We now present a few examples to more clearly explain possible vulnerabilities of existing PLS schemes in VLC systems. Specifically, we study three examples showing that well-known PLS transmission techniques—i.e., beamforming, artificial jamming, and LED selection—can be overcome by artful eavesdropper behavior.
In PLS theories, the secrecy capacity
is a fundamental metric relating to the maximum rate a transmitter can send to satisfy the reliability and secrecy [
3]. The secrecy capacity is defined as
where
denotes the mutual information. Also,
is the input distribution on the transmitted signal
X at the transmitter, and
Y and
Z denote the signals observed at the legitimate user and the eavesdropper, respectively. On the other hand, when the instantaneous CSI of an eavesdropper is not available at the transmitter, while only its statistical information is possible, a secrecy outage probability (SOP) is used as a primary security performance metric instead of the secrecy capacity [
17]. The SOP is defined as the likelihood that the instantaneous secrecy capacity
is less than a threshold value
, i.e.,
. Since this paper discusses the secrecy performance in the presence of a passive eavesdropper whose CSI is assumed to be unavailable at the transmitter, we utilize the SOP (with setting
) to measure the secrecy performance in the following subsections.
3.1. Beamforming
Beamforming strategies are popular methods to improve the secrecy performance in RF systems. The transmitters take the CSI of receivers into account in transmitting the information signals such that the waveforms reach only the UE sites with a high SNR, while suppressing the information signals elsewhere, especially at electron device (ED) sites [
18]. Various beamforming approaches were also rigorously proposed and studied for VLC systems to increase secrecy by tailoring RF beamforming to VLC environments; however, the VLC beamforming schemes retain weak points that an ED might exploit. This section explains the VLC beamforming’s weakness in the simultaneous presence of active and passive EDs by explaining the ZF (zero-forcing) beamforming [
6] as an example.
ZF precoding is a well-known and practical PLS transmission technique in VLC systems that eliminates information reception at an unintended user by carefully designing the precoding matrix. ZF was shown to effectively decouple a legitimate user from possible malicious users and significantly improve various security measures. More specifically, according to [
6], the precoding matrix can be designed to lie in the nullspace of the eavesdropper’s channel. In this case, multiple LED transmitters multiply a data signal by the precoding matrix before transmitting, which can force the reception of the unintended user to zero. Therefore, the achievable secure communication rate under ZF can be almost equal to the achievable rate of the intended user’s point-to-point channel.
