Investigation of Secure Communication of Modbus TCP/IP Protocol: Siemens S7 PLC Series Case Study
Abstract
1. Introduction
- A novel hardware device that passively detects ARP spoofing activity in Modbus TCP/IP networks and prevents traffic redirection without relying on computer-based security tools.
- An experimental demonstration of a real-world infiltration scenario involving Siemens S7-1200 PLCs, highlighting the ease of exploiting ARP spoofing to compromise Modbus communication.
- The proposed mitigation toolkit, compatible with both legacy ICS setups and modern, monitored environments.
2. Background on Modbus TCP/IP Communication and ARP Spoofing Attacks
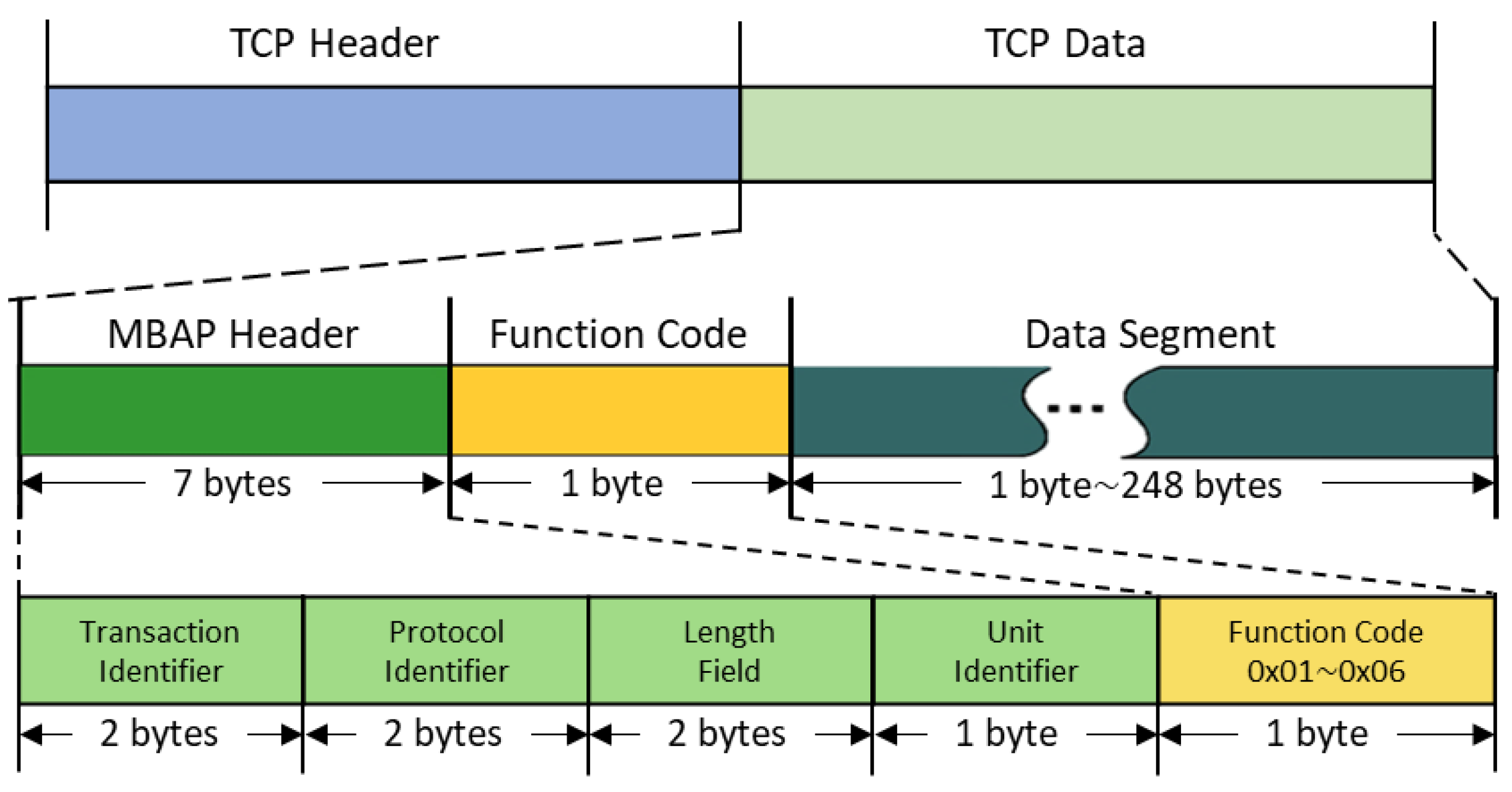
2.1. Modbus TCP/IP Protocol
- Plain text data transmission: Modbus TCP/IP transmits data packets without encryption, leaving sensitive information exposed and easily accessible to attackers. This allows them to gather crucial information, potentially aiding in the preparation for system attacks.
- Lack of authentication: the absence of robust authentication mechanisms between the client and server enables attackers to impersonate legitimate users and send control commands to devices.
- Abuse of function codes: unrestricted function codes allow any client user to issue commands, potentially leading to unintended actions like device restarts or shutdowns without adequate server safeguards.
- Data tampering: the Modbus TCP/IP protocol lacks a data integrity check, allowing attackers to modify transmitted data undetected.
