Implementing Artificial Intelligence in Chaos-Based Image Encryption Algorithms †
Abstract
1. Introduction
- A general architecture is proposed for implementing AI functionalities in image encryption algorithms based on chaotic systems;
- A modified version of an existing algorithm, which combines a chaotic system and a Fibonacci matrix with AI capabilities, is presented. The modification leads to improved performance compared to the classical algorithm;
- A security analysis of the modified algorithm implemented in a MATLAB environment is conducted, demonstrating an increased level of protection.
2. Mathematical Foundations
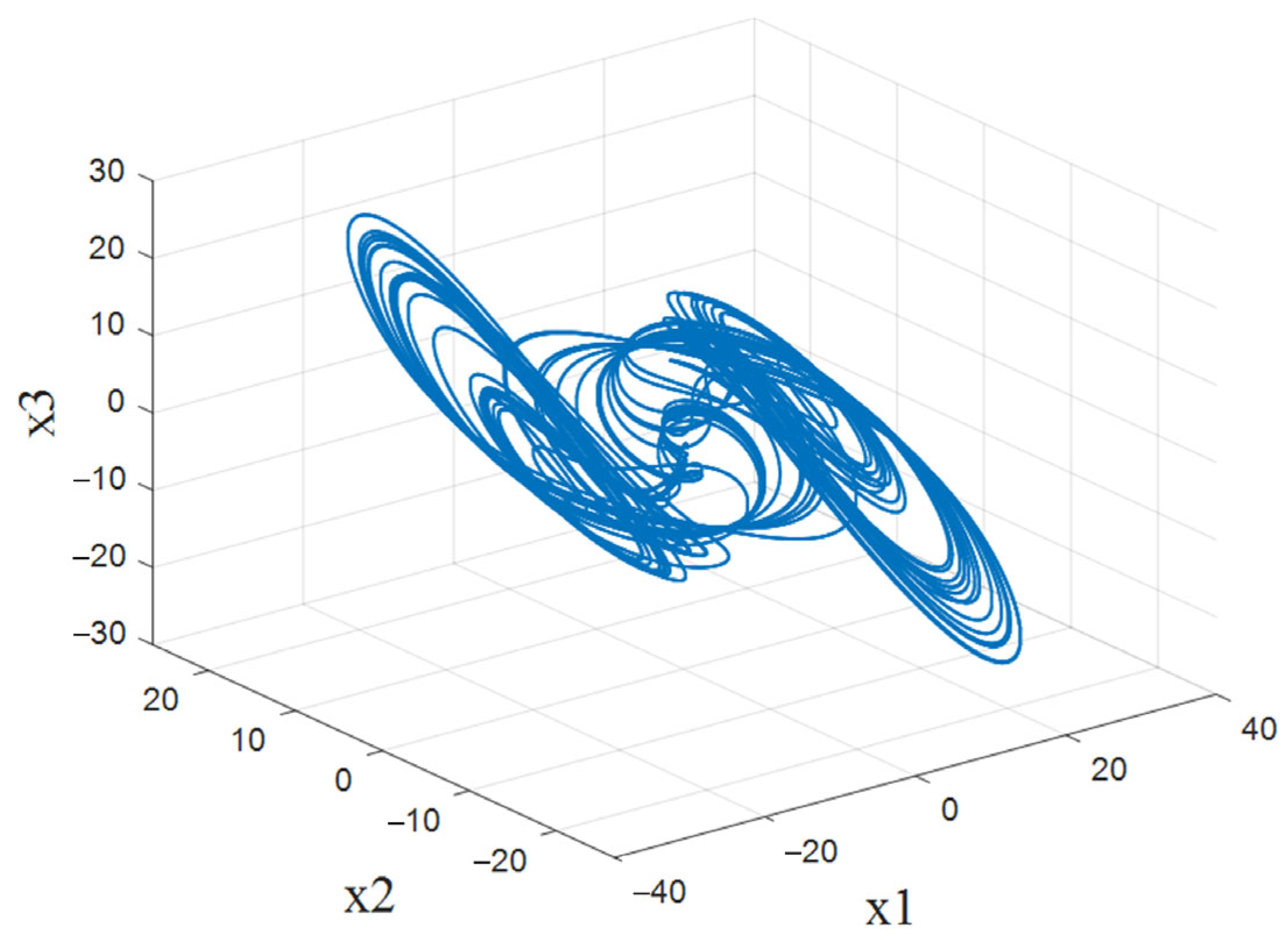
2.1. Chaotic Model
2.2. Fibonacci Q-Matrix
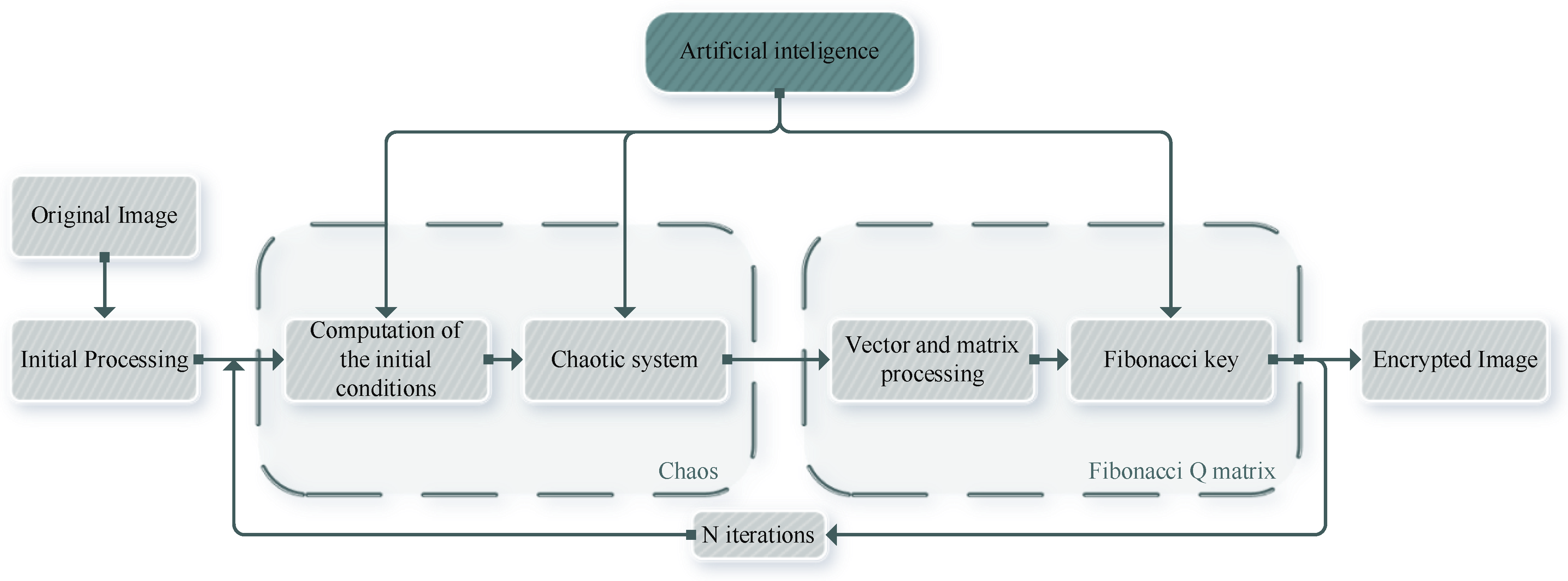
3. Modification of the Encryption Algorithm
3.1. Introducing a Modified Algorithm Based on Chaos and the Fibonacci Q-Matrix
3.2. Structure of the Modified Algorithm with AI Functionalities
- No parameters have been received from the AI—In this case, the request is resent, but no more than three times. If the request fails after the third attempt, it is assumed that there is no internet access, and default values are used.
- The parameter values are out of range—A check is performed to ensure that the values do not exceed predefined limits, which determine the chaotic nature of the system. It is desirable that the parameters acting as bifurcation points for the system do not vary widely, but their modification is crucial, as they ensure the key sensitivity condition of the algorithm.
- Initial conditions of the state vector—Due to the characteristic sensitivity of chaotic systems to initial conditions, these are chosen within specific areas of attraction of the attractor, with the aim of ensuring the desired dynamics.
3.3. Implementation and Integration of AI Functionality in the Modified Algorithm
- prompt = sprintf([‘Generate optimized chaotic encryption parameters (a, b, c, d) for a Shukur system based on image entropy %.2f, mean intensity %.2f, and contrast %.2f. Output only four floating point numbers separated by spaces.’], entropy_value, mean_intensity, contrast).
