Extending the Quality of Secure Service Model to Multi-Hop Networks
Abstract
:1. Introduction
2. Related Work
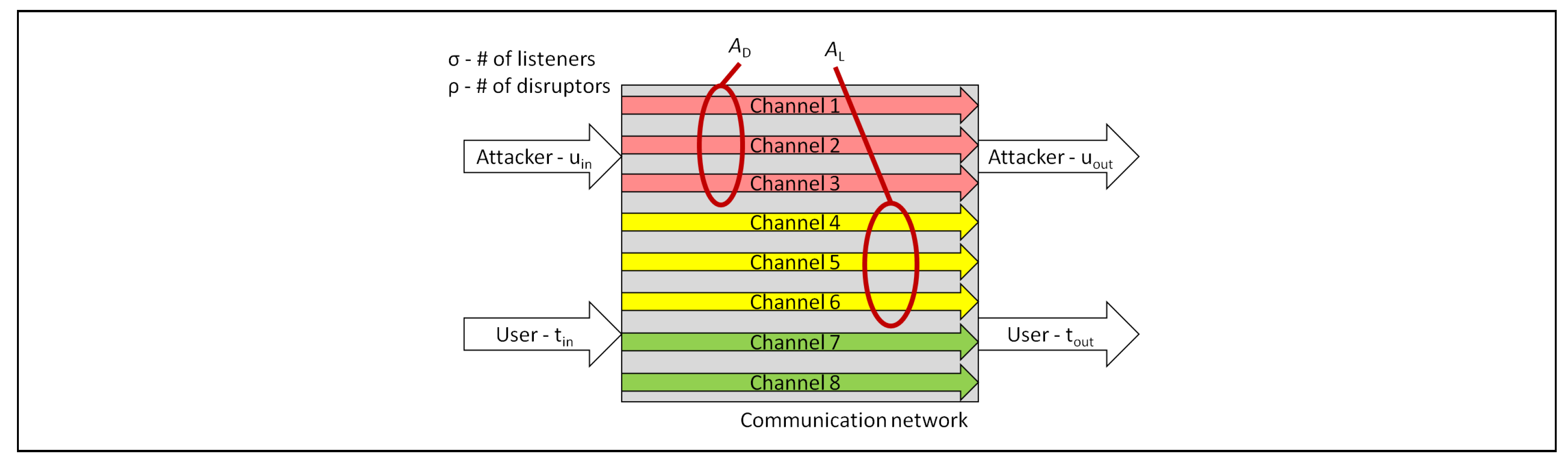
3. QoSS Applied to a Multi-Hop Network
3.1. Reliability of Systems
3.2. Reliability Applied to QoSS
3.3. Combinational Considerations such as Fragmentation and Duplication
3.4. Calculation of Multi-Hop Network QoSS
3.4.1. Step 1
3.4.2. Step 2
3.4.3. Step 3
4. Case Studies of Multi-Channel and Multi-Hop QoSS
4.1. Single-Channel, Point-to-Point Network
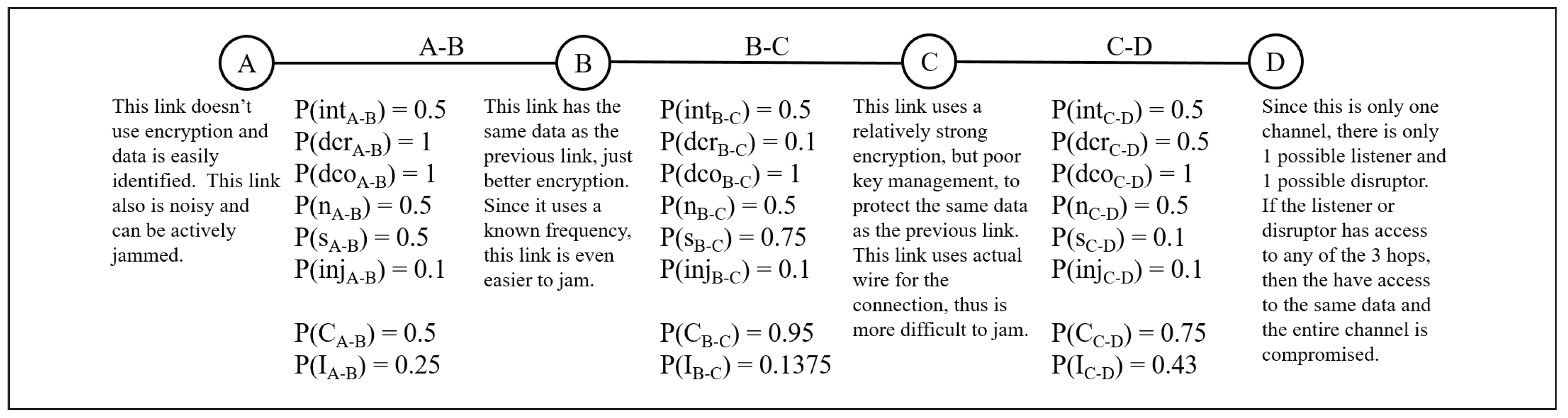
4.2. Single-Channel, Three-Hop Network
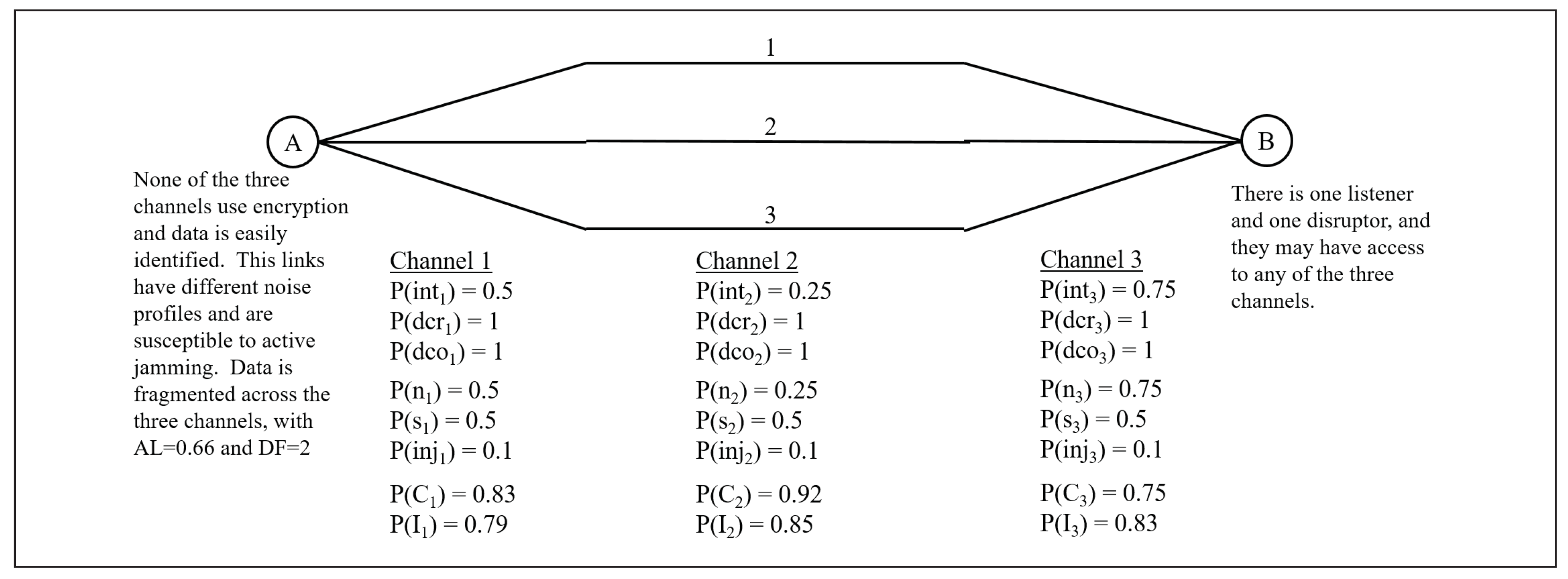
4.3. Three-Channel, Point-to-Point Network
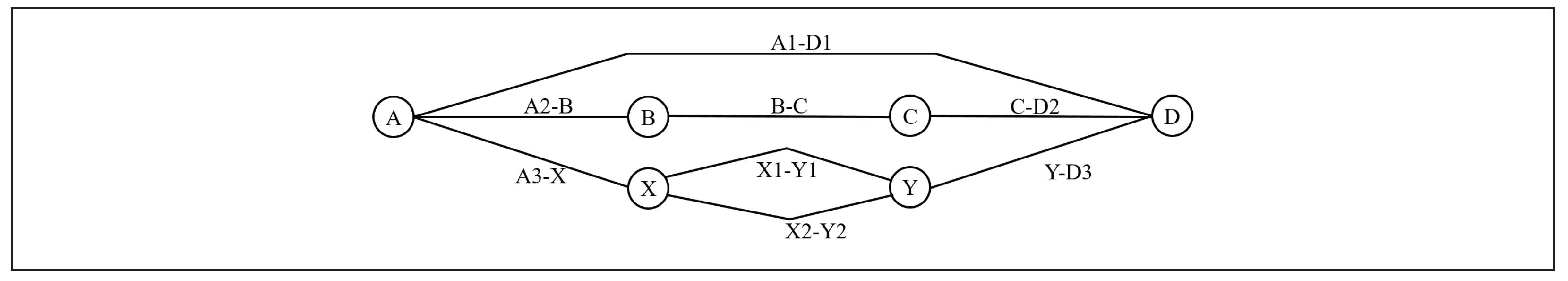
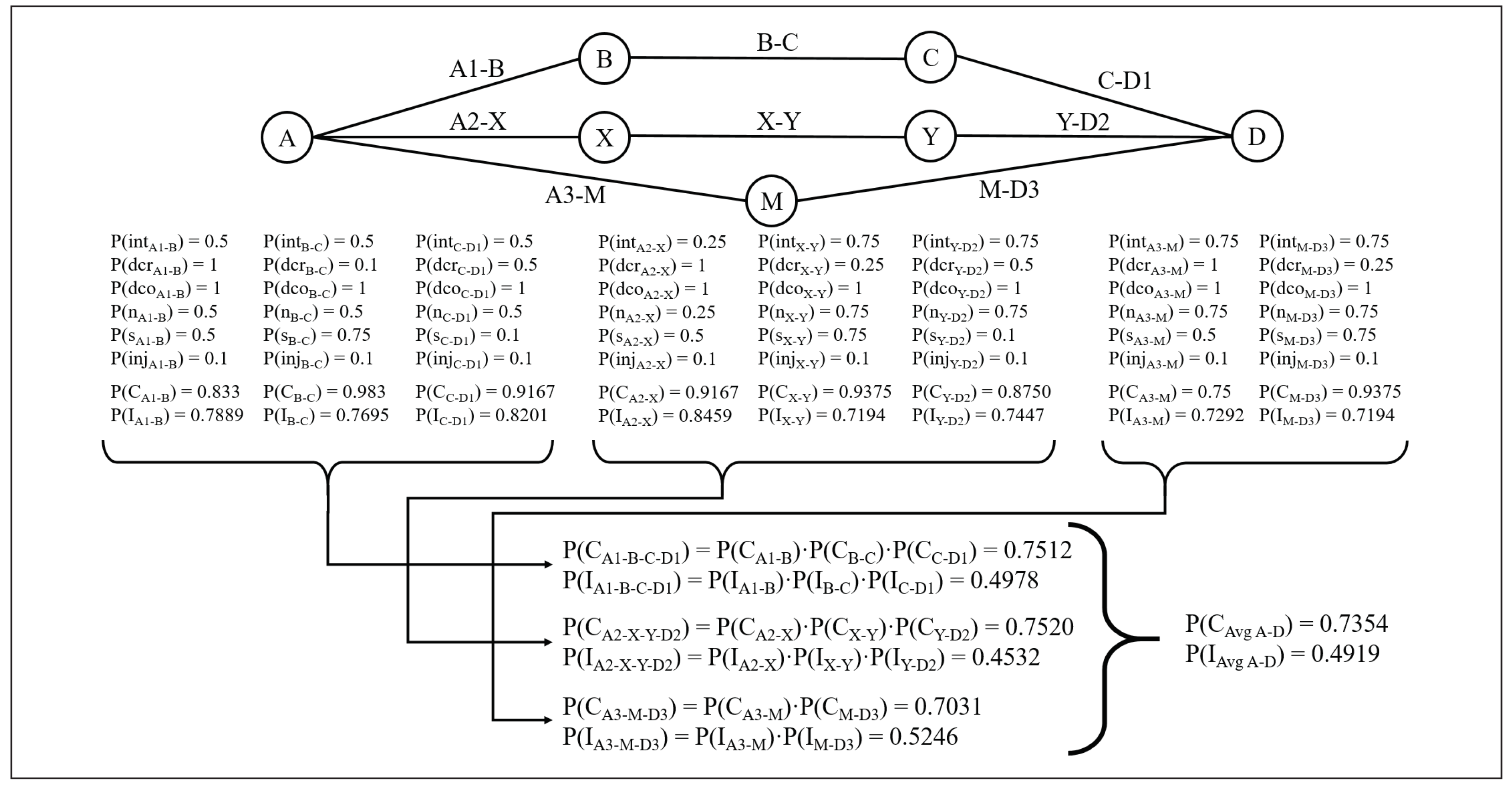
4.4. 3-Channel, 3-Hop Network
4.5. Implications of Results
5. Conclusions and Future Work
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Wang, J.A.; Xia, M.; Zhang, F. Metrics for information security vulnerabilities. J. Appl. Glob. Res. 2008, 1, 48–58. [Google Scholar]
- Leon, P.G.; Saxena, A.S. An approach to quantitatively measure information security. In Proceedings of the 3rd India Software Engineering Conference, Mysore, India, 25–27 February 2010. [Google Scholar]
