Cyber Insurance for Energy Economic Risks
Highlights
- Developed a two-stage hierarchical planning model incorporating cyber insurance to bolster the resilience of ICT-integrated multi-energy systems against cyberattacks. This model effectively reduces operation costs by 29.0% and mitigates load shedding by 0.68 MWh, as demonstrated in simulation studies on a 33-20 distribution multi-energy grid system.
- Utilized a distributionally robust optimization approach, leveraging conditional value at risk (CVaR), to handle the emergent and uncertain nature of cyberattacks, making the problem tractable through sample average approximation techniques.
- The inclusion of cyber insurance in energy management strategies offers a proactive and financially viable approach to managing cyber risks, ensuring the continuity and resilience of smart city operations. This approach facilitates better preparedness and response to potential cyber incidents.
- The proposed model provides a valuable framework for city managers, aiding in making informed decisions regarding the procurement of cyber insurance and the implementation of real-time defense strategies. This not only enhances the economic performance and operational stability of smart city energy systems but also promotes a collaborative approach between insurers and energy system operators, setting a precedent for future research and development in the field of cyber risk management for ICT-integrated multi-energy systems.
Abstract
1. Introduction
1.1. Related Work
1.2. The Proposed Approach and Novelties
- ✓
- In comparison to prior studies in the realm of cyber insurance management for electric vehicle charging stations or local energy systems, the present work encompasses a more comprehensive scope; it takes a full array of physical constraints and system functionalities into account, including optimal power flow, generator dispatch, and energy-balancing conditions. The proposed cyber insurance framework does not merely represent a risk-transfer solution; rather, it represents a cooperative risk-management strategy for energy system operators.
- ✓
