1. Introduction
Global navigation satellite system (GNSS) receivers are now embedded in our daily lives. The GNSS positioning, navigation, and timing (PVT) services have been used in multiple applications such as aviation, space, mapping, agriculture, military, and many other applications [
1,
2,
3,
4]. The rapidly increasing number of GNSS navigation services has resulted in demands for higher accuracy and increased receiver integrity and reliability. However, one key drawback of GNSS receivers is their vulnerability to a wide variety of interference signals within the GNSS frequency bands [
5].
The definition of interference is a signal that lies within the GNSS band and out-powers the satellite signal, which in turn leads to difficulties in input decoding (jamming) or the induction of intentional false reading (spoofing). There are many types of interference sources including natural, man-made unintentional, and man-made intentional. Therefore, the most suitable noise characterization method is by bandwidth, which can be organized into two categories: narrrowband and broadband (wideband).
Jamming is the intentional interference by the emission of in-band electromagnetic radiations. This in turn blocks the GNSS signal, which is equivalent to a denial-of-service attack. It can use both narrrowband and wideband types of interference. One of the most popular jamming sources is the personal protection device (PPD), which is a jamming signal emitter that aims to disrupt the operation of nearby GNSS systems. Often, such devices are used in vehicles in order to hide their location. One such example is an accident that occurred in 2011 at the Newark International Airport. In November 2009, the local-area augmentation system (LAAS) of the airport installed a ground-based augmentation system (GBAS). However, this system was interrupted by the presence of radio-frequency interference. An investigation was launched and discovered the presence of jamming signals whose power exceeded more than 20 dB of the receiver antenna’s noise, resulting in tracking errors. After a lengthy investigation that reached two years, it was discovered that a truck driver was using a GPS jammer in order to hide the location of the vehicle. It turns out, however, that the jamming device used in this case was able to disrupt the operation of GNSS receivers within a radius of hundreds of meters. This led to the driver being fined more than 30,000 dollars [
6,
7,
8,
9]. Another incident occurred in Hong Kong in 2018, where more than 40 drones fell from the sky during a light show. The Hong Kong Tourism Bond’s Executive Director, Anthony Lau, stated that the reason was a GPS jammer [
7,
10]. In 2019, a jammer set up at a nearby pig farm was blamed for the intermittent GPS signal loss experienced by an aircraft landing at Harbin airport in north-eastern China. According to The
South China Morning Post, the jammer was intended to stop criminal gangs from using drones dropping swine fever-infested packets on the herd, forcing farmers to sell them sick meat at a lower price [
11]. In 2020, a French maker of high-precision GNSS technology claimed that GPS and Galileo signals were being frequently disrupted at their factory. After investigating, the French Radio Frequency Agency (ANFR) discovered the cause of the disturbance was a broadband router installed in a citizen’s adjacent flat. It was found that the malfunctioning router was producing detrimental interference at a frequency of 1581.15 MHz, which is very close to the GPS L1 and Galileo E1 signals at a frequency of 1575.42 MHz [
12].
Figure 1 shows the main concept of the jamming source interfering with an object such as a warship.
Spoofing, on the other hand, is an interference technique that records the real GNSS signal, modifies it, and emits it back as if it was the original signal. This in turn causes the GNSS receiver to make false readings. The re-emitted signal is far more powerful than the original and can easily mask it. Simpler spoofing devices simply change the phase of the GNSS signal, whereas more advanced devices can transmit a specific location. This does not directly cause any harm; however, systems that rely heavily on GNSS navigation can be compromised. This includes goods transportation. Some shipments are secured throughout their journey and are unlocked once the final destination is reached. In such examples, the security systems use the GNSS geo-location in order to identify the location of the load. Spoofing can interfere with the security system, allowing access to the shipment. Other applications such as autopilots use GNSS data for navigation and by spoofing the receiver and can steer the vehicle in the wrong direction. This is especially dangerous since military units such as drones rely on GNSS for navigation.
Figure 2 shows a spoofing attack on the GNSS receiver.
The robustness of a GNSS receiver that has the capability to be protected from unintentional and intentional (jamming) interference is necessary to ensure reliability in GNSS services. Current GPS receivers have begun including anti-jamming algorithms that provide defence against jamming and unwanted interferences [
13]. Current GNSS receivers have RF sections with automatic gain control (AGC) and multi-bit analogue-to-digital converters (ADCs) to provide protection against signal fluctuations and pulsed interference [
14]. Moreover, the direct sequence spread spectrum (DSSS) is used in GNSS receivers to spread the received signal power over a wider bandwidth than the one used for information data. As a result, this spreading of the gain of the receiver reduces the effect caused by the narrowband interference [
15].
