Analyzing Threats and Attacks in Edge Data Analytics within IoT Environments
Abstract
:1. Introduction
| Ref. | Description | Threat Considered | Impact of the Threat | Analysis of the Threat Model Considered | Remarks |
|---|---|---|---|---|---|
| [10] | Secure data analytics in edge computing | ✓ | × | ✓ | Propose key requirements for secure data analytics and identify pros and cons of existing works on data analytics. |
| [11] | Data security in edge computing | × | × | ✓ | Review different cryptography-based solutions to address data security issues in edge computing. |
| [21] | Security issues during authentication schemes for data integrity | × | × | ✓ | Evaluate existing methods to preserve data integrity in fog and cloud computing and identify their limitations. |
| [7] | Security issues in edge computing | × | × | ✓ | Review security issues in terms of access control, key management, privacy, attack mitigation, and anomaly detection. |
| [22] | Security-as-a-Service in multi-access edge computing | ✓ | × | ✓ | Evaluate IDS, secure communication, and access control mechanisms, and propose a secure service deployment framework. |
| [23] | Security issues that are caused by adopting virtualization in edge computing | ✓ | × | ✓ | Discuss the advantages of adopting virtualization, containers, Uni kernels, and real-time OS in edge computing. Security issues and attacks on these technologies with different use case scenarios are addressed. |
| [24] | Security and prevention mechanisms in fog computing | × | × | ✓ | Comparative analysis of different techniques to address common security issues in edge computing. |
| [25] | Security threats in mobile edge computing | ✓ | × | ✓ | Review the advantages of using machine learning techniques to improve network efficiency and handle malicious attacks. |
| [26] | Security aspects in fog computing | × | × | × | Discuss security issues in edge computing caused due to its operations in the physical environment and the need for interoperability between edge nodes and IoT devices with various solutions. |
| [27] | Security issues in edge, fog, and IoT applications | × | × | × | Identify security issues and evaluate authentication and encryption schemes to address these issues. |
| [28] | Review of fog-based applications’ architecture and security issues at the architectural level | × | × | × | Discuss four edge-based applications and security concerns to prevent malicious access and data modification in these applications. |
| [29] | Security issues due to fog infrastructure in various applications | × | × | ✓ | The present data analytics taxonomy discusses the complexity during data processing with research challenges. |
| [17] | Discuss how to improve security issues and protocols in fog computing | × | × | ✓ | Present a comprehensive survey on overall issues in edge computing. Analyze security models that address location and data privacy, secure communication, and various intrusion systems. |
| [11] | Analyze fog computing architecture, security, and trust issues | × | ✓ | ✓ | Discuss security issues, various mechanisms, and different technologies to handle data security and privacy in edge computing. |
| [16] | A comprehensive review of edge computing security issues with a few proposed solutions | δ | δ | ✓ | Identify the challenges of the existing security models to handle threats in edge computing and suggest a few solutions that can be applied to a similar edge computing paradigm. |
| [8] | Security and privacy issues due to fog computing architecture | × | × | × | Identify the threats in the edge computing platform. |
| [30] | Challenges due to data security and privacy | δ | ✓ | × | Justify how cloud data security solutions cannot be applied to edge computing and highlight the importance of addressing this issue in edge computing. |
| [31] | Layer-wise security and threat issues | × | × | ✓ | Identify the threats in each layer and propose a risk-based trust model to secure the decision-making process and secure data in the edge layer. |
| [14] | Review of security and privacy issues to secure fog-based IoT application | δ | ✓ | × | Identify the threats and security issues related to data storage, computation, and data sharing in the fog layer. |
| [13] | Potential security issues in the fog-based application | ✓ | ✓ | × | Various edge computing solutions are analyzed, and security models related to privacy-preserving, insider attacks, resource management, encryption, and authentication schemes are discussed. |
| [32] | Address all the common security and privacy issues in fog computing and identify gaps in the existing security solutions | × | × | ✓ | Propose solution toward establishing trust, secure communication channels, and privacy-preserving schemes. |
| [33] | Concerning security and resilience edge and fog computing architectures are analyzed | × | × | × | Address issues related to virtualized infrastructure and software-driven communication. |
| [12] | Using fog computing, how to secure healthcare data is discussed | ✓ | × | × | Propose encryption algorithms to secure data on the edge layer. |
| [19] | MITM attacks are studied exclusively by CPU and memory consumption on fog devices | × | ✓ | × | Present authentication and authorization techniques to protect edge nodes from an MITM attack. |
| [34] | Security threats when adopting edge computing in IoT applications | × | × | × | Review existing security models that address MITM, intrusion detection, malicious nodes, and data protection models. |
| [18] | Security threats that affect the confidentiality, integrity, and availability of the architecture | × | ✓ | × | Discuss the advantages of adopting edge computing in IoT applications. Recommend a few solutions to address the vulnerabilities and threats due to adoption. |
| Current study | Security issues on edge nodes that affect decision-making and analytics of the applications | ✓ | ✓ | ✓ | Review potential threats that affect edge nodes and disturb the normal functioning of applications. Identify research gaps in existing security models. |
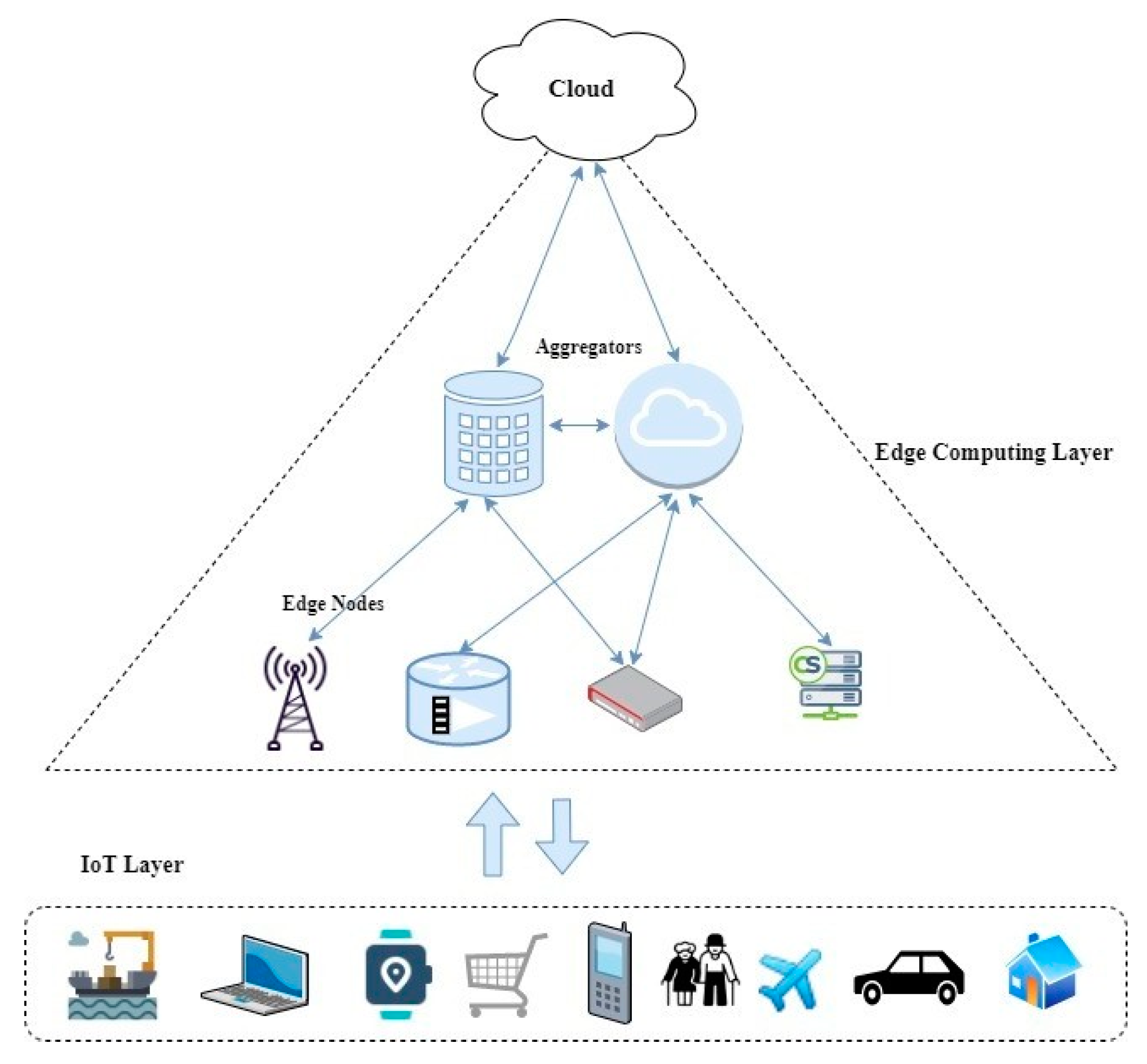
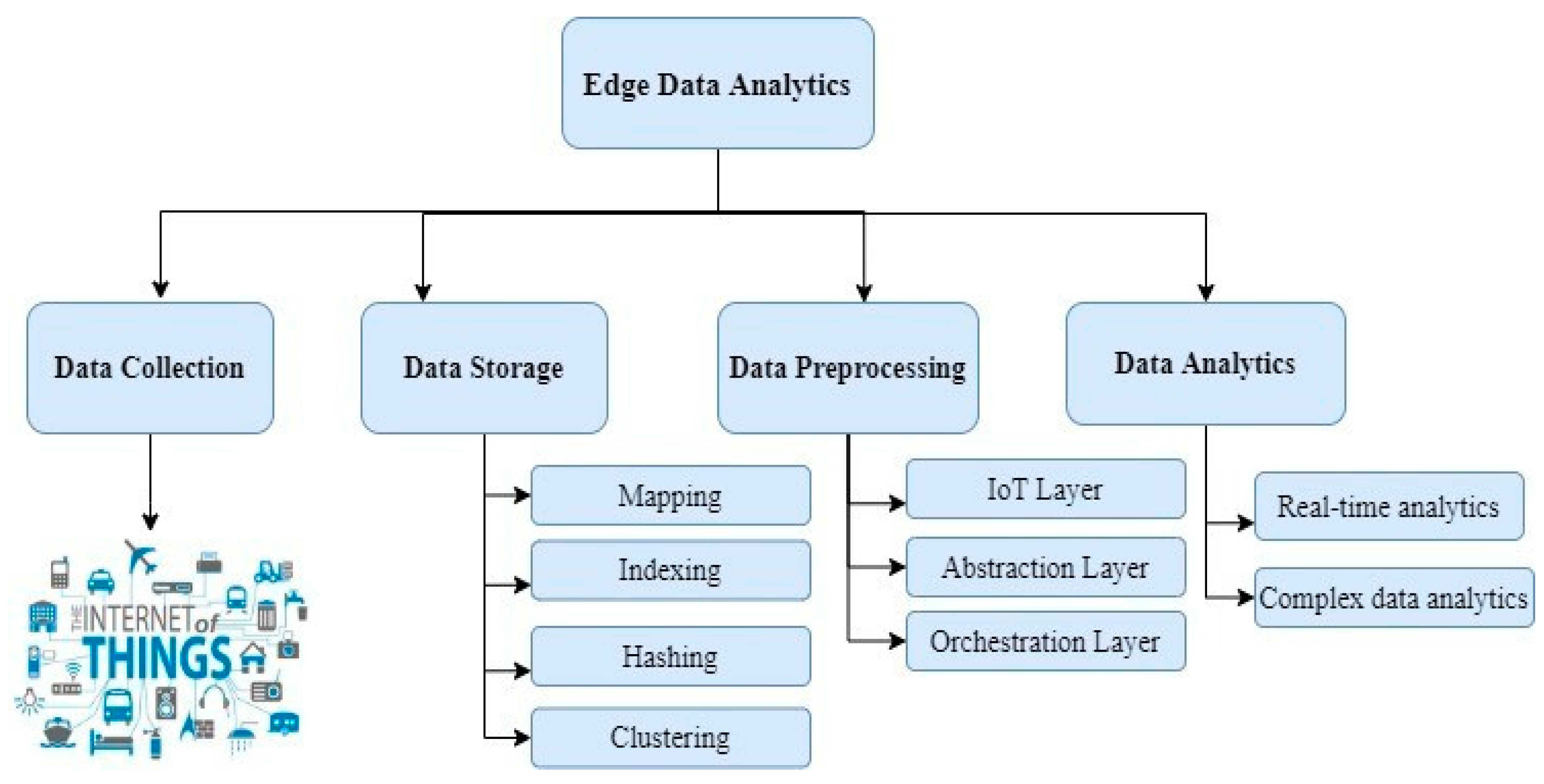
2. Edge Data Analytics
Decision-Making in Edge Data Analytics
3. Security Threats during Edge Data Analytics
| Types | Ref. | Threats | Definition | Impact on the Edge Nodes and Networks |
|---|---|---|---|---|
| Insider or Malicious Attack | [68] | Data Breach | Illegal data access and data leak | Disclosure of confidential and sensitive data to an unauthorized person |
| [69] | Hacking | Illegitimate users modifying or altering the edge and user data | Loss of data integrity, manipulation of decision-making, and disturb the normal functioning of the application | |
| [70] | Identity and Password Leak | Illegally hacked username and password to gain access to the application | Gain unrestricted access to the application and misuse of sensitive information | |
| [63] | Malicious Insider | Illegally access the network and control all the nodes | Behave legitimately and take advantage of the services | |
| [71] | Forgery | Forge the identities and profiles | Generate fake information and mislead other users. Consume more bandwidth, storage, and energy | |
| Hardware Attack | [72] | Jamming | Blocking communication channel | Loss of data or increased data transmission rate |
| [73] | Side- Channel Attack | Deliberately block communication channel | Falsification of data and increased computation time | |
| [74] | Resource Depletion | Flood traffic and saturated storage or network resources | Affects data processing and delays decision-making due to a lack of resources | |
| [75] | Equipment Sabotage | Deliberately create resource deficiency | Damage resources and disturb real-time services | |
| [76] | DoS attack | Disruption of edge nodes, hardware devices, or software applications | Consume more node resources, disrupt network operations, and generate false messages | |
| Software Attack | [77] | SQL Injection | Inject code to access sensitive data | Modify sender data or fabricate new malicious data to affect data confidentiality |
| [78] | Impersonation | Claim to be an alternative user by using a forged character | Acquire illegitimate benefits and access confidential data with malicious intentions | |
| [14] | Tampering | Unauthorized entities intentionally modifying data | Causes privacy leakage, hijacks services, or creates other attacks | |
| [79] | Eavesdropping | Illegally gain access to the network and listen to the network communication | Hack users’ data and intercept communication channels to degrade efficiency | |