- Cyberattacks in power systems are known to trigger a cascade of effects that propagate through interconnected subsystems. Previous work in the realm of MEGs has not considered the implications of such attacks on cyber insurance management. To address this, the present work leverages optimal coordination of system interdependencies in order to mitigate attack consequences and minimize losses.
- ✓
- Given the lack of historical data and the unpredictable nature of cyberattacks, a novel two-stage DRO method is adopted to estimate the potential impact of such attacks and formulate the total cost of the TCIP model. Unlike traditional SMP methods, the DRO approach seeks an optimal solution under the worst-case uncertainty distribution and provides robust mitigation against cyberattacks.
2. Modeling of Cyber Intrusions in Energy Systems
3. The Proposed Cyber Insurance Planning Model
3.1. Objective Function
3.2. Constraints
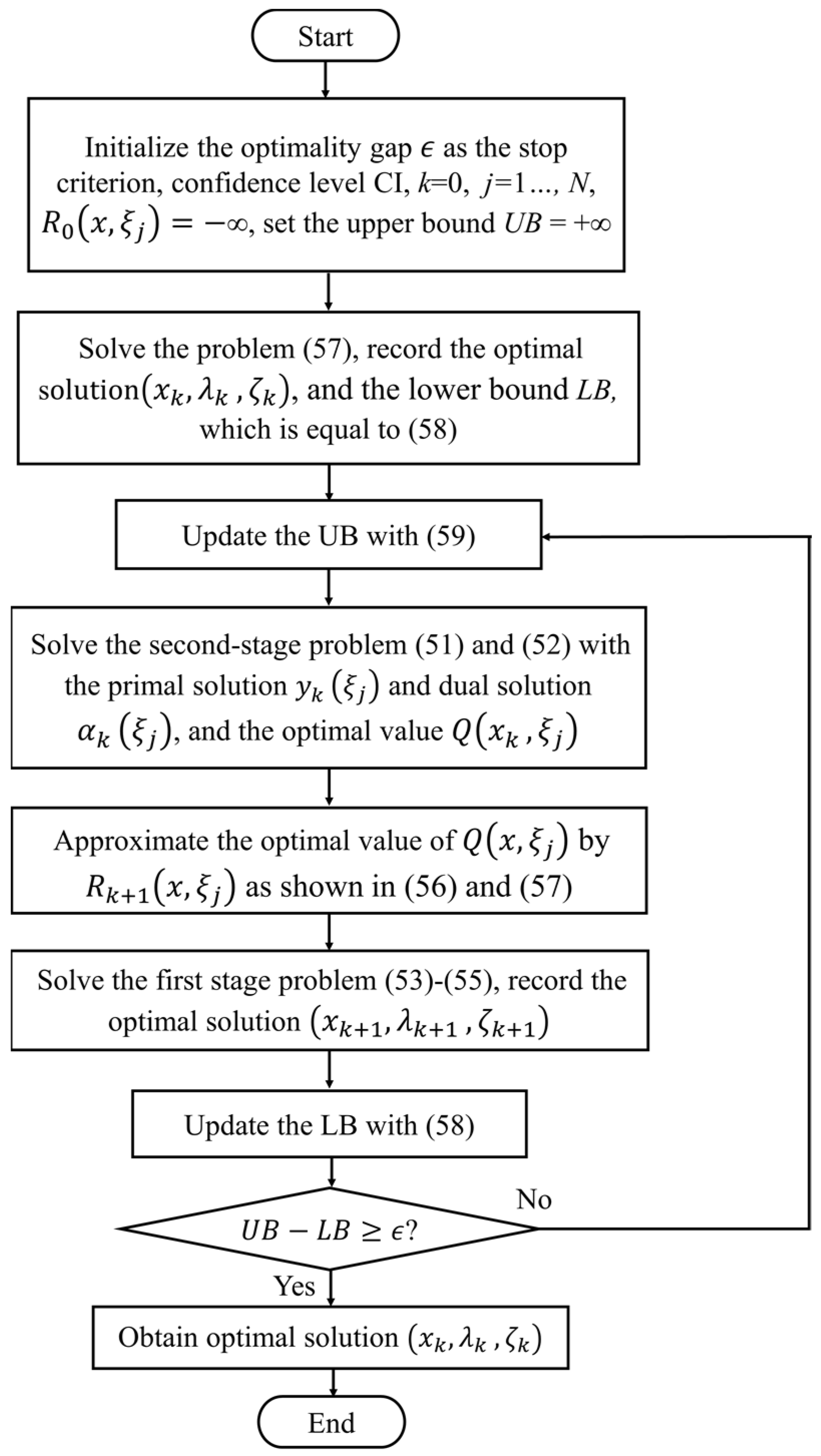
4. Distributionally Robust Decision Making
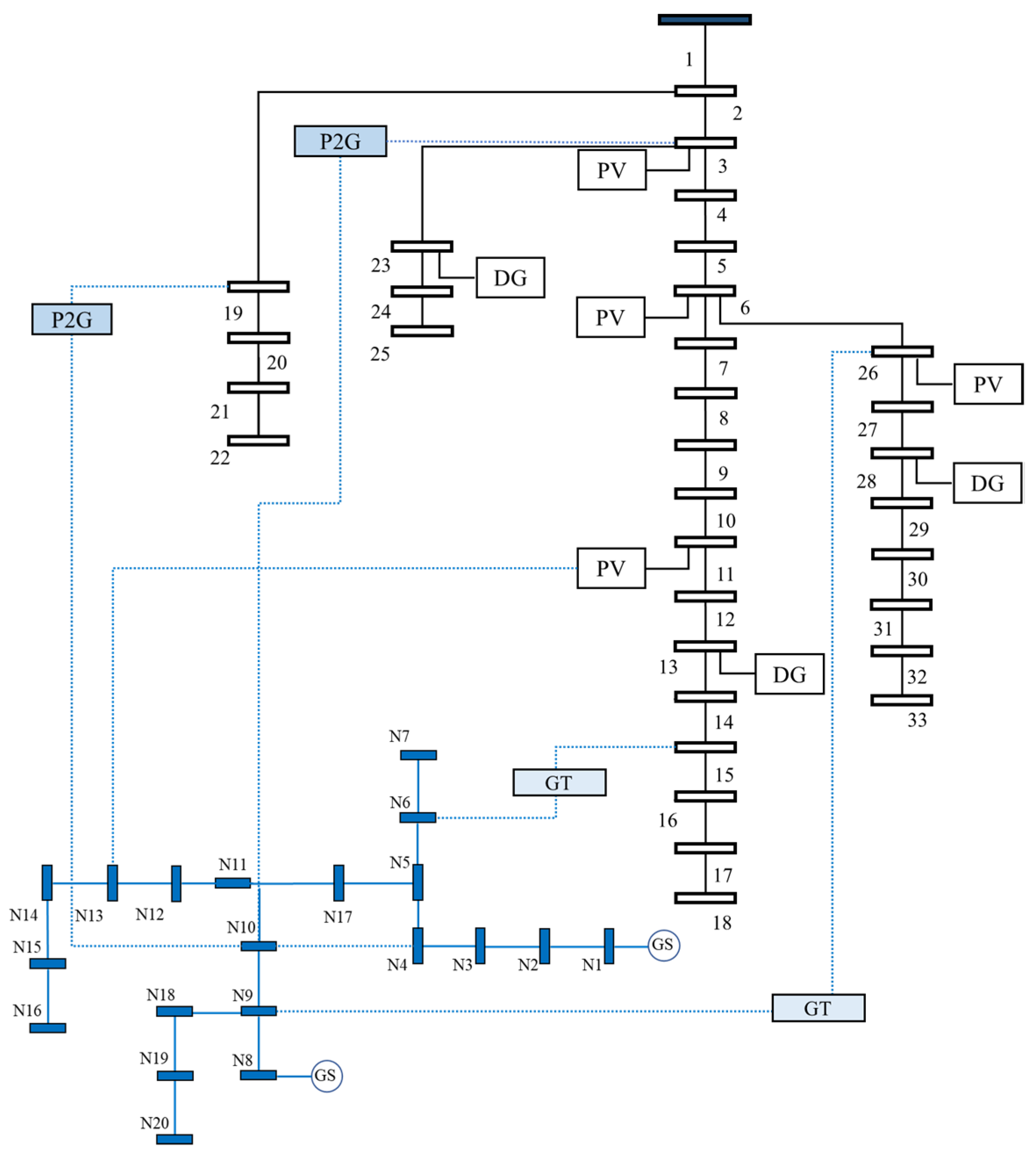
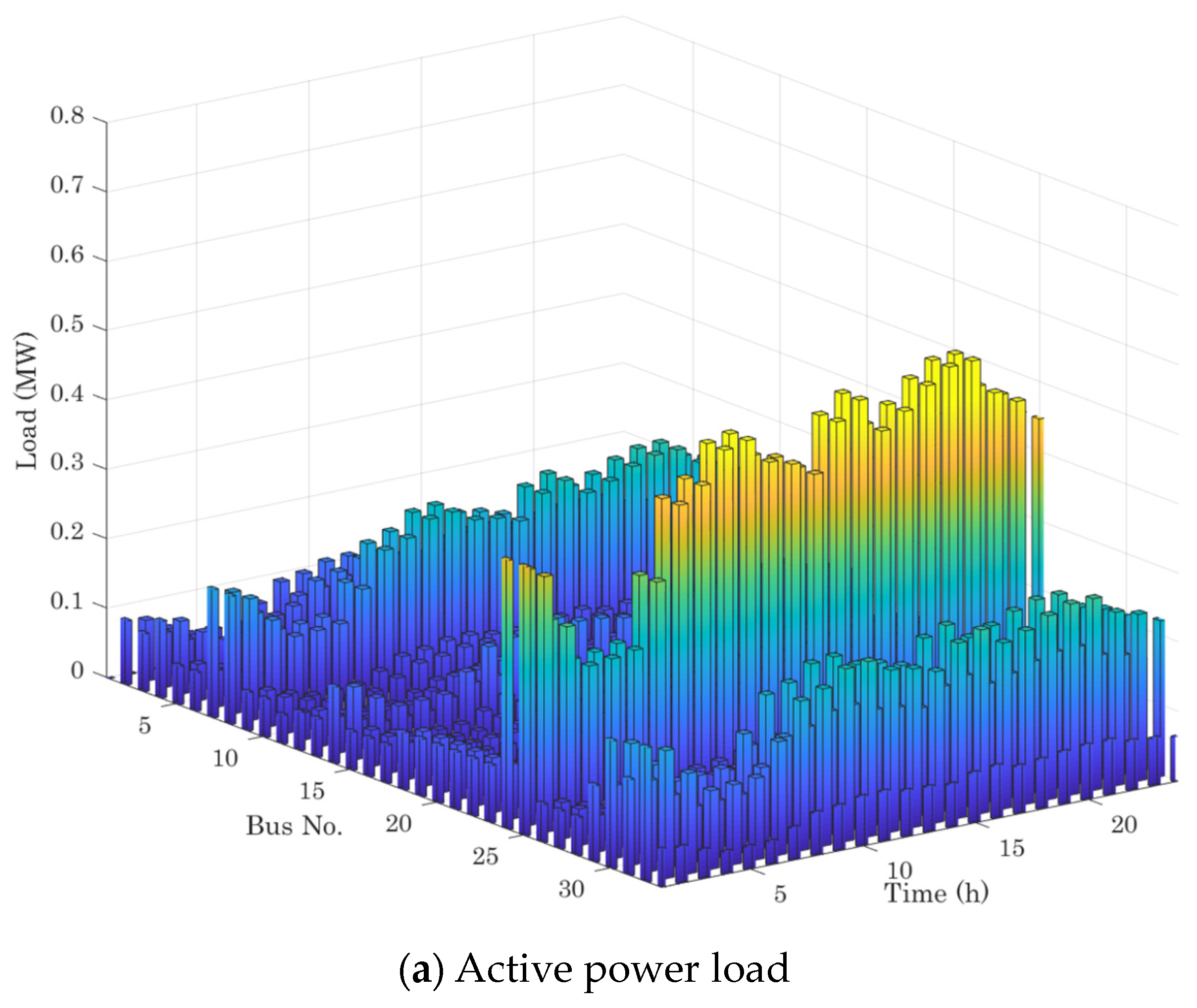
5. Case Studies
- Case I: Baseline case.
- Case II: Limiting the insurance purchase amount by 20%.
- Case III: Limiting the insurance purchase amount by 50%.
- Case IV: Increasing the insurance price by 25%.
- Case V: Increasing the insurance price by 50%.
- Case VI: Omitting the renewable generation uncertainty.
6. Comparative Analysis of Cybersecurity Methodologies
7. Concluding Remarks
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ICT | Information and Communication Technologies |
| FDI | false data injection |
| SE | state estimation |
| EV | electric vehicle |
| DC | direct current |
| DRO | Distributionally Robust Optimization |
| SMP | semi-Markov process |
| CVaR | conditional value at risk |
| SAA | sample average approximation |
| MEGs | multi-energy grids |
| TCIP | two-stage hierarchical cyber insurance planning |
| DG | distributed generator |
| SDDP | stochastic dual dynamic programming |
| QoS | quality of service |
| AI | artificial intelligence |
| SCADA | supervisory control and data acquisition |
| IoT | Internet of Things |
| NIST | National Institute of Standards and Technology |
| ISO | International Organization for Standardization |
| NERC | North American Electric Reliability Corporation |
| CPS | cyber–physical systems |
| P2G | power to gas |
| CI | confidence interval |