However, these techniques are insufficient for applications such as military, aviation, and emergency services that require a high level of reliability. Over the past years, many researchers have detailed the interference effect and mitigations at different stages of the GNSS system, including antennas, low noise amplifier (LNA), AGC, intermediate frequency (IF), signal processing, and time-frequency domain techniques [
16]. Interference increases the effect, which can be observed firstly in the receiver’s RF section, a decrease in AGC, and change in the distribution across ADC. When the interference power is too high, the available carrier-to-noise density ratio
is reduced, degrading the performance of the receiver acquisition and tracking loops [
14,
17]. As the interference exceeds the GNSS systems’ anti-jamming ability, it will degrade the performance and ultimately result in the failure of the system.
There are different types of interferences to be considered, broadly categorised into narrowband and wideband interference. This work addresses narrowband interference sources as wideband interference is generally addressed by multi-antenna beamforming techniques such as Novatel GAJT [
18]. Within narrowband interference, continuous-wave interference (CWI), pulsed CWI, and sweeping interference are the most harmful interference impacting the quality of the received GNSS signals [
17,
19,
20]. Therefore, CWI interference and sweeping interferences will be used in this research to illustrate the effect of the mitigation technique and compare it against other related techniques in the literature.
There is a huge array of algorithms that can improve the GNSS signal. Until recently, such devices were only discussed as theoretical solutions due to their computational costs. In this paper, the proposed interference excision filters were performed using fast Fourier transforms (FFTs), which were used as a powerful interference mitigation method. Furthermore, a novel hardware implementation for this mitigation technique was designed and tested using field programmable gate arrays (FPGAs), preserving the desired performance of GNSS receiver operations such as tracking, acquisition, and navigation against the required hardware resources. Moreover, a comparison between the results of the GNSS software receiver and the GNSS hardware implementation was conducted to demonstrate the proof of concept.
This interference mitigation algorithm was developed with a GPS L1 C/A signal generated by the front-end NSL Stereo at the intermediate frequency of 6.5 MHz, a 3 dB bandwidth of around 2.75 MHz, and frequency sampling at 26 MHz with a 2-bits resolution.
This paper is organized as follows.
Section 2 reviews the recent related research on interference mitigation techniques for GNSS receivers.
Section 3 illustrates the stages of developing the proposed FFT excision mitigation technique by discussing the MATLAB simulations.
Section 4 demonstrates the VHDL hardware implementation stages.
Section 5 discusses and evaluates the simulation results of the hardware implementation using VHDL and the validation stages. Finally,
Section 6 concludes the paper.
2. Related Work
There has been a large amount of progress made not only in GNSS receiver technology but also regarding its application in which they perform relevant functions such as in the field of military, aircraft, maritime, space, and land applications. Furthermore, many studies have investigated the methods of mitigation of GNSS receiver interference. The aim of these studies is to remove or reduce the interference effects on the GNSS receiver and realise the desired carrier-to-noise density ratio . As a result, receiver manufacturers and researchers have investigated different kinds of GNSS interference mitigation techniques.
The first and most widely used method is an adaptive notch filter. A notch or bandstop filter is a good choice for mitigating CW interference in the passband of the GNSS signals. This sort of interference is generally either self-generated or from a fixed source nearby such as a transmitting antenna. Analogue notch filters can be applied at the RF path or digital filters can be employed at the sampled IF signal to provide more flexibility. An adaptive notch filter is able to detect the centre frequency of the interference and adjust the notch filter to match. This can provide a trade-off in terms of power consumption and processing power [
21,
22,
23]. The authors in [
24] present two frequency lock loop (FLL) equivalent models of an adaptive notch filter to detect sweeping jammers: one is standard and the second one is exponential filtering FLLs. They showed that the standard FLL has a better performance regarding the interference than the FLL exponential filter. This research work was extended in [
25] by the proposal of an FLL-equivalent adaptive notch filter (ANF) to mitigate different types of interference. The ANF process consists of three parts. The first part is the adaption unit, which estimates the centre frequency to be removed. The second part is the detection unit, which decides whether to remove any narrowband interference. The third part is the notch filter, which is activated by the detector to process the input signal by suppressing a narrowband frequency around the rejected frequency set by the adaption unit. The drawback of this study is the power consumption issue, as the proposed detection method is based on the output-input power ratio. This detection method results in high-power consumption being efficient for interference mitigation; the stronger the interference is, the higher the suppression power that is required. In [
13], the estimation of the jammer’s frequency band is performed with a Prony estimator instead of FFT/IFFT in order to decrease the complexity of the whole algorithm. The adaptive notch filter shows small performance improvements (~10 dB) at the level of interference that can be tolerated with sweeping continuous-wave (CW) interference. This small improvement is due to the relatively simple implementation of using one or two-pole notch filters, which can only achieve a very limited depth in the null of the notch filter. Similar levels of mitigation can be seen in mass-market receivers as investigated in [
13]. They considered a low level of interference while this paper aimed to achieve greater levels of resistance to interference using higher-order filtering.
