Web3: Exploring Decentralized Technologies and Applications for the Future of Empowerment and Ownership
Abstract
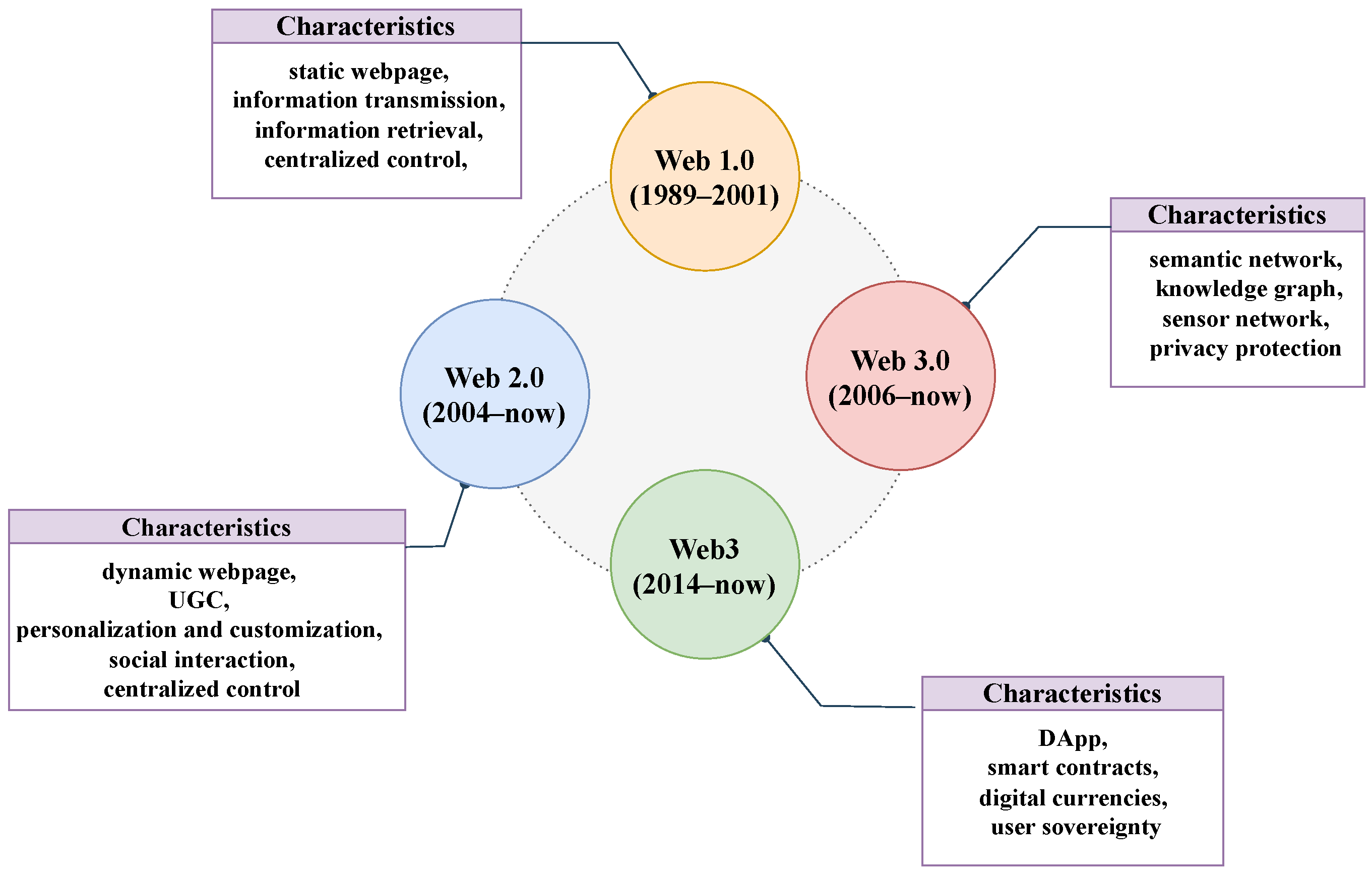
:1. Introduction
- We conducted a survey of 84 papers related to Web3, providing an analysis of the current research status.
- We detail and explain the relevant technologies and applications of Web3 to provide enhanced clarity on the key techniques of system construction and application scenarios of Web3.
- Through an SWOT analysis, we have performed an objective analysis of the present challenges and outlined future development trends for Web3.