| Network Attack | [80] | Message Replay | Illegitimate user sending authorized messages in the network | Compromises other nodes and exposes sensitive data |
| [81] | Spoofing | Fake users repetitively requesting services | Divert communication channel toward attackers’ destination. Consumes more bandwidth and increases processing times | |
| [14] | Man-In-The-Middle | An illegitimate insider in the network with malicious intention | Steal users’ credentials, attack communication channels, or alter data | |
| [82] | Flooding | Generate enormous illegitimate messages and increase network traffic | Disrupt the network and prevent legitimate users from accessing the network | |
| [77] | Pattern Analyses | Intercepting and examining the data flow and network pattern in the communication channels | Gain unauthorized access to the network and steal data | |
| [83] | Spamming | Send spontaneous messages to all the nodes requesting services | Collect user credentials and gain access to the network | |
| [84] | Sybil | Create a fake identity and gain access to the network | Acquire privileged access to the services | |
| [85] | Sinkhole attack | The malicious node sends a fake message and establishes a connection with a legitimate node | Creates maximum traffic flow and makes adjoining nodes collide. Increases bandwidth, leading to resource contention and message destruction |
4. Motivating Use Case Applications
4.1. Healthcare Applications
4.2. Traffic Management Applications
4.3. Smart City Applications
| Use Case | Ref. | Working Model | Decision Making Node | Evaluation | Insider Attack | Software Attack | Hardware Attack | Network Attack | Effect of Threats on the Model |
|---|---|---|---|---|---|---|---|---|---|
| Health Care Applications | [90] | Emergency alert message for COVID-19 infection | Artificial intelligence-based fog node | Generate medical report and alert message to caregivers and doctors | Data breach | - | Equipment malfunction | - | Hack data or may degrade alert message efficiency |
| [96] | FAST—Fall detection system for stroke patients | Back-end module server on the cloud | Detects if the stroke patient is about to fall and triggers message to the emergency phone number | Forgery, MITM | Tampering | - | - | Causes false predictions, degrades efficiency, and maliciously drops or delays information | |
| [95] | Fall detection or electrocardiography monitoring | Edge gateway—Fall detection system | Notification and alert message to caregivers | Forgery, MITM | Tampering | - | - | May degrade notification efficiency | |
| [98] | eWall—Home management for senior citizens | eCloud or ePSOS | Track daily activities of an elderly patient. Alert message from eWall cloud to relatives or hospital | MITM, malicious insider | - | Resource depletion | - | Affect confidentiality, breach privacy, tamper with hardware devices, and disturb normal data flow | |
| [99] | Activity monitoring | Cloud Access Security Broker | Activity detection and calories burnt are sent to hospitals and nutritionists | MITM, insider, hacking | Impersonation | - | - | Affect confidentiality, privacy, and reliability of the decision | |
| [119] | Healthcare and Assisted Living (AAL) in Smart ambient | Fog Accelerator Nodes | Aggregate data from IoT sensors and monitor patients’ fall or cardiovascular issues. In case of emergency, informs caretakers | - | SQL Injection | Equipment sabotage | - | Affect confidentiality, leak sensitive information, and destroy hardware devices | |
| [120] | Smart e-Healt hcare system | Gateway nodes | Gather medical information of patients from sensors, aggregate in edge layer, and generate EWS in case of emergency for doctors or caretakers | Malicious insider | Impersonation, jamming | - | - | Malicious insider can watch the activities, illegitimately communicate with other users, falsify data, or send a false alarm | |
| [92] | Chikungunya virus diagnosis solutions | Alert generation component in fog layer | Alert message is sent to government and healthcare to control outbreak of virus | - | - | Equipment sabotage | - | May not create an alert message or causes a delay in generating the alert message | |
| [93] | Detect cancer and monitor patients | Smart gateway nodes in fog layer | Send e-report to patients, send ambulance in case of emergency, and monitor patients until they recover | Data breach | - | - | Eavesdropping | Intruder may hack patients’ personal data or may be a silent spectator | |
| Traffic Management Application | [103] | Traffic Management Scheme | Cloudlets | Minimize response delay for traffic management by load balancing | Data breach, malicious insider | - | - | - | Breach data privacy |
| [105] | Vehicular Network collaboration | Fog Controller Node | Accident notification and avoid road congestion Traffic prioritization in case of emergency and directs fast rescue route | Location privacy | - | Fault tolerance | Sinkhole, sniffing, spoofing | Track users’ location or deprive them from the network | |
| [106] | Smart Traffic Control | Traffic Control Node | Identifies road congestion and avoids traffic jams | Location privacy | - | Fault tolerance | Sinkhole, sniffing, spoofing | Track users’ location or deprive them from the network | |
| [109] | 5G-based Intelligent Transport System | Transportation authority at the edge layer | Sends traffic violation report (TVR) based on the vehicle’s speed sensors | - | - | Equipment sabotage, side channel attack | Physical damage to sensor nodes, blocks communication channels, and increases waiting time. | ||
| [121] | Smart Car Parking system | Microcontroller device generates parking status | Identifies traffic jam and shows parking spots | Location privacy | - | Jamming | Track users and vehicle information, cause traffic congestion | ||
| Smart City Applications | [122] | Surveillance videos for smart cities | Fog Aggregate Nodes | Send compressed video data to the cloud | Side channel attack | Tampering | Equipment sabotage | Eavesdropping, Sybil, DDoS, pattern analysis | Maliciously drop or delay information, block the resource or request from the users, hack user privacy |
| [123] | Smart things to machine interaction | Fog Controller Node | Intelligent lighting—sensor identifies when to turn the switch on/off | - | Tampering | - | - | Device tampering | |
| [118] | Smart pipeline monitoring system | Fog Controller Node | Closes gas pipeline in case of gas leakage or fire detection | - | Tampering | - | - | Device tampering | |
| [114] | Powerline communication for smart meters | Fog Computing Nodes | Summary of electric power consumption data is sent to the cloud | Data alteration | - | - | Eavesdropping, pattern analysis, jamming, DoS | Device tampering | |
| [124] | Forest Fire management systems | Prediction system | Identifies and generates an alert message to forest authorities | - | Tampering | - | - | Alters the decision with malicious intentions |
5. Analyses of Existing Security Threat Models
5.1. Intrusion Detection System
5.2. Combination of an Intrusion Detection and Intrusion Prevention System
5.3. Automated Intrusion Detcetion System
5.4. Machine Learning-Based Intrusion Detection System
5.5. Cryptography-Based Systems
5.6. Authentication Scheme in the Edge Computing Layer
5.7. Hybrid Models
5.8. Application-Specific Security Models
5.9. Container and Consensus Protocols in Edge-Based Security Models
5.10. Bridging Gap with Cloud Security
5.11. Impact of Threats on Edge Data Analytics
6. Future Research Directions
- Adopting federated learning (FL) algorithms for edge data analytics—Following observation #1, the integration of AI in edge computing is widely adopted, especially in healthcare applications. It remarkably enhances the scope and computational efficiency of edge nodes [90]. However, the challenging aspects of AI models are their short battery life, power-hungry, delay-intolerant portable devices, vulnerable to security threats, and a loss of their reliability [91]. These limitations can be resolved by adopting the federated learning framework in AI models. Federated learning is an ML technique used to train data across decentralized edge devices without exchanging them with other devices. This reduces the amount of data in wireless uplinks, adapts well with heterogeneous cellular networks, and preserves privacy. Pace steering in FL is a flow control mechanism that controls data uplinks by regulating the device connection pattern [162]. FL deploys secure data aggregation mechanism, where data remains secure even in the memory to protect additional security in data centers [163]. Therefore, FL can be best applied for applications such as edge computing, where device data are more relevant, for better data transmission and to provide security.