The second method is empirical mode decomposition (EMD) and blind source separation (BSS) [
26]. In this method, the signal is decomposed iteratively by interpolating the min and max of the signal and removing this interpolated signal from the original signal. The work published in [
26] developed two-stage algorithms. In the first stage, EMD is used to find the pseudo-periodic signals amid the received signal. This works well for stationary signals. However, nonstationary signals are more complicated, and the use of a second stage is required. The second stage is a blind source separation algorithm (or BSS). The drawback of this stage is that BSS is a complex algorithm (e.g., matrix inversion, determinant), hence requiring a large number of computations. Moreover, this method works with jamming to signal power ratios (JSRs) of up to 45 dB with nonstationary jamming. However, the method starts to be degraded at 50 dB [
26]. To overcome this issue, a suggested solution has been discussed of combining spatial filtering with this technique [
27,
28]. Another solution is to integrate the Kalman filter with this algorithm to estimate the phase/code delay. As a result, this combination may enable processing in the presence of a stronger or higher level of jamming [
26].
The third method is the wavelet filter. Recently, wavelet filters have been implemented to mitigate interference in GNSS as proposed in [
29,
30]. In these references, interference detection is achieved through a time-scale representation of the GNSS-interfered received signal exploiting the wavelet functions. The wavelet transform provides decomposition of a signal by taking advantage of a group of orthogonal local basis functions [
30]. The suppression is observed by the threshold in each wavelet scale. Each coefficient of the wavelet packet decomposition is compared to a predetermined threshold, and it is blanked or clipped when such a threshold is exceeded. Threshold determination is performed according to the required false alarm probability and a statistical characterization of the GNSS signal obtained in an interference-free environment [
29]. However, the results are not compelling, and a wavelet filter would only be suitable for specific high-grade receivers because of the processing time and high complexity.
The fourth method is zero-memory non-linearity. This algorithm, which is also called complex signum non-linearity, is another statistical approach, derived from the Laplace distribution. These techniques mitigate the interference by generalising the correlation process. This is achieved by extracting the sign of each sample, resulting in +1 for positive values and −1 for negative values. The major advantage of this algorithm is that no signal estimation is required as it is often the weak point in many interference mitigation techniques. This also implies that no settings are required for the optimal operation of the filter. In addition, the algorithm is relatively efficient when it comes to computational costs. In fact, it only works if part of the samples is affected by the interference (pulsed jamming); therefore, it cannot mitigate continuous jamming [
31].
The fifth method is pulse blanking, which is a widely used technique in mitigating the pulsed interference of GNSS receivers due to its simplicity and effectiveness. Pulse blanking (PB) uses the zeroing techniques of the received signal sample that is affected by the interferences [
32]. PB is a pre-correlation mitigation technique and it is applied to the down-converted signal before the correlation process. The disturbing signal is removed by zeroing the samples corrupted by the interference pulses. In order to accomplish this, it is important to determine the pulse position. The techniques that are used to estimate the pulse position are ideal blanking and thresholding [
32]. However, this method works with a combination of automatic gain control (AGC). AGC should be reduced in the case of no existing interference. Otherwise, this technique will remove parts of the original signal. This technique can be used in combination with other techniques to address the specific problem of pulsed interference.
The sixth method is the fast Fourier transform (FFT) filter. FFT excision is a powerful tool for detection and interference removal. The ability to modify the received spectrum allows for rapid and efficient removal of jammers with different characteristics (bandwidth, frequency, pulsed, sweeping rate) compared to other algorithms [
33,
34]. Additionally, it has the ability to act on multiple jamming sources and can even be used as an equalization filter of the receiver’s RF front-end biases. The performance of transform domain interference suppression in GNSS receivers based on fractional Fourier transform (FrFT) with an adaptive threshold was presented in [
34]. However, the limitation of their proposed algorithm is the adaptive selected threshold, which was unable to handle a wide bandwidth of interference. As a result, this distorts the desired signal when spectral components suppress the interference. The results of the proposed algorithm worked with up to 45 dB (
J/No) of the CW jammer. On the other hand, our proposed FFT mitigation algorithm works with wideband interference and the results demonstrated that our algorithm has the capability to suppress more than 100 dB (J/No) of the CW jammer without distortion of the original signal. The disadvantage of the FFT excision has been related to the complexity of the implementation in the receiver hardware. However, efficient computation of FFTs is now common in almost all receiver architectures and possible in low-power ASICs for the mass-market [
35]. The hardware implementation of interference mitigation using FFT algorithms has not been extensively explored in the literature. It can be deduced from the literature review that the current studies have focused on interference mitigation algorithms in terms of software simulations and only a few studies have focused on hardware implementations. In [
36], the authors proposed a high-rate DFT-based data manipulator (HDDM) algorithm with different FPGA-based GNSS dual-band receivers. These receivers were pre-selected based on the number of bits ADC. They used 4, 8, and 14 bits ADC. This algorithm only works against the pulsed interference, with suppression of 50 dB JSR. However, HDDM has shown disappointing results for simple CW interference due to its limited selectivity of frequency and limited robustness of HDDM. The authors mentioned that to overcome this challenge, a notch filter has to be combined with the HDDM algorithm. This research work is extended in [
37] by suggesting HDDM with AGC instead of pulse blanking (PB) to overcome the challenge of removing parts of the signal in the presence of wideband noise interference. HDDM-AGC has real-time FPGA implemented on a wideband receiver. The limitation of this study is the test setup by 1-bit DAC used by the R&S up-converter. This introduces a significant quantization loss, which results in a
loss of 6 dB.