2. Materials and Methods
3. Key Technologies in Web3
3.1. Blockchains
3.1.1. Digital Signatures
3.1.2. Merkle Trees
3.1.3. Consensus Mechanisms
3.1.4. Smart Contracts
3.2. Data Storage
3.2.1. Filecoin
3.2.2. Storj
3.2.3. Sia
3.3. Self-Sovereign Identity
- Decentralized Identification [47]: individuals use decentralized identifiers (DID) to establish unique identities within the network; DID is a globally unique identifier that can be implemented through blockchain technology or other distributed ledger technologies, ensuring secure and tamper-proof identity verification.
- User Control: in the SSI model, individuals have complete autonomy over their identity information; they have the freedom to determine when, where, and with whom their identifiable information is shared, providing enhanced safeguards for personal privacy and data protection.
- Decentralized Identity Verification [48]: SSI relies on a decentralized identity certificates (VC) without the need for centralized identity verification agencies; this approach ensures greater independence, privacy, and control over one’s personal identity credentials.
- Data Ownership: in the SSI model, individuals retain full ownership of their identity data, possessing the freedom to store their identity data in decentralized storage systems and the authority to grant or revoke access to this data for other entities; this allows individuals to exercise enhanced control over their personal information, enabling them to make informed decisions regarding its use and disclosure.

3.4. NFTs
4. Application Prospect
4.1. Decentralized Autonomous Organization
- Establishment: the establishment of a DAO usually starts with an initial stage in which the creator or initiator develops and publishes the governance agreement, smart contracts, and associated rules and conditions. These rules may encompass voting mechanisms, governance processes, token economics, and other aspects.
- Participant joining: anyone can freely choose to participate in the DAO and become a member by holding DAO tokens. By purchasing tokens, participating in pledges, or making other contributions, members acquire rights and privileges within the DAO and gain the ability to participate in decision-making progresses.
- Decision-making: DAO decision-making is achieved through members’ votes. Each member has the opportunity to vote for or against specific proposals based on their token holdings or other designated stake. These proposals can encompass crucial decisions, including funding allocations, changes to governance rules, project development directions, and more. The collective voting process ensures that decision are made in a democratic and transparent manner, reflecting the consensus and preferences of the DAO community.
- Smart contract execution: governance protocols and regulations for DAOs are commonly implemented as smart contracts and carried out on the blockchain. Decisions automatically executed according to the voting results of members, ensuring transparency, accuracy, and tamper-resistance in a process that becomes trustless and immutable. This obviates the need for intermediaries and provide a reliable framework for decision-making.
- Governance and operation: DAO members can submit proposals, discuss issues, participate in voting, and supervise the operation of the DAO during the process of participating in governance and operation. The governance and operation of the DAO can be achieved through regular voting, community discussions, governance committees, etc.
- Distribution and rewards: DAOs can motivate and reward members’ contributions through the token economic model. According to the rules of the DAO, members may receive token rewards, dividends, governance rights, or other forms of rewards to encourage participation and contribution.
- Audit and supervision: because the smart contracts and decisions of the DAO are open and transparent, members and other relevant parties can audit and supervise the activities of the DAO to ensure its compliance, fairness, and transparency.
4.2. Decentralized Finance
- The infrastructure layer primarily consists of the blockchain and its underlying protocols, which serve as the foundational infrastructure for the upper layers. This layer establishes a reliable and secure environment for transactions, ensuring that transaction status transitions are confirmed through the consensus mechanism. It provides a trustworthy storage mechanism for transactions, guaranteeing the integrity and immutability of the data.
- The asset layer is primarily comprised of the native protocol of the blockchain and other asset protocols that are compatible with the underlying blockchain infrastructure. These protocols play a crucial role in determining the standards and rules for handling different types of assets within the ecosystem. They facilitate the generation, transfer, and administration of diverse digital assets, including cryptocurrencies, tokens, and both fungible and non-fungible assets.
- The protocol layer establishes standardized protocols for transactions, lending, and cryptocurrency derivatives within the DeFi ecosystem. It sets the rules and frameworks for executing these financial activities in a decentralized and trustless manner. Additionally, developers have created various user application interfaces that interact with smart contracts through web browsers, enabling users to access and utilize the services provided by these protocols.
4.3. Metaverse
5. Challenges and Future Research Opportunities
5.1. SWOT Analysis
5.2. Application
5.3. Security
- Smart Contracts: as the core component of Web3, smart contracts are bound to have a huge impact on the security of specific Web3 projects. Due to the inability to modify smart contracts after deployment, any vulnerabilities or errors may result in user funding or system paralysis [72]. CeriK, a blockchain security audit firm, reported that in the first half of 2022 Web3 initiatives incurred losses exceeding USD 2 billion from cyberattacks and vulnerabilities, primarily within the domain of smart contracts. Vulnerabilities in smart contracts are mainly caused by programming errors or insufficient security audits, such as re-entrancy [73], gas-related vulnerabilities [74], permission bugs [75], and integer overflow/underflow [76]. Therefore, enhancing the security of smart contracts stands as the focus of Web3-related research.