- Enhancing IEEE communication standards in edge-based healthcare applications—The sensors in healthcare applications are connected through BAN or WPAN. As noted in observation #2, the network may not offer necessary bitrates for biomedical signals’ transmission. This will delay communication or reduce the quality of a link within body devices, especially when many body sensors are interconnected [97]. Currently, IEEE 802.15 technical standards are used in BAN or WPAN, which results in low-rate data transmission in edge data analytics, but this standard was designed for Zigbee or 6LoWPAN, whereas IEEE 802.15.6 is a standard for WBANs that helps healthcare service providers to monitor patients at any time and location. It provides human body communication with a data rate of more than 2 Mbps (Mega Bytes Per Second) and an operation band of 27 MHz (Mega Hertz). These operation bands are valid in the major European countries. Apart from that, it also provides secure communication with three different security levels through authentication and encryption. This provides solutions for integrity, reply defense, confidentiality, privacy protection, and message authentication problems. Therefore, adopting IEEE 802.15.6 in healthcare applications can enhance the reliability, service quality, low power, data rate, and non-interference. This standard also deals with particular BAN requirements, such as security, energy consumption, range of communication, scale of the network, and data rate [164].
- Developing a robust and efficient data dissemination technique in VANET for a node selection strategy—As noted in observation #3, in VANET it is challenging to maintain a specific topology for every vehicle due to the high mobility and uneven distribution of vehicles. Conventional routing protocols use a street-centric divide-and-conquer approach. This approach can be efficient if a succession of vehicles between the source and destination is determined in advance [165]. However, it may not be possible in a real-time scenario, as it results in unavoidable collision problems. Therefore, a robust and efficient data dissemination technique is required that considers selecting efficient relaying nodes to forward packets even when the source and destination of the vehicles are not known in advance [166]. The data dissemination technique should be aware of the vehicle topology within its coverage and monitor the changes in topology so that the data transmission between edge nodes and devices can be scheduled and secured with the assigned frame. This approach can greatly reduce the data transmission delay for edge analytics and secure the transmitted data.
- Employing energy harvesting techniques to preserve longevity and processing capabilities of edge nodes in smart city applications—In an efficient smart city application, integrating energy harvesting techniques into edge computing for smart city applications offers a robust solution to safeguarding against data threats, ensuring the integrity, confidentiality, and authenticity of critical information. By harnessing renewable energy sources, edge devices can maintain continuous operation, facilitating real-time data analysis and threat detection. This uninterrupted surveillance capability is pivotal in detecting and mitigating potential security breaches. As noted in observation #5, high battery consumption is the most common problem in crowdsensing when actively collecting data, and this may affect the quality of data collected and the processing capabilities of edge nodes [167]. Moreover, with decentralized processing at the edge, sensitive data can be processed closer to its source, minimizing the risk of exposure during transit to centralized servers [168]. Additionally, energy harvesting supports the implementation of advanced encryption protocols and authentication mechanisms, further fortifying data security measures [102]. By combining energy harvesting with edge computing, smart city infrastructures can establish resilient defenses against evolving data threats, ensuring the trustworthiness and reliability of their systems in safeguarding citizen safety and critical infrastructure.
- Enhancing network infrastructure in the edge layer—Different technologies, such as SD, NFV, 5G, or virtualization, can significantly bolster security measures against threats and attacks in edge data analytics. SDN and NFV enable centralized management and orchestration of network resources, allowing for dynamic and granular control over security policies and access permissions [169]. The 5G networks provide higher bandwidth, lower latency, and greater reliability, facilitating secure and real-time communication between edge devices and centralized servers [170]. Virtualization techniques enable the isolation of critical network functions and applications, limiting the potential impact of security breaches or attacks [171]. By leveraging these technologies collectively, organizations can establish resilient and adaptive network infrastructures capable of mitigating risks and ensuring the integrity, confidentiality, and availability of data in edge-based IoT environments.
- Adopting fine-grained access control mechanisms in the edge layer—It can be noted from observation #6 that when data are stored in the edge layer for a long time before transferring them to the cloud, it can lead to any catastrophic events. This can result in data authentication and integrity issues, affecting the decision-making capabilities of the edge nodes. It is also observed that hybrid models and encryption techniques are used to address these issues in the existing security model. However, as stated in observation #7, complex keys due to these techniques can result in network congestion in communication channels. Therefore, adopting access control mechanisms between data owners and the edge layer, which is a straightforward approach, can overcome these issues. This approach has proved to be efficient in cloud computing [172]. However, in edge computing, the access control mechanism has to be fine-grained, which supports secure collaboration, interoperability between heterogeneous devices, and enhances data tracking. At the same time, the design goals and resource constraints of edge nodes have to be considered so that it provides a lightweight and secure data analytics scheme.
- Designing trust management models in an edge computing framework—The decentralized edge computing has a huge obstacle of collecting and managing information from various edge nodes to perform data analytics. These criteria can be distinct to various applications and services [32]. Further, edge nodes might frequently move from one area to another [10]. This movement causes challenges in establishing trust among edge nodes during data processing. Thus, designing a trust model that supports mobility and scalability is required in an edge computing framework. The trust models can be third-party models used to decrease the computation overload of the edge nodes and should manage interregional trust values through historical data to track the mobility of edge nodes.
- Isolating the infected edge nodes in the edge computing layer—In the currently available edge threat models, malicious nodes are the common threats that affect the decision-making process. Malicious nodes can always compromise other nodes and create other attacks in the edge layer, such as DoS, repeated storage/processing requests, spoofing, or leakage of confidential data [158]. This induces security and trust risks, spreading among the edge nodes and to the whole edge layer. Therefore, a strategy needs to be developed to identify the malicious node and isolate it from the other nodes to reduce the risk of malicious nodes gaining control on the edge layer.
- Enhancing security with emerging technologies, such as AI and blockchain—AI algorithms can play a crucial role in real-time threat detection and anomaly detection at the edge layer, continuously monitoring device behavior and network traffic to identify potential security threats. Additionally, AI-based techniques can leverage historical data to improve the accuracy and effectiveness of security measures in edge data analytics systems [173]. Furthermore, blockchain technology offers promising solutions for ensuring data integrity and enhancing trust in edge data analytics. By providing a decentralized and immutable ledger, blockchain can create tamper-proof records of data transactions, ensuring the authenticity and transparency of data collected and processed at the edge layer [174]. Moreover, blockchain facilitates secure and transparent data sharing among multiple parties in edge computing environments, preserving data privacy and confidentiality while enabling efficient collaboration [175]. Combining AI and blockchain technologies presents an exciting avenue for future research in enhancing security in edge data analytics. By integrating AI algorithms for threat detection with blockchain for secure data transactions, edge data analytics systems can achieve a higher level of security, trustworthiness, and resilience against security threats [176]. Exploring innovative approaches that leverage the synergies between AI and blockchain holds great potential for advancing the security capabilities of edge data analytics systems and addressing evolving security challenges in edge computing environments.