References
- Sun, C.-C.; Hahn, A.; Liu, C.-C. Cyber security of a power grid: State-of-the-art. Int. J. Electr. Power Energy Syst. 2018, 99, 45–56. [Google Scholar] [CrossRef]
- Boakye-Boateng, K.; Ghorbani, A.A.; Lashkari, A.H. Implementation of a Trust-Based Framework for Substation Defense in the Smart Grid. Smart Cities 2024, 7, 99–140. [Google Scholar] [CrossRef]
- Zhao, P.; Cao, Z.; Zeng, D.D.; Gu, C.; Wang, Z.; Xiang, Y.; Qadrdan, M.; Chen, X.; Yan, X.; Li, S. Cyber-Resilient Multi-Energy Management for Complex Systems. IEEE Trans. Ind. Inform. 2022, 18, 2144–2159. [Google Scholar] [CrossRef]
- Zhao, P.; Li, S.; Hu, P.J.H.; Cao, Z.; Gu, C.; Xie, D.; Zeng, D.D. Coordinated Cyber Security Enhancement for Grid-Transportation Systems With Social Engagement. IEEE Trans. Emerg. Top. Comput. Intell. 2022, 1–15. [Google Scholar] [CrossRef]
- Alasali, F.; Itradat, A.; Abu Ghalyon, S.; Abudayyeh, M.; El-Naily, N.; Hayajneh, A.M.; AlMajali, A. Smart Grid Resilience for Grid-Connected PV and Protection Systems under Cyber Threats. Smart Cities 2024, 7, 51–77. [Google Scholar] [CrossRef]
- Bitirgen, K.; Filik, Ü.B. A hybrid deep learning model for discrimination of physical disturbance and cyber-attack detection in smart grid. Int. J. Crit. Infrastruct. Prot. 2023, 40, 100582. [Google Scholar] [CrossRef]
- Tian, J.; Wang, B.; Li, J.; Konstantinou, C. Datadriven false data injection attacks against cyber-physical power systems. Comput. Secur. 2022, 121, 102836. [Google Scholar] [CrossRef]
- Li, B.; Xiao, G.; Lu, R.; Deng, R.; Bao, H. On Feasibility and Limitations of Detecting False Data Injection Attacks on Power Grid State Estimation Using D-FACTS Devices. IEEE Trans. Ind. Inform. 2020, 16, 854–864. [Google Scholar] [CrossRef]
- Yao, H.; Xiang, Y.; Liu, J. Virtual Prosumers’ P2P Transaction Based Distribution Network Expansion Planning. IEEE Trans. Power Syst. 2023, 39, 1044–1057. [Google Scholar] [CrossRef]
- Vincent, E.; Korki, M.; Seyedmahmoudian, M.; Stojcevski, A.; Mekhilef, S. Detection of false data injection attacks in cyber–physical systems using graph convolutional network. Electr. Power Syst. Res. 2023, 217, 109118. [Google Scholar] [CrossRef]