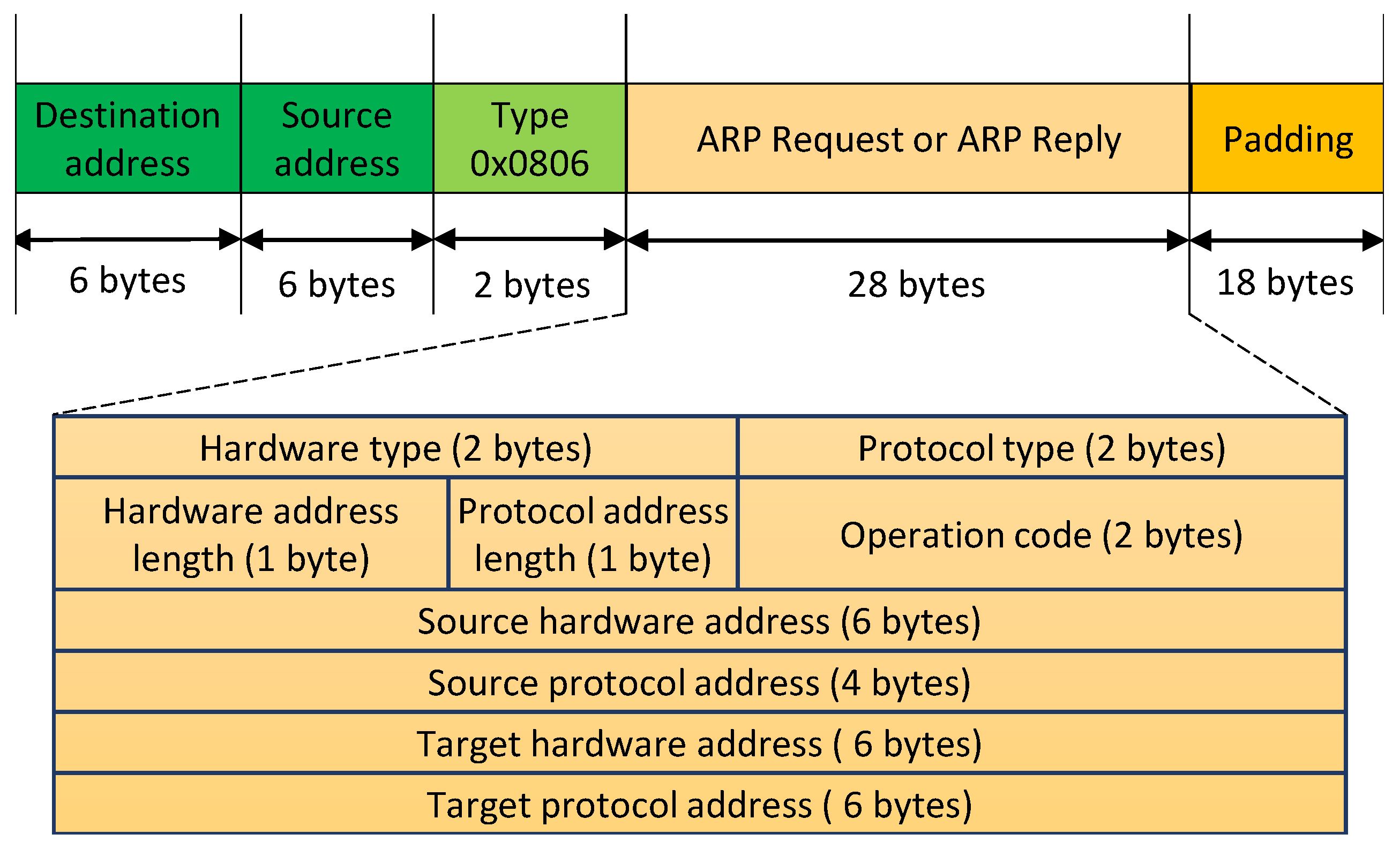
2.2. Address Resolution Protocol
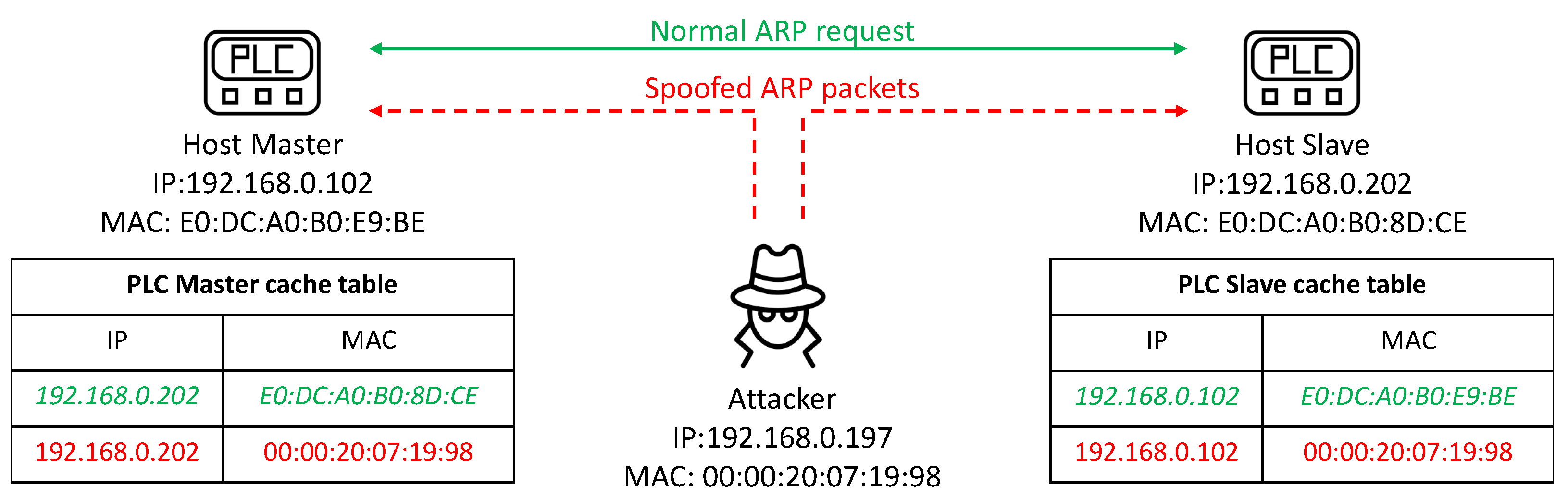
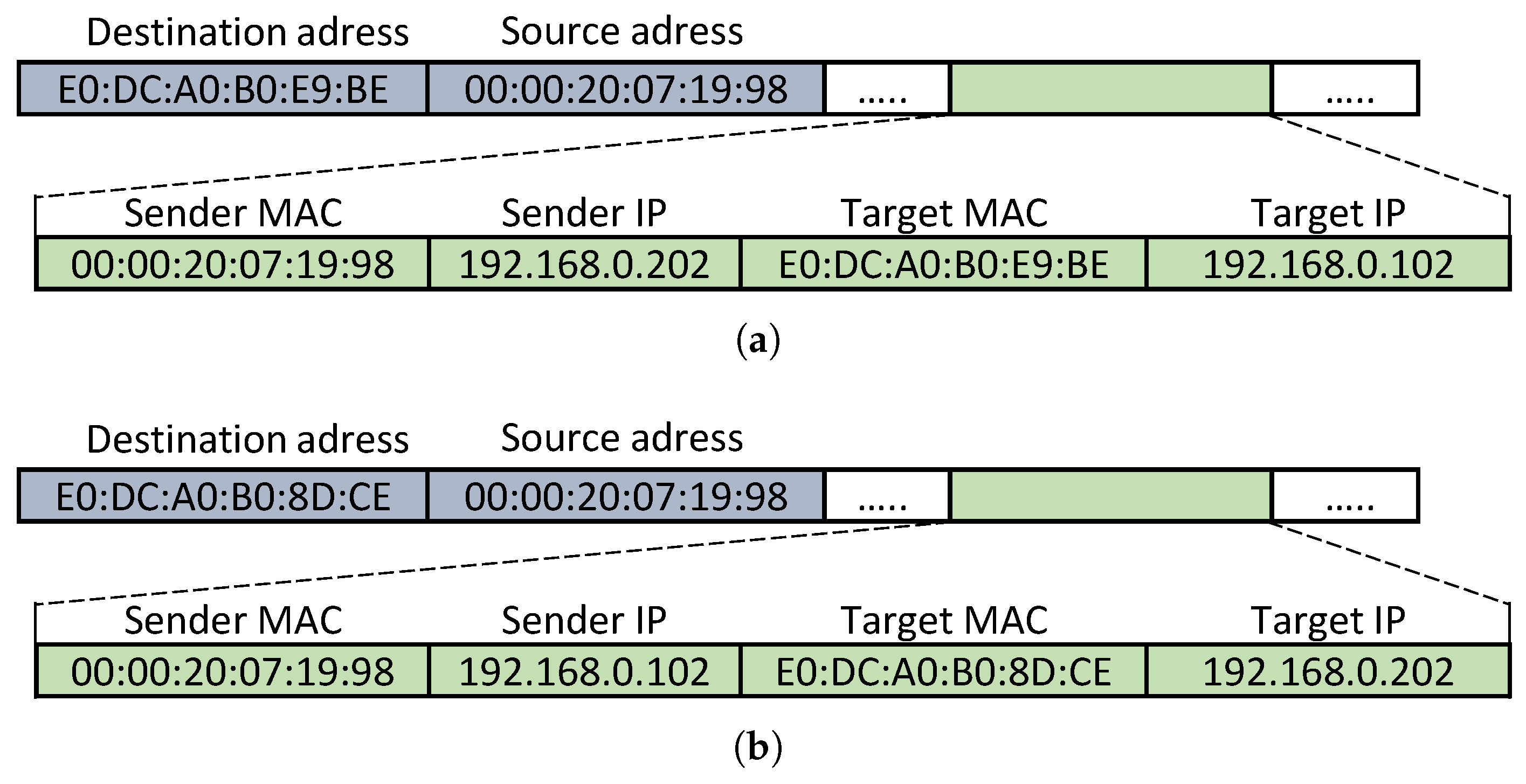
2.3. ARP Spoofing
2.4. Threat Landscape and Related Work