7. Discussion and Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yahuza, M.; Bin Idris, M.Y.I.; Wahab, A.W.B.A.; Ho, A.T.S.; Khan, S.; Musa, S.N.B.; Taha, A.Z.B. Systematic review on security and privacy requirements in edge computing: State of the art and future research opportunities. IEEE Access 2020, 8, 76541–76567. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on fog computing: Architecture, key technologies, applications and open issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Röckl, J.; Wagenhäuser, A.; Müller, T. Veto: Prohibit Outdated Edge System Software from Booting. In Proceedings of the International Conference on Information Systems Security and Privacy, Lisbon, Portugal, 22–24 February 2023; pp. 46–57. [Google Scholar] [CrossRef]
- Rajkumar, V.S.; Stefanov, A.; Musunuri, S.; de Wit, J. Exploiting Ripple20 to Compromise Power Grid Cyber Security and Impact System Operations. IET Conf. Proc. 2021, 2021, 3092–3096. [Google Scholar] [CrossRef]
- Yang, K.; Jia, X. Data storage auditing service in cloud computing: Challenges, methods and opportunities. World Wide Web 2012, 15, 409–428. [Google Scholar] [CrossRef]
- Satyanarayanan, M. The emergence of edge computing. Computer 2017, 50, 30–39. [Google Scholar] [CrossRef]
- Zeyu, H.; Geming, X.; Zhaohang, W.; Sen, Y. Survey on Edge Computing Security. In Proceedings of the 2020 International Conference on Big Data, Artificial Intelligence and Internet of Things Engineering, ICBAIE, Fuzhou, China, 12–14 June 2020; pp. 96–105. [Google Scholar] [CrossRef]
- Aljumah, A.; Ahanger, T.A. Fog computing and security issues: A review. In Proceedings of the 2018 7th International Conference on Computers Communications and Control, ICCCC 2018, Oradea, Romania, 8–12 May 2018; pp. 237–239. [Google Scholar] [CrossRef]
- Kumar, K.S.; Chythanya, K.R.; Jamalpur, B.; Kumar, K.S.; Harshavardhan, A. Contemporary Applications of Fog Computing along with Security Problems and Solutions. J. Study Res. 2019, XI, 116–142. [Google Scholar]
- Liu, D.; Yan, Z.; Ding, W.; Atiquzzaman, M. A Survey on Secure Data Analytics in Edge Computing. IEEE Internet Things J. 2019, 6, 4946–4967. [Google Scholar] [CrossRef]
- Zhang, J.; Chen, B.; Zhao, Y.; Cheng, X.; Hu, F. Data Security and Privacy-Preserving in Edge Computing Paradigm: Survey and Open Issues. IEEE Access 2018, 6, 18209–18237. [Google Scholar] [CrossRef]
- Al Hamid, H.A.; Rahman, S.M.M.; Hossain, M.S.; Almogren, A.; Alamri, A. A Security Model for Preserving the Privacy of Medical Big Data in a Healthcare Cloud Using a Fog Computing Facility with Pairing-Based Cryptography. IEEE Access 2017, 5, 22313–22328. [Google Scholar] [CrossRef]
- Khan, S.; Parkinson, S.; Qin, Y. Fog computing security: A review of current applications and security solutions. J. Cloud Comput. 2017, 6, 19. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X.S. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 601–628. [Google Scholar] [CrossRef]
- Gupta, M.; Sandhu, R. Authorization Framework for Secure Cloud Assisted Connected Cars and Vehicular Internet of Things. In Proceedings of the 23rd ACM on Symposium on Access Control Models and Technologies, Indianapolis, IN, USA, 13–15 June 2018; ACM: New York, NY, USA; pp. 193–204. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile edge computing, Fog et al.: A survey and analysis of security threats and challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All one needs to know about fog computing and related edge computing paradigms: A complete survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Shropshire, J. Extending the cloud with fog: Security challenges & opportunities. In Proceedings of the 20th Americas Conference on Information Systems, AMCIS 2014, Savannah, GA, USA, 7–9 August 2014; pp. 1–10. [Google Scholar]
- Stojmenovic, I.; Wen, S.; Huang, X.; Luan, H. An overview of Fog computing and its security issues. Concurr. Comput. Pract. Exp. 2016, 28, 2991–3005. [Google Scholar] [CrossRef]
- Varghese, B.; Wang, N.; Bermbach, D.; Hong, C.-H.; De Lara, E.; Shi, W.; Stewart, C. A Survey on Edge Performance Benchmarking. ACM Comput. Surv. 2021, 54, 1–33. [Google Scholar] [CrossRef]
- Maheswari, K.; Bhanu, S.S.; Nickolas, S. A Survey on Data Integrity Checking and Enhancing Security for Cloud to Fog Computing. In Proceedings of the 2020 2nd International Conference on Innovative Mechanisms for Industry Applications (ICIMIA), Bangalore, India, 5–7 March 2020; pp. 121–127. [Google Scholar] [CrossRef]
- Tourani, R.; Bos, A.; Misra, S.; Esposito, F. Towards security-as-a-service in multi-access edge. In Proceedings of the 4th ACM/IEEE Symposium on Edge Computing, Arlington, VA, USA, 7–9 November 2019; ACM: New York, NY, USA, 2019; pp. 358–363. [Google Scholar] [CrossRef]
- Caprolu, M.; Di Pietro, R.; Lombardi, F.; Raponi, S. Edge Computing Perspectives: Architectures, Technologies, and Open Security Issues. In Proceedings of the 2019 IEEE International Conference on Edge Computing, EDGE 2019—Part of the 2019 IEEE World Congress on Services, Milan, Italy, 8–13 July 2019; pp. 116–123. [Google Scholar] [CrossRef]
- Ashraf, M.U.; Ilyas, I.; Younas, F. A Roadmap: Towards Security Challenges, Prevention Mechanisms for Fog Computing. In Proceedings of the 2019 International Conference on Electrical, Communication, and Computer Engineering (ICECCE), Swat, Pakistan, 24–25 July 2019; pp. 1–9. [Google Scholar] [CrossRef]
- Subramaniam, P.; Kaur, M.J. Review of Security in Mobile Edge Computing with Deep Learning. In Proceedings of the 2019 Advances in Science and Engineering Technology International Conferences (ASET), Dubai, United Arab Emirates, 26 March–10 April 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Martin, B.A.; Michaud, F.; Banks, D.; Mosenia, A.; Zolfonoon, R.; Irwan, S.; Schrecker, S.; Zao, J.K. OpenFog security requirements and approaches. In Proceedings of the 2017 IEEE Fog World Congress (FWC), Santa Clara, CA, USA, 30 October–1 November 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Lioliou, P.; Lazaridis, G. Security and Privacy in Edge, Fog Computing and Internet of Things Applications: A Review. 2020. Available online: https://d1wqtxts1xzle7.cloudfront.net/63284174/Security_and_Privacy_in_Edge__Fog_Computing_and_Internet_of_Things_applications_A_review20200512-111442-timb6r-libre.pdf?1589288892=&response-content-disposition=inline%3B+filename%3DSecurity_and_Privacy_in_Edge_Fog_Computi.pdf&Expires=1709613571&Signature=Tl90PkqJ1ONhYgA5xciRwsYxK3MQDiLI67T3cpbnoPJIPLP4aTpU5edfpkKuV9GuGDFuceBdpHl8K4ZvZiPG1pIjFymEKTh6iU124Ziitf2zJjEip5o8jdcFavdJii2Zwu7WPrNsee74krrQZHQ3xHjxIVTmS2cMKU~EKSaBsIqB-TXkUkqwTiQ7211P-hWXF-lTQrW2cTopJGlrZhMpTLX-HH2T8meicAmqAhnVTI5dCcF3yuxSm4JCFX6tnhlSwe7Cko0yAyTG0-IBfWN9ww-yLWgA6FQbS4S5X~gMm-fO7GJ2~20Sv2GMlX5L9PQugDsAi5nFKq1qmH2G2Q3wfA__&Key-Pair-Id=APKAJLOHF5GGSLRBV4ZA (accessed on 23 February 2024).
- Kunal, S.; Saha, A.; Amin, R. An overview of cloud-fog computing: Architectures, applications with security challenges. Secur. Priv. 2019, 2, e72. [Google Scholar] [CrossRef]
- Kumari, A.; Tanwar, S.; Tyagi, S.; Kumar, N.; Parizi, R.M.; Choo, K.R. Fog data analytics: A taxonomy and process model. J. Netw. Comput. Appl. 2019, 128, 90–104. [Google Scholar] [CrossRef]
- Guan, Y.; Shao, J.; Wei, G.; Xie, M. Data Security and Privacy in Fog Computing. IEEE Netw. 2018, 32, 106–111. [Google Scholar] [CrossRef]
- Rauf, A.; Shaikh, R.A.; Shah, A. Security and privacy for IoT and fog computing paradigm. In Proceedings of the 2018 15th Learning and Technology Conference (L&T), Jeddah, Saudi Arabia, 25–26 February 2018; pp. 96–101. [Google Scholar] [CrossRef]
- Mukherjee, M.; Matam, R.; Shu, L.; Maglaras, L.; Ferrag, M.A.; Choudhury, N.; Kumar, V. Security and Privacy in Fog Computing: Challenges. IEEE Access 2017, 5, 19293–19304. [Google Scholar] [CrossRef]
- Shirazi, S.N.; Gouglidis, A.; Farshad, A.; Hutchison, D. The extended cloud: Review and analysis of mobile edge computing and fog from a security and resilience perspective. IEEE J. Sel. Areas Commun. 2017, 35, 2586–2595. [Google Scholar] [CrossRef]
- Lee, K.; Kim, D.; Ha, D.; Rajput, U.; Oh, H. On security and privacy issues of fog computing supported Internet of Things environment. In Proceedings of the 2015 6th International Conference on the Network of the Future (NOF), Montreal, QC, Canada, 30 September–2 October 2015; pp. 1–3. [Google Scholar] [CrossRef]
- Hashem, I.A.T.; Yaqoob, I.; Anuar, N.B.; Mokhtar, S.; Gani, A.; Khan, S.U. The rise of “big data” on cloud computing: Review and open research issues. Inf. Syst. 2015, 47, 98–115. [Google Scholar] [CrossRef]
- Dautov, R.; Distefano, S.; Bruneo, D.; Longo, F.; Merlino, G.; Puliafito, A. Data processing in cyber-physical-social systems through edge computing. IEEE Access 2018, 6, 29822–29835. [Google Scholar] [CrossRef]
- Zhang, J.; Ma, M.; He, W.; Wang, P. On-demand deployment for IoT applications. J. Syst. Archit. 2020, 111, 101794. [Google Scholar] [CrossRef]
- Tychalas, D.; Karatza, H. A Scheduling Algorithm for a Fog Computing System with Bag-of-Tasks Jobs: Simulation and Performance Evaluation. Simul. Model. Pract. Theory 2020, 98, 101982. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog computing and its role in the internet of things. In The First Edition of the MCC Workshop on MOBILE Cloud Computing—MCC’12; ACM Press: New York, NY, USA, 2012; p. 13. [Google Scholar] [CrossRef]
- Nikouei, S.Y.; Xu, R.; Nagothu, D.; Chen, Y.; Aved, A.; Blasch, E. Real-Time Index Authentication for Event-Oriented Surveillance Video Query using Blockchain. In Proceedings of the 2018 IEEE International Smart Cities Conference (ISC2), Kansas City, MO, USA, 16–19 September 2018. [Google Scholar]