- prompt = sprintf([‘Generate a 2 × 2 matrix based on Fibonacci numbers, suitable for use as a Q-matrix in dynamic system modeling. Base the values on image entropy %.2f, mean intensity %.2f, and contrast %.2f. Output only four floating point numbers (Fibonacci-based) in row-major order separated by spaces.’], entropy_value, mean_intensity, contrast).
4. Results and Analysis
4.1. Main Results
4.2. Additional Results
4.2.1. Differential Attacks
4.2.2. Brute Force Attacks
4.2.3. Resistance to Noise and Data Loss
4.2.4. Run-Time Performance Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ajitha, P.V.; Nagra, A. An overview of artificial intelligence in automobile industry—A case study on Tesla cars. Solid State Technol. 2021, 64, 503–512. [Google Scholar]
- Madhavaram, C.R.; Sunkara, J.R.; Kuraku, C.; Galla, E.P.; Gollangi, H.K. The future of automotive manufacturing: Integrating AI, ML, and Generative AI for next-Gen Automatic Cars. Int. Multidiscip. Res. J. Rev. 2024, 1, 010103. [Google Scholar] [CrossRef]
- Tyagi, A.K.; Mishra, A.K.; Kukreja, S. Role of Artificial Intelligence Enabled Internet of Things (IoT) in the Automobile Industry: Opportunities and Challenges for Society. In Proceedings of the International Conference on Cognitive Computing and Cyber Physical Systems, Bhimavaram, India, 5–7 April 2023; Springer Nature: Singapore, 2023; pp. 379–397. [Google Scholar]
- Liyakat, K.S.S.; Liyakat, K.K.S. ML in the electronics manufacturing industry. J. Switch. Hub 2023, 8, 9–13. [Google Scholar] [CrossRef]
- Agrawal, A.V.; Raju, K.M.; Sravya, G.; Chandrashekhar, A.; Ramya, J. AI-Driven Test and Measurement Automation in Electronics Manufacturing. In Proceedings of the 2024 Ninth International Conference on Science Technology Engineering and Mathematics (ICONSTEM), Chennai, India, 4–5 April 2024; pp. 1–6. [Google Scholar]
- Vasudevan, K. Applications of artificial intelligence in power electronics and drives systems: A comprehensive review. J. Power Electron. 2023, 1, 1–14. [Google Scholar]
- Zhang, P.; Kamel Boulos, M.N. Generative AI in medicine and healthcare: Promises, opportunities and challenges. Future Internet 2023, 15, 286. [Google Scholar] [CrossRef]
- Beam, A.L.; Drazen, J.M.; Kohane, I.S.; Leong, T.Y.; Manrai, A.K.; Rubin, E.J. Artificial intelligence in medicine. N. Engl. J. Med. 2023, 388, 1220–1221. [Google Scholar] [CrossRef]
- Al-Antari, M.A. Artificial intelligence for medical diagnostics—Existing and future AI technology! Diagnostics 2023, 13, 688. [Google Scholar] [CrossRef]
