BARI+: A Biometric Based Distributed Key Management Approach for Wireless Body Area Networks
Abstract
:1. Introduction
1.1. Background
1.2. Motivation and Problem Statement
1.3. Main Contributions
2. Related Work
3. System Model and Assumptions
4. BARI+
4.1. Initial Deployment
4.2. Re-keying
4.3. Node Addition
5. Analysis and Comparison
5.1. Storage Overhead
5.2. Communication Overhead
5.3. Security Analysis
5.3.1. Authentication
5.3.2. Confidentiality
5.3.3. Forward Secrecy
5.3.4. Replay Attacks
5.3.5. Node Compromise
5.3.6. Routing Attacks
5.3.7. Other Attacks
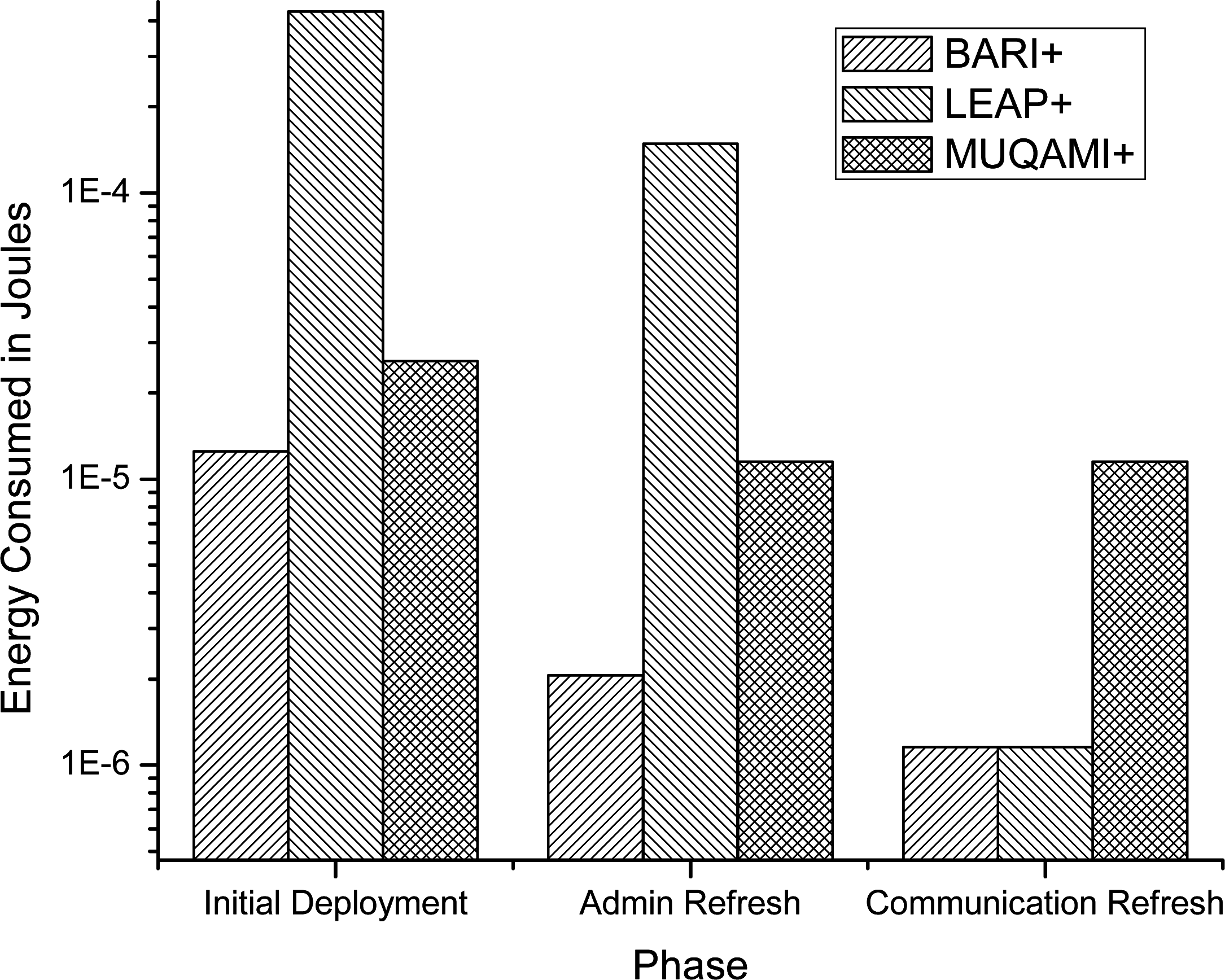
6. Simulation Results
7. Conclusions and Future Work
Acknowledgments
References
- Tilak, S.; Abu-Ghazaleh, N.; Heinzelman, W. A taxonomy of wireless microsensor network models. ACM Mobile Comput. Commun 2002, 6, 1–8. [Google Scholar]
- Dierks, T.; Allen, C. The TLS Protocol Version 1.0; The Internet Society: Reston, VA, USA, January 1999; RFC 2246. [Google Scholar]
- Kohl, J.; Neuman, C. The Kerberos Network Authentication Service (V5); The Internet Society: Reston, VA, USA, September 1993; RFC 1510. [Google Scholar]
- Zhu, S.; Setia, S.; Jajodia, S. LEAP+: Efficient security mechanisms for large-scale distributed sensor networks. ACM Trans. Sen. Netw 2006, 2, 500–528. [Google Scholar]
- Younis, M.F.; Ghumman, K.; Eltoweissy, M. Location-aware combinatorial key management scheme for clustered sensor networks. IEEE Trans. Parallel Distrib. Syst 2006, 17, 865–882. [Google Scholar]
- Raazi, S.M.K.; Lee, H.; Lee, S.; Lee, Y.K. MUQAMI+: A scalable and locally distributed key management scheme for clustered sensor networks. Annals Telecommun 2010, 65, 101–116. [Google Scholar]
- Raazi, S.M.K.; Lee, S.; Lee, Y.K. TIMAR: An efficient key management scheme for ubiquitous health care environments. Proceedings of the 5th International ICST Mobile Multimedia Communications Conference (Mobimedia’09), London, UK, September 7–9, 2009; pp. 1–7.
- Otto, C.; Milenkovic, A.; Sanders, C.; Jovanov, E. System architecture of a wireless body area sensor network for ubiquitous health monitoring. J. Mob. Multimed 2006, 1, 307–326. [Google Scholar]
- Szczepanski, J.; Wajnryb, E.; Amigó, J.M.; Sanchez-Vives, M.V.; Slater, M. Biometric random number generators. Comput. Secur 2004, 23, 77–84. [Google Scholar]
- Poon, C.; Zhang, Y.; Bao, S. A novel biometrics method to secure wireless body area sensor networks for telemedicine and m-health. IEEE Commun. Mag 2006, 44, 73–81. [Google Scholar]
- Cherukuri, S.; Venkatasubramanian, K.K.; Gupta, E.K.S. BioSec: A biometric based approach for securing communication. Proceedings of Wireless Networks of Biosensors Implanted in the Human Body, Workshop on Wireless Security and Privacy (WiSPr), International Conference on Parallel Processing Workshops, Kaohsiung, Taiwan, October 6–9, 2003.
