A Review of Recent Developments in 6G Communications Systems †
Abstract
:1. Introduction
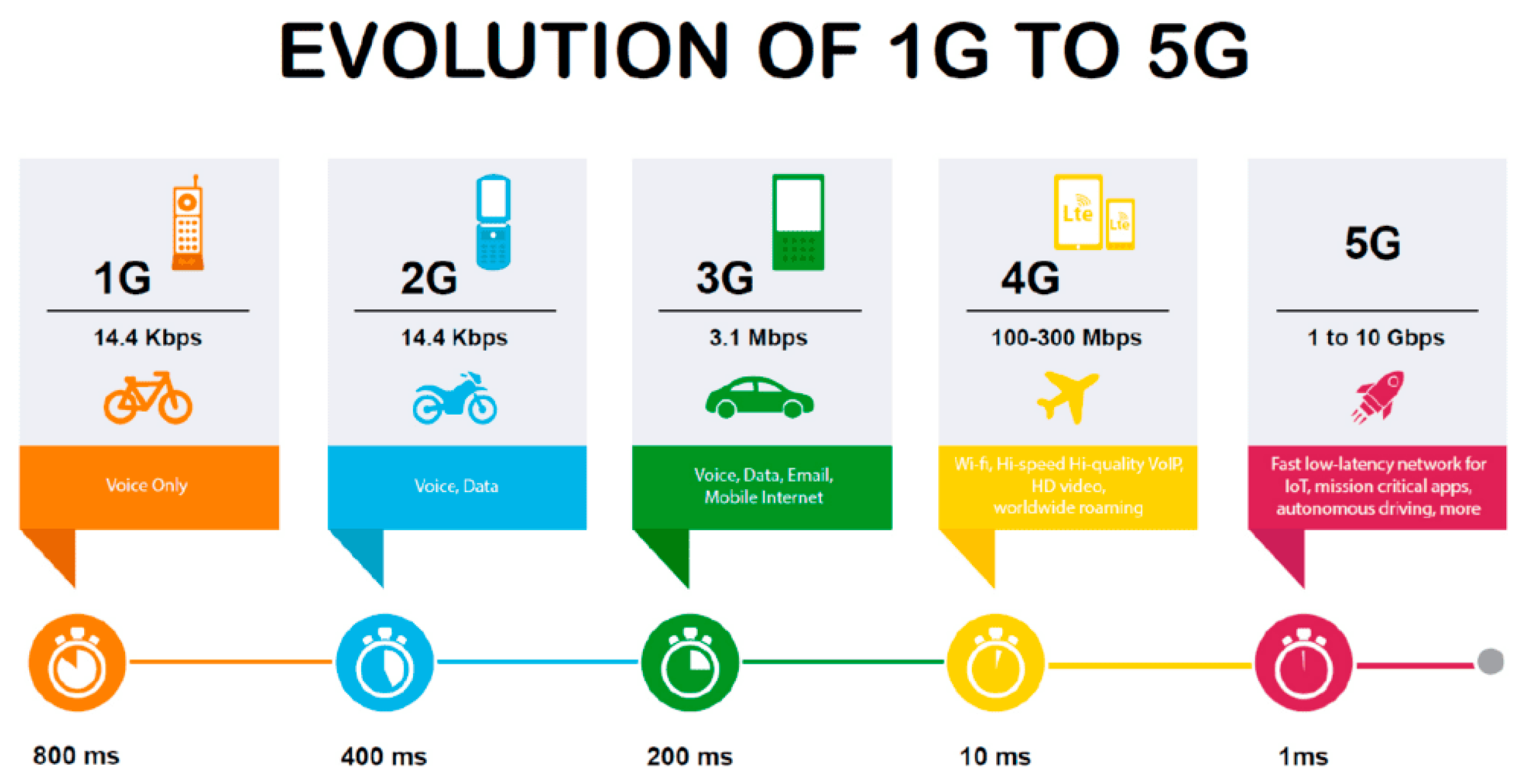
1.1. 5G Limitations and 6G Vision
1.2. Application and Use Cases
1.3. Challenges during the Transition to 6G and Its Solutions
2. Ultra-Reliable Low-Latency Communications in 6G
2.1. Key Performance Indicators
- Low-Latency: End-to-End (E2E) Round Trip Latency (RTL) measures data travel between application layers on a source and end device, including propagation, processing delays, and request and response. For tactile internet haptic feedback, RTL within 20 ms is necessary, while strict E2E RTL is required for haptic steering.