- Yang, J.; Xiang, Y. Deep Transfer Learning based Surrogate Modeling for Optimal Investment Decision of Distribution Networks. IEEE Trans. Power Syst. 2023, 39, 2506–2516. [Google Scholar] [CrossRef]
- Xiang, Y.; Lu, Y.; Liu, J. Deep reinforcement learning based topology-aware voltage regulation of distribution networks with distributed energy storage. Appl. Energy 2023, 332, 120510. [Google Scholar] [CrossRef]
- Panagiotis, F.; Taxiarxchis, K.; Georgios, K.; Maglaras, L.; Ferrag, M.A. Intrusion Detection in Critical Infrastructures: A Literature Review. Smart Cities 2021, 4, 1146–1157. [Google Scholar] [CrossRef]
- Su, Q.; Wang, H.; Sun, C.; Li, B.; Li, J. Cyber-attacks against cyber-physical power systems security: State estimation, attacks reconstruction and defense strategy. Appl. Math. Comput. 2022, 413, 126639. [Google Scholar] [CrossRef]
- Aoufi, S.; Derhab, A.; Guerroumi, M. Survey of false data injection in smart power grid: Attacks, countermeasures and challenges. J. Inf. Secur. Appl. 2020, 54, 102518. [Google Scholar] [CrossRef]
- Gjesvik, L.; Szulecki, K. Interpreting cyber-energy-security events: Experts, social imaginaries, and policy discourses around the 2016 Ukraine blackout. Eur. Secur. 2022, 32, 104–124. [Google Scholar] [CrossRef]
- Pawlak, P. Protecting and defending Europe’s cyberspace. Hacks Leaks Disrupt. Russ. Cyber Strateg. ISS Chaillot Pap. 2018, 148, 103–115. [Google Scholar]
- Sun, Y.; Chai, J.; Li, W.; Ren, Y. Research on the Evaluation Index System and Methodology for the Construction of Ecological Civilization Model Cities—Yancheng City as an Example. Open J. Bus. Manag. 2022, 10, 1549–1568. [Google Scholar] [CrossRef]
- Wei, F.; Wan, Z.; He, H. Cyber-attack recovery strategy for smart grid based on deep reinforcement learning. IEEE Trans. Smart Grid 2019, 11, 2476–2486. [Google Scholar] [CrossRef]
- Mustafa, A.; Poudel, B.; Bidram, A.; Modares, H. Detection and Mitigation of Data Manipulation Attacks in AC Microgrids. IEEE Trans. Smart Grid 2020, 11, 2588–2603. [Google Scholar] [CrossRef]
- Kabir, M.E.; Ghafouri, M.; Moussa, B.; Assi, C. A Two-Stage Protection Method for Detection and Mitigation of Coordinated EVSE Switching Attacks. IEEE Trans. Smart Grid 2021, 12, 4377–4388. [Google Scholar] [CrossRef]
