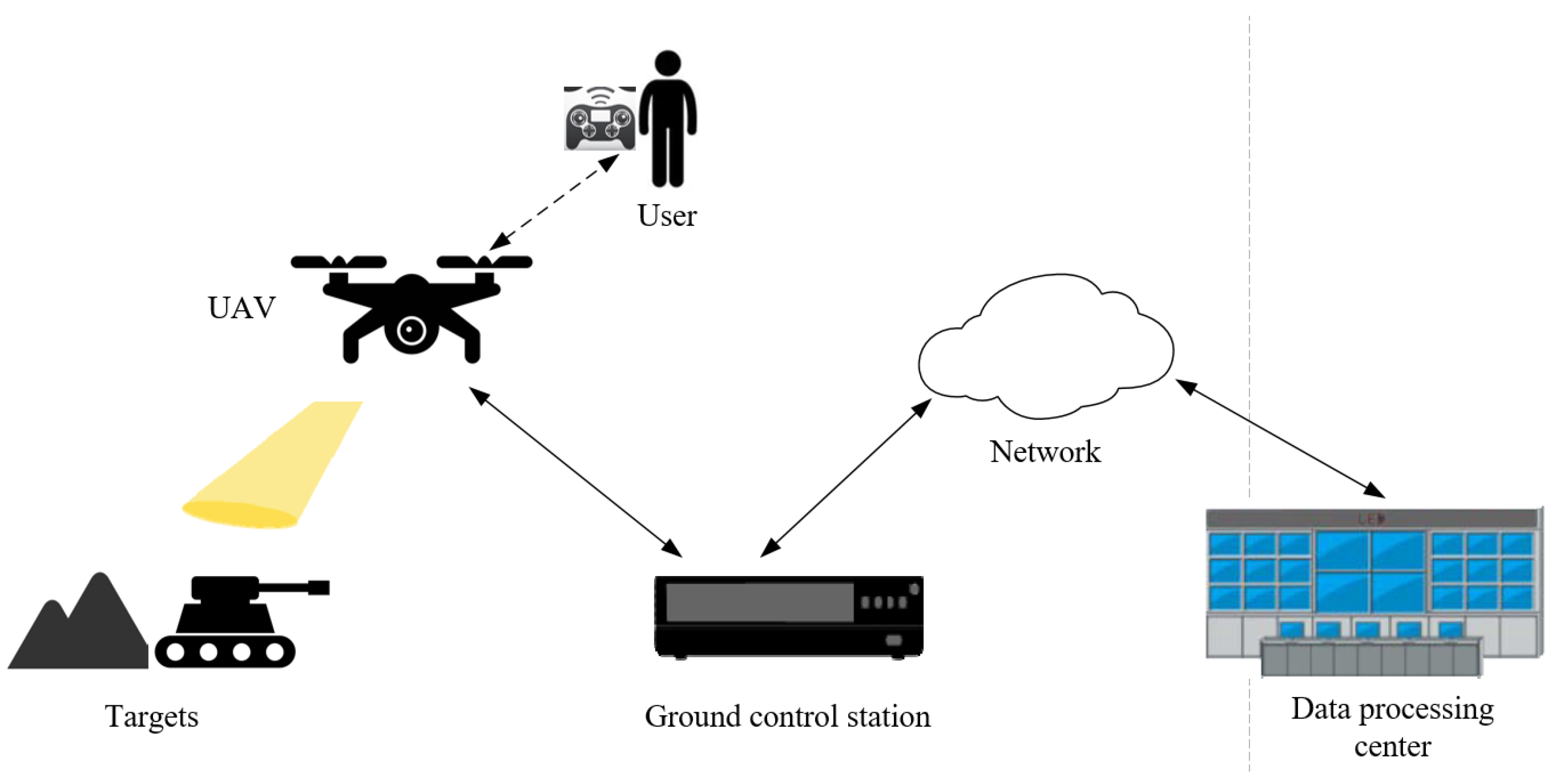
:1. Introduction
2. Background and Related Works
2.1. Elliptical Curve Cryptography Scheme
2.2. EDHOC Scheme
2.3. Problem Analysis
- Public key preset problem.
- Session key backward security.
3. Proposed Scheme
3.1. Design Principles
3.2. Symbols and Meanings
3.3. Pre-Registration Phase
3.4. Authentication Phase
- (1)
- Step 1
- (2)
- Step 2
- (3)
- Step 3
- (4)
- Step 4
- Decode message_2 and record the timestamp to determine the freshness of the message.
- XOR the Auth_G with the key K_1 to decrypt the Auth_G field.
- Verify MAC_2 using the algorithm in the selected cipher suite.
- (5)
- Step 5
- (6)
- Step 6
3.5. Session Key Update Phase
- Decode the message and obtain and check the freshness of the message.