- Yip, M.; Salcudean, S.; Goldberg, K.; Althoefer, K.; Menciassi, A.; Opfermann, J.D.; Lee, I.C. Artificial intelligence meets medical robotics. Science 2023, 381, 141–146. [Google Scholar] [CrossRef]
- DiGiorgio, A.M.; Ehrenfeld, J.M. Artificial intelligence in medicine & ChatGPT: De-tether the physician. J. Med. Syst. 2023, 47, 32. [Google Scholar]
- Waisberg, E.; Ong, J.; Masalkhi, M.; Kamran, S.A.; Zaman, N.; Sarker, P.; Tavakkoli, A. GPT-4: A new era of artificial intelligence in medicine. Ir. J. Med. Sci. 2023, 192, 3197–3200. [Google Scholar] [CrossRef]
- Rial, R.C. AI in analytical chemistry: Advancements, challenges, and future directions. Talanta 2024, 274, 125949. [Google Scholar] [CrossRef]
- Han, R.; Yoon, H.; Kim, G.; Lee, H.; Lee, Y. Revolutionizing medicinal chemistry: The application of artificial intelligence (AI) in early drug discovery. Pharmaceuticals 2023, 16, 1259. [Google Scholar] [CrossRef]
- Qin, Z.; Liang, L.; Wang, Z.; Jin, S.; Tao, X.; Tong, W.; Li, G.Y. AI empowered wireless communications: From bits to semantics. Proc. IEEE 2024, 112, 621–652. [Google Scholar] [CrossRef]
- Xu, F.; Hussain, T.; Ahmed, M.; Ali, K.; Mirza, M.A.; Khan, W.U.; Han, Z. The state of ai-empowered backscatter communications: A comprehensive survey. IEEE Internet Things J. 2023, 10, 21763–21786. [Google Scholar] [CrossRef]
- Zuo, Y.; Guo, J.; Gao, N.; Zhu, Y.; Jin, S.; Li, X. A survey of blockchain and artificial intelligence for 6G wireless communications. IEEE Commun. Surv. Tutor. 2023, 25, 2494–2528. [Google Scholar] [CrossRef]
- Malthouse, E.; Copulsky, J. Artificial intelligence ecosystems for marketing communications. Int. J. Advert. 2023, 42, 128–140. [Google Scholar] [CrossRef]
- Ahammed, T.B.; Patgiri, R.; Nayak, S. A vision on the artificial intelligence for 6G communication. ICT Express 2023, 9, 197–210. [Google Scholar] [CrossRef]
- Alahi, M.E.E.; Sukkuea, A.; Tina, F.W.; Nag, A.; Kurdthongmee, W.; Suwannarat, K.; Mukhopadhyay, S.C. Integration of IoT-Enabled Technologies and Artificial Intelligence (AI) for Smart City Scenario: Recent Advancements and Future Trends. Sensors 2023, 23, 5206. [Google Scholar] [CrossRef] [PubMed]
- de Azambuja, A.J.G.; Plesker, C.; Schützer, K.; Anderl, R.; Schleich, B.; Almeida, V.R. Artificial Intelligence-Based Cyber Security in the Context of Industry 4.0—A Survey. Electronics 2023, 12, 1920. [Google Scholar] [CrossRef]
- Khompysh, A.; Dyusenbayev, D.; Maxmet, M. Development and analysis of symmetric encryption algorithm. Int. J. Electr. Comput. Eng. 2025, 15, 1900–1911. [Google Scholar] [CrossRef]