- Spectral-Efficiency: Spectral efficiency measures the quantity of data transferable under a given bandwidth constraint [2]. With 6G, a greater number of devices will expand, necessitating support for a greater number of services within a given bandwidth.
- Jitter: The launch of 6G will increase the appeal of mobile augmented reality/virtual reality (AR/VR) applications [2]. To provide the greatest user experience possible, the jitter and delay between consecutive updates should be kept to a minimum.
2.2. Integration of URLLCs with Deep Learning
- Supervised Learning: Apart from contributions in the field of computer science, supervised deep learning will also play a major role in wireless networks. Some of the areas where it will be useful are channel estimation or prediction, quality of service (QoS) prediction, quality of experience (QoE) prediction, and traffic prediction [2].
- Unsupervised learning: Unsupervised learning algorithms use unlabeled training data to identify hidden patterns and clusters, enabling optimal policy determination in URLLCs. K-means and fuzzy C-means address interference mitigation and node clustering, while deep neural networks optimize and train for QoS criteria using unsupervised DL [3].
- Deep Reinforcement Learning: The deep-RL and URLLC work together to deliver more dependable peak data throughput and reduce interface latency by enabling autonomous symbol creation, protection, energy harvesting, beamforming, channel-tracking, and complicated network layer multi-routing. Some of the deep reinforcement learning techniques useful in resource allocation are Q-learning, fuzzy RL, and deep deterministic policy gradient (DDPG) [3].
2.3. Real-Life Applications
- Industrial Automation—Utilize 6G URLLCS; a key driver of the fourth industrial revolution; alongside artificial intelligence; genetic engineering; and 3D printing; for reliable connectivity and enhanced capabilities like sonar; GPS; radar; and odometry.
- Extended-Reality—Extended Reality (XR) combines AR; VR; and MR; utilizing 3-D objects and artificial intelligence. Wearable gadgets with XR technology, high-definition visuals, and five communication senses enable human-to-human and object conversations [4].
- Healthcare Industry—URLLC is utilized by healthcare organizations for patient visits; asset tracking; real-time patient monitoring; and staff training. It enables remote surgery with low latency and a reliable 6G network, enabling rapid and reliable data transport in the medical industry [4].
2.4. Extreme URLLCs (xURLLC)
2.5. Challenges
3. Federated Learning in 6G
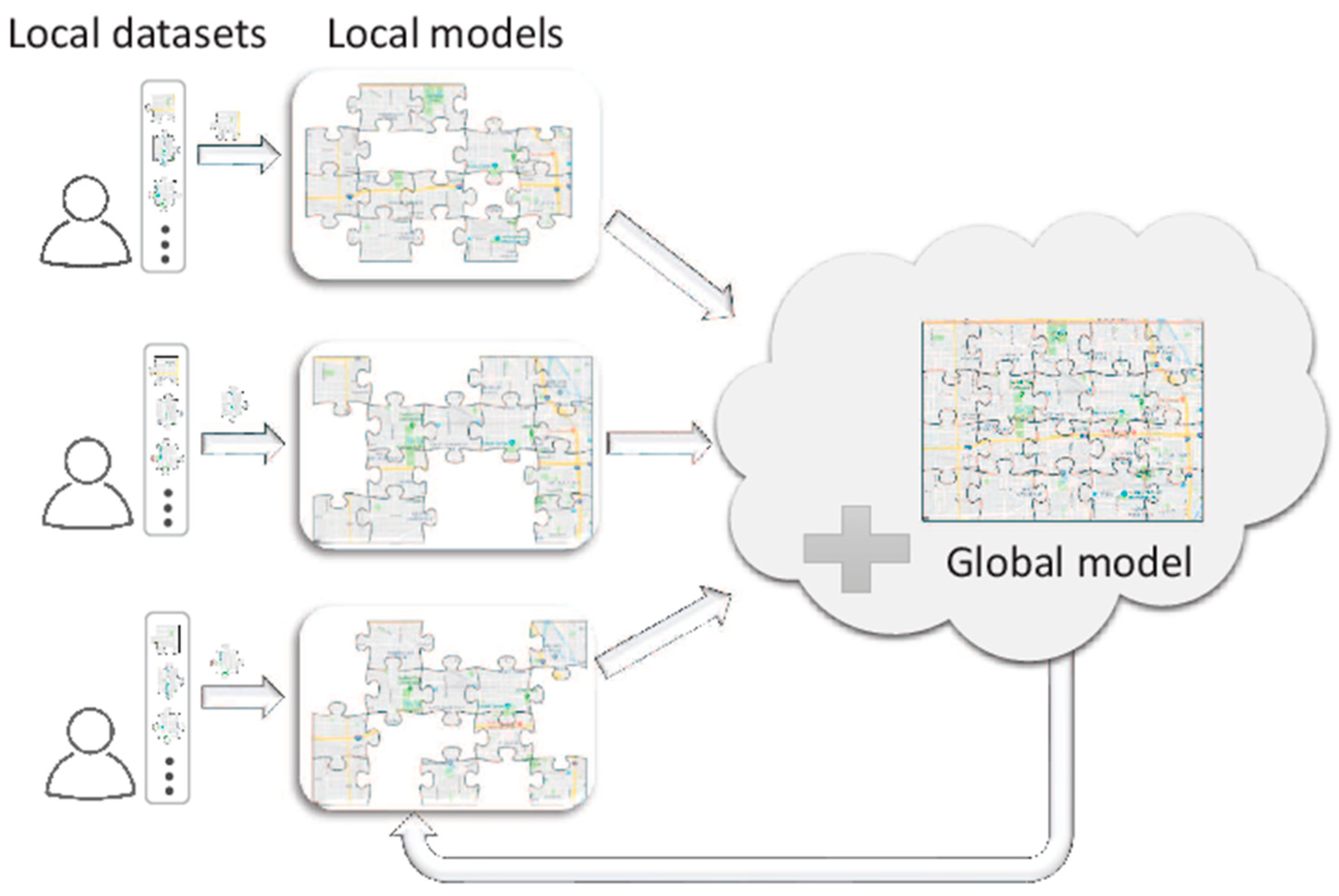