However, ZF has limitations with regard to feasibility and performance. First, due to intrinsic condition that the LED transmitters have to retain the CSI of both the legitimate user and malicious users, ZF cannot cope with the threat of unknown passive eavesdroppers (i.e., their CSI is not known to LEDs), which limits the practical use of this approach.
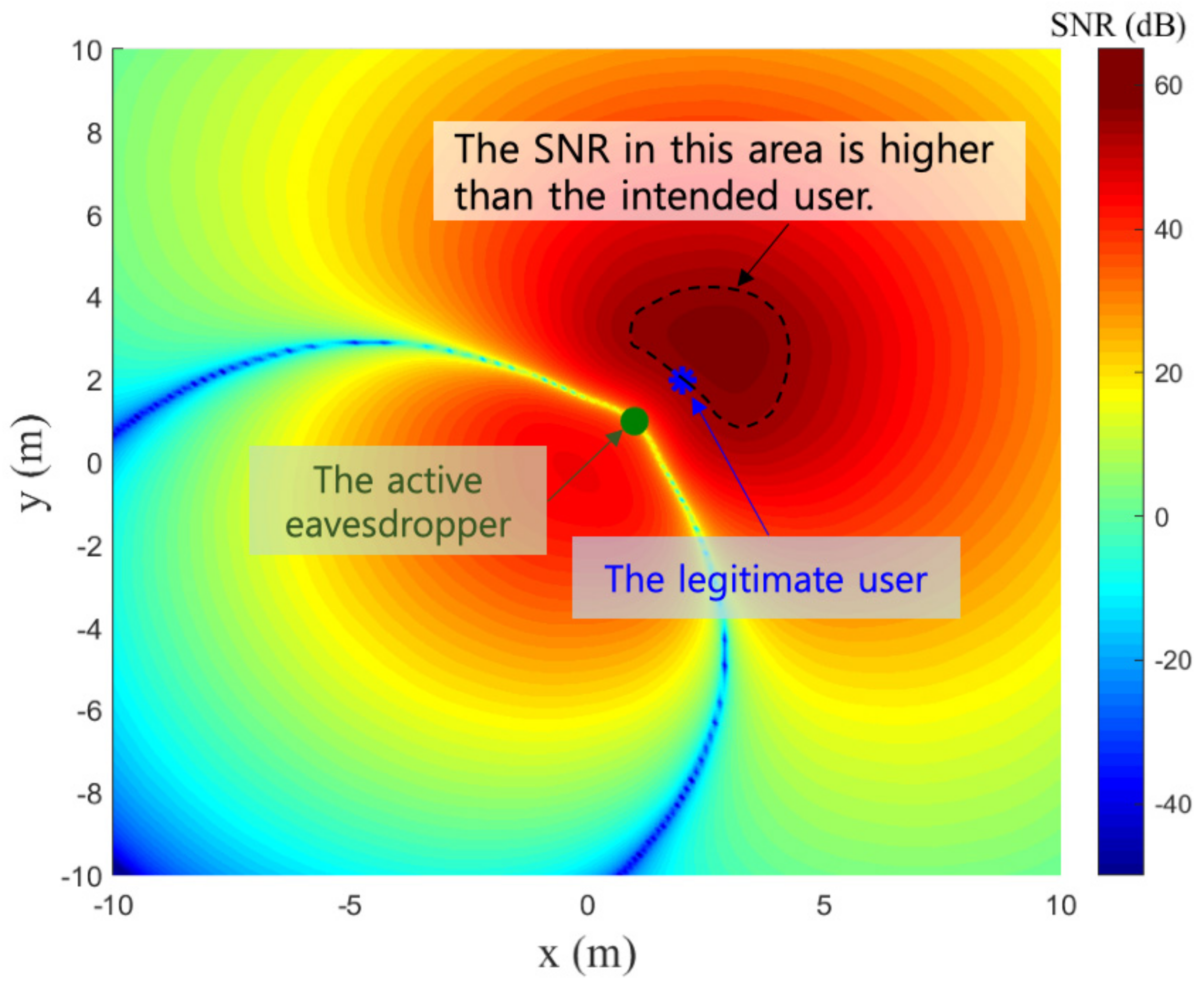
Second, ZF can make the VLC system more vulnerable when passive eavesdroppers are present together with an active eavesdropper whose CSI is known, as illustrated in the example in
Figure 1. The figure shows the SNRs according to the receiver location when ZF is adopted. A
transmitter array is assumed to consist of uniformly distributed LEDs on a square lattice in a room of dimension
. One legitimate user and one active eavesdropper are assumed to be present. These receivers are marked with blue and green dots in the figure. Also, multiple passive eavesdroppers are assumed to be distributed according to a Poisson point process (PPP) with the density
.
In
Figure 1, even when the active eavesdropper is located close to the legitimate user, ZF effectively minimizes the information reception at the active eavesdropper site by utilizing precoding. From this result, ZF appears to secure the transmission against the eavesdropper. However, from the perspective of the passive randomly located eavesdroppers, as shown in
Figure 1, it is possible to achieve a higher SNR than the legitimate user. Note that if any passive eavesdropper is located in the dashed area in
Figure 1, it can achieve a higher SNR than the legitimate user. Although ZF precoding can minimize the SNR at the active eavesdropper site, ZF precoding for the nearby eavesdropper expands the dashed area in which the SNR is higher than that of the legitimate user. This vulnerability comes from the fact that the ZF design purely aims at forcing the active eavesdropper’s SNR to zero without consideration for the legitimate user’s SNR (or, indeed, SNRs of other unknown receivers in the area).
Figure 2 verifies the vulnerability of ZF by depicting the secure outage probability (SOP) as a function of the distance between the legitimate user and the active eavesdropper. Note that a secure outage occurs only when one or more passive eavesdroppers can decode the transmitted message; while the SNR of the active eavesdropper is minimized by the ZF precoder. As the active eavesdropper approaches the legitimate user, the SOP increases, indicating that ZF precoding presents more wiretap opportunities to passive eavesdroppers located in the region.
Our recent work [
13] proposed an enhanced ZF beamforming scheme to mitigate the weakness from the presence of active and passive eavesdroppers; however, it cannot entirely eliminate the dashed area in which the eavesdroppers can achieve higher SNR. To the author’s best knowledge, this weakness is inevitable due to the VLC’s intrinsic characteristics that fading does not exist and that a received SNR mainly depends on the geometric properties of the transmitter and receiver.
