1. Introduction
Some of the predictions made by quantum mechanics appear to be at odds with common sense. Yet quantum mechanics remains the most precisely tested and successful quantitative theory of nature. It is therefore believed that even if quantum mechanics is someday replaced, any successor will have to inherit at least some of its “preposterous” but highly predictive principles. Perhaps the most counter-intuitive quantum mechanical feature is
nonlocality [
1]: the correlations exhibited by remote parties may exceed those allowed by any local realistic model.
The mystery of nonlocality is not only why nature is as nonlocal as it is, but why nature is not
more nonlocal than it is. There are alternative
Non-Signaling theories which permit nonlocality beyond the quantum limit [
2,
3]; why doesn’t nature choose one of these theories over quantum mechanics? In
Section 1.1 we review several previously proposed explanations. This paper presents another explanation, from statistics.
In this paper we construct a protocol (a repeated oblivious transfer) which sends messages through a disconnected channel. We show that Alice can communicate nontrivial information to Bob via this protocol if and only if the maximal quantum mechanical violation of the Bell–CHSH inequality [
1,
4],
Tsirelson’s bound [
5], is exceeded. We thus provide a statistical explanation of this bound that is independent of the mathematical formalism of quantum mechanics.
We briefly recall the setting for the Bell–CHSH experiment.
Section 2 provides a more detailed account. A famous application of nonlocality is to construct an
1-2 oblivious transfer protocol between two distant agents (A)lice and (B)ob. Alice and Bob each hold a box. Alice’s box might, for example, contain one half of a singlet state of spin–
particles, with Bob’s box containing the other half [
1,
4]. In addition, Alice possesses a pair of bits
and
, each of which is a zero or a one. Using boolean algebra and her boxes (the protocol will be described later), Alice encodes her pair of bits into a single bit
which she sends across a classical channel to Bob. Bob wants to know the value either of
or of
, but Alice doesn’t know which of these Bob wants to know. Bob uses the received bit
, his box, and some boolean algebra to construct an estimate
for his desired bit
. See
Figure 2 later on.
What is the probability that Bob correctly estimates the bit he wishes to know? He has two possible sources of knowledge—the bit
he received from Alice, and some mysterious “nonlocal” correlation between his box and Alice’s. The strength of such a nonlocal coordination between two systems is captured by a parameter
called the
Bell–CHSH correlator. Bob’s probability of guessing the value of Alice’s bit correctly is
. The
Bell–CHSH inequality states that
in a world governed by classical (non-quantum) mechanics [
1,
4].
Nonlocality is the state of affairs in which the Bell–CHSH inequality is violated. To the best of our knowledge, real world physics is nonlocal. Over the years, the violation of the Bell–CHSH inequality has been measured in increasingly accurate and loophole-free experiments, culminating in celebrated loophole-free verifications [
6,
7,
8].
Thus, we know that
can exceed
. How large can
be? Tsirelson’s bound tells us that
cannot exceed
in a world described by quantum mechanics [
5]. This quantum bound on nonlocality:
has been tested experimentally, with the current state of the art being an experiment which has achieved a value of
c which is only
distant from Tsirelson’s bound [
9]. Such experimental evidence supports the contention that Tsirelson’s bound indeed holds true in the real world. Tsirelson’s result as presented in the original paper is a specifically quantum mechanical fact, following from the Hilbert-space mathematical formalism for quantum mechanics, for which there has been no good conceptual physical explanation. How fundamental is Tsirelson’s bound? Must this inequality also hold for any future theory which might someday supercede quantum mechanics [
10]? We are led to the following question:
Can we identify a plausible physical principle, independent of quantum mechanics (or independent of functional analysis), which is necessary and sufficient to guarantee that ? 1.1. Existing Principles
For the last two decades, people have searched for physical principles that bound nonlocality. It was initially expected that the physical principle of relativistic causality (no-signaling) itself restricts the strength of nonlocality [
11,
12,
13]. But then it was discovered that no-signaling theories may exist for which
. This led to the device-independent formalism of
No-Signaling (NS)–boxes [
2,
14] (see also [
3]). In particular, maximum violation of the Bell–CHSH inequality is achieved by
Popescu–Rohrlich (PR)–boxes which are consistent with relativistic causality.