3.1. Introduction
3.2. Advantages of Federated Learning
- Privacy preservation: Federated learning in 6G communication aims to preserve the privacy of users’ data by keeping it on their devices rather than centralizing it.
- Decentralized learning: Federated learning allows for machine learning models to be developed and improved in a decentralized manner, leveraging the computational resources of multiple devices.
- Improved accuracy: The aggregation of data and computation from multiple devices leads to more robust and accurate models compared to traditional centralized learning approaches.
- Reduced latency: By bringing the computation to the data, federated learning reduces the latency and bandwidth requirements for communication, improving the overall efficiency of the system.
- Enhanced security: Federated learning protects against data breaches, tampering, and other security threats by keeping sensitive data on the devices of users rather than centralizing it in a single location.
3.3. Real-Life Uses
- Group knowledge transfer: increased CNN size improves model accuracy, but it is challenging for training on resource-constrained edge devices. FedGKT, a group knowledge transfer training algorithm, addresses this issue by addressing edge node compute capability limitations.
- Federated Learning for Mobile Keyboard Prediction (Google).
- Frameworks like “Flower: A Friendly Federated Learning Framework”, which supports heterogeneous environments, including mobile and edge devices, and scales to many distributed clients.
3.4. Challenges in Federated Learning
- Communication Overhead: FLs iterative nature does not completely solve network congestion due to data offloading from the edge to the cloud. Communication overhead is significant for complicated models, big-scale applications, and high-frequency updates, making it challenging to handle [3].
- Privacy and Security Concerns: Federated Learning models are susceptible to attacks, similar to any machine learning model. These attacks can be initiated by individuals, a compromised central server, or local devices. Common attacks include Membership Interference, Data poisoning, Model poisoning, and Backdoor attacks [4].
- Expensive Communication: Federated Learning generally involves multiple devices for model training. Some studies prior to this [5,6,7,8,9,10,11,12] show some work conducted to improve communication efficiency. To minimize the communication overhead, we take two things into account: (i) minimizing the total number of communication rounds, or (ii) minimizing the number of gradients used in each round [13].