- Zhang, J.; Sahoo, S.; Peng, J.C.H.; Blaabjerg, F. Mitigating Concurrent False Data Injection Attacks in Cooperative DC Microgrids. IEEE Trans. Power Electron. 2021, 36, 9637–9647. [Google Scholar] [CrossRef]
- Lakshminarayana, S.; Karachiwala, J.S.; Teng, T.Z.; Tan, R.; Yau, D.K.Y. Performance and Resilience of Cyber-Physical Control Systems With Reactive Attack Mitigation. IEEE Trans. Smart Grid 2019, 10, 6640–6654. [Google Scholar] [CrossRef]
- Zhang, Z.; Huang, S.; Chen, Y.; Li, B.; Mei, S. Diversified Software Deployment for Long-Term Risk Mitigation in Cyber-Physical Power Systems. IEEE Trans. Power Syst. 2022, 37, 377–387. [Google Scholar] [CrossRef]
- Liu, C.; Zhou, M.; Wu, J.; Long, C.; Kundur, D. Financially Motivated FDI on SCED in Real-Time Electricity Markets: Attacks and Mitigation. IEEE Trans. Smart Grid 2019, 10, 1949–1959. [Google Scholar] [CrossRef]
- Mokarim, A.; Gaggero, G.B.; Marchese, M. Evaluation of the Impact of Cyber-Attacks Against Electric Vehicle Charging Stations in a Low Voltage Distribution Grid. In Proceedings of the 2023 IEEE International Conference on Communications, Control, and Computing Technologies for Smart Grids (SmartGridComm), Glasgow, UK, 31 October–3 November 2023; pp. 1–7. [Google Scholar] [CrossRef]
- Marotta, A.; Martinelli, F.; Nanni, S.; Orlando, A.; Yautsiukhin, A. Cyber-insurance survey. Comput. Sci. Rev. 2017, 24, 35–61. [Google Scholar] [CrossRef]
- Fuhrman-Wenman, T. Cyber Insurance in International Mergers and Acquisitions. Denver Law Rev. Forum 2016, 93, 361–376. [Google Scholar]
- Mott, G.; Turner, S.; Nurse, J.R.C.; MacColl, J.; Sullivan, J.; Cartwright, A.; Cartwright, E. Between a rock and a hard(ening) place: Cyber insurance in the ransomware era. Comput. Secur. 2023, 128, 103162. [Google Scholar] [CrossRef]
- Liu, Z.; Wei, W.; Wang, L.; Ten, C.W.; Rho, Y. An Actuarial Framework for Power System Reliability Considering Cybersecurity Threats. IEEE Trans. Power Syst. 2021, 36, 851–864. [Google Scholar] [CrossRef]
- Niyato, D.; Hoang, D.T.; Wang, P.; Han, Z. Cyber Insurance for Plug-In Electric Vehicle Charging in Vehicle-to-Grid Systems. IEEE Netw. 2017, 31, 38–46. [Google Scholar] [CrossRef]
- Lau, P.; Wang, L.; Liu, Z.; Wei, W.; Ten, C.W. A Coalitional Cyber-Insurance Design Considering Power System Reliability and Cyber Vulnerability. IEEE Trans. Power Syst. 2021, 36, 5512–5524. [Google Scholar] [CrossRef]