3. Design and Implementation
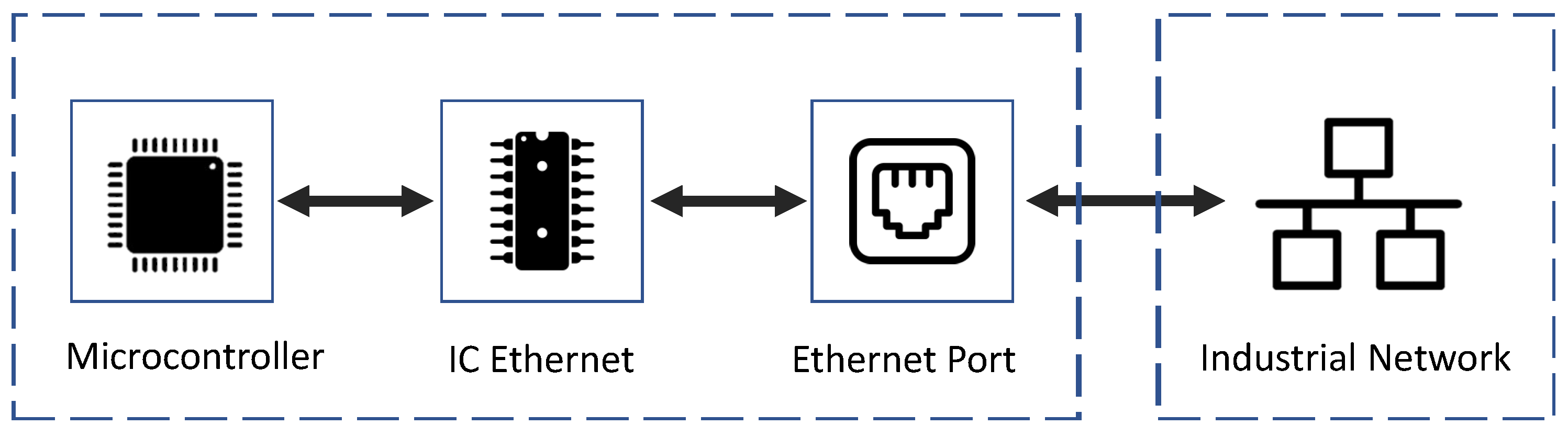
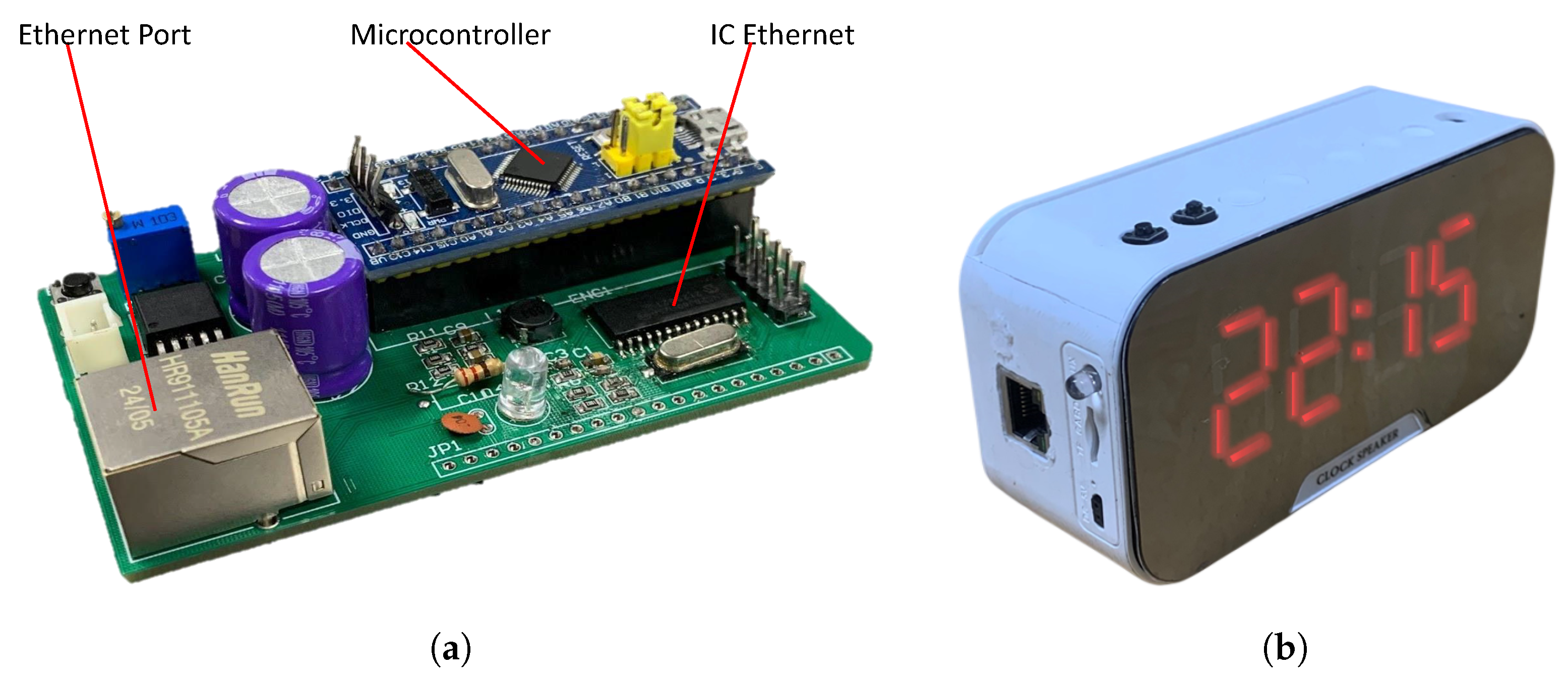
3.1. Hardware Devices
- Microcontroller STM32F103C8T6: Compact size, maximum clock speed of 72 MHz.