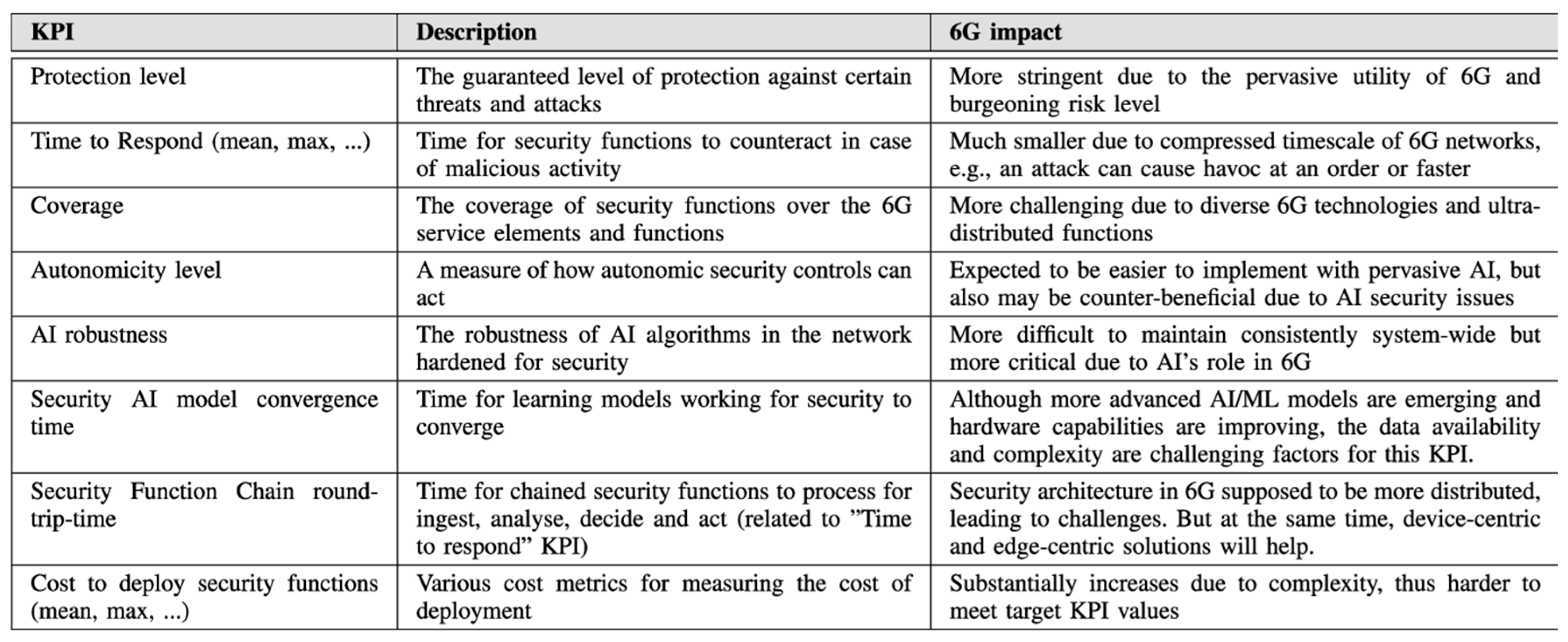
4. Security in 6G and Blockchain
4.1. Security Threats
- Physical-Level Security Threats
- Designing and implementing of resource isolation for base stations for full-duplex operations in the case of full-duplex radio stations.
- New Requirements
- To ensure service quality when using Enhanced Ultra-Reliable, Low-Latency Communication (ERLLC/eURLLC), security systems need to be implemented, taking latency into account.
- Features and architecture guaranteeing high reliability need efficient security solutions protecting users, resources, and services.
- Further improved Mobile Broadband (FeMBB) resulted in higher data rates, which caused traffic processing issues for attack detection, encryption, and traffic analysis.
- The Internet of Everything (IoE) will render existing encryption models obsolete due to its extensive and diverse capabilities.
- New Architecture
- The advancement of AI chips has resulted in a breakthrough in which hardware can be isolated from transceiver algorithms, and they can configure and update themselves based on environmental inputs.
- Intelligent radio today is expected to solve many problems of accurate channel modeling, dynamic spectrum access, improved network deployment, optimization, and autonomous orchestration that lead to malicious attacks/activities during communication systems.
- Intelligent networks lead to DdoS (Distributed Denial-of-Service attacks) and MITM (Man in the Middle) attacks.
- Intercepting information in the process of transmission.
- Performance-Privacy balance.