3.2. Artificial Jamming
In reality, since an eavesdropper should escape the vigilance of a legitimate user or a network manager, it should strive for concealment while eavesdropping the transmission. However, since the channel gain in VLC systems largely depends on the distance between the transmitter and the receiver, the eavesdropper must be located in close proximity to the LED transmitter that serves the target user, thus risking being detected. Alternatively, the eavesdropper can augment its receiver sensitivity by, for example, increasing an area of its PD, adopting a high-gain optical lens, or directing its orientation toward the LED transmitter. These modifications can allow the eavesdropper to achieve a higher SNR even when located at a significant distance from the target user. For example, in [
19], a telescope was used to increase the gain of the receiver in an experimental test, and the VLC transmission was successfully eavesdropped a large distance from the transmitter. On the other hand, to cope with an eavesdropper equipped with a better receiver than the intended user, various artificial jamming strategies for VLC systems were proposed [
8,
9,
11,
20]. The jamming strategy was shown to be a powerful and practical approach to secure VLC systems, particularly against eavesdroppers with enhanced receiver architectures, since it would be impossible to distinguish between the information and jamming signals.
On the other hand, two intrinsic properties of VLC systems enable eavesdroppers to overcome the jamming strategy. The first is that the multiple LED transmitters must be spatially distributed to illuminate the entire room evenly within the lighting standards, and the second is that the channel gain in VLC systems largely depends on the distance between the transmitter and the receiver. These two properties lead the jamming strategies to perform in a way that the LEDs near to the intended user emit the information, while the distant LEDs emit the jamming signals [
11]. In other words, unlike RF systems, the eavesdropper can anticipate which LED performs as either an information transmitter or a jammer, and selectively receives only the information signal, excluding the jamming signals, by narrowing the receiver FoV and accurately aligning the receiver’s orientation toward the target LED transmitter. Note that, in RF systems, multiple antennas being positioned at the same location simultaneously emit the information and jamming signals, which contrasts significantly with the VLC case.
Figure 3 illustrates an example that an eavesdropper narrows its FoV and attempts to wiretap an information-bearing signal while minimizing the reception of jamming signals. In the figure,
LEDs are assumed to be uniformly distributed on a square lattice in a room of
, and one legitimate user and one eavesdropper are supposed to be positioned in the region. The nearest LED to the legitimate user is chosen to transmit the information-bearing signal, while all the other LEDs act as jammers. Also, it is assumed that the transmitters know the CSI of both the intended and malicious users. According to [
8], the jammers obtain the precoding matrix by designing an optimization problem that maximizes the jamming signal reception at the eavesdropper while aligning it to the null space of the legitimate user’s channel. Then, the jammers multiply a random noise signal by the precoding matrix and transmit it to hinder information reception at the eavesdropper site.
Figure 4 shows the results from numerical experiments that simulate the signal-to-interference-plus-noise ratio (SINR) for the scenario explained in
Figure 3.
Figure 4a shows the SINR as a function of the distance between the legitimate user and the eavesdropper for different eavesdropper FoVs
. We note that the eavesdropper with a narrow FoV can effectively exclude the jamming signals and achieve a higher SINR than the legitimate user when the eavesdropper is located not too far from the legitimate user. According to the VLC channel gain model [
16], a receiver equipped with an optical concentration lens with a narrower FoV would yield a better receiver sensitivity. Therefore, the eavesdropper can achieve a higher SINR than the legitimate user to exclude the jamming signal even at a further distance. Also,
Figure 4a shows that as the FoV becomes narrower, the eavesdropper can exclude the jamming signal at a further distance. For example, the eavesdropper with
should be within
of the legitimate user to exclude the effects of the jamming signal. But, an eavesdropper with a narrower FoV, e.g.,
, can wiretap the transmission as far as
from the legitimate user. In contrast, when the eavesdropper fails to exclude the jamming signals due to the extended sight of its PD, the eavesdropper’s SINR suddenly drops.