So relativistic causality doesn’t limit nonlocality after all; Why then does nature not permit (
1) to be violated (as far as we know)? Several suggestions have been made. Superquantum correlations lead to violations of the Heisenberg uncertainty principle [
15,
16], which is another seemingly purely quantum result. PR–boxes would allow distributed computation to be performed with only one bit of communication [
17], which looks unlikely but doesn’t violate any known physical law. Similarly, in stronger-than-quantum nonlocal theories some computations exceed reasonable performance limits [
18]. The principle of
Information Causality [
19] shows that no sensible measure of mutual information exists between pairs of systems in superquantum nonlocal theories. Our approach is most directly comparable with Information Causality, with a conceptual difference being that we use variance of an efficient estimator, therefore Fisher information, whereas information causality uses mutual information (Shannon information). The relationship between our approach and theirs is the topic of
Section 6. Finally, it was shown that superquantum nonlocality does not permit local (non-nonlocal) physics to emerge in the limit of infinitely many microscopic systems [
20,
21].
1.2. Tsirelson’s Bound from a Statistical No-Signaling Condition
Here we show that Tsirelson’s bound follows from the following principle applied to a certain limiting Bell–CHSH setting:
Statistical No-Signaling: It is impossible to communicate a nontrivial message through a channel whose output is independent of its input.
Our strategy is to construct a channel whose input is a Bernoulli random variable
X of mean
and whose output is another Bernoulli random variable
Y (
Section 3.2). The construction of our channel is not new— it is a reinterpretation of the well-known van Dam protocol [
17]. Through the channel, Alice sends
samples
from
X, and at the other end Bob receives a set of values
.
We imagine as encoding a message, perhaps in the digits of its binary expansion. Bob’s task is to estimate . The following theorem states that he can do so if and only if Tsirelson’s bound fails.
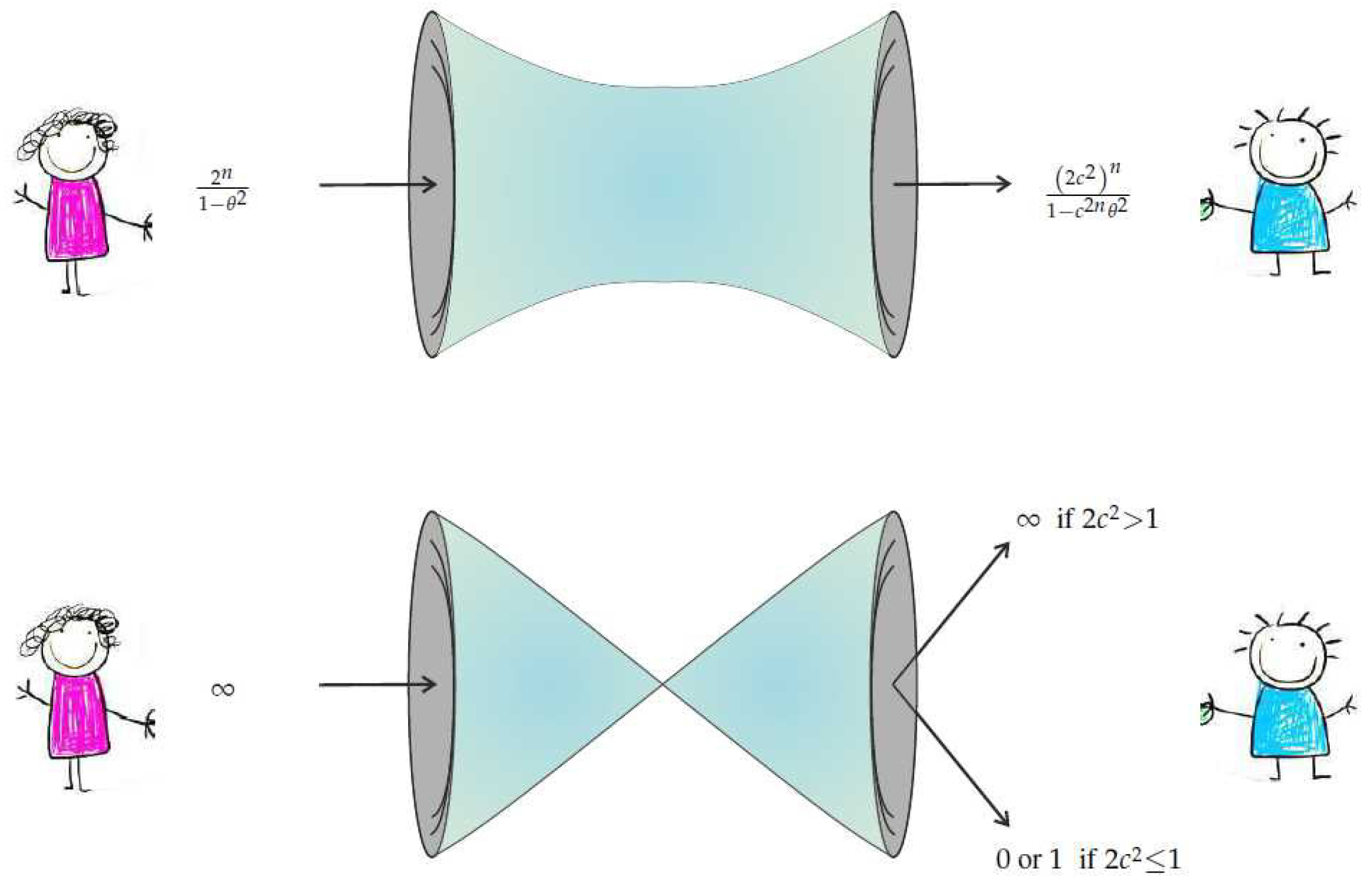
Theorem 1.1. - (1)
The channel from X to Y we construct is described by the conditional probability , where c is the Bell–CHSH correlator. Its output satisfies: In the limit it disconnects for (i.e., we can arrange that ).
