Abstract
Although deep learning (DL) methods are effective for detecting protocol attacks involving drones in sixth-generation (6G) nonterrestrial networks (NTNs), classifying novel attacks and identifying anomalous sequences remain challenging. The internal capture processes and matching results of DL models are useful for addressing these issues. The key challenges involve obtaining this internal information from DL-based anomaly detection methods, using this internal information to establish new classifications for uncovered protocol attacks and tracing the input back to the anomalous protocol sequences. Therefore, in this paper, we propose an interpretable anomaly classification and identification method for 6G NTN protocols. We design an interpretable anomaly detection framework for 6G NTN protocols. In particular, we introduce explainable artificial intelligence (XAI) techniques to obtain internal information, including the matching results and capture process, and design a collaborative approach involving different detection methods to utilize this internal information. We also design a self-evolving classification method for the proposed interpretable framework to classify uncovered protocol attacks. The rule and baseline detection approaches are made transparent and work synergistically to extract and learn from the fingerprint features of the uncovered protocol attacks. Furthermore, we propose an online method to identify anomalous protocol sequences; this intrinsic interpretable identification approach is based on a two-layer deep neural network (DNN) model. The simulation results show that the proposed classification and identification methods can be effectively used to classify uncovered protocol attacks and identify anomalous protocol sequences, with the precision increasing by a maximum of 32.8% and at least 26%, respectively, compared with that of existing methods.
1. Introduction
Nonterrestrial networks (NTNs) for sixth-generation (6G) systems are becoming increasingly popular owing to their comprehensive coverage, mobility, and resilience to severe natural disasters [1]. With the rapid advancement of drones and cost-effective low-altitude platform aerial vehicle manufacturing methods [2], drone swarming has emerged as a promising solution to address various issues for 6G NTNs, enabling information flow through interconnections, cooperative control, and resource sharing among base stations (BSs) and core networks (CNs) [3,4,5,6].
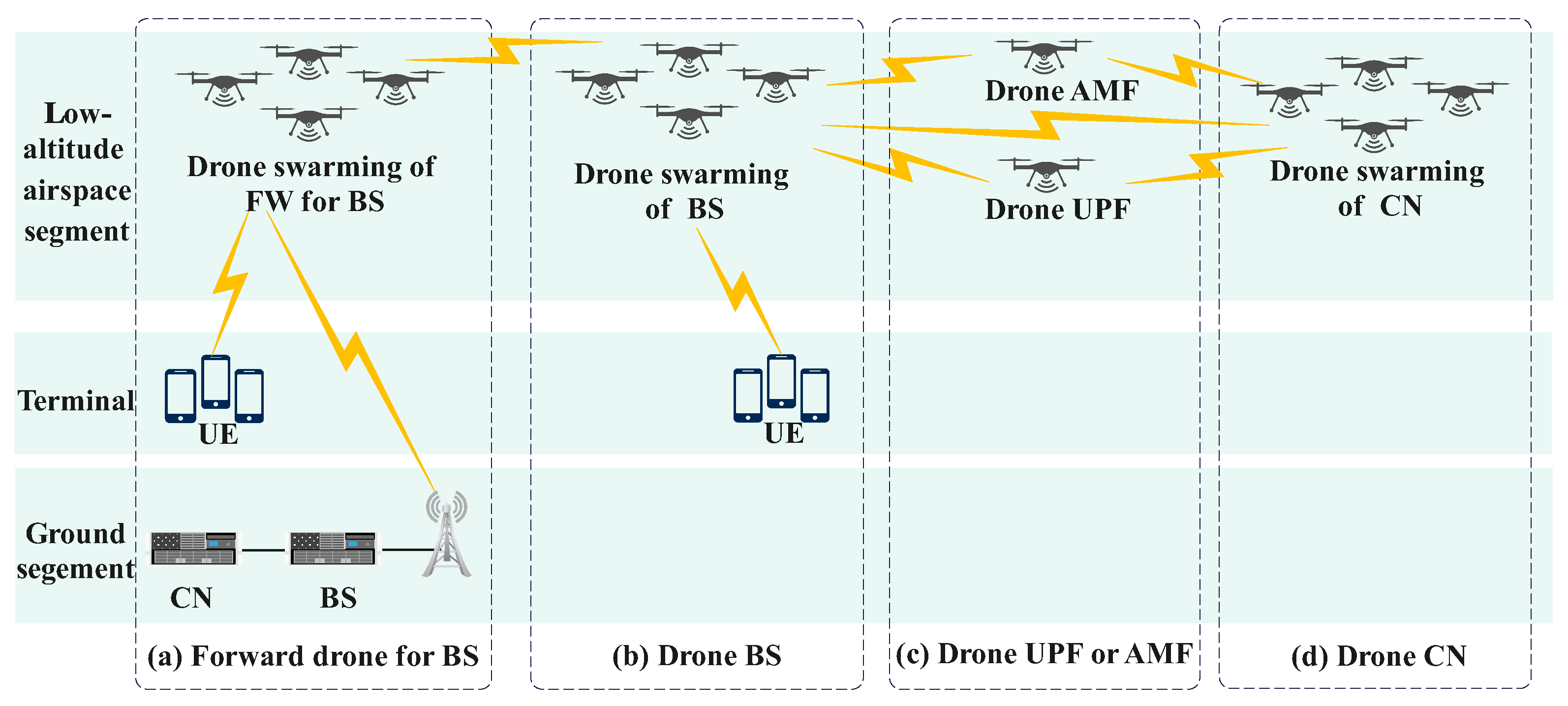
Drone swarming techniques for 6G NTNs have been designed for both BSs and CNs in 3rd generation partnership project (3GPP) standards and ongoing research. Drone swarming techniques involving BSs in low-altitude airspace, as defined by 3GPP standards, can be used to forward signals, as shown in Figure 1a, or act as BSs cooperatively, as shown in Figure 1b, thereby achieving continuous ground coverage [7,8,9,10,11]. Drone swarming techniques involving CNs in low-altitude airspace are still being developed on the basis of 3GPP standards, with options for deploying some or all functions of CNs through drone swarming [11,12,13]. The CNs in 6G NTNs are based on service-based architectures (SBAs) and have multiple network functions (NFs), including the user plane function (UPF) and various control plane NFs, such as the access and mobile management function (AMF). Drone swarming techniques involving CNs can be used to deploy the UPF or AMF, as shown in Figure 1c, or all NFs, as illustrated in Figure 1d. In this type of deployment, low-altitude airspace and ground NFs cooperate to facilitate the transmission of spatial information to ground stations and support the long-range transfer of terminal information, significantly reducing ground transmission latency [14].
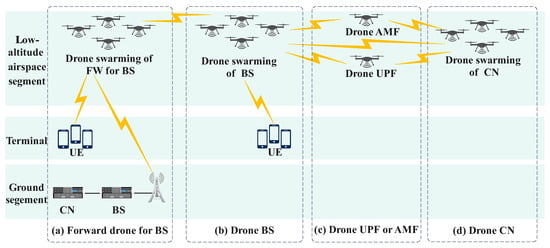
Figure 1.
Drone swarming of 6G NTNs.
6G NTN with drones will serve as an essential communication infrastructure [15]. The scenarios for 6G NTNs encompass global seamless connectivity, IoT services, emergency communications, disaster recovery, and autonomous driving, which require the available communication service [15,16,17]. In 6G NTNs, protocols are crucial for defining communication rules among NFs, ensuring efficient and reliable data transmission. However, low-altitude airspace NFs are particularly vulnerable to malicious protocol traffic from terrestrial user equipment (UE) and NFs in areas with unprotected coverage. This malicious protocol traffic can, for example, infiltrate CNs in low-altitude airspace through drone swarming involving BSs, resulting in paralysis of the entire low-altitude airspace network [5,18]. To prevent malicious protocol traffic [19,20,21], it is essential to detect, classify, and identify protocol attacks. Specifically, detection involves monitoring the presence of protocol attacks in 6G NTNs. Classification involves matching the detected attacks with predefined attack categories, which aids in selecting appropriate prevention strategies. Identification involves determining the anomalous protocol sequences associated with the detected attacks and the targets that must be protected with prevention strategies.
Recently, deep learning (DL)-based anomaly detection methods have shown exceptional performance in capturing complex patterns in drone and terrestrial mobile communication networks [22,23,24,25,26]. These methods can be categorized into rule-based and baseline-based detection methods, known as rule detection and baseline et aldetection [24,25,26]. In rule detection methods, covered attacks are effectively detected by comparing the attacks with threat features extracted from historical data; however, these methods have difficulty detecting uncovered attacks and identifying anomalous protocol sequences. Baseline detection methods, which are trained on attack-free 6G NTN traffic data, can detect deviations from normal behavior and are thus useful for detecting uncovered attacks; however, these methods provide only Boolean results and cannot be used to classify or identify specific anomalous sequences. In recent research, these methods have been designed for unmanned aerial vehicles (UAVs) [23,24,25,26,27,28], the internet of unmanned aerial vehicles (IoUAVs) [29,30,31], 6G networks [30,32], internet of thing (IoT) networks [22], and other networks, improving the detection of both covered and uncovered attacks [20,21,22,23,24,25,26,27,28,29,30,31,32] and the classification of known attacks [20,21,22,23,24,25,30,31,32].
However, these combined methods still fail in classifying uncovered attacks without new classifications and identifying specific anomalous protocol sequences, focusing instead on Boolean detection and classification labels.
The internal information and processes of DL models could be utilized to address these limitations. DL models can capture fingerprint information during the detection process, which is useful in classifying uncovered attacks, but this information is often obscured by the black-box nature of these models and high-dimensional mappings. Similarly, anomalous data captured via baseline detection methods are represented by intermediate features, making tracing these data back to the original protocol sequences difficult.
In recent studies, explainable artificial intelligence (XAI) techniques have been used to elucidate the processes underlying DL models, facilitating the extraction and utilization of internal information and processes in DL-based detection methods. The aim of XAI-based anomaly detection research and other communication networks is to make the detection process more transparent, thereby providing more credible results and optimizing accuracy. However, a significant gap remains in applying these explanations for classification and identification, posing substantial challenges.
Lack of explainability and collaboration. The objectives of existing interpretable detection methods are to provide credible results and optimize accuracy; however, these methods do not output the internal information of the DL model necessary for classification and identification, hindering the utilization of this information in classifying uncovered attacks and identifying anomalous protocol sequences of 6G NTNs. An explainable detection framework is needed to support the extraction of internal process information during the baseline and rule detection processes for classification and identification. Furthermore, this framework should enable real-time collaboration during the baseline and rule detection processes to ensure that the internal process information can be fully utilized. The key challenges are determining what information from the baseline and rule detection processes should be provided and how this information should be collaboratively utilized by the baseline and rule detection methods to improve classification and identification performance.
Extracting and improving black-box models with internal information. While baseline detection methods primarily provide Boolean outputs, they also capture deviations from normal behavior; these deviations contain critical fingerprint features of uncovered attacks but are not explicitly output. In DL-based rule detection methods, new classifications are established by retraining the model on the basis of new data to extract these fingerprint features, but this process can introduce delays in both training and deployment. The key challenges are determining how to extract internal fingerprint features from black-box baseline detection methods and how to establish a new online rule detection classification of 6G NTNs using the external fingerprint features captured during the baseline detection process.
Capturing original anomalous protocol sequences in the internal irreversible mapping process. During the baseline detection process, deviations between attacks and the baseline process are extracted by DL models from protocol data containing anomalies. To trace these protocol attacks of 6G NTNs back to the original anomalous data points, the deviation capture process must be reversed. However, this process involves high-dimensional abstractions within the black-box DL model, which are not explicitly provided and are challenging to reverse. The protocol sequences must be transformed into images so that deep learning models can process them while ensuring this conversion retains sufficient information for the reverse conversion of the DL model, which needs to be explainable.
To address these challenges and enhance the security of 6G NTN protocols, the explanation requirements and applications of classification and identification methods must be explored. Therefore, in this paper, we propose an XAI-based interpretable anomaly classification and identification method for 6G NTN protocols. In the proposed method, the rule and baseline detection processes are elucidated through XAI techniques. These methods operate synergistically to classify uncovered protocol attacks and identify specific anomalous protocol sequences. The contributions of this paper can be summarized as follows:
- We introduce an interpretable and collaborative detection framework for 6G NTN protocols. This framework analyzes in detail the interpretability demands of baseline and rule detection methods and their collaboration. Result and process explanations for the baseline and rule detection processes are integrated, fostering collaboration between these methods and supporting the classification of attacks and identification of anomalies with robust explanatory and collaborative capabilities.
- We design a self-evolving classification method for uncovered protocol attacks within the proposed framework. The rule and baseline detection processes are clarified, enabling synergistic extraction and learning of attack fingerprint features to classify uncovered protocol attacks.
- We design an online identification method to detect anomalous protocol sequences within the proposed interpretable framework. In this method, protocol sequences are transformed into images for DL-based detection, ensuring the traceability of the original anomalous protocol sequences after identifying the anomalous image section. To identify the anomalous image section, a two-layer architecture consisting of a prediction model and a detection model is designed, where traditional deep neural network (DNN) convolutions are replaced with exclusive OR (XOR) operations. This enables efficient and synchronized identification and detection of anomalies. Thus, the capturing of original anomalous protocol sequences in the internal irreversible mapping process is achieved.
The remainder of this paper is organized as follows. In Section 2, the current research on DL- and XAI-based anomaly detection methods and other communication networks is summarized. In Section 3, the protocol threat models for 6G NTNs and representative attack cases are introduced. In Section 4, the interpretable anomaly detection framework for 6G NTN protocols is designed. With the proposed interpretable framework, a self-evolving classification method for uncovered protocol attacks and an online identification method for anomalous protocol sequences are designed in Section 5 and Section 6. In Section 7, the simulation results are discussed, demonstrating the effectiveness of the proposed classification and identification methods. Finally, the conclusions of the paper are presented in Section 8.
2. Related Work
Anomaly detection methods based on DL models have demonstrated outstanding performance because of their ability to capture complex patterns in network traffic [22]. The DL models used in anomaly detection include convolutional neural networks (CNNs), DNNs, Gaussian mixture models (GMMs), generative adversarial networks (GANs), recurrent neural networks (RNNs), long short-term memory (LSTM) networks, and deep autoencoders (AEs).
Among the anomaly detection methods, rule detection approaches train models using historical attack data to extract features that represent these past attacks, known as fingerprint features. Consequently, the historical attacks and their fingerprint features are covered within the rule detection approach [25]. Attacks are classified by comparing the analyzed data with the fingerprint features of the attacks covered in rule-based detection methods. Rule detection methods based on DL models have been widely studied, with a focus on protocol and application attacks in UAV networks [23,27,28] and IoUAVs [29,30,31]. Various DL models, such as CNNs [27], DNNs [29], and RNNs [31], have been used to extract static or temporal fingerprint features. Hybrid models that combine CNNs and LSTM networks have also been employed to capture data anomaly features [28,29], making them suitable for 6G protocol traffic, which is inherently a time series [32]. These methods have been validated with datasets such as CICDDoS2019 [23], INS [27], KDD-CUP99 [28], CICIDS [29], MDVD [30], and 5G-NIDD [31]. However, existing rule detection methods are ineffective for classifying uncovered protocol attacks in 6G NTNs, as prior knowledge of the attack is not available. In addition, existing methods cannot be used to identify anomalous data.
On the other hand, baseline detection methods can be used to monitor uncovered protocol attacks by detecting deviations from normal protocol classifications with DL models, which can be trained on the attack-free protocol traffic data of 6G NTNs. Baseline detection methods have been studied for various scenarios, including UAV networks [24,33,34] and IoUAVs [35]. DL models and techniques such as YOLOv8 [24], one-class support vector machines (OC-SVMs) [33], LSTM networks [34], and Bayesian-LSTM [35] have been employed to establish normal baseline behaviors. However, baseline detection methods, which output Boolean results indicating only the presence or absence of attacks, have difficulty classifying uncovered protocol attacks and identifying anomalous protocol sequences in 6G NTNs.
To combine detection and classification, rule and baseline detection methods have been sequentially integrated to monitor attacks in UAV networks, IoUAVs, and the IoT in recent research. For IoUAVs, an AE and a DNN model [36] have been combined. A toolset is used to define normal behaviors and cover attack conditions, whereas the DNN model is used to classify normal behaviors, cover attacks, and uncover attacks. For UAV networks [37] and IoT [38] attacks, data are first processed through rule detection methods using RNN–LSTM [37] or CNN–LSTM [38] to identify covered attacks. Data that do not match covered attacks are then analyzed via baseline detection methods using the synthetic minority oversampling technique (SMOTE) algorithm [37] or convolutional LSTM [38] to detect uncovered attacks. These hybrid approaches achieve over 90% accuracy on the CICIDS2017, NSL-KDD, and KDD Cup-99 datasets. However, existing rule and baseline detection methods are merely sequentially connected; thus, these approaches are limited to the capabilities of the two individual methods, including detecting uncovered and covered attacks and classifying covered protocol attacks. With respect to detection, classification, and identification requirements, these rule detection methods, baseline detection methods, and sequential methods fail in terms of two key aspects. First, these methods fail in classifying uncovered attacks without establishing new classifications. Second, these methods fail in identifying specific anomalous protocol sequences, focusing on outputting Boolean detection results and classification labels. The related work of baseline and rule detection methods is summarized in Table 1.

Table 1.
Related work of baseline and rule detection methods.
Several methods have been developed to classify uncovered attacks by establishing new categories through retraining using meta-learning [39] or adding detection conditions inefficiently using tree models [40,41,42]. In meta-learning-based anomaly detection methods, models for multiple tasks are iteratively trained to extract attack features continuously, enabling the adaptive classification of uncovered attacks [39]. However, this iterative training process introduces detection delays because of the time consumed during training, which is unacceptable for 6G NTN services owing to their high communication availability requirements [40,41,42]. To address this issue, a real-time detection method based on the Hoeffding tree (HT) algorithm has been designed [43]. In this method, a new online branch is added to classify uncovered attacks when the cumulative deviations or other dynamic thresholds are met. This method can establish a new online protocol for attack classification in a 6G NTN. However, simply adding new branches for different detection conditions can degrade the detection performance because of the failure to leverage the precise fingerprint information of uncovered attacks. In fact, the DL model can capture fingerprint information during the baseline and rule detection processes, but this information remains incomprehensible and inaccessible because of the model’s black-box nature and high-dimensional mapping.
