A Review of Physical Layer Security in Aerial–Terrestrial Integrated Internet of Things: Emerging Techniques, Potential Applications, and Future Trends
Abstract
:1. Introduction
1.1. Background and Motivations
- Information Eavesdropping: Due to the broadcast nature of ATI-IoT, any user within communication coverage can receive information, so aerial–terrestrial integrated communications are at risk of eavesdropping [20]. Currently, ATI-IoT mainly uses the upper-layer key encryption technique to protect information security. However, the security of the key encryption technique is based on the limited computing capacity of eavesdropping users [21]. Therefore, the application area of key encryption techniques is limited. In addition, complex encryption algorithms and key distribution mechanisms also limit the use of key encryption techniques in future miniaturized and dense B5G networks [22].
- Information Interference: A large number of communication devices and data transmission requirements make various wireless signals superimposed on each other [23]. However, limited spectrum and space resources make it difficult to ensure the uninterrupted transmission of information in the current region. Therefore, with the use of interference within the network and interference between networks, malicious interference users can transmit interference signals to interfere with or even prevent legitimate users from correctly receiving information, resulting in the interruption of information transmission [24].
- Unauthorized Access: Due to the adoption of unified communication protocols and standards, ATI-IoT is easy to access and configure. However, malicious users can pretend to be legitimate users according to the characteristics of the current network and signals, illegally access the network, and collect users’ private information, resulting in economic losses [25].
1.2. Related Works
1.3. Contributions
- Overview of Physical Layer Security and ATI-IoT Architectures: This review provides a detailed exploration of the fundamental principles of physical layer security in ATI-IoT, focusing on the mechanisms of key generation and agreement. Unlike prior work that primarily discusses general physical layer security techniques, this paper emphasizes how these techniques are applied within the aerial–terrestrial integrated architectures. In addition, an in-depth discussion of their components and functions is offered.
- Emerging Techniques for Enhancing Physical Layer Security: This work highlights several innovative technologies enabling physical layer security in ATI-IoT systems, including IRS-assisted networks, D2D communications, covert communications, and cooperative transmissions. Compared with previous research that focused on traditional methods, this paper explores the latest developed technologies and analyzes their applications in ATI-IoT.
- Potential Applications: This review provides valuable insights into the practical applications of ATI-IoT with physical layer security, particularly in areas such as emergency communications, vehicular networks, and intelligent agriculture. By considering the flexible deployment capabilities of aerial platforms, this paper provides novel perspectives on how ATI-IoT systems can be utilized in real-world scenarios to improve the security.
- Open Issues and Future Directions: Finally, this work discusses key unresolved challenges related to technical, security, and sustainability aspects in ATI-IoT systems. We outline potential research directions and suggest practical solutions for overcoming these challenges, ensuring the continuous advancement and adoption of physical layer security techniques in future ATI-IoT applications.
1.4. Structure
2. Preliminaries of Physical Layer Security
2.1. Wireless Communication Security
- Secrecy Capacity: Secrecy capacity refers to the maximum rate at which secret information can be transmitted over a communication channel without being intercepted. It is calculated by the difference between the channel capacities of the legitimate user and the eavesdropper.
- Secrecy Outage Probability: Secrecy outage probability is the probability that the secrecy capacity falls below a given threshold. It represents the possibility of unsafe communication due to changes in channel conditions.
- Secure Throughput: Secure throughput is the average rate of secure data transmission over a network. It accounts for both the legitimate user’s transmission rate and the eavesdropper’s interference.
- Key Generation Rate: Key generation rate is the rate at which secret keys are generated for secure communication. It is often used in key establishment protocols, where a secret key is derived from the physical layer’s channel properties.
2.2. Shannon’s Theory on Information-Theoretic Security
2.3. Key Generation and Agreement
2.3.1. Key-Based Security and Keyless Security
2.3.2. Key Agreement Mechanism
3. Emerging Techniques in ATI-IoT to Guarantee Information Security
3.1. Physical Layer Security Enhancement Exploiting IRS
3.2. Physical Layer Security in D2D-Aided Cellular Networks
3.3. Covert Communications in ATI-IoT
3.4. Secure Transmission in Cooperative Relaying Systems
3.5. Comparative Analysis
4. Application Scenarios of Physical Layer Security Techniques in ATI-IoT
4.1. Emergency Communication
4.2. Vehicular Ad-Hoc Networks
4.3. Intelligent Agriculture
4.4. Expansion to Maritime Communication Networks
5. Challenges and Future Trends for ATI-IoT
5.1. Technical, Security and Sustainability Challenges
- Technical Challenges: The main technical challenges in ATI-IoT systems are related to signal coverage, data processing capabilities, and multi-platform collaboration. First, in ATI-IoT, we need to ensure and sufficient computational ability to support real-time data analysis and decision-making. Third, the challenge of multi-platform collaboration concerns the compatibility between different types of devices, such as HAPSs, LAPSs, drones, and ground terminal systems, which must be seamlessly integrated to achieve efficient data collection and resource sharing. Addressing these technical challenges requires continuous technological innovation and standardization efforts to facilitate better integration among devices and platforms.
- Security Challenges: In terms of security, ATI-IoT faces key challenges including data security, cybersecurity, and physical security of devices. First, to protect data transmitted between devices and platforms from unauthorized interception, further research on encryption algorithms and security protocols is needed. Second, to prevent external attackers from damaging systems through ATI-IoT, protection is needed at the software level as well as the continuous monitoring and management of network traffic. Third, the physical security of the devices is crucial. In this situation, enhancing the physical robustness and tamper-resistance of ATI-IoT access terminals is essential.
