Intelligent Security Sensors in Cloud Computing
A topical collection in Sensors (ISSN 1424-8220). This collection belongs to the section "Internet of Things".
Viewed by 34383
Share This Topical Collection
Editors
 Dr. Lidia Ogiela
Dr. Lidia Ogiela
 Dr. Lidia Ogiela
Dr. Lidia Ogiela
E-Mail
Website
Collection Editor
Head of Department of Cryptography and Cognitive Informatics, Pedagogical University of Krakow, Poland
Interests: cryptography, cognitive informatics, artificial intelligence, mathematical linguistics, biomedical engineering, pattern recognition, security systems, cloud computing
 Prof. Dr. Makoto Takizawa
Prof. Dr. Makoto Takizawa
 Prof. Dr. Makoto Takizawa
Prof. Dr. Makoto Takizawa
E-Mail
Website
Collection Editor
Department of Advanced Sciences, Hosei University, Tokyo, Japan
Interests: eco distributed systems, high-speed communication protocols, group communication protocols, distributed object systems, distributed database systems, distributed transaction management, fault-tolerant distributed systems, distributed systems security, role-based access control, transactional mobile agent systems, peer-to-peer (P2P) systems
Topical Collection Information
Dear Colleagues,
Overview:
In advanced data security protocols and IT systems, one of the most important paradigm are intelligent security approaches, used in data distribution processes and analysis. Such solutions allow not only to facilitate data analytics tasks, but also allow to perform intelligent and secure information distribution, interpretation, and development of new technologies and security approaches. Nowadays there is a great demand to efficiently store and analyze a huge amount of data, originated from distributed sensors, as well as expectation to forecasting activities and analyzes in cloud computing. Possibility of development of such intelligent sensors will be connected with timely activities and procedures dedicated to intelligent security in cloud computing technologies. These subjects, as well as others, connected with intelligent security protocols and technologies, security sensors and security protocols, will form the subject of ISSCC 2020 Topical Collection.
Topics
Topics of interest include, but are not limited to, the following scope:
- Security sensors in Cloud Computing
- Intelligent sensors in the Cloud
- New computational approaches for Cloud security
- Ambient intelligence for the Cloud
- New application of security sensors
- Innovative security and privacy protocols
- Evaluations, and application of security sensors
- Security and privacy approaches
- Computational intelligence in data and sensors analysis
- Cryptography and secret data management
- Advanced sensors in cryptography and steganography systems
Dr. Lidia Ogiela
Prof. Dr. Makoto Takizawa
Dr. Arcangelo Castiglione
Collection Editors
Manuscript Submission Information
Manuscripts should be submitted online at www.mdpi.com by registering and logging in to this website. Once you are registered, click here to go to the submission form. Manuscripts can be submitted until the deadline. All submissions that pass pre-check are peer-reviewed. Accepted papers will be published continuously in the journal (as soon as accepted) and will be listed together on the collection website. Research articles, review articles as well as short communications are invited. For planned papers, a title and short abstract (about 100 words) can be sent to the Editorial Office for announcement on this website.
Submitted manuscripts should not have been published previously, nor be under consideration for publication elsewhere (except conference proceedings papers). All manuscripts are thoroughly refereed through a single-blind peer-review process. A guide for authors and other relevant information for submission of manuscripts is available on the Instructions for Authors page. Sensors is an international peer-reviewed open access semimonthly journal published by MDPI.
Please visit the Instructions for Authors page before submitting a manuscript.
The Article Processing Charge (APC) for publication in this open access journal is 2600 CHF (Swiss Francs).
Submitted papers should be well formatted and use good English. Authors may use MDPI's
English editing service prior to publication or during author revisions.
