AI Makes Crypto Evolve
Abstract
:1. Introduction
1.1. Goals and Objectives
- What stages should cryptography go through in order to adopt AI?
- What does AI add to the capabilities of cryptosystems in each of the identified stages?
- Which existing trends in the AI realm will affect the future of AIIC?
- What effects will AI trends have on the future of AIIC?
1.2. Achievements
- 1.
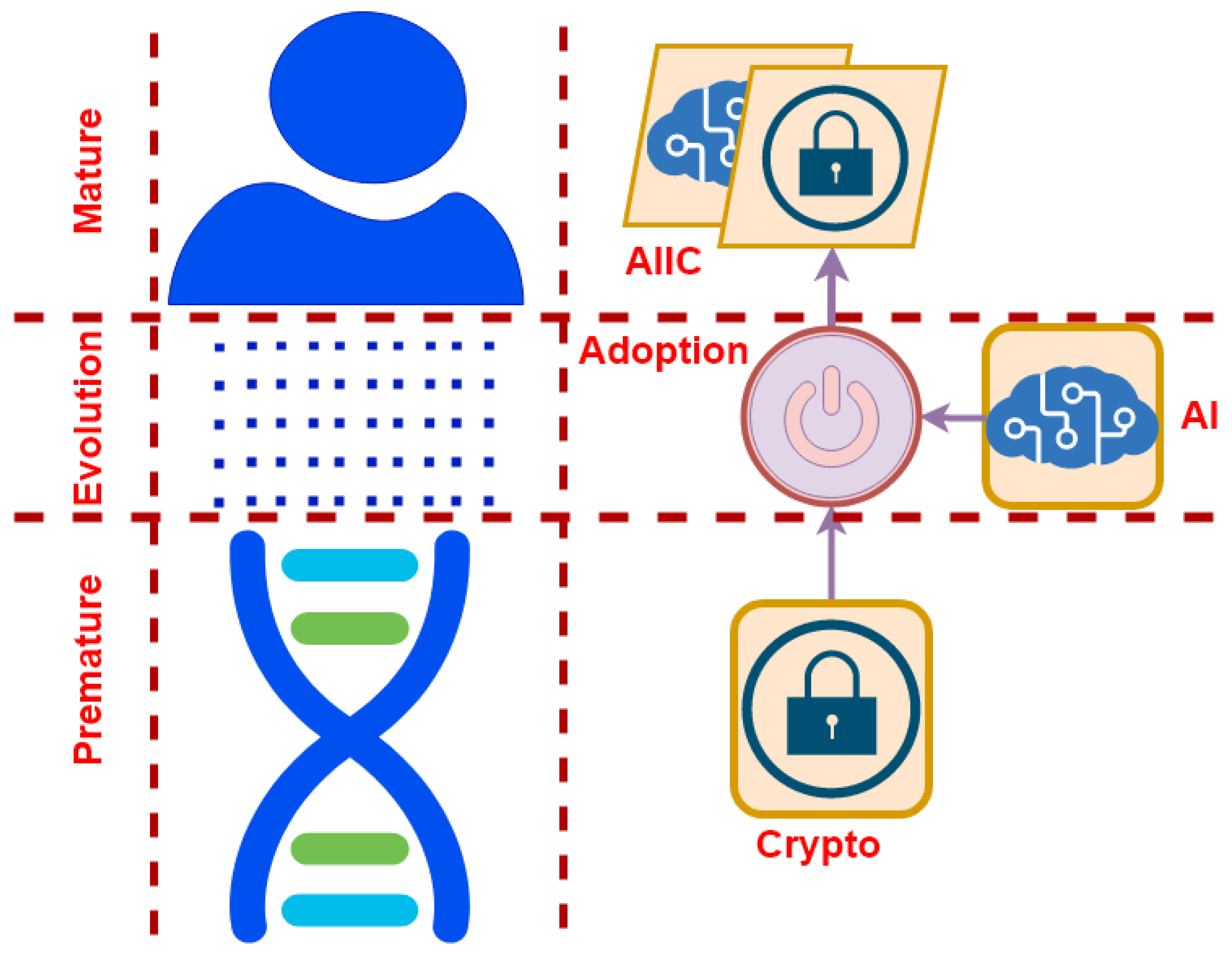
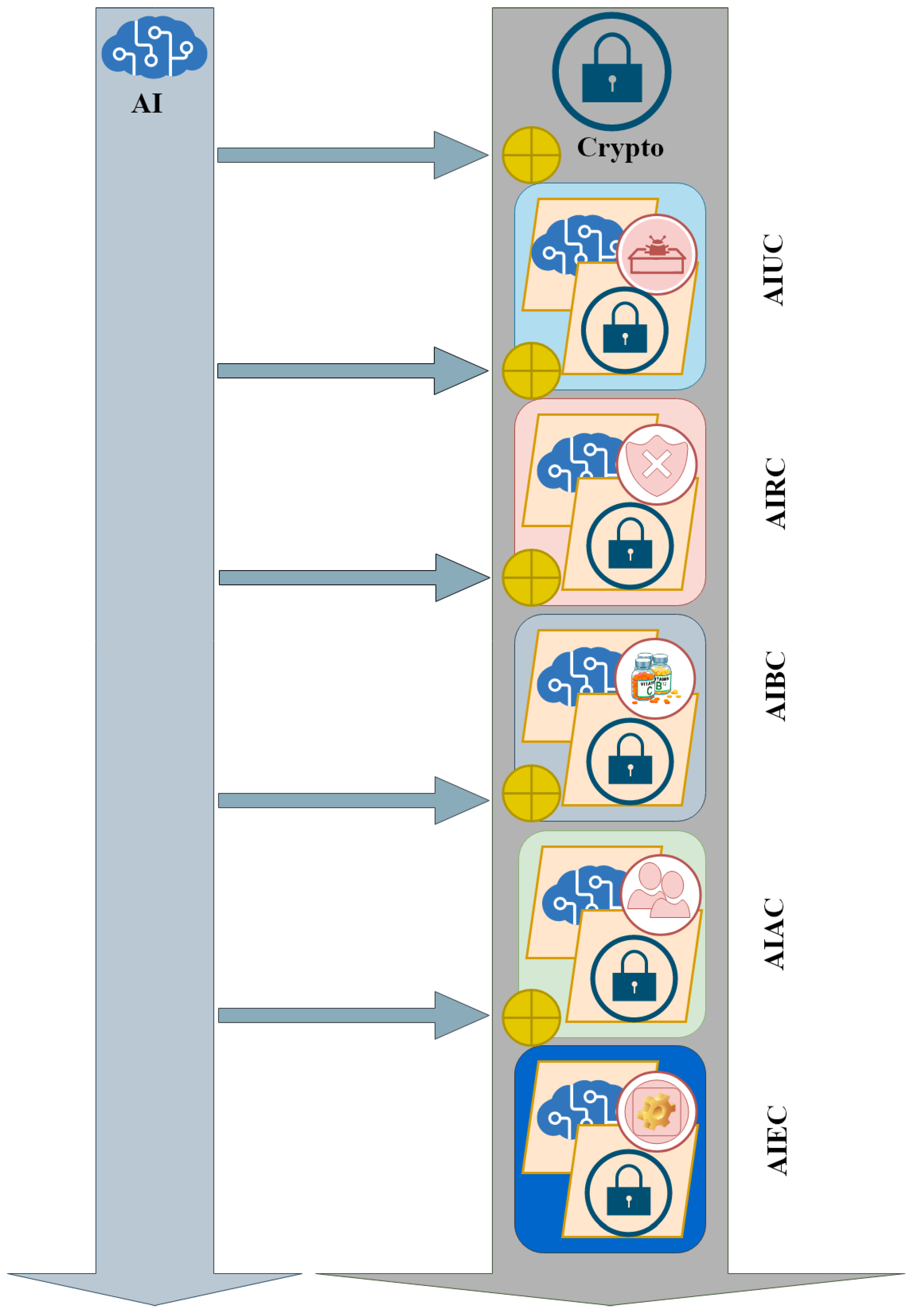
- We recognized and defined the following five stages in the evolutionary path of AIIC.
- AI-Unaware Cryptography (AIUC) (Section 3): At this stage, cryptography is vulnerable to Machine Learning (ML) and Deep Learning (DL) attacks. It can be targeted by AI-based attacks without any specialized defensive measure or mechanism.
- AI-Resilient Cryptography (AIRC) (Section 4): This is the second evolutionary stage, wherein cryptosystems adopt caution towards ML and DL attacks. In this stage, cryptographic methods and devices are designed to be as resilient as possible against AI-based attacks.
- AI-Boosted Cryptography (AIBC) (Section 5): In the third stage, cryptographic techniques, protocols, methods, devices, etc., are supported by AI models in two possible ways. First, they might be improved with the help of AI in terms of different design objectives not including security. These objectives may include performance, efficiency, etc. Second, they might be assisted by AI for use in security-related scenarios not including cryptography. These scenarios include authentication, privacy, information hiding, etc.
- AI-Assisted Cryptography (AIAC) (Section 6): In this stage, as well as the next one, AI is utilized by one or more of the internal components of the cryptosystem, and directly for cryptographic purposes. What differentiates these two stages is the component where AI is used. A cryptosystem often consists of an encryption/decryption component along with some extra components, which perform cryptographic mechanisms such as hashing, random number generation, etc. In the AIAC stage, AI is used by the components running cryptographic mechanisms.
- AI-Embedded Cryptography (AIEC) (Section 7): In the last stage, AI is used by the encryption/decryption component.