- This model is high on AI/ML dependency, where any contamination of data that is already in volumes can have a detrimental impact on the models we use.
4.2. Blockchain Solutions in the Security Domain
Solutions
4.3. Challenges with Blockchain
- High costs: The average cost of a transaction, for example, Ethereum, is 150 USD per transaction. Ethereum because it is a highly used and decentralized network with ease of understanding.
- The average cost of storage is 100 dollars per GB, which is very cost-efficient given that large storage is mostly impossible on blockchain.
- SLAs-SLAs storage is carried out off-chain and requires constant monitoring and transparency among stakeholders, which often leads to delays and inefficiency.
- Common blockchain threats include 51% majority attacks, Sybil attacks, and selfish mining.
- Since data are with everyone, the aspect of transparency compromises privacy.
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Pocovi, G.; Shariatmadari, H.; Berardinelli, G.; Pedersen, K.; Steiner, J.; Li, Z. Achieving Ultra-Reliable Low-Latency Communications: Challenges and Envisioned System Enhancements. IEEE Netw. 2018, 32, 8–15. [Google Scholar] [CrossRef]
- She, C.; Sun, C.; Gu, Z.; Li, Y.; Yang, C.; Poor, H.V.; Vucetic, B. A Tutorial on Ultrareliable and Low-Latency Communications in 6G: Integrating Domain Knowledge Into Deep Learning. Proc. IEEE 2021, 109, 204–246. [Google Scholar] [CrossRef]
- Shi, Z.; Xie, X.; Garg, S.; Lu, H.; Yang, H.; Xiong, Z. Deep Reinforcement Learning Based Big Data Resource Management for 5G/6G Communications. In Proceedings of the 2021 IEEE Global Communications Conference (GLOBECOM), Madrid, Spain, 7–11 December 2021; pp. 01–06. [Google Scholar] [CrossRef]
- Chowdhury, M.Z.; Shahjalal, M.; Ahmed, S.; Jang, Y.M. 6G Wireless Communication Systems: Applications, Requirements, Technologies, Challenges, and Research Directions. IEEE Open J. Commun. Soc. 2020, 1, 957–975. [Google Scholar] [CrossRef]
- Salh, A.; Audah, L.; Shah, N.S.M.; Alhammadi, A.; Abdullah, Q.; Kim, Y.H.; Al-Gailani, S.A.; Hamzah, S.A.; Esmail, B.A.F. A Survey on Deep Learning for Ultra-Reliable and Low-Latency Communications Challenges on 6G Wireless Systems. IEEE Access 2021, 9, 55098–55131. [Google Scholar] [CrossRef]
- Niknam, S.; Dhillon, H.S.; Reed, J.H. Federated Learning for Wireless Communications: Motivation, Opportunities, and Challenges. IEEE Commun. Mag. 2020, 58, 46–51. [Google Scholar] [CrossRef]
- Caldarola, D.; Caputo, B.; Ciccone, M.; di Torino, P.; CINI. Improving Generalization in Federated Learning by Seeking Flat Minima. Available online: https://arxiv.org/abs/2203.11834 (accessed on 20 March 2022).
- Al-Saedi, A.A.; Boeva, V.; Casalicchio, E. Reducing Communication Overhead of SFederated Learning through Clustering Analysis. In Proceedings of the 2021 IEEE Symposium on Computers and Communications (ISCC), Athens, Greece, 5–8 September 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Priyanka Mary Mammen, University of Massachusetts, Amherst. Federated Learning: Opportunities and Challenges. Available online: https://arxiv.org/abs/2101.05428 (accessed on 14 January 2021).
- Konečný, J.; McMahan, H.B.; Yu, F.X.; Richtárik, P.; Suresh, A.T.; Bacon, D. Federated learning: Strategies for improving communication efficiency. arXiv 2016, arXiv:1610.05492. [Google Scholar]
- Tran, N.H.; Bao, W.; Zomaya, A.; Nguyen, M.N.H.; Hong, C.S. Federated learning over wireless networks: Optimization model design and analysis. In Proceedings of the IEEE Conference on Computer Communications, Paris, France, 29 April–2 May 2019; IEEE: Toulouse, France, 2019; pp. 1387–1395. [Google Scholar]
- Bonawitz, K.; Eichner, H.; Grieskamp, W.; Huba, D.; Ingerman, A.; Ivanov, V.; Kiddon, C.; Konečný, J.; Mazzocchi, S.; McMahan, B.; et al. Towards Federated Learning at Scale: System Design. in SysML 201. [Online]. Available online: https://arxiv.org/abs/1902.01046 (accessed on 4 February 2019).