Published Papers (8 papers)
Open AccessArticle
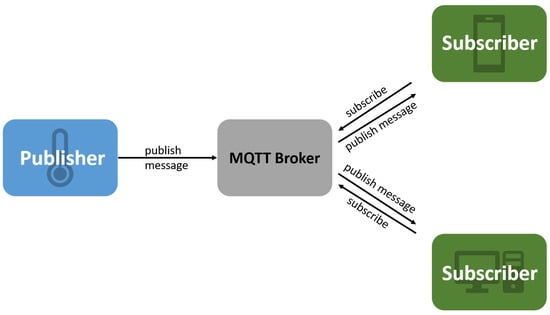
Assertive, Selective, Scalable IoT-Based Warning System
by
Ion-Dorinel Filip, Cristian-Mihai Iliescu and Florin Pop
Cited by 5 | Viewed by 3274
Abstract
With the evolution of technology, developed systems have become more complex and faster. Thirty years ago, there were no protocols or databases dedicated to developing and implementing IoT projects. We currently have protocols such as MQTT, AMQP, CoAP, and databases such as InfluxDB.
[...] Read more.
With the evolution of technology, developed systems have become more complex and faster. Thirty years ago, there were no protocols or databases dedicated to developing and implementing IoT projects. We currently have protocols such as MQTT, AMQP, CoAP, and databases such as InfluxDB. They are built to support a multitude of data from an IoT system and scale very well with the system. This paper presents the design and implementation of an IoT alert system that uses MQTT and InfluxDB to collect and store data. We design a scalable system to display assertive alerts on a Raspberry Pi. Each user can select a subset of alerts in our system using a web interface. We present a bibliographic study of SoTA, the proposed architecture, the challenges posed by such a system, a set of tests for the performance and feasibility of the solution, and a set of conclusions and ideas for further developments.
Full article
►▼
Show Figures
Open AccessArticle
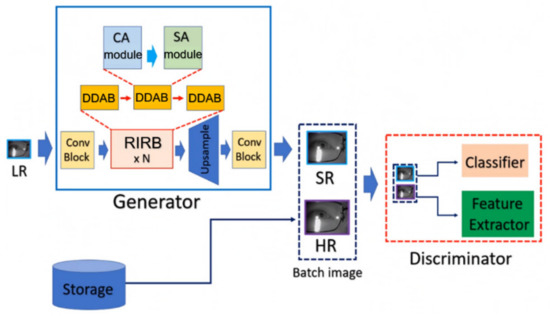
Super-Resolution Generative Adversarial Network Based on the Dual Dimension Attention Mechanism for Biometric Image Super-Resolution
by
Chi-En Huang, Yung-Hui Li, Muhammad Saqlain Aslam and Ching-Chun Chang
Cited by 9 | Viewed by 3568
Abstract
There exist many types of intelligent security sensors in the environment of the Internet of Things (IoT) and cloud computing. Among them, the sensor for biometrics is one of the most important types. Biometric sensors capture the physiological or behavioral features of a
[...] Read more.
There exist many types of intelligent security sensors in the environment of the Internet of Things (IoT) and cloud computing. Among them, the sensor for biometrics is one of the most important types. Biometric sensors capture the physiological or behavioral features of a person, which can be further processed with cloud computing to verify or identify the user. However, a low-resolution (LR) biometrics image causes the loss of feature details and reduces the recognition rate hugely. Moreover, the lack of resolution negatively affects the performance of image-based biometric technology. From a practical perspective, most of the IoT devices suffer from hardware constraints and the low-cost equipment may not be able to meet various requirements, particularly for image resolution, because it asks for additional storage to store high-resolution (HR) images, and a high bandwidth to transmit the HR image. Therefore, how to achieve high accuracy for the biometric system without using expensive and high-cost image sensors is an interesting and valuable issue in the field of intelligent security sensors. In this paper, we proposed DDA-SRGAN, which is a generative adversarial network (GAN)-based super-resolution (SR) framework using the dual-dimension attention mechanism. The proposed model can be trained to discover the regions of interest (ROI) automatically in the LR images without any given prior knowledge. The experiments were performed on the CASIA-Thousand-v4 and the CelebA datasets. The experimental results show that the proposed method is able to learn the details of features in crucial regions and achieve better performance in most cases.