The above stages are shown in Figure 2 along with the icon we used for each of them in the rest of this paper.In Table 1, the first entry in each row contains one of the evolutionary stages demonstrated in Figure 2. The second entry contains “Yes” if cryptographic modules and systems in the related stage are aware of and resilient against Ml and DL attacks. The third entry indicates whether or not cryptosystems in the related stage are improved via the use of AI in terms of objectives not related to security. The fourth entry shows the existence or lack of support from AI for cryptographic mechanisms in security-related scenarios. A “Yes” in the fifth entry shows that the stage mentioned in the first entry makes use of AI in some internal cryptographic components, but not exactly in the encryption/decryption module. The sixth entry indicates whether or not the related stage utilizes AI models exactly in the design and implementation of the encryption/decryption component. - 2.
- We reviewed current trends in research on AI such as bio-inspired and quantum-inspired AI, and attempted to anticipate the influence of these trends in terms of what the future may hold for AIIC. We developed a future roadmap for further research in this area (Section 8).
1.3. Organization
2. Existing Surveys
2.1. Surveys on AI in Security
2.2. Surveys on AI in Cryptography (AIIC)
2.3. Summary
2.4. Motivations
- Covering all aspects of AI;
- Focusing specifically on cryptography among all security aspects and controls;
- Establishing an evolutionary path for the studied area;
- Developing a future roadmap;
- Discussing the role of quantum computing in the future of the studied area.
3. AIUC
3.1. Encryption Detection
3.2. Attack and Cryptanalysis
3.3. AI-Unaware PUF
3.3.1. ML Attacks
3.3.2. DL Attacks
3.3.3. Hybrid Attacks
4. AIRC
PUFs Resilient against ML Attacks
5. AIB
5.1. Improved Design Objectives
5.1.1. Performance
5.1.2. Reliability
5.1.3. Signal Quality and Noise Resistance
5.2. Security-Related Scenarios
5.2.1. Authentication
5.2.2. Privacy
5.2.3. Trust
5.2.4. Information Hiding
5.2.5. Visual Cryptography
6. AIAC
6.1. AI-Assisted Key Management
6.2. Neural Hashing
6.3. AI-Assisted Random Number Generation
Design
6.4. Attack, Test and Cryptanalysis
6.4.1. Test and Analysis
6.4.2. Cryptanalysis
6.4.3. Attack
6.5. AI-Assisted Cryptographic Arithmetic Module
6.6. AI-Assisted Substitution Boxes
6.7. AI-Assisted PUF
7. AIEC
7.1. Neural Cryptography
Security of Neural Cryptography
7.2. Homomorphic Neural Cryptography
8. Future Roadmap: The Promise of Secure AI
8.1. Quantum-Inspired AI
8.2. (Quantum-AI)-Supported Cryptography
9. Conclusions and Further Works
- Investigating challenges and applications of AIIC;
- Developing a taxonomy, an ecosystem or a life cycle for AIIC;
- Studying the impact of bio computing on the future of AIIC given its impact on current trends in AI as well as cryptography;
- Providing a look-ahead at the future of Crypto-Influenced AI (CIAI) with a focus on the role of bio computing;
- Anticipating the role of information theory in future AI, and consequently on the future of both AIIC and CIAI;
- Investigating the coevolution of AI and blockchain.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Yu, M.; Yao, H.; Qin, C.; Zhang, X. A Comprehensive Analysis Method for Reversible Data Hiding in Stream-Cipher-Encrypted Images. IEEE Trans. Circuits Syst. Video Technol. Early Access Artic. 2022, 1. [Google Scholar] [CrossRef]
- Teranishi, K.; Sadamoto, T.; Chakrabortty, A.; Kogiso, K. Designing Optimal Key Lengths and Control Laws for Encrypted Control Systems based on Sample Identifying Complexity and Deciphering Time. IEEE Trans. Autom. Control. Early Access Artic. 2022, 1. [Google Scholar] [CrossRef]
- Vo, V.; Yuan, X.; Sun, S.; Liu, J.K.; Nepal, S.; Wang, C. ShieldDB: An Encrypted Document Database with Padding Countermeasures. IEEE Trans. Knowl. Data Eng. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Parida, P.; Pradhan, C.; Gao, X.Z.; Roy, D.S.; Barik, R.K. Image Encryption and Authentication With Elliptic Curve Cryptography and Multidimensional Chaotic Maps. IEEE Access 2021, 9, 76191–76204. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Khalil, A.; Hasbullah, I.H. Security and Privacy Schemes in Vehicular Ad-Hoc Network With Identity-Based Cryptography Approach: A Survey. IEEE Access 2021, 9, 121522–121531. [Google Scholar] [CrossRef]
- Xiong, L.; Han, X.; Yang, C.N.; Shi, Y.Q. Robust Reversible Watermarking in Encrypted Image with Secure Multi-party based on Lightweight Cryptography. IEEE Trans. Circuits Syst. Video Technol. Early Access Artic. 2021, 32, 75–91. [Google Scholar] [CrossRef]
- Li, F.; Liu, K.; Zhang, L.; Huang, S.; Wu, Q. EHRChain: A Blockchain-based EHR System Using Attribute-Based and Homomorphic Cryptosystem. IEEE Trans. Serv. Comput. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Chen, D.; Wang, H.; Zhang, N.; Nie, X.; Dai, H.N.; Zhang, K.; Choo, K.R. Privacy-Preserving Encrypted Traffic Inspection with Symmetric Cryptographic Techniques in IoT. IEEE Internet Things J. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Zhou, Y.; Hu, Z.; Li, F. Searchable Public-Key Encryption with Cryptographic Reverse Firewalls for Cloud Storage. IEEE Trans. Cloud Comput. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Koshiba, T. Chaotic Image Encryption: State-of-the-Art, Ecosystem, and Future Roadmap. Appl. Syst. Innov. 2022, 5, 57. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Bibak, K.; Koshiba, T. The Odyssey of Entropy: Cryptography. Entropy 2022, 24, 266. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Singh, V.; Rai, B.K.; Bibak, K.; Koshiba, T. Cryptography in Hierarchical Coded Caching: System Model and Cost Analysis. Entropy 2021, 23, 1459. [Google Scholar] [CrossRef]
- Bibak, K.; Ritchie, R.; Zolfaghari, B. Everlasting security of quantum key distribution with 1K-DWCDM and quadratic hash. Quantum Inf. Comput. 2021, 21, 181–202. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Bibak, K.; Nemati, H.R.; Koshiba, T.; Mitra, P. Statistical Trend Analysis on Physically Unclonable Functions: An Approach via Text Mining; CRC Press: Boca Raton, FL, USA, 2021. [Google Scholar]
- Sun, Y.; Lo, F.P.W.; Lo, B. Light-weight Internet-of-Things Device Authentication, Encryption and Key Distribution using End-to-End Neural Cryptosystems. IEEE Internet Things J. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Ding, Y.; Tan, F.; Qin, Z.; Cao, M.; Choo, K.K.R.; Qin, Z. DeepKeyGen: A Deep Learning-Based Stream Cipher Generator for Medical Image Encryption and Decryption. IEEE Trans. Neural Netw. Learn. Syst. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Dai, S. Quantum Cryptanalysis on a Multivariate Cryptosystem Based on Clipped Hopfield Neural Network. IEEE Trans. Neural Netw. Learn. Syst. Early Access Artic. 2021, 1–5. [Google Scholar] [CrossRef]
- Olaniyan, R.; Maheswaran, M. A Fast Edge-Based Synchronizer for Tasks in Real-Time Artificial Intelligence Applications. IEEE Internet Things J. Early Access Artic. 2021, 9, 3825–3837. [Google Scholar] [CrossRef]
- Wen, S.; Rios, A.; Ge, Y.; Itti, L. Beneficial Perturbation Network for Designing General Adaptive Artificial Intelligence Systems. IEEE Trans. Neural Netw. Learn. Syst. Early Access Artic. 2021, 1–14. [Google Scholar] [CrossRef]
- Mühlroth, C.; Grottke, M. Artificial Intelligence in Innovation: How to Spot Emerging Trends and Technologies. IEEE Trans. Eng. Manag. Early Access Artic. 2020, 69, 493–510. [Google Scholar] [CrossRef]
- Lai, H.; Lee, S. The Application of Artificial Intelligence and VR Technology in Clothing Store Display Design. IEEE Access (Early Access Artic.) 2020, 1. [Google Scholar] [CrossRef]
- Stock, S.; Babazadeh, D.; Becker, C. Applications of Artificial Intelligence in Distribution Power System Operation. IEEE Access (Early Access Artic.) 2021, 9, 150098–150119. [Google Scholar] [CrossRef]
- Letaief, K.B.; Shi, Y.; Lu, J.; Lu, J. Edge Artificial Intelligence for 6G: Vision, Enabling Technologies, and Applications. IEEE J. Sel. Areas Commun. Early Access Artic. 2021, 40, 5–36. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Koshiba, T. The Dichotomy of Neural Networks and Cryptography: War and Peace. Appl. Syst. Innov. 2022, 5, 61. [Google Scholar] [CrossRef]
- Zolfaghari, B.; Rabieinejad, E.; Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A. Crypto Makes AI Evolve. arXiv 2022, arXiv:2206.12669. [Google Scholar]