- Ethernet shield ENC28J60: Standalone Ethernet controller utilizing the SPI.
- Ethernet port: Module RJ45.
- Source: Lithium battery, DC low-voltage circuit LM2596.
- Buttons, LEDs.
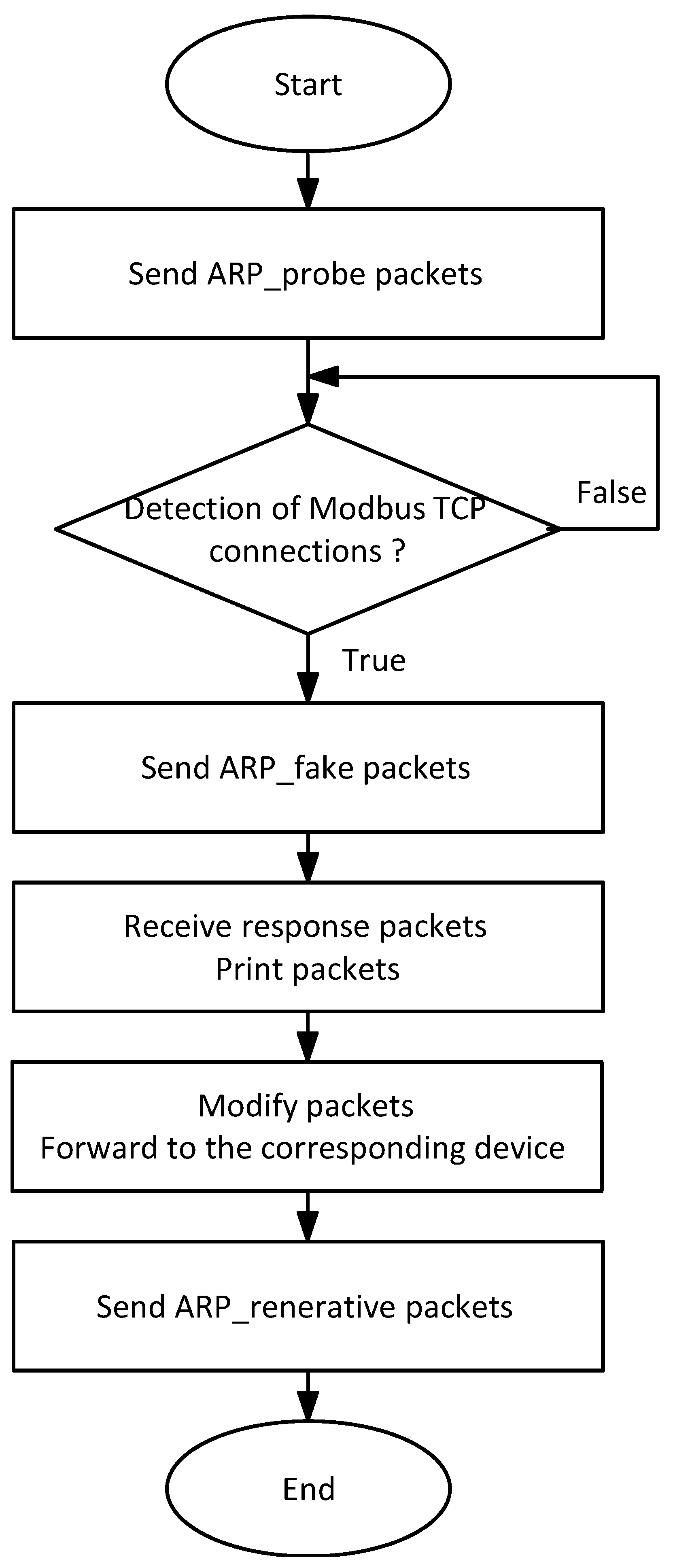
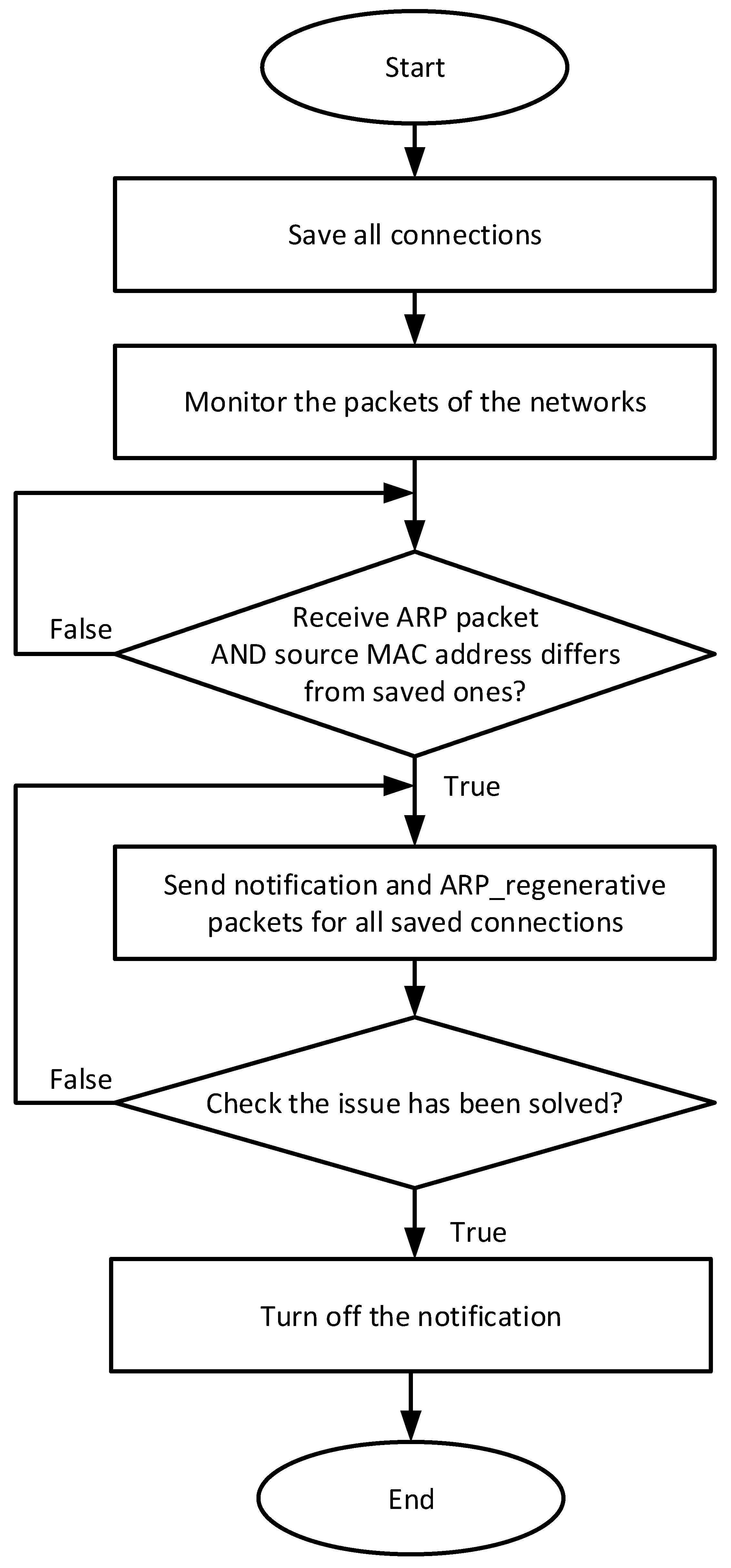
3.2. Software Flowchart
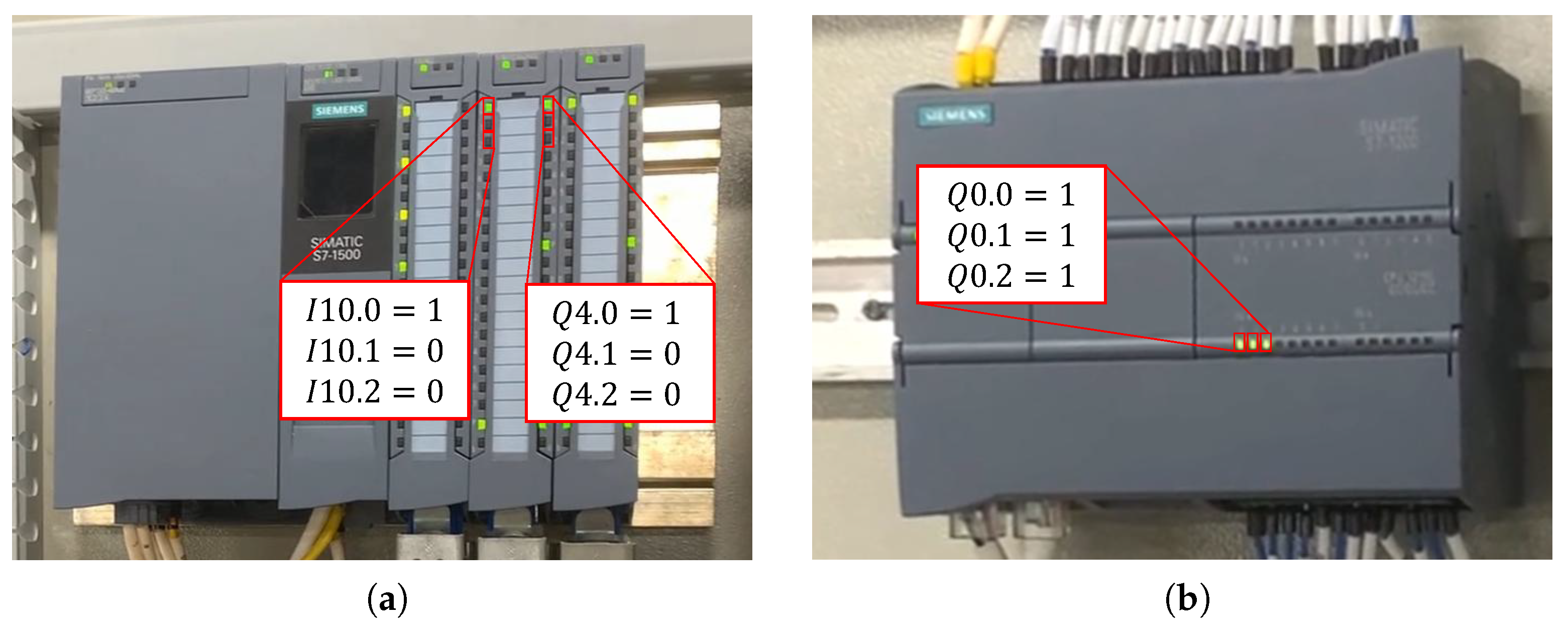
- Query Write: the master PLC transmitted data to the slave PLC, including the starting register address, the number of registers utilized, and the corresponding data for each register.
- Response Write: the slave PLC responded with data to the master PLC, including the starting register address and the number of registers utilized.
- Query Read: the master PLC sent a request to the slave PLC, specifying the starting register address and the number of registers to be retrieved.
- Response Read: data were sent from the slave PLC to the master PLC, including the starting register address, the number of registers used, and the data for each register.