- Sustainability Challenges: Sustainability poses another significant challenge for the implement of ATI-IoT, including environmental and economic impacts. On the one hand, IoT devices and operations may disturb natural ecosystems, such as frequent drone usage potentially affecting wildlife habits, and the manufacturing and disposal of devices may create a certain environmental burden. On the other hand, while ATI-IoT technologies can improve efficiency, the high initial investment and maintenance costs may limit its use in low-income areas.
5.2. Possible Solutions
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yu, A.; Yang, Q.; Dou, L.; Cheriet, M. Federated imitation learning: A cross-domain knowledge sharing framework for traffic scheduling in 6G ubiquitous IoT. IEEE Netw. 2021, 35, 136–142. [Google Scholar] [CrossRef]
- Guo, Y.; Li, Q.; Li, Y.; Zhang, N.; Wang, S. Service coordination in the space-air-ground integrated network. IEEE Netw. 2021, 35, 168–173. [Google Scholar] [CrossRef]
- Rahim, S.; Peng, L. Intelligent space-air-ground collaborative computing networks. IEEE Internet Things Mag. 2023, 6, 76–80. [Google Scholar] [CrossRef]
- Li, N.; Song, X.; Li, K.; Jiang, R.; Li, J. Multiagent federated deep-reinforcement-learning-enabled resource allocation for an air-ground-integrated internet of vehicles network. IEEE Internet Comput. 2023, 27, 15–23. [Google Scholar] [CrossRef]
- Shah, S.A.A.; Fernando, X.; Kashef, R. A survey on artificial-intelligence-based internet of vehicles utilizing unmanned aerial vehicles. Drones 2024, 8, 353. [Google Scholar] [CrossRef]
- Cui, H.; Zhang, J.; Geng, Y.; Xiao, Z.; Sun, T.; Zhang, N.; Liu, J.; Wu, Q.; Cao, X. Space-air-ground integrated network (SAGIN) for 6G: Requirements, architecture and challenges. China Commun. 2022, 19, 90–108. [Google Scholar] [CrossRef]
- Devoti, F.; Mursia, P.; Sciancalepore, V.; Costa-Pérez, X. Taming aerial communication with flight-assisted smart surfaces in the 6G era: Novel use cases, requirements, and solutions. IEEE Veh. Technol. Mag. 2023, 18, 38–47. [Google Scholar] [CrossRef]
- Alfattani, S.; Jaafar, W.; Yanikomeroglu, H.; Yongaçoglu, A. Multimode high-altitude platform stations for next-generation wireless networks: Selection mechanism, benefits, and potential challenges. IEEE Veh. Technol. Mag. 2023, 18, 20–28. [Google Scholar] [CrossRef]
- Lou, Z.; Belmekki, B.E.Y.; Alouini, M.-S. HAPS in the non-terrestrial network nexus: Prospective architectures and performance insights. IEEE Wirel. Commun. 2023, 30, 52–58. [Google Scholar] [CrossRef]
- Abbasi, O.; Yadav, A.; Yanikomeroglu, H.; Đào, N.-D.; Senarath, G.; Zhu, P. HAPS for 6G networks: Potential use cases, open challenges, and possible solutions. IEEE Wirel. Commun. 2024, 31, 324–331. [Google Scholar] [CrossRef]
- Qi, F.; Xie, W. Enhancing IoT services in 6G non-terrestrial networks with multicast massive MIMO. IEEE Netw. 2024, 38, 88–95. [Google Scholar] [CrossRef]
- Chen, Z.; Chen, G.; Tang, J.; Zhang, S.; So, D.K.C.; Dobre, O.A.; Wong, K.-K.; Chambers, J. Reconfigurable-intelligent-surface-assisted B5G/6G wireless communications: Challenges, solution, and future opportunities. IEEE Commun. Mag. 2023, 61, 16–22. [Google Scholar] [CrossRef]
- Xu, P.; Chen, G.; Quan, J.; Huang, C.; Krikidis, I.; Wong, K.-K.; Chae, C.-B. Deep learning driven buffer-aided cooperative networks for B5G/6G: Challenges, solutions, and future opportunities. IEEE Wirel. Commun. 2024, 31, 215–222. [Google Scholar] [CrossRef]
- Abdullah, Z.; Kisseleff, S.; Martins, W.A.; Chen, G.; Sanguinetti, L.; Ntontin, K.; Papazafeiropoulos, A.; Chatzinotas, S.; Ottersten, B. Cooperative hybrid networks with active relays and RISs for B5G: Applications, challenges, and research directions. IEEE Wireless Commun. 2024, 31, 126–132. [Google Scholar] [CrossRef]
- Kyung, Y.; Ko, H.; Lee, J.; Pack, S.; Park, N.; Ko, N. Location-aware B5G LAN-type services: Architecture, use case, and challenges. IEEE Commun. Mag. 2024, 62, 88–94. [Google Scholar] [CrossRef]
- Meira, G.d.S.; Guedes, J.V.F.; Bias, E.d.S. UAV-embedded sensors and deep learning for pathology identification in building façades: A review. Drones 2024, 8, 341. [Google Scholar] [CrossRef]
- Huang, G.; Hu, M.; Yang, X.; Wang, X.; Wang, Y.; Huang, F. A review of constrained multi-objective evolutionary algorithm-based unmanned aerial vehicle mission planning: Key techniques and challenges. Drones 2024, 8, 316. [Google Scholar] [CrossRef]
- Jin, X.; Zarco-Tejada, P.J.; Schmidhalter, U.; Reynolds, M.P.; Hawkesford, M.J.; Varshney, R.K.; Yang, T.; Nie, C.; Li, Z.; Ming, B.; et al. High-throughput estimation of crop traits: A review of ground and aerial phenotyping platforms. IEEE Geosci. Remote Sens. Mag. 2021, 9, 200–231. [Google Scholar] [CrossRef]
- Askarzadeh, T.; Bridgelall, R.; Tolliver, D. Monitoring nodal transportation assets with uncrewed aerial vehicles: A comprehensive review. Drones 2024, 8, 233. [Google Scholar] [CrossRef]
- Dong, R.; Wang, B.; Cao, K. Security enhancement of UAV swarm enabled relaying systems with joint beamforming and resource allocation. China Commun. 2021, 18, 71–87. [Google Scholar] [CrossRef]
- Sun, X.; Ng, D.W.K.; Ding, Z.; Xu, Y.; Zhong, Z. Physical layer security in UAV systems: Challenges and opportunities. IEEE Wirel. Commun. 2019, 26, 40–47. [Google Scholar] [CrossRef]
- Li, B.; Fei, Z.; Zhang, Y.; Guizani, M. Secure UAV communication networks over 5G. IEEE Wirel. Commun. 2019, 26, 114–120. [Google Scholar] [CrossRef]
- Wang, H.-M.; Zhang, X.; Jiang, J.-C. UAV-involved wireless physical-layer secure communications: Overview and research directions. IEEE Wirel. Commun. 2019, 26, 32–39. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Wang, D.; Chen, B.; Li, T.; Zhang, R. Performance analysis and optimization design of AAV-assisted vehicle platooning in NOMA-enhanced Internet of Vehicles. IEEE Trans. Intell. Transp. Syst. 2025, 1–10. [Google Scholar] [CrossRef]
- Ogunbunmi, S.; Chen, Y.; Blasch, E.; Chen, G. A survey on reputation systems for UAV networks. Drones 2024, 8, 253. [Google Scholar] [CrossRef]
- Topal, O.A.; Demir, M.O.; Liang, Z.; Pusane, A.E.; Dartmann, G.; Ascheid, G.; Kur, G.K. A physical layer security framework for cognitive cyber-physical systems. IEEE Wirel. Commun. 2020, 27, 32–39. [Google Scholar] [CrossRef]
- Tang, J.; Wen, H.; Zeng, K.; Liao, R.-f.; Pan, F.; Hu, L. Light-weight physical layer enhanced security schemes for 5G wireless networks. IEEE Netw. 2019, 33, 126–133. [Google Scholar] [CrossRef]
- Chen, R.; Li, C.; Yan, S.; Malaney, R.; Yuan, J. Physical layer security for ultra-reliable and low-latency communications. IEEE Wirel. Commun. 2019, 26, 6–11. [Google Scholar] [CrossRef]
- Chen, X.; Zhong, C.; Yuen, C.; Chen, H.-H. Multi-antenna relay aided wireless physical layer security. IEEE Commun. Mag. 2015, 53, 40–46. [Google Scholar] [CrossRef]