Therefore, the main aim of this paper was to assess the complexity and feasibility of the FFT excision filter implementation in current FPGA technology. Additionally, we aimed to overcome the challenges encountered in the previous research. The proposed FFT excision filter algorithm has the capability to work with different types of GNSS interference such as narrrowband interference, wideband interference, CW interference, pulsed CW interference, and sweeping interference. The estimation of jammer characteristics often requires FFT even if a different technique is used for interference removal. Compared to the EMD and wavelet filter, they have not convincingly shown better performance results than the FFT excision filtering algorithm. Additionally, the complexity is expected to be much higher due to their high computing requirements, so they were not considered for hardware implementation. For these reasons, FFT excision filtering was used in this research work to mitigate the influence of interference on the GNSS receiver and enhance its performance for tracking and navigation operations. The proposed interference mitigation algorithm demonstrated a significant performance improvement compared to other algorithms, developed in the software simulations, and implemented in FPGA hardware.
3. Proposed Methodology
This research methodology is based on quantitative research methods. The quantitative methods are presented using experimental research methodology and engineering-oriented research methodology.
Figure 3 shows the full scheme of the proposed methodology and experimental work for this research. This research work consists of three stages as shown in
Figure 3, which are GNSS data capture, MATLAB simulation, and FPGA implementation. The first stage is called GNSS data capture. The first block of this stage represents the GNSS simulator (Spirent GSS8000), which produces representative GNSS signals whose power levels can be controlled as desired. The output of the simulator represents the RF GNSS signal at the output of the receiver’s antenna. It is then amplified using the low noise amplifier (LNA). LNA is a fundamental component because it amplifies the signal that comes from the antenna without adding a significant level of noise. This boosts the signal to protect it from the noise sources generated within the system (switching noise, harmonics, etc). The next block is the RF front-end datalogger. This block has two phases. Regarding the first phase, the RF signal is converted to an intermediate frequency (IF) that has a sufficient frequency to support the signal bandwidth. The second phase is the signal being converted to digital signals using an analogue digital converter (ADC) with automatic gain control (AGC). The output digital IF is passed to PC and stored as a data file. The second stage is the simulation and testing of the GNSS receiver performance using MATLAB. This stage contains three main blocks, which is the addition of interference, interference mitigation (the FFT excision), and the software GNSS receiver. The narrowband interferences that can be applied are single jammer, multiple jammers, and sweeping jammers, all with configurable power levels and frequencies. After this, the data is sent to the interference removal filter block, which represents the designed FFT excision filter, to mitigate the GNSS receiver interference. Finally, the signals are sent to the software GNSS receiver after the interference mitigation to test the influence of the jamming on the receiver operations.
The fundamental stage of this research is the third stage, which is the implementation stage in FPGA. This stage is carried out for both the hardware implementation and to validate the simulation and testing stage. As shown in
Figure 3, the output signal data with the added interference acts as an input for the very high-speed integrated circuit hardware description language (VHDL) test bench. Then, the output of the VHDL test bench is verified by sending it back to the software GNSS receiver to test the performance and compare it with the MATLAB simulation results. Using this comparison algorithm, the FFT excision-designed filter is verified as an optimal solution to mitigate the interference of the GNSS receiver in terms of software simulation and hardware implementation. The following sections illustrate the stages of developing the proposed scheme.
3.1. Scenarios: Different Types of Interference
This scheme was evaluated using different scenarios that have been discussed according to the related works in [
13,
38,
39]. There are main parameters for each scenario, which are the centre frequency (
) of the jamming signal, the intermediate frequency (
) of the jamming signal, and the jamming to noise density ratio (
). The centre frequency (
) is a measure of the centre frequency between the upper and lower cut-off frequency. The centre frequency is relative to the RF front-end’s intermediate frequency (
). The intermediate frequency (
) is a frequency in which a carrier wave is shifted as an intermediate step in transmission or receiving. In this work,
was selected to be 6.5 MHz and the jamming to noise density ratio (
) increased with the amplitude of the jamming signals. The applied jamming interferences in the simulation were continuous-wave (CW) interference and the sweeping frequency jammer.