- Zhang, C.; Yu, Y.; Wang, Y.; Han, Z.; Zhou, M. Chaotic Neural Network-Based Hysteresis Modeling With Dynamic Operator for Magnetic Shape Memory Alloy Actuator. IEEE Trans. Magn. 2021, 57, 1–4. [Google Scholar] [CrossRef]
- Cui, Z.; Chen, Z.H.; Zhang, Q.; Gribova, V.V.; Filaretov, V.F.; Huang, D.S. RMSCNN: A Random Multi-Scale Convolutional Neural Network for Marine Microbial Bacteriocins Identification. IEEE/ACM Trans. Comput. Biol. Bioinform. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Cho, K.; Miyano, T. Chaotic Cryptography Using Augmented Lorenz Equations Aided by Quantum Key Distribution. IEEE Trans. Circuits Syst. Regul. Pap. 2015, 62, 478–487. [Google Scholar] [CrossRef]
- Feng, Y.; Wu, J.; Zhan, X.; Liu, J.; Sun, Z.; Zhang, J.; Kobayashi, M.; Chen, J. A Novel Encrypted Computing-in-Memory (eCIM) by Implementing Random Telegraph Noise (RTN) as Keys Based on 55 nm NOR Flash Technology. IEEE Electron Device Lett. Early Access Artic. 2022, 69, 1698–1705. [Google Scholar]
- Buczak, A.L.; Guven, E. A Survey of Data Mining and Machine Learning Methods for Cyber Security Intrusion Detection. IEEE Commun. Surv. Tutorials 2016, 18, 1153–1176. [Google Scholar] [CrossRef]
- Boulgouris, N.V.; Plataniotis, K.N.; Micheli-Tzanakou, E. A Comparative Survey on Biometric Identity Authentication Techniques Based on Neural Networks. In Biometrics: Theory, Methods, and Applications; Boulgouris, N.V., Plataniotis, K.N., Micheli-Tzanakou, E., Eds.; Wiley-IEEE Press: Hoboken, NJ, USA, 2010; Chapter 3; pp. 47–79. [Google Scholar]
- Vinayakvitthal, L.; Charniya, N.N. Review of advances in Neural Network based biometric authentication. In Proceedings of the International Conference on Communications and Signal Processing (ICCSP), Melmaruvathur, India, 2–4 April 2015. [Google Scholar]
- Dibaei, M.; Zheng, X.; Xia, Y.; Xu, X.; Jolfaei, A.; Bashir, A.K.; Tariq, U.; Yu, D.; Vasilakos, A.V. Investigating the Prospect of Leveraging Blockchain and Machine Learning to Secure Vehicular Networks: A Survey. IEEE Trans. Intell. Transp. Syst. Early Access Artic. 2021, 23, 683–700. [Google Scholar] [CrossRef]
- Alimi, O.A.; Ouahada, K.; Abu-Mahfouz, A.M. A Review of Machine Learning Approaches to Power System Security and Stability. IEEE Access 2020, 8, 113512–113531. [Google Scholar] [CrossRef]
- Hossain, E.; Khan, I.; Un-Noor, F.; Sikander, S.S.; Sunny, M.S.H. Application of Big Data and Machine Learning in Smart Grid, and Associated Security Concerns: A Review. IEEE Access 2019, 7, 13960–13988. [Google Scholar] [CrossRef]
- Singh, S.; Sulthana, R.; Shewale, T.; Chamola, V.; Benslimane, A.; Sikdar, B. Machine Learning Assisted Security and Privacy Provisioning for Edge Computing: A Survey. IEEE Internet Things J. Early Access Artic. 2021, 9, 236–260. [Google Scholar] [CrossRef]
- Zaman, S.; Alhazmi, K.; Aseeri, M.A.; Ahmed, M.R.; Khan, R.T.; Kaiser, M.S.; Mahmud, M. Security Threats and Artificial Intelligence Based Countermeasures for Internet of Things Networks: A Comprehensive Survey. IEEE Access 2021, 9, 94668–94690. [Google Scholar] [CrossRef]
- Wu, H.; Han, H.; Wang, X.; Sun, S. Research on Artificial Intelligence Enhancing Internet of Things Security: A Survey. IEEE Access 2020, 8, 153826–153848. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutorials 2020, 22, 1646–1685. [Google Scholar] [CrossRef] [Green Version]
- Uprety, A.; Rawat, D.B. Reinforcement Learning for IoT Security: A Comprehensive Survey. IEEE Internet Things J. 2021, 8, 8693–8706. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A Survey on Machine Learning Techniques for Cyber Security in the Last Decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Hadke, P.P.; Kale, S.G. Use of Neural Networks in cryptography: A review. In Proceedings of the World Conference on Futuristic Trends in Research and Innovation for Social Welfare (Startup Conclave), Coimbatore, India, 29 February–1 March 2016. [Google Scholar]
- Meraouche, I.; Dutta, S.; Tan, H.; Sakurai, K. Neural Networks-Based Cryptography: A Survey. IEEE Access 2021, 9, 124727–124740. [Google Scholar] [CrossRef]
- Blackledge, J.; Mosola, N. Applications of Artificial Intelligence to Cryptography. Trans. Mach. Learn. Artif. Intell. 2020, 8, 21–60. [Google Scholar] [CrossRef]
- Su, J.; Kankani, A.; Zajko, G.; Elchouemi, A.; Kurniawan, H. Review of Image encryption techniques using neural network for optical security in the healthcare sector—PNO System. In Proceedings of the 5th International Conference on Innovative Technologies in Intelligent Systems and Industrial Applications (CITISIA), Sydney, Australia, 25–27 November 2020. [Google Scholar]
- Alani, M. Applications of Machine Learning in Cryptography: A Survey. arXiv 2019, arXiv:1902.04109v1. [Google Scholar]
- Sooksatra, K.; Rivas, P. A Review of Machine Learning and Cryptography Applications. In Proceedings of the International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 16–18 December 2020. [Google Scholar]
- ÖzÇakmak, B.; ÖzbIlen, A.; YavanoGlu, U.; CIn, K. Neural and Quantum Cryptography in Big Data: A Review. In Proceedings of the IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019. [Google Scholar]
- Nassif, A.B.; Talib, M.A.; Nasir, Q.; Albadani, H.; Dakalbab, F.M. Machine Learning for Cloud Security: A Systematic Review. IEEE Access 2021, 9, 20717–20735. [Google Scholar] [CrossRef]
- Wright, J.L.; Manic, M. Neural network approach to Locating Cryptography in object code. In Proceedings of the IEEE Conference on Emerging Technologies & Factory Automation, Palma de Mallorca, Spain, 22–25 September 2009. [Google Scholar]
- Jia, L.; Zhou, A.; Jia, P.; Liu, L.; Wang, Y.; Liu, L. A Neural Network-Based Approach for Cryptographic Function Detection in Malware. IEEE Access 2020, 8, 23506–23521. [Google Scholar] [CrossRef]
- Pastor, A.; Mozo, A.; Vakaruk, S.; Canavese, D.; López, D.R.; Regano, L.; Gómez-Canaval, S.; Lioy, A. Detection of Encrypted Cryptomining Malware Connections With Machine and Deep Learning. IEEE Access 2020, 8, 158036–158055. [Google Scholar] [CrossRef]
- Yu, W. Convolutional neural network attack on cryptographic circuits. Electron. Lett. 2019, 55, 246–248. [Google Scholar] [CrossRef]
- Albassal, A.; Wahdan, A.M. Neural network based cryptanalysis of a feistel type block cipher. In Proceedings of the International Conference on Electrical, Electronic and Computer Engineering, Cairo, Egypt, 5–7 September 2004. [Google Scholar]
- Apolinario, J.; Mendonca, P.; Chaves, R.; Caloba, L. Cryptanalysis of speech signals ciphered by TSP using annealed Hopfield neural network and genetic algorithms. In Proceedings of the the 39th Midwest Symposium on Circuits and Systems, Ames, IA, USA, 18–21 August 1996. [Google Scholar]
- Kumar, S.; Niamat, M. Machine Learning based Modeling Attacks on a Configurable PUF. In Proceedings of the IEEE National Aerospace and Electronics Conference, Dayton, OH, USA, 23–26 July 2018. [Google Scholar]
- Aseeri, A.O.; Zhuang, Y.; Alkatheiri, M.S. A Subspace Pre-learning Approach to Fast High-Accuracy Machine Learning of Large XOR PUFs with Component-Differential Challenges. In Proceedings of the IEEE International Conference on Big Data (Big Data), Seattle, WA, USA, 10–13 December 2018. [Google Scholar]
- Hospodar, G.; Maes, R.; Verbauwhede, I. Machine learning attacks on 65 nm Arbiter PUFs: Accurate modeling poses strict bounds on usability. In Proceedings of the IEEE International Workshop on Information Forensics and Security (WIFS), Costa Adeje, Spain, 2–5 December 2012. [Google Scholar]
- Alamro, M.A.; Zhuang, Y.; Aseeri, A.O.; Alkatheiri, M.S. Examination of Double Arbiter PUFs on Security against Machine Learning Attacks. In Proceedings of the IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019. [Google Scholar]
- Sahoo, D.P.; Nguyen, P.H.; Mukhopadhyay, D.; Chakraborty, R.S. A Case of Lightweight PUF Constructions: Cryptanalysis and Machine Learning Attacks. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2015, 34, 1334–1343. [Google Scholar] [CrossRef]
- Aseeri, A.O.; Zhuang, Y.; Alkatheiri, M.S. A Machine Learning-Based Security Vulnerability Study on XOR PUFs for Resource-Constraint Internet of Things. In Proceedings of the IEEE International Congress on Internet of Things (ICIOT), San Francisco, CA, USA, 2–7 July 2018. [Google Scholar]