- Data Issues: the data problem for Web3 consists of two aspects: on the one hand, DApps in Web3 usually store data on a blockchain or distributed storage system. While this provides data transparency and tamper resistance, all data are publicly visible. This means that users’ personal data may not be anonymized unless additional privacy protection measures are taken [68]. On the other hand, owing to the inherent limitations in storing extensive data on the blockchain, Web3 applications usually need to interact with traditional internet applications and external data sources. Linking off-chain data (such as personally identifiable information) with on-chain data (such as transaction records) can threaten user privacy. Without proper privacy protection measures, sensitive information may be disclosed.
5.4. Legality
5.5. Opportunities
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Wang, Q.; Li, R.; Wang, Q.; Chen, S.; Ryan, M.; Hardjono, T. Exploring web3 from the view of blockchain. arXiv 2022, arXiv:2206.08821. [Google Scholar]
- Hasan, R.; Anwar, Z.; Yurcik, W.; Brumbaugh, L.; Campbell, R. A survey of peer-to-peer storage techniques for distributed file systems. In Proceedings of the International Conference on Information Technology: Coding and Computing (ITCC’05)-Volume II, Las Vegas, NV, USA, 4–6 April 2005; Volume 2, pp. 205–213. [Google Scholar]
- Jain, A.; Farkas, C. Secure resource description framework: An access control model. In Proceedings of the Eleventh ACM Symposium on Access Control Models and Technologies, Lake Tahoe, CA, USA, 7–9 June 2006; pp. 121–129. [Google Scholar]
- Nakamoto, S.; Bitcoin, A. A peer-to-peer electronic cash system. Bitcoin 2008, 4, 15. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Cai, W.; Wang, Z.; Ernst, J.B.; Hong, Z.; Feng, C.; Leung, V.C. Decentralized applications: The blockchain-empowered software system. IEEE Access 2018, 6, 53019–53033. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Chen, W.; Chen, X.; Weng, J.; Imran, M. An overview on smart contracts: Challenges, advances and platforms. Future Gener. Comput. Syst. 2020, 105, 475–491. [Google Scholar] [CrossRef]
- Karantias, K. SoK: A Taxonomy of Cryptocurrency Wallets. Available online: https://eprint.iacr.org/2020/868 (accessed on 6 December 2023).
- Filipčić, S. Web3 & DAOs: An overview of the development and possibilities for the implementation in research and education. In Proceedings of the 2022 45th Jubilee International Convention on Information, Communication and Electronic Technology (MIPRO), Opatija, Croatia, 23–27 May 2022; pp. 1278–1283. [Google Scholar]
- Keizer, N.V.; Yang, F.; Psaras, I.; Pavlou, G. The case for AI based Web3 reputation Systems. In Proceedings of the 2021 IFIP Networking Conference (IFIP Networking), Espoo and Helsinki, Finland, 21–24 June 2021; pp. 1–2. [Google Scholar]
- Borgen, K.A.T. Web3 for sensitive data, enterprise, government, private, and permissioned use. In Proceedings of the 2022 IEEE 1st Global Emerging Technology Blockchain Forum: Blockchain & Beyond (iGETblockchain), Irvine, CA, USA, 7–11 June 2022; pp. 1–6. [Google Scholar]
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Khan, J.A.; Ozbay, K. AFFIRM: Privacy-by-Design Blockchain for Mobility Data in Web3 using Information Centric Fog Networks with Collaborative Learning. In Proceedings of the 2023 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 20–22 February 2023; pp. 456–462. [Google Scholar]
- Chen, C.; Zhang, L.; Li, Y.; Liao, T.; Zhao, S.; Zheng, Z.; Huang, H.; Wu, J. When digital economy meets web 3.0: Applications and challenges. IEEE Open J. Comput. Soc. 2022, 3, 233–245. [Google Scholar] [CrossRef]
- Guan, C.; Ding, D.; Guo, J. Web3. 0: A Review And Research Agenda. In Proceedings of the 2022 RIVF International Conference on Computing and Communication Technologies (RIVF), Ho Chi Minh City, Vietnam, 20–22 December 2022; pp. 653–658. [Google Scholar]
- Weyl, E.G.; Ohlhaver, P.; Buterin, V. Decentralized Society: Finding Web3’s Soul. Available at SSRN 4105763. 2022. Available online: https://www.microsoft.com/en-us/research/publication/decentralized-society-finding-web3s-soul/ (accessed on 6 December 2023).