- Calculate random challenges.
- Calculate and check:z × P = G_X′ + c × P_D?
4. Security Analysis
4.1. Security Properties Analysis
4.2. Security Properties Proof
5. Time Cost Analysis
5.1. Computation Cost Analysis
- For the authentication phase:
- For the session key update phase:
5.2. Communication Cost Analysis
- Message Interaction Cost
- Message Size Cost
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mozaffari, M.; Saad, W.; Bennis, M.; Nam, Y.-H.; Debbah, M. A tutorial on UAVs for wireless networks: Applications, challenges, and open problems. IEEE Commun. Surv. Tutor. 2018, 21, 2334–2360. [Google Scholar] [CrossRef]
- Hayat, S.; Yanmaz, E.; Muzaffar, R. Survey on Unmanned Aerial Vehicle Networks for Civil Applications: A Communications Viewpoint. IEEE Commun. Surv. Tutor. 2016, 18, 2624–2661. [Google Scholar] [CrossRef]
- Motlagh, N.H.; Taleb, T.; Arouk, O. Low-Altitude Unmanned Aerial Vehicles-Based Internet of Things Services: Comprehensive Survey and Future Perspectives. IEEE Internet Things J. 2016, 3, 899–922. [Google Scholar] [CrossRef]
- Jangirala, S.; Das, A.K.; Kumar, N.; Rodrigues, J. Tcalas: Temporal credential-based anonymous lightweight authentication scheme for internet of drones environment. IEEE Trans. Veh. Technol. 2019, 68, 6903–6916. [Google Scholar]
- Li, B.; Fei, Z.; Zhang, Y.; Guizani, M. Secure UAV Communication Networks over 5G. IEEE Wirel Commun. 2019, 26, 114–120. [Google Scholar] [CrossRef]
- Gaurang, B.; Naren, N.; Vinay, C.; Biplab, S. SHOTS: Scalable Secure Authentication-Attestation Protocol Using Optimal Trajectory in UAV Swarms. IEEE Trans. Veh. Technol. 2022, 71, 5827–5836. [Google Scholar]
- Kaufman, C.; Hoffman, P.; Nir, Y.; Eronen, P.; Kivinen, T. RFC 7296: Internet Key Exchange Protocol Version 2 (IKEv2); RFC Editor; IETF: Fremont, CA, USA, 2014. [Google Scholar]
- Rescorla, E. RFC 8446: The Transport Layer Security (TLS) Protocol Version 1.3; RFC Editor; IETF: Fremont, CA, USA, 2018. [Google Scholar]
- Zhong, C.; Yao, J.; Xu, J. Secure uav communication with cooperative jamming and trajectory control. IEEE Commun. Lett. 2018, 23, 286–289. [Google Scholar] [CrossRef]
- Zeng, Y.; Zhang, R. Energy-efficient uav communication with trajectory optimization. IEEE Trans. Wirel. Commun. 2017, 16, 3747–3760. [Google Scholar] [CrossRef]
- Grover, A.; Berghel, H. A survey of RFID deployment and security issues. Inf. Process. Syst. 2011, 7, 561–580. [Google Scholar] [CrossRef]
- Gope, P.; Sikdar, B. An efficient privacy-preserving authenticated key agreement scheme for edge-assisted internet of drones. IEEE Trans. Veh. Technol. 2020, 69, 13621–13630. [Google Scholar] [CrossRef]
- Gope, P.; Millwood, O.; Saxena, N. A provably secure authentication scheme for RFID-enabled UAV applications. Comput. Commun. 2021, 166, 19–25. [Google Scholar] [CrossRef]
- Khattab, A.; Jeddi, Z.; Amini, E.; Bayoumi, M. RFID Security Threats and Basic Solutions; Springer International Publishing: Cham, Switzerland, 2017; pp. 27–41. [Google Scholar]
- Lopez, P.P.; Hernandez-Castro, J.C.; Estevez-Tapiador, J.M.; Ribagorda, A. RFID Systems: A Survey on Security Threats and Proposed Solutions; Springer: Berlin/Heidelberg, Germany, 2006; pp. 159–170. [Google Scholar]
- Suh, G.; Devadas, S. Physical unclonable functions for device authentication and secret key generation. In Proceedings of the Design Automation Conference (DAC ’07), San Diego, CA, USA, 4–6 June 2007. [Google Scholar]
- Sung, J.Y.; Ashok, K.D.; Youngho, P.; Pascal, L. SLAP-IoD: Secure and lightweight authentication protocol using physical unclonable functions for internet of drones in smart city environments. IEEE Trans. Veh. Technol. 2022, 71, 10374–10388. [Google Scholar]