- Alkatheiri, M.S.; Zhuang, Y. Towards fast and accurate machine learning attacks of feed-forward arbiter PUFs. In Proceedings of the IEEE Conference on Dependable and Secure Computing, Taipei, Taiwan, 7–10 August 2017. [Google Scholar]
- Che, W.; Martinez-Ramon, M.; Saqib, F.; Plusquellic, J. Delay model and machine learning exploration of a hardware-embedded delay PUF. In Proceedings of the IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018. [Google Scholar]
- Ganji, F.; Forte, D.; Seifert, J.P. PUFmeter a Property Testing Tool for Assessing the Robustness of Physically Unclonable Functions to Machine Learning Attacks. IEEE Access 2019, 7, 122513–122521. [Google Scholar] [CrossRef]
- Ikezaki, Y.; Nozaki, Y.; Yoshikawa, M. Deep learning attack for physical unclonable function. In Proceedings of the IEEE 5th Global Conference on Consumer Electronics, Kyoto, Japan, 11–14 October 2016. [Google Scholar]
- Khalafalla, M.; Gebotys, C. PUFs Deep Attacks: Enhanced modeling attacks using deep learning techniques to break the security of double arbiter PUFs. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Florence, Italy, 25–29 March 2019. [Google Scholar]
- Atakhodjaev, I.; Bosworth, B.T.; Grubel, B.C.; Kossey, M.R.; Villalba, J.; Cooper, A.B.; Dehak, N.; Foster, A.C.; Foster, M.A. Investigation of Deep Learning Attacks on Nonlinear Silicon Photonic PUFs. In Proceedings of the Conference on Lasers and Electro-Optics (CLEO), San Jose, CA, USA, 13–18 May 2018. [Google Scholar]
- Xu, X.; Burleson, W. Hybrid side-channel/machine-learning attacks on PUFs: A new threat? In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 24–28 March 2014. [Google Scholar]
- Yu, W.; Wen, Y. Efficient hybrid side-channel/machine learning attack on XOR PUFs. Electron. Lett. 2019, 55, 1080–1082. [Google Scholar] [CrossRef]
- Tanaka, Y.; Bian, S.; Hiromoto, M.; Sato, T. Coin Flipping PUF: A Novel PUF With Improved Resistance Against Machine Learning Attacks. IEEE Trans. Circuits Syst. II Express Briefs 2018, 65, 602–606. [Google Scholar] [CrossRef]
- Suresh, V.; Kumar, R.; Anders, M.; Kaul, H.; De, V.; Mathew, S. A 0.26% BER, 1028 Challenge-Response Machine-Learning Resistant Strong-PUF in 14 nm CMOS Featuring Stability-Aware Adversarial Challenge Selection. In Proceedings of the IEEE Symposium on VLSI Circuits, Honolulu, HI, USA, 16–19 June 2020. [Google Scholar]
- Suresh, V.B.; Kumar, R.; Mathew, S. INVITED: A 0.26% BER, Machine-Learning Resistant 1028 Challenge-Response PUF in 14nm CMOS Featuring Stability-Aware Adversarial Challenge Selection. In Proceedings of the 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 20–24 July 2020. [Google Scholar]
- Yu, M.D.; Hiller, M.; Delvaux, J.; Sowell, R.; Devadas, S.; Verbauwhede, I. A Lockdown Technique to Prevent Machine Learning on PUFs for Lightweight Authentication. IEEE Trans. -Multi-Scale Comput. Syst. 2016, 2, 146–159. [Google Scholar] [CrossRef] [Green Version]
- Dubrova, E.; Näslund, O.; Degen, B.; Gawell, A.; Yu, Y. CRC-PUF: A Machine Learning Attack Resistant Lightweight PUF Construction. In Proceedings of the IEEE European Symposium on Security and Privacy Workshops (EuroS&PW), Stockholm, Sweden, 17–19 June 2019. [Google Scholar]
- Wu, Q.; Zhang, J. CT PUF: Configurable Tristate PUF against Machine Learning Attacks. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 12–14 October 2020. [Google Scholar]
- Venkatesh, A.; Venkatasubramaniyan, A.B.; Xi, X.; Sanyal, A. 0.3 pJ/Bit Machine Learning Resistant Strong PUF Using Subthreshold Voltage Divider Array. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 1394–1398. [Google Scholar] [CrossRef]
- Awano, H.; Sato, T. Ising-PUF: A machine learning attack resistant PUF featuring lattice-like arrangement of Arbiter-PUFs. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19–23 March 2018. [Google Scholar]
- Rai, V.K.; Tripathy, S.; Mathew, J. 2SPUF: Machine Learning Attack Resistant SRAM PUF. In Proceedings of the Third ISEA Conference on Security and Privacy (ISEA-ISAP), Guwahati, India, 27 February–1 March 2020. [Google Scholar]
- Chen, S.; Li, B.; Dan, F.; Chen, J. A machine learning resistant Arbiter PUFs scheme based on polynomial reconstruction. In Proceedings of the IEEE 2nd International Conference on Signal and Image Processing (ICSIP), Singapore, 4–6 August 2017. [Google Scholar]
- Amsaad, F.; Choudhury, M.; Chaudhuri, C.R.; Niamat, M. An innovative delay based algorithm to boost PUF security against machine learning attacks. In Proceedings of the Annual Connecticut Conference on Industrial Electronics, Technology & Automation (CT-IETA), Bridgeport, CT, USA, 14–15 October 2016. [Google Scholar]
- Su, H.; Zwolinski, M.; Halak, B. A Machine Learning Attacks Resistant Two Stage Physical Unclonable Functions Design. In Proceedings of the IEEE 3rd International Verification and Security Workshop (IVSW), Costa Brava, Spain, 2–4 July 2018. [Google Scholar]
- Pundir, N.; Hazari, N.A.; Amsaad, F.; Niamat, M. A novel hybrid delay based physical unclonable function immune to machine learning attacks. In Proceedings of the IEEE National Aerospace and Electronics Conference (NAECON), Dayton, OH, USA, 27–30 June 2017. [Google Scholar]
- Ma, Q.; Gu, C.; Hanley, N.; Wang, C.; Liu, W.; O’Neill, M. A machine learning attack resistant multi-PUF design on FPGA. In Proceedings of the 23rd Asia and South Pacific Design Automation Conference (ASP-DAC), Jeju, Korea, 22–25 January 2018. [Google Scholar]
- Zhuang, H.; Xi, X.; Sun, N.; Orshansky, M. A Strong Subthreshold Current Array PUF Resilient to Machine Learning Attacks. IEEE Trans. Circuits Syst. Regul. Pap. 2020, 67, 135–144. [Google Scholar] [CrossRef]
- Xi, X.; Zhuang, H.; Sun, N.; Orshansky, M. Strong subthreshold current array PUF with 265 challenge-response pairs resilient to machine learning attacks in 130 nm CMOS. In Proceedings of the Symposium on VLSI Circuits, Kyoto, Japan, 5–8 June 2017. [Google Scholar]
- Venkatesh, A.; Sanyal, A. A Machine Learning Resistant Strong PUF using Subthreshold Voltage Divider Array in 65 nm CMOS. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Sapporo, Japan, 26–29 May 2019. [Google Scholar]
- Pang, Y.; Wu, H.; Gao, B.; Wu, D.; Chen, A.; Qian, H. A novel PUF against machine learning attack: Implementation on a 16 Mb RRAM chip. In Proceedings of the IEEE International Electron Devices Meeting (IEDM), San Francisco, CA, USA, 2–6 December 2017. [Google Scholar]
- Mahmoodi, M.; Nili, H.; Larimian, S.; Guo, X.; Strukov, D. ChipSecure: A Reconfigurable Analog eFlash-Based PUF with Machine Learning Attack Resiliency in 55 nm CMOS. In Proceedings of the 56th ACM/IEEE Design Automation Conference (DAC), Las Vegas, NV, USA, 2–6 June 2019. [Google Scholar]
- Zhang, Y.; Xue, T.; Zhai, Z.; Ma, C.; Cai, X. The Improvement of Public Key Cryptography Based on Chaotic Neural Networks. In Proceedings of the Eighth International Conference on Intelligent Systems Design and Applications, Kaohsuing, Taiwan, 26–28 November 2008. [Google Scholar]
- Wen, Y.; Lao, Y. Enhancing PUF reliability by machine learning. In Proceedings of the IEEE International Symposium on Circuits and Systems (ISCAS), Baltimore, MD, USA, 28–31 May 2017. [Google Scholar]
- Dogaru, R.; Murgan, A.; Ioan, D. Chains of discrete-time chaotic neural networks for generation of broadband signals with applications in improved ciphering systems. In Proceedings of the 8th Mediterranean Electrotechnical Conference on Industrial Applications in Power Systems, Computer Science and Telecommunications, Bari, Italy, 16 May 1996. [Google Scholar]
- Hu, G.; Kou, W.; Dong, J.; Peng, J. A Novel Image Encryption Algorithm Based on Cellular Neural Networks Hyper Chaotic System. In Proceedings of the IEEE 4th International Conference on Computer and Communications (ICCC), Chengdu, China, 7–10 December 2018. [Google Scholar]
- Liu, Y.; Zhang, J.; Tang, W. Noise removal using Cohen-Grossberg neural network for improving the quality of the decrypted image in color encryption. In Proceedings of the IEEE 3rd International Conference on Communication Software and Networks, Xi’an, China, 27–29 May 2011. [Google Scholar]
- Chatterjee, B.; Das, D.; Maity, S.; Sen, S. RF-PUF: Enhancing IoT Security Through Authentication of Wireless Nodes Using In-Situ Machine Learning. IEEE Internet Things J. 2019, 6, 388–398. [Google Scholar] [CrossRef] [Green Version]