- Nikhat, P.; Beg, M.R.; Khan, M.H. Model to quantify confidentiality at requirement phase. In Proceedings of the 2015 International Conference on Advanced Research in Computer Science Engineering & Technology (ICARCSET 2015), Unnao, India, 6–7 March 2015. [Google Scholar]
- Simon, P.M.; Graham, S.; Talbot, C.; Hayden, M. Model for Quantifying the Quality of Secure Service. J. Cybersecur. Priv. 2021, 1, 289–301. [Google Scholar] [CrossRef]
- Hennessy, L.J.; Patterson, D.A. Computer Architecture: A Quantitative Approach; Elsevier: Amsterdam, The Netherlands, 2011. [Google Scholar]
- Ghali, C.; Narayanan, A.; Oran, D.; Tsudik, G.; Wood, C.A. Secure Fragmentation for Content-Centric Networks. In Proceedings of the 2015 IEEE 14th International Symposium on Network Computing and Applications, Boston, MA, USA, 28 September 2015. [Google Scholar]
- Lim, K.W.; Kapusta, K.; Memmi, G.; Jung, W.S. Multi-Hop Data Fragmentation in Unattended Wireless Sensor Networks. arXiv 2019, arXiv:1901.05831. [Google Scholar]
- Modarressi, A.R.; Ronald, A.S. Signaling system no. 7: A tutorial. IEEE Commun. Mag. 1990, 28, 19–20. [Google Scholar] [CrossRef]
- Russell, T. Signaling System # 7; McGraw-Hill: New York, NY, USA, 2002; Volume 2. [Google Scholar]