- Tan, H.; Xie, N.; Liu, A.X. Physical layer security in distributed antenna systems using one-bit feedback information. IEEE Netw. 2022, 36, 191–196. [Google Scholar] [CrossRef]
- Assaf, T.; Al-Dweik, A.; Iraqi, Y.; Jangsher, S.; Pandey, A.; Giacalone, J.-P.; Abulibdeh, E.E.; Saleh, H.; Mohammad, B. High-rate secret key generation using physical layer security and physical unclonable functions. IEEE Open J. Commun. Soc. 2023, 4, 209–225. [Google Scholar] [CrossRef]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and applications of physical layer security techniques for confidentiality: A comprehensive survey. IEEE Commun. Surv. Tutor. 2019, 21, 1773–1828. [Google Scholar] [CrossRef]
- Aghdam, S.R.; Nooraiepour, A.; Duman, T.M. An overview of physical layer security with finite-alphabet signaling. IEEE Commun. Surv. Tutor. 2019, 21, 1829–1850. [Google Scholar] [CrossRef]
- Illi, E.; Qaraqe, M.; Althunibat, S.; Alhasanat, A.; Alsafasfeh, M.; de Ree, M.; Mantas, G.; Rodriguez, J.; Aman, W.; Al-Kuwari, S. Physical layer security for authentication, confidentiality, and malicious node detection: A paradigm shift in securing IoT networks. IEEE Commun. Surv. Tutor. 2024, 26, 347–388. [Google Scholar] [CrossRef]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.-K.; Gao, X. A survey of physical layer security techniques for 5G wireless networks and challenges ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef]
- Haus, M.; Waqas, M.; Ding, A.Y.; Li, Y.; Tarkoma, S.; Ott, J. Security and privacy in device-to-device (D2D) communication: A review. IEEE Commun. Surv. Tutor. 2017, 19, 1054–1079. [Google Scholar] [CrossRef]
- Zhu, Y.; Mao, B.; Kato, N. Intelligent reflecting surface in 6G vehicular communications: A survey. IEEE Open J. Veh. Technol. 2022, 3, 266–277. [Google Scholar] [CrossRef]
- Wang, D.; Wang, Z.; Zhao, H.; Zhou, F.; Alfarraj, O.; Yang, W.; Mumtaz, S.; Leung, V. Secure energy efficiency for ARIS networks with deep learning: Active beamforming and position optimization. IEEE Trans. Wireless Commun. 2025. Early Access. [Google Scholar] [CrossRef]
- Oruma, S.O.; Petrovic, S. Security threats to 5G networks for social robots in public spaces: A survey. IEEE Access 2023, 11, 63205–63237. [Google Scholar] [CrossRef]
- Khuwaja, A.A.; Chen, Y.; Zhao, N.; Alouini, M.-S.; Dobbins, P. A survey of channel modeling for UAV communications. IEEE Commun. Surv. Tutor. 2018, 20, 2804–2821. [Google Scholar] [CrossRef]
- Khawaja, W.; Guvenc, I.; Matolak, D.W.; Fiebig, U.-C.; Schneckenburger, N. A survey of air-to-ground propagation channel modeling for unmanned aerial vehicles. IEEE Commun. Surv. Tutor. 2019, 21, 2361–2391. [Google Scholar] [CrossRef]
- Zhang, L.; Zhao, H.; Hou, S.; Zhao, Z.; Xu, H.; Wu, X.; Wu, Q.; Zhang, R. A survey on 5G millimeter wave communications for UAV-assisted wireless networks. IEEE Access 2019, 7, 117460–117504. [Google Scholar] [CrossRef]
- Xiao, Z.; Zhu, L.; Liu, Y.; Yi, P.; Zhang, R.; Xia, X.-G.; Schober, R. A survey on millimeter-wave beamforming enabled UAV communications and networking. IEEE Commun. Surv. Tutor. 2022, 24, 557–610. [Google Scholar] [CrossRef]
- Cao, P.; Lei, L.; Cai, S.; Shen, G.; Liu, X.; Wang, X.; Zhang, L.; Zhou, L.; Guizani, M. Computational intelligence algorithms for UAV swarm networking and collaboration: A comprehensive survey and future directions. IEEE Commun. Surv. Tutor. 2024, 26, 2684–2728. [Google Scholar] [CrossRef]
- Wang, D.; Yuan, L.; Zhao, H.; Min, L.; He, Y. Secure transmission of IRS-UAV buffer-aided relaying system with delay constraint. Chin. J. Aeronaut. 2024. Early Access. [Google Scholar] [CrossRef]
- Zhao, D.; Ji, G.; Zhang, Y.; Han, X.; Zeng, S. A network security situation prediction method based on SSA-GResNeSt. IEEE Trans. Netw. Serv. Manag. 2024, 21, 3498–3510. [Google Scholar] [CrossRef]
- Iqbal, W.; Abbas, H.; Daneshmand, M.; Rauf, B.; Bangash, Y.A. An in-depth analysis of IoT security requirements, challenges, and their countermeasures via software-defined security. IEEE Internet Things J. 2020, 7, 10250–10276. [Google Scholar] [CrossRef]
- Mitev, M.; Chorti, A.; Poor, H.V.; Fettweis, G.P. What physical layer security can do for 6G security. IEEE Open J. Veh. Technol. 2023, 4, 375–388. [Google Scholar] [CrossRef]
- Qiu, S.; Wei, Z.; Huang, Y.; Abbaszadeh, M.; Charmet, J.; Li, B.; Guo, W. Review of physical layer security in molecular Internet of Nano-Things. IEEE Trans. Nano Biosci. 2024, 23, 91–100. [Google Scholar] [CrossRef]
- Wu, X.; Shao, H.; Lin, J.; Pan, Y.; Xiong, W. Secure Wireless Communication for Correlated Legitimate User and Eavesdropper Channels via Movable-Antenna Enhanced Frequency Diverse Array. Entropy 2025, 27, 401. [Google Scholar] [CrossRef]
- Moqurrab, S.A.; Anjum, A.; Tariq, N.; Srivastava, G. Instant-anonymity: A lightweight semantic privacy guarantee for 5G-enabled IIoT. IEEE Trans. Ind. Inform. 2023, 19, 951–959. [Google Scholar] [CrossRef]
- Alnashwan, R.; Gope, P.; Dowling, B. Privacy-aware secure region-based handover for small cell networks in 5G-enabled mobile communication. IEEE Trans. Inf. Forensics Secur. 2023, 18, 1898–1913. [Google Scholar] [CrossRef]
- Zuo, J.; Guo, Z.; An, T.; Xu, Z.; Lu, Y. A security resilience metric framework based on the evolution of attack and defense scenarios. IEEE Internet Things J. 2023, 10, 17007–17021. [Google Scholar] [CrossRef]
- Chen, H.; Han, X.; Zhang, Y. Endogenous security formal definition, innovation mechanisms, and experiment research in industrial Internet. Tsinghua Sci. Technol. 2024, 29, 492–505. [Google Scholar] [CrossRef]
- Li, H.; Li, X.; Zhang, Z.; Hu, C.; Dunkin, F.; Ge, S.S. ESUAV-NI: Endogenous security framework for UAV perception system based on neural immunity. IEEE Trans. Ind. Inform. 2024, 20, 732–743. [Google Scholar] [CrossRef]
- Qian, P.; Huynh, V.S.H.; Wang, N.; Anmulwar, S.; Mi, D.; Tafazolli, R.R. Remote production for live holographic teleportation applications in 5G networks. IEEE Trans. Broadcast. 2022, 68, 451–463. [Google Scholar] [CrossRef]
- Xu, J.; Ota, K.; Dong, M. Aerial edge computing: Flying attitude-aware collaboration for multi-UAV. IEEE Trans. Mob. Comput. 2023, 22, 5706–5718. [Google Scholar] [CrossRef]
- Qin, X.; Song, Z.; Hou, T.; Yu, W.; Wang, J.; Sun, X. Joint optimization of resource allocation, phase shift, and UAV trajectory for energy-efficient RIS-assisted UAV-enabled MEC systems. IEEE Trans. Green Commun. Netw. 2023, 7, 1778–1792. [Google Scholar] [CrossRef]
- Huang, Y.; Liang, S.; Cui, T.; Mu, X.; Luo, T.; Wang, S.; Wu, G. Edge computing and fault diagnosis of rotating machinery based on MobileNet in wireless sensor networks for mechanical vibration. Sensors 2024, 24, 5156. [Google Scholar] [CrossRef]
- Chen, L.; Liu, G.; Zhu, X.; Li, X. A heuristic routing algorithm for heterogeneous UAVs in time-constrained MEC systems. Drones 2024, 8, 379. [Google Scholar] [CrossRef]