Table 1 shows the parameters of these scenarios carried out in this work. The first scenario was simulated using one continuous-wave jammer that had a centre frequency (
) at 6.5 MHz and the interval frequency was between −1 and 1 MHz with a jamming to noise (
) ratio from 0 to 130 dB-Hz. The second scenario was simulated using multiple continuous-wave jammers with the same parameters as the first scenario. We followed the same approach in [
13,
39] to simulate the frequency fixed jammer to achieve the first and second scenarios using the following Equation (1):
where
p is the number of jammers (equal to one in the first scenario and equal to 2 or 3 or a higher number than 1 in the second scenario).
is the centre frequency and
is the change in the frequency due to the interval.
is included in the interval [5.5–7.5] MHz as mentioned in
Table 1. The jamming signal amplitude increases with (
) in the simulations. However, the amplitude does not vary between multiple jammers in the same simulation file and the phase of the jammer is omitted from this definition and set to zero in our simulations.
Figure 4 shows an example of a continuous-wave jammer at (
) = 80 dB-Hz.
The third scenario was simulated using a sweep jammer that had a certain frequency of 6.5 MHz and the swept bandwidth was −1 to 1 MHz with a jamming to noise ratio from 0 to 130 dB-Hz and the frequency rate was set to 8.4 GHz/s for a comparison with the results given in [
13]. The sweeping frequency jammers were defined with the following Equation (2):
where
is a time-varying frequency offset.
Figure 5 shows an example of the frequency variation of a jammer sweeping at a sweeping rate of 8.4 GHz/s (with a sampling frequency of 26 MHz).
3.2. Degradation of the GNSS Receiver Performance
There are various ways to monitor the degradation of GNSS receiver performances. The first way is at the signal level (i.e., bit error rate, carrier-to-noise ratio, monitoring phase/frequency lock loop, saturation phenomenon of AGC). The second way is at the observation level (i.e., noise on pseudoranges and carrier-phase observations) or the navigation level (i.e., position accuracy).
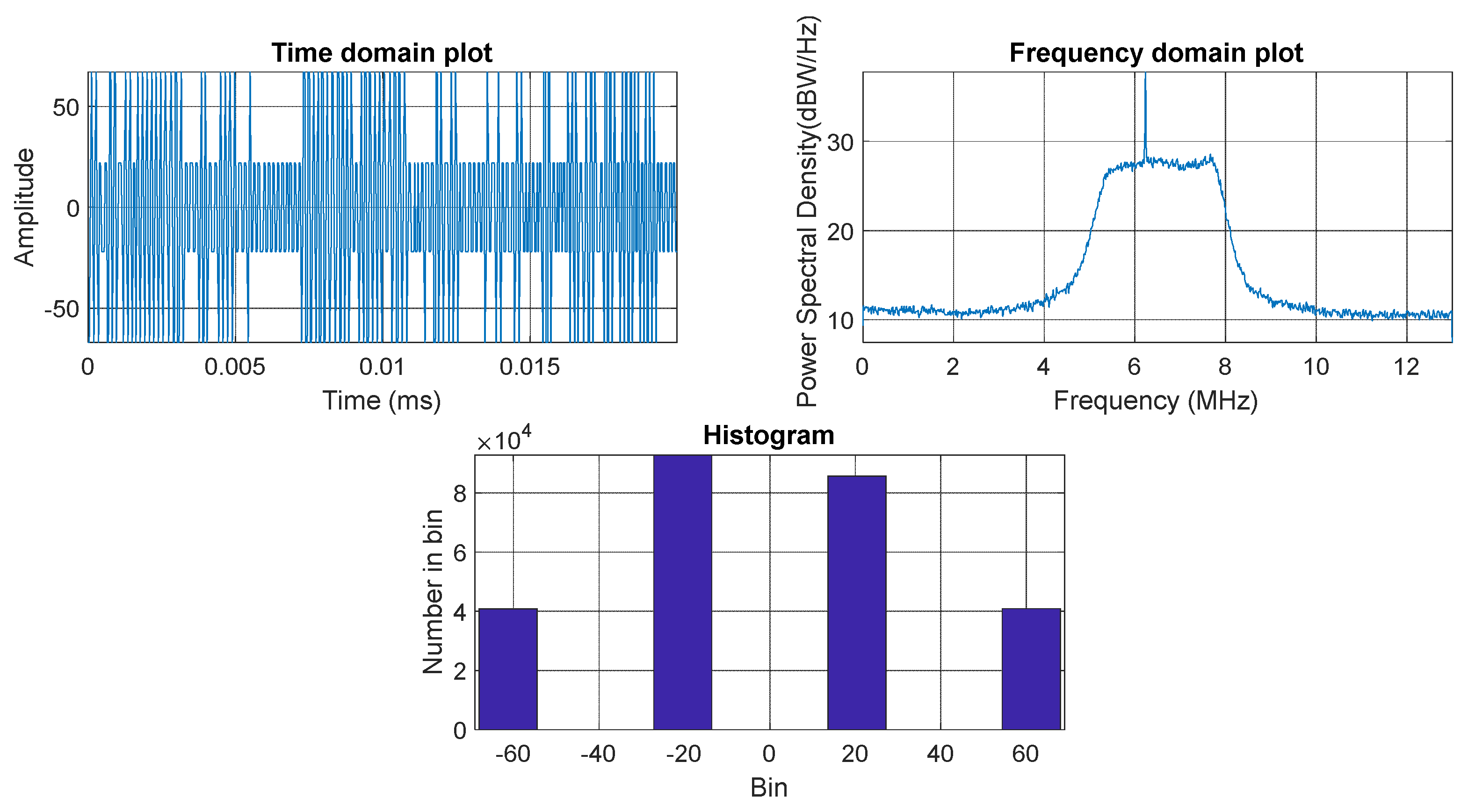
The first step for the simulations and experiments was the collection of the raw data. The raw data was logged for a typical terrestrial scenario, with all GNSS satellites set to a power level of −130 dBmW. The reason behind this power level is that the minimum received power level of GPS L1 C/A code (signed used) is −128.5 dBmW (from IS-GPS-200-M), assuming a 3 dBi receiver antenna. Therefore, −130 dBmW is slightly conservative but reasonable for a low-cost antenna. The power spectral density and bit distribution of the sampled signal is shown in
Figure 6. It illustrates the raw data before the addition of the interference in three different representations, which are the frequency domain, the time domain, and the histogram representations. The sampling frequency, IF, and bandwidth used were determined by the utilized GNSS front end, which is defined by the GNSS datalogger (NSL Stereo). The interference frequencies were chosen to be in line with [
13,
20] to provide a comparison against the notch filter approach, which is widely used in mass market receivers. The front end was configured to down-convert the GPS L1 C/A signal to an intermediate frequency (