- Moulika, V.; Bhagyalakshmi, L. Performance Investigation of Cooperative Diversity Techniques for 5G Wireless Networks. In Proceedings of the 2019 IEEE 1st International Conference on Energy, Systems and Information Processing (ICESIP), Chennai, India, 4–6 July 2019. [Google Scholar]
- Dolev, D.; Dwork, C.; Waarts, O.; Yung, M. Perfectly secure message transmission. J. ACM 1993, 40, 17–47. [Google Scholar] [CrossRef]
- Srinathan, K.; Arvind, N.; Pandu, C.R. Optimal perfectly secure message transmission. In Annual International Cryptology Conference; Springer: Berlin/Heidelberg, Germany, 2004. [Google Scholar]
- Desmedt, Y.; Wang, Y. Perfectly secure message transmission revisited. In International Conference on the Theory and Applications of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Spini, G.; Zemor, G. Efficient Protocols for Perfectly Secure Message Transmission With Applications to Secure Network Coding. IEEE Trans. Inf. Theory 2020, 66, 6340–6353. [Google Scholar] [CrossRef]
- Wampler, J.A.; Chien, H.; Andrew, T. Efficient distribution of fragmented sensor data for obfuscation. In Proceedings of the MILCOM 2017-2017 IEEE Military Communications Conference (MILCOM), Baltimore, MD, USA, 23–25 October 2017. [Google Scholar]