- Chen, X.; Chang, Z.; Zhao, N.; Hämäläinen, T. IRS-Based Secure UAV-Assisted Transmission with Location and Phase Shifting Optimization. In Proceedings of the 2023 IEEE International Conference on Communications Workshops, Rome, Italy, 28 May–1 June 2023; pp. 1672–1677. [Google Scholar]
- Cai, S.; Qu, H.; Zhang, J.; Shi, X.; Zhu, H. Symbol-level precoding design in IRS-aided secure wireless communication systems. IEEE Wirel. Commun. Lett. 2022, 11, 2315–2319. [Google Scholar] [CrossRef]
- Wu, M.; Chen, W.; Li, K.; Qian, L. Secure Computation Offloading for IRS-Assisted Mobile Edge Computing Networks. In Proceedings of the 2023 IEEE/CIC International Conference on Communications in China, Dalian, China, 10–12 August 2023; pp. 1–6. [Google Scholar]
- Wang, D.; Wang, Z.; Yu, K.; Wei, Z.; Zhao, H.; Al-Dhahir, N.; Guizani, M.; Leung, V.C.M. Active aerial reconfigurable intelligent surface assisted secure communications: Integrating sensing and positioning. IEEE J. Sel. Areas Commun. 2024, 42, 2769–2785. [Google Scholar] [CrossRef]
- Fang, X. Joint channel estimation algorithm for IRS-assisted multi-user MIMO systems. IEEE Commun. Lett. 2024, 28, 367–371. [Google Scholar] [CrossRef]
- Zhang, Y.; Fei, M.; Du, D.; Hu, Y. Security State Assessment in Cyber-Physical Systems Post-DoS Attack Based on Cyber Layer Partitioning. IEEE Trans. Ind. Inform. 2025, 21, 2204–2213. [Google Scholar] [CrossRef]
- Li, M.; Xue, P.; Yuan, H.; Han, Y. Physical Layer Security for CR-NOMA Network with Cooperative Jamming. Tsinghua Sci. Technol. 2025, 30, 708–720. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Alsamhi, S.H.; Barb, G.; Zywiołek, J.; Ullah, I.; Noor, F.; Shah, J.A.; Almuhaideb, A.M. Security and Privacy Issues and Solutions for UAVs in B5G Networks: A Review. IEEE Trans. Netw. Serv. Manag. 2025, 22, 892–912. [Google Scholar] [CrossRef]
- Chen, H.; Chen, Z.; Ou, R.; Chen, R.; Wu, Z.; Li, B. An IEEE 802.15.4z-Compliant Reconfigurable Pulse-Shaping UWB Digital Power Amplifier in 28-nm CMOS. IEEE Trans. Microw. Theory Tech. 2023, 71, 4366–4376. [Google Scholar] [CrossRef]
- Meshram, A.K.; Kumar, S.; Querol, J.; Andrenacci, S.; Chatzinotas, S. Reduced Complexity Initial Synchronization for 5G NR Multibeam LEO-Based Non-Terrestrial Networks. IEEE Open J. Commun. Soc. 2025, 6, 1528–1551. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Bibak, K.; Koshiba, T. The odyssey of entropy: Cryptography. Entropy 2022, 24, 266. [Google Scholar] [CrossRef]
- Natal, J.; Ávila, I.; Tsukahara, V.B.; Pinheiro, M.; Maciel, C.D. Entropy: From thermodynamics to information processing. Entropy 2021, 23, 1340. [Google Scholar] [CrossRef]
- Rioul, O. Information theoretic proofs of entropy power inequalities. IEEE Trans. Inf. Theory 2011, 57, 33–55. [Google Scholar] [CrossRef]
- Tan, A.; Shi, S.; Wu, W.-Z.; Li, J.; Pedrycz, W. Granularity and entropy of intuitionistic fuzzy information and their applications. IEEE Trans. Cybern. 2022, 52, 192–204. [Google Scholar] [CrossRef] [PubMed]
- Sabirov, D.S.; Shepelevich, I.S. Information entropy in chemistry: An overview. Entropy 2021, 23, 1240. [Google Scholar] [CrossRef]
- Girardin, V.; Lhote, L. Rescaling entropy and divergence rates. IEEE Trans. Inf. Theory 2015, 61, 5868–5882. [Google Scholar] [CrossRef]
- Langley, R.S. Probability functionals for self-consistent and invariant inference: Entropy and Fisher information. IEEE Trans. Inf. Theory 2013, 59, 4397–4407. [Google Scholar] [CrossRef]
- Zhou, Z.; Tang, W.; Li, M.; Cao, W.; Yuan, Z. A novel hybrid intelligent SOPDEL model with comprehensive data preprocessing for long-time-series climate prediction. Remote Sens. 2023, 15, 1951. [Google Scholar] [CrossRef]
- Edelsbrunner, H.; Ölsböck, K.; Wagner, H. Understanding higher-order interactions in information space. Entropy 2024, 26, 637. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhao, S.; Shen, Y.; Jiang, X.; Shiratori, N. Enhancing the Physical Layer Security of Two-Way Relay Systems With RIS and Beamforming. IEEE Trans. Inf. Forensics Secur. 2024, 19, 5696–5711. [Google Scholar] [CrossRef]
- Lv, L.; Xu, D.; Hu, R.Q.; Ye, Y.; Yang, L.; Lei, X.; Wang, X.; Kim, D.I.; Nallanathan, A. Safeguarding Next-Generation Multiple Access Using Physical Layer Security Techniques: A Tutorial. Proc. IEEE 2024, 112, 1421–1466. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Wang, D.; Zhang, R. Outage Probability Analysis of MISO-NOMA Downlink Communications in UAV-Assisted Agri-IoT With SWIPT and TAS Enhancement. IEEE Trans. Netw. Sci. Eng. 2025, 1–14. [Google Scholar] [CrossRef]
- AHaq, U.; Sefati, S.S.; Nawaz, S.J.; Mihovska, A.; Beliatis, M.J. Need of UAVs and Physical Layer Security in Next-Generation Non-Terrestrial Wireless Networks: Potential Challenges and Open Issues. IEEE Open J. Veh. Technol. 2025, 6, 554–595. [Google Scholar]
- Wang, D.; Li, J.; Lv, Q.; He, Y.; Li, L.; Hua, Q.; Alfarraj, O.; Zhang, J. Integrating Reconfigurable Intelligent Surface and UAV for Enhanced Secure Transmissions in IoT-Enabled RSMA Networks. IEEE Internet Things J. 2024, 12, 9405–9419. [Google Scholar] [CrossRef]
- Zhao, C.; Du, H.; Niyato, D.; Kang, J.; Xiong, Z.; Kim, D.I.; Shen, X.; Letaief, K.B. Generative AI for Secure Physical Layer Communications: A Survey. IEEE Trans. Cogn. Commun. Netw. 2025, 11, 3–26. [Google Scholar] [CrossRef]
- Shi, Q.; Yang, Z.; Cheng, T.; Wang, C.; Wu, Z.; Zhang, X.; Xu, P. QKBAKA: A quantum-key-based authentication and key agreement scheme for internet of vehicles. IEEE Internet Things J. 2024, 11, 12292–12306. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Xu, Y.; Liu, L. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs. IEEE Trans. Mob. Comput. 2022, 21, 3280–3297. [Google Scholar] [CrossRef]
- Xu, P.; Cumanan, K.; Ding, Z.; Dai, X.; Leung, K.K. Group secret key generation in wireless networks: Algorithms and rate optimization. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1831–1846. [Google Scholar] [CrossRef]
- Xu, P.; Yang, J.; Chen, G.; Yang, Z.; Li, Y.; Win, M.Z. Physical-layer secret and private key generation in wireless relay networks with correlated eavesdropping channels. IEEE Trans. Inf. Forensics Secur. 2024, 19, 985–1000. [Google Scholar] [CrossRef]
- Yerrapragada, A.K.; Eisman, T.; Kelley, B. Physical layer security for beyond 5G: Ultra secure low latency communications. IEEE Open J. Commun. Soc. 2021, 2, 2232–2242. [Google Scholar] [CrossRef]
- Katti, R.S.; Vosoughi, A. On the security of key-based interval splitting arithmetic coding with respect to message indistinguishability. IEEE Trans. Inf. Forensics Secur. 2012, 7, 895–903. [Google Scholar] [CrossRef]
- Parameswarath, R.P.; Sikdar, B. A puf-Based Lightweight and Secure Mutual Authentication Mechanism for Remote Keyless Entry Systems. In Proceedings of the 2022 IEEE Global Communications Conference (GLOBECOM 2022), Rio de Janeiro, Brazil, 4–8 December 2022; pp. 1776–1781. [Google Scholar]