4. Experimental Evaluation
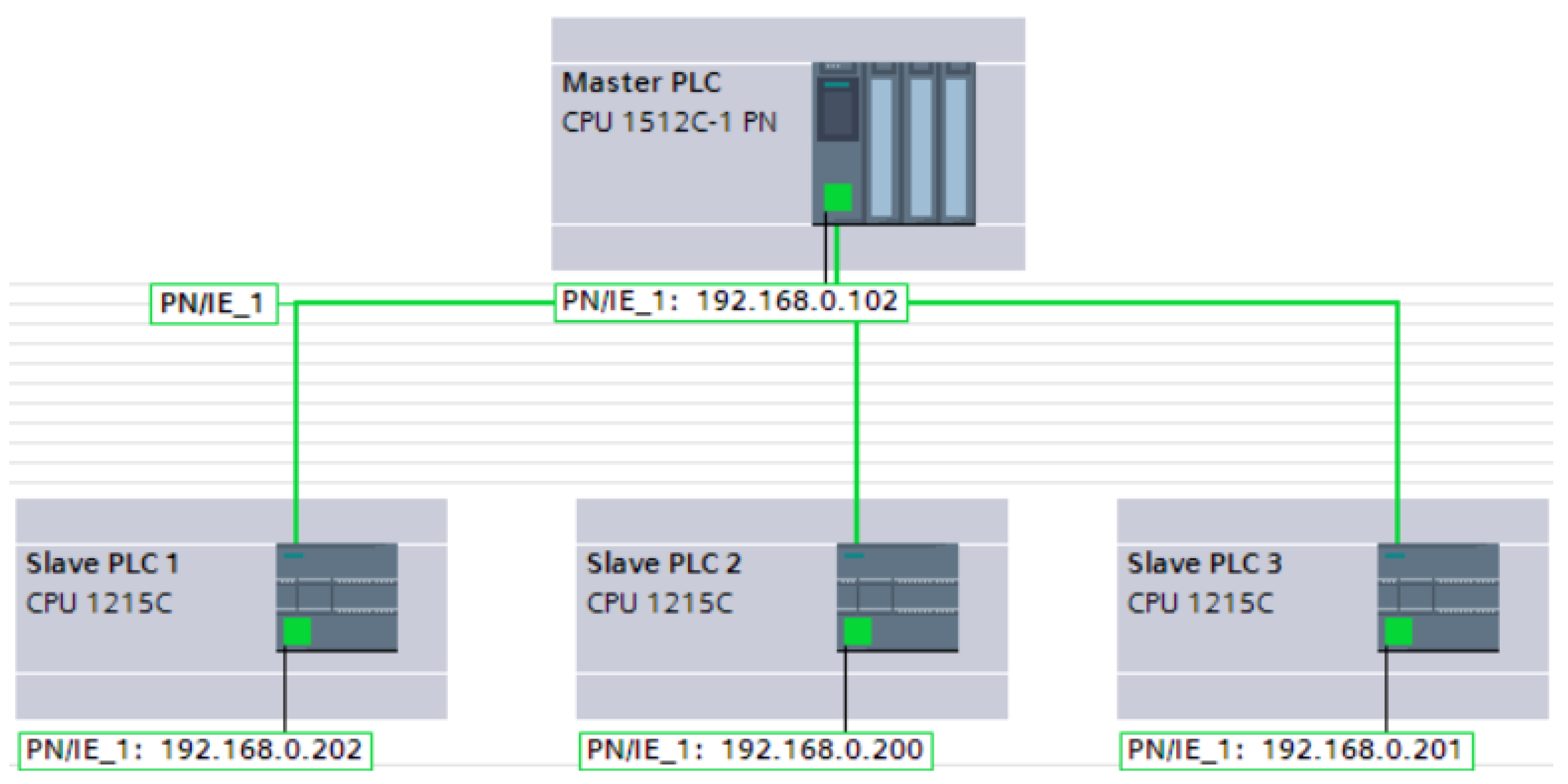
4.1. Experimental Setup
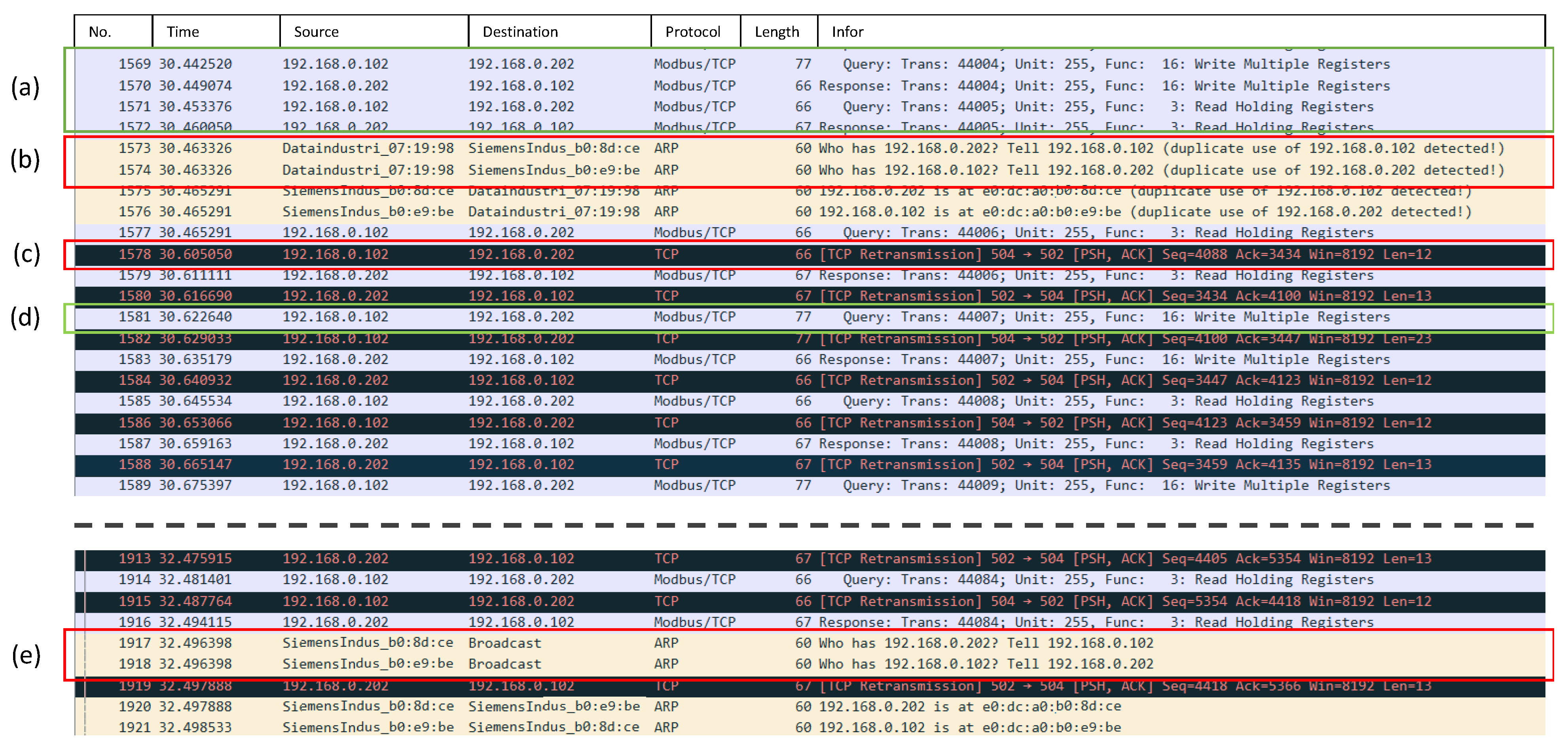
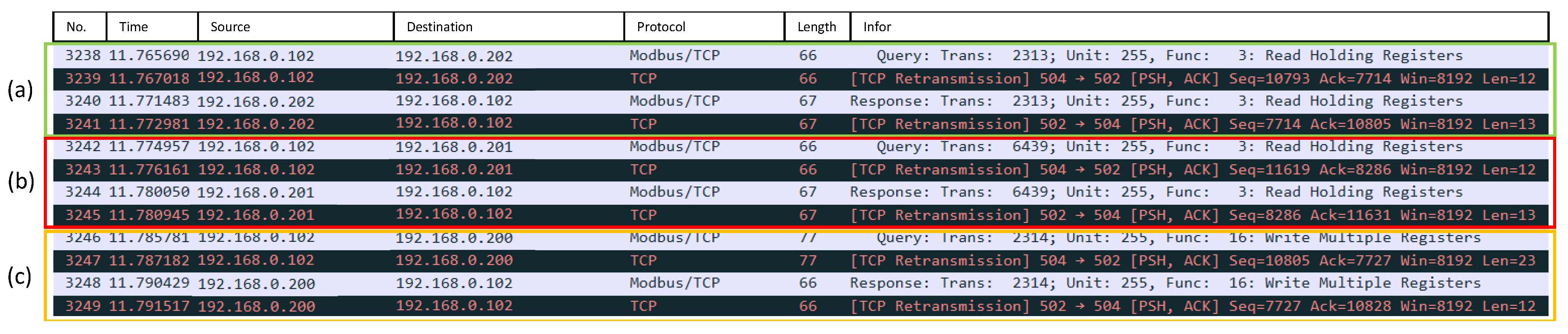
4.2. Experimental Results of the First Scenario
4.3. Experimental Results of the Second Scenario
5. Proposed Security Solution
6. Conclusions and Future Work
- Integration of lightweight encryption mechanisms or secure tunneling methods to provide confidentiality for Modbus communications without compromising real-time requirements.