To identify the anomalies of the detected attacks, existing methods have been applied to localize anomalous NFs or communication processes in 5G core networks (5GCs) on the basis of logs [44]. However, these methods cannot provide the original protocol data at a finer granularity. To solve this problem, the protocol data interaction process between NFs is modeled as a graph to identify paths by which NFs interact with the corresponding anomalous protocol process [45]. However, anomalous protocol sequences or fields cannot be provided. In fact, these anomalous sequences or fields have already been captured and mapped to a high-dimensional space during the internal matching process by the DL-based baseline detection method. However, the captured anomalous protocol data are usually represented by intermediate information, such as instantaneous envelopes and statistical features, rather than the original protocol sequence, and the high-dimensional mapping process is irreversible.
To develop more understandable artificial intelligence (AI) models while maintaining high prediction accuracy, XAI technology represents a promising approach for obtaining internal fingerprint information and tracing it back to the original anomalous 6G NTN protocol sequences. Several popular XAI frameworks have been proposed to analyze the activities of DL models [46]. In the local interpretable model-agnostic explanations (LIME) approach, which was introduced in 2016, the local behaviors of AI models are explained through easily understandable proxy models, and the quantitative contributions of different inputs to the outputs are provided. A similar local rule-based explanations (LORE) approach was introduced in 2018. To improve the precision of the LIME approach, the high-precision model-agnostic explanations (Anchors) method was proposed in 2018. To further enhance the theoretical foundation of this approach, the Shapley additive explanations (SHAP) framework was designed in 2017, and an additive explanation model was used to determine the contributions of the inputs to the outputs. With respect to CNN models, class activation mapping (CAM) and gradient-weighted class activation mapping (Grad-CAM) were introduced in 2016 and 2019, respectively. In these methods, information from the last convolutional layer and gradients are utilized to highlight critical image areas using heatmaps, which can analyze 6G signal data or detect anomalous regions in drone images. These XAI frameworks offer explanations through proxy models, which map rules from inputs to outputs and quantify the contributions of inputs to outputs, as these proxy models and rules derived from DL models can provide consistent predictions and judgments, which is essential for protocol anomaly detection of the 6G NTN. These explanation capacities are useful in DL-based anomaly detection.
To improve the transparency and trustworthiness of DL-based anomaly detection methods, research on XAI frameworks and heuristic methods applied in anomaly detection has been performed, which can help classify uncovered protocol attacks; however, these frameworks have difficulty identifying anomalous protocol sequences.
The detection results can be explained by XAI methods to quantify the contributions of the inputs to the detection results. The LIME and SHAP frameworks have been deployed to analyze DNN-based [47] and LSTM network-based [48] anomaly detection models. The anomaly detection results of CNN-based models can be explained by the Grad-CAM framework [49]. In addition to XAI frameworks, heuristic adversarial-based [50] explanation methods have been developed to explain DNN-based anomaly detection results. These explanation methods were designed by combining approximate historical inputs, weighted random sampling, feature groups, and sparse group lasso methods to interpret the results of four DL–NIDS models, including the Kitsune, ODDS, RNN–IDS, and AE–IDS models [51]. These studies have provided the quantitative contributions of the inputs to the outputs, reflecting the degree of deviation. However, the use of quantitative contributions to extract the fingerprint features of uncovered protocol attacks and classify these attacks remains challenging.
Explanations of the detection results are used to enhance the detection scheme of anomaly detection methods. With the quantified contributions of the inputs to the detection results, the fingerprint features are obtained for use in the detection scheme. Random forest-based anomaly detection results can be interpreted via SHAP frameworks, which provide fingerprint features of intrusion traffic [52], and SVM-based anomaly detection results can be interpreted by the LIME framework, which provides fingerprint features of normal traffic patterns [53]. The fingerprint features representing the contributions of the inputs to the detection results are thus obtained. With these explanations, feature-matching detection strategies are designed and applied in conjunction with DL models to reduce the anomaly detection time, where merely the features affected by the anomalies are processed to reduce the volume of processed data [52,53]. However, using fingerprint features to classify uncovered protocol attacks remains challenging.
Explanation of the detection model for optimization. BD–GNNExplainer can be used to interpret GNN-based anomaly detection results to evaluate the detection performance and interpretability of models with different layers and configurations. On the basis of these interpretation results, the optimal structures and configurations of the GNN model can be determined [54]. XGBoost-based anomaly detection results can be interpreted by the SHAP framework to identify the typical features associated with different intrusion types. The explanation results can be used to guide the design of AEs for anomaly detection [55]. In these studies, the detection models have been elucidated, emphasizing the model architecture design and parameter selection process. The aim of interpretable classification is to increase the capability of the model rather than increase the accuracy within the existing detection range.
3. Threat Model
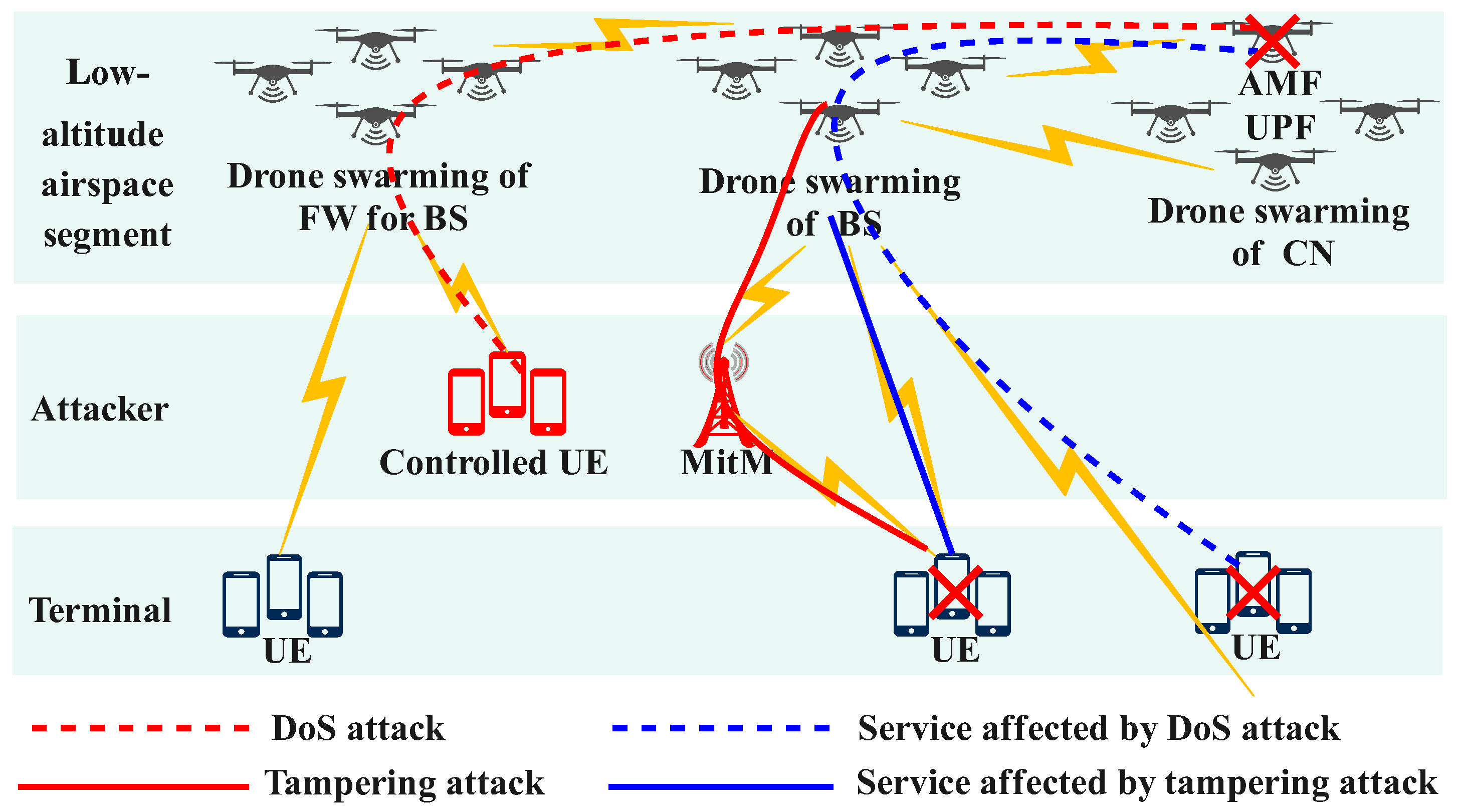
In 6G NTNs, protocol threats are particularly significant in low-altitude airspace; these threats often originate from malicious traffic generated by UE and man-in-the-middle (MitM) devices in remote and distributed ground areas with inadequate protection. This malicious traffic can penetrate the drone swarming CN through the distributed drones of BSs, potentially leading to paralysis of the entire low-altitude airspace network, as illustrated in Figure 2. The drones in 6G NTNs are still under discussion, protocols for both NTN terminals and the network side have been developed based on the core protocol standards established by 3GPP 5G [56,57]. Significant optimizations have been implemented in satellite and terminal-side protocols to facilitate seamless NTN smartphone connectivity. These improvements specifically address critical aspects such as time-frequency synchronization, precise timing relationships, efficient hybrid automatic repeat request (HARQ) configurations, and advanced mobility management strategies, as shown in Table 2.
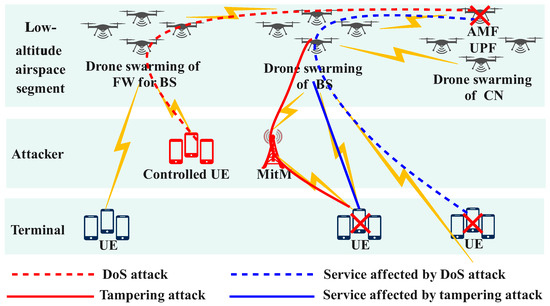
Figure 2.
Threat model for segmenting low-altitude airspace in protocol of 6G NTNs.

Table 2.
The relationship between NTN protocol and 5G protocol.
Thus, this paper presents case studies of UPF denial of service (DoS) and protocol tampering threats in 5G networks, as well as the corresponding protocol data collection process.
3.1. UPF DoS
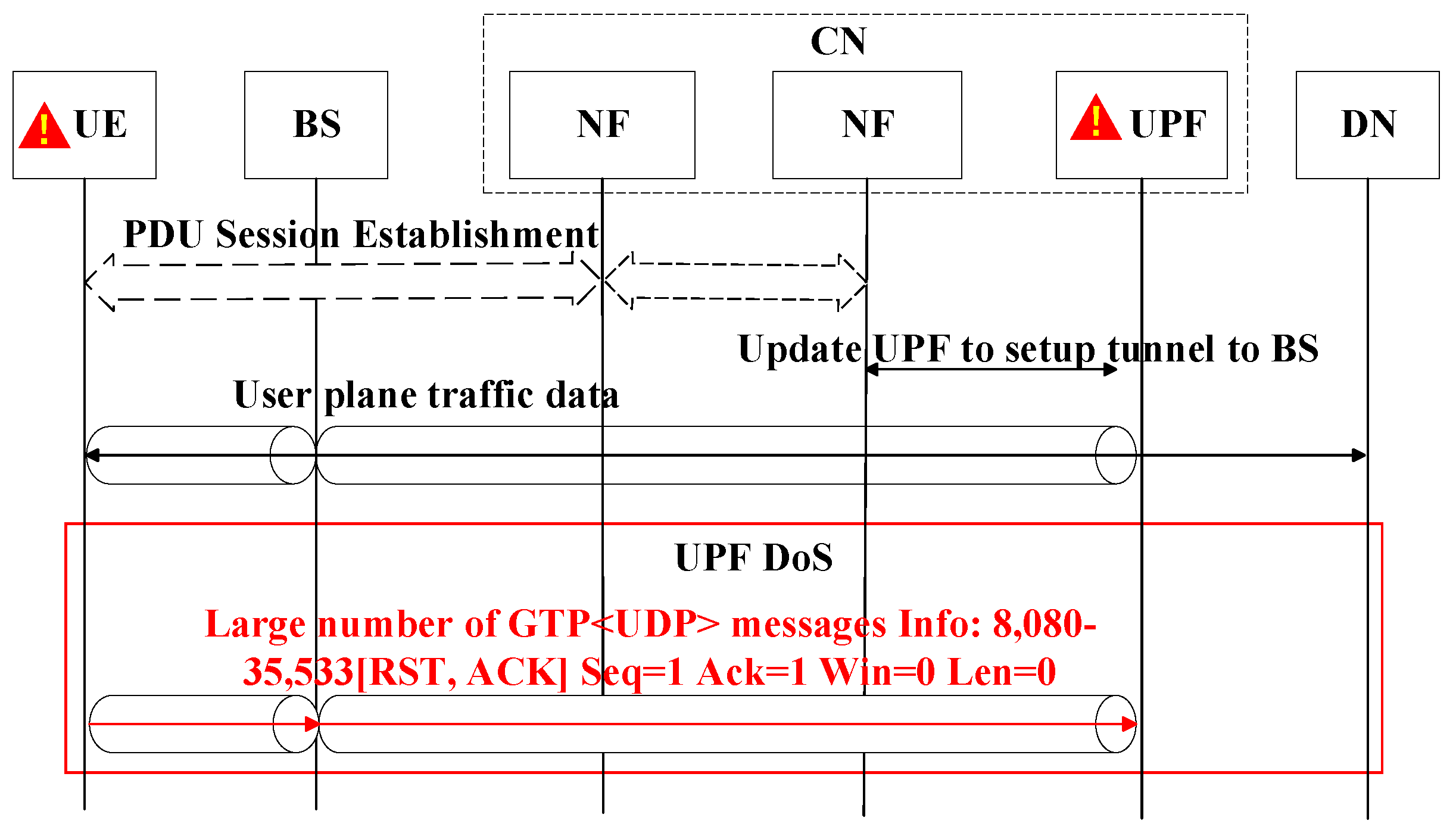
The UPF is responsible primarily for transmitting user data, and if it is overloaded, service disruptions occur [64]. Specifically, the UPF drone is particularly vulnerable to serious threats from malicious ground traffic at the intersection between low-altitude airspace and ground segments, as shown in Figure 3.
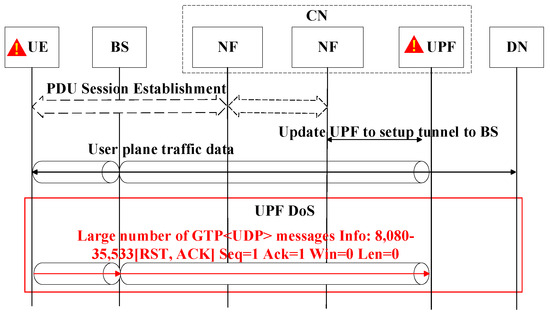
Figure 3.
Messages involved in UPF DoS attacks.
Here, we assume that attackers deliver malicious UE to unprotected remote areas covered by the 6G NTNs. The malicious UE can generate a large volume of protocol traffic, which is transmitted wirelessly to the low-altitude airspace of BSs and then to the UPF via the N3 interface connected to the low-altitude airspace of BSs. This surge in protocol traffic can overwhelm the UPF, leading to a DoS attack. The steps involved in the UPF DoS attack are as follows:
- The attacker UE is launched, with each piece of UE connected to the target 6G NTN.
- The malicious tool installed in the attacker UE generates a substantial volume of messages following the protocols of transmission control protocols (TCPs), user datagram protocols (UDPs), and internet control message protocols (ICMPs) within a short time. These requests are specifically configured with a high sending rate and large payload size.
- The UPF receives an overwhelming number of TCP, UDP, and ICMP requests from the attacker terminals.
After these steps are completed in the UPF DoS case, a significant burden is imposed on the computing resources of UPFs, rendering them incapable of effectively handling legitimate UE services. The malicious traffic in the second step can be generated using tools such as Bonesi (https://github.com/Markus-Go/bonesi.git, accessed on 2 December 2018) and Hulk (https://github.com/grafov/hulk.git, accessed on 17 May 2012). In this article, the tool of Bonesi is used to generate misconfigured traffic.
3.2. Protocol Tampering
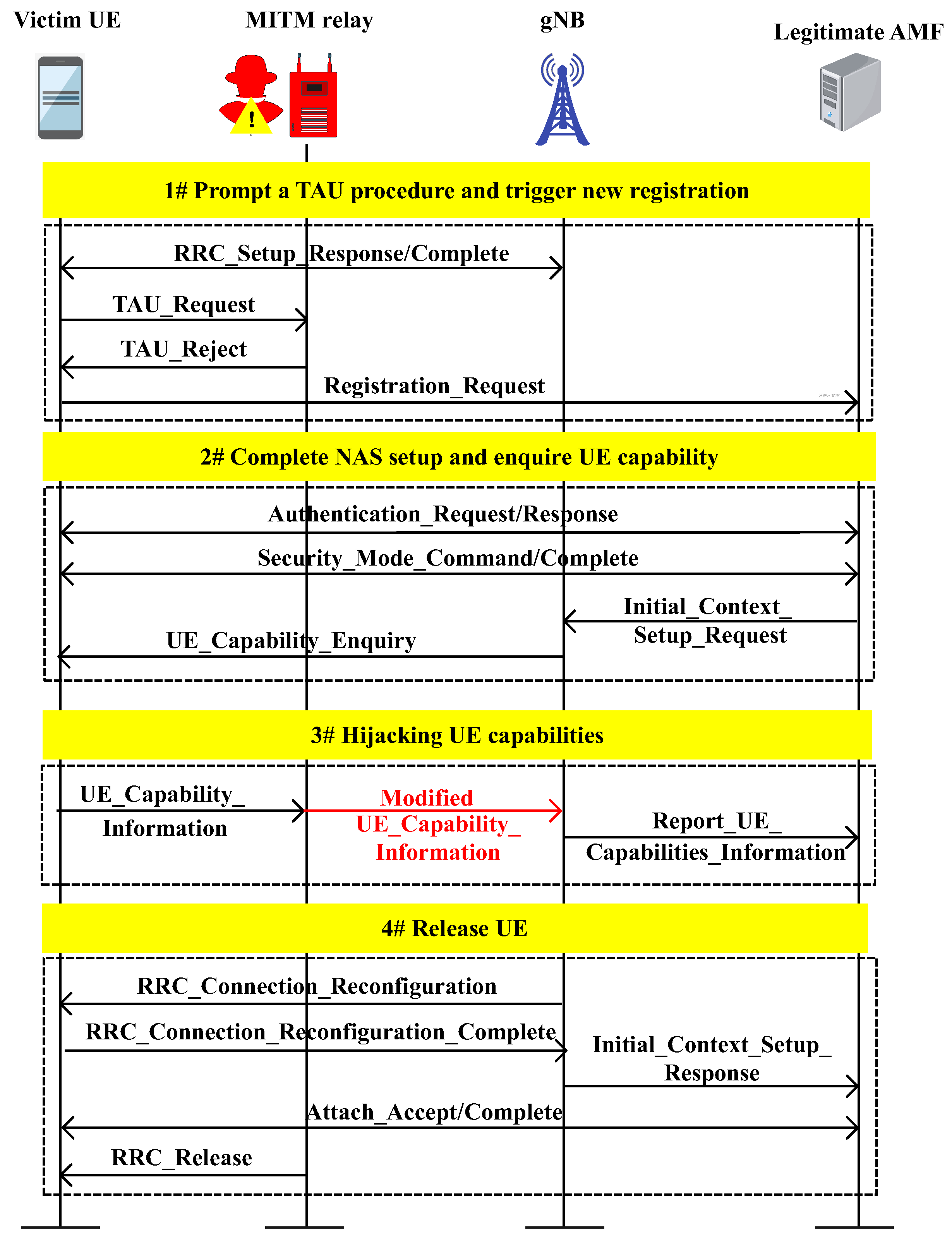
The attacks and the corresponding anomalous protocol sequences create vulnerabilities in the initial registration procedure of 6G NTNs, allowing for hijacking, forging, and replaying of control protocol signals via MitM attacks [65,66] or BS intrusions [5] owing to the aerial transmission of wireless signals. By utilizing these vulnerabilities, two threat cases for 5G protocols, i.e., UE capability hijacking and sequence number desynchronization, are discussed, as shown in Figure 4 and Figure 5.