- Ouyang, Z.; Niu, J.; Ren, T.; Li, Y.; Cui, J.; Wu, J. MBBNet: An edge IoT computing-based traffic light detection solution for autonomous bus. J. Syst. Archit. 2020, 109, 101835. [Google Scholar] [CrossRef]
- Wen, Z.; Yang, R.; Garraghan, P.; Lin, T.; Xu, J.; Rovatsos, M. Fog orchestration for IoT Services: Issues, Challenges and Directions. IEEE Internet Comput. 2017, 21, 16–24. [Google Scholar] [CrossRef]
- Dsouza, C.; Ahn, G.-J.; Taguinod, M. Policy-driven security management for fog computing: Preliminary framework and a case study. In Proceedings of the 2014 IEEE 15th International Conference on Information Reuse and Integration (IEEE IRI 2014), Redwood City, CA, USA, 13–15 August 2014; pp. 16–23. [Google Scholar] [CrossRef]
- Dou, C.; Zhang, S.; Wang, H.; Sun, L.; Huang, Y.; Yue, W. ADHD fMRI short-time analysis method for edge computing based on multi-instance learning. J. Syst. Archit. 2020, 111, 101834. [Google Scholar] [CrossRef]
- Alkawsi, G.; Al-Amri, R.; Baashar, Y.; Ghorashi, S.; Alabdulkreem, E.; Tiong, S.K. Towards lowering computational power in IoT systems: Clustering algorithm for high-dimensional data stream using entropy window reduction. Alex. Eng. J. 2023, 70, 503–513. [Google Scholar] [CrossRef]
- Al-Amri, R.; Murugesan, R.K.; Almutairi, M.; Munir, K.; Alkawsi, G.; Baashar, Y. A Clustering Algorithm for Evolving Data Streams Using Temporal Spatial Hyper Cube. Appl. Sci. 2022, 12, 6523. [Google Scholar] [CrossRef]
- Varghese, B.; Gohil, B.N.; Ray, S.; Vega, S. Research challenges in query processing and data analytics on the edge. In Proceedings of the CASCON 2019 Proceedings—Conference of the Centre for Advanced Studies on Collaborative Research—Proceedings of the 29th Annual International Conference on Computer Science and Software Engineering, Toronto, ON, Canada, 4–6 November 2019; pp. 317–322. [Google Scholar] [CrossRef]
- Bellavista, P.; Berrocal, J.; Corradi, A.; Das, S.K.; Foschini, L.; Zanni, A. A survey on fog computing for the Internet of Things. Pervasive Mob. Comput. 2018, 52, 71–99. [Google Scholar] [CrossRef]
- Brogi, A.; Forti, S.; Guerrero, C.; Lera, I. How to place your apps in the fog: State of the art and open challenges. Softw.—Pract. Exp. 2020, 50, 719–740. [Google Scholar] [CrossRef]
- Shruti; Rani, S.; Srivastava, G. Secure hierarchical fog computing-based architecture for industry 5.0 using an attribute-based encryption scheme. Expert Syst. Appl. 2024, 235, 121180. [Google Scholar] [CrossRef]
- Mamatas, L.; Demiroglou, V.; Kalafatidis, S.; Skaperas, S.; Tsaoussidis, V. Protocol-Adaptive Strategies for Wireless Mesh Smart City Networks. IEEE Netw. 2023, 37, 136–143. [Google Scholar] [CrossRef]
- Jumani, A.K.; Shi, J.; Laghari, A.A.; Hu, Z.; Nabi, A.U.; Qian, H. Fog computing security: A review. Secur. Priv. 2023, 6, e313. [Google Scholar] [CrossRef]
- Ali, M.; Naeem, F.; Kaddoum, G.; Hossain, E. Metaverse Communications, Networking, Security, and Applications: Research Issues, State-of-the-Art, and Future Directions. In IEEE Communications Surveys & Tutorials; IEEE: Piscataway, NJ, USA, 2023; p. 1. [Google Scholar] [CrossRef]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of fog computing: Fundamental, network applications, and research challenges. In IEEE Communications Surveys and Tutorials; IEEE: Piscataway, NJ, USA, 2018; Volume 20, pp. 1826–1857. [Google Scholar] [CrossRef]
- Katal, A.; Dahiya, S.; Choudhury, T. Energy efficiency in cloud computing data centers: A survey on software technologies. Clust. Comput. 2023, 26, 1845–1875. [Google Scholar] [CrossRef]
- Bhushan, B.; Sahoo, G.; Rai, A.K. Man-in-the-middle attack in wireless and computer networking—A review. In Proceedings of the 2017 3rd International Conference on Advances in Computing, Communication \& Automation (ICACCA)(Fall), Dehradun, India, 15–16 September 2017; pp. 1–6. [Google Scholar]
- de Kok, J.W.T.M.; de la Hoz, M.A.; de Jong, Y.; Brokke, V.; Elbers, P.W.G.; Thoral, P.; Castillejo, A.; Trenor, T.; Castellano, J.M.; Bronchalo, A.E.; et al. A guide to sharing open healthcare data under the General Data Protection Regulation. Sci. Data 2023, 10, 404. [Google Scholar] [CrossRef]
- Kafi, A.; Akter, N. Securing Financial Information in the Digital Realm: Case Studies in Cybersecurity for Accounting Data Protection. Am. J. Trade Policy 2023, 10, 15–26. [Google Scholar] [CrossRef]
- Ahmed, S.F.; Bin Alam, S.; Afrin, S.; Rafa, S.J.; Rafa, N.; Gandomi, A.H. Insights into Internet of Medical Things (IoMT): Data fusion, security issues and potential solutions. Inf. Fusion 2024, 102, 102060. [Google Scholar] [CrossRef]
- Papagiannidis, E.; Mikalef, P.; Conboy, K.; Van de Wetering, R. Uncovering the dark side of AI-based decision-making: A case study in a B2B context. Ind. Mark. Manag. 2023, 115, 253–265. [Google Scholar] [CrossRef]
- Viswanathan, S.B.; Singh, G. Advancing Financial Operations: Leveraging Knowledge Graph for Innovation. Int. J. Comput. Trends Technol. 2023, 71, 51–60. [Google Scholar] [CrossRef]
- Schultz, E. A framework for understanding and predicting insider attacks. Comput. Secur. 2002, 21, 526–531. [Google Scholar] [CrossRef]
- Gunasekhar, T.; Rao, K.T.; Basu, M.T. Understanding insider attack problem and scope in cloud. In Proceedings of the 2015 International Conference on Circuits, Power and Computing Technologies [ICCPCT-2015], Nagercoil, India, 19–20 March 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Phukan, J.; Li, K.F.; Gebali, F. Hardware covert attacks and countermeasures. In Proceedings of the 2016 IEEE 30th International Conference on Advanced Information Networking and Applications (AINA), Crans-Montana, Switzerland, 23–25 March 2016; pp. 1051–1054. [Google Scholar] [CrossRef]
- Gomez-Barrero, M.; Galbally, J.; Tome, P.; Fierrez, J. On the vulnerability of iris-based systems to a software attack based on a genetic algorithm. In Proceedings of the 17th Iberoamerican Congress, CIARP 2012, Buenos Aires, Argentina, 3–6 September 2012; pp. 114–121. [Google Scholar] [CrossRef]
- Martinez-Diaz, M.; Fierrez, J.; Galbally, J.; Ortega-Garcia, J. An evaluation of indirect attacks and countermeasures in fingerprint verification systems. Pattern Recognit. Lett. 2011, 32, 1643–1651. [Google Scholar] [CrossRef]
- Hoque, N.; Bhuyan, M.H.; Baishya, R.; Bhattacharyya, D.; Kalita, J. Network attacks: Taxonomy, tools and systems. J. Netw. Comput. Appl. 2014, 40, 307–324. [Google Scholar] [CrossRef]
- Kronabeter, A.; Fenz, S. Cloud Security and Privacy in the Light of the 2012 EU Data Protection Regulation. In Proceedings of the Third International Conference, CloudComp 2012, Vienna, Austria, 24–26 September 2012; pp. 114–123. [Google Scholar] [CrossRef]
- Jeun, I.; Lee, Y.; Won, D. A Practical Study on Advanced Persistent Threats. In Proceedings of the International Conferences, SecTech, CA, CES3 2012, Jeju Island, Republic of Korea, 28 November–2 December 2012; pp. 144–152. [Google Scholar] [CrossRef]
- Claycomb, W.R.; Nicoll, A. Insider threats to cloud computing: Directions for new research challenges. In Proceedings of the International Computer Software and Applications Conference, Izmir, Turkey, 16–20 July 2012; pp. 387–394. [Google Scholar] [CrossRef]
- Aslam, M.; Mohsin, B.; Nasir, A.; Raza, S. FoNAC—An automated Fog Node Audit and Certification scheme. Comput. Secur. 2020, 93, 101759. [Google Scholar] [CrossRef]
- Guo, W.; Chen, Y. An Improved Dendritic Cell Algorithm Based Intrusion Detection System for Wireless Sensor Networks. Int. J. Secur. Its Appl. 2017, 11, 11–26. [Google Scholar] [CrossRef]
- Yu, Z.; Au, M.H.; Xu, Q.; Yang, R.; Han, J. Towards leakage-resilient fine-grained access control in fog computing. Future Gener. Comput. Syst. 2018, 78, 763–777. [Google Scholar] [CrossRef]
- Okafor, K.; Anulika, J.; Ononiwu, G. Vulnerability Bandwidth Depletion Attack on Distributed Cloud Computing Network: A QoS Perspective. Int. J. Comput. Appl. 2016, 138, 18–30. [Google Scholar] [CrossRef]
- Hoyhtya, M.; Huusko, J.; Kiviranta, M.; Solberg, K.; Rokka, J. Connectivity for autonomous ships: Architecture, use cases, and research challenges. In Proceedings of the 2017 International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Republic of Korea, 18–20 October 2017; pp. 345–350. [Google Scholar] [CrossRef]
- Jhaveri, R.H.; Patel, S.J.; Jinwala, D.C. DoS attacks in mobile ad hoc networks: A survey. In Proceedings of the 2012 2nd International Conference on Advanced Computing and Communication Technologies, ACCT 2012, Rohtak, India, 7–8 January 2012; pp. 535–541. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N. Machine Learning Models for Secure Data Analytics: A taxonomy and threat model. Comput. Commun. 2020, 153, 406–440. [Google Scholar] [CrossRef]
- Tu, S.; Waqas, M.; Rehman, S.U.; Aamir, M.; Rehman, O.U.; Jianbiao, Z.; Chang, C.-C. Security in Fog Computing: A Novel Technique to Tackle an Impersonation Attack. IEEE Access 2018, 6, 74993–75001. [Google Scholar] [CrossRef]
- Yuan, S.; Stewart, D. Protection of optical networks against interchannel eavesdropping and jamming attacks. In Proceedings of the 2014 International Conference on Computational Science and Computational Intelligence, CSCI 2014, Las Vegas, NV, USA, 10–13 March 2014; pp. 34–38. [Google Scholar] [CrossRef]
- Kumar, V.; Sharma, A.; Mitali, V.K.; Sharma, A. A survey on various cryptography techniques. Int. J. Emerg. Trends Technol. Comput. Sci. IJETTCS 2014, 3, 307–312. [Google Scholar]
- Xia, S.; Li, N.; Xiaofeng, T.; Fang, C. Multiple Attributes Based Spoofing Detection Using an Improved Clustering Algorithm in Mobile Edge Network. In Proceedings of the 2018 1st IEEE International Conference on Hot Information-Centric Networking (HotICN), Shenzhen, China, 15–17 August 2018; pp. 242–243. [Google Scholar] [CrossRef]