- Acharya, S.; Mieth, R.; Konstantinou, C.; Karri, R.; Dvorkin, Y. Cyber Insurance Against Cyberattacks on Electric Vehicle Charging Stations. IEEE Trans. Smart Grid 2021, 13, 1529–1541. [Google Scholar] [CrossRef]
- Mazzoccoli, A.; Naldi, M. Robustness of Optimal Investment Decisions in Mixed Insurance/Investment Cyber Risk Management. Risk Anal. 2020, 40, 550–564. [Google Scholar] [CrossRef]
- Pal, R.; Golubchik, L.; Psounis, K.; Hui, P. Will cyber-insurance improve network security? A market analysis. In Proceedings of the IEEE INFOCOM 2014-IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 235–243. [Google Scholar] [CrossRef]
- Wang, S.S. Integrated framework for information security investment and cyber insurance. Pac. Basin Financ. J. 2019, 57, 101173. [Google Scholar] [CrossRef]
- Martinelli, F.; Orlando, A.; Uuganbayar, G.; Yautsiukhin, A. Preventing the Drop in Security Investments for Non-competitive Cyber-Insurance Market. In Risks and Security of Internet and Systems; Cuppens, N., Cuppens, F., Lanet, J.L., Legay, A., Garcia-Alfaro, J., Eds.; Springer: Cham, Switzerland, 2018; pp. 159–174. [Google Scholar]
- Pal, R.; Golubchik, L. Analyzing Self-Defense Investments in Internet Security under Cyber-Insurance Coverage. In Proceedings of the 2010 IEEE 30th International Conference on Distributed Computing Systems, Genoa, Italy, 21–25 June 2010; pp. 339–347. [Google Scholar] [CrossRef]
- Lu, X.; Chan, K.W.; Xia, S.; Shahidehpour, M.; Ng, W.H. An Operation Model for Distribution Companies Using the Flexibility of Electric Vehicle Aggregators. IEEE Trans. Smart Grid 2021, 12, 1507–1518. [Google Scholar] [CrossRef]
- Zare, A.; Chung, C.Y.; Zhan, J.; Faried, S.O. A Distributionally Robust Chance-Constrained MILP Model for Multistage Distribution System Planning With Uncertain Renewables and Loads. IEEE Trans. Power Syst. 2018, 33, 5248–5262. [Google Scholar] [CrossRef]
- Ning, X.; Jiang, J. Design, Analysis and Implementation of a Security Assessment/Enhancement Platform for Cyber-Physical Systems. IEEE Trans. Ind. Inform. 2022, 18, 1154–1164. [Google Scholar] [CrossRef]