- Expansion of detection capabilities to cover additional network-layer threats such as TCP session hijacking, replay attacks, or Modbus function code manipulation.
- Field testing in larger-scale, real-world industrial environments to evaluate scalability, robustness, and long-term operational impacts.
Supplementary Materials
| Name | Type | Description |
| 1. Toolkit design | SCHDOC File (.SchDoc) | Altium design of the Toolkit |
| 2. Toolkit firmware | Compressed File (.rar) | Toolkit’s source code used Keil C |
| 3. TIA_Portal_Project | Compressed File (.rar) | PLCs’ source code |
| 4. First Scenario | Video (.mp4) | Video of the first scenario |
| 5. Second Scenario | Video (.mp4) | Video of the second scenario |
| 6. Protective Scenario | Video (.mp4) | Video of the security solution |
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ICS | Industrial Control System |
| LAN | Local Area Network |
| IIoT | Industrial Internet of Things |
| PLC | Programmable Logic Controller |
| ARP | Address Resolution Protocol |
| TCP | Transmission Control Protocol |
| IP | Internet Protocol |
| MAC | Media Access Control |
| MITM | Man-in-the-middle |
| SPI | Serial Peripheral Interface |
| ADU | Application data unit |
| OT | Operational Technology |
| SCADA | Supervisory Control And Data Acquisition |
References
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of Things: A Survey on Enabling Technologies, Protocols, and Applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Balda, J.C.; Mantooth, A.; Blum, R.; Tenti, P. Cybersecurity and Power Electronics: Addressing the Security Vulnerabilities of the Internet of Things. IEEE Power Electron. Mag. 2017, 4, 37–43. [Google Scholar] [CrossRef]
- Thomas, G. Introduction to the modbus protocol. Extension 2008, 9, 1–4. [Google Scholar]
- Baezner, M.; Robin, P. Stuxnet. Report 4, Zurich, 2017-10-18. Version 1. Available online: https://www.research-collection.ethz.ch/handle/20.500.11850/200661 (accessed on 8 February 2025).
- Radziwill, N.M. Countdown to Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon. Qual. Manag. J. 2018, 25, 109–110. [Google Scholar] [CrossRef]
- Lipovsky, R.; Cherepanov, A. Blackenergy Trojan Strikes Again: Attacks Ukrainian Electric Power Industry. 2016. Available online: https://www.welivesecurity.com/2016/01/04/blackenergy-trojan-strikes-again-attacks-ukrainian-electric-power-industry/ (accessed on 16 February 2025).
- Smith, S. Out of Gas: A Deep Dive into the Colonial Pipeline Cyberattack; SAGE Business Cases Originals; SAGE Publications: Thousand Oaks, CA, USA, 2022. [Google Scholar] [CrossRef]
- Kaspersky, I. Threat landscape for industrial automation systems. Stat. H 2021, 1, 2021. [Google Scholar]
- Fovino, I.N.; Carcano, A.; Masera, M.; Trombetta, A. Design and Implementation of a Secure Modbus Protocol. In Proceedings of the Critical Infrastructure Protection III; Palmer, C., Shenoi, S., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 83–96. [Google Scholar] [CrossRef]
- Hayes, G.; El-Khatib, K. Securing modbus transactions using hash-based message authentication codes and stream transmission control protocol. In Proceedings of the 2013 Third International Conference on Communications and Information Technology (ICCIT), Beirut, Lebanon, 19–21 June 2013; pp. 179–184. [Google Scholar] [CrossRef]
- Ferst, M.K.; de Figueiredo, H.F.M.; Denardin, G.; Lopes, J. Implementation of Secure Communication With Modbus and Transport Layer Security protocols. In Proceedings of the 2018 13th IEEE International Conference on Industry Applications (INDUSCON), Sao Paulo, Brazil, 12–14 November 2018; pp. 155–162. [Google Scholar] [CrossRef]
- Xuan, L.; Yongzhong, L. Research and Implementation of Modbus TCP Security Enhancement Protocol. J. Phys. Conf. Ser. 2019, 1213, 052058. [Google Scholar] [CrossRef]
- Martins, T.; Oliveira, S.V.G. Enhanced Modbus/TCP Security Protocol: Authentication and Authorization Functions Supported. Sensors 2022, 22, 8024. [Google Scholar] [CrossRef] [PubMed]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Role-Based Access Control Model in Modbus SCADA Systems. A Centralized Model Approach. Sensors 2019, 19, 4455. [Google Scholar] [CrossRef] [PubMed]
- Katulić, F.; Sumina, D.; Groš, S.; Erceg, I. Protecting Modbus/TCP-Based Industrial Automation and Control Systems Using Message Authentication Codes. IEEE Access 2023, 11, 47007–47023. [Google Scholar] [CrossRef]
- de Brito, I.B.; de Sousa, R.T., Jr. Development of an Open-Source Testbed Based on the Modbus Protocol for Cybersecurity Analysis of Nuclear Power Plants. Appl. Sci. 2022, 12, 7942. [Google Scholar] [CrossRef]
- Alsabbagh, W.; Langendörfer, P. Security of Programmable Logic Controllers and Related Systems: Today and Tomorrow. IEEE Open J. Ind. Electron. Soc. 2023, 4, 659–693. [Google Scholar] [CrossRef]
- Mughaid, A.; Alzu’bi, S.; Alkhatib, A.A.; AlZioud, A.; Ghazo, A.A.; AL-Aiash, I. Simulation-based framework for authenticating SCADA systems and cyber threat security in edge-based autonomous environments. Simul. Model. Pract. Theory 2025, 140, 103078. [Google Scholar] [CrossRef]