- Talreja, V.; Soleymani, S.; Valenti, M.C.; Nasrabadi, N.M. Learning to Authenticate with Deep Multibiometric Hashing and Neural Network Decoding. In Proceedings of the IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019. [Google Scholar]
- Hu, D.; Wang, Y. Secure Authentication on WiMAX with Neural Cryptography. In Proceedings of the International Conference on Information Security and Assurance, Busan, Korea, 24–26 April 2008. [Google Scholar]
- Chatterjee, B.; Das, D.; Sen, S. RF-PUF: IoT security enhancement through authentication of wireless nodes using in-situ machine learning. In Proceedings of the IEEE International Symposium on Hardware Oriented Security and Trust (HOST), Washington, DC, USA, 30 April–4 May 2018. [Google Scholar]
- Hu, D.; Lao, H. Privacy Research on Ubicomp Computing with Neural Cryptography. In Proceedings of the The 3rd International Conference on Grid and Pervasive Computing—Workshops, Kunming, China, 25–28 May 2008. [Google Scholar]
- Navghare, N.; Kulkarni, D.B. Data Privacy and Prediction Using Neural Network and Homomorphic Encryption. In Proceedings of the Second International Conference on Intelligent Computing and Control Systems (ICICCS), Madurai, India, 14–15 June 2018. [Google Scholar]
- Sirichotedumrong, W.; Kinoshita, Y.; Kiya, H. On the Security of Pixel-Based Image Encryption for Privacy-Preserving Deep Neural Networks. In Proceedings of the IEEE 8th Global Conference on Consumer Electronics (GCCE), Osaka, Japan, 15–18 October 2019. [Google Scholar]
- Sirichotedumrong, W.; Maekawa, T.; Kinoshita, Y.; Kiya, H. Privacy-Preserving Deep Neural Networks with Pixel-Based Image Encryption Considering Data Augmentation in the Encrypted Domain. In Proceedings of the IEEE International Conference on Image Processing (ICIP), Taipei, Taiwan, 22–25 September 2019. [Google Scholar]
- Fragkos, G.; Minwalla, C.; Plusquellic, J.; Tsiropoulou, E.E. Reinforcement Learning Toward Decision-Making for Multiple Trusted-Third-Parties in PUF-Cash. In Proceedings of the IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020. [Google Scholar]
- Seethalakshmi, K.; A, U.B.; N, S.K. Security enhancement in image steganography using neural networks and visual cryptography. In Proceedings of the International Conference on Computation System and Information Technology for Sustainable Solutions (CSITSS), Bengaluru, India, 6–8 October 2016. [Google Scholar]
- Yue, T.W.; Chiang, S. A neural network approach for visual cryptography. In Proceedings of the the IEEE-INNS-ENNS International Joint Conference on Neural Networks, Como, Italy, 27 July 2000. [Google Scholar]
- Ge, S.; Changgen, P.; Xuelan, M. Visual Cryptography Scheme Using Pi-sigma Neural Networks. In Proceedings of the International Symposium on Information Science and Engineering, Shanghai, China, 20–22 December 2008. [Google Scholar]
- Firmino, M.; Brandão, G.B.; Guerreiro, A.M.G.; de M. Valentim, R.A. Neural cryptography applied to key management protocol with mutual authentication in RFID systems. In Proceedings of the International Conference for Internet Technology and Secured Transactions, (ICITST), London, UK, 9–12 November 2009. [Google Scholar]
- Thoms, G.R.W.; Muresan, R.; Al-Dweik, A. Chaotic Encryption Algorithm With Key Controlled Neural Networks for Intelligent Transportation Systems. IEEE Access 2019, 7, 158697–158709. [Google Scholar] [CrossRef]
- Allam, A.M.; Abbas, H.M. Group key exchange using neural cryptography with binary trees. In Proceedings of the 24th Canadian Conference on Electrical and Computer Engineering(CCECE), Niagara Falls, ON, Canada, 8–11 May 2011. [Google Scholar]
- Kinzel, W.; Kanter, I. Neural cryptography. In Proceedings of the the 9th International Conference on Neural Information Processing, Singapore, 18–22 November 2002. [Google Scholar]
- Zhang, J.; Qu, G. Physical Unclonable Function-Based Key Sharing via Machine Learning for IoT Security. IEEE Trans. Ind. Electron. 2020, 67, 7025–7033. [Google Scholar] [CrossRef]
- Turcaník, M. Using recurrent neural network for hash function generation. In Proceedings of the International Conference on Applied Electronics (AE), Pilsen, Czech Republic, 5–6 September 2017. [Google Scholar]
- Yang, Q.T.; Gao, T.G.; Fan, L.; Gu, Q.L. Analysis of One-way Alterable Length Hash Function Based on Cell Neural Network. In Proceedings of the Fifth International Conference on Information Assurance and Security, Xi’an, China, 18–20 August 2009. [Google Scholar]
- Abdoun, N.; Assad, S.E.; Taha, M.A.; Assaf, R.; Deforges, O.; Khalil, M. Secure Hash Algorithm based on Efficient Chaotic Neural Network. In Proceedings of the International Conference on Communications (COMM), Bucharest, Romania, 9–10 June 2016. [Google Scholar]
- Turcaník, M.; Javurek, M. Hash function generation by neural network. In Proceedings of the New Trends in Signal Processing (NTSP), Demanovska dolina, Slovakia, 12–14 October 2016. [Google Scholar]
- Lian, S.; Liu, Z.; Ren, Z.; Wang, H. Hash function based on chaotic neural networks. In Proceedings of the IEEE International Symposium on Circuits and Systems, Island of Kos, 21–24 May 2006. [Google Scholar]
- Abdoun, N.; Assad, S.E.; Taha, M.A.; Assaf, R.; Deforges, O.; Khalil, M. Hash function based on efficient Chaotic Neural Network. In Proceedings of the 10th International Conference for Internet Technology and Secured Transactions (ICITST), London, UK, 14–16 December 2015. [Google Scholar]
- Turcaník, M. Hash function generation based on neural networks and chaotic maps. In Proceedings of the Communication and Information Technologies (KIT), Vysoke Tatry, Slovakia, 4–6 October 2017. [Google Scholar]
- Abdoun, N.; Assad, S.E.; Hammoud, K.; Assaf, R.; Khalil, M.; Deforges, O. New keyed chaotic neural network hash function based on sponge construction. In Proceedings of the 12th International Conference for Internet Technology and Secured Transactions (ICITST), Cambridge, UK, 11–14 December 2017. [Google Scholar]
- Zolfaghari, B.; Bibak, K.; Koshiba, T. From Random Numbers to Random Objects. Entropy 2022, 24, 928. [Google Scholar] [CrossRef]
- Yayık, A.; Kutlu, Y. Improving Pseudo random number generator using artificial neural networks. In Proceedings of the 21st Signal Processing and Communications Applications Conference (SIU), Haspolat, Turkey, 24–26 April 2013. [Google Scholar]
- Singla, P.; Sachdeva, P.; Ahmad, M. A Chaotic Neural Network Based Cryptographic Pseudo-Random Sequence Design. In Proceedings of the Fourth International Conference on Advanced Computing & Communication Technologies, Rohtak, India, 8–9 February 2014. [Google Scholar]
- Lokesh, S.; Kounte, M.R. Chaotic neural network based pseudo-random sequence generator for cryptographic applications. In Proceedings of the International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Davangere, India, 29–31 October 2015. [Google Scholar]
- Crounse, K.; Yang, T.; Chua, L. Pseudo-random sequence generation using the CNN universal machine with applications to cryptography. In Proceedings of the Fourth IEEE International Workshop on Cellular Neural Networks and Their Applications Proceedings (CNNA-96), Seville, Spain, 24–26 June 1996. [Google Scholar]
- Hameed, S.M.; Ali, L.M.M. Utilizing Hopfield Neural Network for Pseudo-Random Number Generator. In Proceedings of the IEEE/ACS 15th International Conference on Computer Systems and Applications (AICCSA), Aqaba, Jordan, 28 October–1 November 2018. [Google Scholar]
- Wang, Y.H.; Shen, Z.D.; Zhang, H.G. Pseudo Random Number Generator Based on Hopfield Neural Network. In Proceedings of the International Conference on Machine Learning and Cybernetics, Dalian, China, 13–16 August 2006. [Google Scholar]
- Tirdad, K.; Sadeghian, A. Hopfield neural networks as pseudo random number generators. In Proceedings of the Annual Meeting of the North American Fuzzy Information Processing Society, Toronto, ON, Canada, 12–14 July 2010. [Google Scholar]
- Desai, V.; Deshmukh, V.; Rao, D.H. Pseudo random number generator using Elman neural network. In Proceedings of the IEEE Recent Advances in Intelligent Computational Systems, Trivandrum, India, 22–24 September 2011. [Google Scholar]
- Bao, L.; Wang, Z.; Yu, Z.; Fang, Y.; Yang, Y.; Cai, Y.; Huang, R. Adaptive Random Number Generator Based on RRAM Intrinsic Fluctuation for Reinforcement Learning. In Proceedings of the International Symposium on VLSI Technology, Systems and Applications (VLSI-TSA), Hsinchu, Taiwan, 10–13 August 2020. [Google Scholar]