) of 6.5 MHz, with a 3 dB bandwidth of around 2.75 MHz and frequency sampling at 26 MHz with a 2-bits resolution. It is noticeable that there is a self-generated CW in-band at 6.235 MHz, 10 to 12 dB above the noise, but it is not strong enough to interfere with the GNSS tracking after the matched filter of the spreading code demodulation was applied. The RF data was quantized to 2 bits during logging. As shown in
Figure 6, the time domain’s amplitude fluctuated between negative and positive values. The signal was heavily quantised down to 2 bits, taking on values of (±1, ±3). This is common in GNSS receivers, where the long averaging times result in only a 0.5 dB impact on SNR for 2-bit quantisation. However, in the simulation, we allowed 8 bits of the ADC range to handle the interference. To simulate the automatic gain control of the RF front-end, the standard deviation of the signal was always adjusted to around one-third of the signed 8-bit range (
42). The 8-bit signed has 7 bits of data and one bit of the sign
.
3.3. Mitigation Algorithm (FFT Excision)
The proposed solution for interference mitigation is the FFT excision algorithm. In its most simple form, FFT excision is the process of converting the signal into the frequency domain via FFT, selecting the frequency bins to be removed, and then performing an inverse FFT to return the signal to the time domain for processing by the receiver’s acquisition and tracking routines. However, as we demonstrate, this process can result in the removal of large amounts of the received spectrum for certain jammer frequencies. The frequency bin resolution is an important term for determining the location of the centre of interference in the spectrum. The frequency resolution is the difference in the frequency between each bin, and thus sets a limit on how precise the results can be. The frequency bin resolution (FBN) is calculated as in Equation (3):
where (
) is the sampling frequency. Therefore, for a given front-end bandwidth, the resolution improves with the length of FFT. From this formula, increasing the FFT size results in the frequency resolution decreasing (better resolution). As a result, the FFT results will have more points and represent the spectrum of the signal more precisely, since the distance between these bins (in terms of the frequency resolution) is smaller. If a narrowband (bandwidth less than one bin) jamming signal is not periodic within the length of FFT, its frequency spectrum will not necessarily be confined to a single bin of FFT. Instead, the discontinuities at the boundaries of the data block taken for FFT will broaden the frequency response. In
Figure 7a,b, an FFT of a 6.5 MHz CW interferer and a 6.5033 MHz CW interferer, respectively, is shown when sampling at 26 MHz and
equal to 110 dB-Hz. In the case of 6.5 MHz, CW repeats every four samples and hence is periodic in FFT. Its spectral energy is contained within a single FFT bin. The receiver’s front-end filter shape is shown in
Figure 7a. While in
Figure 7b, the 6.5033 MHz CW is not periodic, and its frequency response is much broader. One can obviously that see more bins of FFT would need to be removed in the non-periodic jammer case. Additionally, at high amplitudes, the sidelobes can raise the effective noise floor of the receiver. In practice, a jammer is seldom perfectly synchronized with the receiver’s sampling frequency and therefore a different approach must be taken.
