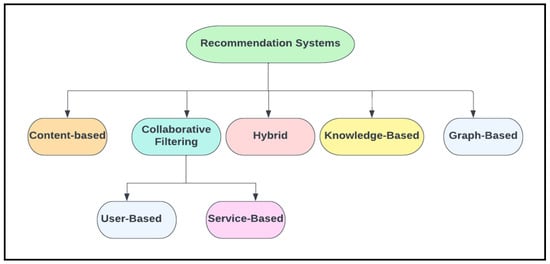
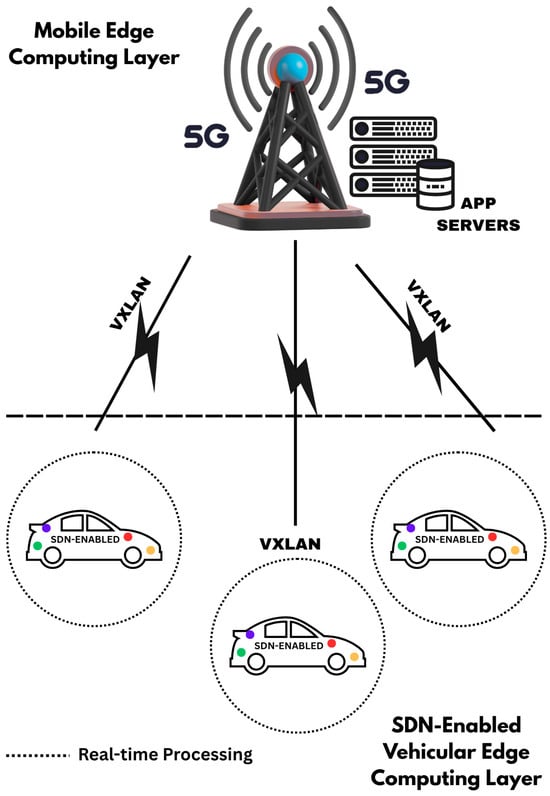
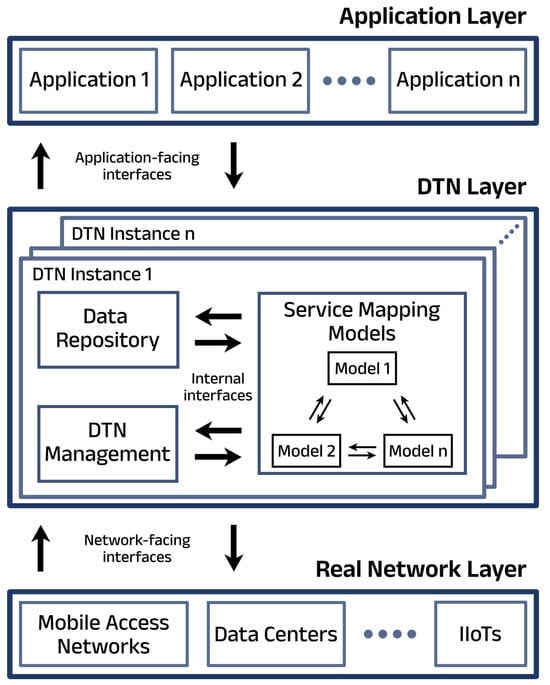
Journal Description
Network
- Open Access— free for readers, with article processing charges (APC) paid by authors or their institutions.
- High Visibility: indexed within ESCI (Web of Science), Scopus, EBSCO, and other databases.
- Journal Rank: JCR - Q2 (Computer Science, Information Systems) / CiteScore - Q1 (Engineering (miscellaneous))
- Rapid Publication: manuscripts are peer-reviewed and a first decision is provided to authors approximately 20.1 days after submission; acceptance to publication is undertaken in 5.6 days (median values for papers published in this journal in the first half of 2025).
- Recognition of Reviewers: APC discount vouchers, optional signed peer review, and reviewer names published annually in the journal.
- Network is a companion journal of Electronics.
Latest Articles
Highly Accessed Articles
Latest Books
E-Mail Alert
News
Topics
Deadline: 31 October 2025
Deadline: 31 May 2026
Deadline: 30 September 2026
Conferences
Special Issues
Deadline: 15 October 2025
Deadline: 31 October 2025
Deadline: 31 October 2025
Deadline: 20 November 2025