- Mohammadi, P.; Ghaffari, A. Defending Against Flooding Attacks in Mobile Ad-Hoc Networks Based on Statistical Analysis. Wirel. Pers. Commun. 2019, 106, 365–376. [Google Scholar] [CrossRef]
- Paharia, B.; Bhushan, K. A comprehensive review of distributed denial of service (DDoS) attacks in fog computing environment. In Handbook of Computer Networks and Cyber Security; Springer: Berlin/Heidelberg, Germany, 2019. [Google Scholar] [CrossRef]
- Rajadurai, H.; Gandhi, U.D. Fuzzy Based Collaborative Verification System for Sybil Attack Detection in MANET. Wirel. Pers. Commun. 2020, 110, 2179–2193. [Google Scholar] [CrossRef]
- Vasudeva, A.; Sood, M. Survey on sybil attack defense mechanisms in wireless ad hoc networks. J. Netw. Comput. Appl. 2018, 120, 78–118. [Google Scholar] [CrossRef]
- Srirama, S.N. A decade of research in fog computing: Relevance, challenges, and future directions. Softw.-Pract. Exp. 2024, 54, 3–23. [Google Scholar] [CrossRef]
- Hartmann, M.; Hashmi, U.S.; Imran, A. Edge computing in smart health care systems: Review, challenges, and research directions. Trans. Emerg. Telecommun. Technol. 2019, 33, e3710. [Google Scholar] [CrossRef]
- Brochado, Â.F.; Rocha, E.M.; Costa, D. A Modular IoT-Based Architecture for Logistics Service Performance Assessment and Real-Time Scheduling towards a Synchromodal Transport System. Sustainability 2024, 16, 742. [Google Scholar] [CrossRef]
- Ray, P.P.; Dash, D.; De, D. Edge computing for Internet of Things: A survey, e-healthcare case study and future direction. J. Netw. Comput. Appl. 2019, 140, 1–22. [Google Scholar] [CrossRef]
- Singh, P.; Kaur, R. An integrated fog and Artificial Intelligence smart health framework to predict and prevent COVID-19. Glob. Transit. 2020, 2, 283–292. [Google Scholar] [CrossRef]
- Hammoud, A.; Sami, H.; Mourad, A.; Otrok, H.; Mizouni, R.; Bentahar, J. AI, Blockchain, and Vehicular Edge Computing for Smart and Secure IoV: Challenges and Directions. IEEE Internet Things Mag. 2020, 3, 68–73. [Google Scholar] [CrossRef]
- Sood, S.K.; Mahajan, I. Wearable IoT sensor-based healthcare system for identifying and controlling chikungunya virus. Comput. Ind. 2017, 91, 33–44. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Mohamed, M. RETRACTED: A novel and powerful framework based on neutrosophic sets to aid patients with cancer. Future Gener. Comput. Syst. 2019, 98, 144–153. [Google Scholar] [CrossRef]
- Bhosale, K.S.; Nenova, M.; Iliev, G. A study of cyber attacks: In the healthcare sector. In Proceedings of the 2021 Sixth Junior Conference on Lighting (Lighting), Gabrovo, Bulgaria, 23–25 September 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Queralta, J.P.; Gia, T.N.; Tenhunen, H.; Westerlund, T. Edge-AI in LoRa-based health monitoring: Fall detection system with fog computing and LSTM recurrent neural networks. In Proceedings of the 2019 42nd International Conference on Telecommunications and Signal Processing, TSP 2019, Budapest, Hungary, 1–3 July 2019; pp. 601–604. [Google Scholar] [CrossRef]
- Cao, Y.; Chen, S.; Hou, P.; Brown, D. FAST: A fog computing assisted distributed analytics system to monitor fall for stroke mitigation. In Proceedings of the 2015 IEEE International Conference on Networking, Architecture and Storage, NAS 2015, Boston, MA, USA, 6–7 August 2015; pp. 2–11. [Google Scholar] [CrossRef]
- Kraemer, F.A.; Braten, A.E.; Tamkittikhun, N.; Palma, D. Fog Computing in Healthcare–A Review and Discussion. IEEE Access 2017, 5, 9206–9222. [Google Scholar] [CrossRef]
- Kyriazakos, S.; Mihaylov, M.; Anggorojati, B.; Mihovska, A.; Craciunescu, R.; Fratu, O.; Prasad, R. eWALL: An Intelligent Caring Home Environment Offering Personalized Context-Aware Applications Based on Advanced Sensing. Wirel. Pers. Commun. 2016, 87, 1093–1111. [Google Scholar] [CrossRef]
- Ahmad, M.; Amin, M.B.; Hussain, S.; Kang, B.H.; Cheong, T.; Lee, S. Health Fog: A novel framework for health and wellness applications. J. Supercomput. 2016, 72, 3677–3695. [Google Scholar] [CrossRef]
- Osama, M.; Ateya, A.A.; Sayed, M.S.; Hammad, M.; Pławiak, P.; Abd El-Latif, A.A.; Elsayed, R.A. Internet of Medical Things and Healthcare 4.0: Trends, Requirements, Challenges, and Research Directions. Sensors 2023, 23, 7435. [Google Scholar] [CrossRef] [PubMed]
- Al Ameen, M.; Liu, J.; Kwak, K. Security and Privacy Issues in Wireless Sensor Networks for Healthcare Applications. J. Med. Syst. 2012, 36, 93–101. [Google Scholar] [CrossRef] [PubMed]
- Sethuraman, S.C.; Vijayakumar, V.; Walczak, S. Cyber Attacks on Healthcare Devices Using Unmanned Aerial Vehicles. J. Med. Syst. 2020, 44, 29. [Google Scholar] [CrossRef] [PubMed]
- Ning, Z.; Huang, J.; Wang, X. Vehicular Fog Computing: Enabling Real-Time Traffic Management for Smart Cities. IEEE Wirel. Commun. 2019, 26, 87–93. [Google Scholar] [CrossRef]
- Shafiq, H.; Rehman, R.A.; Kim, B.-S. Services and Security Threats in SDN Based VANETs: A Survey. Wirel. Commun. Mob. Comput. 2018, 2018, 8631851. [Google Scholar] [CrossRef]
- Nobre, J.C.; de Souza, A.M.; Rosário, D.; Both, C.; Villas, L.A.; Cerqueira, E.; Braun, T.; Gerla, M. Vehicular software-defined networking and fog computing: Integration and design principles. Ad Hoc Netw. 2019, 82, 172–181. [Google Scholar] [CrossRef]
- Wu, Q.; Shen, J.; Yong, B.; Wu, J.; Li, F.; Wang, J.; Zhou, Q. Smart fog-based workflow for traffic control networks. Future Gener. Comput. Syst. 2019, 97, 825–835. [Google Scholar] [CrossRef]
- Bariah, L.; Shehada, D.; Salahat, E.; Yeun, C.Y. Recent advances in VANET security: A survey. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference, VTC Fall 2015, Boston, MA, USA, 6–9 September 2015. [Google Scholar] [CrossRef]
- Verma, K.; Hasbullah, H.; Kumar, A. Prevention of DoS Attacks in VANET. Wirel. Pers. Commun. 2013, 73, 95–126. [Google Scholar] [CrossRef]
- Nkenyereye, L.; Liu, C.H.; Song, J. Towards secure and privacy preserving collision avoidance system in 5G fog-based Internet of Vehicles. Future Gener. Comput. Syst. 2019, 95, 488–499. [Google Scholar] [CrossRef]
- Engoulou, R.G.; Bellaïche, M.; Pierre, S.; Quintero, A. VANET security surveys. Comput. Commun. 2014, 44, 1–13. [Google Scholar] [CrossRef]
- Al-Amri, R.; Murugesan, R.K.; Alshari, E.M.; Alhadawi, H.S. Toward a Full Exploitation of IoT in Smart Cities: A Review of IoT Anomaly Detection Techniques. Lect. Notes Netw. Syst. 2022, 322, 193–214. [Google Scholar] [CrossRef]
- Nasir, M.; Muhammad, K.; Lloret, J.; Sangaiah, A.K.; Sajjad, M. Fog computing enabled cost-effective distributed summarization of surveillance videos for smart cities. J. Parallel Distrib. Comput. 2019, 126, 161–170. [Google Scholar] [CrossRef]
- Firdous, S.N.; Baig, Z.; Valli, C.; Ibrahim, A. Modelling and evaluation of malicious attacks against the IoT MQTT protocol. In Proceedings of the 2017 IEEE International Conference on Internet of Things, IEEE Green Computing and Communications, IEEE Cyber, Physical and Social Computing, IEEE Smart Data, iThings-GreenCom-CPSCom-SmartData 2017, Exeter, UK, 21–23 June 2017; pp. 748–755. [Google Scholar] [CrossRef]
- Nazmudeen, M.S.H.; Wan, A.T.; Buhari, S.M. Improved throughput for Power Line Communication (PLC) for smart meters using fog computing based data aggregation approach. In Proceedings of the IEEE 2nd International Smart Cities Conference: Improving the Citizens Quality of Life, ISC2 2016, Trento, Italy, 12–15 September 2016; pp. 3–6. [Google Scholar] [CrossRef]
- Ben-Shakhar, G. A survey of attacks and countermeasures in mobile ad hoc networks. In Memory Detection: Theory and Application of the Concealed Information Test; Cambridge University Press: Cambridge, UK, 2011; pp. 200–214. [Google Scholar] [CrossRef]
- Mukta, M.Y.; Rahman, M.A.; Asyhari, A.T.; Bhuiyan, M.Z.A. IoT for energy efficient green highway lighting systems: Challenges and issues. J. Netw. Comput. Appl. 2020, 158, 102575. [Google Scholar] [CrossRef]
- Jin, D.; Hannon, C.; Li, Z.; Cortes, P.; Ramaraju, S.; Burgess, P.; Buch, N.; Shahidehpour, M. Smart Street lighting system: A platform for innovative smart city applications and a new frontier for cyber-security. Electr. J. 2016, 29, 28–35. [Google Scholar] [CrossRef]
- Tang, B.; Chen, Z.; Hefferman, G.; Pei, S.; Wei, T.; He, H.; Yang, Q. Incorporating Intelligence in Fog Computing for Big Data Analysis in Smart Cities. IEEE Trans. Ind. Inform. 2017, 13, 2140–2150. [Google Scholar] [CrossRef]
- Cerina, L.; Notargiacomo, S.; Paccanit, M.G.; Santambrogio, M.D. A fog-computing architecture for preventive healthcare and assisted living in smart ambients. In Proceedings of the 2017 IEEE 3rd International Forum on Research and Technologies for Society and Industry (RTSI), Modena, Italy, 11–13 September 2017. [Google Scholar] [CrossRef]
- Rahmani, A.M.; Gia, T.N.; Negash, B.; Anzanpour, A.; Azimi, I.; Jiang, M.; Liljeberg, P. Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: A fog computing approach. Future Gener. Comput. Syst. 2018, 78, 641–658. [Google Scholar] [CrossRef]
- Alsafery, W.; Alturki, B.; Reiff-Marganiec, S.; Jambi, K. Smart Car Parking System Solution for the Internet of Things in Smart Cities. In Proceedings of the 1st International Conference on Computer Applications and Information Security, ICCAIS 2018, Riyadh, Saudi Arabia, 4–6 April 2018. [Google Scholar] [CrossRef]
- Aliyu, F.; Sheltami, T.; Shakshuki, E.M. A Detection and Prevention Technique for Man in the Middle Attack in Fog Computing. Procedia Comput. Sci. 2018, 141, 24–31. [Google Scholar] [CrossRef]
- Stojmenovic, I. Fog computing: A cloud to the ground support for smart things and machine-to-machine networks. In Proceedings of the 2014 Australasian Telecommunication Networks and Applications Conference (ATNAC), Southbank, Australia, 26–28 November 2014; pp. 117–122. [Google Scholar]