Full article
►▼
Show Figures
Open AccessArticle
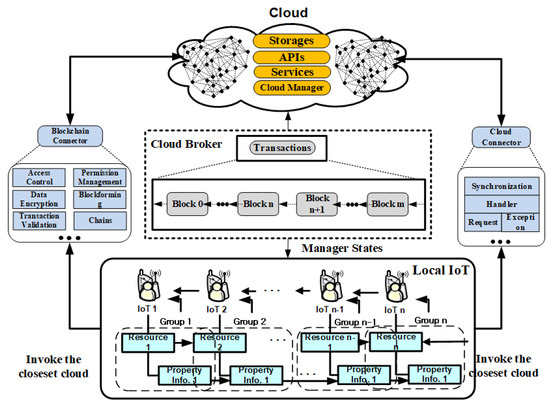
Blockchain Processing Technique Based on Multiple Hash Chains for Minimizing Integrity Errors of IoT Data in Cloud Environments
by
Yoon-Su Jeong
Cited by 8 | Viewed by 3155
Abstract
As IoT (Internet of Things) devices are diversified in the fields of use (manufacturing, health, medical, energy, home, automobile, transportation, etc.), it is becoming important to analyze and process data sent and received from IoT devices connected to the Internet. Data collected from
[...] Read more.
As IoT (Internet of Things) devices are diversified in the fields of use (manufacturing, health, medical, energy, home, automobile, transportation, etc.), it is becoming important to analyze and process data sent and received from IoT devices connected to the Internet. Data collected from IoT devices is highly dependent on secure storage in databases located in cloud environments. However, storing directly in a database located in a cloud environment makes it not only difficult to directly control IoT data, but also does not guarantee the integrity of IoT data due to a number of hazards (error and error handling, security attacks, etc.) that can arise from natural disasters and management neglect. In this paper, we propose an optimized hash processing technique that enables hierarchical distributed processing with an n-bit-size blockchain to minimize the loss of data generated from IoT devices deployed in distributed cloud environments. The proposed technique minimizes IoT data integrity errors as well as strengthening the role of intermediate media acting as gateways by interactively authenticating blockchains of n bits into n + 1 and n − 1 layers to normally validate IoT data sent and received from IoT data integrity errors. In particular, the proposed technique ensures the reliability of IoT information by validating hash values of IoT data in the process of storing index information of IoT data distributed in different locations in a blockchain in order to maintain the integrity of the data. Furthermore, the proposed technique ensures the linkage of IoT data by allowing minimal errors in the collected IoT data while simultaneously grouping their linkage information, thus optimizing the load balance after hash processing. In performance evaluation, the proposed technique reduced IoT data processing time by an average of 2.54 times. Blockchain generation time improved on average by 17.3% when linking IoT data. The asymmetric storage efficiency of IoT data according to hash code length is improved by 6.9% on average over existing techniques. Asymmetric storage speed according to the hash code length of the IoT data block was shown to be 10.3% faster on average than existing techniques. Integrity accuracy of IoT data is improved by 18.3% on average over existing techniques.
Full article
►▼
Show Figures
Open AccessCommunication
Influence of Features on Accuracy of Anomaly Detection for an Energy Trading System
by
Hoon Ko, Kwangcheol Rim and Isabel Praça
Cited by 5 | Viewed by 2690
Abstract
The biggest problem with conventional anomaly signal detection using features was that it was difficult to use it in real time and it requires processing of network signals. Furthermore, analyzing network signals in real-time required vast amounts of processing for each signal, as
[...] Read more.
The biggest problem with conventional anomaly signal detection using features was that it was difficult to use it in real time and it requires processing of network signals. Furthermore, analyzing network signals in real-time required vast amounts of processing for each signal, as each protocol contained various pieces of information. This paper suggests anomaly detection by analyzing the relationship among each feature to the anomaly detection model. The model analyzes the anomaly of network signals based on anomaly feature detection. The selected feature for anomaly detection does not require constant network signal updates and real-time processing of these signals. When the selected features are found in the received signal, the signal is registered as a potential anomaly signal and is then steadily monitored until it is determined as either an anomaly or normal signal. In terms of the results, it determined the anomaly with 99.7% (0.997) accuracy in
f(4)(S0) and in case
f(4)(REJ) received 11,233 signals with a normal or 171anomaly judgment accuracy of 98.7% (0.987).