- Lalem, F.; Laouid, A.; Kara, M.; Al-Khalidi, M.; Eleyan, A. A Novel Digital Signature Scheme for Advanced Asymmetric Encryption Techniques. Appl. Sci. 2023, 13, 5172. [Google Scholar] [CrossRef]
- Zhang, B.; Liu, L. Chaos-Based Image Encryption: Review, Application, and Challenges. Mathematics 2023, 11, 2585. [Google Scholar] [CrossRef]
- Inam, S.; Kanwal, S.; Batool, M.; Al-Otaibi, S.; Jamjoom, M.M. A blockchain-integrated chaotic fractal encryption scheme for secure medical imaging in industrial IoT settings. Sci. Rep. 2025, 15, 7652. [Google Scholar] [CrossRef]
- Alanzy, M.; Alomrani, R.; Alqarni, B.; Almutairi, S. Image Steganography Using LSB and Hybrid Encryption Algorithms. Appl. Sci. 2023, 13, 11771. [Google Scholar] [CrossRef]
- Thorat, N.N.; Singla, A.; Dhaigude, T. Sharing Secret Colour Images with Embedded Visual Cryptography Using the Stamping Algorithm and OTP Procedure. Int. J. Recent Innov. Trends Comput. Commun. 2023, 11, 63–70. [Google Scholar] [CrossRef]
- Konwar, R.; Jha, D.; Agrawal, R.; Purkayastha, R.; Banerjee, I. A Two-Factor Authentication Mechanism Using a Novel OTP Generation Algorithm for Cloud Applications. In Proceedings of the 2024 14th International Conference on Cloud Computing, Data Science & Engineering (Confluence), Noida, India, 18–19 January 2024; pp. 245–250. [Google Scholar] [CrossRef]
- Saeed, N.A.; Saleh, H.A.; Hou, L.; Nasr, E.A. A novel chaotic oscillator with a half-line of unstable equilibria: Basins of attraction, chaos control, chaos synchronization, and encryption applications. Mod. Phys. Lett. B 2025, 39, 2450436. [Google Scholar] [CrossRef]
- Shi, Q.; Zhao, Y.; Ding, Q. Design and FPGA implementation of encrypted frame transmission scheme based on chaotic reverse synchronization. Nonlinear Dyn. 2025, 113, 5511–5535. [Google Scholar] [CrossRef]
- Yang, C.-H.; Lee, J.-D.; Tam, L.-M.; Li, S.-Y.; Cheng, S.-C. FPGA Implementation of Image Encryption by Adopting New Shimizu–Morioka System-Based Chaos Synchronization. Electronics 2025, 14, 740. [Google Scholar] [CrossRef]
- Hosny, K.M.; Kamal, S.T.; Darwish, M.M.; Papakostas, G.A. New Image Encryption Algorithm Using Hyperchaotic System and Fibonacci Q-Matrix. Electronics 2021, 10, 1066. [Google Scholar] [CrossRef]
- Shukur, A.A.; Neamah, A.A.; Pham, V.T.; Grassi, G. A novel chaotic system with one absolute term: Stability, ultimate boundedness, and image encryption. Heliyon 2025, 11, e37239. [Google Scholar] [CrossRef]