- Huang, M.; Li, Z.; Jia, D.; Lu, X. Survey of Wiretap Channel Security Model. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM 2021), Madrid, Spain, 7–11 December 2021; pp. 1–6. [Google Scholar]
- Kolli, A.; Casamassima, F.; Possegger, H.; Bischof, H. Robust localization of Key Fob Using Channel Impulse Response of Ultra Wide Band Sensors for Keyless Entry Systems. In Proceedings of the 2024 International Conference on Acoustics, Speech, and Signal Processing (ICASSP 2024), Seoul, Republic of Korea, 14–19 April 2024; pp. 7825–7829. [Google Scholar]
- Ahmad, S.; Alam, K.M.R.; Rahman, H.; Tamura, S. A Comparison Between Symmetric and Asymmetric Key Encryption Algorithm Based Decryption Mixnets. In Proceedings of the 2015 International Conference on Networking Systems and Security (NSysS), Dhaka, Bangladesh, 5–7 January 2015; pp. 1–5. [Google Scholar]
- Zhang, Y.; He, D.; Vijayakumar, P.; Luo, M.; Huang, X. SAPFS: An efficient symmetric-key authentication key agreement scheme with perfect forward secrecy for industrial internet of things. IEEE Internet Things J. 2023, 10, 9716–9726. [Google Scholar] [CrossRef]
- Ban, H.; Peng, T.; Lin, D. A Novel Channel Estimation Method for UAV in High-Capacity CDMA Network. In Proceedings of the 2020 IEEE 6th International Conference on Computer and Communications (ICCC 2020), Chengdu, China, 11–14 December 2020; pp. 1–7. [Google Scholar]
- Vlachos, E.; Mavrokefalidis, C.; Berberidis, K. Channel Estimation for UAV-Based mmwave Massive MIMO Communications with Beam Squint. In Proceedings of the 2022 30th European Signal Processing Conference (EUSIPCO), Belgrade, Serbia, 29 August–2 September 2022; pp. 1696–1700. [Google Scholar]
- Fan, D.; Gao, F.; Ai, B.; Wang, G.; Zhong, Z.; Deng, Y.; Nallanathan, A. Channel estimation and self-positioning for UAV swarm. IEEE Trans. Commun. 2019, 67, 7994–8007. [Google Scholar] [CrossRef]
- Basu, S.; Banerjee, S.; Arya, R.K.; Nanda, S.; Mohanty, S.; Patnaik, S. Performance Enhancement of UAV-Assisted Wireless Communication Using the MVC Channel Estimation Algorithm in a Diamond-Shaped Network Topology. In Proceedings of the 2023 International Conference in Advances in Power, Signal, and Information Technology (APSIT 2023), Bhubaneswar, India, 9–11 June 2023; pp. 463–468. [Google Scholar]
- Jung, H.; Ko, S.-W. Performance analysis of UAV-enabled over-the-air computation under imperfect channel estimation. IEEE Wirel. Commun. Lett. 2022, 11, 438–442. [Google Scholar] [CrossRef]
- Mukherjee, P.; Psomas, C.; Krikidis, I. Differential Chaos Shift Keying-Based Wireless Power Transfer over a Frequency Selective Channel. In Proceedings of the 2022 IEEE 95th Vehicular Technology Conference (VTC2022-Spring), Helsinki, Finland, 19–22 June 2022; pp. 1–6. [Google Scholar]
- He, Y.; Huang, F.; Xu, Q.; Wang, D.; Tolba, A.; Yu, K.; Kumar, N.; Leung, V.C.M. Air-to-ground integrated internet of vehicles enhanced by LAPSs and RISs: Location, power, and phase shift optimization. IEEE Internet Things J. 2024, 11, 18020–18034. [Google Scholar] [CrossRef]
- Bansal, A.; Agrawal, N.; Singh, K.; Li, C.-P.; Mumtaz, S. RIS selection scheme for UAV-based multi-RIS-aided multiuser downlink network with imperfect and outdated CSI. IEEE Trans. Commun. 2023, 71, 4650–4664. [Google Scholar] [CrossRef]
- Liu, X.; Yu, Y.; Li, F.; Durrani, T.S. Throughput maximization for RIS-UAV relaying communications. IEEE Trans. Intell. Transp. Syst. 2022, 23, 19569–19574. [Google Scholar] [CrossRef]
- Tang, Z.; Hou, T.; Liu, Y.; Zhang, J.; Zhong, C. A novel design of RIS for enhancing the physical layer security for RIS-aided NOMA networks. IEEE Wirel. Commun. Lett. 2021, 10, 2398–2401. [Google Scholar] [CrossRef]
- Ukyam, U.M.R.; Sireesha, P.; Kumar, P.D.P.; Ashish, A.P.N.V.R.M.; Gurrala, K.K. Enhanced Physical Layer Security for RIS Aided Wireless Network with Control Jammer and Power Allocation Scheme. In Proceedings of the 2023 2nd International Conference on Paradigm Shifts in Communications Embedded Systems, Machine Learning and Signal Processing (PCEMS 2023), Nagpur, India, 5–6 April 2023; pp. 1–5. [Google Scholar]
- Xing, J.; Lv, T.; Cao, Y.; Zeng, J.; Huang, P. Downlink power minimization in intelligent reflecting surface aided security classification wireless communications system. IEEE Syst. J. 2023, 17, 407–418. [Google Scholar] [CrossRef]
- Ngo, Q.T.; Phan, K.T.; Mahmood, A.; Xiang, W. Physical layer security in IRS-assisted cache-enabled satellite communication networks. IEEE Trans. Green Commun. Netw. 2023, 7, 1920–1931. [Google Scholar] [CrossRef]
- Qi, Y.; Vaezi, M. IRS-assisted physical layer security in MIMO-NOMA networks. IEEE Commun. Lett. 2023, 27, 792–796. [Google Scholar] [CrossRef]
- Zhai, L.; Zou, Y.; Zhu, J.; Li, B. Improving physical layer security in IRS-aided WPCN multicast systems via Stackelberg game. IEEE Trans. Commun. 2022, 70, 1957–1970. [Google Scholar] [CrossRef]
- Ge, Y.; Fan, J. Robust secure beamforming for intelligent reflecting surface assisted full-duplex MISO systems. IEEE Trans. Inf. Forensics Secur. 2022, 17, 253–264. [Google Scholar] [CrossRef]
- Wang, Z.; Li, Z.; Wen, J.; Zhao, M.; Zhou, X.; Yu, L. Secure Communication Scheme for IRS-UAV Enabled Cognitive Network. In Proceedings of the 2023 3rd International Conference on Intelligent Communications and Computing (ICC 2023), Nanchang, China, 24–26 November 2023; pp. 37–41. [Google Scholar]
- Cheng, T.; Wang, B.; Cao, K.; Zheng, B.; Tian, J.; Dong, R.; Diao, D.; Chen, J. Aerial IRS-assisted secure SWIPT system with UAV jitter. IEEE Trans. Green Commun. Netw. 2024, 8, 1530–1544. [Google Scholar] [CrossRef]
- Park, Y.M.; Tun, Y.K.; Han, Z.; Hong, C.S. Trajectory optimization and phase-shift design in IRS-assisted UAV network for smart railway. IEEE Trans. Veh. Technol. 2022, 71, 11317–11321. [Google Scholar] [CrossRef]
- Yadav, K.; Upadhyay, P.K.; Magarini, M. Physical Layer Security Analysis of IRS-Aided UAV Relaying Systems with NOMA. In Proceedings of the 2023 IEEE International Mediterranean Conference on Communications and Networking (MeditCom), Dubrovnik, Croatia, 4–7 September 2023; pp. 157–163. [Google Scholar]
- He, Y.; Huang, F.; Wang, D.; Yang, L.; Zhang, R. Delay Minimization for NOMA-MEC Offloading in ABS-Aided Maritime Communication Networks. IEEE Trans. Veh. Technol. 2025. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Wang, D.; Zhang, R.; Gu, X.; Pan, J. NOMA-enhanced cooperative relaying systems in drone-enabled IoV: Capacity analysis and height optimization. IEEE Trans. Veh. Technol. 2024, 73, 19065–19079. [Google Scholar] [CrossRef]
- Lyu, J.; Wang, H.-M.; Huang, K.-W. Physical layer security in D2D underlay cellular networks with Poisson cluster process. IEEE Trans. Commun. 2020, 68, 7123–7139. [Google Scholar] [CrossRef]
- Zhao, B.-Q.; Wang, H.-M.; Deng, H. Does D2D communication always benefit physical-layer security? IEEE Internet Things J. 2023, 10, 224–240. [Google Scholar] [CrossRef]