- Wan, S.; Lin, H.; Gan, W.; Chen, J.; Yu, P.S. Web3: The Next Internet Revolution. arXiv 2023, arXiv:2304.06111. [Google Scholar]
- Kumar, A.; Krishnamurthi, R.; Nayyar, A.; Sharma, K.; Grover, V.; Hossain, E. A novel smart healthcare design, simulation, and implementation using healthcare 4.0 processes. IEEE Access 2020, 8, 118433–118471. [Google Scholar] [CrossRef]
- Belk, R.; Humayun, M.; Brouard, M. Money, possessions, and ownership in the Metaverse: NFTs, cryptocurrencies, Web3 and Wild Markets. J. Bus. Res. 2022, 153, 198–205. [Google Scholar] [CrossRef]
- Wang, X.; Yang, J.; Han, J.; Wang, W.; Wang, F.Y. Metaverses and DeMetaverses: From digital twins in CPS to parallel intelligence in CPSS. IEEE Intell. Syst. 2022, 37, 97–102. [Google Scholar] [CrossRef]
- Schlatt, V.; Sedlmeir, J.; Feulner, S.; Urbach, N. Designing a framework for digital KYC processes built on blockchain-based self-sovereign identity. Inf. Manag. 2022, 59, 103553. [Google Scholar] [CrossRef]
- Qin, R.; Ding, W.; Li, J.; Guan, S.; Wang, G.; Ren, Y.; Qu, Z. Web3-based decentralized autonomous organizations and operations: Architectures, models, and mechanisms. IEEE Trans. Syst. Man Cybern. Syst. 2022, 53, 2073–2082. [Google Scholar] [CrossRef]
- Subramanian, H.; Subramanian, S. Improving diagnosis through digital pathology: Proof-of-concept implementation using smart contracts and decentralized file storage. J. Med. Internet Res. 2022, 24, e34207. [Google Scholar] [CrossRef] [PubMed]
- Buldas, A.; Draheim, D.; Gault, M.; Laanoja, R.; Nagumo, T.; Saarepera, M.; Shah, S.A.; Simm, J.; Steiner, J.; Tammet, T.; et al. An ultra-scalable blockchain platform for universal asset tokenization: Design and implementation. IEEE Access 2022, 10, 77284–77322. [Google Scholar] [CrossRef]
- Vidal-Tomás, D. The illusion of the metaverse and meta-economy. Int. Rev. Financ. Anal. 2023, 86, 102560. [Google Scholar] [CrossRef]
- George, W.; Al-Ansari, T. Review of Blockchain Applications in Food Supply Chains. Blockchains 2023, 1, 34–57. [Google Scholar] [CrossRef]
- Liu, Z.; Xiang, Y.; Shi, J.; Gao, P.; Wang, H.; Xiao, X.; Wen, B.; Li, Q.; Hu, Y.C. Make web3. 0 connected. IEEE Trans. Dependable Secur. Comput. 2021, 19, 2965–2981. [Google Scholar] [CrossRef]
- Yang, T.; Zhang, Y.; Xiao, S.; Zhao, Y. Digital signature based on ISRSAC. China Commun. 2021, 18, 161–168. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef]
- Buterin, V. A next-generation smart contract and decentralized application platform. White Pap. 2014, 3, 1–2. [Google Scholar]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A provably secure proof-of-stake blockchain protocol. In Proceedings of the A37th Annual International Cryptology Conference, Santa Barbara, CA, USA, 20–24 August 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 357–388. [Google Scholar]
- Xu, G.; Liu, Y.; Khan, P.W. Improvement of the DPoS consensus mechanism in blockchain based on vague sets. IEEE Trans. Ind. Inform. 2019, 16, 4252–4259. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. In Proceedings of the OsDI, New Orleans, LA, USA, 22–25 February 1999; Volume 99, pp. 173–186. [Google Scholar]
- Zhang, T.Y.; Feng, T.T.; Cui, M.L. Smart contract design and process optimization of carbon trading based on blockchain: The case of China’s electric power sector. J. Clean. Prod. 2023, 397, 136509. [Google Scholar] [CrossRef]
- Jiang, Z.; Zheng, Z.; Chen, K.; Luo, X.; Tang, X.; Li, Y. Exploring smart contract recommendation: Towards efficient blockchain development. IEEE Trans. Serv. Comput. 2022, 16, 1822–1832. [Google Scholar] [CrossRef]
- Dimakis, A.G.; Ramchandran, K.; Wu, Y.; Suh, C. A survey on network codes for distributed storage. Proc. IEEE 2011, 99, 476–489. [Google Scholar] [CrossRef]
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 162, 102656. [Google Scholar] [CrossRef]