- (2)
The unbiased estimator:for θ has variance: - (3)
The estimator isefficient, i.e., it has the minimal variance of any estimator of θ constructed from Bob’s set of samples for all .
The theorem is visually summarized by
Figure 1.
The theorem shows that failure of Tsirelson’s bound leads to failure of the following consequence of Statistical No-Signaling—Consequence of Statistical No-Signaling—In the above notation, if X and Y are independent, then no estimator constructed from has both mean and variance 0.
Section 5 shows that a violation of Uffink’s inequality [
22], a generalization of Tsirelson’s bound, also leads to the failure of the same consequence of Statistical No-Signaling. Uffink’s inequality is also known to be recovered by Information Causality [
23].
Theorem 1.1 is formulated as an asymptotic construction, but in practice a finite number of samples suffices because for any experimental setup there exists a nonzero minimal possible environmental noise level . By Theorem 1.1, is physically indistinguishable from when the absolute value of is less than . Since , we need trials. As an example, for a photon pair where is greater than or equal to the reduced Planck constant ℏ, we find that suffices to make physically indistinguishable from when . Thus, if we can still distinguish from for , we know that Tsirelson’s bound has been violated, and if not then it holds.
1.3. Organization of This Paper
Section 2 recalls the bipartite Bell experiment and exhibits the Bell–CHSH correlator
c as the correlator of a certain noisy symmetric channel.
Section 3 presents the van Dam protocol as an extension of the Bell–CHSH setup, and explain how it defines a noisy symmetric channel with correlator
.
Section 4 computes the means and variance of an estimator
for
, and proves that
is an efficient estimator.
Section 5 extends Theorem 1.1 to recover Uffink’s inequality [
22,
23] for anisotropic correlators from Statistical No-Signaling. Finally,
Section 6 discusses the relationship of Statistical No-Signaling with Information Causality.
3. The Van Dam Protocol as a Noisy Symmetric Channel
In this section we recall the construction of the van-Dam protocol [
17,
19]. We then reinterpret this protocol as underlying a noisy symmetric binary channel, as a special case of the construction of
Section 2. We compute its correlator, and establish the effect of noise on its classical component.