Full article
►▼
Show Figures
Open AccessArticle
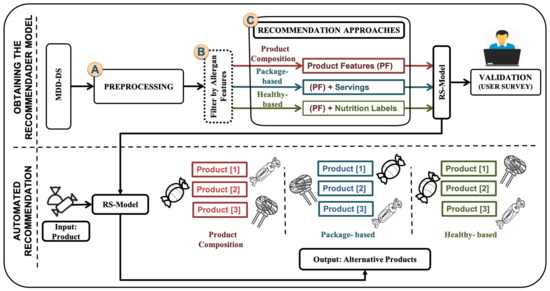
Multi-Criteria Recommendation Systems to Foster Online Grocery
by
Manar Mohamed Hafez, Rebeca P. Díaz Redondo, Ana Fernández Vilas and Héctor Olivera Pazó
Cited by 7 | Viewed by 4829
Abstract
With the exponential increase in information, it has become imperative to design mechanisms that allow users to access what matters to them as quickly as possible. The recommendation system (RS) with information technology development is the solution, it is an intelligent system. Various
[...] Read more.
With the exponential increase in information, it has become imperative to design mechanisms that allow users to access what matters to them as quickly as possible. The recommendation system (RS) with information technology development is the solution, it is an intelligent system. Various types of data can be collected on items of interest to users and presented as recommendations. RS also play a very important role in e-commerce. The purpose of recommending a product is to designate the most appropriate designation for a specific product. The major challenge when recommending products is insufficient information about the products and the categories to which they belong. In this paper, we transform the product data using two methods of document representation: bag-of-words (BOW) and the neural network-based document combination known as vector-based (Doc2Vec). We propose three-criteria recommendation systems (product, package and health) for each document representation method to foster online grocery shopping, which depends on product characteristics such as composition, packaging, nutrition table, allergen, and so forth. For our evaluation, we conducted a user and expert survey. Finally, we compared the performance of these three criteria for each document representation method, discovering that the neural network-based (Doc2Vec) performs better and completely alters the results.
Full article
►▼
Show Figures
Open AccessArticle
Modeling of Recommendation System Based on Emotional Information and Collaborative Filtering
by
Tae-Yeun Kim, Hoon Ko, Sung-Hwan Kim and Ho-Da Kim
Cited by 41 | Viewed by 5235
Abstract
Emotion information represents a user’s current emotional state and can be used in a variety of applications, such as cultural content services that recommend music according to user emotional states and user emotion monitoring. To increase user satisfaction, recommendation methods must understand and
[...] Read more.
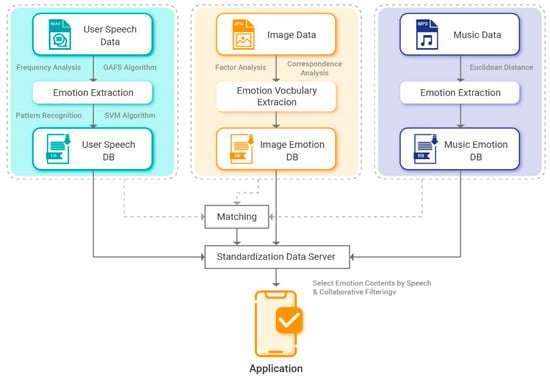
Emotion information represents a user’s current emotional state and can be used in a variety of applications, such as cultural content services that recommend music according to user emotional states and user emotion monitoring. To increase user satisfaction, recommendation methods must understand and reflect user characteristics and circumstances, such as individual preferences and emotions. However, most recommendation methods do not reflect such characteristics accurately and are unable to increase user satisfaction. In this paper, six human emotions (neutral, happy, sad, angry, surprised, and bored) are broadly defined to consider user speech emotion information and recommend matching content. The “genetic algorithms as a feature selection method” (GAFS) algorithm was used to classify normalized speech according to speech emotion information. We used a support vector machine (SVM) algorithm and selected an optimal kernel function for recognizing the six target emotions. Performance evaluation results for each kernel function revealed that the radial basis function (RBF) kernel function yielded the highest emotion recognition accuracy of 86.98%. Additionally, content data (images and music) were classified based on emotion information using factor analysis, correspondence analysis, and Euclidean distance. Finally, speech information that was classified based on emotions and emotion information that was recognized through a collaborative filtering technique were used to predict user emotional preferences and recommend content that matched user emotions in a mobile application.