- Bolcskei, H. MIMO-OFDM Wireless Systems: Basics, Perspectives, and Challenges. IEEE Wirel. Commun. 2006, 13, 31–37. [Google Scholar]
- Firoiu, V.; Le Boudec, J.Y.; Towsley, D.; Zhang, Z.L. Theories and models for internet quality of service. Proc. IEEE 2002, 90, 1565–1591. [Google Scholar] [CrossRef] [Green Version]
- Rass, S.; Schartner, P. Multipath Authentication without shared Secrets and with Applications in Quantum Networks. In Proceedings of the International Conference on Security and Management (SAM), Las Vegas, NV, USA, 12–15 July 2010; Volume 1, pp. 111–115. [Google Scholar]
- Clarkson, M.R.; Schneider, F.B. Quantification of integrity. Math. Struct. Comput. Sci. 2015, 25, 207–258. [Google Scholar] [CrossRef] [Green Version]
- Rausand, M.; Hoyland, A. System Reliability Theory: Models, Statistical Methods, and Applications; John Wiley & Sons: Hoboken, NJ, USA, 2003; Volume 396. [Google Scholar]
- Patra, A.; Choudhury, A.; Pandu Rangan, C.; Srinathan, K. Unconditionally reliable and secure message transmission in undirected synchronous networks: Possibility, feasibility and optimality. Int. J. Appl. Cryptogr. 2010, 2, 159–197. [Google Scholar] [CrossRef] [Green Version]