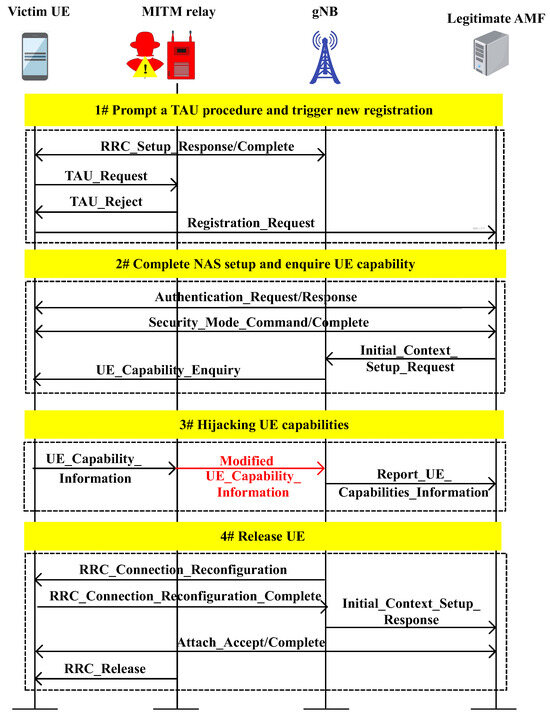
Figure 4.
Messages involved in hijack UE capability attacks.
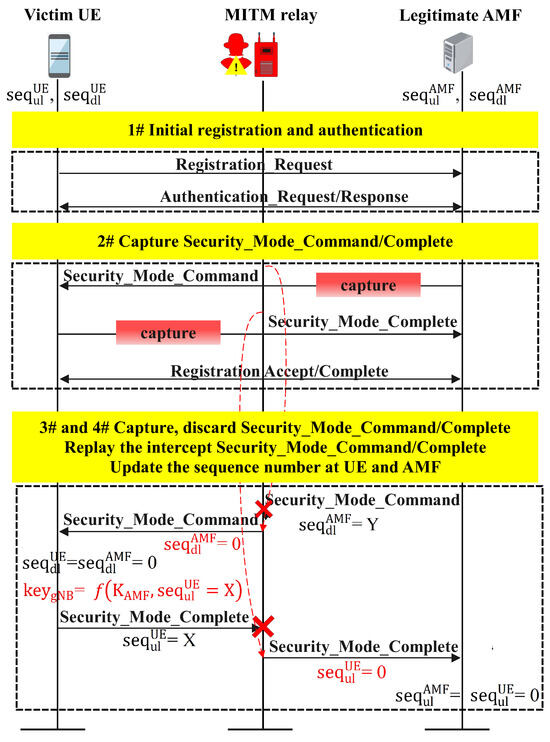
Figure 5.
Messages involved in sequence number desynchronization attacks.
3.2.1. Hijacking UE Capability
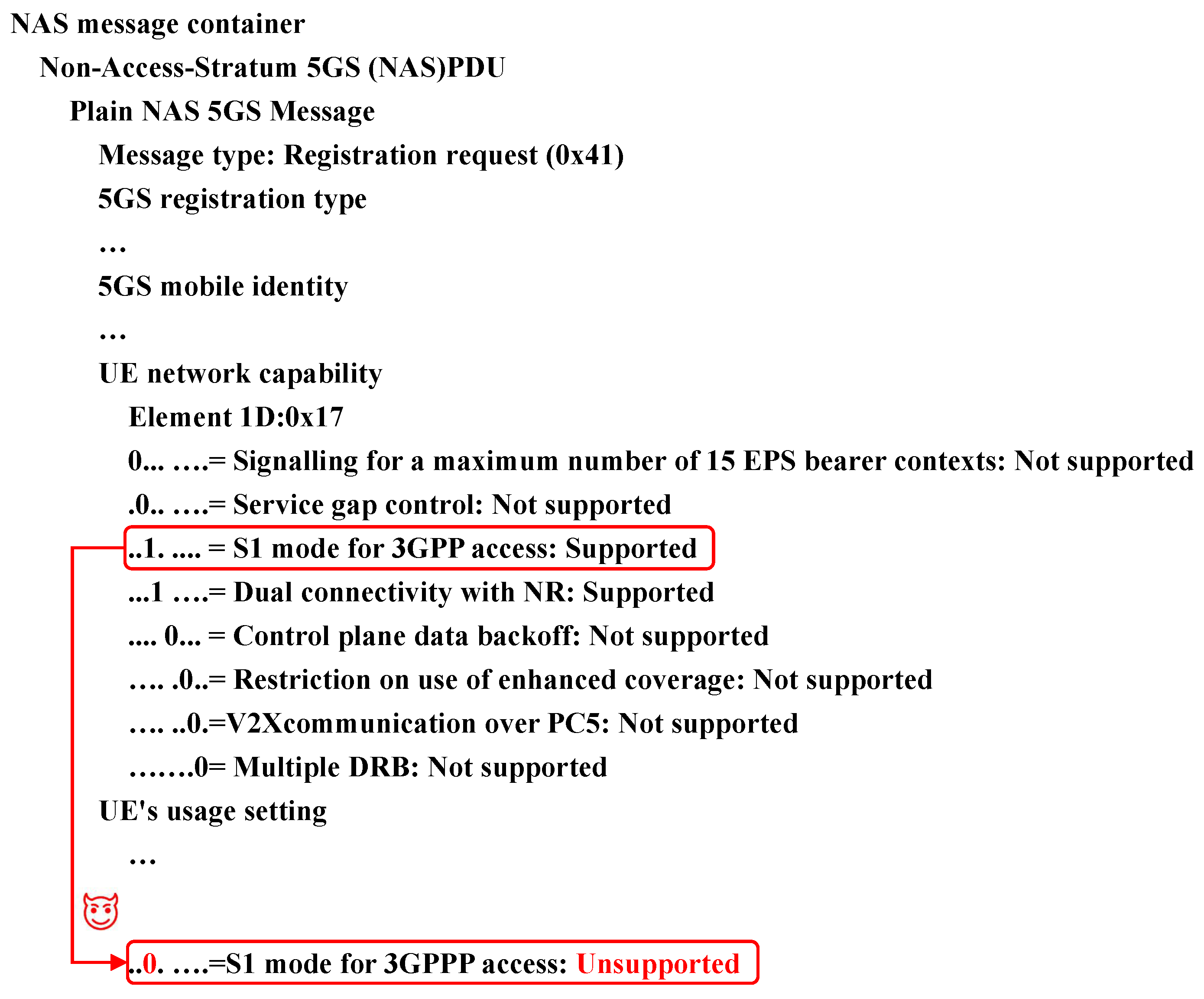
In protocol tampering attacks, hijacking UE capability involves intercepting and altering the capability information of the UE transmitted in plaintext format. This information, defined by the integration of hardware, software, and applications in a terminal device according to 3GPP standards, includes the supported frequency bands, data transmission rates, and carrier aggregation technologies. The plaintext transmission method makes the UE capability data vulnerable to interception and modification by MitM relay attacks. The hijack UE capability attack [65,66] proceeds through the following four stages, as shown in Figure 4:
- To initiate the attack, the MitM relay uses a different tracking area code (TAC) from the device’s registration area, which prompts a tracking area update (TAU) procedure. The relay then rejects this with a TAU request message, erasing the current security context and temporary identities, and a new registration is triggered via an attach request to the MitM relay.
- By forwarding the messages, the nonaccess stratum (NAS) security setup for the UE can be completed. As this involves the creation of a new registration, the AMF prompts the next generation node B (gNB) to obtain the capabilities of the UE.
- Before the UE capability information is sent from the UE to the gNB, the MitM relay changes the S1 mode from supported to unsupported. The modified message is then sent to the network, allowing the RRC security and registration processes for the UE to be completed.
- The UE is released to the network with an RRC release message. The modified capabilities are forwarded by the gNB to the AMF, eliminating the need to repeat the capability transaction.
After the attack, the piece of UE is recognized as a device without supporting the S1 mode when it next connects to the gNB, resulting in reduced service quality. The S1 mode enables it to be served by non-standalone networks, whereas the N1 mode allows the UE to be served in standalone networks. To transition into a non-standalone network region, the network checks the UE’s previously stored capabilities to ascertain whether it supports the S1 mode. However, if the UE’s S1 mode support status is maliciously changed from “supported” to “unsupported”, the UE will encounter a service interruption when entering the non-standalone network service area.
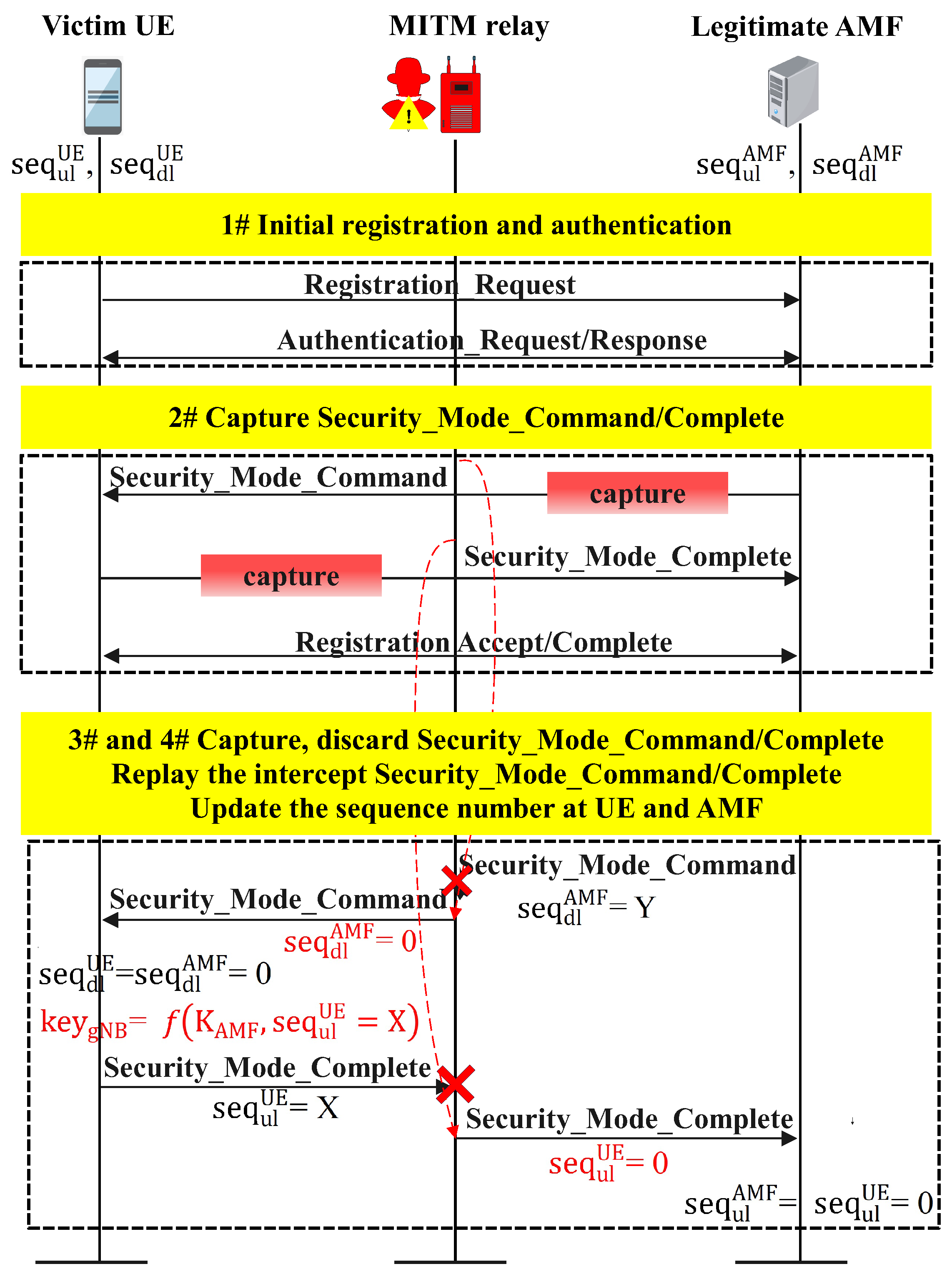
3.2.2. Sequence Number Desynchronization
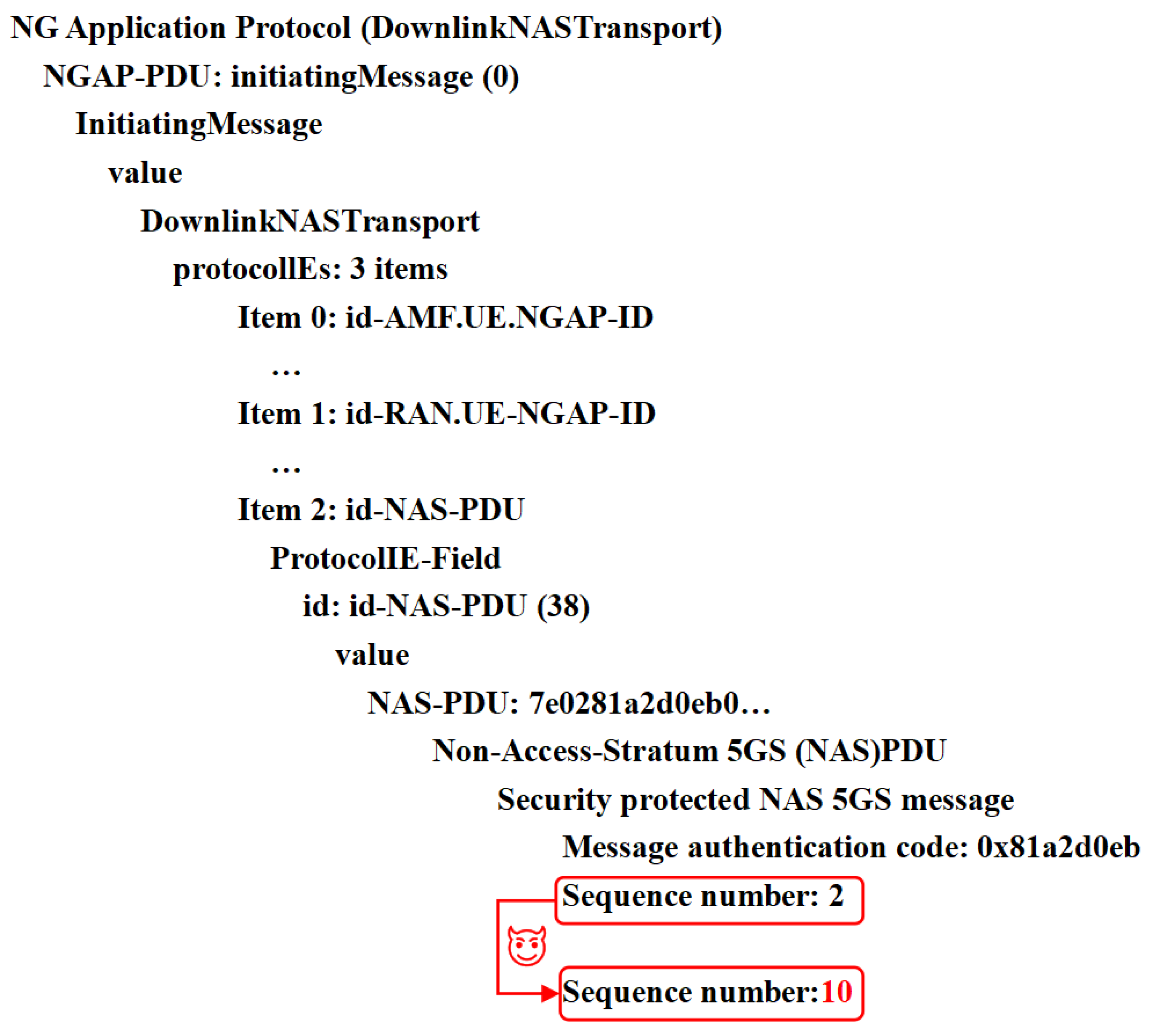
As with the other attack cases involving protocol tampering, sequence number desynchronization [67] involves exploiting vulnerabilities in the synchronization mechanism between the UE and 6G NTNs. To prevent replay during the registration procedure, the UE and 6G networks are synchronized by storing NAS counters for sending and receiving at the UE and AMF ends. An NAS counter is a 24-bit unsigned integer composed of a 16-bit overflow counter (oc) concatenated with an 8-bit sequence number (seq). The stored sequence numbers are denoted , , , and , indicating the numbers of uplink (ul) and downlink (dl) protocol messages at the ends of the UE and AMF. and are local parameters obtained by counting the messages sent by the UE and AMF, respectively, and and are the network parameters obtained via the received message at the UE and AMF ends, respectively. There is a vulnerability in refreshing and with the received and when the sequence number of the newly received message (for example, ) is less than the sequence number of the last message that was accepted (). Thus, a MitM relay attack may involve capturing and replaying the Sec_Mode_Command and Sec_Mode_Complete messages with the uplink and downlink sequence numbers being 0, as shown in Figure 5. Sequence number desynchronization attacks are performed according to the following four stages, as shown in Figure 5:
- The adversary forces the victim UE to establish a connection with the MitM relay, and the MitM relay transmits unauthenticated initial broadcast messages at a higher signal strength.
- The MitM relay intercepts both the Sec_Mode_Command and Sec_Mode_Complete messages during the initial registration process.