- Yang, J.; Zhou, C.; Yang, S.; Xu, H.; Hu, B. Anomaly Detection Based on Zone Partition for Security Protection of Industrial Cyber-Physical Systems. IEEE Trans. Ind. Electron. 2018, 65, 4257–4267. [Google Scholar] [CrossRef]
- Tsohou, A.; Diamantopoulou, V.; Gritzalis, S.; Lambrinoudakis, C. Cyber insurance: State of the art, trends and future directions. Int. J. Inf. Secur. 2023, 22, 737–748. [Google Scholar] [CrossRef]
- Xie, H.; Sun, X.; Fu, W.; Chen, C.; Bie, Z. Risk management for integrated power and natural gas systems against extreme weather: A coalitional insurance contract approach. Energy 2023, 263, 125750. [Google Scholar] [CrossRef]
- Lu, K.D.; Zeng, G.Q.; Luo, X.; Weng, J.; Luo, W.; Wu, Y. Evolutionary Deep Belief Network for Cyber-Attack Detection in Industrial Automation and Control System. IEEE Trans. Ind. Inform. 2021, 17, 7618–7627. [Google Scholar] [CrossRef]
- Jiang, W.; Song, Z.; Zhan, J.; Liu, D.; Wan, J. Layerwise Security Protection for Deep Neural Networks in Industrial Cyber Physical Systems. IEEE Trans. Ind. Inform. 2022, 18, 8797–8806. [Google Scholar] [CrossRef]
- Jorjani, M.; Seifi, H.; Varjani, A.Y. A Graph Theory-Based Approach to Detect False Data Injection Attacks in Power System AC State Estimation. IEEE Trans. Ind. Inform. 2021, 17, 2465–2475. [Google Scholar] [CrossRef]
- Wang, G.; Yin, S.; Kaynak, O. An LWPR-Based Data-Driven Fault Detection Approach for Nonlinear Process Monitoring. IEEE Trans. Ind. Inform. 2014, 10, 2016–2023. [Google Scholar] [CrossRef]
- Zhang, Q.; Ma, Z.; Zhu, Y.; Wang, Z. A Two-Level Simulation-Assisted Sequential Distribution System Restoration Model With Frequency Dynamics Constraints. IEEE Trans. Smart Grid 2021, 12, 3835–3846. [Google Scholar] [CrossRef]
- García-Marín, S.; González-Vanegas, W.; Murillo-Sánchez, C. MPNG: A MATPOWER-Based Tool for Optimal Power and Natural Gas Flow Analyses. IEEE Trans. Power Syst. 2022, 39, 5455–5464. [Google Scholar] [CrossRef]
- Golodnikov, A.; Kuzmenko, V.; Uryasev, S. CVaR regression based on the relation between CVaR and mixed-quantile quadrangles. J. Risk Financ. Manag. 2019, 12, 107. [Google Scholar] [CrossRef]
- Lan, G. Correction to: Complexity of stochastic dual dynamic programming. Math. Program. 2022, 194, 1187–1189. [Google Scholar] [CrossRef]