- Venkatasubramanian, K.K.; Gupta, S.K.S. Security for Pervasive Health Monitoring Sensor Applications. Proceedings of the 4th International Conference on Intelligent Sensing and Information Processing (ICISIP’06), Kunming, Yunnan Province, China, August 16–19, 2006; pp. 197–202.
- Bui, F.M.; Hatzinakos, D. Biometric methods for secure communications in body sensor networks: resource-efficient key management and signal-level data scrambling. EURASIP J. Adv. Signal Process 2008, 2008. [Google Scholar] [CrossRef]
- Falck, T.; Baldus, H.; Espina, J.; Klabunde, K. Plug ’n play simplicity for wireless medical body sensors. Mob. Netw. Appl 2007, 12, 143–153. [Google Scholar]
- Raazi, S.M.K.; Lee, H.; Lee, S.; Lee, Y.K. BARI: A distributed key management approach for wireless body area networks. In CIS (2); IEEE Computer Society: Washington, DC, USA, 2009; pp. 324–329. [Google Scholar]
- Li, G.; He, J.; Fu, Y. A hexagon-based key predistribution scheme in sensor networks. Proceedings of the 2006 International Conference on Parallel Processing Workshops (ICPPW’06), Columbus, OH, USA, August 14–18, 2006; IEEE Computer Society: Washington, DC, USA, 2006; pp. 175–180. [Google Scholar]
- Chan, H.; Perrig, A.; Song, D. Random Key Predistribution Schemes for Sensor Networks. Proceedings of the 2003 IEEE Symposium on Security and Privacy (SP’03), Berkeley, CA, USA, May 11–14, 2003; IEEE Computer Society: Washington, DC, USA, 2003; pp. 197–213. [Google Scholar]
- Du, W.; Deng, J.; Han, Y.S.; Varshney, P.K. A pairwise key pre-distribution scheme for wireless sensor networks. Proceedings of the 10th ACM Conference on Computer and Communications Security (CCS’03), Washington, DC, USA, October 27–30, 2003; ACM: New York, NY, USA, 2003; pp. 42–51. [Google Scholar]
- Eschenauer, L.; Gligor, V.D. A key-management scheme for distributed sensor networks. Proceedings of the 9th ACM Conference on Computer and Communications Security (CCS’02), Washington, DC, USA, November 18–22, 2002; ACM: New York, NY, USA, 2002; pp. 41–47. [Google Scholar]
- Çamtepe, S.A.; Yener, B. Combinatorial design of key distribution mechanisms for wireless sensor networks. IEEE/ACM Trans. Netw 2007, 15, 346–358. [Google Scholar]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A link layer security architecture for wireless sensor networks. Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys’04), Baltimore, MD, USA, November 3–5, 2004; ACM: New York, NY, USA, 2004; pp. 162–175. [Google Scholar]
- Shaikh, R.; Lee, S.; Khan, M.; Song, Y. LSec: Lightweight security protocol for distributed wireless sensor networks. Proceedings of the 11th IFIP International Conference on Personal Wireless Communications (PWC’06), Albacete, Spain, September 20–22, 2006; 4217, pp. 367–377.