- Liu, Y.; Yuan, X.; Xiong, Z.; Kang, J.; Wang, X.; Niyato, D. Federated learning for 6G communications: Challenges, methods, and future directions. China Commun. 2020, 17, 105–118. [Google Scholar] [CrossRef]
- Siriwardhana, Y.; Porambage, P.; Liyanage, M.; Ylianttila, M. AI and 6G Security: Opportunities and Challenges. In Proceedings of the 2021 Joint European Conference on Networks and Communications & 6G Summit (EuCNC/6G Summit), Porto, Portugal, 8–11 June 2021; pp. 616–621. [Google Scholar] [CrossRef]
- Gracia, M.B.; Malele, V.; Ndlovu, S.P.; Mathonsi, T.E.; Maaka, L.; Muchenje, T. 6G Security Challenges and Opportunities. In Proceedings of the 2022 IEEE 13th International Conference on Mechanical and Intelligent Manufacturing Technologies (ICMIMT), Cape Town, South Africa, 25–27 May 2022; pp. 339–343. [Google Scholar] [CrossRef]
- Li, W.; Su, Z.; Li, R.; Zhang, K.; Wang, Y. Blockchain-Based Data Security for Artificial Intelligence Applications in 6G Networks. IEEE Netw. 2020, 34, 31–37. [Google Scholar] [CrossRef]
- Singh, D. Features Architecture and Security Issues in 5G and 6G Communication. In Proceedings of the 2022 8th International Conference on Signal Processing and Communication (ICSC), Noida, India, 1–3 December 2022; pp. 117–120. [Google Scholar] [CrossRef]
- Bindu, G.; S, I.T.J.; Kanakala, V.R.; Niharika, G.L.K.; Raj, B.E. Impact of Blockchain Technology in 6G Network: A Comprehensive survey. In Proceedings of the 2022 International Conference on Inventive Computation Technologies (ICICT), Lalitpur, Nepal, 20–22 July 2022; pp. 328–334. [Google Scholar] [CrossRef]
- Hewa, T.; Gür, G.; Kalla, A.; Ylianttila, M.; Bracken, A.; Liyanage, M. The Role of Blockchain in 6G: Challenges, Opportunities and Research Directions. In Proceedings of the 2020 2nd 6G Wireless Summit (6G SUMMIT), Levi, Finland, 17–20 March 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Manoharan, V.S.R.; Ramachandran, S.; Rajasekar, V. Blockchain Based Privacy Preserving Framework for Emerging 6G Wireless Communications. IEEE Trans. Ind. Inform. 2022, 18, 4868–4874. [Google Scholar] [CrossRef]
| Key Performance Indicators (KPIs) | 5G | 6G |
|---|---|---|
| Maximum Achievable Data Rate | 10 Gbps | 1 Tbps |
| End-to-End latency | 10 ms | 1 ms |
| Spectral Efficiency | 30 bps/Hz | 100 bps/Hz |
| Reliability (FER) | 10−5 | 10−9 |
| Jitter | Not Specified | 1 us |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kamath, S.; Anand, S.; Buchke, S.; Agnihotri, K. A Review of Recent Developments in 6G Communications Systems. Eng. Proc. 2023, 59, 167. https://doi.org/10.3390/engproc2023059167
Kamath S, Anand S, Buchke S, Agnihotri K. A Review of Recent Developments in 6G Communications Systems. Engineering Proceedings. 2023; 59(1):167. https://doi.org/10.3390/engproc2023059167
Chicago/Turabian StyleKamath, Srikanth, Somilya Anand, Suyash Buchke, and Kaushikee Agnihotri. 2023. "A Review of Recent Developments in 6G Communications Systems" Engineering Proceedings 59, no. 1: 167. https://doi.org/10.3390/engproc2023059167
APA StyleKamath, S., Anand, S., Buchke, S., & Agnihotri, K. (2023). A Review of Recent Developments in 6G Communications Systems. Engineering Proceedings, 59(1), 167. https://doi.org/10.3390/engproc2023059167