- Bonfiglio, A.; Bruno, S.; Martino, M.; Minetti, M.; Procopio, R.; Velini, A. Renewable Energy Communities Virtual Islanding: A Novel Service for Smart Distribution Networks. In Proceedings of the 2024 IEEE/IAS 60th Industrial and Commercial Power Systems Technical Conference (I&CPS), Las Vegas, NV, USA, 19–23 May 2024; pp. 1–8. [Google Scholar] [CrossRef]
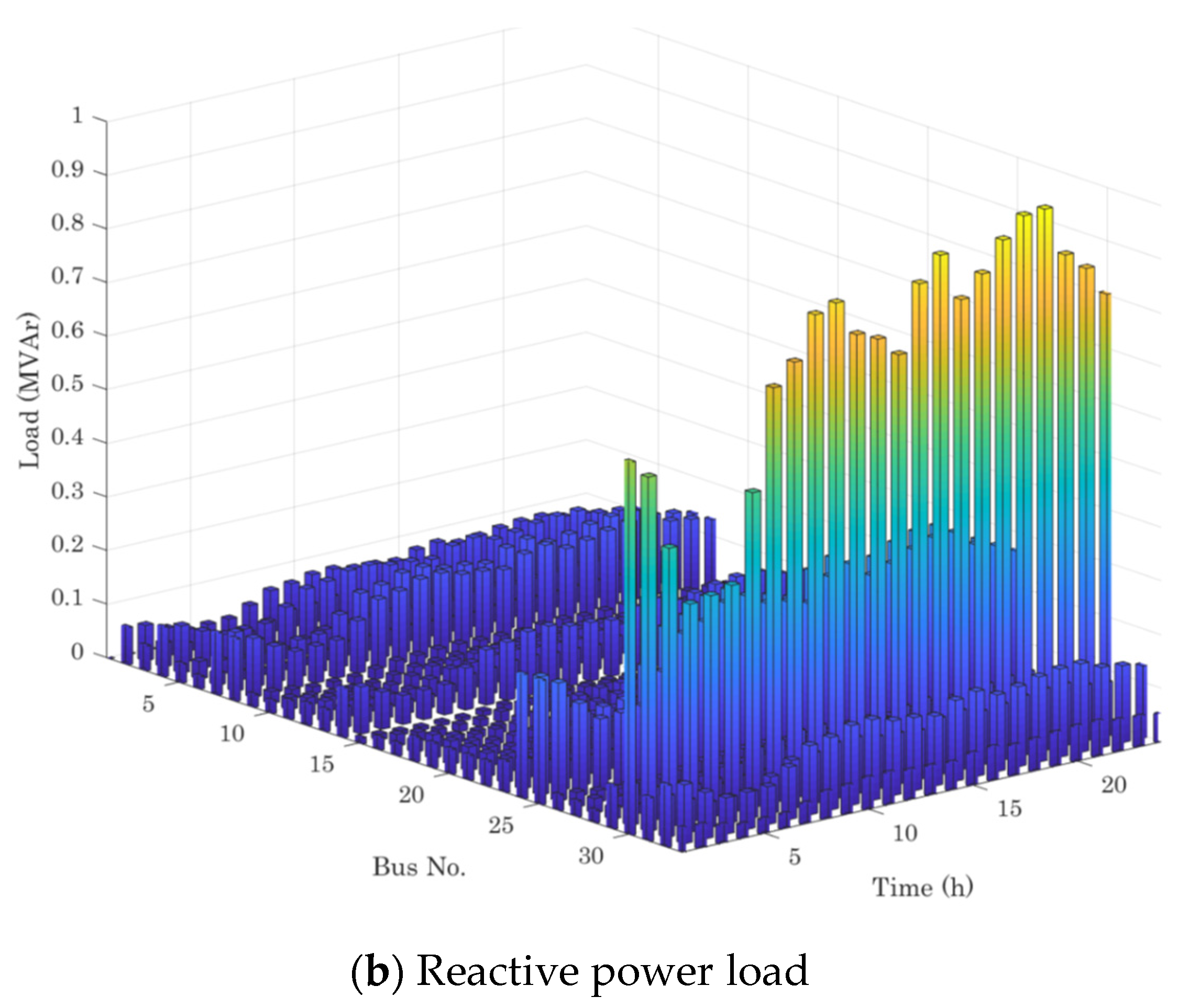
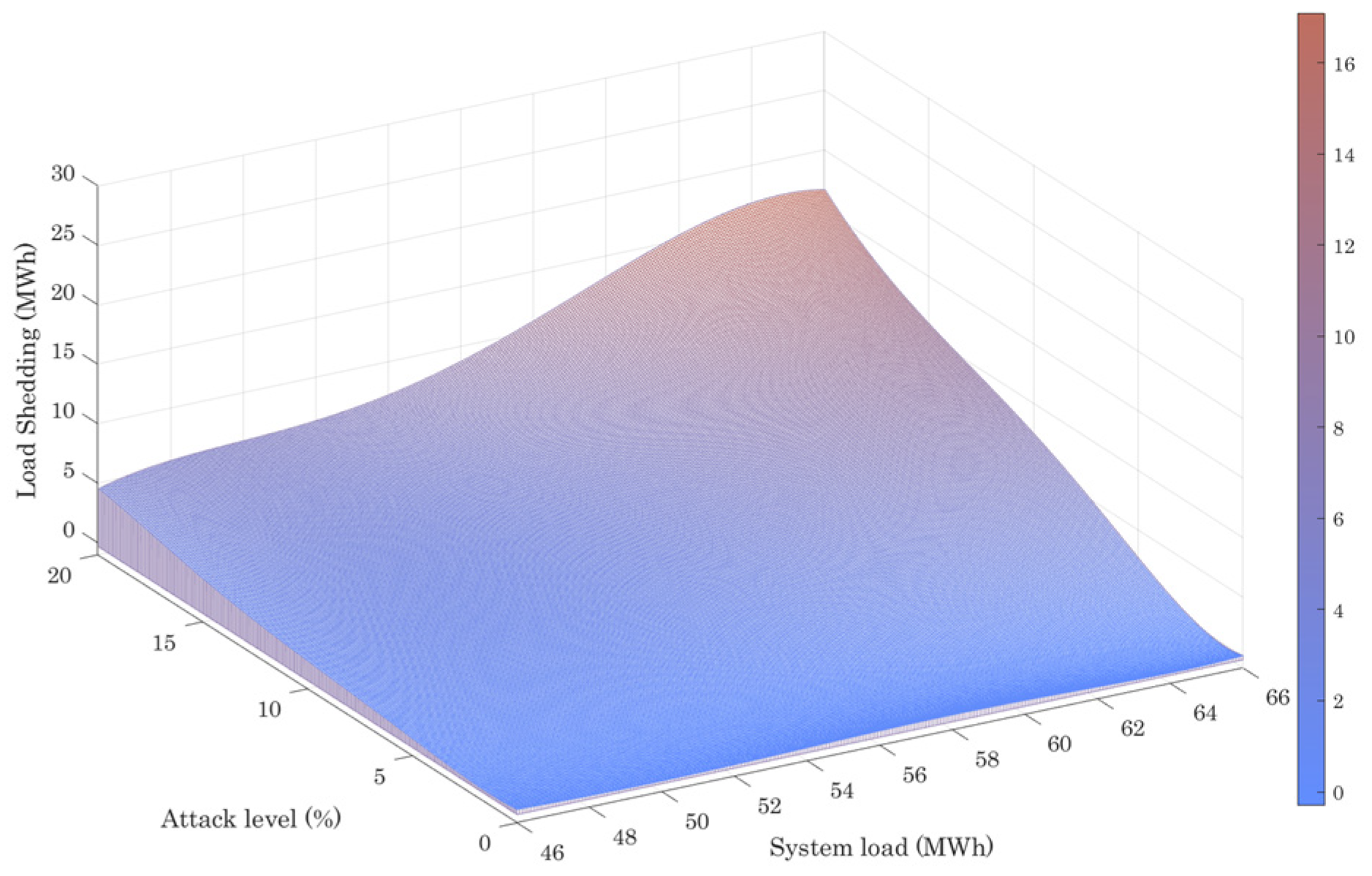

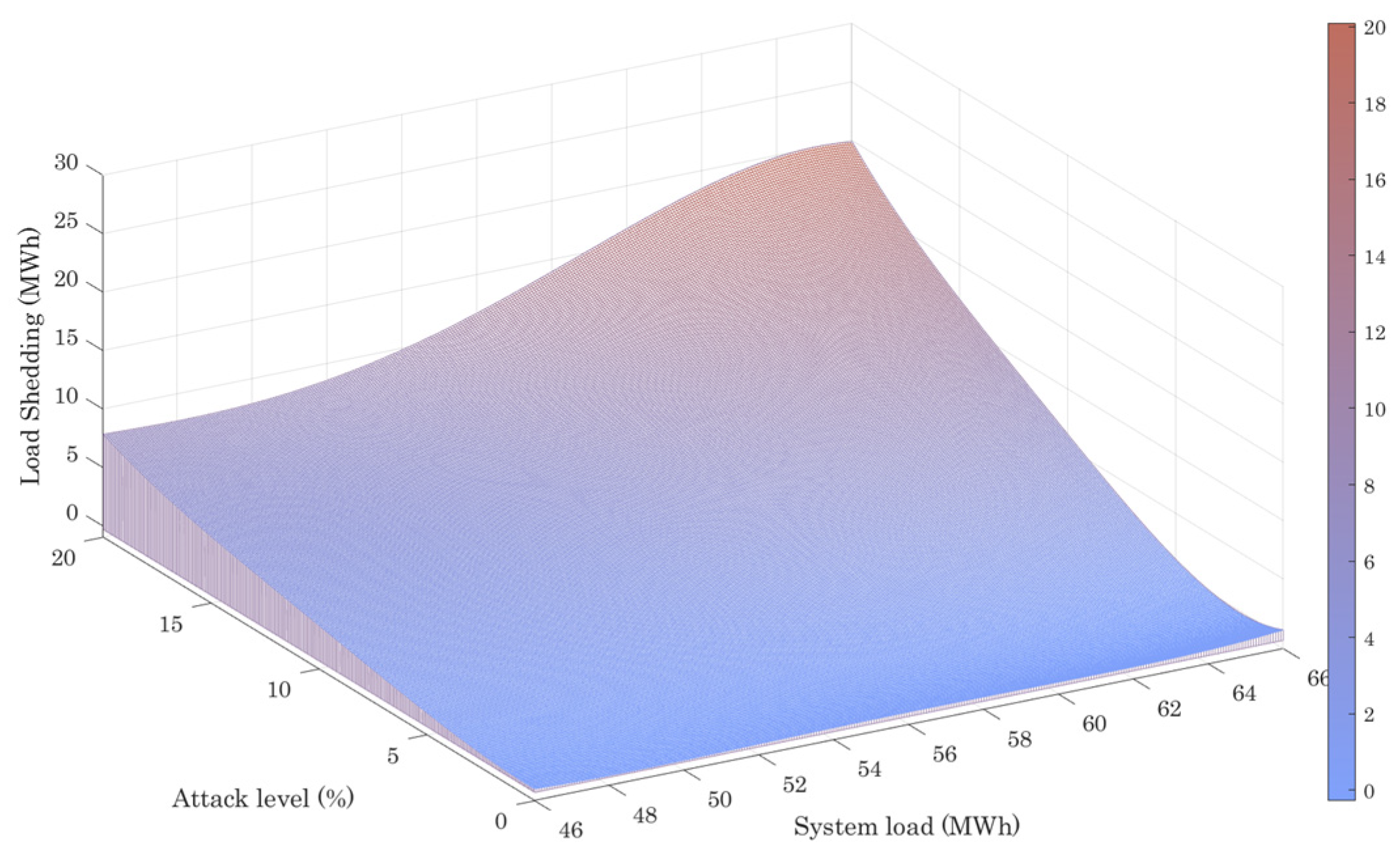

| Node No. | (kcf/h) | (kcf/h) | |
|---|---|---|---|
| N1 | 35.31 | 0 | 22 |
| N8 | 70.63 | 0 | 20 |
| Node No. | (MW) | (MW) | |
|---|---|---|---|
| 13 | 1.2 | 0.3 | 7100 |
| 23 | 1.2 | 0.3 | 10,500 |
| 28 | 1.0 | 0.1 | 10,500 |
| Economic Result (USD) | Case I | Case II | Case III | Case IV | Case V | Case VI |
|---|---|---|---|---|---|---|
| First stage | 305,288 | 364,120 | 392,158 | 321,804 | 336,085 | 299,594 |
| Expected second stage | 41,762 | 52,819 | 55,402 | 44,187 | 46,820 | 36,142 |
| Total | 347,050 | 416,939 | 447,560 | 365,991 | 382,905 | 335,736 |
| Method | Cost Reduction (%) | Risk Mitigation Efficiency (%) |
|---|---|---|
| The proposed DRO method | 12.5 | 82.3 |
| Coalitional Cyber Insurance Model | 10.2 | 75.5 |
| Actuarial Cybersecurity Framework | 8.7 | 70.8 |
| Method | Cost Reduction (%) | Risk Mitigation Efficiency (%) | Cost–Benefit Ratio |
|---|---|---|---|
| The proposed DRO method | 14.3 | 40.6 | 1:4.2 |
| Coalitional Cyber Insurance Model | 12.8 | 35.4 | 1:3.5 |
| Actuarial Cybersecurity Framework | 10.9 | 30.7 | 1:2.9 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, A.P.; Fei, F.X.; Alhazmi, M. Cyber Insurance for Energy Economic Risks. Smart Cities 2024, 7, 2042-2064. https://doi.org/10.3390/smartcities7040081
Zhao AP, Fei FX, Alhazmi M. Cyber Insurance for Energy Economic Risks. Smart Cities. 2024; 7(4):2042-2064. https://doi.org/10.3390/smartcities7040081
Chicago/Turabian StyleZhao, Alexis Pengfei, Faith Xue Fei, and Mohannad Alhazmi. 2024. "Cyber Insurance for Energy Economic Risks" Smart Cities 7, no. 4: 2042-2064. https://doi.org/10.3390/smartcities7040081
APA StyleZhao, A. P., Fei, F. X., & Alhazmi, M. (2024). Cyber Insurance for Energy Economic Risks. Smart Cities, 7(4), 2042-2064. https://doi.org/10.3390/smartcities7040081