- Paek, K.J.; Kim, J.; Hwang, C.S.; Song, U.S. An energy-efficient key management protocol for large-scale wireless sensor networks. Proceedings of the 2007 International Conference on Multimedia and Ubiquitous Engineering (MUE’07), Seoul, Korea, April 26–28, 2007; IEEE Computer Society: Washington, DC, USA, 2007; pp. 201–206. [Google Scholar]
- Qiang, H.; Johnas, C.; Hisashi, K.; Bede, L.; Jinyun, Z. Fast authenticated key establishment protocols for self-organizing sensor networks. Proceedings of the 2nd ACM International Conference on Wireless Sensor Networks and Applications (WSNA’03), San Diego, CA, USA, September 19, 2003; ACM: New York, NY, USA, 2003; pp. 141–150. [Google Scholar]
- Kotzanikolaou, P.; Magkos, E.; Vergados, D.; Stefanidakis, M. Secure and practical key establishment for distributed sensor networks. In Security and Communication Networks; Wiley-InterScience: Malden, MA, USA, 2009. [Google Scholar]
- Eltoweissy, M.; Heydari, M.H.; Morales, L.; Sudborough, I.H. Combinatorial optimization of group key management. J. Netw. Syst. Manage 2004, 12, 33–50. [Google Scholar]
- Dini, G.; Savino, I.M. An efficient key revocation protocol for wireless sensor networks. Proceedings of the 2006 International Symposium on World of Wireless, Mobile and Multimedia Networks (WOWMOM’06), Buffalo, New York, NY, USA, June 26–29, 2006; IEEE Computer Society: Washington, DC, USA, 2006; pp. 450–452. [Google Scholar]
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar]
- Moharram, R.; Mukkamala, R.; Eltoweissy, M. TKGS: Threshold-based key generation scheme for wireless ad hoc networks. Proceedings of IEEE International Conference on Computer Communication and Networking (ICCCN’04), Chicago, IL, USA, October 2004.
- Venkatasubramanian, K.; Banerjee, A.; Gupta, S. Plethysmogram-based secure inter-sensor communication in Body Area Networks. Proceedings of Military Communications Conference (MILCOM 2008), San Diego, CA, USA, November 17–19, 2008; pp. 1–7.