- Ash-Saki, A.; Alam, M.; Ghosh, S. Improving Reliability of Quantum True Random Number Generator using Machine Learning. In Proceedings of the 21st International Symposium on Quality Electronic Design (ISQED), Santa Clara, CA, USA, 25–26 March 2020. [Google Scholar]
- Wang, B.J.; Cao, H.J.; Wang, Y.H.; Zhang, H.G. Random Number Generator of BP Neural Network Based on SHA-2 (512). In Proceedings of the International Conference on Machine Learning and Cybernetics, Hong Kong, China, 19–22 August 2007. [Google Scholar]
- Kimura, H.; Isobe, T.; Ohigashi, T. Neural-Network-Based Pseudo-Random Number Generator Evaluation Tool for Stream Ciphers. In Proceedings of the Seventh International Symposium on Computing and Networking Workshops (CANDARW), Nagasaki, Japan, 26–29 November 2019. [Google Scholar]
- Fischer, T. Testing Cryptographically Secure Pseudo Random Number Generators with Artificial Neural Networks. In Proceedings of the 17th IEEE International Conference On Trust, Security And Privacy In Computing And Communications/ 12th IEEE International Conference On Big Data Science And Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018. [Google Scholar]
- Yu, Y.; Moraitis, M.; Dubrova, E. Can Deep Learning Break a True Random Number Generator? IEEE Trans. Circuits Syst. II Express Briefs 2021, 68, 1710–1714. [Google Scholar] [CrossRef]
- Zou, A.; Xiao, X. An Asynchronous Encryption Arithmetic Based on Laguerre Chaotic Neural Networks. In Proceedings of the WRI Global Congress on Intelligent Systems, Xiamen, China, 19–21 May 2009. [Google Scholar]
- Chung, D.; Lee, S.; Choi, D.; Lee, J. Alternative Tower Field Construction for Quantum Implementation of the AES S-box. IEEE Trans. Comput. Early Access Artic. 2021, 1. [Google Scholar] [CrossRef]
- Ahmad, M.; Malik, M. Design of chaotic neural network based method for cryptographic substitution box. In Proceedings of the International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016. [Google Scholar]
- Chen, Y.; Wang, Z.; Patil, A.; Basu, A. A 2.86-TOPS/W Current Mirror Cross-Bar-Based Machine-Learning and Physical Unclonable Function Engine For Internet-of-Things Applications. IEEE Trans. Circuits Syst. I Regul. Pap. 2019, 66, 2240–2252. [Google Scholar] [CrossRef]
- Wang, Z.; Chen, Y.; Patil, A.; Jayabalan, J.; Zhang, X.; Chang, C.H.; Basu, A. Current Mirror Array: A Novel Circuit Topology for Combining Physical Unclonable Function and Machine Learning. IEEE Trans. Circuits Syst. I Regul. Pap. 2018, 65, 1314–1326. [Google Scholar] [CrossRef]
- Wassermann, S.; Seufert, M.; Casas, P.; Gang, L.; Li, K. ViCrypt to the Rescue: Real-time, Machine-Learning-driven Video-QoE Monitoring for Encrypted Streaming Traffic. IEEE Trans. Netw. Serv. Manag. Early Access Artic. 2020, 17, 2007–2023. [Google Scholar] [CrossRef]
- Ghouse, M.; Nene, M.J.; Vembuselvi, C. Data Leakage Prevention for Data in Transit using Artificial Intelligence and Encryption Techniques. In Proceedings of the International Conference on Advances in Computing, Communication and Control (ICAC3), Mumbai, India, 20–21 December 2019. [Google Scholar]
- Jain, N.; Naik, O.; Yalagoud, A.; Bhuyan, P.; K, M. Face-Crypt Messenger: Enhancing Security of Messaging Systems using AI based Facial Recognition and Encryption. In Proceedings of the 6th International Conference on Computing Methodologies and Communication (ICCMC), Tamil Nadu, India, 29–31 March 2022. [Google Scholar]
- Sahoo, A.K.; Rudra, S.; Mohanty, A.S. Artificial intelligence based electric grid operation enabled with data encryption. In Proceedings of the International Conference on Electrical, Electronics, and Optimization Techniques (ICEEOT), Chennai, India, 3–5 March 2016. [Google Scholar]
- Allam, A.M.; Abbas, H.M.; El-Kharashi, M.W. Authenticated key exchange protocol using neural cryptography with secret boundaries. In Proceedings of the 2013 International Joint Conference on Neural Networks (IJCNN), Amman, Jordan, 14–15 July 2013. [Google Scholar]
- Hu, D. A New Service-Based Computing Security Model with Neural Cryptography. In Proceedings of the Second Pacific-Asia Conference on Web Mining and Web-based Application, Wuhan, China, 6–7 June 2009. [Google Scholar]
- Godhavari, T.; Alamelu, N.; Soundararajan, R. Cryptography Using Neural Network. In Proceedings of the Annual IEEE India Conference—Indicon, Chennai, India, 11–13 December 2005. [Google Scholar]
- Dong, T.; Huang, T. Neural Cryptography Based on Complex-Valued Neural Network. IEEE Trans. Neural Netw. Learn. Syst. Early Access Artic. 2019, 31, 4999–5004. [Google Scholar] [CrossRef] [PubMed]
- Tenorio, R.H.V.; Sham, C.W.; Vargas, D.V. Preliminary study of applied binary neural networks for neural cryptography. In Proceedings of the the 2020 Genetic and Evolutionary Computation Conference Companion, Cancún, Mexico, 8–12 July 2020. [Google Scholar]
- Fei, X.; Liu, G.; Zheng, B. A chaotic encryption system using PCA neural networks. In Proceedings of the IEEE Conference on Cybernetics and Intelligent Systems, Chengdu, China, 21–24 September 2008. [Google Scholar]
- Roy, S.S.; Shahriyar, S.A.; Asaf-Uddowla, M.; Alam, K.M.R.; Morimoto, Y. A novel encryption model for text messages using delayed chaotic neural network and DNA cryptography. In Proceedings of the 20th International Conference of Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 22–24 December 2017. [Google Scholar]
- Gaffar, A.F.O.; Putra, A.B.W.; Malani, R. The Multi Layer Auto Encoder Neural Network (ML-AENN) for Encryption and Decryption of Text Message. In Proceedings of the 5th International Conference on Science in Information Technology (ICSITech), Yogyakarta, Indonesia, 23–24 October 2019. [Google Scholar]
- Liu, C.Y.; Woungang, I.; Chao, H.C.; Dhurandher, S.K.; Chi, T.Y.; Obaidat, M.S. Message Security in Multi-Path Ad Hoc Networks Using a Neural Network-Based Cipher. In Proceedings of the IEEE Global Telecommunications Conference, Houston, TX, USA, 5–9 December 2011. [Google Scholar]
- Hu, D.; Wang, Y. Security Research on WiMAX with Neural Cryptography. In Proceedings of the International Conference on Information Security and Assurance, Busan, Korea, 24–26 April 2008. [Google Scholar]
- Ismail, I.A.; Galal-Edeen, G.H.; Khattab, S.; Bahtity, M.A.E.M.E. Satellite image encryption using neural networks backpropagation. In Proceedings of the 22nd International Conference on Computer Theory and Applications (ICCTA), Alexandria, Egypt, 13–15 October 2012. [Google Scholar]
- Zhou, S. Image Encryption Technology Research Based on Neural Network. In Proceedings of the International Conference on Intelligent Transportation, Big Data and Smart City, Halong Bay, Vietnam, 19–20 December 2015. [Google Scholar]
- Kumar, S.; Aid, R. Image encryption using wavelet based chaotic neural network. In Proceedings of the International Conference on Advances in Computing, Communications and Informatics (ICACCI), Jaipur, India, 21–24 September 2016. [Google Scholar]
- Lin, J.; Luo, Y.; Liu, J.; Bi, J.; Qiu, S.; Cen, M.; Liao, Z. An Image Compression-Encryption Algorithm Based on Cellular Neural Network and Compressive Sensing. In Proceedings of the IEEE 3rd International Conference on Image, Vision and Computing (ICIVC), Chongqing, China, 27–29 June 2018. [Google Scholar]
- de Almeida Ramos, E.; Filho, J.C.B.; Reis, R. Cryptography by Synchronization of Hopfield Neural Networks that Simulate Chaotic Signals Generated by the Human Body. In Proceedings of the 17th IEEE International New Circuits and Systems Conference (NEWCAS), Munich, Germany, 23–26 June 2019. [Google Scholar]
- Joshi, S.D.; Udupi, V.R.; Joshi, D.R. A novel neural network approach for digital image data encryption/decryption. In Proceedings of the International Conference on Power, Signals, Controls and Computation, Thrissur, India, 3–6 January 2012. [Google Scholar]
- Dridi, M.; Hajjaji, M.A.; Bouallegue, B.; Mtibaa, A. Cryptography of medical images based on a combination between chaotic and neural network. IET Image Process. 2016, 10, 830–839. [Google Scholar] [CrossRef]
- Han, B.; Jia, Y.; Huang, G.; Cai, L. A Medical Image Encryption Algorithm Based on Hermite Chaotic Neural Network. In Proceedings of the IEEE 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chongqing, China, 12–14 June 2020. [Google Scholar]
- Xiao, J.; Wang, W.; Wang, M. Image Encryption Algorithm Based on Memristive BAM Neural Networks. In Proceedings of the IEEE Third International Conference on Data Science in Cyberspace (DSC), Guangzhou, China, 18–21 June 2018. [Google Scholar]