- The adversary waits to capture and discard the subsequent Sec_Mode_Command and Sec_Mode_Complete messages during the RRC layer key refreshing process and then relays the intercepted Sec_Mode_Command and Sec_Mode_Complete messages and sets them to 0 to pass the integrity verification.
- The locally maintained and are updated to 0 at the AMF, and the UE ends on the basis of the received and . Notably, with this attack, the adversary cannot reset the and that are locally maintained by the UE and AMF, respectively.
With this attack, the adversary can reset and , which the AMF and UE maintain remotely. This attack disrupts the connection between the UE and the network, leading to repeated reconnections that can block services and drain the battery. It also risks incurring excessive charges through continuously resending identical data packets.
3.3. Classification and Identification Demands
DoS attacks of 6G NTN protocols, such as UPF DoS attacks, cause network service disruptions by disabling NFs. Thus, the key to defending against DoS attacks of 6G NTN protocols is to classify the attacks and identify the failed NFs. When a DoS attack is classified, the protocol traffic received by the identified failed NFs needs to be intercepted. It is easy to identify the failed NFs; for example, a failed UPF can be easily identified through logs in UPF DoS attacks. However, the lack of 6G NTN protocol attack data makes classifying UPF DoS attacks challenging. Thus, we design self-evolving classification methods to cover unclassified protocol attacks.
Attacks such as hijacking UE capabilities and sequence number desynchronization, which involve tampering with protocol sequences or fields, are more covert in 6G NTN environments than in other networks. Degraded NFs, such as those of UE, may not correspond to the entities actually sending or receiving the attack protocol message. Consequently, the protection target differs from the failed NF. The critical defense strategy is to identify anomalous protocol sequences, analyze their transmission paths, and intercept and monitor the corresponding NF and protocol messages. Here, we design online methods for identifying anomalous protocol sequences.
4. Interpretable Anomaly Detection Framework for 6G NTN Protocols
To classify uncovered protocol attacks and identify anomalous protocol sequences online, transparent and synergistic approaches must be applied. Here, we present an XAI-based interpretable anomaly detection framework for 6G NTN protocols. To achieve this, we first analyze the explainability and collaboration requirements of the framework. We then assess the existing capacity of XAI-based anomaly detection methods, determining what knowledge gaps remain to be addressed. Finally, a coordinated and explanatory approach for classifying uncovered attacks and identifying anomalous protocol sequences is designed.
4.1. Explanation and Collaboration Demands
DL-based anomaly detection methods process protocol data and output detection results. The explanatory and collaboration demands of DL-based anomaly detection are analyzed considering both the detection process and the detection outputs of rule detection and baseline detection, with a focus on classifying uncovered protocol attacks and identifying anomalous protocol sequences.
To classify uncovered protocol attacks, we need to develop a self-evolving rule detection method based on the fingerprint features of uncovered attacks. Despite the lack of fingerprint features for uncovered attacks, these fingerprint features can be reflected by the deviations captured during the baseline detection process and used as the basis for analyzing the detection results. Therefore, the baseline detection results must be explained to output the deviation information, which can be used to extract the fingerprint features of uncovered attacks. To establish a new rule classification method using external fingerprint features in an online environment, we need to make the rule detection process interpretable, focusing on how fingerprint features influence the detection process and results. With this approach, the system can self-evolve, and the focus of the feature can be adapted according to the external fingerprint feature information.
The collaboration between rule and base detection methods is also analyzed. The detection results for uncovered attacks from rule detection can trigger baseline detection. Baseline detection can abstract and output the weights of fingerprint features to rule detection. Rule detection must be designed to support explanations and adjust the weights of fingerprint features accordingly.
To identify anomalous protocol sequences online, tracing anomalous protocol sequences on the basis of the detection and/or classification results is essential. An explanation of the detection process focusing on the high-dimensional matching process offers little assistance for this task. The baseline detection results can be used to determine the quantitative contributions of the fingerprint features, as the features with larger contributions may reflect the anomalous protocol sequences caused by attacks. However, extracting these features using irreversible statistical methods or high-dimensional mapping approaches makes it difficult to obtain the original anomalous protocol sequences. To address this challenge, we must integrate XAI capabilities into baseline detection methods. This integration enables the tracking of protocol data and the original information throughout the entire mapping process, allowing us to output the detection results alongside the corresponding anomalous protocol sequences.
4.2. Interpretable Framework
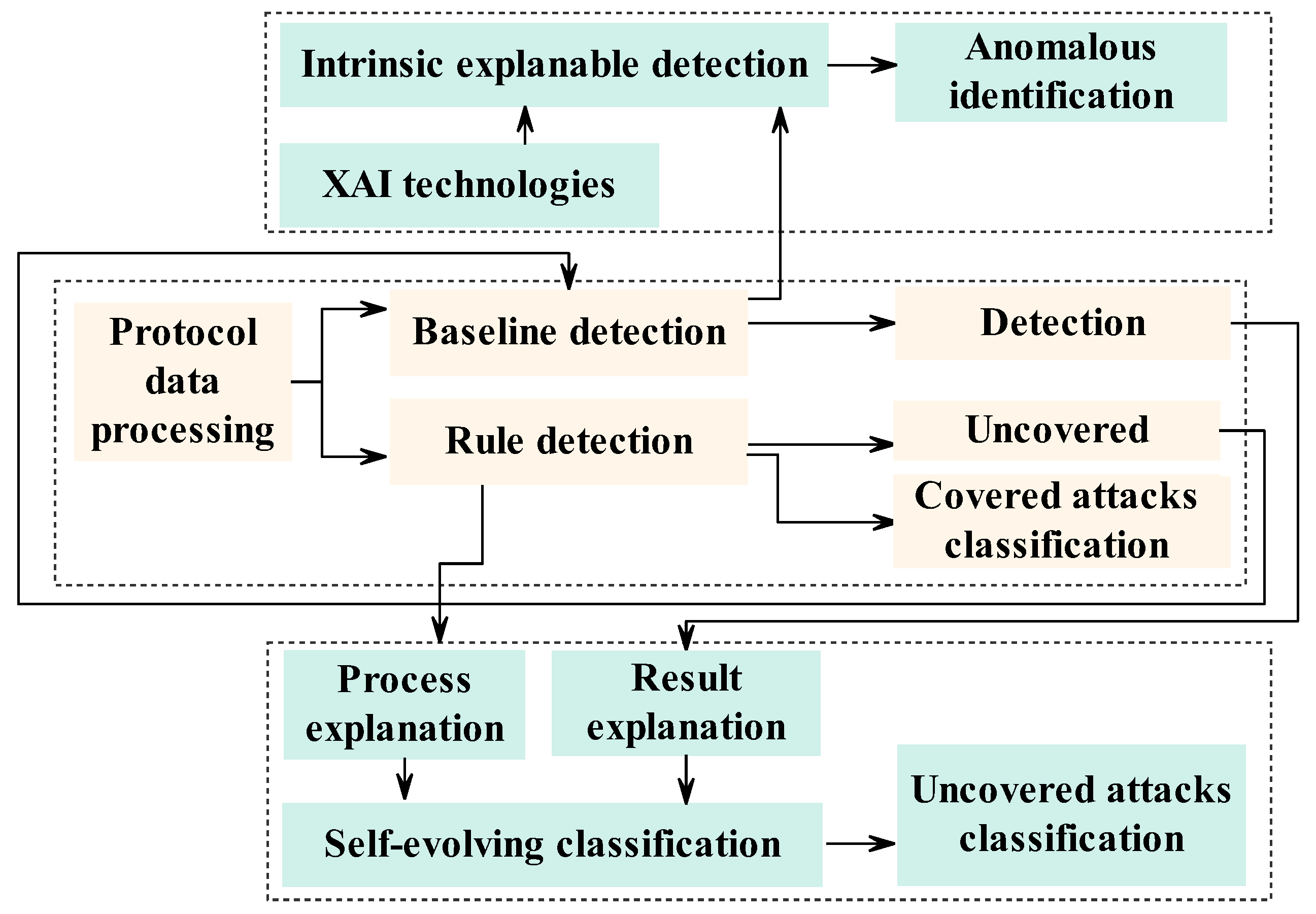
To design an interpretable framework and thereby obtain explainable detection results, an explainable detection process, and interpretable baseline detection results, an XAI approach was introduced to the current detection framework, as shown in Figure 6. The explainable detection results can be obtained via the current XAI method, whereas an explainable detection process and interpretable baseline detection method still need to be designed. With these explainable capacities, self-evolving classification and online identification of anomalous protocol sequences can be achieved.
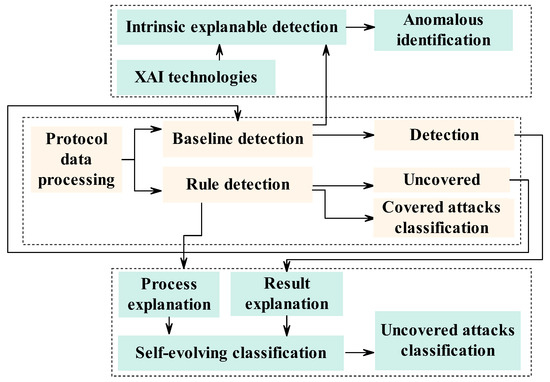
Figure 6.
Self-evolving anomaly detection framework with an online identity.
In the self-evolving classification process, an XAI method is used to explain the rule detection process and baseline detection results. The focus of the explanation of the detection results is the deviations of the attacks from the normal baseline, and these deviations are used to extract fingerprint features. The rule detection’s DL model trains feature weights, assigning larger weights to fingerprint features of the covered attacks, a process referred to as the attention mechanism; features with larger weights receive more attention. To classify the uncovered protocol attacks, their fingerprints must also receive more attention. Thus, an explanation of the attention mechanism is required to support the adjustment of the weights in the self-evolving classification of uncovered protocol attacks. By combining the baseline and rule detection methods with explanations of the detection results and process, a self-evolving classification method for uncovered attacks can be developed.
In the online identification of anomalous protocol sequences, an XAI method is used to provide inherently interpretable baseline detection results, which can be used to track protocol data and the original information throughout the entire mapping process. Furthermore, the detection results and the corresponding anomalous protocol data can be obtained simultaneously, thereby enabling effective anomaly identification.
The designs of the self-evolving classification method for uncovered protocol attacks and the online identification method for anomalous protocol sequences used in the explainable framework are discussed in the following sections.
5. Self-Evolving Classification Method
To create a self-evolving classification method for uncovered 6G NTN protocol attacks, the rule and baseline detection processes are elucidated using XAI technologies. Furthermore, these methods operate synergistically to extract and learn from the fingerprint features of uncovered protocol attacks. Fingerprint features, which represent the normal behavior of protocol attacks, which have distinct trends, are represented by feature parameters extracted from protocol traffic. To extract the fingerprint features of uncovered attacks, transparent baseline detection results are obtained using XAI technologies. This transparency allows the deviations of uncovered attacks from the normal baseline behavior to be identified and their fingerprint features to be extracted. To learn from these fingerprint features, a transparent rule detection process is also obtained using XAI technologies. With this transparency, understandable and adjustable attention can be directed to specific features during the rule detection process. A collaborative approach involving the baseline and rule detection methods is then designed. In particular, the fingerprint features obtained from the baseline detection process are shared with the rule detection method, enabling the latter to increase the classification accuracy on the basis of this external information.
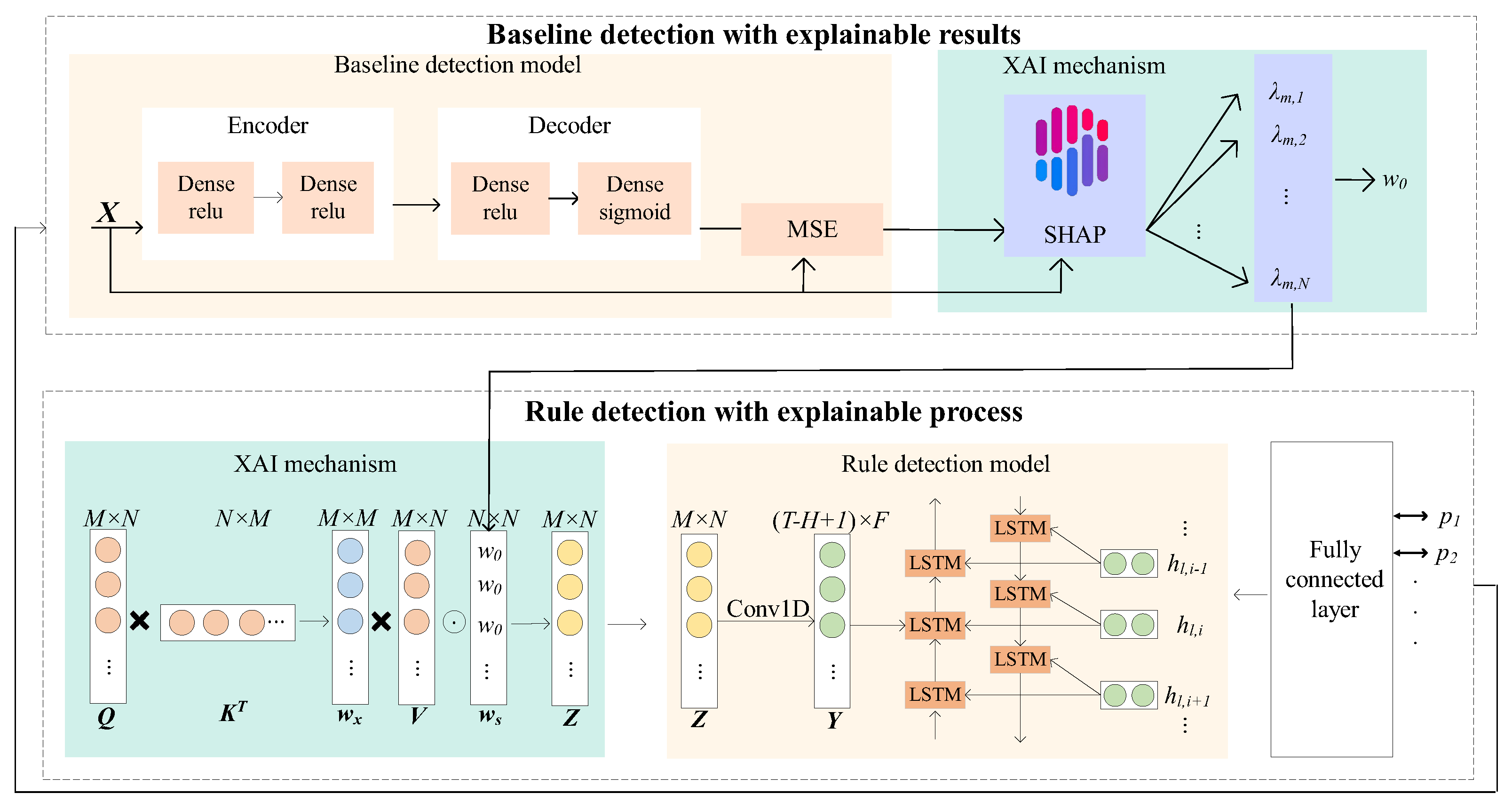
The self-evolving classification method is designed considering a baseline detection method with explainable detection results. In particular, the fingerprint features of uncovered attacks are extracted by explaining the quantitative contributions of the protocol features to the detection results. Furthermore, rule detection with an explainable detection process is implemented; in this process, the attention to the features is explainable and can be adjusted during the detection process, as shown in Figure 7.
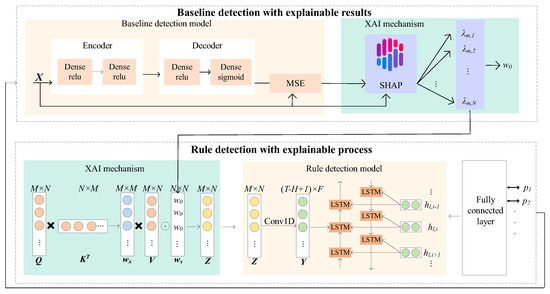
Figure 7.
Self-evolving classification method.
5.1. Baseline Detection with Explainable Results
The baseline detection method is made transparent on the basis of the explainable results. This method includes the baseline detection model, which matches the detected protocol features with the normal baseline, and an XAI mechanism applied to the detection results, which captures the deviation between the protocol traffic and the baseline, as shown in Figure 7. The baseline detection model is designed on the basis of an AE DL model to form the baseline of normal protocol behavior. With this approach, attacks can be efficiently detected, including uncovered protocol attacks. The SHAP-based XAI mechanism is applied to the detection results to make the baseline detection model transparent; this model provides the quantitative contributions of the protocol features to the detection results. The features with significant contributions are considered fingerprint features. The fingerprint features will be sent to the rule detection process, where attention is adjusted based on their quantitative contributions.
To obtain the quantitative contributions, the anomalous protocol feature flows detected by the baseline detection model are first consolidated; these flows are referred to as attack flows. The quantitative contributions of each attack flow are obtained, normalized, and fed back into the rule detection model. First, the SHAP model interprets local anomalous protocol data that deviate from the baseline. Then, the quantitative contributions of the features for each attack flow are calculated with the SHAP model. For attack flow k, the quantitative contribution of the nth feature is represented by , which is given by its Shapley value as follows:
where S is the set of all the features except the nth feature. indicates the number of elements. The function f represents the prediction probability. Equation (1) provides the marginal contribution, which is the variation in the prediction value of the baseline model when the nth feature is input. With Equation (1), the quantitative contributions of each feature can be normalized among the attack flows. The contribution of feature n is calculated as
where is the expectation function, and . The contribution values reflect the fingerprint features of the uncovered attacks. Larger positive values indicate that the features significantly deviate from the normal baseline values, whereas larger negative values indicate that the features closely match the normal baseline values. The explanation results of the baseline need to be expressed as feature weights properly to support the adjustment of the rule detection’s focus. Thus, the weight of feature n is denoted and is calculated as
Define the weight set . Let with .
With Equation (3), it can be seen that the weights are calculated by the contributions. The negative contributions of the features indicate no anomalous trends of those features. Including these contributions will decrease the probability of the classification, where the probability of being the classification is calculated by adding the contributions of the features. For the features indicating no anomalous trends, their contributions are negative. Including these contributions will decrease the probability of the classification. Therefore, the attention of the positive contribution features can be enhanced, and the attention of negative contribution features will be decreased in rule detection.
5.2. Rule Detection with an Explainable Process
In this section, the rule detection process is made transparent, allowing the focused features and their weights to be adaptively adjusted to classify the uncovered protocol attacks in 6G NTNs.