3.1. The Van Dam Protocol
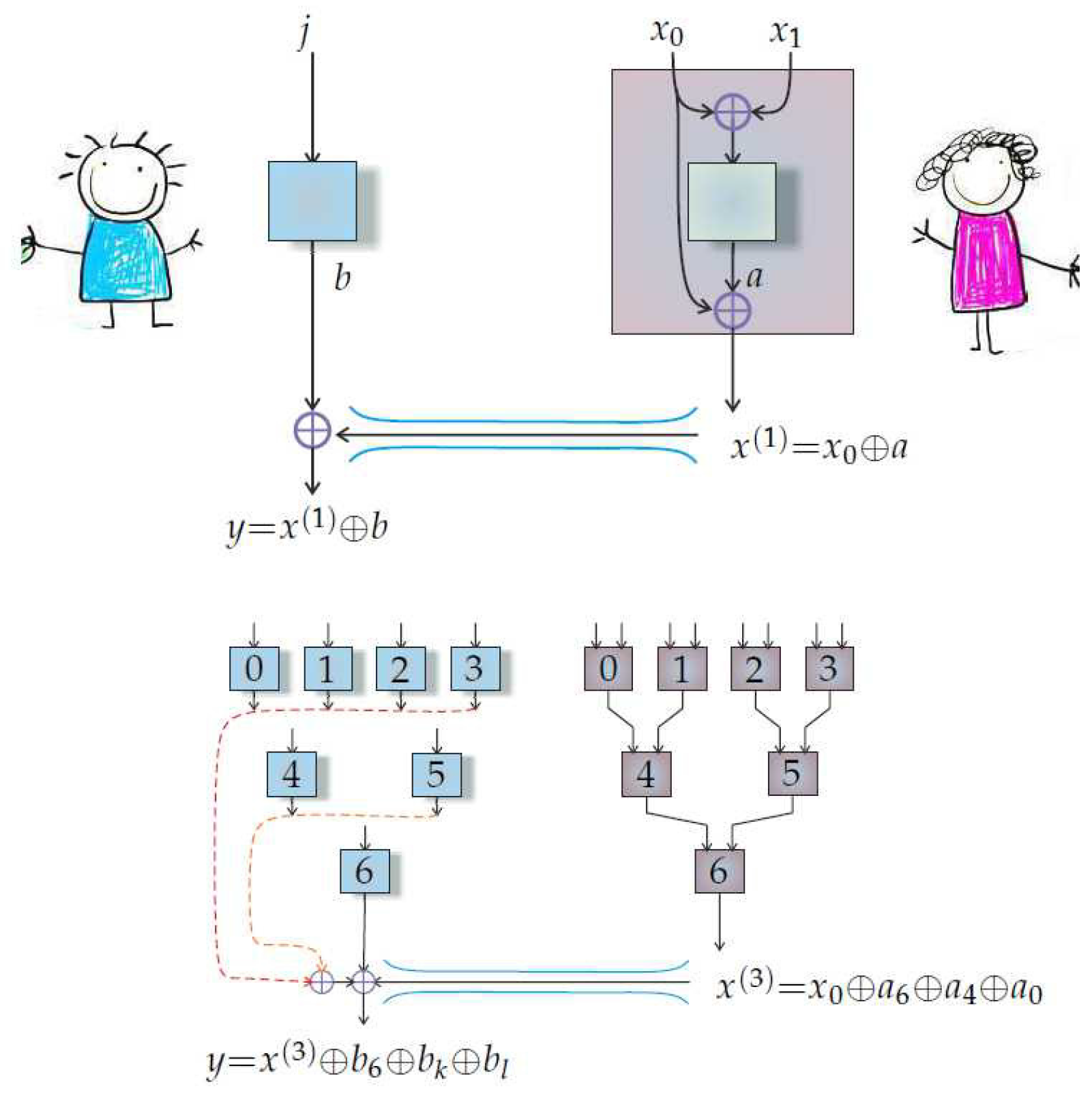
The van Dam protocol realizes an oblivious transfer protocol by means of a classical channel and a collection of NS-boxes. Each of Alice’s boxes has a corresponding box on Bob’s side, and different pairs of boxes are statistically independent. Suppose that Alice has in her possession the bits where , . Bob wishes to know the value of one of her bits. He may do so by specifying the address of the bit whose value he wishes to know via its binary address . For example, if then Bob may specify which of the bits to he wants by specifying a binary address, 00, 01, 10, or 11. Alice bits and Bob addresses are encoded into the inputs of NS-boxes following a particular protocol which is described next.
Alice uses outputs of boxes and choices of measuring device to determine choices of measuring device for other boxes. Such a procedure is called
wiring. The wiring of boxes on Alice side admits a recursive description which we now give. Let
denote the output of Alice’s
lth box on the
kth level for the input
i. We follow the convention that box outputs for the van Dam protocol are 0/1–valued (rather than
–valued) random variables. Let also:
Suppose that Alice wishes to encode
bits with her boxes. To do so, she first picks two boxes and computes:
This forms the first level in her construction. The second level then follows:
In this example there are only two levels and so is the bit which Alice transmits to Bob through the classical channel. In case where there will be n levels and thus is the bit Bob will receive from Alice.