- Moualeu, J.M.; Ngatched, T.M.N. Physical-layer security enhancement via relay-aided D2D communications underlaying cellular networks. IEEE Open J. Commun. Soc. 2020, 1, 413–427. [Google Scholar] [CrossRef]
- Zhang, Z.; Tian, J.; Wang, D.; Qiao, J.; Li, T. TD3-Based Joint UAV Trajectory and Power Optimization in UAV-Assisted D2D Secure Communication Networks. In Proceedings of the 2022 IEEE 96th Vehicular Technology Conference (VTC2022-Fall), London, UK, 26–29 September 2022; pp. 1–5. [Google Scholar]
- Yin, C.; Yang, H.; Xiao, P.; Chu, Z.; Garcia-Palacios, E. Resource allocation for UAV-assisted wireless powered D2D networks with flying and ground eavesdropping. IEEE Commun. Lett. 2023, 27, 2103–2107. [Google Scholar] [CrossRef]
- Hu, H.; Xu, Y.; Wang, Q.; Huang, D. Robust Resource Allocation for Energy Harvesting-Powered UAV-Assisted D2D Networks. In Proceedings of the 2021 13th International Conference on Wireless Communications and Signal Processing (WCSP), Changsha, China, 20–22 October 2021; pp. 1–5. [Google Scholar]
- Ji, J.; Zhu, K.; Niyato, D.; Wang, R. Joint Cache and Trajectory Optimization for Secure UAV-Relaying with Underlaid D2D Communications. In Proceedings of the 2020 IEEE International Conference on Communications (ICC 2020), Dublin, Ireland, 7–11 June 2020; pp. 1–6. [Google Scholar]
- Yang, B.; Taleb, T.; Fan, Y.; Shen, S. Mode selection and cooperative jamming for covert communication in D2D underlaid UAV networks. IEEE Netw. 2021, 35, 104–111. [Google Scholar] [CrossRef]
- Wang, S.; Yang, B.; Wang, W.; Shen, S.; Jiang, X. On UAV-IRS-Aided Covert Communication of D2D-Enabled Cellular Networks. In Proceedings of the 2023 International Conference on Networking and Network Applications (NaNA 2023), Qingdao, China, 18–21 August 2023; pp. 58–63. [Google Scholar]
- Tian, W.; Ding, X.; Liu, G.; Dai, Y.; Han, Z. A UAV-assisted secure communication system by jointly optimizing transmit power and trajectory in the Internet of Things. IEEE Trans. Green Commun. Netw. 2023, 7, 2025–2037. [Google Scholar] [CrossRef]
- Fan, H.; Yang, W.; Wang, Y.; Yuan, Z.; Tian, B. Achieving Covert Communication in Underlay Cognitive Radio Networks Using a Multi-Antenna Receiver. In Proceedings of the 2023 9th International Conference on Computer and Communications (ICCC 2023), Chengdu, China, 8–11 December 2023; pp. 1153–1157. [Google Scholar]
- Xiong, W.; Yao, Y.; Fu, X.; Li, S. Covert communication with cognitive jammer. IEEE Wirel. Commun. Lett. 2020, 9, 1753–1757. [Google Scholar] [CrossRef]
- Chen, X.; An, J.; Xiong, Z.; Xing, C.; Zhao, N.; Yu, F.R.; Nallanathan, A. Covert communications: A comprehensive survey. IEEE Commun. Surv. Tutor. 2023, 25, 1173–1198. [Google Scholar] [CrossRef]
- Wang, D.; Qi, P.; Zhao, Y.; Li, C.; Wu, W.; Li, Z. Covert wireless communication with noise uncertainty in space-air-ground integrated vehicular networks. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2784–2797. [Google Scholar] [CrossRef]
- Wang, D.; Wu, M.; Chakraborty, C.; Min, L.; He, Y.; Guduri, M. Covert communications in air-ground integrated urban sensing networks enhanced by federated learning. IEEE Sens. J. 2024, 24, 5636–5643. [Google Scholar] [CrossRef]
- Jiao, L.; Chen, X.; Xu, L.; Deng, N.; Zhao, N.; Wang, X. UAV-relayed finite-blocklength covert communication with channel estimation. IEEE Trans. Veh. Technol. 2024, 73, 9032–9037. [Google Scholar] [CrossRef]
- Wang, C.; Chen, X.; An, J.; Xiong, Z.; Xing, C.; Zhao, N.; Niyato, D. Covert communication assisted by UAV-IRS. IEEE Trans. Commun. 2023, 71, 357–369. [Google Scholar] [CrossRef]
- Bai, J.; He, J.; Jiang, X. Covert Communication in NOMA Systems with Decision-Assisted Q-Learning. In Proceedings of the Tenth International Symposium on Computing and Networking, Himeji, Japan, 21–24 November 2022; pp. 283–287. [Google Scholar]
- Su, Y.; Fu, S.; Si, J.; Xiang, C.; Zhang, N.; Li, X. Optimal hovering height and power allocation for UAV-aided NOMA covert communication system. IEEE Wirel. Commun. Lett. 2023, 12, 937–941. [Google Scholar] [CrossRef]
- Lv, L.; Wu, Q.; Li, Z.; Ding, Z.; Al-Dhahir, N.; Chen, J. Covert communication in intelligent reflecting surface-assisted NOMA systems: Design, analysis, and optimization. IEEE Trans. Wirel. Commun. 2022, 21, 1735–1750. [Google Scholar] [CrossRef]
- Li, X.; Tian, Z.; He, W.; Chen, G.; Gursoy, M.C.; Mumtaz, S.; Nallanathan, A. Covert communication of STAR-RIS aided NOMA networks. IEEE Trans. Veh. Technol. 2024, 73, 9055–9060. [Google Scholar] [CrossRef]
- Zhang, L.; Li, G.; Chen, J.; Wang, H.; He, W.; Yi, J. Joint Transmit Power and Trajectory Optimization for UAV Covert Communication Assisted by Artificial Noise. In Proceedings of the 2023 International Conference on Ubiquitous Communication (Ucom 2923), Xi’an, China, 7–9 July 2023; pp. 46–51. [Google Scholar]
- Yang, G. Covert wireless communications for augmented reality systems with dual cooperative UAVs. IEEE J. Sel. Top. Signal Process. 2023, 17, 1119–1130. [Google Scholar] [CrossRef]
- Qin, X.; Na, Z.; Wen, Z.; Wu, X. Relaying IRS-UAV assisted covert communications in uplink C-NOMA network. IEEE Commun. Lett. 2024, 28, 2136–2140. [Google Scholar] [CrossRef]
- Hoang, T.M.; Duong, T.Q.; Suraweera, H.A.; Tellambura, C.; Poor, H.V. Cooperative beamforming and user selection for improving the security of relay-aided systems. IEEE Trans. Commun. 2015, 63, 5039–5051. [Google Scholar] [CrossRef]
- Nawaz, M.; Khan, W.U.; Ali, Z.; Ihsan, A.; Waqar, O.; Sidhu, G.A.S. Resource optimization framework for physical layer security of dual-hop multi-carrier decode and forward relay networks. IEEE Open J. Antennas Propag. 2021, 2, 634–645. [Google Scholar] [CrossRef]
- Wang, K.; Yuan, L.; Miyazaki, T.; Zeng, D.; Guo, S.; Sun, Y. Strategic antieavesdropping game for physical layer security in wireless cooperative networks. IEEE Trans. Veh. Technol. 2017, 66, 9448–9457. [Google Scholar] [CrossRef]
- Hu, T.; Ma, F.; Shang, Y.; Cheng, Y. Physical Layer Security of Untrusted UAV-Enabled Relaying NOMA Network Using SWIPT and Cooperative Jamming. In Proceedings of the 2021 IEEE 94th Vehicular Technology Conference, Norman, OK, USA, 27 September–28 October 2021; pp. 1–6. [Google Scholar]
- Lan, T.; Hu, Z.; Zhang, Y. Improving Physical Layer Security Using Multi-UAVs-Enabled Mobile Relaying. In Proceedings of the 2021 IEEE International Conference on Energy Internet (ICEI 2021), Southampton, UK, 27–29 September 2021; pp. 125–130. [Google Scholar]
- Yin, Z.; Jia, M.; Cheng, N.; Wang, W.; Lyu, F.; Guo, Q.; Shen, X. UAV-assisted physical layer security in multi-beam satellite-enabled vehicle communications. IEEE Trans. Intell. Transp. Syst. 2022, 23, 2739–2751. [Google Scholar] [CrossRef]
- Zhong, C.; Yao, J.; Xu, J. Secure UAV communication with cooperative jamming and trajectory control. IEEE Commun. Lett. 2019, 23, 286–289. [Google Scholar] [CrossRef]