The DL model for rule detection trains feature weights, assigning larger weights to fingerprint features of the covered attacks, a process referred to as the attention mechanism; features with larger weights receive more attention. To classify the uncovered protocol attacks, their fingerprints must also receive more attention. Thus, an explanation of the attention mechanism is required to support the adjustment of the weights. To make the attention mechanism understandable and thus adjustable, i.e., input the feature weights of the uncovered features, the self-attention model is introduced, which is applied before the deep learning models in rule detection.
This method is designed to consist of an XAI mechanism in the detection process, which involves adjusting the rule detection feature patterns, and a rule detection model, which involves matching the detected protocol features with the feature patterns of the covered attacks, as illustrated in Figure 7. During training, a wide range of fingerprint features of covered attacks can be obtained from extensive open-source datasets and used to predefine the rule detection patterns. In the rule detection model, a one-dimensional CNN and a bidirectional LSTM (BiLSTM) network are integrated; this approach enables efficient matching of the protocol features with the covered attack patterns.
The XAI mechanism used in the detection process is placed before the rule detection model, which is the key to establishing a new classification. The XAI mechanism used in the detection process is designed with a modified attention method, in which an additional weight adjustment is performed on the basis of the feedback results from the baseline detection process. Assume that the protocol features that need to be detected are represented by X, where represents the mth protocol flow and nth feature. The attention layer parameters, i.e., the value vector, query vector, and key vector, are represented by V, Q, and K and given by
where are the weight matrices obtained by the backpropagation algorithm and , , . By setting , .
Then, on the basis of the input protocol features X, a modified attention layer is designed to output the adjusted protocol features represented by Z, as follows:
where represents the output of the original attention layer and where represents the enhancement in the time series characteristics of X. is the introduced weight for adjustment, which adjusts the focus of the protocol features on the basis of the feedback, namely, the quantitative contributions of the features.
To obtain Z, is calculated on the basis of Q and K, as follows:
where and is normalized by to avoid the extreme output of the Softmax function. is calculated via Equation (6), which is expressed as
where contains M values; thus, . On the basis of Equations (5)–(7), the output of the attention mechanism Z can be calculated, where and . With , the focus on the features and their weights can be adjusted on the basis of the fingerprint features of the uncovered protocol attacks. The process of the self-evolving classification method is given in Algorithm 1. It can be seen that the baseline and rule detection models are trained first. Then, the detection begins with the rule detection. The uncovered attack detection results from rule detection can trigger the baseline detection. The baseline detection can detect, abstract, and output the weights of the fingerprint features to the rule detection. Finally, the rule detection can adjust these weights of fingerprint features to classify uncovered protocol attacks. In the proposed self-evolving classification method, no more than one iteration occurs. When there are no uncovered protocol attacks, no interaction takes place. If an uncovered protocol attack exists, the rule detection first identifies it and outputs that it is uncovered. Then, the baseline detection runs to indicate that it is an uncovered attack. Finally, the rule detection evolves and classifies the uncovered detection. Additionally, to further reduce time consumption, the first and second steps can be performed simultaneously, which will require more computational resources.
| Algorithm 1 Self-evolving classification algorithm. |
|
6. Online Identification Method
In the proposed interpretable detection framework, an intrinsically interpretable identification method is designed to capture and output anomalous protocol sequences during the detection process. To achieve this, since all XAI frameworks are extrinsic and cannot be adopted directly, the main principles used to design an intrinsic anomaly identification method for 6G NTN protocols are analyzed as follows.
The original information of the protocol signals is input instead of the instantaneous envelope and statistical features. The inputs with positive contributions can be inverted to retrieve the original protocol, namely, the anomalous protocol sequences. Additionally, inputs must be formatted to ensure compatibility with the DL models.
Inputs are processed with the original protocol information efficiently in the DL models. To reduce the computational load associated with the original protocol data, inputs can be segmented into static and dynamic parts on the basis of their variability during 6G NTN operations. The model can be trained to predict the static parts offline, whereas the dynamic parts must be predicted in real time.
The identification and detection processes are synchronized. An inherently interpretable scheme that detects and interprets anomalous protocols simultaneously, namely, a network that directly identifies anomalous protocol sequences, is designed. Thus, the necessary conditions for real-time prevention can be achieved.
On the basis of these principles, the original protocol signal information is transformed into images and fed into the model, providing a rich context for tracing the input back to the anomalous data points. The identification method is structured as a two-layer architecture composed of a prediction layer and a detection layer; this method efficiently processes the input protocol data. In the detection layer, traditional in Section 7.1 calculations are replaced with XOR operations, enabling simultaneous identification and detection of anomalous protocol sequences. In the process of actively identifying anomalous data points, an XAI mechanism is employed to provide inherently interpretable baseline detection results, ensuring that the protocol data and original information can be tracked throughout the entire mapping process. This approach concurrently obtains the detection results and the corresponding anomalous protocol data, facilitating effective anomaly identification. In the following sections, we leverage the explainable framework to design a self-evolving method for classifying uncovered protocol attacks and develop an active approach for identifying anomalous protocol data, as shown in Figure 8.
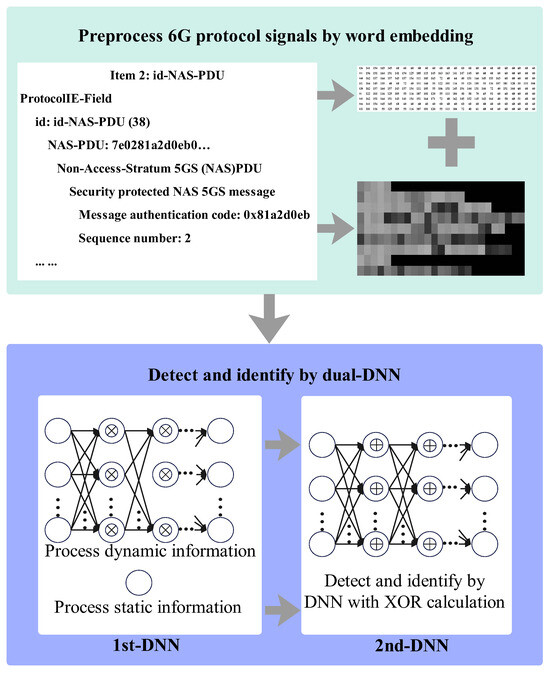
Figure 8.
Self-evolving classification method.
6.1. Preprocessing on the Basis of Coding
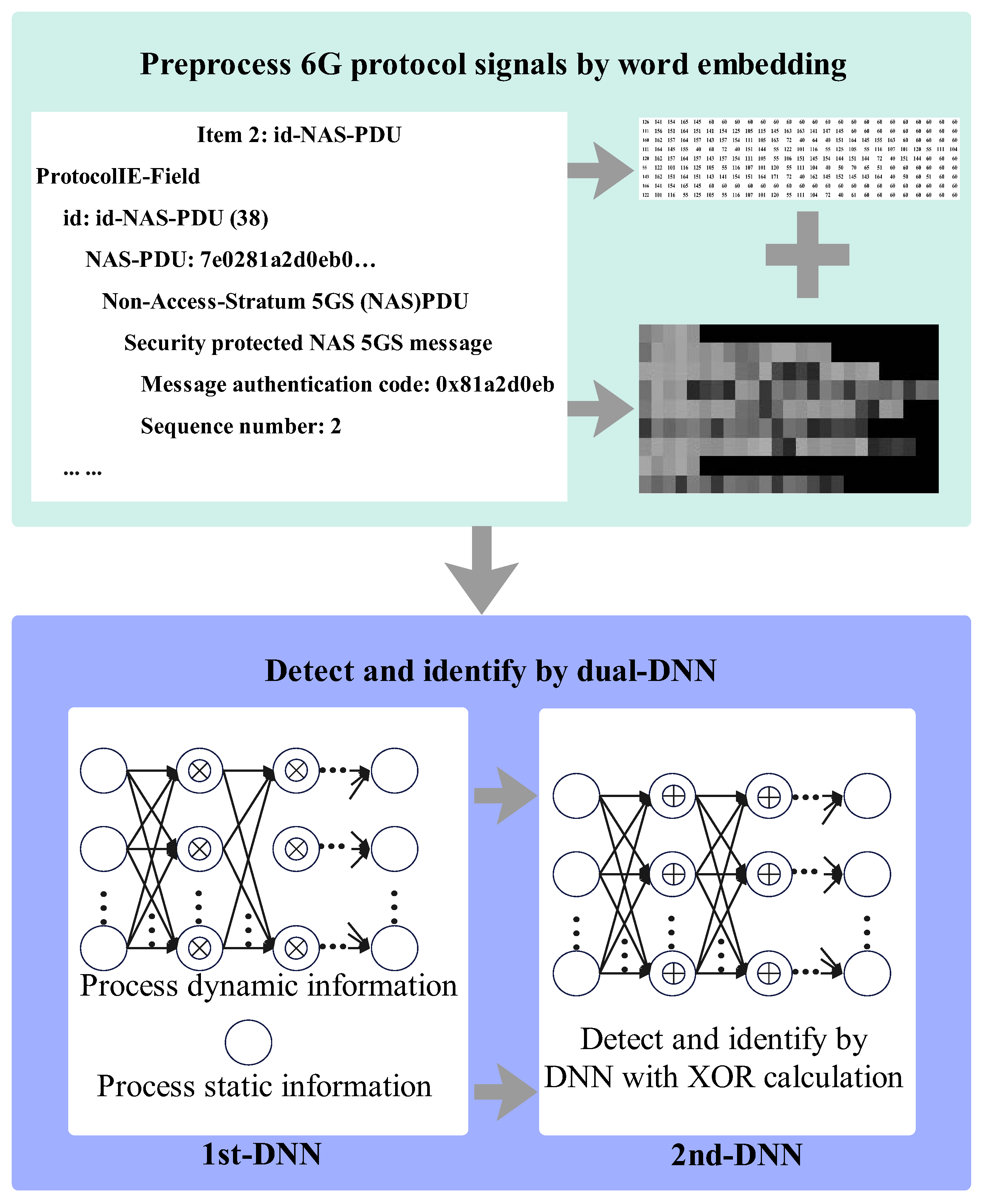
Anomalies are embedded within 6G NTN protocol sequences instead of traffic features in attacks such as hijacking UE capability and sequence number desynchronization. Thus, the protocol sequences, not the traffic features, must serve as the inputs to detect and identify anomalies. However, the original protocol sequences contain unstructured descriptions, which are unsuitable for direct input into DL models.
To solve this problem, we need to convert 6G protocol sequences into images, which need to fulfill two demands: one is that a DL model can process it, and the other is to retain enough information to reverse back to protocol data. A single 6G protocol message consists of many sequences that include semantic English words, phrases, and special symbols as non-numeric components, along with numeric components. To preserve all this information, we utilize the one-hot encoding or ASCII encoding method to transform each message into a matrix. Each row of the matrix represents a sequence, and each column corresponds to a character in that sequence. For the non-numeric components, we first apply a regular expression tokenization algorithm to separate them, then use either one-hot encoding or ASCII encoding methods; for the numeric parts, we directly apply one-hot encoding or ASCII encoding methods. This encoding process converts both non-numeric and numeric components into unique binary vectors. Next, we combine the numeric and non-numeric vectors, group them in 8-bit segments, and pad the final group with zeros if it contains fewer than 8 bits. We then convert the grouped sub-vectors from binary to decimal, ensuring that the values fall within the range of [0, 255]. These can be represented via a grayscale image and then input into the DL model for anomaly detection. The grayscale image mapping serves as an intuitive example (e.g., mapping temporal signaling features to pixel intensity), but it can be replaced with graph embedding or other forms without affecting the core contribution.
The preprocessing method preserves the integrity of the protocol sequence information and ensures the reversibility of the mapping process. In addition, the images can be processed by the detection model. Therefore, the essential condition for identifying anomalous protocol sequences via XAI mechanisms is fulfilled.
6.2. Intrinsic Identification via a Dual-DNN Approach
With images serving as inputs, sufficient information is provided to trace the inputs back to the anomalous 6G NTN protocol sequences. However, the tracing method still needs to be designed, which can be achieved through the intrinsic explainable baseline detection process. This approach should simultaneously identify anomalous protocol sequences and provide explainable detection results. Additionally, the intrinsic explainable detection method must efficiently process the inputs, which contain information about the 6G NTN protocol that is richer than the abstracted information, such as statistical data or envelopes.
Therefore, we design a dual-DNN model to detect anomalies in 6G NTN protocol sequences efficiently. The proposed dual-DNN consists of two DNN models: the first DNN model is the prediction model, and the second model is the detection model.
The first model predicts the corresponding normal data for the data under detection. Among them, static fields can be obtained during training. Firstly, training the historical protocol data can acquire static information, which remains consistent across different terminals and network infrastructures. Secondly, the static data vary between various terminals and network infrastructures but remain unchanged within the same UE, and the infrastructure is obtained by training protocol data collected from the corresponding terminals and networks in the 6G network under detection. These static fields can be accomplished during training. But the dynamic fields varying across different communication protocol processes and even sequences still need to be predicted based on the information of the protocol data under detection. This prediction is completed during the online inference process.
To reduce computational complexity, the dual-DNN model predicts only the dynamic information of protocol sequences, whereas static information is directly obtained from the trained model. The dynamic baseline information predicted by the 1st DNN is then input into the 2nd DNN, at which point the information is combined with the static prediction results to generate a comprehensive representation of the normal baseline information.
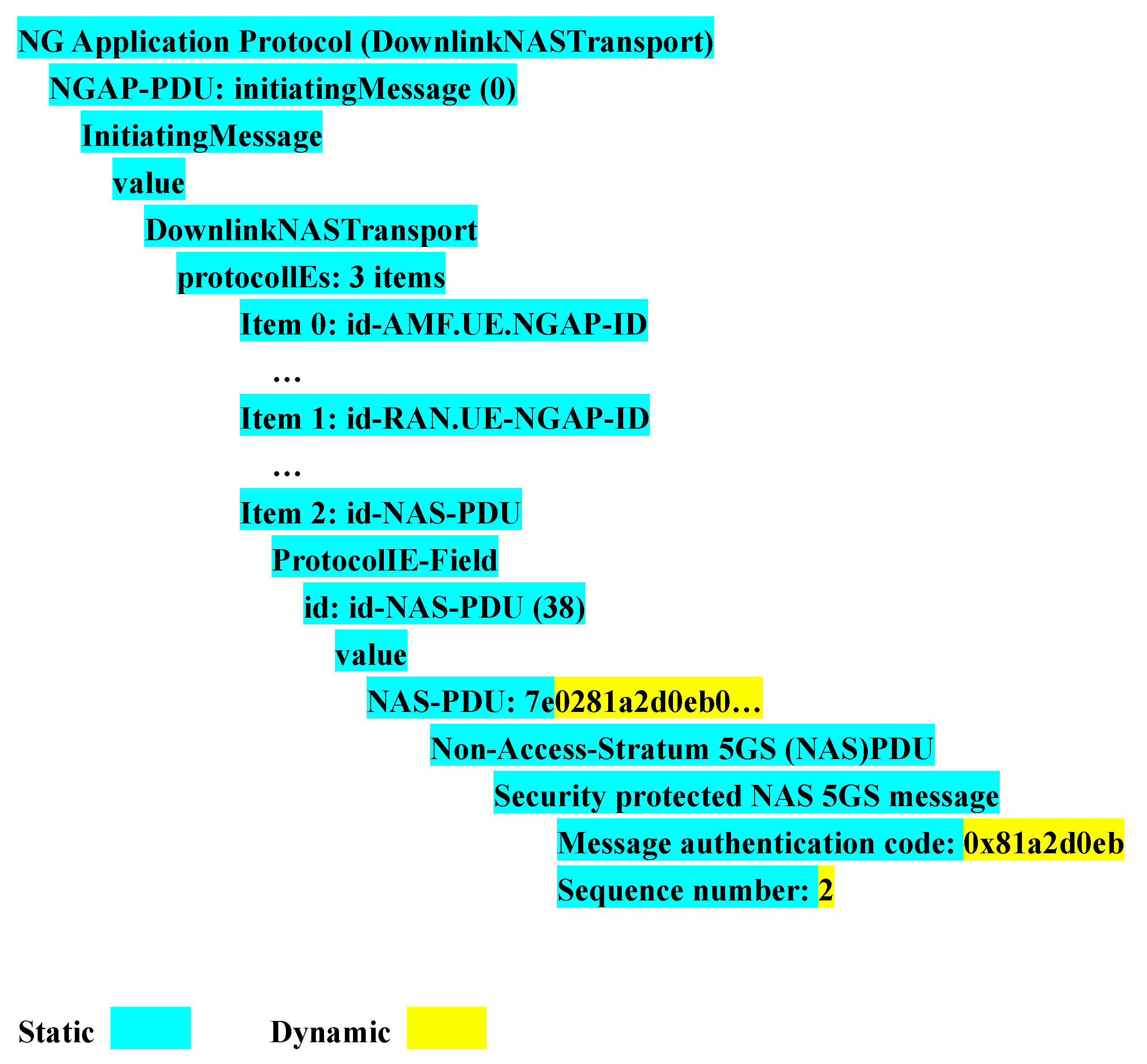
For the 6G NTN protocol sequences, more than 95% of the fields are static. For example, in the NG application protocol (downlink NASTransport) signal sequence used during the registration process, as shown in Figure 9, only the information about the encryption algorithm identifier, integrity protection algorithm identifier, message authentication code, and sequence number is dynamic. Thus, the dual-DNN model can process the protocol signals efficiently.
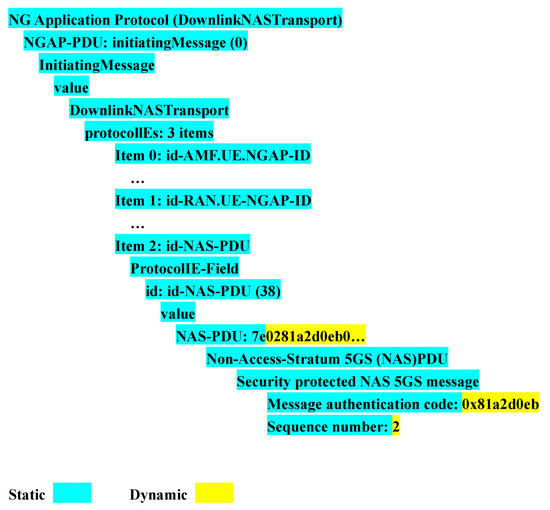
Figure 9.
Static and dynamic fields of one 5G protocol sequence.
In the second DNN model, convolutional computations are replaced with XOR operations. By comparing the predicted normal sequence with the sequence under detection, mismatched portions are identified as anomalous fields. If there is no attack, the detection matrix will be zero. Otherwise, there will be elements in the detection matrix that are one, corresponding to the anomalous signal fields. Lastly, the anomalous signal fields can be obtained by reversing the matrix to derive the protocol information. This approach not only detects anomalies but also localizes the exact positions of the anomalous fields. To identify the anomalous protocol fields, they are usually local, such as tampering with the sequence number, which is a specific protocol field. Therefore, the interpretable ability can be local or global, but it is necessary to target those anomalous protocol fields specifically. The proposed dual-DNN model is globally interpretable because the detection matrix includes the anomalous or normal state of all the protocol data.