- Srividhya, S.; Sankaranarayanan, S. IoT–Fog Enabled Framework for Forest Fire Management System. In Proceedings of the 2020 Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 273–276. [Google Scholar] [CrossRef]
- Pacheco, J.; Benitez, V.H.; Felix-Herran, L.C.; Satam, P. Artificial Neural Networks-Based Intrusion Detection System for Internet of Things Fog Nodes. IEEE Access 2020, 8, 73907–73918. [Google Scholar] [CrossRef]
- Li, G.; Wu, S.X.; Zhang, S.; Li, Q. Neural Networks-Aided Insider Attack Detection for the Average Consensus Algorithm. IEEE Access 2020, 8, 51871–51883. [Google Scholar] [CrossRef]
- Farjana, N.; Roy, S.; Mahi, M.J.N.; Whaiduzzaman, M. An Identity-Based Encryption Scheme for Data Security in Fog Computing. In Studies in Computational Intelligence; Uddin, M.S., Bansal, J.C., Eds.; Algorithms for Intelligent Systems; Springer: Singapore, 2020; Volume 669, pp. 215–226. [Google Scholar] [CrossRef]
- Hou, S.; Li, H.; Yang, C.; Wang, L. A New Privacy-Preserving Framework based on Edge-Fog-Cloud Continuum for Load Forecasting. In Proceedings of the 2020 IEEE Wireless Communications and Networking Conference (WCNC), Seoul, Republic of Korea, 25–28 May 2020. [Google Scholar] [CrossRef]
- Amin, R.; Kunal, S.; Saha, A.; Das, D.; Alamri, A. CFSec: Password based secure communication protocol in cloud-fog environment. J. Parallel Distrib. Comput. 2020, 140, 52–62. [Google Scholar] [CrossRef]
- Singh, S.; Kumari, K.; Gupta, S.; Dua, A.; Kumar, N. Detecting different attack instances of ddos vulnerabilities on edge network of fog computing using gaussian naive bayesian classifier. In Proceedings of the 2020 IEEE International Conference on Communications Workshops, ICC Workshops, Dublin, Ireland, 7–11 June 2020. [Google Scholar] [CrossRef]
- Khalid, T.; Khan, A.N.; Ali, M.; Adeel, A.; Khan, A.U.R.; Shuja, J. A fog-based security framework for intelligent traffic light control system. Multimed. Tools Appl. 2018, 78, 24595–24615. [Google Scholar] [CrossRef]
- Xiao, J.; Kou, P. A hierarchical distributed fault diagnosis system for hydropower plant based on fog computing. In Proceedings of the 2017 IEEE 2nd Information Technology, Networking, Electronic and Automation Control Conference, ITNEC 2017, Chengdu, China, 15–17 December 2017; pp. 1138–1142. [Google Scholar] [CrossRef]
- Ben Amor, A.; Abid, M.; Meddeb, A. A Privacy-Preserving Authentication Scheme in an Edge-Fog Environment. In Proceedings of the 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, Tunisia, 30 October–3 November 2017; pp. 1225–1231. [Google Scholar] [CrossRef]
- Sohal, A.S.; Sandhu, R.; Sood, S.K.; Chang, V. A cybersecurity framework to identify malicious edge device in fog computing and cloud-of-things environments. Comput. Secur. 2018, 74, 340–354. [Google Scholar] [CrossRef]
- Bazm, M.-M.; Lacoste, M.; Sudholt, M.; Menaud, J.-M. Secure Distributed computing on untrusted fog infrastructures using trusted linux containers. In Proceedings of the International Conference on Cloud Computing Technology and Science, CloudCom, Nicosia, Cyprus, 10–13 December 2018; pp. 239–242. [Google Scholar] [CrossRef]
- Deepali; Bhushan, K. DDoS attack mitigation and resource provisioning in cloud using fog computing. In Proceedings of the 2017 International Conference on Smart Technology for Smart Nation, SmartTechCon 2017, Bengaluru, India, 17–19 August 2017; pp. 308–313. [Google Scholar] [CrossRef]
- Sharma, S. Data theft prevention using user behavior profiling and decoy documents. In Proceedings of the 2017 International Conference on Smart Technologies for Smart Nation (SmartTechCon), Bengaluru, India, 17–19 August 2017; pp. 957–961. [Google Scholar] [CrossRef]
- Rebahi, Y.; Catal, F.; Tcholtchev, N.; Maedje, L.; Alkhateeb, O.; Elangovan, V.K.; Apostolakis, D. Towards Accelerating Intrusion Detection Operations at the Edge Network using FPGAs. In Proceedings of the 2020 5th International Conference on Fog and Mobile Edge Computing, FMEC 2020, Paris, France, 20–23 April 2020; pp. 104–111. [Google Scholar] [CrossRef]
- de Souza, C.A.; Westphall, C.B.; Machado, R.B.; Sobral, J.B.M.; Vieira, G.d.S. Hybrid approach to intrusion detection in fog-based IoT environments. Comput. Netw. 2020, 180, 107417. [Google Scholar] [CrossRef]
- Almiani, M.; AbuGhazleh, A.; Al-Rahayfeh, A.; Atiewi, S.; Razaque, A. Deep recurrent neural network for IoT intrusion detection system. Simul. Model. Pract. Theory 2020, 101, 102031. [Google Scholar] [CrossRef]
- Sharma, S.K.; Wang, X. Live Data Analytics with Collaborative Edge and Cloud Processing in Wireless IoT Networks. IEEE Access 2017, 5, 4621–4635. [Google Scholar] [CrossRef]
- Wang, T.; Zhang, G.; Liu, A.; Alam Bhuiyan, Z.; Jin, Q. A Secure IoT Service Architecture with an Efficient Balance Dynamics Based on Cloud and Edge Computing. IEEE Internet Things J. 2019, 6, 4831–4843. [Google Scholar] [CrossRef]
- Lakshminarayana, D.H.; Philips, J.; Tabrizi, N. A survey of intrusion detection techniques. In Proceedings of the 18th IEEE International Conference on Machine Learning and Applications, ICMLA 2019, Boca Raton, FL, USA, 16–19 December 2019; pp. 1122–1129. [Google Scholar] [CrossRef]
- Modi, C.; Patel, D.; Borisaniya, B.; Patel, H.; Patel, A.; Rajarajan, M. A survey of intrusion detection techniques in Cloud. J. Netw. Comput. Appl. 2013, 36, 42–57. [Google Scholar] [CrossRef]
- Konorski, J.; Szott, S. Modeling a Traffic Remapping Attack Game in a Multi-Hop Ad Hoc Network. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Al-amri, R.; Murugesan, R.K.; Man, M.; Abdulateef, A.F.; Al-Sharafi, M.A.; Alkahtani, A.A. A Review of Machine Learning and Deep Learning Techniques for Anomaly Detection in IoT Data. Appl. Sci. 2021, 11, 5320. [Google Scholar] [CrossRef]
- Wu, D.; Yan, J.; Wang, H.; Wang, R. Multiattack intrusion detection algorithm for edge-assisted internet of things. In Proceedings of the IEEE International Conference on Industrial Internet Cloud, ICII 2019, Orlando, FL, USA, 11–12 November 2019; pp. 210–218. [Google Scholar] [CrossRef]
- Yuen, T.H.; Susilo, W.; Mu, Y. How to construct identity-based signatures without the key escrow problem. Int. J. Inf. Secur. 2010, 9, 297–311. [Google Scholar] [CrossRef]
- Narayanan, A.; Shmatikov, V. Fast dictionary attacks on passwords using time-space tradeoff. In Proceedings of the ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 7–11 November 2005; pp. 364–372. [Google Scholar] [CrossRef]
- Karthikeyan, R.; Geetha, T.; Vijayalakshmi, S. Honeypots for Network Security. Int. J. Res. Dev. Technol. 2017, 7, 62–66. [Google Scholar]
- Bazm, M.-M.; Lacoste, M.; Sudholt, M.; Menaud, J.-M. Side-channels beyond the cloud edge: New isolation threats and solutions. In Proceedings of the 2017 1st Cyber Security in Networking Conference (CSNet), Rio de Janeiro, Brazil, 18–20 October 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Mahadevappa, P.; Murugesan, R.K. Study of Container-Based Virtualisation and Threats in Fog Computing. In Proceedings of the Second International Conference, ACeS 2020, Penang, Malaysia, 8–9 December 2020; Abdullah, A.N., Manickam, S., Eds.; Communications in Computer and Information Science. Springer: Singapore, 2021; Volume 1347, pp. 535–549. [Google Scholar] [CrossRef]
- Rahbari-Asr, N.; Ojha, U.; Zhang, Z.; Chow, M.-Y. Incremental Welfare Consensus Algorithm for Cooperative Distributed Generation/Demand Response in Smart Grid. IEEE Trans. Smart Grid 2014, 5, 2836–2845. [Google Scholar] [CrossRef]
- Sha, K.; Yang, T.A.; Wei, W.; Davari, S. A survey of edge computing-based designs for IoT security. Digit. Commun. Netw. 2020, 6, 195–202. [Google Scholar] [CrossRef]
- Ahmadi, S. Security Implications of Edge Computing in Cloud Networks. J. Comput. Commun. 2024, 12, 26–46. [Google Scholar] [CrossRef]
- Makitalo, N.; Ometov, A.; Kannisto, J.; Andreev, S.; Koucheryavy, Y.; Mikkonen, T. Safe, Secure Executions at the Network Edge: Coordinating Cloud, Edge, and Fog Computing. IEEE Softw. 2017, 35, 30–37. [Google Scholar] [CrossRef]
- Javadpour, A.; Wang, G.; Rezaei, S. Resource Management in a Peer-to-Peer Cloud Network for IoT. Wirel. Pers. Commun. 2020, 115, 2471–2488. [Google Scholar] [CrossRef]
- Zhang, P.; Zhou, M.; Fortino, G. Security and trust issues in Fog computing: A survey. Future Gener. Comput. Syst. 2018, 88, 16–27. [Google Scholar] [CrossRef]
- Mahadevappa, P.; Murugesan, R.K. Review of data integrity attacks and mitigation methods in edge computing. In Proceedings of the Advances in Cyber Security: Third International Conference, ACeS 2021, Penang, Malaysia, 24–25 August 2021; Revised Selected Papers 3. pp. 505–514. [Google Scholar]
- Ren, J.; Zhang, D.; He, S.; Zhang, Y.; Li, T. A survey on end-edge-cloud orchestrated network computing paradigms: Transparent computing, mobile edge computing, fog computing, and cloudlet. ACM Comput. Surv. 2019, 52, 1–36. [Google Scholar] [CrossRef]
- Chatterjee, J.; Das, M.K.; Ghosh, S.; Das, A.; Bag, R. A review on security and privacy concern in IOT health care. Internet Things Healthc. Technol. 2020, 247–271. [Google Scholar]
- Xia, Q.; Ye, W.; Tao, Z.; Wu, J.; Li, Q. A survey of federated learning for edge computing: Research problems and solutions. High-Confid. Comput. 2021, 1, 100008. [Google Scholar] [CrossRef]
- Bonawitz, K.; Eichner, H.; Grieskamp, W.; Huba, D.; Ingerman, A.; Ivanov, V.; Kiddon, C.; Konečný, J.; Mazzocchi, S.; McMahan, H.B.; et al. Towards federated learning at scale: System design. arXiv 2019, arXiv:1902.01046. [Google Scholar]
- Salehi, S.A.; Razzaque, M.A.; Tomeo-Reyes, I.; Hussain, N. IEEE 802.15.6 standard in wireless body area networks from a healthcare point of view. In Proceedings of the Asia-Pacific Conference on Communications, APCC 2016, Yogyakarta, Indonesia, 25–27 August 2016; pp. 523–528. [Google Scholar] [CrossRef]