- Wang, M.; Duan, M.; Zhu, J. Research on the security criteria of hash functions in the blockchain. In Proceedings of the 2nd ACM Workshop on Blockchains, Cryptocurrencies, and Contracts, Incheon, Republic of Korea, 4 June 2018; pp. 47–55. [Google Scholar]
- Guidi, B.; Michienzi, A.; Ricci, L. Evaluating the decentralisation of filecoin. In Proceedings of the 3rd International Workshop on Distributed Infrastructure for the Common Good, Quebec City, QC, Canada, 7 November 2022; pp. 13–18. [Google Scholar]
- Damgård, I.; Ganesh, C.; Orlandi, C. Proofs of replicated storage without timing assumptions. In Proceedings of the Advances in Cryptology–CRYPTO 2019: 39th Annual International Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 355–380. [Google Scholar]
- Moran, T.; Orlov, I. Simple proofs of space-time and rational proofs of storage. In Proceedings of the Advances in Cryptology–CRYPTO 2019: 39th Annual International Cryptology Conference, Santa Barbara, CA, USA, August 18–22 2019; Springer: Berlin/Heidelberg, Germany, 2019; pp. 381–409. [Google Scholar]
- de Figueiredo, S.; Madhusudan, A.; Reniers, V.; Nikova, S.; Preneel, B. Exploring the Storj Network: A Security Analysis. In Proceedings of the 36th Annual ACM Symposium on Applied Computing, New York, NY, USA, 4 March 2021; SAC ’21. pp. 257–264. [Google Scholar] [CrossRef]
- Zhang, X.; Grannis, J.; Baggili, I.; Beebe, N.L. Frameup: An incriminatory attack on Storj: A peer to peer blockchain enabled distributed storage system. Digit. Investig. 2019, 29, 28–42. [Google Scholar] [CrossRef]
- Vorick, D.; Champine, L. Sia: Simple decentralized storage. Retrieved May 2014, 8, 2018. [Google Scholar]
- Merkle, R.C. Protocols for public key cryptosystems. In Secure Communications and Asymmetric Cryptosystems; Routledge: Abingdon, UK, 2019; pp. 73–104. [Google Scholar]
- Soltani, R.; Nguyen, U.T.; An, A. A survey of self-sovereign identity ecosystem. Secur. Commun. Netw. 2021, 2021, 8873429. [Google Scholar] [CrossRef]
- Reed, D.; Sporny, M.; Longley, D.; Allen, C.; Grant, R.; Sabadello, M.; Holt, J. Decentralized Identifiers (Dids) v1. 0.; Draft Community Group Report; W3C: Wakefield, MA, USA, 2020. [Google Scholar]
- Sporny, M.; Longley, D.; Chadwick, D. Verifiable Credentials Data Model v1.1.; W3C Recommendation; W3C: Wakefield, MA, USA, 2022. [Google Scholar]
- Mühle, A.; Grüner, A.; Gayvoronskaya, T.; Meinel, C. A survey on essential components of a self-sovereign identity. Comput. Sci. Rev. 2018, 30, 80–86. [Google Scholar] [CrossRef]
- Chohan, U.W. Non-fungible tokens: Blockchains, scarcity, and value. Crit. Blockchain Res. Initiat. (CBRI) Work. Pap. 2021. Available online: https://www.semanticscholar.org/paper/Non-Fungible-Tokens%3A-Blockchains%2C-Scarcity%2C-and-Chohan/a37918195898f80d083fdc3a6d83ed79d9f01ded (accessed on 6 December 2023). [CrossRef]
- Roy, A.; Karforma, S. A Survey on digital signatures and its applications. J. Comput. Inf. Technol. 2012, 3, 45–69. [Google Scholar]
- Balduf, L.; Florian, M.; Scheuermann, B. Dude, where’s my NFT: Distributed infrastructures for digital art. In Proceedings of the 3rd International Workshop on Distributed Infrastructure for the Common Good, Quebec City, QC, Canada, 7 November 2022; pp. 1–6. [Google Scholar]
- Aragón, P.; Volkovich, Y.; Laniado, D.; Kaltenbrunner, A. When a movement becomes a party: Computational assessment of new forms of political organization in social media. In Proceedings of the International AAAI Conference on Web and Social Media, Cologne, Germany, 17–20 May 2016; Volume 10, pp. 12–21. [Google Scholar]
- Ferber, J.; Weiss, G. Multi-Agent Systems: An Introduction to Distributed Artificial Intelligence; Addison-Wesley Reading: Boston, MS, USA, 1999; Volume 1. [Google Scholar]
- Wang, S.; Ding, W.; Li, J.; Yuan, Y.; Ouyang, L.; Wang, F.Y. Decentralized autonomous organizations: Concept, model, and applications. IEEE Trans. Comput. Soc. Syst. 2019, 6, 870–878. [Google Scholar] [CrossRef]