To design the dual-DNN model, there is one base DNN model consisting of the input, output, and hidden layers, and the number of hidden layers is denoted by L. The activation function is Sigmoid.
The first DNN model uses the base DNN model directly. The input of the first DNN model is the data matrix mapping for the protocol data; each matrix corresponds to one protocol message, with dimensions equal to the number of lines in the protocol message and the ASCII-coded maximal line length of the sequences included by this message. The number of neurons in the hidden layer must be no less than the total number of elements contained in the input data matrix. The output of the first DNN model is the predicted normal matrix, which has the same dimensions as the input.
The second DNN model is designed to replace the convolution calculation with the XOR of the base DNN model. The model focuses on all the image sections instead of the image margins. The input for this second DNN model consists of the data matrix that requires detection and the corresponding predicted data matrix. Furthermore, the number of neurons in the hidden layer must be at least equal to the total number of elements in the input data matrix. For any layer l, is the output vector, which is also the input to the th layer. The XOR operation is performed between the weights of the neurons in the th layer. Further, the activation function denoted by f follows this operation to obtain , which is given by
where denotes the weight.
After performing the XOR calculation between the predicted data matrix and the data matrix to be detected, we obtain the detection result matrix. On the basis of the output of the 2nd DNN, a label is assigned to each grayscale value, with 0 and 1 indicating normal and anomalous points, respectively. Anomalies are highlighted in red. Because the grayscale-to-signal transformation is reversible, anomalous signal points can be precisely located.
With the former design, the intrinsic identify is achieved. The process is summarized below. The identification model begins with inputting an ASIC-encoded grayscale image, which is a matrix consisting of elements that are either zero or one. Then, the identification model continues to process, detect, and identify. One layer of the DNN predicts the expected value when the system is not under attack. In the second layer of the DNN, the predicted matrix and the input matrix undergo an XOR operation to output the detection matrix. If there is no attack, the detection matrix will be zero. Otherwise, there will be elements in the detection matrix that are one, corresponding to the anomalous signal fields. Lastly, the anomalous signal fields can be obtained by reversing the matrix to derive the protocol information.
7. Simulation Results
The efficiency of the proposed XAI-based detection framework for 6G NTN drones is validated from two aspects: the self-evolving classification of uncovered attacks and the online identification of anomalous protocol sequences.
The protocol data for simulation include the data for the UPF DoS case proposed in Section 3 and the open-source dataset CICIDS2017, as described in Table 3.

Table 3.
Simulation data.
The attack protocol data in the attack cases described in Section 3 are collected, which will be used to validate the designed methods. Thus, an experimental platform is established on one x86 computer with a simulated UE, a simulated RAN, and a 5G CN running on two virtual machines. One virtual machine hosts the simulated UE and RAN via UERANSIM, whereas the other is used to run the 5G CN using Open5GS software v2.6.4. We assume that the gNB is intruded and that the attacker delivers the MitM relay tool to the intruded gNB. The air interface between the MitM relay and the gNB is omitted. Then, the UPF DoS attack, protocol sequence tampering, and a normal case are implemented on the simulation platform. During the implementation of the three threat cases, the protocol data of the Ng interface are collected to verify the effectiveness of the proposed methods. The parameters are provided in Table 4, where , , and represent the numbers of normal users, attacker users, CNs and BSs, respectively. To ensure that the input data are balanced, the undersampling method randomly selects an equal number of data samples from each case. More than 3,000,000 labeled flows are collected from the Ng interface via Wireshark, consisting of normal traffic data (806,205), UPF DoS data (1,595,999), hijack UE capacity data (6404), and sequence number desynchronization data (4384). With these data, the proposed methods are validated in Section 7.1 and Section 7.2.

Table 4.
Attack case parameters.
This article evaluates the self-evolving classification and the online identification methods with the basic metrics, including the accuracy (denoted ), precision (denoted ), recall (denoted ), and F1 score (denoted ), which are formulated as
where the numbers of true positives, false positives, true negatives, and false negatives are denoted , , , and , respectively.
7.1. Self-Evolving Classification
To evaluate the effectiveness of the self-evolving classification method for uncovered attacks (SECs) with the proposed XAI detection framework, CNN–BiLSTM-based [35] and Hoeffding Anytime Tree (HATT)-based [43] detection methods are used for comparison. The CNN–BiLSTM method is configured according to Table 5, and the HATT method is set as described in [43].

Table 5.
Configuration of models.
The performance of the proposed SEC method is validated with the basic detection metrics defined in Equation (9). Further, the classification performance of uncovered attacks is also assessed, where the basic metrics of classification and detection are equal for rule detection methods. For example, the accuracy of classification equals the accuracy of detection for rule detection methods. Besides, to evaluate the abstraction of fingerprint features related to uncovered protocol attacks, the contributions of these features are represented by the waterfall figure of the SHAP method. To assess the adjustable capability, the attention of the features of the rule detection model is also provided. Comparing the attention figures before and after the adjustment, it can be seen that the rule detection model has enhanced the fingerprint features of uncovered protocol attacks after the adjustment.
First, the detection performance of the SEC, CNN–BiLSTM, and HATT methods, namely, the average detection performance for uncovered attacks, is given in Table 6. For the detection of UPF DoS attacks, the precision, recall, and F1 score are used to evaluate performance. Here, the accuracy is omitted since the accuracy is equal to the precision if only uncovered attacks are considered. The CNN–BiLSTM model exhibits high precision (100%) and low recall (50.2%) for UPF DoS attacks, indicating that many of these uncovered attacks are missed, leading to many missed detections. The HATT model has low precision (75.3%) and high recall (78.2%) for UPF DoS attacks. In contrast, the proposed SEC method achieves high precision (100%) and recall rates (93.8%) for UPF DoS attacks. These findings indicate that the SEC method can accurately detect almost all uncovered attacks while maintaining a low false positive rate. This balance results in an F1 score of 96.6%, which is 44.6% and 25.7% higher than those of the CNN–BiLSTM and HATT methods on average, respectively. The detection performance metrics of the SEC method are better than those of the CNN–BiLSTM and HATT methods because the SEC method utilizes the fingerprint features of the uncovered attacks extracted from the detection process. Thus, the SEC model can detect and classify uncovered attacks efficiently.

Table 6.
Detection performance for uncovered attacks with “↑” meaning increase.
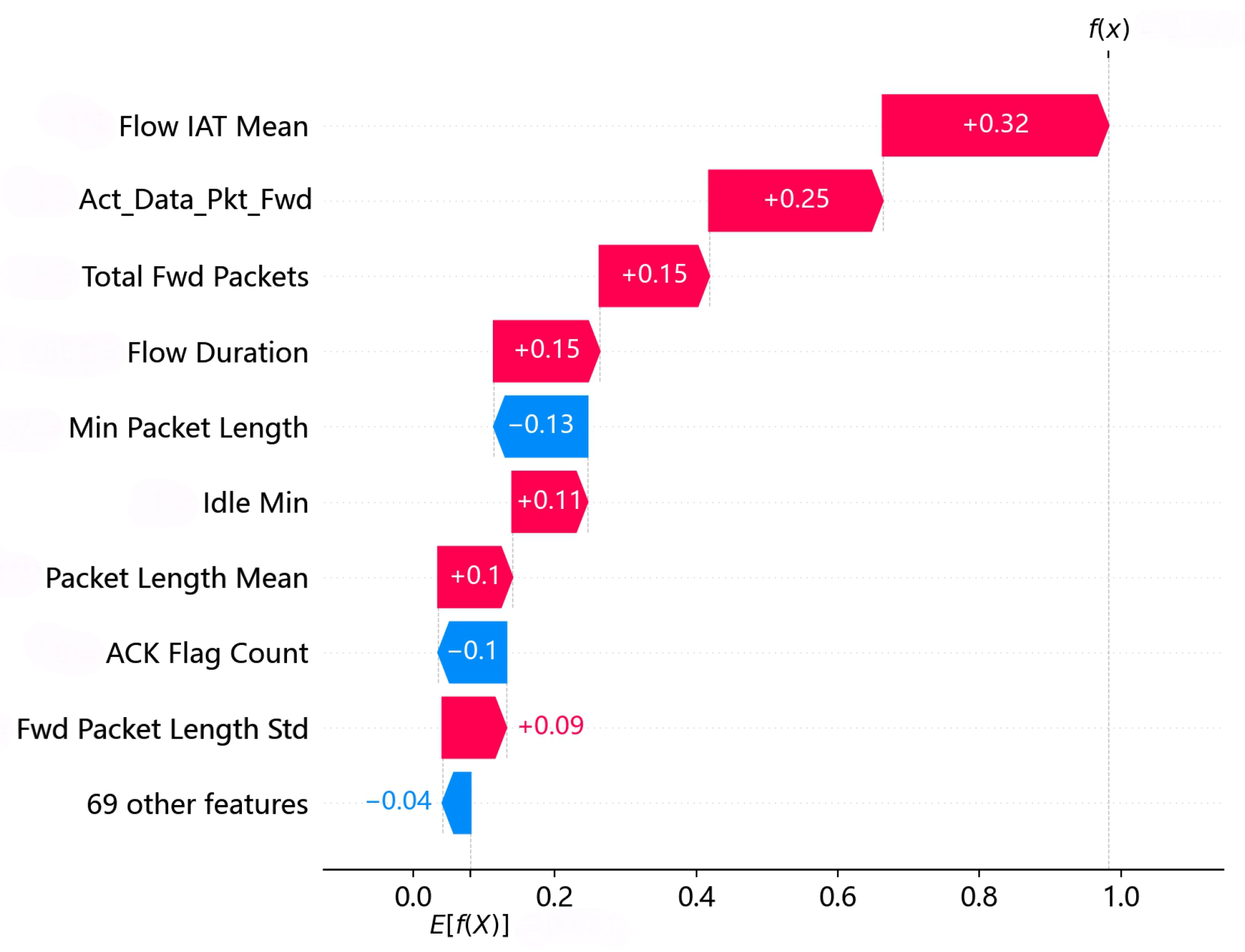
Next, we evaluate the performance of the proposed SEC in extracting the fingerprint features. After the baseline model detects the uncovered protocol attacks, the XAI mechanism used in the baseline detection model is used to capture the fingerprint features of these attacks. Figure 10 illustrates the quantitative contributions of the protocol features for the detected UPF DoS attacks across our dataset when the system is under UPF DoS. The red and blue bars represent the positive and negative contributions to the detection results. The protocol features with positive and negative contributions to the detection results are defined as the positive and negative fingerprint features, respectively. In the case of the UPF DoS attack, the positive fingerprint features are numbered 2, 3, 8, 17, 42, 69, and 78 [68], which are Flow Duration, Total Fwd Packets, Fwd Packet Length Mean, Flow IAT Mean, Packet Length Std, Act Data Pkt Fwd, and Idle Min. The negative fingerprint features are numbered 39 and 48 [68], which are Min Packet Length and ACK Flag Count, with reduced attention to negative fingerprint features during the rule detection process, as described in the following subsection.
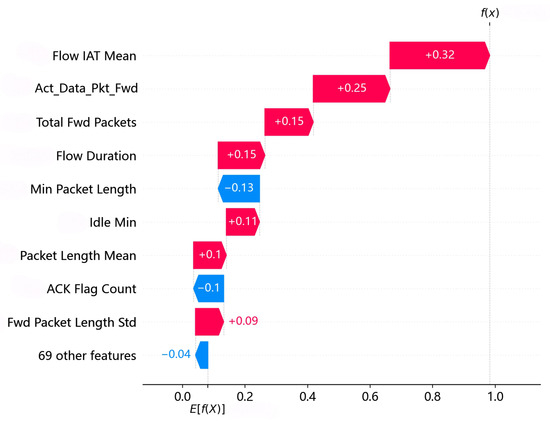
Figure 10.
Quantitative contributions of different features to UPF DoS attacks.
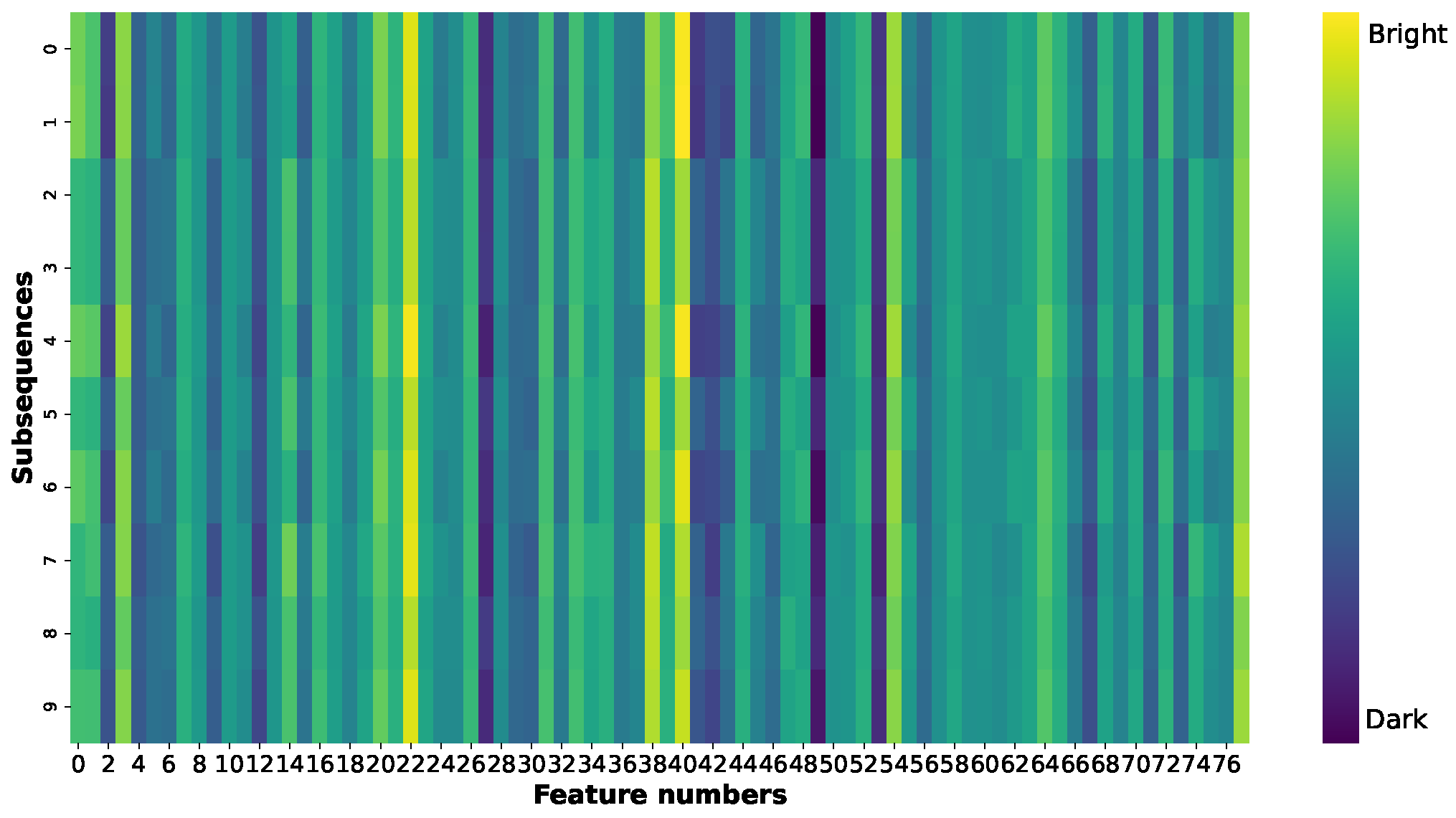
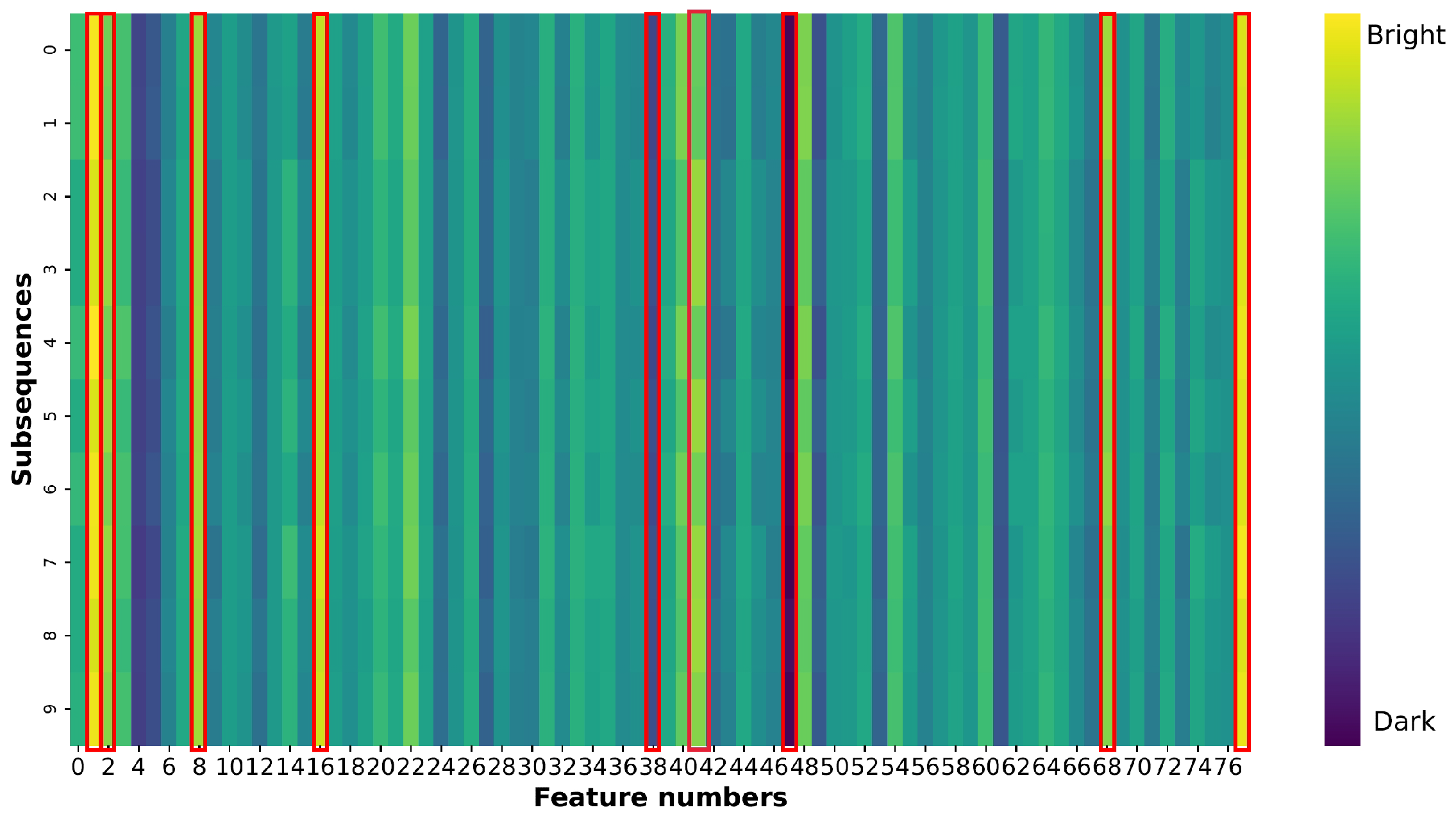
To assess the effectiveness of the self-evolving features in the rule detection method, we compared the attention maps before and after the self-evolving method based on the fingerprint characteristics was applied, as shown in Figure 11 and Figure 12. The color intensity in these figures indicates the degree of attention: brighter colors represent greater attention and thus more significant influence on the prediction results, whereas darker colors signify less attention and thus less contribution to the prediction results. Based on these feature contributions revealed by Figure 10, we have adjusted our feature attention strategy by shifting focus from Figure 11 to Figure 12, increasing attention to positively contributing features while decreasing focus on negative contributors. Figure 11 shows the attention map for covered DoS attacks before the self-evolving method is applied. The rule detection model focuses the most on features numbered 4, 23, 39, 41, 55, and 78 [68], which are Total Backward Packets, Fwd IAT Std, Min Packet Length, Packet Length Mean, AvgBwdSegmentSize, and IdleMin, as highlighted by the brighter colors in the plots. After the self-evolving method is applied to classify UPF DoS attacks, the attention given to features numbered 39 and 48 [68]—which are Min Packet Length and ACK Flag Count—is reduced, as indicated by the darker colors, and the attention given to features numbered 2, 3, 8, 17, 42, 69, and 78 [68]—which are Flow Duration, Total Fwd Packets, Fwd Packet Length Mean, Flow IAT Mean, Packet Length Std, Act Data Pkt Fwd, and Idle Min,—is increased, as highlighted by the brighter colors, as shown in Figure 12. Thus, the rule detection method can dynamically reassign more attention to features with higher positive contributions and reduce the attention given to features with negative contributions. This enhances its effectiveness in detecting and classifying uncovered anomalies.