Full article
►▼
Show Figures
Open AccessArticle
Research on Secure Debugging Interaction of Sensor Nodes Based on Visible Light Communication
by
Yuanchu Yin, Jiefan Qiu, Zhiqiang Li and Mingsheng Cao
Cited by 2 | Viewed by 2718
Abstract
When a wireless sensor node’s wireless communication fails after being deployed in an inaccessible area, the lost node cannot be repaired through a debugging interaction that relies on that communication. Visible light communication (VLC) as a supplement of radio wave communication can improve
[...] Read more.
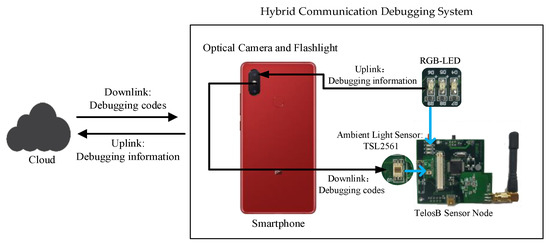
When a wireless sensor node’s wireless communication fails after being deployed in an inaccessible area, the lost node cannot be repaired through a debugging interaction that relies on that communication. Visible light communication (VLC) as a supplement of radio wave communication can improve the transmission security at the physical layer due to its unidirectional propagation characteristic. Therefore, we implemented a VLC-based hybrid communication debugging system (HCDS) based on VLC using smartphone and sensor node. For the system’s downlink, the smartphone is taken as the VLC gateway and sends the debugging codes to the sensor node by the flashlight. To improve the transmission efficiency of the downlink, we also propose a new coding method for source coding and channel coding, respectively. For the source coding, we analyze the binary instructions and compress the operands using bitmask techniques. The average compression rate of the binary structure reaches 84.11%. For the channel coding, we optimize dual-header pulse interval (DH-PIM) and propose overlapped DH-PIM (ODH-PIM) by introducing a flashlight half-on state. The flashlight half-on state can improve the representation capability of individual symbols. For the uplink of HCDS, we use the onboard LED of the sensor node to transmit feedback debugging information to the smartphone. At the same time, we design a novel encoding format of DH-PIM to optimize uplink transmission. Experimental results show that the optimized uplink transmission time and BER are reduced by 10.71% and 22%, compared with the original DH-PIM.
Full article
►▼
Show Figures
Open AccessCommunication
Imagechain—Application of Blockchain Technology for Images
by
Katarzyna Koptyra and Marek R. Ogiela
Cited by 26 | Viewed by 6659
Abstract
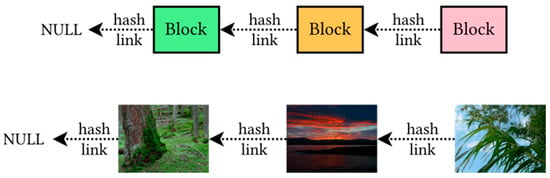
Imagechain is a cryptographic structure that chain digital images with hash links. The most important feature, which differentiates it from blockchain, is that the pictures are not stored inside the blocks. Instead, the block and the image are combined together in the embedding
[...] Read more.
Imagechain is a cryptographic structure that chain digital images with hash links. The most important feature, which differentiates it from blockchain, is that the pictures are not stored inside the blocks. Instead, the block and the image are combined together in the embedding process. Therefore, the imagechain is built from standard graphic files that may be used in the same way as any other image, but additionally, each of them contains a data block that links it to a previous element of the chain. The presented solution does not require any additional files except the images themselves. It supports multiple file formats and embedding methods, which makes it portable and user-friendly. At the same time, the scheme provides a high level of security and resistance to forgery. This is achieved by hashing the whole file with embedded data, so the image cannot be altered or removed from the chain without losing integrity. This article describes the basic concept of an imagechain together with building blocks and applications. The two most important issues are embedding methods and block structure.
Full article
►▼
Show Figures