- Kitzler, S.; Victor, F.; Saggese, P.; Haslhofer, B. Disentangling decentralized finance (DeFi) compositions. ACM Trans. Web 2023, 17, 1–26. [Google Scholar] [CrossRef]
- Wu, Z.; Liu, J.; Wu, J.; Zheng, Z.; Luo, X.; Chen, T. Know Your Transactions: Real-time and Generic Transaction Semantic Representation on Blockchain & Web3 Ecosystem. In Proceedings of the ACM Web Conference 2023, Austin, TX, USA, 30 April–4 May 2023; pp. 1918–1927. [Google Scholar]
- Schär, F. Decentralized finance: On blockchain-and smart contract-based financial markets. FRB St. Louis Rev. 2021, 103, 153–174. [Google Scholar] [CrossRef]
- Wang, Y.; Chen, Y.; Wu, H.; Zhou, L.; Deng, S.; Wattenhofer, R. Cyclic arbitrage in decentralized exchanges. In Proceedings of the WWW’22: The ACM Web Conference 2022, Lyon, France, 25–29 April 2022; pp. 12–19. [Google Scholar]
- Chen, Z.; Wu, J.; Gan, W.; Qi, Z. Metaverse security and privacy: An overview. In Proceedings of the 2022 IEEE International Conference on Big Data (Big Data), Osaka, Japan, 17–20 December 2022; pp. 2950–2959. [Google Scholar]
- Lin, H.; Wan, S.; Gan, W.; Chen, J.; Chao, H.C. Metaverse in education: Vision, opportunities, and challenges. In Proceedings of the 2022 IEEE International Conference on Big Data (Big Data), Osaka, Japan, 17–20 December 2022; pp. 2857–2866. [Google Scholar]
- Wei, L.; Wang, X.; Wang, T.; Duan, Z.; Hong, Y.; He, X.; Huang, H. Recommendation Systems for the Metaverse. Blockchains 2023, 1, 19–33. [Google Scholar] [CrossRef]
- Puyt, R.W.; Lie, F.B.; Wilderom, C.P. The origins of SWOT analysis. Long Range Plan. 2023, 56, 102304. [Google Scholar] [CrossRef]
- Ferraro, C.; Wheeler, M.A.; Pallant, J.I.; Wilson, S.G.; Oldmeadow, J. Not so trustless after all: Trust in Web3 technology and opportunities for brands. Bus. Horiz. 2023, 66, 667–678. [Google Scholar] [CrossRef]
- Fang, Z.; Zhao, L.; Xiao, M.; Zhou, Y. The Honeycomb Theory of Web3.0. In Proceedings of the 2008 IEEE International Symposium on Service-Oriented System Engineering, Jhongli, Taiwan, 18–19 December 2008; pp. 263–268. [Google Scholar]
- Ding, W.; Hou, J.; Li, J.; Guo, C.; Qin, J.; Kozma, R.; Wang, F.Y. DeSci based on Web3 and DAO: A comprehensive overview and reference model. IEEE Trans. Comput. Soc. Syst. 2022, 9, 1563–1573. [Google Scholar] [CrossRef]
- Xu, H.; Sun, Y.; Li, Z.; Sun, Y.; Zhang, L.; Zhang, X. deController: A Web3 native cyberspace infrastructure perspective. IEEE Commun. Mag. 2023, 61, 68–74. [Google Scholar] [CrossRef]
- Park, A.; Wilson, M.; Robson, K.; Demetis, D.; Kietzmann, J. Interoperability: Our exciting and terrifying Web3 future. Bus. Horiz. 2023, 66, 529–541. [Google Scholar] [CrossRef]
- Murray, A.; Kim, D.; Combs, J. The promise of a decentralized internet: What is Web3 and how can firms prepare? Bus. Horiz. 2023, 66, 191–202. [Google Scholar] [CrossRef]
- Sadowski, J.; Beegle, K. Expansive and extractive networks of Web3. Big Data Soc. 2023, 10, 20539517231159629. [Google Scholar] [CrossRef]
- Winter, P.; Lorimer, A.H.; Snyder, P.; Livshits, B. What’s in your wallet? privacy and security issues in web 3.0. arXiv 2021, arXiv:2109.06836. [Google Scholar]
- Li, H.; Dang, R.; Yao, Y.; Wang, H. A Review of Approaches for Detecting Vulnerabilities in Smart Contracts within Web 3.0 Applications. Blockchains 2023, 1, 3–18. [Google Scholar] [CrossRef]
- Xue, Y.; Ma, M.; Lin, Y.; Sui, Y.; Ye, J.; Peng, T. Cross-contract static analysis for detecting practical reentrancy vulnerabilities in smart contracts. In Proceedings of the 35th IEEE/ACM International Conference on Automated Software Engineering, Virtual, 21–25 December 2020; pp. 1029–1040. [Google Scholar]
- Ghaleb, A.; Rubin, J.; Pattabiraman, K. eTainter: Detecting gas-related vulnerabilities in smart contracts. In Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual, 18–22 June 2022; pp. 728–739. [Google Scholar]