- Bansal, G.; Sikdar, B. S-MAPS: Scalable Mutual Authentication Protocol for Dynamic UAV Swarms. IEEE Trans. Veh. Technol. 2021, 70, 12088–12100. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J. Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Ever, Y.K. A secure authentication scheme framework for mobile-sinks used in the Internet of Drones applications. Comput. Commun. 2020, 155, 143–149. [Google Scholar] [CrossRef]
- Tao, X.; Jun, H. An Identity Authentication Scheme Based on SM2 Algorithm in UAV Communication Network. Wirel. Commun. Mob. Comput. 2022, 4, 1–10. [Google Scholar]
- Lin, L.; Xiao, F.L.; Yu, L.W.; Tan, L. CSECMAS: An Efficient and Secure Certificate Signing Based Elliptic Curve Multiple Authentication Scheme for Drone Communication Networks. Appl. Sci. 2022, 12, 9203. [Google Scholar] [CrossRef]
- Hankerson, D.; Vanstone, S.; Menezes, A.J. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Cohn-Gordon, K.; Cremers, C.; Garratt, L. On post-compromise security. In Proceedings of the 2016 IEEE 29th Computer Security Foundations Symposium (CSF), Lisboa, Portugal, 27 June–1 July 2016. [Google Scholar]
- He, Y.X.; Sun, F.J.; Li, Q.A.; He, J.; Wang, L.M. A survey on public key mechanism in wireless sensor networks. Jisuanji Xuebao/Chin. J. Comput. 2020, 43, 381–408. [Google Scholar]
- Huang, Z.; Wang, Q. A PUF-based unified identity verification framework for secure IoT hardware via device authentication. World Wide Web 2020, 23, 1057–1088. [Google Scholar] [CrossRef]
- Li, X.; Liu, J.; Ding, B.; Li, Z.; Wu, H.; Wang, T. A SDR-based verification platform for 802.11 PHY layer security authentication. World Wide Web 2020, 23, 1011–1034. [Google Scholar] [CrossRef]
- Shao, S.; Chen, F.; Xiao, X.; Gu, W.; Lu, Y.; Wang, S.; Tang, W.; Liu, S.; Wu, F.; He, J.; et al. IBE-BCIOT: An IBE based cross-chain communication mechanism of blockchain in IoT. World Wide Web 2021, 24, 1665–1690. [Google Scholar] [CrossRef]
- Xu, X.; Zhu, P.; Wen, Q.; Jin, Z.; Zhang, H.; He, L. A secure and efficient authentication and key agreement scheme based on ECC for telecare medicine information systems. J. Med. Syst. 2014, 38, 1–7. [Google Scholar] [CrossRef]
- Wu, F.; Li, X.; Sangaiah, A.K.; Xu, L.; Kumari, S.; Wu, L.; Shen, J. A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Gener. Comput. Syst. 2018, 82, 727–737. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Wei, F.; Tian, Y.; Shen, J.; Yang, Y. An untraceable temporal-credential-based two-factor authentication scheme using ECC for wireless sensor networks. J. Netw. Comput. Appl. 2016, 76, 37–48. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Bhuiyan, M.Z.A.; Wu, F.; Karuppiah, M.; Kumari, S. A robust ECC-based provable secure authentication protocol with privacy preserving for industrial Internet of Things. IEEE Trans. Industr. Inform. 2018, 14, 3599–3609. [Google Scholar] [CrossRef]
- Li, X.; Niu, J.; Kumari, S.; Wu, F.; Sangaiah, A.K.; Choo, K.-K.R. A three-factor anonymous authentication scheme for wireless sensor networks in IoT environments. J. Netw. Comput. Appl. 2018, 103, 194–204. [Google Scholar] [CrossRef]
- Chang, I.P.; Lee, T.F.; Lin, T.H.; Liu, C.M. Enhanced two-factor authentication and key agreement using dynamic identities in wireless sensor networks. Sensors 2015, 15, 29841–29854. [Google Scholar] [CrossRef] [PubMed]
- Lu, Y.R.; Xu, G.Q.; Li, L.X.; Yang, Y. Anonymous three-factor authenticated key agreement for wireless sensor networks. Wirel. Netw. 2019, 25, 1461–1475. [Google Scholar] [CrossRef]
- Chatterjee, S.; Roy, S.; Das, A.K.; Chattopadhyay, S.; Kumar, N.; Vasilakos, A.V. Secure biometric-based authentication scheme using chebyshev chaotic map for multi-server environment. IEEE Trans. Dependable Secur. Comput. 2018, 15, 824–839. [Google Scholar] [CrossRef]
- Saeed, U.J.; Irshad, A.A.; Fahad, A.; Adnan, S.K. A Verifiably Secure ECC Based Authentication Scheme for Securing IoD Using FANET. IEEE Access 2022, 10, 95321–95343. [Google Scholar]