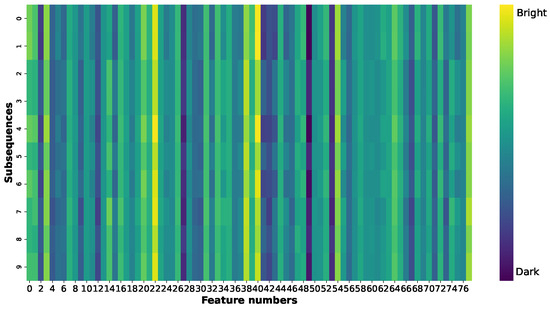
Figure 11.
Attention map for a DoS attack.
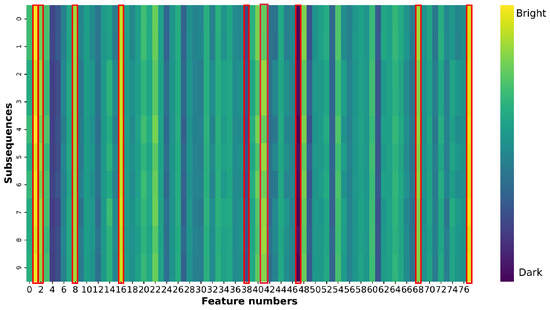
Figure 12.
Attention map for a UPF DoS attack.
7.2. Online Identification
The performance of the proposed online identification method is assessed by the basic metrics defined in Equation (9). Further, the identification results are displayed for the two proposed protocol tamper attack cases: the tampered capacity of N1 mode 3GPP access and the tampered sequence number.
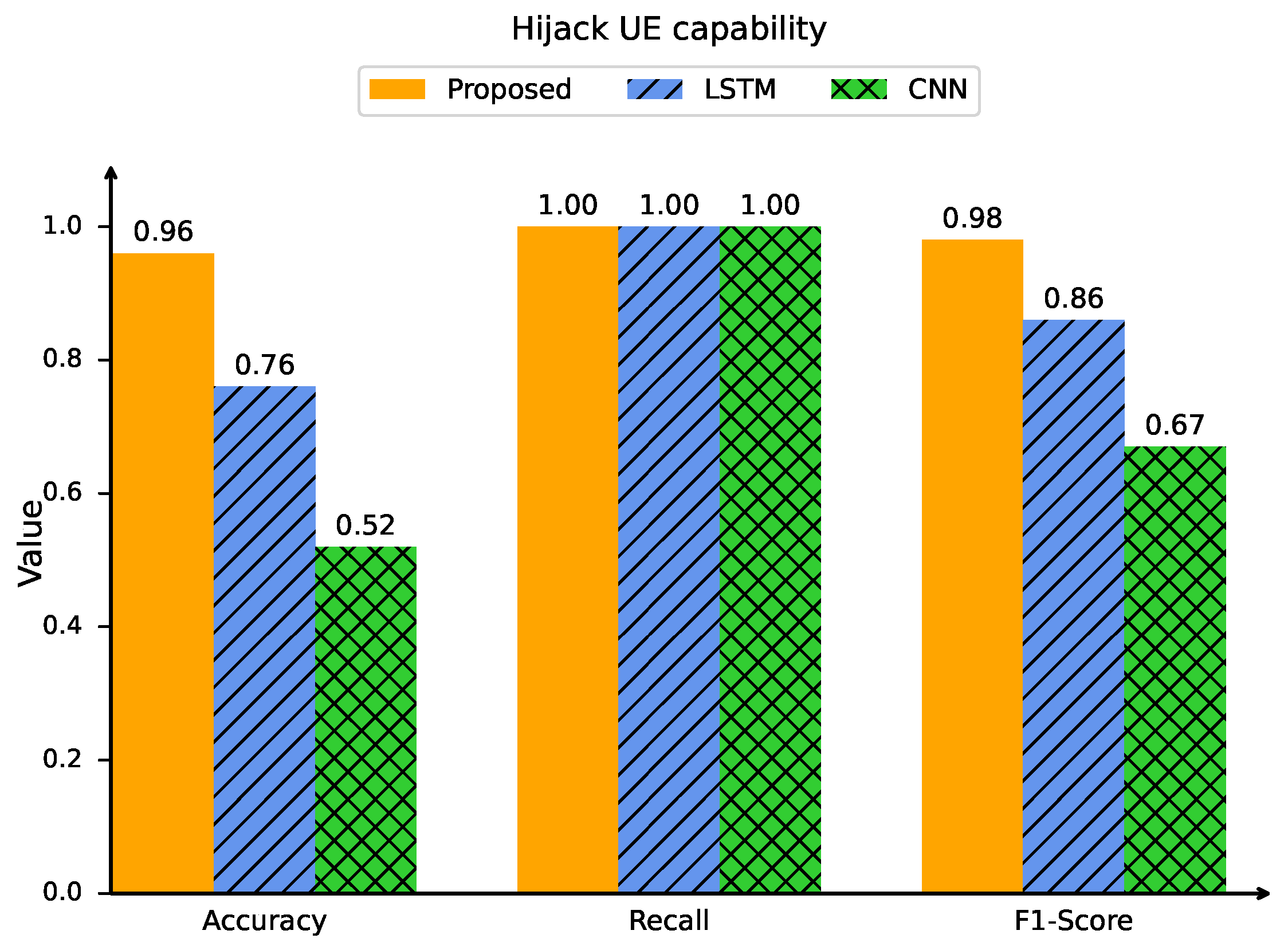
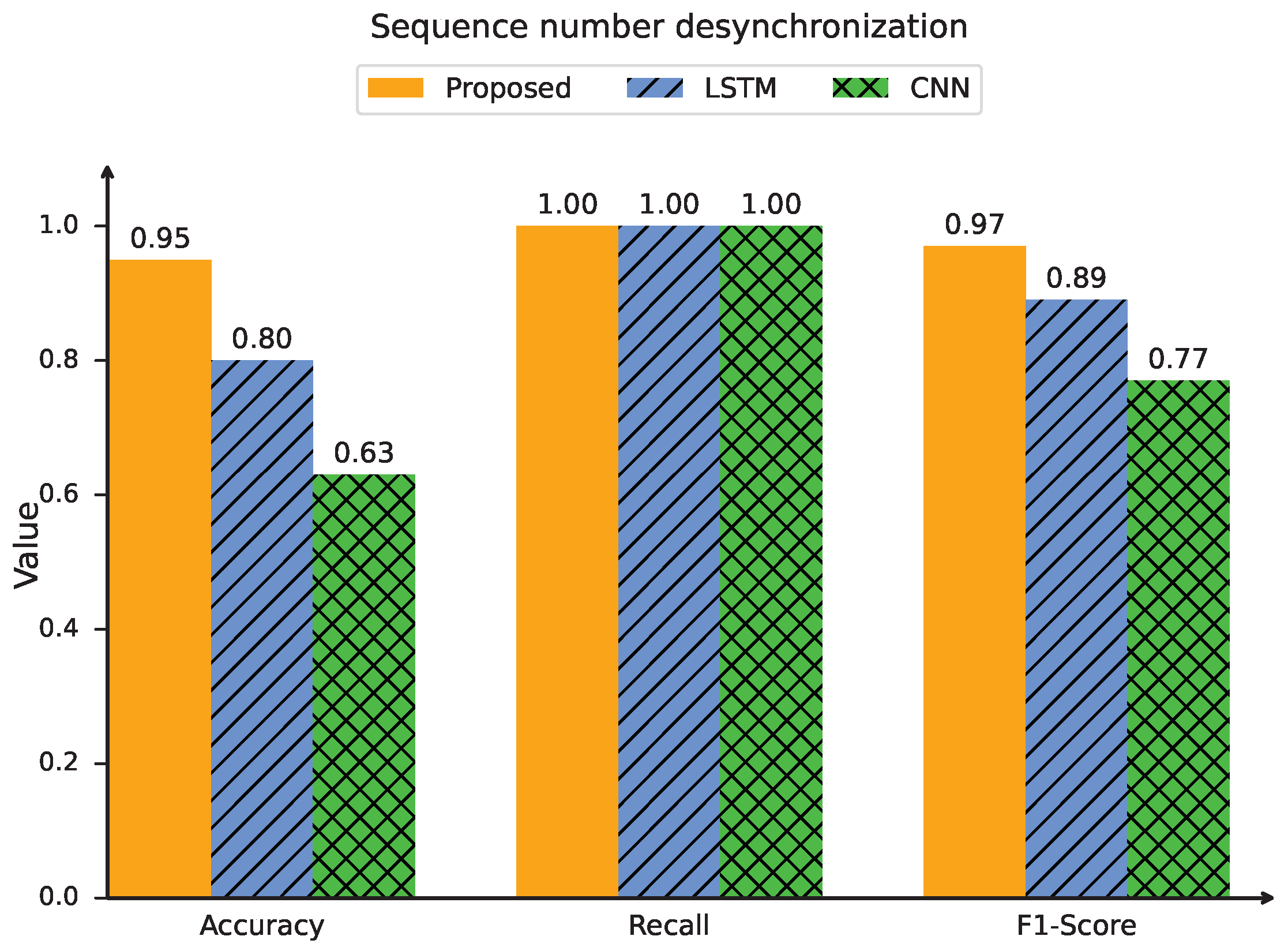
The first aspect is the detection performance, which is evaluated using three key metrics: the precision, recall, and F1 score. Figure 13 shows the detection performance in the hijacking UE capability and sequence number desynchronization attacks. The detection performance of the proposed intrinsic identification method is compared with that of the CNN and LSTM methods. In the hijacking UE capability case, the accuracy, recall, and F1 score of the proposed intrinsic scheme reach 96%, 1, and 98%, respectively. Compared with those of the CNN [38] and LSTM [33] methods, the precision is improved by 84% and 26%, respectively; the F1 score is increased by 46% and 14%, respectively; and the recall remains constant. The trends for the sequence number desynchronization case are similar to those for the hijacking UE capability case, where the proposed intrinsic scheme outperforms both the CNN and LSTM methods.
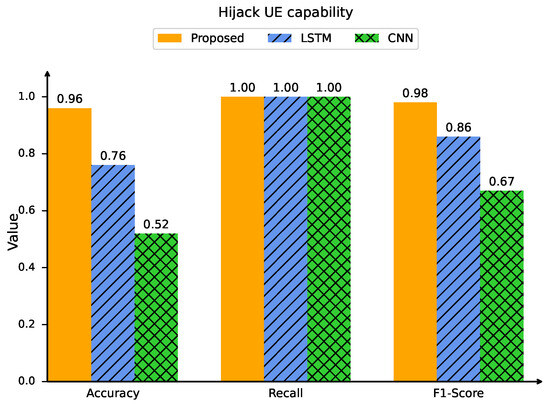
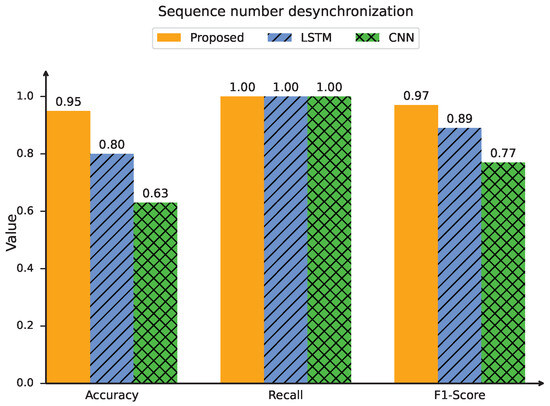
Figure 13.
Detection performance of online identification method.
The second aspect is the identification performance, as shown in Figure 14 and Figure 15. The detection matrix is calculated using the bitwise XOR of the attack-free reference matrix (predicted by the identification model) and the test input matrix. Nonzero elements (logical ‘1’) in the resulting matrix indicate anomalous signal fields, which are then mapped back to their original signal domains through matrix inversion. The anomalous sections of the images are clearly highlighted in the two attack cases, hijacking the UE capability and sequence number desynchronization. This proves that the proposed detection scheme provides intrinsic explanations, and the corresponding detection and identification results are presented in the figures. The highlighted sections can be converted into protocol signal sequences. Thus, the anomalous signal sequences can be identified.
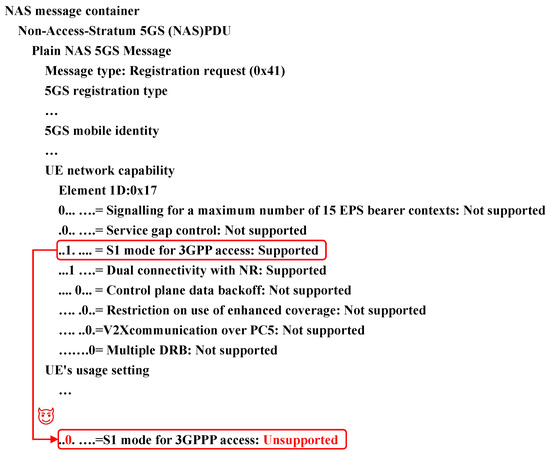
Figure 14.
Identification of hijacking UE capability attacks.
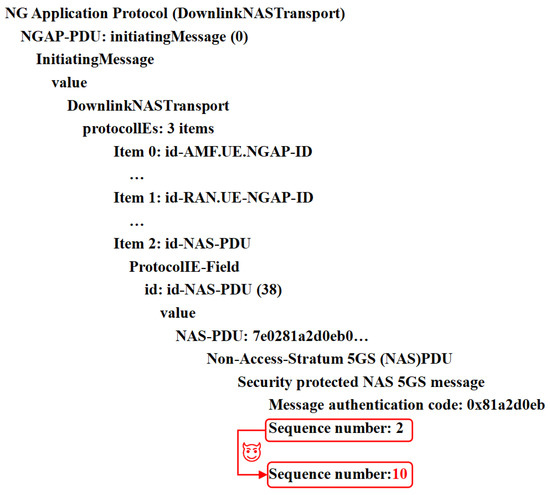
Figure 15.
Identification of sequence number desynchronization attacks.
8. Conclusions
Given the serious security threats to drones using 6G NTN protocols, it is important to detect, classify, and identify protocol attacks. However, classifying uncovered protocol attacks and identifying anomalous protocol data remain challenging. To address these issues, this paper presents an interpretable anomaly classification and identification method for 6G NTN protocols. We design an interpretable anomaly detection framework that introduces XAI techniques and can be used in conjunction with existing detection methods, thereby ensuring both interpretability and cooperation with other approaches. Using this framework, we develop a self-evolving classification method to identify uncovered protocol attacks. The rule detection process and baseline detection results are made transparent through XAI technologies; this information is used synergistically to extract and learn from the fingerprint features of uncovered protocol attacks, and these features are used in the classification process. Additionally, an online identification method is designed within the proposed framework to capture and output anomalous protocol data during the detection process on the basis of an intrinsic interpretable model. The simulation results show that the proposed classification and identification methods can effectively classify uncovered protocol attacks and identify anomalous protocol sequences. Compared with existing methods, the precision of the self-evolving classification method is improved by a maximum of 32.8%, and that of the online identification method for anomalous protocol sequences is increased by at least 26%.
Author Contributions
Conceptualization, Q.S. and J.Z.; methodology, Q.S. and L.D.; software, L.D. and Y.H.; validation, L.D. and Y.H.; formal analysis, Q.S. and J.Z.; investigation, L.D. and Y.H.; resources, L.T. and J.Z.; data curation, Y.H.; writing—original draft preparation, Q.S.; writing—review and editing, J.Z. and Q.S.; visualization, L.D. and Y.H.; supervision, J.Z. and L.T.; project administration, L.T.; funding acquisition, L.T. and J.Z. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the Beijing Natural Science Foundation (No. L222004) and the National Natural Science Foundation of China (No. 62371039).