- Liu, Y.; Li, Y.; Lin, S.W.; Artho, C. Finding permission bugs in smart contracts with role mining. In Proceedings of the 31st ACM SIGSOFT International Symposium on Software Testing and Analysis, Virtual, 18–22 June 2022; pp. 716–727. [Google Scholar]
- Gao, J.; Liu, H.; Liu, C.; Li, Q.; Guan, Z.; Chen, Z. Easyflow: Keep ethereum away from overflow. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Montreal, QC, Canada, 25–31 May 2019; pp. 23–26. [Google Scholar]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.K.R. P4-to-blockchain: A secure blockchain-enabled packet parser for software defined networking. Comput. Secur. 2020, 88, 101629. [Google Scholar] [CrossRef]
- Yazdinejadna, A.; Parizi, R.M.; Dehghantanha, A.; Khan, M.S. A kangaroo-based intrusion detection system on software-defined networks. Comput. Netw. 2021, 184, 107688. [Google Scholar] [CrossRef]
- Robinson, P. Survey of crosschain communications protocols. Comput. Netw. 2021, 200, 108488. [Google Scholar] [CrossRef]
- Bhargavan, K.; Delignat-Lavaud, A.; Fournet, C.; Gollamudi, A.; Gonthier, G.; Kobeissi, N.; Kulatova, N.; Rastogi, A.; Sibut-Pinote, T.; Swamy, N.; et al. Formal verification of smart contracts: Short paper. In Proceedings of the 2016 ACM Workshop on Programming Languages and Analysis for Security, Vienna, Austria, 24 October 2016; pp. 91–96. [Google Scholar]
- Tambare, P.; Meshram, C.; Lee, C.C.; Ramteke, R.J.; Imoize, A.L. Performance measurement system and quality management in data-driven Industry 4.0: A review. Sensors 2021, 22, 224. [Google Scholar] [CrossRef]
- Javaid, M.; Haleem, A.; Singh, R.P.; Suman, R. Significance of Quality 4.0 towards comprehensive enhancement in manufacturing sector. Sensors Int. 2021, 2, 100109. [Google Scholar] [CrossRef]
- AlKhader, W.; Jayaraman, R.; Salah, K.; Sleptchenko, A.; Antony, J.; Omar, M. Leveraging blockchain and NFTs for quality 4.0 implementation in digital manufacturing. J. Manuf. Technol. Manag. 2023, 34, 1208–1234. [Google Scholar] [CrossRef]








| Title | Year | Work | Limitation |
|---|---|---|---|
| When Digital Economy Meets Web3.0: Applications and Challenges [14] | 2022 | A comprehensive examination of the integration of Web3 in the digital economy and its prospective evolution. | Primarily concentrates on the digital economy, with designed technologies lacking depth and specificity. |
| Web3.0: A Review And Research Agenda [15] | 2022 | A Web3 research overview with the use of Latent Dirichlet Allocation to identify key research topics. | There is a lack of specific analysis on the Web3 architecture. |
| Decentralized Society: Finding Web3’s Soul [16] | 2022 | Foundational Web3 technologies summarized to facilitate further research. | Offers a restricted viewpoint underlying social identity. |
| Web3: The Next Internet Revolution [17] | 2023 | Foundational Web3 technologies summarized to facilitate further research. | Offers a restricted viewpoint underlying blockchain. |
| Author | Year | Citation | Topic | Key Techniques | The Applications Involved |
|---|---|---|---|---|---|
| Kumar et al. [18] | 2020 | 202 | They proposed a smart healthcare system. | Blockchain, Smart Contracts | Metaverse |
| Belk et al. [19] | 2022 | 162 | They introduced a novel theoretical concept of ownership within the metaverse. | Blockchain, Non-Fungible Tokens | Metaverse |
| Wang et al. [20] | 2022 | 50 | They explored the last decade’s research, introducing the concept of DeMetaverses. | Blockchain | Metaverse, Decentralized Autonomous Organizations |
| Schlatt et al. [21] | 2022 | 45 | They proposed a blockchain-based solution to achieve the goal of ’know(ing) your customer’ without compromising customer privacy. | Blockchain, Self-Sovereign Identity, Digital Wallets | - |
| Qin et al. [22] | 2022 | 27 | They proposed a five-tier intelligent architecture for Decentralized Autonomous Organizations. | Blockchain, Smart Contracts | Decentralized Autonomous Organizations, Metaverse |