- Dang-Ngoc, H.; Nguyen, D.N.; Ho-Van, K.; Hoang, D.T.; Dutkiewicz, E.; Pham, Q.-V.; Hwang, W.-J. Secure swarm UAV-assisted communications with cooperative friendly jamming. IEEE Internet Things J. 2022, 9, 25596–25611. [Google Scholar] [CrossRef]
- Ye, R.; Peng, Y.; Al-Hazemi, F.; Boutaba, R. A robust cooperative jamming scheme for secure UAV communication via intelligent reflecting surface. IEEE Trans. Commun. 2024, 72, 1005–1019. [Google Scholar] [CrossRef]
- Liu, Z.; Weng, J.; Guo, J.; Ma, J.; Huang, F.; Sun, H.; Cheng, Y. PPTM: A privacy-preserving trust management scheme for emergency message dissemination in space–air–ground-integrated vehicular networks. IEEE Internet Things J. 2022, 9, 5943–5956. [Google Scholar] [CrossRef]
- Tang, Y.; Lv, S.; Lin, X.; Liu, C.; Zhaod, Z. Air-Ground Integrated Cooperative Scheduling Optimization for Emergency Satellite Communication. In Proceedings of the 2023 IEEE 5th International Conference on Civil Aviation Safety and Information Technology (ICCASIT 2023), Dali, China, 11–13 October 2023; pp. 1491–1496. [Google Scholar]
- Lu, Z.; Jia, Z.; Wu, Q.; Han, Z. Joint trajectory planning and communication design for multiple UAVs in intelligent collaborative air-ground communication systems. IEEE Internet Things J. 2024, 11, 31053–31067. [Google Scholar] [CrossRef]
- Song, X.; Cheng, M.; Lei, L.; Yang, Y. Multitask and multiobjective joint resource optimization for UAV-assisted air-ground integrated networks under emergency scenarios. IEEE Internet Things J. 2023, 10, 20342–20357. [Google Scholar] [CrossRef]
- Zhou, Y.; Jin, Z.; Shi, H.; Shi, L.; Lu, N.; Dong, M. Enhanced emergency communication services for post-disaster rescue: Multi-IRS assisted air-ground integrated data collection. IEEE Trans. Netw. Sci. Eng. 2024, 11, 4651–4664. [Google Scholar] [CrossRef]
- Madhuvanthi, T.; Revathi, A. Survey on Current Developments in UAV Secure Communication Techniques and Protocols. In Proceedings of the 2023 International Conference on Research Methodologies in Knowledge Management, Artificial Intelligence and Telecommunication Engineering (RMKMATE 2023), Chennai, India, 1–2 November 2023; pp. 1–5. [Google Scholar]
- Andreou, A.; Mavromoustakis, C.X.; Batalla, J.M.; Markakis, E.; Bourdena, A.; Mastorakis, G.; Song, H. Enhancing Secure Communication in 6G-Enabled IoV Through UAV and Control Center Integration. In Proceedings of the 2024 International Wireless Communications and Mobile Computing (IWCMC 2024), Ayia Napa, Cyprus, 27–31 May 2024; pp. 186–191. [Google Scholar]
- Garcia, M.H.C.; Molina-Galan, A.; Boban, M.; Gozalvez, J.; Coll-Perales, B.; Şahin, T. A tutorial on 5G NR V2X communications. IEEE Commun. Surv. Tutor. 2021, 23, 1972–2026. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Wang, D.; Chen, B.; Zhang, R. Emergency communications in post-disaster scenarios: IoT-enhanced airship and buffer support. IEEE Internet Things J. 2024. [Google Scholar] [CrossRef]
- Cheng, N.; Wu, S.; Wang, X.; Yin, Z.; Li, C.; Chen, W.; Chen, F. AI for UAV-assisted IoT applications: A comprehensive review. IEEE Internet Things J. 2023, 10, 14438–14461. [Google Scholar] [CrossRef]
- Fawaz, W.; Atallah, R.; Assi, C.; Khabbaz, M. Unmanned aerial vehicles as store-carry-forward nodes for vehicular networks. IEEE Access 2017, 5, 23710–23718. [Google Scholar] [CrossRef]
- Eiza, M.H.; Owens, T.; Ni, Q. Secure and robust multi-constrained QoS aware routing algorithm for VANETs. IEEE Trans. Dependable Secur. Comput. 2016, 13, 32–45. [Google Scholar] [CrossRef]
- Akbari, M.; Syed, A.; Kennedy, W.S.; Erol-Kantarci, M. Constrained federated learning for AoI-limited SFC in UAV-aided MEC for smart agriculture. IEEE Trans. Mach. Learn. Commun. Netw. 2023, 1, 277–295. [Google Scholar] [CrossRef]
- Guo, J.; Gao, H.; Liu, Z.; Huang, F.; Zhang, J.; Li, X.; Ma, J. ICRA: An intelligent clustering routing approach for UAV ad hoc networks. IEEE Trans. Intell. Transp. Syst. 2023, 24, 2447–2460. [Google Scholar] [CrossRef]
- Katyal, A. Geolocation Based Optimal Load Balanced Clustering and Hybrid Routing in Large Scale Flying ad Hoc Network. In Proceedings of the 2023 International Conference on Data Science and Network Security (ICDSNS 2023), Tiptur, India, 28–29 July 2023; pp. 1–9. [Google Scholar]
- Nomikos, N.; Gkonis, P.K.; Bithas, P.S.; Trakadas, P. A survey on UAV-aided maritime communications: Deployment considerations, applications, and future challenges. IEEE Open J. Commun. Soc. 2023, 4, 56–78. [Google Scholar] [CrossRef]
- Wang, W.; Li, X.; Wang, R.; Cumanan, K.; Feng, W.; Ding, Z.; Dobre, O.A. Robust 3D-trajectory and time switching optimization for dual-UAV-enabled secure communications. IEEE J. Sel. Areas Commun. 2021, 39, 3334–3347. [Google Scholar] [CrossRef]
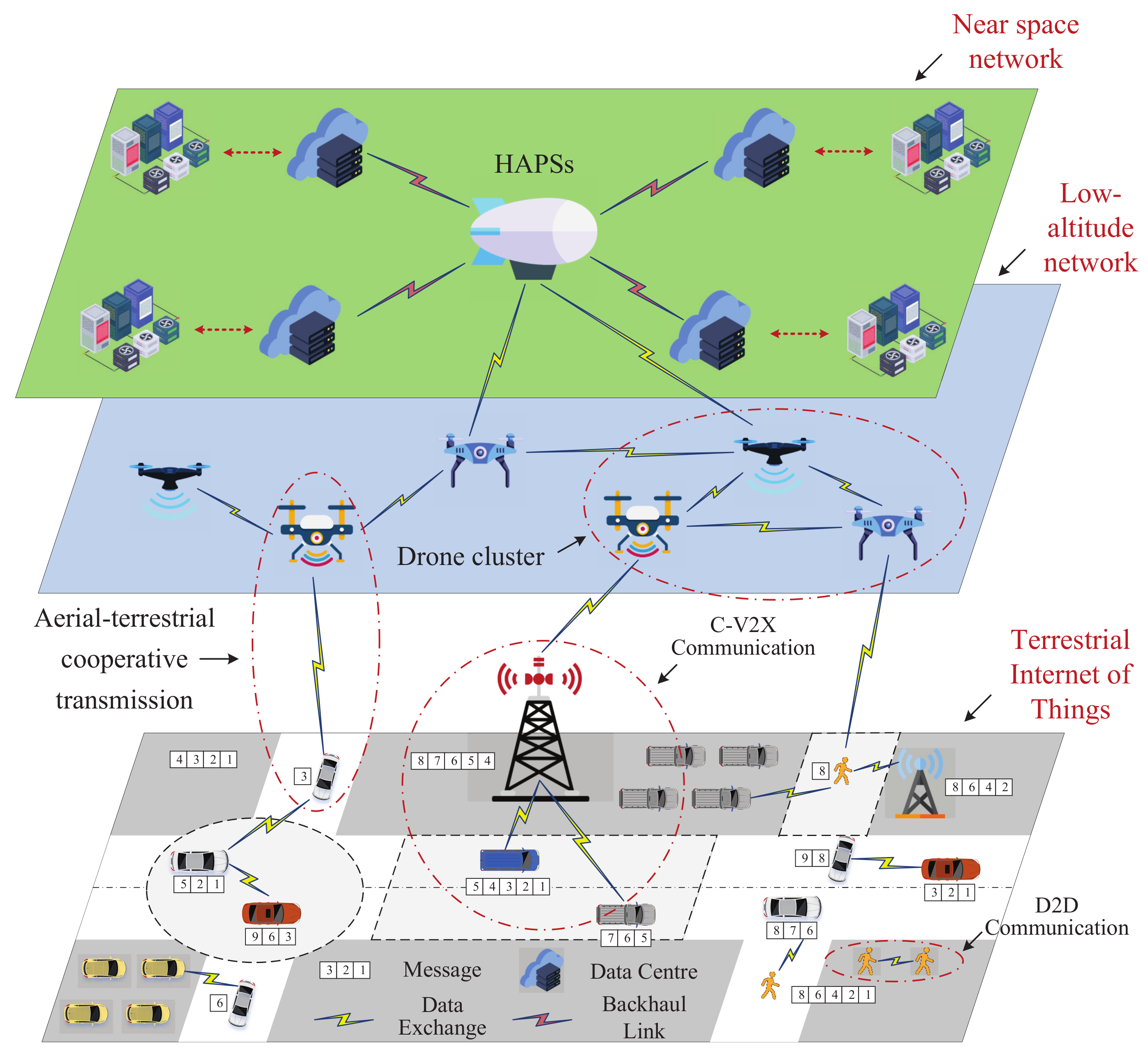



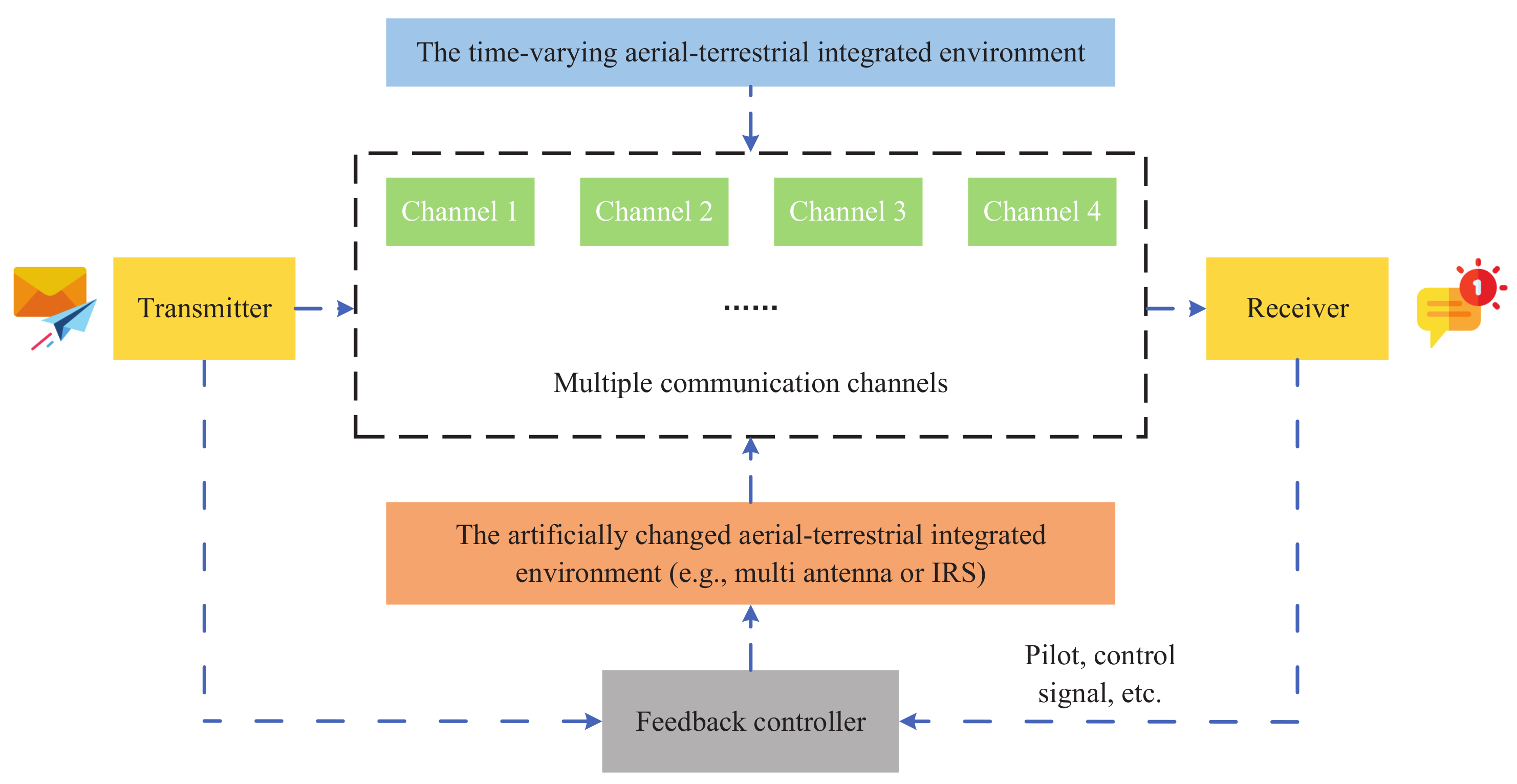


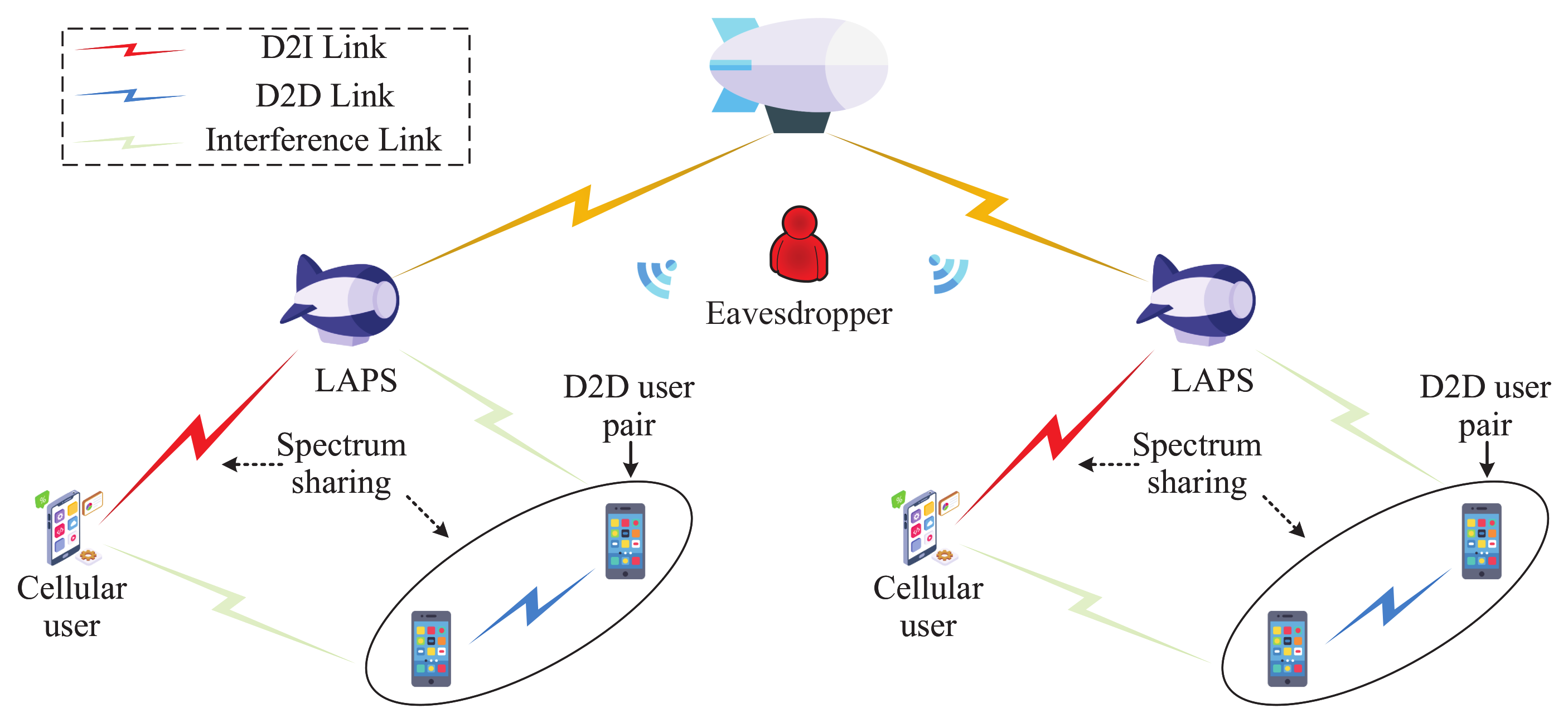
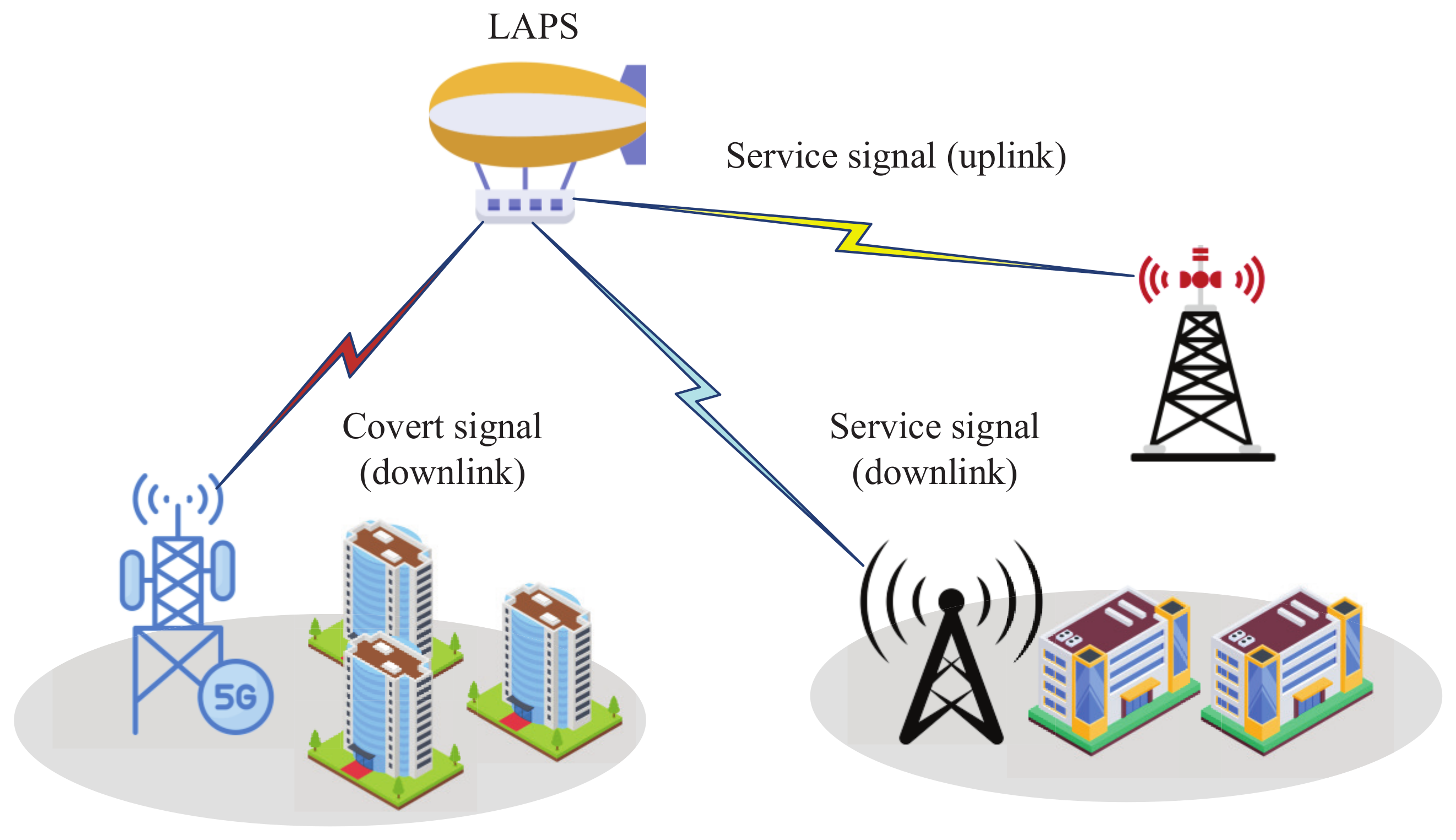



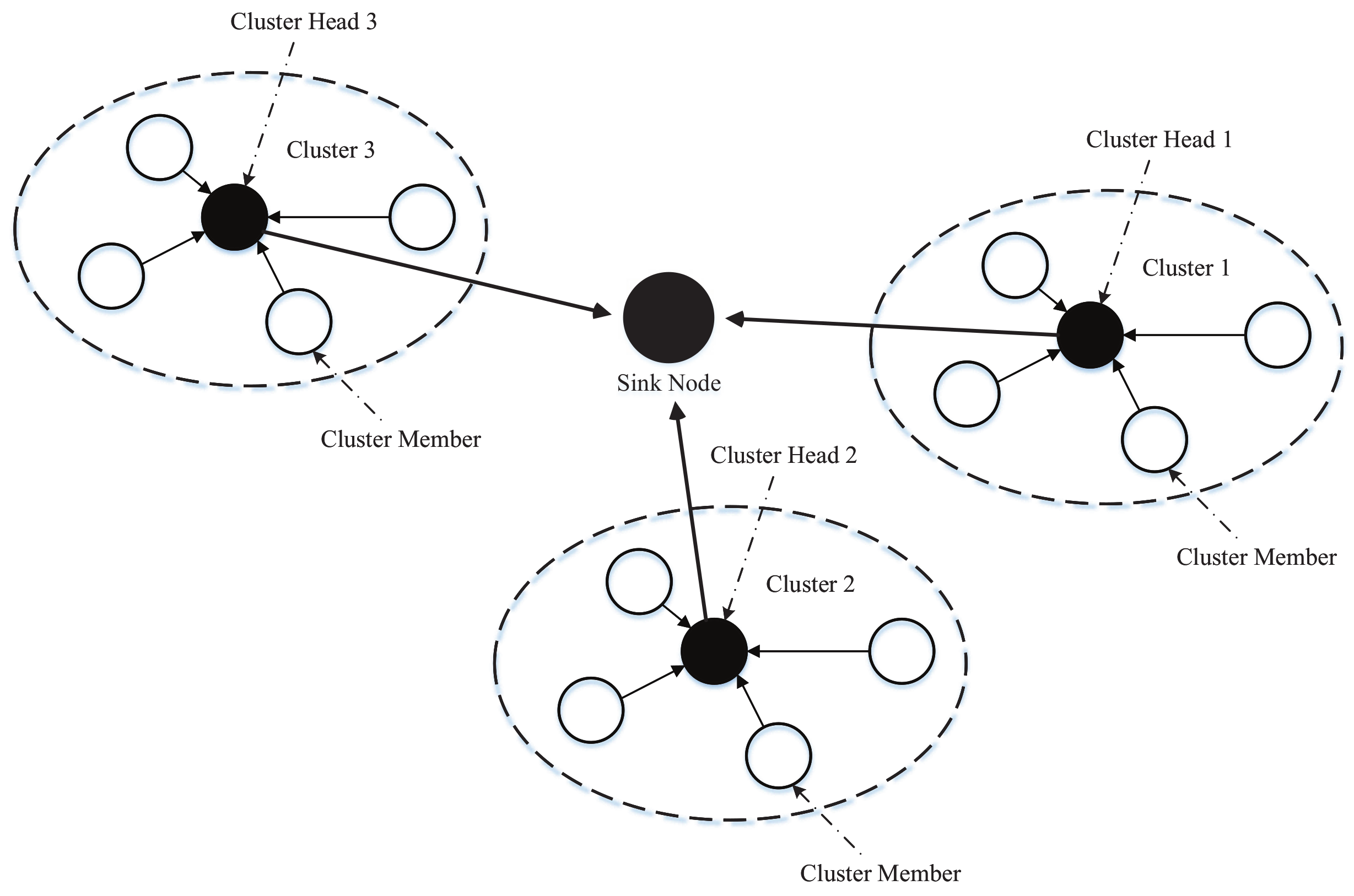

| Reference | Focus | Content Type | Physical Layer Security | Aerial–Terrestrial Integrated Communications | Emerging Techniques |
|---|---|---|---|---|---|
| [32,33,34] | These works propose the comprehensive and expandable frameworks for classifying PLS techniques, categorizing them into signal-to-interference-plus-noise ratio-based and complexity-based approaches, and reviewing their applications in various communication systems. | Theoretical and analytical | These works exploit wireless channel characteristics, such as noise, fading, and interference, to design transmission schemes that enhance the security of legitimate users while preventing eavesdropping. | × | × |
| [35] | These works exploit wireless channel characteristics, such as noise, fading, and interference, to design transmission schemes that enhance the security of legitimate users while preventing eavesdropping. | Analytical | The paper explores the application of PLS coding to enhance data confidentiality using the intrinsic randomness of the transmission channel. | × | × |
| [36,37,38] | These works provide a comprehensive review of covert communication as a promising solution for securing wireless networks, emphasizing its principle, applications, and the challenges it faces in practical implementation. | Theoretical | These works focus on utilizing randomness to conceal transmitted signals in covert communication networks, ensuring security by avoiding detection by the warden. | × | These works discuss the application of covert communication in various network topologies, along with the emerging techniques aimed at enhancing its security and practicality in future networks. |