- Zhang, X.; Cao, X.; Yan, L.; Sung, D.K. A Street-Centric Opportunistic Routing Protocol Based on Link Correlation for Urban VANETs. IEEE Trans. Mob. Comput. 2016, 15, 1586–1599. [Google Scholar] [CrossRef]
- Shen, X.; Cheng, X.; Yang, L.; Zhang, R.; Jiao, B. Data dissemination in VANETs: A scheduling approach. IEEE Trans. Intell. Transp. Syst. 2014, 15, 2213–2223. [Google Scholar] [CrossRef]
- Lau, B.P.L.; Marakkalage, S.H.; Zhou, Y.; Hassan, N.U.; Yuen, C.; Zhang, M.; Tan, U.-X. A survey of data fusion in smart city applications. Inf. Fusion 2019, 52, 357–374. [Google Scholar] [CrossRef]
- Weddell, A.S.; Magno, M.; Merrett, G.V.; Brunelli, D.; Al-hashimi, B.M.; Benini, L. A Survey of Multi-Source Energy Harvesting Systems. In Proceedings of the 2013 Design, Automation & Test in Europe Conference & Exhibition (DATE), Grenoble, France, 18–22 March 2013. [Google Scholar]
- Baktir, A.C.; Ozgovde, A.; Ersoy, C. How Can Edge Computing Benefit from Software-Defined Networking: A Survey, Use Cases, and Future Directions. IEEE Commun. Surv. Tutor. 2017, 19, 2359–2391. [Google Scholar] [CrossRef]
- Liu, D.; Li, Z.; Jia, D. Secure distributed data integrity auditing with high efficiency in 5G-enabled software-defined edge computing. Cyber Secur. Appl. 2023, 1, 100004. [Google Scholar] [CrossRef]
- Bari, F.; Boutaba, R.; Esteves, R.; Granville, L.Z.; Podlesny, M.; Rabbani, G.; Zhang, Q.; Zhani, M.F. Data Center Network Virtualization: A Survey. IEEE Commun. Surv. Tutor. 2013, 15, 909–928. [Google Scholar] [CrossRef]
- Zhang, P.; Chen, Z.; Liu, J.K.; Liang, K.; Liu, H. An efficient access control scheme with outsourcing capability and attribute update for fog computing. Future Gener. Comput. Syst. 2018, 78, 753–762. [Google Scholar] [CrossRef]
- Hernandez-Jaimes, M.L.; Martinez-Cruz, A.; Ramírez-Gutiérrez, K.A.; Feregrino-Uribe, C. Artificial intelligence for IoMT security: A review of intrusion detection systems, attacks, datasets and Cloud–Fog–Edge architectures. Internet Things 2023, 23, 100887. [Google Scholar] [CrossRef]
- Wang, X.; Ren, X.; Qiu, C.; Xiong, Z.; Yao, H.; Leung, V.C. Synergy of Edge Intelligence and Blockchain: A Comprehensive Survey. TechRxiv 2021. [Google Scholar]
- Zhou, Z.; Wan, Y.; Cui, Q.; Yu, K.; Mumtaz, S.; Yang, C.-N.; Guizani, M. Blockchain-Based Secure and Efficient Secret Image Sharing with Outsourcing Computation in Wireless Networks. IEEE Trans. Wirel. Commun. 2023, 23, 423–435. [Google Scholar] [CrossRef]
- Li, J.; Herdem, M.S.; Nathwani, J.; Wen, J.Z. Methods and applications for Artificial Intelligence, Big Data, Internet of Things, and Blockchain in smart energy management. Energy AI 2023, 11, 100208. [Google Scholar] [CrossRef]
| Ref | Solution Approach | Performance | Findings |
|---|---|---|---|
| [125] | Artificial neural network-based IDS | Detects malicious edge nodes based on the node’s profile features. Identifies DoS, flooding, and replay attacks | High accuracy and low false alarm rate. Efficient to maintain the edge network’s resilience by discarding the intruders |
| [126] | Identifies insider attacks using random Gossip Consensus algorithm | Detects insider attacks using edge node’s state information without any supervision | Extensive resource consumption |
| [127] | Hierarchical Identity-Based Encryption Scheme to achieve data security | Four hierarchical layered security keys are used to secure data from the attack | Escrow key problem |
| [128] | Data privacy-preserving scheme based on data load forecasting | Smart meters are used to calculate the workload using the Oblivious Multivariate Polynomial valuation (OMPE) protocol and protect data from unauthorized access | Reduces computational overheads and data load to the cloud |
| [129] | Password-based secure communication protocol for data transmission between cloud and edge devices | Establishes secure communication based on pivotal agreement between user and edge devices. Eavesdropping, data alteration, MITM, impersonation, and malicious insider attacks are restricted | Most of the threats are addressed, and communication channels are secured. However, phishing can be used to easily hack the password |
| [130] | Gaussian Naive Bayesian theorem is used to analyze the packets and identify an intruder | Analyze the network using the Markov model and lure attackers using the Virtual Honeypot method | Attacker can act legitimately and gain access to the Honeypot method |
| [78] | Q-Learning-based reinforcement learning technique to identify impersonation attacks | Detects attack accurately in edge layer. False alarm rate, misdetection rate, and the average error rate are identified using channel state information | Channel state information can be considered to study further attacks, such as DoS, spoofing, jamming, authentication, etc. However, it is not considered in this approach |
| [122] | Intrusion detection and intrusion prevention system | Identifies MITM attack. Interrogates communication channel using Advanced Symmetric Encryption, and exchanges keys using the Diffie–Hellman method | Not suitable for multi-hop attacks |
| [131] | Automated validation of Internet Security Protocols to secure Intelligent Edge-based Transport System | Generates a 64-bit symmetric key or 512-bit asymmetric key to secure communication. It is very complicated for attackers to break this key | It is impractical to assume that all vehicles are legitimate |
| [132] | Fault diagnosis of the hardware components | Case-based reasoning model to classify the fault type for a hydropower plant using storm-based architecture | System-specific application |
| [133] | Anonymous and Secure authentication scheme | Secure cryptographic algorithms are used to establish confidentially, privacy, and mutual authentication among edge nodes | Cryptographic algorithms may increase computational time |
| [134] | Cybersecurity framework to identify a malicious node | Identifies malicious node through Markov model and shifts that node to a Virtual Honeypot device | Efficiently traps the malicious node, but the attacker can act legitimately and gain access to the Honeypot method |
| [135] | Container-based map reduction protocol to secure computation | Hardware-assisted remote attestation mechanism is used to establish trusted containers | Linux containers encapsulate the application and establish trust during execution |
| [136] | The DDoS attack traffic system | Identifies spoofing or infinite false requests and mitigates to avoid power wastage | Challenging to implement during peak traffic |
| [12] | Privacy-preserving model in healthcare applications | Hybrid user profiling is used to identify the attacker and direct toward a decoy message to trap the attacker | The focus is only on multimedia data. It cannot be applied to other data |
| [137] | User profiling to handle data theft | Prototype-based web patterns validate the effectiveness of decoy messages in the edge layer | Decoy data generation is time-consuming |
| [138] | Snort-based Field Programmable Array Intrusion model | Signature-based detection through network traffic monitoring and generates an alert message | Edge networks accelerate at the generic level |
| [139] | A hybrid approach using machine learning | Two-stage detection: (a) identify intrusion using binary detection, and (b) detect and confirm attacks | High precision and recovery rate. Cannot classify the attack precisely |
| [140] | Fully automated IDS using multi-layered recurrent neural network | Detect attacks using traffic analyses engine and multi-layered recurrent neural network | Accurately identifies DoS attacks and works efficiently in real time |
| [106] | Multi-attack IDS | Identifies abnormality using the backpropagation neural network and detects using the radial basis function | Mobile edge nodes assist to achieve high accuracy. Identifies combinations of mixed attacks |
| [81] | Spoofing detection using multichannel attribute | Creates clusters at edge servers using a local heuristics algorithm and identifies spoofing attacks | Clusters are created at close optimal solutions |
| [141] | Live data analytics with collaborative edge and cloud processing | Integrates edge computing and cloud computing to leverage their respective advantages and address the challenges of processing massive amounts of data generated by IoT devices | Resource optimization and efficient data analytics to address the challenges of handling large volumes of data and enhance network performance |
| [142] | Secure IoT service with an efficient balance dynamic based on cloud and edge computing | Creates new parsing templates, prioritize services with stringent demands, and ensures the reliability of IoT data transfer | Enhances trust evaluation mechanisms and collaborative strategies |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mahadevappa, P.; Al-amri, R.; Alkawsi, G.; Alkahtani, A.A.; Alghenaim, M.F.; Alsamman, M. Analyzing Threats and Attacks in Edge Data Analytics within IoT Environments. IoT 2024, 5, 123-154. https://doi.org/10.3390/iot5010007
Mahadevappa P, Al-amri R, Alkawsi G, Alkahtani AA, Alghenaim MF, Alsamman M. Analyzing Threats and Attacks in Edge Data Analytics within IoT Environments. IoT. 2024; 5(1):123-154. https://doi.org/10.3390/iot5010007
Chicago/Turabian StyleMahadevappa, Poornima, Redhwan Al-amri, Gamal Alkawsi, Ammar Ahmed Alkahtani, Mohammed Fahad Alghenaim, and Mohammed Alsamman. 2024. "Analyzing Threats and Attacks in Edge Data Analytics within IoT Environments" IoT 5, no. 1: 123-154. https://doi.org/10.3390/iot5010007
APA StyleMahadevappa, P., Al-amri, R., Alkawsi, G., Alkahtani, A. A., Alghenaim, M. F., & Alsamman, M. (2024). Analyzing Threats and Attacks in Edge Data Analytics within IoT Environments. IoT, 5(1), 123-154. https://doi.org/10.3390/iot5010007