| Subramanian et al. [23] | 2022 | 19 | They developed a digital pathology system leveraging smart contracts and non-fungible tokens. | Blockchain, Decentralized Storage, Non-Fungible Tokens, Smart Contracts | - |
| Buldas et al. [24] | 2022 | 19 | They introduced a shared blockchain technology and developed the Alphabill platform. | Blockchain | Decentralized Finance |
| David Vidal-Tom´as [25] | 2023 | 45 | The author conducted a review of the existing metaverse economy and evaluated the metaverse economy of Web3. | Non-fungible tokens | Metaverse, Decentralized Finance |
| Solution | Platform | Token for Rewarding | Consensus Mechanism | File Structure | Gas |
|---|---|---|---|---|---|
| Filecoin | Blockchain with IPFS | Filecoin | PoRep and PoSt | Merkle Directed Acyclic Graph | Yes |
| Storj | Ethereum with Distributed Hash Table | Storj (ERC-20 token) | - | Encrypted file sharding | No |
| Sia | Blockchain | Siacoin | PoW | Encrypted file sharding | Yes |
| Project | Creation Methods | Language of Smart Contract | Main Platform | Field |
|---|---|---|---|---|
| ERC-721 NFT | ERC721 | Solidity | Ethereum | Artworks, games, digital collectibles |
| ERC-1155 NFT | ERC1155 | Solidity | Multi chain support, Ethereum compatible | Mass distribution of digital assets |
| Binance Smart Chain NFT | Standards of Binance Smart Chain | Solidity | Binance Smart Chain | Simple tokenization projects, digital collectibles |
| Flow (Dapper Labs) | Flow Protocol | Cadence | NBA Top Shot | Games, virtual assets |
| (+) Positive Impact | (−) Negative Impact | |
|---|---|---|
| Internal factors | Strengths (S) | Weaknesses (W) |
| (1) Decentralization and immutability | (1) Scalability and latency | |
| (2) User data ownership empowerment | (2) Unfriendly user interface | |
| (3) Equal access for users | (3) High gas price | |
| (4) Trust in trustless networks | (4) Digital divide | |
| (5) Information standardization across diverse public platforms | (5) Supervision lacking and social instability | |
| (6) Automated execution of smart contracts | (6) Numerous node dependencies of the front-end | |
| (7) Seamless interoperability among various platforms and applications | (7) Difficulty in restoring stored data on external pages | |
| (8) New business models | (8)Additional learning costs | |
| (9) A agile solution for community governance | (9) The significant resource consumption of PoW | |
| (10) A solution for identity authentication | ||
| External factors | Opportunities (O) | Threats (T) |
| (1) Blockchain Innovation | (1) Cross site tracking of users | |
| (2) Social trust crisis | (2) Regulatory challenges | |
| (3) Elimination of necessity of trust | (3) Vulnerability of smart contract | |
| (4) An increasingly complete developer ecosystem | ||
| (5) The escalating demand for data privacy | ||
| (6) Integration with Quality 4.0 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lai, Y.; Yang, J.; Liu, M.; Li, Y.; Li, S. Web3: Exploring Decentralized Technologies and Applications for the Future of Empowerment and Ownership. Blockchains 2023, 1, 111-131. https://doi.org/10.3390/blockchains1020008
Lai Y, Yang J, Liu M, Li Y, Li S. Web3: Exploring Decentralized Technologies and Applications for the Future of Empowerment and Ownership. Blockchains. 2023; 1(2):111-131. https://doi.org/10.3390/blockchains1020008
Chicago/Turabian StyleLai, Yiwei, Jingyi Yang, Mingzhe Liu, Yibei Li, and Shanlin Li. 2023. "Web3: Exploring Decentralized Technologies and Applications for the Future of Empowerment and Ownership" Blockchains 1, no. 2: 111-131. https://doi.org/10.3390/blockchains1020008
APA StyleLai, Y., Yang, J., Liu, M., Li, Y., & Li, S. (2023). Web3: Exploring Decentralized Technologies and Applications for the Future of Empowerment and Ownership. Blockchains, 1(2), 111-131. https://doi.org/10.3390/blockchains1020008