- Bharadwaj, G.V.S.E.; Vijaya, K.; Balaga, S.K.; Thanikaiselvan, V. Image Encryption Based on Neural Network Architecture and Chaotic Systems. In Proceedings of the Second International Conference on Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 29–31 March 2018. [Google Scholar]
- Liu, X.; Jin, X.; Zhao, Y. Optical Image Encryption Using Fractional-Order Quantum Cellular Neural Networks in a Fractional Fourier Domain. In Proceedings of the 14th International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery (ICNC-FSKD), Huangshan, China, 28–30 July 2018. [Google Scholar]
- Lin, M.; Long, F.; Guo, L. Grayscale image encryption based on Latin square and cellular neural network. In Proceedings of the Chinese Control and Decision Conference (CCDC), Yinchuan, China, 28–30 May 2016. [Google Scholar]
- Li, H.; Li, C.; Ouyang, D.; Nguang, S.K. Impulsive Synchronization of Unbounded Delayed Inertial Neural Networks With Actuator Saturation and Sampled-Data Control and Its Application to Image Encryption. IEEE Trans. Neural Netw. Learn. Syst. Early Access Artic. 2020, 32, 1460–1473. [Google Scholar] [CrossRef] [PubMed]
- Yang, F.; Mou, J.; Cao, Y.; Chu, R. An image encryption algorithm based on BP neural network and hyperchaotic system. China Commun. 2020, 17, 21–28. [Google Scholar] [CrossRef]
- Wen, S.; Zeng, Z.; Huang, T.; Meng, Q.; Yao, W. Lag Synchronization of Switched Neural Networks via Neural Activation Function and Applications in Image Encryption. IEEE Trans. Neural Netw. Learn. Syst. 2015, 26, 1493–1502. [Google Scholar] [CrossRef] [Green Version]
- Liu, L.; Zhang, L.; Jiang, D.; Guan, Y.; Zhang, Z. A Simultaneous Scrambling and Diffusion Color Image Encryption Algorithm Based on Hopfield Chaotic Neural Network. IEEE Access 2019, 7, 185796–185810. [Google Scholar]
- Anikin, I.V.; Makhmutova, A.Z.; Gadelshin, O.E. Symmetric encryption with key distribution based on neural networks. In Proceedings of the 2nd International Conference on Industrial Engineering, Applications and Manufacturing (ICIEAM), Chelyabinsk, Russia, 19–20 May 2016. [Google Scholar]
- Liu, N.; Guo, D. Security Analysis of Public-key Encryption Scheme Based on Neural Networks and Its Implementing. In Proceedings of the International Conference on Computational Intelligence and Security, Guangzhou, China, 3–6 November 2006. [Google Scholar]
- Ohira, T. Neural network model with delay toward encryption. In Proceedings of the the IEEE-INNS-ENNS International Joint Conference on Neural Networks, Como, Italy, 27 July 2000. [Google Scholar]
- Wang, J.; Cheng, L.M.; Su, T. Multivariate Cryptography Based on Clipped Hopfield Neural Network. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 353–363. [Google Scholar] [CrossRef]
- Sagar, V.; Kumar, K. A symmetric key cryptography using genetic algorithm and error back propagation neural network. In Proceedings of the 2nd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 11–13 March 2015. [Google Scholar]
- Fadil, T.A.; Yaakob, S.N.; Ahmad, B. A hybrid chaos and neural network cipher encryption algorithm for compressed video signal transmission over wireless channel. In Proceedings of the 2nd International Conference on Electronic Design (ICED), Penang, Malaysia, 19–21 August 2014. [Google Scholar]
- Su, S.; Lin, A.; Yen, J.C. Design and realization of a new chaotic neural encryption/decryption network. In Proceedings of the IEEE Asia-Pacific Conference on Circuits and Systems. Electronic Communication Systems. (Cat. No.00EX394), Tianjin, China, 4–6 December 2000. [Google Scholar]
- Chatzidakis, S.; Forsberg, P.; Tsoukalas, L.H. Chaotic neural networks for intelligent signal encryption. In Proceedings of the The 5th International Conference on Information, Intelligence, Systems and Applications, Chania, Greece, 7–9 July 2014. [Google Scholar]
- Kanter, I. The theory of neural networks: Learning from examples, time-series and cryptography. In Proceedings of the IEEE International Workshop on VLSI Design and Video Technology, Suzhou, China, 28–30 May 2005. [Google Scholar]
- Zhang, X.; Sheng, S.; Lu, G.; Zheng, Y. Synchronization for arrays of coupled jumping delayed neural networks and its application to image encryption. In Proceedings of the IEEE 56th Annual Conference on Decision and Control (CDC), Melbourne, VIC, Australia, 12–15 December 2017. [Google Scholar]
- Wang, W.; Wang, X.; Luo, X.; Yuan, M. Finite-Time Projective Synchronization of Memristor-Based BAM Neural Networks and Applications in Image Encryption. IEEE Access 2018, 6, 56457–56476. [Google Scholar] [CrossRef]
- Bi, M.; Zhuo, X.; Fu, X.; Yang, X.; Hu, W. Cellular Neural Network Encryption Scheme for Time Synchronization and CPAs Resistance in OFDM-PON. IEEE Access 2019, 7, 57129–57137. [Google Scholar] [CrossRef]
- Chen, W.H.; Luo, S.; Zheng, W.X. Impulsive Synchronization of Reaction–Diffusion Neural Networks With Mixed Delays and Its Application to Image Encryption. IEEE Trans. Neural Netw. Learn. Syst. 2016, 27, 2696–2710. [Google Scholar] [CrossRef]
- Wang, W.; Yu, X.; Luo, X.; Kurths, J. Finite-Time Synchronization of Chaotic Memristive Multidirectional Associative Memory Neural Networks and Applications in Image Encryption. IEEE Access 2018, 6, 35764–35779. [Google Scholar] [CrossRef]
- Song, X.; Man, J.; Song, S.; Ning, Z. Event-triggered synchronisation of Markovian reaction–diffusion inertial neural networks and its application in image encryption. IET Control. Theory Appl. 2020, 14, 2726–2740. [Google Scholar] [CrossRef]
- Vandewalle, J.; Preneel, B.; Csapodi, M. Data security issues, cryptographic protection methods, and the use of cellular neural networks and cellular automata. In Proceedings of the Fifth IEEE International Workshop on Cellular Neural Networks and their Applications. Proceedings (Cat. No.98TH8359), London, UK, 14–17 April 1998. [Google Scholar]
- Mislovaty, R.; Klein, E.; Kanter, I.; Kinzel, W. Security of neural cryptography. In Proceedings of the the 2004 11th IEEE International Conference on Electronics, Circuits and Systems, Tel Aviv, Israel, 15 December 2004. [Google Scholar]
- Choi, Y.; Sim, J.; Kim, L.S. CREMON: Cryptography Embedded on the Convolutional Neural Network Accelerator. IEEE Trans. Circuits Syst. II Express Briefs (Early Access Artic.) 2020, 67, 3337–3341. [Google Scholar] [CrossRef]
- Arora, B.; Srishti, K.; Khatri, N.; Niranjan, V. Application of Artificial Neural Network in Cryptography. In Proceedings of the 2nd International Conference on Power Energy, Environment and Intelligent Control (PEEIC), Greater Noida, India, 18–19 October 2019. [Google Scholar]
- Zhu, Y.; Vargas, D.V.; Sakurai, K. Neural Cryptography Based on the Topology Evolving Neural Networks. In Proceedings of the Sixth International Symposium on Computing and Networking Workshops (CANDARW), Takayama, Japan, 27–30 November 2018. [Google Scholar]
- Wright, J.L.; Manic, M. Neural network architecture selection analysis with application to cryptography location. In Proceedings of the International Joint Conference on Neural Networks (IJCNN), Barcelona, Spain, 18–23 July 2010. [Google Scholar]
- Munukur, R.K.; Gnanam, V. Neural network based decryption for random encryption algorithms. In Proceedings of the 3rd International Conference on Anti-Counterfeiting, Security, and Identification in Communication, Hong Kong, China, 20–22 August 2009. [Google Scholar]
- Lytvyn, V.; Peleshchak, I.; Peleshchak, R.; Vysotska, V. Information Encryption Based on the Synthesis of a Neural Network and AES Algorithm. In Proceedings of the 3rd International Conference on Advanced Information and Communications Technologies (AICT), Lviv, Ukraine, 2–6 July 2019. [Google Scholar]
- Srivastava, S.; Bhatia, A. On the Learning Capabilities of Recurrent Neural Networks: A Cryptographic Perspective. In Proceedings of the IEEE International Conference on Big Knowledge (ICBK), Singapore, 17–18 November 2018. [Google Scholar]
- Skovajsová, L. Comparison of Cryptography by Chaotic Neural Network and by AES. In Proceedings of the IEEE 19th International Symposium on Computational Intelligence and Informatics and 7th IEEE International Conference on Recent Achievements in Mechatronics, Automation, Computer Sciences and Robotics (CINTI-MACRo), Szeged, Hungary, 14–16 November 2019. [Google Scholar]