- Banerjee, A.; Venkatasubramanian, K.; Gupta, S.K.S. Challenges of implementing cyber-physical security solutions in body area networks. Proceedings of the 4th International Conference on Body Area Networks (BodyNets’09), Getty Center, Los Angeles, CA, USA, April 1–3, 2009; ICST: Brussels, Belgium, 2009; pp. 1–8. [Google Scholar]
- Wang, Y.; Attebury, G.; Ramamurthy, B. A survey of security issues in wireless sensor networks. IEEE Commun. Surv. Tutor 2006, 8, 2–23. [Google Scholar]
- Seetharam, D.; Rhee, S. An efficient pseudo random number generator for low-power sensor networks. Proceedings of the 29th Annual IEEE International Conference on Local Computer Networks (LCN’04), Tampa, FL, USA, November 16–18, 2004; IEEE Computer Society: Washington, DC, USA, 2004; pp. 560–562. [Google Scholar]
- Xing, G.; Lu, C.; Zhang, Y.; Huang, Q.; Pless, R. Minimum power configuration in wireless sensor networks. Proceedings of the 6th ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc’05), Urbana-Champaign, IL, USA, May 25–27, 2005; ACM: New York, NY, USA, 2005; pp. 390–401. [Google Scholar]
- Venugopalan, R.; Ganesan, P.; Peddabachagari, P.; Dean, A.; Mueller, F.; Sichitiu, M. Encryption overhead in embedded systems and sensor network nodes: modeling and analysis. Proceedings of the 2003 International Conference on Compilers, Architecture and Synthesis for Embedded Systems (CASES’03), San Jose, CA, USA, October 30–November 1, 2003; ACM: New York, NY, USA, 2003; pp. 188–197. [Google Scholar]





| WBAN | WSN | |
|---|---|---|
| Scale | Small scale (Number of nodes may not exceed 20) | Large scale (Number of nodes may exceed even 1,000) |
| Size of Operational Area | Very small (Size of human body). All nodes may be in communication range of each other | Spans area like battlefields or natural habitat large |
| Human Intervention | Possible rather inevitable in some cases | Not possible in most cases |
| Key Management Support from application | Yes, Sensor nodes need not generate random numbers | No |
| WBAN | WSN | |
|---|---|---|
| Message Integrity | Required | Required |
| Node Authentication | Required | Required |
| Prevention from Eavesdropping | Required | Required |
| Node eviction through software | Not necessary | Required |
| Strategies to prevent routing attacks | Not required | Required |
| Prevention of attack propagation | Not required | Required |
| WSN | Wireless Sensor Network |
| WBAN | Wireless Body Area Network |
| MS | Medical Server |
| PS | Personal Server |
| SNi | Sensor Node i |
| Key shared between Node i and the MS. It is preloaded in every node and refreshed whenever it is used | |
| Basic Key of Node i shared with the PS. It is preloaded in every node and is refreshed whenever it is used | |
| Kcomm | Communication Key |
| Administrative Key i | |
| mi | Message number i in a particular communication sequence |
| EK{A|B} | Values A and B are put together in a block/chunk and then the chunk is encrypted using Key K |
| Personal Server | Sensor Node | |
|---|---|---|
| MUQAMI+ | {z × {[l × (k + m)] + r − (k + m) + 2}} + (4 × r) | (z × ((k + 4) + [(2 × (l − 1) × (k + m))/r])) |
| LEAP+ | z × (r + 2) | z × (r + 2) |
| BARI+ | [(r + 2) × z] + (4 × r) | (4 × z) + 4 |
| Personal Server | Sensor Node | |
|---|---|---|
| MUQAMI+ | r | 1 |
| LEAP+ | 2 × (r + 1) | 2 × r + 1 |
| BARI+ | 1 | 1 |
| Personal Server | Sensor Node | |
|---|---|---|
| MUQAMI+ | k + m | (k + m)/r |
| LEAP+ | 1 | − |
| BARI+ | 1 | − |
| Personal Server | Sensor Node | |
|---|---|---|
| MUQAMI+ | (k + m) × (1 + (1/l)) | ((k + m)/r) × (1 + (1/l)) |
| LEAP+ | r | r |
| BARI+ | ((2 × y) + 1)/r | 1/r |
© 2010 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open-access article distributed under the terms and conditions of the Creative Commons Attribution license http://creativecommons.org/licenses/by/3.0/.
Share and Cite
Raazi, S.M.K.-u.-R.; Lee, H.; Lee, S.; Lee, Y.-K. BARI+: A Biometric Based Distributed Key Management Approach for Wireless Body Area Networks. Sensors 2010, 10, 3911-3933. https://doi.org/10.3390/s100403911
Raazi SMK-u-R, Lee H, Lee S, Lee Y-K. BARI+: A Biometric Based Distributed Key Management Approach for Wireless Body Area Networks. Sensors. 2010; 10(4):3911-3933. https://doi.org/10.3390/s100403911
Chicago/Turabian StyleRaazi, Syed Muhammad Khaliq-ur-Rahman, Heejo Lee, Sungyoung Lee, and Young-Koo Lee. 2010. "BARI+: A Biometric Based Distributed Key Management Approach for Wireless Body Area Networks" Sensors 10, no. 4: 3911-3933. https://doi.org/10.3390/s100403911
APA StyleRaazi, S. M. K.-u.-R., Lee, H., Lee, S., & Lee, Y.-K. (2010). BARI+: A Biometric Based Distributed Key Management Approach for Wireless Body Area Networks. Sensors, 10(4), 3911-3933. https://doi.org/10.3390/s100403911