| [39,40,41] | These works present comprehensive surveys of the air-to-ground propagation channel models, focusing on both large and small-scale fading models, their limitations, and the future research directions for UAV secure communication. | Theoretical and analytical | These works emphasize the need for accurate air-to-ground propagation models for secure and efficient UAV communication. | Accurate air-to-ground propagation models can potentially enhance the security of ATI-IoT by ensuring robust and reliable UAV communication. | × |
| [42,43,44] | These works provide comprehensive surveys of computational intelligence-based algorithms designed to enhance the networking and collaboration capabilities of ATI-IoT. | Analytical | × | To improve the performance of ATI-IoT, task allocation, path planning, and communication efficiency can be optimized. | These works highlight emerging computational intelligence-based technologies such as heuristic behavior search, policy learning, and hybrid algorithms that aim to address the challenges in ATI-IoT. |
| Reference | Optimization Objective | Method | IRS Type |
|---|---|---|---|
| [108,109,110] | Secure transmission rate maximization | Optimization of phase shift coefficients | Fixed IRS |
| [111] | Transmission power minimization | Optimization of power allocation and phase shift, and consideration of secure transmission rate | Fixed IRS |
| [112] | Secure transmission rate maximization | Optimization of beamforming, and consideration of artificial noise | Fixed aerial IRS |
| [113] | Minimum average secure transmission rate maximization | Optimization of power allocation, phase shifts, and drone trajectories | Mobile aerial IRS |
| [114,115] | Secure transmission rate maximization | Optimization of user scheduling, phase shifts, and drone trajectories | Mobile aerial IRS |
| [116] | Secure transmission rate maximization | Optimization of drone deployment, decoding order, and phase shift | Fixed aerial IRS |
| Reference | Optimization Objective | Method | Operating Mode |
|---|---|---|---|
| [120,121] | Co-channel interference minimization | Optimization of spectrum reuse and power control strategies | Half-duplex mode |
| [122] | Energy efficiency maximization of secure communications | Optimization of user scheduling and drone three-dimensional flight trajectories | Full-duplex mode |
| [123,124,125] | Secure transmission rate maximization | Optimization of resource allocation, and consideration of active attacks | Full-duplex mode |
| [126,127,128] | Secure transmission rate maximization | Optimization of mode selection, and consideration of cooperative interference and covert communication | Half-duplex and full-duplex modes |
| Technique | Description | Advantages | Disadvantages |
|---|---|---|---|
| IRS-based approach | This technique leverages IRSs to enhance physical layer security by dynamically adjusting the signal propagation environment. | The IRS enhances security by mitigating interference and eavesdropping risks and improves both the channel capacity and reliability of wireless communication. | IRS deployment requires advanced hardware and significant infrastructure. In addition, the signal processing and optimization involved in IRS configurations are complex. |
| D2D communication | This approach integrates D2D communication within ATI-IoT to enhance security by allowing direct communication between devices without involving base stations. | D2D communication reduces transmission distance, decreasing interception opportunities, and typically operates with lower power consumption. | There is a risk of unauthorized communication between devices, which poses a security threat. In addition, this approach will suffer from interference caused by other D2D devices. |
| Covert communication | This method focuses on transmitting information in a manner that makes it difficult for unauthorized parties to detect the communication, thereby ensuring its covert nature in the ATI-IoT. | This technique ensures high-level security by hiding the communication from potential eavesdroppers, and enhances privacy for users and devices. | Covert communications often lead to a reduction in transmission efficiency due to the need to disguise the signal. In addition, there is a potential for detection if covert methods are not implemented effectively. |
| Cooperative relaying systems | This method employs cooperative relaying to forward signals from a source to a receiver, with relays performing additional processing to enhance transmission security. | The presence of multiple relay nodes helps to obscure eavesdropping and improve security. Meanwhile, cooperative relaying increases communication coverage and reliability. | The use of relays introduces additional system complexity and can increase power consumption. In addition, the coordination and synchronization required among multiple relays can pose operational challenges. |
| Technique | Performance Metrics | Beneficial Scenarios |
|---|---|---|
| IRS-based approach | Secrecy capacity, signal-to-noise ratio, and secure throughput. | In large-scale antenna systems and dynamic channel conditions, IRS can be used to achieve confidential information transmission. |
| D2D communication | Secrecy outage probability, secure throughput, and bit error rate. | Scenarios in which D2D communication can enhance direct interaction while ensuring secure data transmission. |
| Covert communication | Secrecy capacity, bit error rate, and key generation rate. | Covert communication can be applied in scenarios with low detectability, such as military or privacy-sensitive applications. |
| Cooperative relaying systems | Secure throughput, secrecy capacity, and transmission delay. | Cooperative relaying systems can be deployed in scenarios where relay nodes are needed to enhance communication reliability and security, especially in areas with poor channel conditions. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, Y.; Wu, J.; Zhu, L.; Huang, F.; Wang, B.; Yang, D.; Wang, D. A Review of Physical Layer Security in Aerial–Terrestrial Integrated Internet of Things: Emerging Techniques, Potential Applications, and Future Trends. Drones 2025, 9, 312. https://doi.org/10.3390/drones9040312
He Y, Wu J, Zhu L, Huang F, Wang B, Yang D, Wang D. A Review of Physical Layer Security in Aerial–Terrestrial Integrated Internet of Things: Emerging Techniques, Potential Applications, and Future Trends. Drones. 2025; 9(4):312. https://doi.org/10.3390/drones9040312
Chicago/Turabian StyleHe, Yixin, Jingwen Wu, Lijun Zhu, Fanghui Huang, Baolei Wang, Deshan Yang, and Dawei Wang. 2025. "A Review of Physical Layer Security in Aerial–Terrestrial Integrated Internet of Things: Emerging Techniques, Potential Applications, and Future Trends" Drones 9, no. 4: 312. https://doi.org/10.3390/drones9040312
APA StyleHe, Y., Wu, J., Zhu, L., Huang, F., Wang, B., Yang, D., & Wang, D. (2025). A Review of Physical Layer Security in Aerial–Terrestrial Integrated Internet of Things: Emerging Techniques, Potential Applications, and Future Trends. Drones, 9(4), 312. https://doi.org/10.3390/drones9040312