3.4. Windowing
One way to reduce the effects of discontinuities that accrue because of FFT is the use of a technique called windowing, which is the multiplication of the original signal by a window function that reaches zero at () and (). Windowing functions that start at a low amplitude, increase to the middle, and finish at a low amplitude can be applied. This form of windowing reduces the amplitude of the discontinuities at the boundaries and can significantly reduce spectral leakage. There are several windowing functions such as Hamming, BlackmanHarris, Hann, rectangle windows, etc. The Hamming window was chosen because it has the best frequency resolution for cancelling the nearest side.
The benefit of using windowing is that is mitigates the effect of spectral leakage. Windows applies the weighting factor to the input signal prior to the computing of FFT. Windowing smooths the discontinuities at the block boundary and therefore lessens the effect of the spectral leakage. However, the selection of windows should be very accurate to trade-off the reduction in the background and the effectiveness of the spectral containment of the interference tone versus the reduction in SNR.
The disadvantage of windows is that by multiplying the signal by a window function, this distorts the signal, causing a broadening of the spectral peaks and worsening the resolution. The windowing inherently causes some loss in the desired signal by reducing the amplitude at the boundaries. However, this can be combated by creating two branches of the data flow with a 50% overlap (delay). The whole proposed algorithm is depicted in
Figure 8. This proposed algorithm consists of 6 main stages, which are splitting the input data into two branches by a 50% overlap, applying the window, FFT, interference suppression, IFFT, and combining the two branches together [
34].
In our implementation, 1024-point FFT and a 26 MHz sampling frequency were used. The 1024-point FFT was used as this is in line with the previous military ASIC devices. This results in a frequency resolution of FFT of ~25.4 kHz as calculated using Equation (3). For the GPS L1 C/A code, we considered the removal of interference in a 3 MHz passband around the centre frequency of the down-converted spectrum, so we used 119 points across our passband. It should be noted that the sampling frequency of our datalogger at 26 MHz is much greater than the frequency required for C/A code signal processing and results in more FFT points. A quarter of this rate at 6.5 MHz is a more typical sampling rate in practice and a 256-point FFT provides the same equivalent FFT resolution of ~25.4 kHz. The interference suppression is achieved by the FFT excision threshold, which is set by calculating the median value of the passband points and setting the threshold to four times its value. This threshold is roughly proportional to the mean noise power without interference and is capable of minimizing GPS signal degradation while mitigating the interference strength. Some small degradation is inevitable if the signal is always passed through the filter. Therefore, the threshold for using the filter should be set at the point the interference starts to influence the receiver. The experimental tests with CW interference confirmed that the threshold suggested in [
40] is a good choice and was therefore adopted. The inherent loss of the windowing when no interference is present is effectively removed by monitoring how many bins exceed the removal threshold. If no interference passes the threshold, then the input signal is simply passed to the output to avoid loss. The signal directly passed through is delayed by a time equivalent to the FFT processing time to avoid any timing discontinuities. The next section provides an analysis of the window types.
Analysis of Window Types
Figure 9 and
Figure 10 show the effect of different types of windowing when a fixed frequency interference is applied to the filter depicted in
Figure 8. Some windows, such as Hann and BlackmannHarris, provide a high level of interference suppression (
Figure 9) while the Hamming window provides the best spectral containment (
Figure 10) with reasonable suppression. The specific interference scenario determines which is the better choice. For example, the Hamming window performs well with multiple jammers as it removes less of the usable spectrum in the passband. However, if only one or two jammers are present, a BlackmannHarris window is preferable.
4. Hardware Implementation
The greatest challenge in previous studies was the hardware implementation due to the significant required number of hardware resources. FPGA was used in the implementation due to its parallelism as the hardware and software technologies are used in parallel with general reconfigurable solutions. Additionally, it has the ability to manipulate the system through software changes. FPGAs are well-structured processors that perform fast Fourier transforms (FFTs), which are often used during a GNSS receiver’s initial signal search and acquisition operations. FPGAs are generally used for prototyping GNSS receiver designs before the fabrication of a dedicated ASIC. In some cases, such as space GNSS receivers, FPGAs are used for the final product (SGR-AXIO, NAVILEO receivers).
The FPGA KCU105 kit has the Xilinx Kintex UltraScale family, which provides a hardware environment for developing and evaluating designs targeting the UltraScale XCKU040-2FFVA1156E device [
41]. The Kintex UltraScale family performs ASIC-class systems with a high-level performance, clock management, and power management. This kit is suitable for prototyping for medium-to-high applications such as data centres, wireless communication, and DSP applications. This kit has a variety of features that make it suitable and sufficient for our design, such as block RAM with 21.1 MB,1920 DSP slices, and 520 I/O pins [
41]. Moreover, this kit is compatible with the NAVLEO GNSS receiver. This receiver provides high-sensitivity acquisition and tracking loops. Furthermore, it supports both passive and active antennas. Additionally, it has a highly customizable and compact design, which makes it suitable for some GNSS space applications. The hardware prototype demonstration is shown in
Figure 11.