- Katulić, F.; Radoš, M. Enhancing Modbus/TCP Security Using a Misuse-Based Intrusion Detection System. In Proceedings of the 2022 International Symposium on Power Electronics, Electrical Drives, Automation and Motion (SPEEDAM), Sorrento, Italy, 22–24 June 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 544–549. [Google Scholar] [CrossRef]
- Tripathy, M.; Niyogi, R.; Kumar, P.S.; Kumbhar, G.B.; Singh, R.; Thakur, V. A Novel Approach for Detection of Cyber Attacks in Microgrid SCADA System. In Proceedings of the 2023 IEEE 3rd International Conference on Sustainable Energy and Future Electric Transportation (SEFET), Bhubaneswar, India, 9–12 August 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Wali, S.; Farrukh, Y.A.; Khan, I.; Hamilton, J.A. Covert penetrations: Analyzing and defending SCADA systems from stealth and Hijacking attacks. Comput. Secur. 2025, 156, 104449. [Google Scholar] [CrossRef]
- Bhukya, R.; Moeed, S.A.; Medavaka, A.; Khadidos, A.O.; Khadidos, A.O.; Selvarajan, S. SPARK and SAD: Leading-edge deep learning frameworks for robust and effective intrusion detection in SCADA systems. Int. J. Crit. Infrastruct. Prot. 2025, 49, 100759. [Google Scholar] [CrossRef]
- Bai, Q.; Jin, B.; Wang, D.; Wang, Y.; Liu, X. Compact Modbus TCP/IP protocol for data acquisition systems based on limited hardware resources. J. Instrum. 2018, 13, T04004. [Google Scholar] [CrossRef]
- Liu, Z.; Liang, T.; Wang, W.; Sun, R.; Li, S. Design and Implementation of a Lightweight Security-Enhanced Scheme for Modbus TCP Protocol. Secur. Commun. Netw. 2023, 2023, 5486566. [Google Scholar] [CrossRef]
- Meghana, J.S.; Subashri, T.; Vimal, K. A survey on ARP cache poisoning and techniques for detection and mitigation. In Proceedings of the 2017 Fourth International Conference on Signal Processing, Communication and Networking (ICSCN), Chennai, India, 16–18 March 2017; pp. 1–6. [Google Scholar] [CrossRef]
- RFC 826; An Ethernet Address Resolution Protocol: Or Converting Network Protocol Addresses to 48.bit Ethernet Address for Transmission on Ethernet Hardware. RFC Editor: Marina del Rey, CA, USA, 1982. [CrossRef]
- Wang, Y.; Feng, X.; Chen, Y.; Zhou, L.; Zhu, Y.; Wu, J. A dual detection method for Siemens inverter motor modbus RTU attack. J. Comput. Commun. 2021, 9, 91–108. [Google Scholar] [CrossRef]
- Morsy, S.M.; Nashat, D. D-ARP: An Efficient Scheme to Detect and Prevent ARP Spoofing. IEEE Access 2022, 10, 49142–49153. [Google Scholar] [CrossRef]
- Bhirud, S.G.; Katkar, V. Light weight approach for IP-ARP spoofing detection and prevention. In Proceedings of the 2011 Second Asian Himalayas International Conference on Internet (AH-ICI), Kathmundu, Nepal, 4–6 November 2011; pp. 1–5. [Google Scholar] [CrossRef]
- Ayub, A.; Yoo, H.; Ahmed, I. Empirical Study of PLC Authentication Protocols in Industrial Control Systems. In Proceedings of the 2021 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 27 May 2021; pp. 383–397. [Google Scholar] [CrossRef]
- Hon, K. Networking and IP addresses. In Technology and Security for Lawyers and Other Professionals; Edward Elgar Publishing: Cheltenham, UK, 2024; pp. 266–287. [Google Scholar] [CrossRef]
- Tampering, P.F. Modbus Protocol Based on the Characteristics. In Proceedings of the Advances in Intelligent Information Hiding and Multimedia Signal Processing: Proceedings of the 15th International Conference on IIH-MSP in Conjunction with the 12th International Conference on FITAT, Jilin, China, 18–20 July 2019; Volume 1, pp. 335–344. [Google Scholar] [CrossRef]



| Parameters | First Scenario | Second Scenario | ||
|---|---|---|---|---|
| Attacking | Normal Working | Attacking | Normal Working | |
| Time Interval | 6 ms | 2 ms | 9 ms | 5 ms |
| Toolkit processing time | 2 ms | - | 2 ms | - |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Published by MDPI on behalf of the International Institute of Knowledge Innovation and Invention. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Dao, Q.-T.; Nguyen, L.-T.; Ha, T.-K.; Nguyen, V.-H.; Nguyen, T.-A. Investigation of Secure Communication of Modbus TCP/IP Protocol: Siemens S7 PLC Series Case Study. Appl. Syst. Innov. 2025, 8, 65. https://doi.org/10.3390/asi8030065
Dao Q-T, Nguyen L-T, Ha T-K, Nguyen V-H, Nguyen T-A. Investigation of Secure Communication of Modbus TCP/IP Protocol: Siemens S7 PLC Series Case Study. Applied System Innovation. 2025; 8(3):65. https://doi.org/10.3390/asi8030065
Chicago/Turabian StyleDao, Quy-Thinh, Le-Trung Nguyen, Trung-Kien Ha, Viet-Hoang Nguyen, and Tuan-Anh Nguyen. 2025. "Investigation of Secure Communication of Modbus TCP/IP Protocol: Siemens S7 PLC Series Case Study" Applied System Innovation 8, no. 3: 65. https://doi.org/10.3390/asi8030065
APA StyleDao, Q.-T., Nguyen, L.-T., Ha, T.-K., Nguyen, V.-H., & Nguyen, T.-A. (2025). Investigation of Secure Communication of Modbus TCP/IP Protocol: Siemens S7 PLC Series Case Study. Applied System Innovation, 8(3), 65. https://doi.org/10.3390/asi8030065









