Computer Simulation of Anti-Drone System †
Abstract
:1. Introduction
2. Model Description
- The countermeasure subsystem with one or several countermeasures.
- The radar subsystem with one or more active antennas and one detector that are detect and localize targets.
2.1. Simulation Process Description
- The flight process (flight) of every drone.
- The ADS’ operating process (operating).
- The countermeasures elimination processes.
- The radar detecting and localizing process (detection).
2.2. The Drone Model
2.3. The Gun Model
2.4. The Radar Model
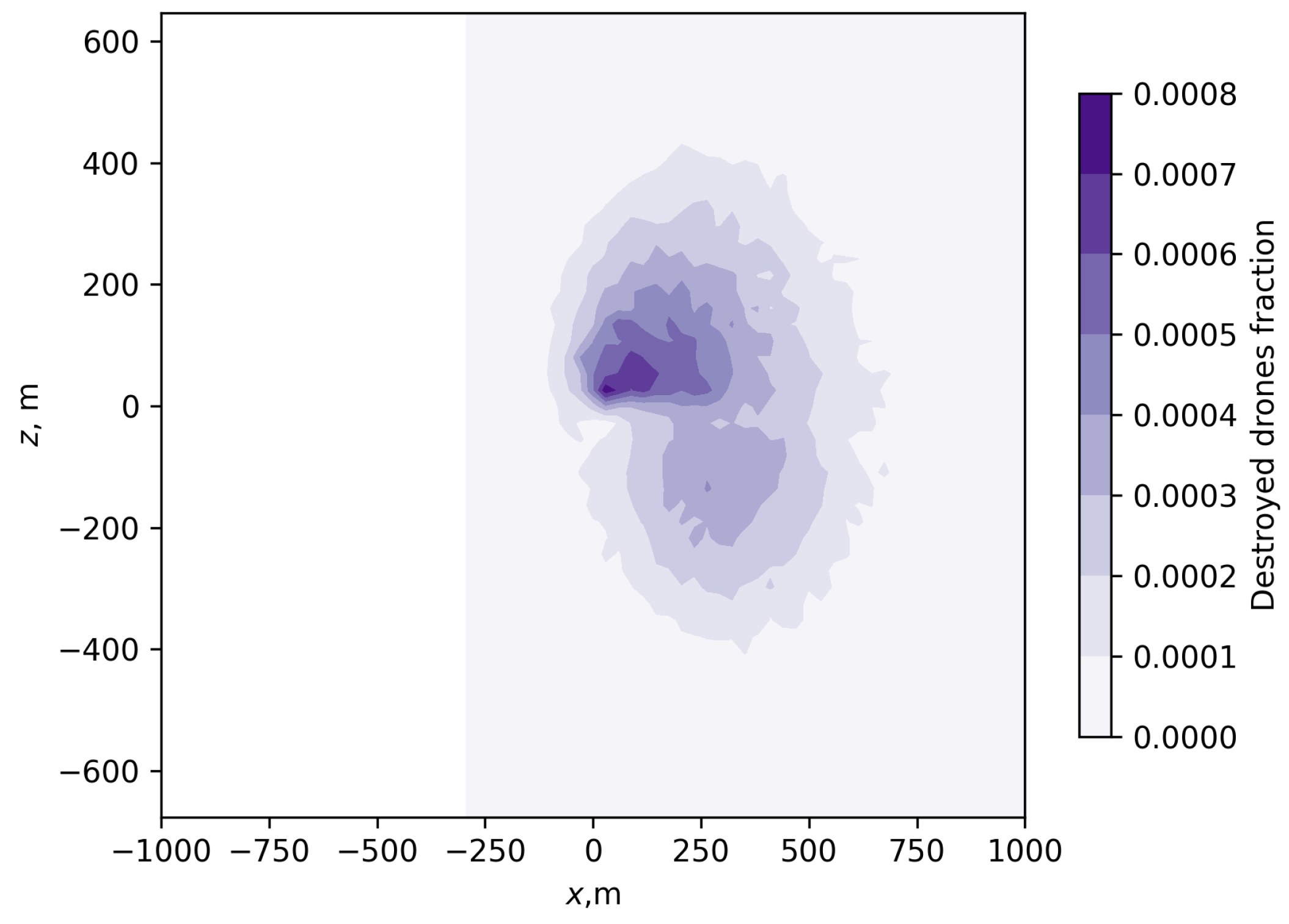
3. Simulation Results
- is a standard deviation of the aiming point at a distance of 1 m to the target;
- is a standard deviation of the mean aiming point of the burst at a distance of 1 m;
- is a standard deviation of each individual hit point at a distance of 1 m.
4. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Nomenclature
| Normal distribution | |
| Mean value | |
| Standard deviation |
References
- Roldan, J.J.; Garcia-Aunon, P.; Pena-Tapia, E.; Barrientos, A. SwarmCity Project: Can an Aerial Swarm Monitor Traffic in a Smart City? In Proceedings of the 2019 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kyoto, Japan, 11–15 March 2019; pp. 862–867. [Google Scholar]
- Alsamhi, S.H.; Ma, O.; Ansari, M.S.; Almalki, F.A. Survey on Collaborative Smart Drones and Internet of Things for Improving Smartness of Smart Cities. IEEE Access 2019, 7, 128125–128152. [Google Scholar] [CrossRef]
- Abualigah, L.; Diabat, A.; Sumari, P.; Gandomi, A.H. Applications, Deployments, and Integration of Internet of Drones (IoD): A Review. IEEE Sens. J. 2021, 21, 25532–25546. [Google Scholar] [CrossRef]
- Calcara, A.; Gilli, A.; Gilli, M.; Marchetti, R.; Zaccagnini, I. Why Drones Have Not Revolutionized War: The Enduring Hider-Finder Competition in Air Warfare. Int. Secur. 2022, 46, 130–171. [Google Scholar] [CrossRef]
- Laufs, J.; Borrion, H.; Bradford, B. Security and the smart city: A systematic review. Sustain. Cities Soc. 2020, 55, 102023. [Google Scholar] [CrossRef]
- Ilgi, G.S.; Ever, Y.K. Critical analysis of security and privacy challenges for the Internet of drones: A survey. In Drones in Smart-Cities; Elsevier: Amsterdam, The Netherlands, 2020; pp. 204–214. [Google Scholar]
- Racek, F.; Balaz, T.; Krejci, J.; Prochazka, S.; Macko, M. Tracking, aiming, and hitting the UAV with ordinary assault rifle. In Proceedings of the SPIE 10441, Counterterrorism, Crime Fighting, Forensics, and Surveillance Technologies, Warsaw, Poland, 11–14 September 2017; pp. 112–122. [Google Scholar]
- Castrillo, V.U.; Manco, A.; Pascarella, D.; Gigante, G. A Review of Counter-UAS Technologies for Cooperative Defensive Teams of Drones. Drones 2022, 6, 65. [Google Scholar] [CrossRef]
- Rothe, J.; Strohmeier, M.; Montenegro, S. A concept for catching drones with a net carried by cooperative UAVs. In Proceedings of the IEEE International Symposium on Safety, Security, and Rescue Robotics (SSRR), Würzburg, Germany, 2–4 September 2019; pp. 126–132. [Google Scholar]
- SimPy. PyPI 2020. Available online: https://pypi.org/project/simpy/ (accessed on 30 August 2022).
- Tovarnov, M.S.; Bykov, N.V.; Vlasova, N.S.; Fedulov, V.A.; Pozharsky, A.A. Computer simulation of the physical neutralization of drones in a Smart City. J. Phys. Conf. Ser. 2022, 2308, 012003. [Google Scholar] [CrossRef]
- Bakulev, P.A. Radar Systems. Textbook for High Schools; Radiotechnics: Moscow, Russia, 2004. [Google Scholar]
- Verba, V.S.; Gavrilov, K.Y.; Ilchuk, A.R.; Tatarsky, B.G.; Filatov, A.A. Radiolocation for Everyone; Technosphere: Moscow, Russia, 2020. [Google Scholar]




| Parameter Name | Distribution Law | Distribution Parameters |
|---|---|---|
| Initial speed | Normal | m/s |
| Angle between initial velocity and Ox axis | Uniform | |
| Initial drone angle of attack | Uniform | |
| Final speed | Normal | m/s |
| Angle between final velocity and Ox axis | Uniform | |
| Final drone angle of attack | Uniform |
| Airframe Part | Local Coordinates, mm | Axis Dimensions, mm |
|---|---|---|
| Central body (parallelepiped) | ||
| 1st engine(ellipsoid) | ||
| 2nd engine(ellipsoid) | ||
| 3rd engine(ellipsoid) | ||
| 4th engine(ellipsoid) |
| Parameter Name | Unit Measure | Value |
|---|---|---|
| Position | m | |
| Rotation speed | rad/s | |
| Range | m | 0 to 600 |
| Azimuth angle range | — | |
| Elevation angle range | — | |
| Detector mean output voltage | V | 12 |
| Detector output voltage standard deviation | V | 3 |
| Detector noise voltage standard deviation | V | 1 |
| Correct detection probability | — | |
| False alarm probability | — |
| Parameter Name | Unit Measure | Value |
|---|---|---|
| Fire rate | shots/min | 800 |
| Burst length | — | 10 |
| Shots capacity | — | 120 |
| Aiming accuracy | — | |
| Burst shots accuracy | — | |
| Individual shot accuracy | — |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bykov, N.; Fedulov, V. Computer Simulation of Anti-Drone System. Eng. Proc. 2023, 33, 24. https://doi.org/10.3390/engproc2023033024
Bykov N, Fedulov V. Computer Simulation of Anti-Drone System. Engineering Proceedings. 2023; 33(1):24. https://doi.org/10.3390/engproc2023033024
Chicago/Turabian StyleBykov, Nikita, and Vadim Fedulov. 2023. "Computer Simulation of Anti-Drone System" Engineering Proceedings 33, no. 1: 24. https://doi.org/10.3390/engproc2023033024