- Bander, A.A.; Ahmed, B.; Shehzad, A.C. A Resource-Friendly Authentication Protocol for UAV-Based Massive Crowd Management Systems. Secur. Commun. Netw. 2021, 2021, 3437373. [Google Scholar] [CrossRef]
- Deebak, B.D.; Al-Turjman, F. A smart lightweight privacy preservation scheme for IoT-based UAV communication systems. Comput. Commun. 2020, 162, 102–117. [Google Scholar] [CrossRef]





| Symbols | Meaning |
|---|---|
| DEV, GWN | the UAV DEV, its ground control station (gateway) GWN |
| P_A, P_B | Ephemeral public key for device A and B |
| P_D, P_G | Authentication public key of the device and the gateway |
| ID_CRED_D, ID_CRED_G | The public key identifier of the device and the gateway |
| AEAD(K;(Plaintext)) | Additional data are encrypted with authentication using a key K derived from the shared secret |
| Extract | Pseudorandom key generation function |
| Expand | Symmetric key generation function |
| MAC | Message authentication code |
| tD | The current timestamp of the device |
| tG | The current timestamp of the gateway |
| ∆t | Maximum time interval allowed |
| H_m | Hash of message data |
| H(*) | Collision resistant hash function |
| || | Connect operation |
| ⊕ | XOR operation |
| Security Properties | LAPEC | EDHOC |
|---|---|---|
| Backward Security | ✓ | ✗ |
| Anti-replay Attack | ✓ | ✓ |
| Forward Security | ✓ | ✓ |
| Session Key Confidentiality | ✓ | ✓ |
| Anti-Camouflage Attack | ✓ | ✓ |
| Oracle | Description |
|---|---|
| Creat (D, r, G) | Create a new session oracle with peer G as D’s identity r |
| Send (D, i, M) | Execute and return the result at the ith session oracle of D |
| Corrupt (C) | Leak C’s long-term key |
| Test-session (s) | If b = 1, C outputs the current session key SK. If b = 0, C returns a random number. If no session key is generated, returns null. |
| Randomness (C, i) | Leak the random number in the ith session of C |
| Session-key (s) | Leaked session key SK |
| Hsm (C) | Hardware security module for C |
| Guess (b) | End game |
| Scheme | Time Cost | Total | ||
|---|---|---|---|---|
| User | GWN | UAV | ||
| Xu [22] | - | - | - | 9TH + 4TSM |
| Wu F [23] | 2TSM + 13TH | 14TH | 2TSM + 4TH | 22TH |
| Jiang [24] | 8TH + 2TSM | 9TH + TSM | 6TH | 23TH + 3TSM |
| Li X [25] | 8TH + 3TSM | 7TH + TSM | 4TH + 2TSM | 19TH + 6TSM |
| Li X [26] | 2TSM + 8TH | TSM + 9TH | 4TH | 3TSM + 21TH |
| Chang [27] | 11TH + 5TSM | 10TH + 4TSM | 4TH + TSM | 25TH + 10TSM |
| Lu [28] | - | - | - | 6TSM + 13TH + 4TS |
| Saeed [29] | TSM + 3TH + 2TS | 2TSM + 3TH | 2TSM + 3TH + 2TS | 5TSM + 9TH + 4TS |
| Bander [30] | 3TSM + 6TH + 3TS | TSM + 9TH + 7TS | 2TSM + 5TH + 3TS | 6TSM + 21TH + 13TS |
| Deebak [31] | - | - | - | 19TH + 12TEX |
| LAPEC | - | 3TSM + 6TH + 2TS | 3TSM + 6TH + 2TS | 6TSM + 12TH + 4TS |
| Phase | LAPEC (Bytes) | EDHOC (Bytes) |
|---|---|---|
| Pre-registration | 32 + 32 | 0 |
| Authentication | 36 + 65 + 128 | 38 + 66 + 129 |
| Key Update | 64 + 32 | 32 + 32 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, S.; Liu, Y.; Han, Z.; Yang, Z. A Lightweight Authentication Protocol for UAVs Based on ECC Scheme. Drones 2023, 7, 315. https://doi.org/10.3390/drones7050315
Zhang S, Liu Y, Han Z, Yang Z. A Lightweight Authentication Protocol for UAVs Based on ECC Scheme. Drones. 2023; 7(5):315. https://doi.org/10.3390/drones7050315
Chicago/Turabian StyleZhang, Shuo, Yaping Liu, Zhiyu Han, and Zhikai Yang. 2023. "A Lightweight Authentication Protocol for UAVs Based on ECC Scheme" Drones 7, no. 5: 315. https://doi.org/10.3390/drones7050315
APA StyleZhang, S., Liu, Y., Han, Z., & Yang, Z. (2023). A Lightweight Authentication Protocol for UAVs Based on ECC Scheme. Drones, 7(5), 315. https://doi.org/10.3390/drones7050315