Data Availability Statement
Restrictions apply to the availability of these data. Data were obtained from Canadian Institute for Cybersecurity (CIC) and are available at https://www.unb.ca/cic/datasets/ids-2017.html with the permission of CIC.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Ning, H.; Sun, Q.; Zeng, J.; Tian, L.; Wang, Y.; Zhou, Y. Mixed Numerology-Based Intelligent Resource Management in a Sliced 6G Space-Terrestrial Integrated Radio Access Network. IEEE Trans. Mob. Comput. 2024, 24, 1338–1356. [Google Scholar]
- Mozaffari, M.; Taleb Zadeh Kasgari, A.; Saad, W.; Bennis, M.; Debbah, M. Beyond 5G with UAVs: Foundations of a 3D Wireless Cellular Network. IEEE Trans. Wirel. Commun. 2019, 18, 357–372. [Google Scholar] [CrossRef]
- Amponis, G.; Lagkas, T.; Zevgara, M.; Katsikas, G.; Xirofotos, T.; Moscholios, I.; Sarigiannidis, P. Drones in B5G/6G Networks as Flying Base Stations. Drones 2022, 6, 39. [Google Scholar] [CrossRef]
- Fan, X.; Wu, P.; Xia, M. Air-to-Ground Communications Beyond 5G: UAV Swarm Formation Control and Tracking. IEEE Trans. Wirel. Commun. 2024, 23, 8029–8043. [Google Scholar] [CrossRef]
- Guo, H.; Li, J.; Liu, J.; Tian, N.; Kato, N. A Survey on Space-Air-Ground-Sea Integrated Network Security in 6G. IEEE Commun. Surv. Tutor. 2021, 24, 53–87. [Google Scholar] [CrossRef]
- Khan, M.A.; Kumar, N.; Mohsan, S.A.H.; Khan, W.U.; Nasralla, M.M.; Alsharif, M.H.; Żywiołek, J.; Ullah, I. Swarm of UAVs for Network Management in 6G: A Technical Review. IEEE Trans. Netw. Serv. Manag. 2023, 20, 741–761. [Google Scholar] [CrossRef]
- 3GPP TR 38.811. Study on New Radio (NR) to Support Non-Terrestrial Networks (Release 15) V0.2.1. 2017. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3234 (accessed on 21 November 2017).
- 3GPP TR 38.821. Solutions for NR to Support Non-Terrestrial Networks (NTN) (Release 16) V1.0.0. 2019. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3525 (accessed on 2 December 2019).
- 3GPP TS 38.101. User Equipment (UE) Radio Transmission and Reception (Release 15) V1.0.0. 2017. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3283 (accessed on 15 December 2017).
- 3GPP TR 38.882. Study on Requirements and Use Cases for Network Verified UE Location for Non-Terrestrial-Networks (NTN) in NR (Release 18) V18.0.0. 2022. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=4074 (accessed on 27 June 2022).
- Mu, J.; Zhang, R.; Cui, Y.; Gao, N.; Jing, X. UAV Meets Integrated Sensing and Communication: Challenges and Future Directions. IEEE Commun. Mag. 2023, 61, 62–67. [Google Scholar] [CrossRef]
- 3GPPTS 23.501. System Architecture for the 5G System (5GS) (Release 15) V15.0.0. 2017. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3144 (accessed on 22 November 2017).
- Bouzid, T.; Chaib, N.; Bensaad, M.L.; Oubbati, O.S. 5G Network Slicing with Unmanned Aerial Vehicles: Taxonomy, Survey, and Future Directions. Trans. Emerg. Telecommun. Technol. 2023, 34, e4721. [Google Scholar] [CrossRef]
- Tomaszewski, L.; KoÅakowski, R. Advanced Air Mobility and Evolution of Mobile Networks. Drones 2023, 7, 556. [Google Scholar] [CrossRef]
- Nguyen, C.T.; Saputra, Y.M.; Van Huynh, N.; Nguyen, T.N.; Hoang, D.T.; Nguyen, D.N.; Pham, V.Q.; Voznak, M.; Chatzinotas, S.; Tran, D.H. Emerging Technologies for 6G Non-Terrestrial-Networks: From Academia to Industrial Applications. IEEE Open J. Commun. Soc. 2024, 5, 3852–3885. [Google Scholar] [CrossRef]
- Aygul, M.A.; Turkmen, H.; Cirpan, H.A.; Arslan, H. Machine Learning-Driven Integration of Terrestrial and Non-Terrestrial Networks for Enhanced 6G Connectivity. Comput. Netw. 2024, 255, 110875. [Google Scholar] [CrossRef]
- Jamshed, M.A.; Kaushik, A.; Manzoor, S.; Shakir, M.Z.; Seong, J.; Toka, M.; Shin, W.; Schellmann, M. A Tutorial on Non-Terrestrial Networks: Towards Global and Ubiquitous 6G Connectivity. Found. Trends Netw. 2025, 14, 160–253. [Google Scholar] [CrossRef]
- Salim, S.; Moustafa, N.; Reisslein, M. Cybersecurity of Satellite Communications Systems: A Comprehensive Survey of the Space, Ground, and Links Segments. IEEE Commun. Surv. Tutor. 2024, 27, 372–425. [Google Scholar] [CrossRef]
- Diro, A.; Kaisar, S.; Vasilakos, A.V.; Anwar, A.; Nasirian, A.; Olani, G. Anomaly Detection for Space Information Networks: A Survey of Challenges, Techniques, and Future Directions. Comput. Secur. 2024, 139, 103705. [Google Scholar] [CrossRef]
- Hussain, S.R.; Echeverria, M.; Karim, I.; Chowdhury, O.; Bertino, E. 5Greasoner: A Property-Directed Security and Privacy Analysis Framework for 5G Cellular Network Protocol. In Proceedings of the ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 669–684. [Google Scholar]
- Dang, T.; Sun, Q.; Lu, D.; Tian, L.; Zeng, J. DR-LSTM Detection Scheme for 5G DDoS Traffic. In Proceedings of the IEEE Global Communications Conference, Cape Town, South Africa, 8–12 December 2024; pp. 1–6. [Google Scholar]
- Wang, Z.; Chen, H.; Yang, S.; Luo, X.; Li, D.; Wang, J. A Lightweight Intrusion Detection Method for IoT Based on Deep Learning and Dynamic Quantization. Peerj Comput. Sci. 2023, 9, e1569. [Google Scholar] [CrossRef]
- Tian, J.; Wang, B.; Guo, R.; Wang, Z.; Cao, K.; Wang, X. Adversarial Attacks and Defenses for Deep-Learning-Based Unmanned Aerial Vehicles. IEEE Internet Things J. 2022, 9, 22399–22409. [Google Scholar] [CrossRef]
- Huang, M.; Mi, W.; Wang, Y. EDGS-YOLOv8: An Improved YOLOv8 Lightweight UAV Detection Model. Drones 2024, 8, 337. [Google Scholar] [CrossRef]
- Ihekoronye, V.U.; Ajakwe, S.O.; Kim, D.; Lee, J.M. Hierarchical Intrusion Detection System for Secured Military Drone Network: A Perspicacious Approach. In Proceedings of the IEEE Military Communications Conference (MILCOM), Rockville, MD, USA, 28 November–2 December 2022; pp. 336–341. [Google Scholar]
- Abro, G.E.M.; Zulkifli, S.A.B.M.; Masood, R.J.; Asirvadam, V.S.; Laouiti, A. Comprehensive Review of UAV Detection, Security, and Communication Advancements to Prevent Threats. Drones 2022, 6, 284. [Google Scholar] [CrossRef]
- Ahn, H.; Chung, S. Deep Learning-Based Anomaly Detection for Individual Drone Vehicles Performing Swarm Missions. Expert Syst. Appl. 2024, 244, 122869. [Google Scholar] [CrossRef]
- Fu, R.; Ren, X.; Li, Y.; Wu, Y.; Sun, H.; Al-Absi, M.A. Machine-Learning-Based UAV-Assisted Agricultural Information Security Architecture and Intrusion Detection. IEEE Internet Things J. 2023, 10, 18589–18598. [Google Scholar] [CrossRef]
- Ntizikira, E.; Lei, W.; Alblehai, F.; Saleem, K.; Lodhi, M.A. Secure and Privacy-Preserving Intrusion Detection and Prevention in the Internet of Unmanned Aerial Vehicles. Sensors 2023, 23, 8077. [Google Scholar] [CrossRef]
- Hadi, H.J.; Cao, Y.; Li, S.; Xu, L.; Hu, Y.; Li, M. Real-Time Fusion Multi-Tier DNN-Based Collaborative IDPS with Complementary Features for Secure UAV-Enabled 6G Networks. Expert Syst. Appl. 2024, 252, 124215. [Google Scholar] [CrossRef]
- Chriki, A.; Touati, H.; Snoussi, H.; Kamoun, F. UAV-Based Surveillance System: An Anomaly Detection Approach. In Proceedings of the IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar]
- Sun, L.; Liang, J.; Zhang, C.; Wu, D.; Zhang, Y. Meta-Transfer Metric Learning for Time Series Classification in 6G-Supported Intelligent Transportation Systems. IEEE Trans. Intell. Transp. Syst. 2024, 25, 2757–2767. [Google Scholar] [CrossRef]
- Hoang, T.M.; Nguyen, N.M.; Duong, T.Q. Detection of Eavesdropping Attack in UAV-Aided Wireless Systems: Unsupervised Learning with One-Class SVM and K-Means Clustering. IEEE Wirel. Commun. Lett. 2019, 9, 139–142. [Google Scholar] [CrossRef]
- Tlili, F.; Ayed, S.; Fourati, L.C. Exhaustive Distributed Intrusion Detection System for UAVs Attacks Detection and Security Enforcement (E-DIDS). Comput. Secur. 2024, 142, 103878. [Google Scholar] [CrossRef]
- Ashraf, S.N.; Manickam, S.; Zia, S.S.; Abro, A.A.; Obaidat, M.; Uddin, M.; Abdelhaq, M.; Alsaqour, R. IoT Empowered Smart Cybersecurity Framework for Intrusion Detection in Internet of Drones. Sci. Rep. 2023, 13, 18422. [Google Scholar] [CrossRef]
- Slimani, C.; Morge-Rollet, L.; Lemarchand, L.; Espes, D.; Le Roy, F.; Boukhobza, J. A Study on Characterizing Energy, Latency and Security for Intrusion Detection Systems on Heterogeneous Embedded Platforms. Future Gener. Comput. Syst. 2025, 162, 107473. [Google Scholar] [CrossRef]
- Gamal, M.; Elhamahmy, M.; Taha, S.; Elmahdy, H. Improving Intrusion Detection Using LSTM-RNN to Protect Drones’ Networks. Egypt. Inform. J. 2024, 27, 100501. [Google Scholar] [CrossRef]
- Alzahrani, A. Novel Approach for Intrusion Detection Attacks on Small Drones Using ConvLSTM Model. IEEE Access 2024, 12, 149238–149253. [Google Scholar] [CrossRef]
- Xu, C.; Shen, J.; Du, X. A Method of Few-Shot Network Intrusion Detection Based on Meta-Learning Framework. IEEE Trans. Inf. Forensics Secur. 2020, 15, 3540–3552. [Google Scholar] [CrossRef]
- Mohammad, M.A.; Kolahkaj, M. Detecting Network Anomalies Using the Rain Optimization Algorithm and Hoeffding Tree-Based Autoencoder. In Proceedings of the International Conference on Web Research, Tehran, Iran, 24–25 April 2024; pp. 137–141. [Google Scholar]
- De AraÃjo Josephik, J.G.A.; Siqueira, Y.; Machado, K.G.; Terada, R.; dos Santos, A.L.; Nogueira, M.; Batista, D.M. Applying Hoeffding Tree Algorithms for Effective Stream Learning in IoT DDoS Detection. In Proceedings of the IEEE Latin-American Conference on Communications, Panama City, PA, USA, 15–17 November 2023; pp. 1–6. [Google Scholar]
- Cengiz, K.; Lipsa, S.; Dash, R.K.; IvkoviÄ, N.; Konecki, M. A Novel Intrusion Detection System Based on Artificial Neural Network and Genetic Algorithm with a New Dimensionality Reduction Technique for UAV Communication. IEEE Access 2024, 12, 4925–4937. [Google Scholar] [CrossRef]
- Weinberg, A.I.; Last, M. Enhat-Synergy of a Tree-Based Ensemble with Hoeffding Adaptive Tree for Dynamic Data Streams Mining. Inf. Fusion 2023, 89, 397–404. [Google Scholar] [CrossRef]
- Khichane, A.; Fajjari, I.; Aitsaadi, N.; Gueroui, M. 5GC-Observer: A Non-Intrusive Observability Framework for Cloud Native 5G System. In Proceedings of the IEEE Network Operations and Management Symposium, Miami, FL, USA, 8–12 May 2023; pp. 1–10. [Google Scholar]
- Pacherkar, H.S.; Yan, G. PROV5GC: Hardening 5G Core Network Security with Attack Detection and Attribution Based on Provenance Graphs. In Proceedings of the ACM Conference on Security and Privacy in Wireless and Mobile Networks, Seoul, Republic of Korea, 27–30 May 2024; pp. 254–264. [Google Scholar]
- Alharbi, A.; Petrunin, I.; Panagiotakopoulos, D. Assuring Safe and Efficient Operation of UAV Using Explainable Machine Learning. Drones 2023, 7, 327. [Google Scholar] [CrossRef]
- Wazid, M.; Singh, J.; Pandey, C.; Sherratt, R.S.; Das, A.K.; Giri, D.; Park, Y. Explainable Deep Learning-Enabled Malware Attack Detection for IoT-Enabled Intelligent Transportation Systems. In Proceedings of the IEEE Transactions on Intelligent Transportation Systems, Gold Coast, QLD, Australia, 18–21 November 2025; p. 3525505. [Google Scholar]
- Hickling, T.; Aouf, N.; Spencer, P. Robust Adversarial Attacks Detection Based on Explainable Deep Reinforcement Learning for UAV Guidance and Planning. IEEE Trans. Intell. Veh. 2023, 8, 4381–4394. [Google Scholar] [CrossRef]
- Zhang, Z.; Liu, Q.; Wu, C.; Zhou, S.; Yan, Z. A Novel Adversarial Detection Method for UAV Vision Systems via Attribution Maps. Drones 2023, 7, 697. [Google Scholar] [CrossRef]
- Li, D.; Zhu, Y.; Chen, M.; Wang, J. Minipatch: Undermining DNN-Based Website Fingerprinting with Adversarial Patches. IEEE Trans. Inf. Forensics Secur. 2022, 17, 2437–2451. [Google Scholar] [CrossRef]
- Wei, F.; Li, H.; Zhao, Z.; Hu, H. XNIDS: Explaining Deep Learning-Based Network Intrusion Detection Systems for Active Intrusion Responses. In Proceedings of the USENIX Security, Anaheim, CA, USA, 9–11 August 2023; pp. 1–18. [Google Scholar]
- Khan, S.; Liew, C.F.; Yairi, T.; McWilliam, R. Unsupervised Anomaly Detection in Unmanned Aerial Vehicles. Appl. Soft Comput. 2019, 83, 105650. [Google Scholar] [CrossRef]
- Tcydenova, E.; Kim, T.W.; Lee, C.; Park, J.H. Detection of Adversarial Attacks in AI-Based Intrusion Detection Systems Using Explainable AI. Hum.-Centered Comput. Inf. Sci. 2021, 11, 1–14. [Google Scholar]
- Zhu, X.; Zhang, Y.; Zhang, Z.; Guo, D.; Li, Q.; Li, Z. Interpretability Evaluation of Botnet Detection Model Based on Graph Neural Network. In Proceedings of the IEEE International Conference on Computer Communications, New York, NY, USA, 2–5 May 2022; pp. 1–6. [Google Scholar]
- Barnard, P.; Marchetti, N.; DaSilva, L.A. Robust Network Intrusion Detection Through Explainable Artificial Intelligence (XAI). IEEE Netw. Lett. 2022, 4, 167–171. [Google Scholar] [CrossRef]
- Wigard, J.; Juan, E.; Stanczak, J.; Lauridsen, M.; Marcone, A.; Hoppe, S.; Ahmadzadeh, A.; Masri, A.; Tran, D.H. Ubiquitous 6G Service Through Non-Terrestrial Networks. IEEE Wirel. Commun. 2023, 30, 12–18. [Google Scholar] [CrossRef]
- Meshram, A.K.; Kumar, S.; Querol, J.; Andrenacci, S.; Chatzinotas, S. Reduced Complexity Initial Synchronization for 5G NR Multibeam LEO-Based Non-Terrestrial Networks. IEEE Open J. Commun. Soc. 2025, 6, 1528–1551. [Google Scholar] [CrossRef]
- 3GPP TR 38.821, Solutions for NR to Support Non-Terrestrial Networks (NTN), V16.2.0. 2023. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3525 (accessed on 3 April 2023).
- 3GPP TS 38.211, Physical Channels and Modulation V17.7.0. 2024. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3213 (accessed on 29 March 2024).
- 3GPP TS 38.331, Radio Resource Control (RRC) Protocol Specification, V18.1.0. 2024. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3197 (accessed on 1 April 2024).
- 3GPP TS 38.213, Physical Layer Procedures for Control V17.9.0. 2024. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3215 (accessed on 29 March 2024).
- 3GPP TS 38.212, Multiplexing and Channel Coding V17.8.0. 2024. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3214 (accessed on 29 March 2024).
- 3GPP TS 38.321, Medium Access Control (MAC) Protocol Specification V17.8.0. 2024. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3194 (accessed on 4 April 2024).
- Cyberattack Brings Down Vodafone Portugal Mobile Voice and TV Services. Available online: https://therecord.media/cyberattack-brings-down-vodafone-portugal-mobile-voice-and-tv-services (accessed on 7 July 2022).
- 3GPP TR 33.809. Study on 5G Security Enhancement Against False Base Stations (FBS) (Release 18) V1.0.0. 2023. Available online: https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3539 (accessed on 6 June 2023).
- Shaik, A.; Borgaonkar, R.; Park, S. New Vulnerabilities in 4G and 5G Cellular Access Network Protocols: Exposing Device Capabilities. In Proceedings of the Security and Privacy, San Francisco, CA, USA, 20–22 May 2019; pp. 221–231. [Google Scholar]
- Hussain, S.R.; Echeverria, M.; Karim, I.; Chowdhury, O.; Bertino, E. 5GReasoner: A Property-Directed Security and Privacy Analysis Framework for 5G Cellular Network Protocol. In Proceedings of the ACM Special Interest Group on Security, Audit and Control Conference, London, UK, 11–15 November 2019; pp. 1–8. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. A Detailed Analysis of the CICIDS2017 Data Set. In Information Systems Security and Privacy: 4th International Conference, ICISSP 2018, Funchal-Madeira, Portugal, 22–24 January 2018, Revised Selected Papers 4; Springer International Publishing: Berlin/Heidelberg, Germany, 2019; pp. 1–12. [Google Scholar]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).