On the other hand,
Figure 4b gives an insight into how one might cope with an eavesdropper with a narrow FoV. The figure shows the SINR for the different numbers of transmitters as a function of the distance between the legitimate user and the eavesdropper. Note that, to maintain a constant level of illumination (even with different numbers of LEDs), we fix the total optical power emitted from the LED array by reducing or increasing the optical power of each LED for the different sets of results. As the number of LEDs increases within a fixed geometry, the distances among the LEDs decrease, which allows the information transmitter and the jammer to be located closer to each other. Therefore, it would be more difficult for the eavesdropper to exclude the jamming signal by using its narrow FoV receiver. More specifically, as shown in the figure, when
and the nearest distance between the information transmitter and the jammers is
, the eavesdropper with
can wiretap the information as long as it is positioned within
of the legitimate user; yet, when the LED array size is increased to
, the eavesdropper must be positioned within
of the legitimate user to intercept the signal (i.e., to achieve a higher SINR). The nonmonotonic results for the long distances between the legitimate user and the eavesdropper are due to the design of the jamming precoding strategy, which is optimized such that the eavesdropper that has the same receiver properties as the legitimate user experiences a high degree of jamming. However, for an eavesdropper with different receiver properties—i.e., narrow FoV aligned with the information LED—jamming is not optimized and instead depends upon geometric factors related to the eavesdropper position relative to the neighboring LEDs.
3.3. Cooperative Eavesdroppers in Multiuser VLC Systems
VLC offers the option of dense spatial reuse due to the fact that visible light cannot penetrate an opaque wall and decays quickly with distance. These features enable VLC systems to serve many users simultaneously with high data rates and short time delays. Thus, various PLS transmission techniques for multiuser VLC systems were proposed [
21,
22]. These works have shown that the PLS can effectively secure VLC transmissions in the presence of either active or passive eavesdroppers under certain conditions.
However, in multiuser VLC systems in large open spaces, it would be challenging to distinguish between legitimate and malicious users and would also be impractical to impose on the number and type of eavesdroppers. Moreover, in a public area, it may be too lenient to issue access authority to network users. These properties of multiuser VLC systems lead us to expect an eavesdropping scenario that a malicious user can legitimately access the network and cooperate with other passive (not registered) eavesdroppers to wiretap the information-bearing signal more efficiently. Here, we will look into such a scenario whereby registered and passive eavesdroppers cooperate.
Figure 5 shows an example of the VLC system in question, in which registered and passive eavesdroppers are present. Since the nearest LED is typically assumed to serve the mobile VLC user to maximize the rate of the communication link [
10], it is assumed here that LED cooperation does not take place. Thus, registered users, including the legitimate user and the registered eavesdropper, would be served by their nearest LEDs, i.e.,
and
, respectively. Also, a few passive eavesdroppers are assumed to be distributed according to a PPP with density
around
to wiretap the transmission from
to the legitimate user. The registered and passive eavesdroppers can cooperate in the following way. Before and while
communicates to the legitimate user employing a wiretap coding scheme, the registered eavesdropper induces its serving transmitter
to emit a
promised signal. Note that this is possible since the registered eavesdropper has the legitimate right to access the network. The promised signal, which is a waveform modulated from any data bits, e.g., a string of random binary numbers, is already disclosed to other passive eavesdroppers and saved in a remote server/node to be requested by the registered eavesdropper. At the same time, the passive eavesdroppers attempt to wiretap the signal being transmitted from
to the legitimate user. Here, since the promised signal, which is supposed to interfere with the signal reception of the desired information, is already known to the passive eavesdroppers, they can cancel the interference to extract only the information component. Note that since the legitimate user does not know the promised signal, the signal coming from
can interfere with the communication between
and the legitimate user, i.e., it acts like a jamming signal. Therefore, the promised signal can reduce the SINR of the legitimate user while not affecting the passive eavesdroppers.
Figure 6 shows the SOP for different passive eavesdropper densities
as a function of the distance between the legitimate user and the registered eavesdropper. Here, the legitimate user is assumed to be located below its serving LED, i.e.,
. When there is no cooperation among the eavesdroppers, the legitimate user can achieve the highest SINR compared to the eavesdroppers. Thus, as shown in the figure, the SOP without eavesdropper cooperation is zero regardless of
. However, when the eavesdroppers cooperate, the promised signal being emitted from
interferes with the transmission from
to the legitimate user, which results in a decrease of the legitimate user’s SINR; hence, an outage can occur. Moreover, as the registered eavesdropper approaches the legitimate user, its serving LED changes to an LED located closer to the legitimate user, which increases the received power of the promised signal at the legitimate user site; thus, the SOP increases. Note that the LED transmitters are discrete; thus, the SOP with the eavesdroppers’ cooperation shows cascading increases. This result verifies that even when the legitimate user is located at nearest place to its serving LED and is expected to retain the highest SNR among multiple users, the cooperation between registered and passive eavesdroppers can weaken the legitimate user’s reception and effectively wiretap the VLC transmission.