- Forgác, R.; Ockay, M. Contribution to Symmetric Cryptography by Convolutional Neural Networks. In Proceedings of the Communication and Information Technologies (KIT), Vysoke Tatry, Slovakia, 9–11 October 2019. [Google Scholar]
- Allam, A.M.; Abbas, H.M. Improved security of neural cryptography using don’t-trust-my-partner and error prediction. In Proceedings of the International Joint Conference on Neural Networks, Atlanta, GA, USA, 14–19 June 2009. [Google Scholar]
- Saraswat, P.; Garg, K.; Tripathi, R.; Agarwal, A. Encryption Algorithm Based on Neural Network. In Proceedings of the 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Ghaziabad, India, 18–19 April 2019. [Google Scholar]
- Zang, H.; Min, L. Generalized synchronization theorems for a kind of Neural Network with application in data encryption. In Proceedings of the 3rd IEEE Conference on Industrial Electronics and Applications, Singapore, 3–5 June 2008. [Google Scholar]
- Cantoro, R.; Deligiannis, N.I.; Reorda, M.S.; Traiola, M.; Valea, E. Evaluating Data Encryption Effects on the Resilience of an Artificial Neural Network. In Proceedings of the IEEE International Symposium on Defect and Fault Tolerance in VLSI and Nanotechnology Systems (DFT), Frascati, Italy, 19–21 October 2020. [Google Scholar]
- Arvandi, M.; Wu, S.; Sadeghian, A. On the use of recurrent neural networks to design symmetric ciphers. IEEE Comput. Intell. Mag. 2008, 3, 42–53. [Google Scholar] [CrossRef]
- Arvandi, M.; Wu, S.; Sadeghian, A.; Melek, W.; Woungang, I. Symmetric Cipher Design Using Recurrent Neural Networks. In Proceedings of the IEEE International Joint Conference on Neural Network, Vancouver, BC, Canada, 16–21 July 2006. [Google Scholar]
- Cai, Y.; Chen, X.; Tian, L.; Wang, Y.; Yang, H. Enabling Secure in-Memory Neural Network Computing by Sparse Fast Gradient Encryption. In Proceedings of the IEEE/ACM International Conference on Computer-Aided Design (ICCAD), Westminster, CO, USA, 4–7 November 2019. [Google Scholar]
- Hu, D. Secure mobile network handover with neural cryptography. In Proceedings of the International Symposium on Communications and Information Technologies, Sydney, Australia, 16–19 October 2007. [Google Scholar]
- Stöttinger, M.; Huss, S.A.; Mühlbach, S.; Koch, A. Side-Channel Resistance Evaluation of a Neural Network Based Lightweight Cryptography Scheme. In Proceedings of the IEEE/IFIP International Conference on Embedded and Ubiquitous Computing, Hong Kong, China, 11–13 December 2010. [Google Scholar]
- Arvandi, M.; Sadeghian, A. Chosen Plaintext Attack against Neural Network-Based Symmetric Cipher. In Proceedings of the International Joint Conference on Neural Networks, Orlando, FL, USA, 12–17 August 2007. [Google Scholar]
- Allam, A.M.; Abbas, H.M.; El-Kharashi, M.W. Security analysis of neural cryptography implementation. In Proceedings of the IEEE Pacific Rim Conference on Communications, Computers and Signal Processing (PACRIM), Victoria, BC, Canada, 27–29 August 2013. [Google Scholar]
- Ganjavi, R.; Sharafat, A.R. Edge-Assisted Public Key Homomorphic Encryption for Preserving Privacy in Mobile Crowdsensing. IEEE Trans. Serv. Comput. Early Access Artic. 2022, 1. [Google Scholar] [CrossRef]
- Zhang, P.; Huang, T.; Sun, X.; Zhao, W.; Liu, H.; Lai, S.; Liu, J.K. Privacy-Preserving and Outsourced Multi-Party K-Means Clustering Based on Multi-Key Fully Homomorphic Encryption. IEEE Trans. Dependable Secur. Comput. Early Access Artic. 2022, 1–12. [Google Scholar] [CrossRef]
- Zhang, L.; Xu, J.; Vijayakumar, P.; Sharma, P.K.; Ghosh, U. Homomorphic Encryption-based Privacy-preserving Federated Learning in IoT-enabled Healthcare System. IEEE Trans. Netw. Sci. Eng. Early Access Artic. 2022, 1–17. [Google Scholar] [CrossRef]
- Yelina, T.N.; Bezzateev, S.V.; Mylnikov, V.A. The Homomorphic Encryption in Pipelines Accident Prediction by Using Cloud-based Neural Network. In Proceedings of the Wave Electronics and its Application in Information and Telecommunication Systems (WECONF), St. Petersburg, Russia, 3–7 June 2019. [Google Scholar]
- Ghimes, A.M.; Vladuta, V.A.; Patriciu, V.V.; Ionita, A. Applying Neural Network Approach to Homomorphic Encrypted Data. In Proceedings of the 10th International Conference on Electronics, Computers and Artificial Intelligence (ECAI), Iasi, Romania, 28–30 June 2018. [Google Scholar]
- Li, X.; Han, Q.; Jin, X. A Secure and Efficient Face-Recognition Scheme Based on Deep Neural Network and Homomorphic Encryption. In Proceedings of the International Conference on Virtual Reality and Visualization (ICVRV), Qingdao, China, 22–24 October 2018. [Google Scholar]
- Li, Y.; Aghvami, A.H.; Dong, D. Intelligent Trajectory Planning in UAV-Mounted Wireless Networks: A Quantum-Inspired Reinforcement Learning Perspective. IEEE Wirel. Commun. Lett. Early Access Artic. 2021, 10, 1994–1998. [Google Scholar] [CrossRef]
- Dong, D.; Chen, C.; Chu, J.; Tarn, T.J. Robust Quantum-Inspired Reinforcement Learning for Robot Navigation. IEEE/ASME Trans. Mechatron. 2012, 17, 86–97. [Google Scholar] [CrossRef]
- Patel, O.P.; Bharill, N.; Tiwari, A.; Prasad, M. A Novel Quantum-Inspired Fuzzy Based Neural Network for Data Classification. IEEE Trans. Emerg. Top. Comput. 2021, 9, 1031–1044. [Google Scholar] [CrossRef]
- Wei, Q.; Ma, H.; Chen, C.; Dong, D. Deep Reinforcement Learning With Quantum-Inspired Experience Replay. IEEE Trans. Cybern. Early Access Artic. 2021, 1–13. [Google Scholar] [CrossRef] [PubMed]
- Masuyama, N.; Loo, C.K.; Seera, M.; Kubota, N. Quantum-Inspired Multidirectional Associative Memory With a Self-Convergent Iterative Learning. IEEE Trans. Neural Netw. Learn. Syst. 2018, 29, 1058–1068. [Google Scholar] [CrossRef] [PubMed]
- Forgác, R.; Ockay, M. Big data protection via neural and quantum cryptography. In Proceedings of the 3rd International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 16–18 March 2016. [Google Scholar]
- Truong, N.D.; Haw, J.Y.; Assad, S.M.; Lam, P.K.; Kavehei, O. Machine Learning Cryptanalysis of a Quantum Random Number Generator. IEEE Trans. Inf. Forensics Secur. 2019, 14, 403–414. [Google Scholar] [CrossRef] [Green Version]
- Niemiec, M.; Mehic, M.; Voznak, M. Security Verification of Artificial Neural Networks Used to Error Correction in Quantum Cryptography. In Proceedings of the 26th Telecommunications Forum (TELFOR), Belgrade, Serbia, 20–21 November 2018. [Google Scholar]
- Anh, T.T.; Thanh, N.V.; Luong, T.D. A construction of cryptography system based on quantum neural network. In Proceedings of the Eighth International Conference on Knowledge and Systems Engineering (KSE), Hanoi, Vietnam, 6–8 October 2016. [Google Scholar]






| Stage | Resil. | Improve Non-Sec. | Support Scen. | Util. Non-Encrypt. | Util. Encrypt. |
|---|---|---|---|---|---|
| AIUC | No | No | No | No | No |
| AIRC | Yes | No | No | No | No |
| AIBC | Yes | Yes | Yes | No | No |
| AIAC | Yes | Yes | Yes | Yes | No |
| AIEC | Yes | Yes | Yes | Yes | Yes |
| Survey | Year | Gen. AI | Crypto | Evol. | Roadmap | Quantum |
|---|---|---|---|---|---|---|
| [39] | 2021 | Yes | No | No | Yes | No |
| [30] | 2021 | No | No | No | No | No |
| [43] | 2021 | No | Yes | No | No | No |
| [34] | 2020 | No | No | No | Yes | No |
| [48] | 2020 | Yes | Yes | No | No | Yes |
| [42] | 2020 | No | No | No | Yes | No |
| [44] | 2020 | Yes | Yes | No | Yes | No |
| [37] | 2020 | Yes | No | No | Yes | No |
| [38] | 2020 | Yes | No | No | Yes | No |
| [33] | 2020 | No | No | No | Yes | No |
| [40] | 2020 | No | No | No | No | No |
| [36] | 2020 | No | No | No | Yes | No |
| [47] | 2020 | No | Yes | No | No | No |
| [45] | 2020 | No | Yes | No | No | No |
| [32] | 2020 | No | No | No | No | No |
| [49] | 2019 | Yes | Yes | No | No | No |
| [46] | 2019 | No | Yes | No | No | No |
| [35] | 2019 | No | No | No | Yes | No |
| [41] | 2019 | No | No | No | No | No |
| [31] | 2010 | No | No | No | No | No |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zolfaghari, B.; Koshiba, T. AI Makes Crypto Evolve. Appl. Syst. Innov. 2022, 5, 75. https://doi.org/10.3390/asi5040075
Zolfaghari B, Koshiba T. AI Makes Crypto Evolve. Applied System Innovation. 2022; 5(4):75. https://doi.org/10.3390/asi5040075
Chicago/Turabian StyleZolfaghari, Behrouz, and Takeshi Koshiba. 2022. "AI Makes Crypto Evolve" Applied System Innovation 5, no. 4: 75. https://doi.org/10.3390/asi5040075
APA StyleZolfaghari, B., & Koshiba, T. (2022). AI Makes Crypto Evolve. Applied System Innovation, 5(4), 75. https://doi.org/10.3390/asi5040075