Unbeknownst to Alice, Bob now decides which bit
he would like to know the value of. He takes its binary address
, and inserts
into all of his boxes whose counterparts are on the
k level on Alice’s side. He then uses the values
that he obtains, together with the bit
he received from Alice, to construct the decoding function:
The values (which boxes Bob uses) are determined by the binary address via the recursive formula for starting from .
The van Dam protocol we have described above is summarized in
Figure 2.
The probability that Bob will decode the correct value of the bit he desires is governed by the NS–box correlator
c. In general, decoding any bit out of
possible bits involves using
n pairs of NS boxes. Noting that an even number of errors,
, will cancel out in such a construction, we obtain the following expression [
19]:
3.2. Van Dam Protocol as a Symmetric Channel
This section describes the modification of the van Dam protocol that we use.
Alice has in her possession an information source that is a -valued Bernoulli random variable X whose mean is . Alice takes m iid samples, , from X and converts them into -valued bits, by mapping 0 to and 1 to 1. Alice and Bob repeat the van Dam protocol m times, once for each of Alice’s samples. Each time, Bob uses the protocol to estimate Alice’s bit, first , then , and so on until .
As in (
12), the van Dam protocol has a
memoryless property:
From this it follows that if Alice’s inputs
are iid then Bob’s outputs
are also iid. Therefore the set of
determines a Bernoulli random variable
Y. In this way, the van Dam protocol may be viewed as a symmetric binary channel whose input is
X and whose output is
Y. By (
11) the channel correlator is:
We generalize slightly, for the purpose of treating the
case in the next section. Suppose that Alice’s bits are contaminated with noise and therefore might be flipped once injected into her boxes. Let
be the probability that the bit
is flipped where
. In this case the corresponding channel correlator (
14) is
, which follows from (
4) and:
where
underlies the channel defined by the ordinary van Dam protocol, and
is the probability of
having been flipped.
3.3. The Van Dam Channel Disconnects in the Limit
If
or
then it follows that:
Therefore, in the
limit:
Combining (
17) with (
18) gives:
Thus X and Y are statistically independent in the limit, proving the first part of Theorem 1.1.
5. Uffink’s Inequality from Statistical No-Signalling
The basic protocol in
Section 3 assumes all box correlators are identical in absolute value. When this assumption is relaxed, Statistical No-Signaling leads to Uffink’s inequality, which is a necessary condition for quantum mechanical Bell-CHSH correlators [
22,
23]. Our approach is based on evaluating the total Fisher information
gained by Bob in
trials of the experiment.
Suppose that the mean of Alice’s bits,
, is
for even
i, and
otherwise. Consider now a pair of NS-boxes with correlators,
. The channel underlying the van Dam protocol in this case is described by
where
is Bob’s guess of Alice’s bit
. It now follows that
For simplicity, assume that
. It can now be verified that for a
n-level construction in the van Dam protocol
where
. According to (
32) the Fisher information about
contained in
is
Assuming
, Bob’s total amount of information about
in
trials is
for large
n. As before, the underlying channel asymptotically disconnects for
in the
limit. Statistical No-Signaling dictates that in this case the variance of Bob’s estimator
, which holds if and only if Uffink’s inequality holds [
22],
6. Relation to Information Causality
Of previous non-quantum justifications of Tsirelson’s bound, Information Causality (IC) is perhaps the closest to Statistical No-Signalling [
19]. IC is also stated as a limit on communication:
Information gain that Bob can reach about a previously unknown to him data set of Alice, by using all his local resources and m classical bits communicated by Alice, is at most m bits.IC is formally a restriction on the classical channel capacity. Detecting violation of this principle therefore requires the utilization of nonlocal resources, which the authors achieve through the application of IC to the van Dam protocol, that is the same communication protocol used in this paper.
The Information Causality quantity
I is defined as the Shannon mutual information of Alice’s input and Bob’s output given the value of the single bit transmitted in the van Dam protocol. IC holds if
and is violated if
. At the end of the supplementary section of [
19], the following expression for the IC quantity is obtained:
where
as in (
4). In the symmetric setting,
, and for
, Equations (
39) and (
32) combine to yield:
In particular, in the
limit, if
then
implying that
. Thus, violation of Statistical No-Signaling implies violation of IC. Conversely, as (
39) is an inequality, it is unknown whether Tsirelson’s bound being satisfied implies
(IC for the van Dam protocol), although, by our main theorem, it does imply
(Statistical No-Signaling for the van Dam protocol).