- Vorobiev, N.N. Fibonacci Numbers; Birkhäuser Verlag: Basel, Switzerland, 2002. [Google Scholar]
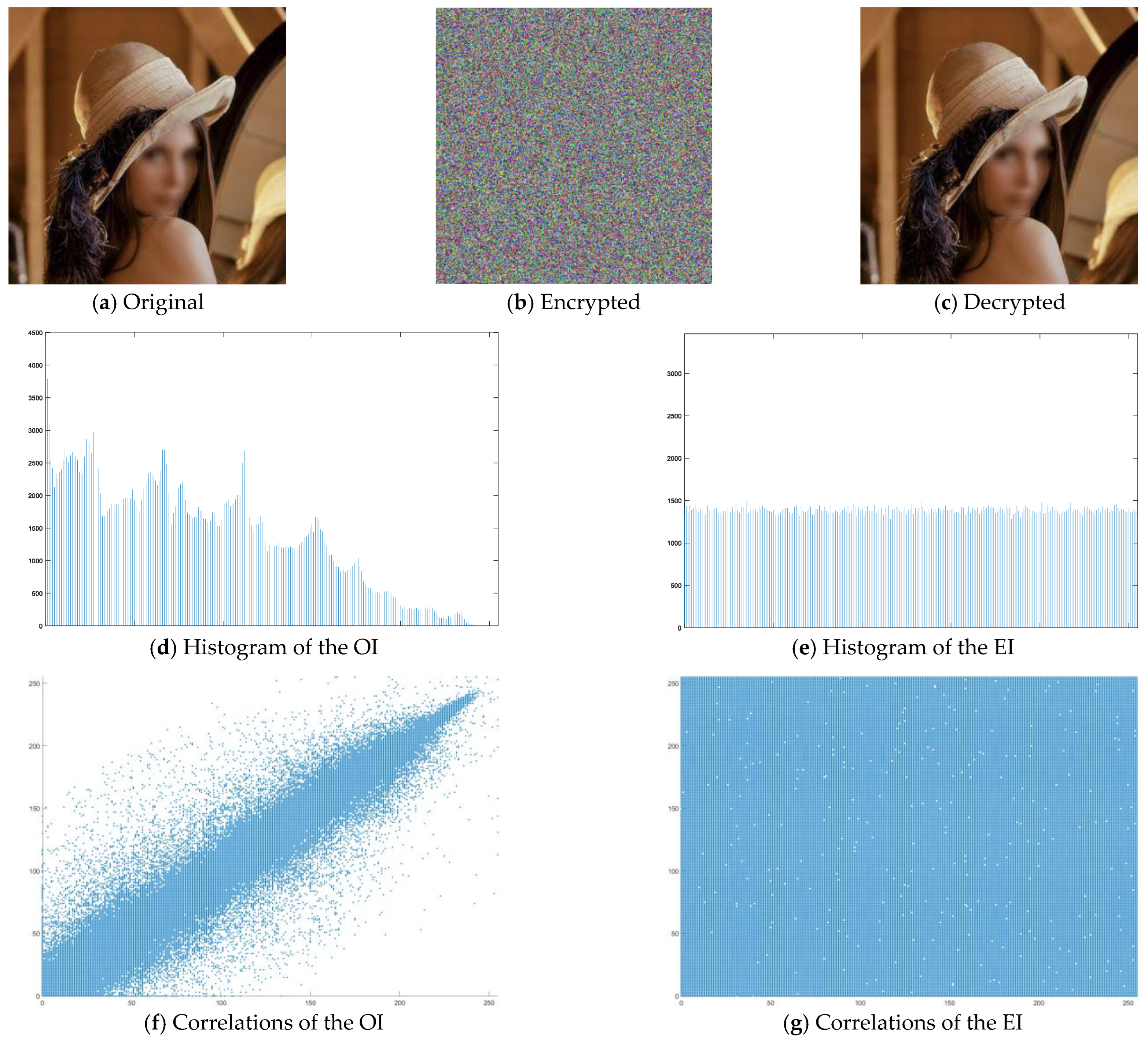
| Entropy | Correlation | NPCR | UACI | |
|---|---|---|---|---|
| Input image | 7.3283 | 0.9864 | - | - |
| Encrypted image | 7.9995 | 0.0037 | 99.6217 | 33.4463 |
| Entropy | Correlation | NPCR | UACI | |
|---|---|---|---|---|
| Input image | 7.3283 | 0.9864 | - | - |
| Original method [32] | 7.9993 | 0.0069 | 99.6174 | 33.4226 |
| Modified | 7.9995 | 0.0037 | 99.6217 | 33.4463 |
 |  |  |  | ||
| Entropy | OI | 3.6779 | 7.6288 | 7.8471 | 7.7563 |
| EI | 7.9707 | 7.9992 | 7.9993 | 7.9994 | |
| Correlation | OI | 0.9365 | 0.9747 | 0.9394 | 0.9829 |
| EI | 0.0172 | 0.0012 | −0.0014 | −0.0018 | |
| Lena | MRI | Parrots | Koala | Flower | |
|---|---|---|---|---|---|
| NPCR | 99.6217 | 98.7732 | 99.6005 | 99.6180 | 99.5985 |
| UACI | 33.4463 | 34.9041 | 32.9957 | 33.2955 | 33.2622 |
| Lena | MRI | Parrots | Koala | Flower | |
|---|---|---|---|---|---|
| S&P noise level 0.002 | 22.6550 | 20.7806 | 23.6613 | 23.4391 | 22.8415 |
| S&P noise level 0.005 | 18.9475 | 16.7527 | 19.6873 | 19.6417 | 19.0693 |
| Data cut—6% | 16.8817 | 14.9539 | 17.7199 | 17.5721 | 17.0821 |
| Data cut—12% | 11.6756 | 10.2426 | 12.4800 | 12.3592 | 11.7835 |
| Image Size | Using AI | Encrypt | Decrypt | Total Time |
|---|---|---|---|---|
| 256 × 256 | 1.615 s | 0.721 s | 0.066 s | 4.7415 s |
| 512 × 512 | 2.062 s | 2.395 s | 0.252 s | 7.584 s |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Stoycheva, H.; Sadinov, S.; Angelov, K.; Kogias, P.; Malamatoudis, M. Implementing Artificial Intelligence in Chaos-Based Image Encryption Algorithms. Eng. Proc. 2025, 104, 20. https://doi.org/10.3390/engproc2025104020
Stoycheva H, Sadinov S, Angelov K, Kogias P, Malamatoudis M. Implementing Artificial Intelligence in Chaos-Based Image Encryption Algorithms. Engineering Proceedings. 2025; 104(1):20. https://doi.org/10.3390/engproc2025104020
Chicago/Turabian StyleStoycheva, Hristina, Stanimir Sadinov, Krasen Angelov, Panagiotis Kogias, and Michalis Malamatoudis. 2025. "Implementing Artificial Intelligence in Chaos-Based Image Encryption Algorithms" Engineering Proceedings 104, no. 1: 20. https://doi.org/10.3390/engproc2025104020
APA StyleStoycheva, H., Sadinov, S., Angelov, K., Kogias, P., & Malamatoudis, M. (2025). Implementing Artificial Intelligence in Chaos-Based Image Encryption Algorithms. Engineering Proceedings, 104(1), 20. https://doi.org/10.3390/engproc2025104020