The system design was implemented with two data formats, which are fixed-point and float-point, in order to obtain the best performance design with the minimum hardware resources used. The fixed-point version was implemented by testing different precision sizes such as 8, 12, 16, 22, and 32 bits. The float-point was implemented with single-precision (32 bits). The algorithm in
Figure 8 was implemented using Xilinx Vivado VHDL and each stage was validated.
Table 2 shows the hardware implementation techniques that were used based on the precision types for the hardware development stage.
Figure 12 shows the block diagram of the hardware implementation for the fixed-point design. The following sections explain the processes of developing the proposed algorithm.
4.1. FFT Excision Algorithm
The FFT excision proposed algorithm is responsible for mitigating the interference from the GNSS receiver signals. This algorithm contains three inputs and two outputs. The main three inputs are the input file name, output file name, and settings. The input file contains the input file with interference, the output file contains the output without interference, and the setting contains the main GNSS receiver settings such as the time of processing, frequency sample, time of turning on the interference, and number of channels. The output of this function contains the number of frequency pins removed from branch A and the number of frequency pins removed from branch B.
Figure 13 shows the flowchart of the proposed interference excision algorithm. It illustrates how the software code works to mitigate interference in the following steps.
Firstly, the size of the block was defined based on the FFT size. In our case, the size of FFT was
or 1024 points, which represents one block in the processing. Then, the number of blocks was specified based on the time of processing of the interference mitigation algorithm. For example, if the time of processing is 10,000 ms, this means the number of blocks will equal 253,906. The calculation of the number of blocks is based on Equation (4):
where
is the time of processing of the algorithm in ms,
is 26 MHz, and
is the size of FFT, which is 1024. The subtraction by one is for the 50% overlap. Then, we multiplied the
by 1.5 to consider the 50% overlap that occurs in the second branch as shown in
Figure 8. So, the full range size is from 1 to 1536 due to the addition of an extra 512 to 1024. As mentioned previously in
Section 3.4, this overlap avoids data loss and reduces the effect of the signal attenuation from the window on the output SNR. After this, based on the algorithm in
Figure 8, the input data was divided into two streams. The first stream is called stream A. This stream starts from 1 to 1024 of the blocks. The second stream is called stream B. This stream is a delayed version of stream A by 50%, which starts from 512 to the end of 1536.
Next, we defined the window size, which should be the same size as FFT. As discussed previously, the Hamming window was chosen with a size of 1024. Next, the hamming windows were multiplied by stream A and stream B. After this, FFT was applied to stream A and stream B to obtain the frequency domain of both streams. After the application of FFT, the algorithm of the suppression of the interference was applied to mitigate the interference, which is explained in
Section 4.2. Then, the inverse fast Fourier transform (IFFT) was applied to the output of the suppression function of stream A and stream B to go back to the time domain. Finally, if interference was found in stream A or stream B, the first half of the output (0 to 512 points) was filled by the centre of stream A (256 to 768 points) and the second half of the output (512 to 1024 points) was filled by the centre of the stream (256 to 768 points). If no interference was found, then the middle of the input data (256 to 1280 points) passed to the output.
4.2. Interference Suppression Algorithm
This proposed algorithm takes the input data from the output of FFT using the same settings as the GNSS receiver and the output is the output spectrum without interference and the number of pins that were removed during the mitigation process. A flowchart of the interference suppression algorithm is shown in
Figure 14. The removal method works in the range of 5 to 8 MHz according to the MAX2769 chip, which is a type of GPS receiver [
42]. As mentioned in
Section 3.4, the frequency resolution of FFT is ~25.4 kHz. For the GPS L1 C/A code, we considered the removal of the interference in a 3 MHz passband around the centre frequency of the down-converted spectrum. By dividing 3 MHz over the frequency resolution, we obtained the number of points across this passband, which was ~119. So, during the mitigation process, the positive and negative ranges of the frequencies were specified. The positive range ranged from 5 to 8 MHz and the negative range ranged from −8 to −5 MHz. Then, an array was created to contain the positive and negative range of frequencies. To remove the interference, a thresholding algorithm should be applied for the suppression of the interference. This threshold is one of the popular algorithms for mitigating or removing interferences. The threshold is a value where any value of the frequency exceeds a certain threshold, which will be flagged as interference to be removed.
One of the difficulties in the thresholding algorithm is the setting of the value of the thresholding. If the threshold is set too high, the interference passes without mitigation. If the threshold is set too low, the original data is removed along with the interference. Therefore, the determination of the threshold should be accurate and valid. The threshold was calculated by multiplying four of the median with the input data according to [
40]. Then, the threshold was set based on the result. Based on the different testing scenarios, we found that it the removal of jamming signals once they start to influence the GNSS signals is a good choice as in [
40]. After this, a comparison of all values of the frequencies with the median value is provided. Any value that exceeds the threshold is considered interference. Then, they can either be nulled or replaced by zero. Finally, the output contains the values after the removal of the interference. The number of excised bins is equal to the length of the interferences found according to the threshold. This method works relatively well and is sufficiently fast for real-time processing.