- Mencík, J. Concise Reliability for Engineers; BoD-Books on Demand/Intech: Rijeka, Croatia, 2016; Chapter 1. [Google Scholar]
- Hayden, M.; Graham, S.; Betances, A.; Mills, R. Multi-Channel Security through Data Fragmentation. In Proceedings of the IFIP International Conference on Critical Infrastructure Protection, Arlington, VA, USA, 16 March 2020; pp. 137–155. [Google Scholar]



Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Simon, P.M.; Graham, S. Extending the Quality of Secure Service Model to Multi-Hop Networks. J. Cybersecur. Priv. 2021, 1, 793-803. https://doi.org/10.3390/jcp1040038
Simon PM, Graham S. Extending the Quality of Secure Service Model to Multi-Hop Networks. Journal of Cybersecurity and Privacy. 2021; 1(4):793-803. https://doi.org/10.3390/jcp1040038
Chicago/Turabian StyleSimon, Paul M., and Scott Graham. 2021. "Extending the Quality of Secure Service Model to Multi-Hop Networks" Journal of Cybersecurity and Privacy 1, no. 4: 793-803. https://doi.org/10.3390/jcp1040038
APA StyleSimon, P. M., & Graham, S. (2021). Extending the Quality of Secure Service Model to Multi-Hop Networks. Journal of Cybersecurity and Privacy, 1(4), 793-803. https://doi.org/10.3390/jcp1040038





